JennisShrestha_Presentation
advertisement

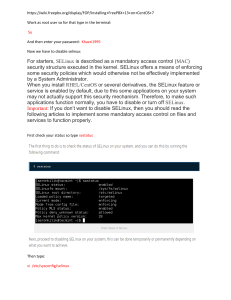
JENNIS SHRESTHA CSC 345 April 22, 2014 Contents Introduction History Flux Advanced Security Kernel Mandatory Access Control Policies MAC Vs DAC Features Distribution Conclusion Introduction Security-Enhanced Linux(SELinux) is a Linux kernel security module that provides the mechanism for supporting access control security policies including United States Department of Defense style mandatory access controls (MAC). Implements Flux Advanced Security Kernel to bring MAC into use in Linux. History Original primary Developer – The United States National Security Agency First version released on Dec 22, 2000 Significant Contributors – Network Associates, Red Hat, Secure Computing Corporation, Tresys Technology and Trusted Computer Solutions Flux Advanced Security Kernel Developed for Mach microkernel by NSA, the University of Utah and Secure Computing Corporation. Operating system security architecture that provides flexible support for security policies. Open Solaris FMAC, TrustedBSD, NSA's SE Linux. FLASK Mechanism •Provides flexibility and coordinate subsystems •Makes security decisions •Evaluates requirements to take decisions •Monitors decisions over time FLASK Mechanism Architecture provides interface for retrieving access, labeling and polyinstantiation. Access Vector Cache module allows object manger to cache access decisions to minimize overhead time. Architecture provides object manager to register changes security policies. Mandatory Access Control Policies Administrator can control and define users’ access to resources. Users cannot modify or change the permissions and access rights. Can be used to protect network, block ports and sockets. MAC Mehanism MAC Vs DAC MAC Vs DAC In DAC, security policies enforced can be easily overridden Depends on ownership of the object and subject identity. Many hacking issues. Features Enforces clean separation of policy Independent of specific security label formats and contents Increased efficiency because of caching of access decisions Initialization, inheritance and program execution can be controlled File systems, directories, files, and open file description can be controlled Distribution • • • • • • Fedora Core 2 Debi an Gentoo SuSe SE-BSD SE-MACH Conclusion More secure operating system Helps administrator to control over resource access Open source allows system to improve rapidly. Digitized materials are in safe hands. References Ray Spencer, Stephen Smalley,, Peter Loscocco, Mike Hibler, David Andersen, and , Jay Lepreau. "The Flask Security Architecture: System Support for Diverse Security Policies." N.p., n.d. Web. "Frequently Asked Questions." SELinux Frequently Asked Questions (FAQ). N.p., n.d. Web. 23 Apr. 2014. <http://www.nsa.gov/research/selinux/faqs.shtml#I2>. "Security Enhanced Linux." Security-Enhanced Linux. N.p., n.d. Web. 23 Apr. 2014. <http://www.nsa.gov/research/selinux/>. "NB TE." - SELinux Wiki. N.p., n.d. Web. 23 Apr. 2014. <http://selinuxproject.org/page/NB_TE>. "16.3. Explanation of MAC." 16.3. Explanation of MAC. N.p., n.d. Web. 23 Apr. 2014. <http://www5.us.freebsd.org/doc/handbook/mac-initial.html>. "Mandatory Access Control." What Is ? N.p., n.d. Web. 23 Apr. 2014. <http://www.webopedia.com/TERM/M/Mandatory_Access_Control.html> "Security-Enhanced Linux." Wikipedia. Wikimedia Foundation, 23 Apr. 2014. Web. 23 Apr. 2014. <http://en.wikipedia.org/wiki/Security-Enhanced_Linux>.