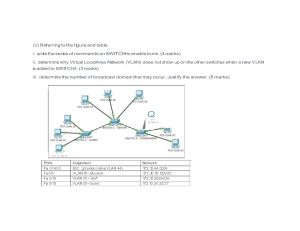
HND Computing Networking Assignment: LAN Design & Implementation
advertisement

INTERNAL VERIFICATION – ASSIGNMENT BRIEF Programme Title - HND in Computing Assessor Name - Oshada Lokuhetty Internal Verifier Name Unit or Component Number and Title Assignment title - Unit 02 - Networking LAN Design & Implementation for Alliance Health Assessment criteria targeted by this assignment brief - LO1, LO2, LO3, LO4 Is this an Authorised Assignment N/A Brief published by Pearson? If so, has it been amended by the Assessor in any way? Please give details. (If using the Authorised Assignment Brief ‘off the shelf’ with no amendments, please answer the question marked in the checklist only) Has this assignment been Yes No submitted to the Assignment Checking Service? (If Yes, please keep a copy of the ACS feedback with this form) √ INTERNAL VERIFIER CHECKLIST Y/N Are the programme and unit details accurate? Y Are clear deadlines for assessment given? TBC Is the time frame of an appropriate duration? Y Is there a suitable vocational scenario or context? Y Are the assessment criteria to be addressed stated accurately? Y Does each task show which criteria are being addressed? Y Do the tasks meet the assessment requirements of the unit/s? Y Is it clear what evidence the learner needs to generate? Y Is it likely to generate evidence that is valid and sufficient? Y Overall, is the Assignment fit for purpose? Yes √ No If ‘No’ is recorded the Internal Verifier must recommend actions detailing the issues to be addressed. The Assessor and the Internal Verifier must then confirm that the action has been undertaken and that the Assignment Brief is authorised for use before being issued to learners. Action required - Target Date for Date Action (If none then please state n/a) Completion Completed General Comments (if appropriate) Assignment Brief Authorised for Use Internal Verifier signature Date Assessor signature Date Lead Internal Verifier signature (if appropriate) oshada@esoft.lk Date 2022/06/13 Higher Nationals Internal verification of assessment decisions – BTEC (RQF) INTERNAL VERIFICATION – ASSESSMENT DECISIONS Programme title BTEC Higher National Diploma in Computing Assessor Internal Verifier Unit 02 - Networking Unit(s) LAN Design & Implementation for Alliance Health Assignment title Student’s name List which assessment criteria Pass the Assessor has awarded. INTERNAL VERIFIER CHECKLIST Merit Distinction Do the assessment criteria awarded match those shown in the assignment brief? Y/N Is the Pass/Merit/Distinction grade awarded justified by the assessor’s comments on the Y/N student work? Has the work been assessed accurately? Y/N Is the feedback to the student Give details Constructive? Linked to relevant assessment criteria? Y/N Identifying opportunities for improved Y/N performance? Y/N Agreeing actions? Y/N Does the assessment decision need amending? Y/N Assessor signature Date Internal Verifier signature Date Programme Leader signature (if required) Date Confirm action completed Remedial action taken Give details - Assessor signature Internal Verifier signature Programme Date Date Leader signature (if required) Date Higher Nationals - Summative Assignment Feedback Form Student Name/ID Unit Title Unit 02 - Networking Assignment Number 1 Assessor Date Received 1st submission Submission Date Date Received 2nd submission Re-submission Date Assessor Feedback LO1 Examine networking principles and their protocols. Pass, Merit & P1 P2 M1 D1 Distinction Descripts LO2 Explain networking devices and operations. Pass, Merit & P3 P4 M2 Distinction Descripts LO3 Design efficient networked systems. Pass, Merit & P5 P6 M3 Distinction Descripts LO4 Implement and diagnose networked systems. Pass, Merit & P7 Distinction Descripts P8 M4 D2 Grade - Assessor Signature - Date - Resubmission Feedback - Grade - Assessor Signature - Date - Internal Verifier’s Comments - Signature & Date Please note that grade decisions are provisional. They are only confirmed once internal and external moderation has taken place and grades decisions have been agreed at the assessment board. Assignment Feedback Formative Feedback - Assessor to Student Action Plan Summative feedback Feedback - Student to Assessor Assessor signature Date Student signature Date Pearson Higher Nationals in Computing Unit 02 - Networking Assignment 01 General Guidelines A Cover page or title page – You should always attach a title page to your assignment. Use previous page as your cover sheet and make sure all the details are accurately filled. Attach this brief as the first section of your assignment. All the assignments should be prepared using a word processing software. All the assignments should be printed on A4 sized papers. Use single side printing. Allow 1” for top, bottom , right margins and 1.25” for the left margin of each page. Word Processing Rules The font size should be 12 point, and should be in the style of Time New Roman. Use 1.5 line spacing. Left justify all paragraphs. Ensure that