IT_Security_Frameworks 2
advertisement

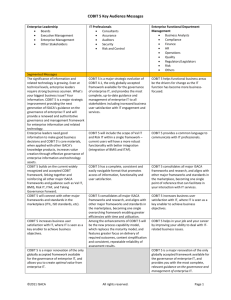
IT Security Frameworks ACG 6415 SPRING 2012 KRISTIN DONOVAN & BETH WILDMAN IT Security Frameworks Governance Framework – specify how to do security planning and implementation Multiple framework exists CobIT ISO/IEC 27000 COSO Why are IT Security Frameworks needed? Sarbanes-Oxley Act of 2002 (SOX) Section 404 – public companies must use an internal control framework and perform annual assessments No specific framework is required PCAOB Audit Standard No. 2 A control framework should be used to test the effectiveness of accurate financial reporting Information can be the most valuable asset a company has Two Popular IT Security Frameworks COBIT & ISO 27000 FAMILY CobIT Control Objectives for Information and Related Technology Developed in conjunction with the “Big Four” accounting firms Published by the IT Governance Institute Broad framework to implement IT controls CobIT Focuses on four areas of control Planning and Organization (Plan) Acquisition and Implementation (Do) Delivery and Support (Check) Monitoring (Correct) 34 high level control objectives 318 detailed control objectives CobIT Maturity Model Tool for management to go through the company’s current IT process and determine if they are effective or non-existent Assists in determining which areas require more effort Once the environment has been assessed, management can develop: Critical success factors Key performance indicators Key goal indicators CobIT Plan and Organize Necessary to ensure objectives of “Acquire & Implement” and “Delivery & Support” are met Establish the corporate vision Determine level of acceptable risk Focuses on the best way to implement the IT structure CobIT Plan and Organize Control Objectives 1. PO1 – Define a strategic IT plan 2. PO2 – Define the information architecture 3. PO3 – Determine technological direction 4. PO4 – Define the IT processes, organization, and relationships 5. PO5 – Manage the IT investment 6. PO6 – Communicate management aims and direction 7. PO7 – Manage IT human resources 8. PO8 – Manage quality 9. PO9 – Assess and manage IT risks 10. PO10 – Manage projects CobIT Acquire and Implement After planning is completed, the company must determine how to implement the new internal control process Can involve acquiring new technologies CobIT Acquire and Implement Control Objectives 1. AI1 – Identify automated solutions 2. AI2 – Acquire and maintain application software 3. AI3 – Acquire and maintain technology infrastructure 4. AI4 – Enable operation and use 5. AI5 – Procure IT resources 6. AI6 – Manage changes 7. AI7 – Install and accredit solutions and changes CobIT Deliver and Support Controls cost Guarantees the three initiatives of confidentiality, availability, and integrity are in place Ensures new controls are maintained CobIT Deliver and Support Control Objectives 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. DS1 – Define and manage service levels DS2 – Manage third party services DS3 – Manage performance and capacity DS4 – Ensure continuous service DS5 – Ensure systems security DS6 – Indentify and allocate costs DS7 – Educate and train users DS8 – Manage service desk incidents DS9 – Manage the configuration DS10 – Manage problems DS11 – Manage data DS12 – Manage the physical environment DS13 – Manage operations CobIT Monitor and Evaluate Measures if the controls implemented are sufficient Assurance that the company is meeting regulatory requirements Attends to the issue of ongoing evaluation CobIT Monitor and Evaluate Control Objectives ME1 – Monitor and evaluate IT performance ME2 – Monitor and evaluate internal controls ME 3- Ensure compliance with external requirements ME4 – Provide IT governance CobIT Broad framework, covering a large range of internal controls Does not give specific ways to make the companies information more secure ISO 27000 Series Issued by the International Standards Organization Popular globally, used by companies within the US and those abroad Includes multiple standards 27001 27002 27003 27004 27005 27006 27007 27008 ISO 27000 Series ISO 27001 “Specifies the requirements for establishing, implementing, operating, monitoring, reviewing, maintaining, and improving a documented Information Security Management System.” ISO ISO 27002 Focuses on information security and lists controls and control mechanisms which can be implemented to comply with ISO 27001 ISO 27000 Series ISO 27002 Covers 11 main areas of information security management 1. Security Policy – creating policies based on the organization’s needs 2. Organization of Information Security – managing of the security infrastructure 3. Asset Management – assigning responsibility for assets & physical security of the assets 4. Human Resource Security – personnel screening, code of conduct, training, and