Optimizing User Administration in SAP -ISACA ATL Chapter (8
advertisement

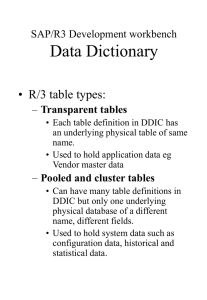
Optimizing User Administration in SAP ISACA Geek Week - Atlanta August 13, 2014 Today's Presenters Aric Quinones Protiviti Managing Director ERP Solutions Practice Chris Aramburu Protiviti Senior Consultant ERP Solutions Practice Connor Hammersmith Protiviti Senior Consultant ERP Solutions Practice © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Who We Are Protiviti (www.protiviti.com) is a global consulting firm that helps companies solve problems in finance, technology, operations, governance, risk and internal audit, and has served more than 35 percent of FORTUNE 1000® and 40 percent of FORTUNE Global 500® companies. Protiviti and its independently owned Member Firms serve clients through a network of more than 70 locations in over 20 countries. The firm also works with smaller, growing companies, including those looking to go public, as well as with government agencies. Protiviti is a wholly owned subsidiary of Robert Half (NYSE: RHI). Founded in 1948, Robert Half is a member of the S&P 500 index. • 3,100 professionals • Over 20 countries in the Americas, Europe, the Middle East and AsiaPacific © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. • 70+ offices • Our revenues: US $ 528.3 million in 2013 The Risk Universe of SAP Security GRC and ERM framework * SAP Security Risks General IT Risks Security Standards Segregation of Duties and Sensitive Access Powerful Users Access Management User and Role Provisioning Process Application Interface Controls IT Infrastructure Controls Change Management Security Administration Backup and Recovery Steering Committee Board of Directors Compliance (Regulatory Requirements) * SAP Business Process and Transactional Data Risks Configurable Application Controls Detective / Monitoring Controls / Reports Procedural Business Process Controls SOX Controls (compliance purposes) External / Internal Audit Other Project / Implementation Risks Project Cost Identification Transaction and Master Data Conversion Go/No Go Decision Criteria Testing and Training Strategy Post Go-Live Support Requirements * Continuous Monitoring Applications and Processes Control Documentation Update, Compliance and Risk Management Optimization and GRC Software Configuration 4 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. What We’ll Cover Common Issues with User Administration in SAP Solutions to Common Issues with User Administration in SAP Recap of Session Takeaways Case Study Wrap-up 5 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. A Few Questions 6 • How many people use one of the major ERP systems (SAP, Oracle or MS Dynamics)? • How many people actually use SAP? • How many people use a GRC tool for Segregation of Duties (SoD) Analysis – such as SAP GRC, Oracle GRC, or Fastpath? • What is an SoD Analysis? • How many people know what a t-code is? © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Common Issues with User Administration Standardized Role Architecture Security Related Change Management Development of Custom Transactions, Objects, Programs, & Tables Backend System Configurations User Provisioning GRC Related Segregation of Duties (SoD) Management of Temporary / Emergency Access 7 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Standardized Role Architecture Key Risks • Role-level SoD issues • Inappropriate organizational level restrictions • Duplicative transaction assignments • Powerful roles with unnecessary access • Excessive number of transactions granting unintended access to end users • Increased efforts of the Security Team for role maintenance and user provisioning Root-Causes 8 • Inconsistent role standards • Lack of role governance • Roles not managed globally • Unintuitive role naming convention • Lack of role documentation © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. B. Smith, Finance Manager • Assigned 114 active roles • Providing access to 6,636 unique transactions (919 duplicate via multiple role assignment) • Of the 6,636 transactions only 6,328 transactions are executable Transactional History Analysis • 115 executable transactions were executed a total of 12,946 times • The top 25 transactions accounted for 89% of the activity Choosing the Appropriate Role Architecture • Derived versus Enabler • Job Based versus Task Based • Ensuring the Architecture is Scalable • Aligns with SAP Resource Skillset & Compliance Culture • Standardized Role Naming convention 9 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Change Management The lack of Change Management can impact role maintenance which is critical to maintaining a secure SAP environment and standardized role architecture. Key Risk: Roles unaligned with the new and existing global business processes 10 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Development of Custom Transactions, Objects, Programs & Tables Key Risks 11 • Lack of functionality knowledge • Circumventing security & gaining unauthorized access to sensitive data • Bypass organizational level security restrictions • Excessive privileges within the scope of the specific transaction • Unauthorized execution of programs • • • • • Absence of SAP customizing governance processes Poor design documentation and/or lack of communication Custom program coded to call powerful transactions (i.e. SE38, SA38, SM30, etc.) Authorization checks not coded in custom program Not assigning custom programs