all the headings are consistent in terms of the font size and font style. Use footer function in the word processor to insert Your Name, Subject, Assignment No, and Page Number on each page. This is useful if individual sheets become detached for any reason. Use word processing application spell check and grammar check function to help editing your assignment. Important Points - It is strictly prohibited to use textboxes to add texts in the assignments, except for the compulsory information. eg - Figures, tables of comparison etc. Adding text boxes in the body except for the before mentioned compulsory information will result in rejection of your work. Avoid using page borders in your assignment body. Carefully check the hand in date and the instructions given in the assignment. Late submissions will not be accepted. Ensure that you give yourself enough time to complete the assignment by the due date. Excuses of any nature will not be accepted for failure to hand in the work on time. You must take responsibility for managing your own time effectively. If you are unable to hand in your assignment on time and have valid reasons such as illness, you may apply (in writing) for an extension. Failure to achieve at least PASS criteria will result in a REFERRAL grade . Non-submission of work without valid reasons will lead to an automatic RE FERRAL. You will then be asked to complete an alternative assignment. If you use other people’s work or ideas in your assignment, reference them properly using HARVARD referencing system to avoid plagiarism. You have to provide both in-text citation and a reference list. If you are proven to be guilty of plagiarism or any academic misconduct, your grade could be reduced to A REFERRAL or at worst you could be expelled from the course Student Declaration I hereby, declare that I know what plagiarism entails, namely to use another’s work and to present it as my own without attributing the sources in the correct form. I further understand what it means to copy another’s work. I know that plagiarism is a punishable offence because it constitutes theft. I understand the plagiarism and copying policy of Pearson UK. I know what the consequences will be if I plagiarise or copy another’s work in any of the assignments for this program. I declare therefore that all work presented by me for every aspect of my program, will be my own, and where I have made use of another’s work, I will attribute the source in the correct way. I acknowledge that the attachment of this document signed or not, constitutes a binding agreement between myself and Pearson, UK. I understand that my assignment will not be considered as submitted if this document is not attached to the assignment. sugasuganthi1996@gmail.com 24/03/2024 Student’s Signature - Date - (Provide E-mail ID) (Provide Submission Date) Higher National Diploma in Computing Assignment Brief Student Name /ID Number Unit Number and Title Unit 2 - Networking Academic Year 2022/23 Unit Tutor Assignment Title LAN Design & Implementation for Alliance Health Issue Date Submission Date IV Name & Date Submission format The submission should be in the form of an individual report written in a concise, formal business style using single spacing and font size 12. You are required to make use of headings, paragraphs and subsections as appropriate, and all work must be supported with research and referenced using Harvard referencing system. Please also provide an end list of references using the Harvard referencing system. The recommended word count is 3,000–3,500 words for the report excluding annexures, although you will not be penalised for exceeding the total word limit. Unit Learning Outcomes - LO1 Examine networking principles and their protocols. LO2 Explain networking devices and operations. LO3 Design efficient networked systems. LO4 Implement and diagnose networked systems. Assignment Brief and Guidance - Scenario Alliance Health is a technology-enabled solutions company that optimizes the revenue cycle of the US healthcare industry where its global delivery center is located in Colombo. The company is planning to expand their business operations with their latest branch at Matara and wants it to be one of the stateof-the-art companies in Matara with the latest facilities. Assume you have been appointed as the new network analyst of Alliance Health to plan, design and restructure the existing network. Prepare a network architectural design and implement it with your suggestions and recommendations to meet the company requirements. The floor plan of the head office in Colombo is as follows Floor 1 Reception area Sales & Marketing Department (10 employees) Customer Services Area – with Wi-Fi facilities Floor 2 Administration Department (30 Employees) HR Department (20 employees) Accounting & Finance Department (15 employees) Audit Department (5 employees) Business Development Department (5 employees) Floor 3 Video conferencing room IT Department (60 employees) The Server Room The floor plan of the branch in Matara