What Does Infosec Do? - OIT Help
advertisement

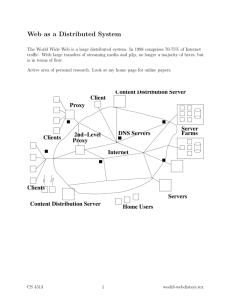
INFORMATION SECURITY University of Notre Dame WHAT DOES INFOSEC DO? University of Notre Dame INFORMATION SECURITY TEAM David Seidl James Smith Brandon Bauer Jaime Preciado-Beas Jason Williams Aaron Wilkey Kolin Hodgson INFORMATION SECURITY TEAM Who do I contact if I have a question? Phone:1-3888 Email: infosec@nd.edu In person: Visit the Duty Officer of the day. After hours: contact Ops INFRASTRUCTURE NETWORK FLOW EXAMPLE NETWORK FLOW TO INDIA SOME OF OUR SERVICES Web Inspect Risk Assessment Compliance Support (PCI-FERPA-HIPAA) Advisories Vulnerability Management (Qualys) Data Center Firewall Management COMPUTER FORENSICS We know what you did. YES YOU COMPUTER FORENSICS Investigations occur after approval from the CIO, Office of General Counsel, and/or HR Investigations can occur on any electronic device Windows, MacOS, Linux based systems, and others Mobile devices Network devices Mostly HR or Incident Response CONSULTS Security Assessments Cloud/Vendor Security Assessments Virtualization Education POLICIES AND STANDARDS Information Security Policy Highly Sensitive Information http://oit.nd.edu/policies/itstandards/infohandling.shtml Responsible Use http://policy.nd.edu/policy_files/InformationSecurityPolicy.pdf http://policy.nd.edu/policy_files/ResponsibleUseITResourcesPolicy.pdf Security Configuration Standards https://secure.nd.edu/standards/index.shtml DNS BLACKLIST Implemented May 2012 Redirects URLs through DNS to prevent users from visiting malicious web pages URL lists (feeds) are from known security vendors, e.g. SANS Refreshed daily URLs can be white listed by contacting the help desk Manually blacklist as phishing attacks occur. To try this visit 12345.com from campus DNS BLACKLIST DNS BLACKLIST TESTING 3,500 3,091 3,000 2,741 2,603 2,500 2,000 1,500 1,528 1,000 500 0 9/11/2012 9/12/2012 9/13/2012 9/14/2012 CREDIT CARD SUPPORT PROGRAM (CCSP) Separate network behind its own firewall Credit Card processing environment for ND merchants All ND merchants required to comply with PCI DSS Governance body Information: ccsp.nd.edu or ccsp@nd.edu TEAM GHOSTSHELL Project WestWind Target: 100 top universities across the world Purpose: To bring attention to the decaying status of higher education around the world Outcome: A massive dump of over 120k student/faculty/staff records pulled from university servers The Data: Usernames, passwords, phone numbers, class numbers, and more WHO IS TEAM GHOSTSHELL? Project WestWind “Hactivists” focused on hacking to bring awareness for what they consider to be the greater good Team GhostShell has made successful dumps prior to Project West Wind IT Wall Street: Dumped 50,000 accounts to support the occupy Wall Street movement Project Dragonfly: Dumped 200,000 accounts to support freedom of speech in communist countries GhostShell was able to take advantage of vulnerabilities in the web applications of the targeted universities to gain access to their servers The vulnerabilities were most likely exploited using SQL injection The attack took up to four months to prepare according to Aaron Titus of Identity Finder (Chief Privacy Officer) THE ATTACK! SQL Injection: A code injection technique that exploits a security vulnerability in a website's software. The Damage Reputation: Anytime there is a data leak, the reputation of the institution is affected Reputation: GhostShell also found many of the machines were already exploited existing exploits. Some of these stored credit card information. Cost: Notification and credit monitoring for those whose information was leaked Sample of Affected Universities University of Michigan (7 servers) University of Wisconsin (4 servers) Cornell University (3 servers) Tokyo University (4 servers) Stanford (2 servers) Cambridge (2 servers) Arizona State (3 servers) HOW NOTRE DAME AVOIDED THE INCIDENT Vigilantly scanning all web applications using tools such as HP Webinspect Limited the exposure of public facing servers with the zone network project and other efforts across the university Luck? WILL GHOSTSHELL GET CAUGHT? It is unlikely that anyone from team GhostShell will get caught. The team used TOR (anonymity network) to extract and dump the data. This allowed them to mask their location through a network of anonymous proxies around the world. QUESTIONS YOU ASKED HOW DO NET IDS GET COMPROMISED? Phishing MALWARE POOR PASSWORDS POOR PASSWORD GoIrish, GoIrish1, GoIrish! password, P@ssword 123123, 12345678, abc123, qwerty iloveyou jesus Trustno1, letmein ashley, Ashley1983 ninja, mustang, dragon QUESTIONS WE DIDN’T ANSWER 1. List all of the security software the University licenses There’s a lot: check the software downloads page for many approved software packages. If you have a specific need, drop us a line. 2. Common ePO troubleshooting steps Rather than talk to the entire room about these, we’ll schedule an ePO users group meeting.