to custom transactions © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Root-Causes Backend System Configurations There are several security related backend tables and configuration that are critical to maintaining a controlled security environment that are often overlooked or maintained which could become a significant security risk. Company Code 1000 Plant 100 Purchasing Group 1 12 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Purchasing Group 2 Purchasing Org 1900 Purchasing Group 3 Governance: Policies & Procedures • A security governance policy contains standards for the SAP ECC production environments to ensure consistency and minimize significant risk to the environment. The should be designed to create standards around the following key areas: ‒ User Access Management ‒ Custom Program and Table Security Requirements ‒ Backend System Configurations ‒ Role Creation and Maintenance Standards ‒ Password Management ‒ Security Parameters 13 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. SAP solutions for Governance, Risk, and Compliance SAP Access Control SAP Process Control SAP Risk Management Manage access risk and prevent fraud Ensure effective controls and ongoing compliance Preserve and grow value © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. GRC Access Control Overview Primary GRC Risks to be discussed today: User Provisioning SoD / Sensitive Access Monitoring User Provisioning Management of Temporary / Emergency Access © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. User Provisioning Key Risks • Assignment of excessive and/or sensitive access • Documenting appropriate approvals for compliance purposes • Delay in provisioning or deprovisioning • Selection of correct roles • User access reviews Root-Causes • • • • 16 The user does not know the appropriate role to select due to current naming convention User provisioning is a manual process Approvals are documented offline or via email Master data has not been maintained appropriately © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. User Provisioning GRC automates the SAP access request and provisioning process by providing customizable workflow options that integrate seamlessly with the SoD Risk Analysis Solution Enhancements Key Benefits • User Provisioning: − Integrates with SAP to prevent SoD Violations − Customizable access request workflows − Template based access requests − Complete audit trail to satisfy compliance requirements − Eliminates manual provisioning to end users • Workflows also available for: − User Access Reviews − FF Log Review − SoD Remediation − Mitigating Control Assignment / Review • Standardized on SAP Business Workflow Technology • Business workflow reduces manual tasks and streamlines access request processing • Gain visibility of User Access Risks before entering a production environment • Faster and easier for users to request the roles they need • Leverage existing resources for workflow administration and configuration • Utilize existing HR structure for automated and compliant position based role assignment • Improved security and richer request context © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Segregation of Duties (SoD) Key Risks • A user with excessive or sensitive access within the system has the ability to perform fraudulent activity • Internal controls may be circumvented by excessive access Root-Causes • • • • 18 Over the course of time a user may switch job functions It may be necessary for the user to have the access within SAP to perform both business functions during the transition period After the transition period is over the user may still retain this excessive access SoD violations can quickly spiral out of control because in some organizations users submit access requests by replicating a user performing the same job function © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. SoD / Sensitive Access Monitoring SoD / Sensitive Access Monitoring • Products such as SAP Access Control can be used to monitor SoD Violations, as well as Sensitive Access. • A custom “rule set” containing function conflicts (e.g., Create Vendor vs. Manual Payments), as well as sensitive transactions/objects can be tailored to your specific risk environment. • Simulations and “what if” analyses can be run before actual security changes are made. • Can be integrated into the user provisioning and role creation process. © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Customizing Your Ruleset It is import to customize your own ruleset by reviewing with all of the key stakeholders: – Risk Relevance - Inactive vs. active – Criticality Level - Low, medium, high, or critical – Modify Rules – There are authorizations which need to be adjusted to ensure accuracy for your organization and to remove false positives – Review Custom Transactions and Tables – All new custom transactions and programs should be reviewed for inclusion in the ruleset Define SoD Ruleset Ruleset Analysis Against Leading Practices Incorporate Feedback from Internal Audit Communicate Proposed Ruleset to Business Controllers © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Update SoD Ruleset with Feedback 20 Finalize SoD Ruleset Management of Temporary / Emergency Access Key Risks • Superuser or privileged access should be approved and reviewed in a timely manner • A user can perform critical actions either accidentally or maliciously to interrupt system availability Root-Causes • • • • 21 Certain