The Farm-to-Table Food Supply Chain is Vulnerable
advertisement

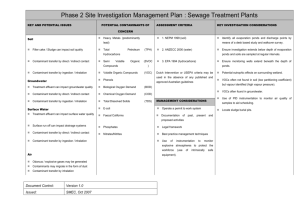
Step one in developing a food defense plan Production Agriculture Supplies Transportation Auctions Feedlots -Farm Food Processing Supplies Employees Bulk Mixing Bulk Storage Water supply Retail Food Sales Supplies Employees Buffet Service Areas Farmer’s Market Fresh Produce Food Defense focuses on protecting the food supply from intentional contamination. Food Safety (HACCP) and Biosecurity focus on protecting the food supply from unintentional contamination. They help with, but are not a substitute for food defense. Disgruntled employee/former employee Contract or temporary employee Members of extremist groups Truck driver Affiliate of a competing facility Visitor to facility Biological Agents: Chemical Agents: Radiological Agents: Injure externally Injure by causing disease, or producing toxin. Injure through toxicity to biological systems, or chemical burns to tissue. (radiation burns) or internally (organ damage). Incubation period/delayed effect Highly effective History of use Available (easily produced in adequate quantity) Low traceability 1973 Fire retardant (PBB) accidentally mixed into feed rations for cattle. Over a year later sickness in animals, and humans is linked to PBBs. Cattle, pigs, sheep, chickens, and contaminated commodities are destroyed and buried. 97% of humans living in Michigan during that time period have PBBs in their system. Consider how a chemical might be “delivered” as an intentional contaminant: Directly added during production process Added to ingredients at the supplier level Indirect addition during the production process(ex. Cleaning supplies or pesticides, packaging materials) Consider how a disease might be “delivered” as an intentional contaminant: Aerosol (airborn) Directs contact (including reproductive) Fomite (contaminated object) Oral (feed or water) Vector-borne (insect transmission) Zoonotic (transmission between humans and animals) Consider how a microbiological agent might be “delivered” as an intentional contaminant: Directly added to finished product Indirect addition to environment or finished product (ex. Listeria) Labeled map of facility Written operational procedures Workforce procedures University extension personnel Law enforcement Insurance Agent USDA – Pre-harvest Security Guide USDA/Food Safety and Inspection Service – Developing a Food Defense Plan for Meat and Poultry Slaughter and Processing Plants Food and Drug Administration – Guidance for Industry, Food Producers, Processers, and Transporters: Food Security Preventative Measures Guidance 1. Is your outside perimeter secure? 2. Is access within your operation limited? 3. Are your processes secure? 4. Is your shipping and receiving secure? 5. Do you have an inventory system for stored materials? 6. Is access to your water supply limited? 7. Is mail opened away from sensitive areas? 8. Do you have screening and training procedures for your workforce? 9. Is access to sensitive areas limited? Family owned auction facility with sales on Monday and Wednesday. Restaurant on premises open Monday through Saturday from 6:00 am to 2:00 pm. Located at the corner of two highways and has a perimeter fence. 8 permanent and 12 part time employees. Arena can seat 300 people. Restaurant can seat 75 people. Can accommodate up to 5,000 animals. Security cameras are located inside the pavilion but not in the pens. Restrooms are shared with arena and restaurant. 2 4’ 24’ Completed By: Mike R. O’Phone Vulnerability Assessment Worksheet Vulnerability Questions 1. Is your outside perimeter secure? 2. Is access within your operation limited? 3. Are your processes or procedures secure? 4. Is your shipping and receiving secure? 5. Do you have an inventory system for stored materials? 6. Is access to your water supply limited? 7. Is mail opened away from sensitive areas? 8. Do you have screening and training procedures for your workforce? 9. Is access to sensitive areas limited? Date: 5-19-09 Y N N/A