his slides for

Somewhere Over the
Rainbow Tables
Bob Weiss
Password Crackers, Inc.
Robert Weiss (pwcrack)
• Owner, Password Crackers, Inc.
• Defcon Speaker Goon
• We don’t learn to hack – we hack to learn.
• Hit me on LinkedIn
• Twitter: @pwcrack
History
• Rainbow Tables are a refinement of an earlier, simpler algorithm by
Martin Hellman (as in Diffie-Hellman) proposed in 1980.
• The Hellman algorithm was then improved by Ronald Rivest (the R in
RSA) in 1982.
• Phillippe Oechslin then proposed a faster improvement in 2003.
Conventional Alternatives
• Password hashes can be brute-forced using tools such as Jack the Ripper,
Hashcat, Cain and Abel, etc. These can be accelerated, but this can still take a very long time.
• A conventional table of all passwords and hashes could be built. But even for LM would take up about 3 Terabytes (without optimization or compression.)
• So conventional alternatives, not very exciting.
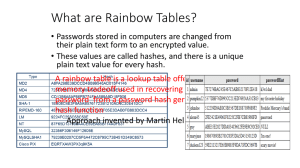
What is a Rainbow Table?
• A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering the plaintext password, up to a certain length and from a specified character set. It is a form of time-memory tradeoff, using less CPU at the cost of more storage.
How do Rainbow Tables
Work?
How do Rainbow Tables Work
– Part 2?
What are the current practical capabilities of Rainbow Tables
• Any LM hash can be easily recovered.
• NTLM, MD5 or SHA1 lower than 7 characters (mixedalpha-numeric-allspace) done.
• Longer NTLM, MD5 or SHA1 with reduced character sets are done.
• New tables continue to be built using distributed systems daily.
You can use Rainbow Tables for anything, though.
• Office 2003 – Elcomsoft
Thundertables or Ophcrack_office
• Unix Crypt()
• MySQL
• CiscoPIX
Using Rainbow Tables
• You can download your own
Rainbow Tables (.rt) and then use a variety of software to test your hash list.
• Tables can vary in size (anywhere from a couple of meg to a couple hundred gb.)
• Rainbow Crack, Ophcrack and Cain and Abel all use .rt files.
Defeating Rainbow Tables
• Rainbow Tables by definition require pre-computing and can be defeated by adding unique salts to hashes that would increase the size or complexity of the table beyond what is practical.
WPA
• Renderman’s WPA tables are not really
“Rainbow Tables.” They are pre-computed lookup tables. Still cool, but someone will probably make a more efficient Rainbow Table out of this data some day.
• Used by coWPAtty for faster lookups on common
SSIDs.
• 33 gb Torrent available at Shmoo site.
• Some individual .torrents for 165 SSIDs available at http://www.offensive-security.com/wpa-tables/, but not well seeded and duplicative of the larger
Torrent. However, more efficient if you only need specific SSIDs.
Why download if there is a online service?
• FreeRainbowTables.com
• OnlineHashCrack.com
• passcracking.com
• md5online.net
• crack-online.com
• hash-cracker.com
Creating Rainbow Tables.
• rtgen
• rtsort
• winrtgen
• Supports:
LM, FastLM,
NTLM,
LMCHALL,
HalfLMCHALL, NTLMCHALL, MSCACHE, MD2,
MD4, MD5, SHA1, RIPEMD160, MySQL323,
MySQLSHA1, CiscoPIX, ORACLE, SHA-2 (256),
SHA-2 (384) and SHA-2 (512) hashes.
• GPU Accelerated Rainbow Tables Generator at cryptohaze.com
.rt naming convention
• md5_loweralpha-numeric#1-
7_0_3800x33554432_0.rt
• rcrack needs file parameters in filename so don’t rename.
• hash_algorithm charset plaintext_len_min plaintext_len_max table_index chain_len chain_num part_index
Common Downloadable RTs
• Shmoo
– http://rainbowtables.shmoo.com/
• Hak5 (1 of 2 is active)
– http://www.hak5.org/w/index.php/Community_Rainbow_Tables
• FreeRainbowTables.com
– http://www.freerainbowtables.com/en/tables/
• WPA from Offensive Security (& Shmoo)
• CiscoPIX and MySQL torrents exist but do not appear to be active.
• GARR Mirror
– http://freerainbowtables.mirror.garr.it/mirrors/freerainbowtables



![Rainbow Sandals[1]](http://s2.studylib.net/store/data/005415944_1-86d746c06518ebd8de8a03e56a4931b4-300x300.png)