a process to address violations 5. Physical & Environmental Security – analyzing the environment, securing physical perimeter, and appropriate controls ISO 27000 Series ISO 27002 6. Communications and Operations Management - ensures correct and secure operations of assets 7. Access Control – “Properly protect access to an organization’s information, such as controls required to combat hacker attempts and other malicious attempts to access organization networks and information.” –Wallace 8. Information Systems Acquisition, Development, & Maintenance – discusses security requirements needed 9. Information Security Incident Management – plan for reporting and managing security events, incidents, and weaknesses ISO 27000 Series ISO 27002 10. Business Continuity Management – plans to address disruptions in normal operations and ongoing reassessment of plans 11. Compliance – “is intended to ensure that the organization avoids breaches of any criminal or civil law, as well as any statutory, regulator or contractual obligations, and of any security requirements.” - Calder ISO 27000 Series If all controls are implemented properly the company with be in compliance with SOX (in regards to IT security) Focuses solely on IT security CobIT vs. ISO 27000 Series Compare Both relate to IT controls Created based on past experience Continuously refined Contrast CobIT is a broad framework on how to implement internal controls ISO focuses exclusively on IT security Combination of CobIT & ISO 27000 provides an organization the best IT security. ISO 27000 and CobIT Mapping IT Governance institute has created a mapping between ISO 27000 and CobIT Links ISO 27000 control objectives to each dimension in the CobIT framework Results in a framework is high level enough to be integrated with IT governance and overall corporate governance Also detailed enough to provide mangers with the necessary steps to implement these controls ISO 27000 and CobIT Mapping CobIT: Deliver & Support 5.2 Relates to identification, access, and authorization “The logical access to and use of IT computing resources should be restricted by the implementation of adequate identification, authentication and authorization mechanisms, linking users and resources with access rules.” (IT Governance, COBIT Mapping) ISO 27000 and CobIT Mapping ISO objectives (listed in parenthesis next to detail below) state exactly what should be done to meet the requirements of COBIT DS5.2 Access of third parties should be controlled (4.2). Adequate privilege management should be included in application systems. Authorizations should be documented and follow a defined process (9.2.2). Passwords should be used for authentication. Passwords should be given to identified users in a secure manner and not in unprotected electronic mail messages (9.2.3). Access controls to internal and external networked services should be in place (9.4). ISO 27000 and CobIT Mapping User authentication for external connections should be controlled. Access restrictions should be based on a risk assessment. Authentication should consider hardware tokens, challenge/response protocols, dial-back or other mechanisms (9.4.3). Authentication mechanisms should be based on node authentication, if applicable (9.4.4). Access controls (e.g., key locks) should ensure that only required access can be obtained. This should include procedures and arrangements (9.4.5). Special access controls should be in place for shared networks (9.4.7). Identity should be verified as part of operation system access control. Identification of the user’s location should be considered (9.5). ISO 27000 and CobIT Mapping Connection to specific locations should be based on automatic terminal identification, when appropriate (9.5.1). Requirements for terminal logon procedures (e.g., maximum number of unsuccessful logon attempts) provided in the ISO standard should be considered (9.5.2). A unique user ID should be required for all individuals. Users’ privileges should not be identifiable by the user ID. A shared user ID should be used only when a clear business case exists. Identification and authentication can be based on passwords, biometric technologies or a combination of technologies (9.5.3). A good password management system raises the quality of passwords and should be implemented. Requirements for password management systems are provided in the ISO standard (9.5.4). Access should be ended after defined time-out delay. Alternatively, screen savers that prevent unauthorized access to terminals can be used (9.5.7). Conclusion SOX strong focus on internal controls has required organizations to implement an IT governance framework Companies must review and report on internal controls with management and external auditors A combination of CobIT and ISO 27000 series is the best way to ensure compliance