File
Wyoming Medical Center, Los
Angeles County, and Raymond
James:
Endpoint Security Gets
Complicated
Group 2:
Marco Hidalgo
Wesley Lao
Michelle Marquez-Lim
Nicole Marquez-Lim
Liza Guades
Rachelle Roque
Golda Go
Overview
Protecting end points is becoming more difficult as the type of endpoint devices (laptops, desktops, smartphones) grows, making security a complex moving target.
Depending on the device and the user’s role, endpoints need to be locked down.
An appropriate software must be used by organizations to protect sensitive information.
Wyoming Medical Center
Open PCs for staff use on hallways, nursing stations, offices, and
PCs on wheels that move in between patient rooms.
Physicians can access patient information via
(Security sockets layer virtual private network)SSL VPN.
They have 850 out of the
900 PCs with the appropriate software use.
With 110 applications and
40 major medical software systems.
They admit, they need more help desk to monitor network activities in the hospital, although they use (Citrix) to monitor and protect their data.
Los Angeles County Dept. of
Health Services
Data Privacy
One concern of Endpoint
Security
The information security officer supports
18,000 computers and operates under the restriction of Health Insurance Portability and
Accountability Act (HIPAA) regulations. They use disk encryption to protect patient information and confidentiality.
Survey
Information Week
Analytics/
Darkreading.com endpoint security survey of 384 business technology pros, 43% classify their organizations as
“Trusting”.
Raymond James
The chief security officer opted for Sopho’s Endpoint
Protection and Data Security Suite, which offers firewall, antivirus, data loss prevention (DLP), antispyware, encryption, and network access control
(NAC).
The company wants tight control over web content available to users, to minimize malware coming in via web browsing.
Mobile devices that could get sensitive information are disk encrypted. Guest users are allowed to use PCs with dedicated wireless network that leads to limited set of servers in a network.
Smartphones
Presents ongoing challenge as companies figure out how to deal with it. (In terms of security)
73% of businesses surveyed are at least somewhat concerned about smartphones being authorized for business use.
Case Questions
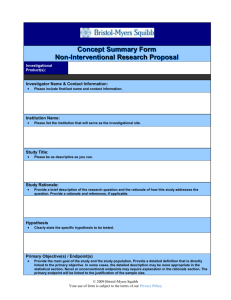
What is the underlying issue behind endpoint security and why is it becoming more difficult for companies to address it?
Case Questions
What are the different approaches taken by the organizations in the case to address this issue? What are the advantages and disadvantages?
At Raymond James:
For LA County Dept. of Health
Services:
-Data encryption and password protected
-Removable Storage (USB drives, are not allowed)
-Used DLP solutions,
Sophos Endpoint Protection and Data Security Suite, which offers firewall, antivirus, antispyware, encryption, and NAC.
Case Questions
A majority of respondents to a survey discussed in the case described their company as “trusting.” What does this mean? What is the upside of a company being
“trusting”? What is the downside?
What they meant by “trusting” was, everyone in the company have
Upside? Trust is great and access to data, allowing them to be everyone can know copied and stored in USB drives or corporate intel inside out.
other related devices without any limitations or preventive measures. Downside? Too much power and information in
Some organizations have full confidence in their employees that they will safe-keep all information shared in the organization.
the hands of all employees.
It may compromise the company.