sensitive or critical transactions are necessary to keep the system running smoothly Restricting and monitoring sensitive access within the system is a top audit concern Log review is a very tedious and time consuming process Some users are assigned the profile SAP_ALL granting unrestricted access © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Management of Temporary / Emergency Access Emergency Access Management • SAP Access Control or Firefighter, can be used to effectively handle temporary and elevated system access. • All activity and the changes performed within Firefighter are logged for review/signoff. • Log review can be integrated into workflow to automatically route and track Firefighter log approvals. • Provisioning of Firefighter IDs can be integrated into Access Request (ARQ). • Centrally managed across all systems (end-user does not need an ID in the target system, only the GRC system). © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. How Firefighter Works? The workflow functionality within SAP GRC can provide an automated and auditable process for: – – – – Requesting elevated access Routing request for approval Automatically assigning approved access for the specified time period Logging and routing the activity logs to the Firefighter Controller for review. • Reduces the effort required to grant and provision emergency access to multiple systems. Provides a structured, documented process around emergency access • Enables documented account of the controller’s review Administered Centrally on GRC System © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Control Optimization • Sometimes we cannot avoid certain risks within the ERP systems we manage. • Luckily, SAP has many configurable controls that can be enabled to help mitigate some of these risks. • For example: – Check for duplicate invoices – 3-Way Match Protiviti’s Control Library: © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. SAP Access Control – Sample Roadmap Start Solution Design Quick Wins Access Request Management Access Risk Analysis SoD Technical Installation / Upgrade Enhanced Functionality SAP PC/RM Integration Integration with Non-SAP Applications Emergency Access Business Role Management Data Migration Ruleset Optimization & Reporting Upgrade Solution Components Process Improvement 25 Optimization Streamlined super user process Automated SAP Provisioning Change Mgmnt. for users & roles SAP Security Remediation © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Risk Mitigation End to end Provisioning Recap of Session Takeaways Common Issues with User Administration in SAP Solutions to Common Issues with User Administration in SAP Recap of Session Takeaways Case Study Wrap-up 26 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Key Points to Take Home Remember: 1. A standardized role architecture simplifies user administration in SAP 2. A strong change management policy is vital when maintaining good SAP Security practices 3. There are many tools available to assess the security in your SAP environment 4. Achieve buy-in & sponsorship across organization 5. Strong Security & Governance policies are crucial to maintaining a secure ERP environment 27 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. What We’ll Cover Common Issues with User Administration in SAP Solutions to Common Issues with User Administration in SAP Recap of Session Takeaways Case Study Wrap-up 28 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Results - Other Role Redesign Project Metrics Before Security and GRC Redesign New User to be provisioned # of transactions per role Average transactions per user 29 After Security and GRC Redesign 15 days 77 2,281 Number of detailed SoD violations 13,054,616 Intra Role SoD Conflicts 94,458 New User to be provisioned % Reduction 4 hours 98.889% # of transactions per role 7.3 90.519% Average transactions per user 371 83.735% 3,149 99.976% 3 99.997% Number of detailed SoD violations Intra Role SoD Conflicts © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Questions? 30 © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Thank You! Aric Quinones 3343 Peachtree Road, NE Suite 600 Atlanta, GA 30326 Direct: +1 404.240.8376 Aric.Quinones@protiviti.com Powerful Insights. Proven Delivery.® Chris Aramburu Connor Hammersmith 3343 Peachtree Road, NE Suite 600 Atlanta, GA 30326 3343 Peachtree Road, NE Suite 600 Atlanta, GA 30326 Direct: +1 404.443.8221 Direct: +1 404.926.4315 Chris.Aramburu@protiviti.com Connor.Hammersmith@protiviti.com Powerful Insights. Proven Delivery.® 31 Powerful Insights. Proven Delivery.® © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party. Confidentiality Statement and Restriction for Use This document contains confidential material proprietary to Protiviti Inc. ("Protiviti"), a wholly-owned subsidiary of Robert Half International Inc. ("RHI"). RHI is a publicly-traded company and as such, the materials, information, ideas, and concepts contained herein are non-public, should be used solely and exclusively to evaluate the capabilities of Protiviti to provide assistance to your Company, and should not be used in any inappropriate manner or in violation of applicable securities laws. The contents are intended for the use of your Company and may not be distributed to third parties. © 2014 Protiviti Inc. An Equal Opportunity Employer. CONFIDENTIAL: This document is for your company's internal use only and may not be copied nor distributed to any third party.