Chap 2
advertisement

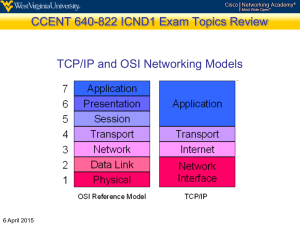
Chapter 2 Network Models Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. Components of Communication Sender Receiver Message Transmission medium Protocol Effectiveness of Communication Delivery (confidentiality) Accuracy (integrity) Timeliness (availability) 2.3 Jitter – a subset of timeliness Data Flow 2.4 Simplex Half-Duplex Duplex Connection Types Point-to-Point Multi-point 2.5 A circuit switch creates a point to point connection. Many packet switched networks are multipoint Physical Topologies 2.6 Bus Ring Star Mesh Compound Physical Topology Links Let n=# of nodes. The number of links is: 2.7 Bus Ring Star Mesh n-1 n n-1 (includes the hub) n*(n-1)/2 Network Types 2.8 LAN – nodes belonging to an address space that are part of a well defined domain. WAN – When two or more LANs are linked together. Chapter 2: Outline 2.1 Protocol Layering 2.2 TCP/IP Protocol Suite 2.3 OSI Model 2-1 PROTOCOL LAYERING A protocol defines the rules that the sender, receiver and all intermediate devices must follow to communicate effectively. 2.10 2.1.1 Scenarios Consider two scenarios. Scenario 1: communication is so simple it occurs in one layer. Scenario 2: communication takes place in three layers. 2.11 2-1 PROTOCOL LAYERING When communication is simple, one simple protocol may be enough; When the communication is complex, layers are introduced, and each layer has its own protocol. 2.12 Figure 2.1: A single-layer protocol 2.13 Figure 2.2: A three-layer protocol Postal carrier facility 2.14 2.1.2 Principles of Protocol Layering Consider two principles of protocol layering. 2.15 2.1.2 Principles of Protocol Layering Consider two principles of protocol layering. 1. For half-duplex or full duplex data flow, each layer must perform a forward operation and the corresponding inverse operation. 2.16 2.1.2 Principles of Protocol Layering Consider two principles of protocol layering. 2. The two objects under each logically linked layer at both sites should be identical. 2.17 2.1.2 Principles of Protocol Layering Consider two principles of protocol layering. 1. For half-duplex or full duplex data flow, each layer must perform a forward operation and the corresponding inverse operation. 2. The two objects under each logically linked layer at both sites should be identical. 2.18 Figure 2.2: A three-layer protocol Postal carrier facility 2.19 2.1.3 Logical Connections The principles of protocol layering lead to a logical connection between the layers at sending and receiving ends of the communication. 2.20 Figure 2.3: Logical connection between peer layers 2.21 2-2 TCP/IP PROTOCOL SUITE A protocol defines the rules that both the sender and receiver and all intermediate devices must follow to communicate effectively. 2.22 2-2 TCP/IP PROTOCOL SUITE TCP/IP is a five layer protocol suite. 2.23 2-2 TCP/IP PROTOCOL SUITE TCP/IP is a five layer protocol suite. •Application Layer 2.24 2-2 TCP/IP PROTOCOL SUITE TCP/IP is a five layer protocol suite. •Application Layer •Transport Layer 2.25 2-2 TCP/IP PROTOCOL SUITE TCP/IP is a five layer protocol suite. •Application Layer •Transport Layer •Network Layer 2.26 2-2 TCP/IP PROTOCOL SUITE TCP/IP is a five layer protocol suite. •Application Layer •Transport Layer •Network Layer •Data Link Layer 2.27 2-2 TCP/IP PROTOCOL SUITE TCP/IP is a five layer protocol suite. •Application Layer •Transport Layer •Network Layer •Data Link Layer •Physical Layer 2.28 Figure 2.4: Layers in the TCP/IP protocol suite 2.29 2.2.1 Layered Architecture TCP/IP protocol suite example: Consider three LANs Each LAN has a group of hosts connected to a switch (aka 2-level switch). Each switch is connected to a router (aka 3-level switch) 2.30 Figure 2.5: Communication through an internet 2.31 2.2.2 Layers in the TCP/IP Protocol Suite Draw a diagram with multiple nodes in each LAN Why is it called a 2-level switch? Why is a router is 3-level switch? 2.32 Figure 2.6: Logical connections between layers in TCP/IP Logical connections 2.33 Network Data Objects Data objects: message 2.34 Network Data Objects Data objects: message segment 2.35 Network Data Objects Data objects: message segment datagram 2.36 Network Data Objects Data objects: message segment datagram frame 2.37 Network Data Objects Network data object taxonomy: message segment datagram frame signals representing bits 2.38 Figure 2.7: Identical objects in the TCP/IP protocol suite Identical objects (messages) Identical objects (segment or user datagram) 2.39 Identical objects (datagram) Identical objects (datagram) Identical objects (frame) Identical objects (frame) Identical objects (bits) Identical objects (bits) Network Data Objects Data Object Taxonomy: Application layer - message Transport layer - segment Network layer - datagram Data link layer - frame Physical layer – signals representing bits 2.40 2.2.3 The TCP/IP Layers Descriptions of the TCP/IP layers will come later; next, we will follow a data object through the layers… 2.41 2.2.4 Encapsulation and Decapsulation One of the important concepts in protocol layering in the Internet is encapsulation/ decapsulation. 2.42 2.2.4 Encapsulation and Decapsulation As the object passes through each layer, an information header (and or trailer) is added to the object. The information header is used to assist in any of these tasks: routing of the object, flow control, error detection, error correction, etc. (see next slide) 2.43 Figure 2.8: Encapsulation / Decapsulation 2.44 Encapsulation payload 2.45 Each layer receives an object that is referred to as the payload, and then attaches a data header. Payload can be relative to each layer, or absolute. The absolute case refers to the original object message. Example Encapsulation 2.46 Q: What is the efficiency of the link in figure 2.8, between LANs if each header is 60 bytes and the message is 1000 bytes? Example Encapsulation 2.47 Q: What is the efficiency of the link in figure 2.8, between LANs if each header is 60 bytes and the message is 1000 bytes? A: 84.7% Example Encapsulation 2.48 Q: How does the efficiency change if the message is only 100 bytes? Example Encapsulation 2.49 Q: How does the efficiency change if the message is only 100 bytes? A: 35.7% Figure 2.9: Addressing in the TCP/IP protocol suite 2.50 2-3 OSI MODEL A seven layer protocol model. It never really caught on due to the success of TCP/IP 2.51 Figure 2.11: The OSI model 2.52 Figure 2.12: TCP/IP and OSI model 2.53 2.3.1 OSI versus TCP/IP When we compare the two models, we find that two layers, session and presentation, are missing from the TCP/IP protocol suite. These two layers were not added to the TCP/IP protocol suite after the publication of the OSI model. The application layer in the suite is usually considered to be the combination of three layers in the OSI model, as shown in Figure 2.12. 2.54