Laptop Security in the IT world
advertisement

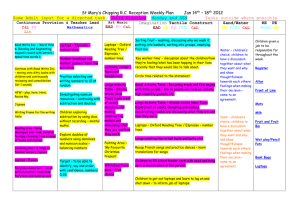
Laptop Security in the current IT world W3 group Motivation • Companies provide laptops to its employees – Work from home – Work during travel • As of 2010 about half of adults go online with a laptop (http://www.pewinternet.org/Reports/2010/Mobile-Access-2010.aspx) – Increasing every year – Use work laptops for personal use at home, on travel • Usage guidelines and restrictions – Strict at work, not so strict when outside the work domain – Not clear what to do in the event of a security breach Motivation (contd) • Malicious users – A begrudged employee – Rival companies – Countries that access information to gain competitive advantage in world markets • Malicious access to laptops – Physical (Stolen laptops, copy data using a USB drive etc.) – Online (Trojan horses, viruses etc.) Confidentiality • Lots of confidential information – – – – – Source code Vital financial information (stock/trade secrets etc.) Personal Identifiable Information (SSN, DOB etc.) Emails (downloaded by email client programs like MS Outlook) Data in re-used laptops • Protecting confidential information – – – – – – Sign NDA Encryption (emails, data, encrypted folders) Don’t allow USB drives Guidelines on how to handle sensitive data Information on what to do in case of a breach Wipe out hard disks of laptops returned to general employee pool Authenticity • Different ways to authenticate access to laptops – – – – – Username/passwords BIOS passwords Hard disk passwords Screen save passwords Usage of laptop locks Integrity • As important as confidentiality – A malicious user can access data in a laptop and change it • A lot of software downloaded from the Internet – Software for office use (Adobe reader, Flash player, Updates etc. ) – Personal use (ITunes, Sticky notes etc. ) – Difficult to distinguish between malicious and authentic sites • Ways to guarantee integrity – MD5 checksums for software recommended for install – Allow only admins to install software Availability • Employee Productivity – Directly affected if laptop is not available • Availability of critical servers – A malicious user could use botnets to launch DOS attacks on internal critical resources Conclusion • With such prevalent usage of laptops, laptop security is of paramount importance • Often not completely thought through • At the minimum a disaster recovery plan should be in place – – – – Identify and prioritize threats Contact information in case of disasters (security breaches) Details on how to get back the data and recover Employee education