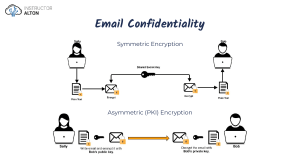
Badr University in Cairo (BUC) Faculty of Engineering and Technology Second Semester 2024 – 2025 Introduction to Malware Analysis ELC 368 Dr. Samar Noor Assignment (3) Question-1: choose the right answer/s 1. Which of the following is a primary difference between symmetric and asymmetric encryption? a) Symmetric encryption uses two keys, while asymmetric encryption uses one key. b) Symmetric encryption is slower than asymmetric encryption. c) Symmetric encryption uses a single shared key, while asymmetric encryption uses a public-private key pair. d) Asymmetric encryption is less secure than symmetric encryption. 2. What is the main advantage of public-key cryptography? a) Faster encryption speed b) No need to share a secret key beforehand c) It is resistant to brute-force attacks d) It does not require complex mathematical operations 3. In Feistel cipher, what happens to the left half of the data during each round? a) It is XORed with the subkey. b) It is swapped with the right half. c) It is passed unchanged to the next round. d) It is combined with the previous round's ciphertext. 4. The Diffie-Hellman key exchange algorithm is primarily used for: a) Encryption of messages b) Digital signatures c) Secure key exchange d) Hash function calculations 5. In the RSA encryption process, what is the purpose of the public key? a) To decrypt the ciphertext b) To sign digital messages c) To encrypt plaintext messages d) To generate session keys Good Luck Page 1 of 2 Badr University in Cairo (BUC) Faculty of Engineering and Technology Second Semester 2024 – 2025 Introduction to Malware Analysis ELC 368 Dr. Samar Noor Question-2: mark the following as true or false (T/F) 1. Symmetric encryption is primarily used for protecting small blocks of data, such as encryption keys. 2. In Feistel cipher design, the encryption and decryption processes are identical except for the order of keys used. 3. The RSA algorithm is based on bitwise operations rather than mathematical functions. 4. Public-key cryptography requires both sender and receiver to have access to a shared secret key. 5. The Data Encryption Standard (DES) uses a 64-bit plaintext and a 56-bit key for encryption. Question-3: Answer the following questions 1) 2) 3) 4) Eexplain the differences between symmetric and asymmetric encryption with examples. Describe the Feistel cipher structure and explain why it is used in encryption algorithms. How does the RSA algorithm work? Provide a step-by-step example. What are the security concerns associated with DES encryption, and why was it replaced? 5) Explain the importance of digital signatures and how they ensure data integrity. Question-4 Draw & Label the Following Diagrams: ➢ Feistel Cipher Structure – Show the data flow through multiple encryption rounds. ➢ Public-Key Cryptosystem – Illustrate the encryption and decryption process. ➢ RSA Key Generation and Encryption – Show the steps from key generation to message encryption. ➢ Comparison of Symmetric and Asymmetric Encryption – Create a table to compare their features. ➢ Data Encryption Standard (DES) Flowchart – Show the steps of DES encryption and decryption. 1. Good Luck Page 2 of 2