is as follows Floor 1 Reception area Customer Services Area– with Wi-Fi facilities Floor 2 Administration Department (10 Employees) HR Department (7 employees) Accounting & Finance Department (8 employees) IT Department (50 employees) Following requirements are given by the Management. All the departments must be separated with unique subnet . The conferencing room of the head office and Customer Services Area s of each branch are to be equipped with Wi -Fi connections . Connectivit y between two branches (Head Office and Matara) would allow the intra branch connectivit y between departments. (Use of VPN is not compulsory) The necessary IP address classes and ranges must be decided by the network designer and should be used for all the departments except the server room. Number of servers required for the Server room need to be decided by the Network designer and should be assigned with 10.254.1 0.0/24 subnet. (Uses static IPs) Sales and Marketing Team also needs to access Network resources using WIF I connectivity. (Note - Clearly state your assumptions. Y ou are allowed to design the network according to your assumptions, but main requirements should not be violated) Activit y 01 Discuss the benefits and constraints of different network system t ypes that can be implemented in the Matara branch and the main IEEE Ethernet standards that can be used in above LAN and WLAN design . Discuss the importance and impact of network topologies and assess the main network protocol suites that are used in network design using examples . Recommend suitable network topology and network protocols for above scenario and evaluate with valid points how the recommended topology demonstrates the efficient utilization of the networking system of Matara branch. Activit y 02 Discuss the operating principles of network devices (Ex - Router, Switch, Etc.) and server t ypes that can be used for above scenario while exploring different servers that are available in today’s market with their specifications . Recommend server/servers for the above scenario and justify your selection with valid points . Discuss the inter-dependence of workstation ha rdware and networking software and provide examples for networking software that can be used in above network design. Activit y 03 Prepare a written network design plan to meet the above-mentioned user requirements including a blueprint drawn using a modeling tool (Ex - Microsoft Visio, EdrawMax) .Test and evaluate the proposed design by anal yzing user feedback with the aim of optimizing your design and improving efficiency. (Support your answer by providing the VLAN and IP subnetting scheme for the above scenario and the list of devices, network components and software used to design the network for above scenario and while justifying your selections. ) Install and configure Network services , devices and applications (Ex - VLAN,WiFi, DNS,Prox y, Web, Etc.) according to the proposed design to accomplish the user requirements and design a detailed Maintenance schedule for above Network. Note - - Screen shots of Configuration scripts should be presented. Activit y 04 Implement a networked system based on your prepared design with valid evidences. Develop test cases and conduct verification (Ex - Ping, extended ping, trace route, telnet, SSH, etc.) to test the above Network and anal yse the test results against the expected results. Recommend potential future enhancements for the networked s ystem with valid justifications and criticall y reflect on the implemented network, including the plan, desig n, configuration s, tests and the decisions made to enhance the s ystem. Grading Rubric Grading Criteria Ach Feedback ieve d LO1 - Examine networking principles and their protocols. P1 Discuss the benefits and constraints of different network types and standards. P2 Explain the impact of network topology, communication and bandwidth requirements. M1 Assess common networking principles and how protocols enable the effectiveness of networked systems. LO2 - Explain networking devices and operations P3 Discuss the operating principles of networking devices and server types. P4 Discuss the interdependence of workstation hardware and relevant networking software M2 Explore a range of server types and justify the selection of a server for a given scenario, regarding cost and performance optimisation LO 1 & LO2 D1 Evaluate the topology protocol selected for a given scenario and how it demonstrates the efficient utilisation of a networking system. LO3 - Design efficient networked systems P5 Design a networked system to meet a given specification. P6 Design a maintenance schedule to support the networked system. M3 Analyse user feedback on your designs with the aim of optimising your design and improving efficiency. D2 Critically reflect on the implemented network, including the design and decisions made to enhance the system. LO4 - Implement and diagnose networked systems P7 Implement a networked system based on a prepared design. P8 Document and analyze test results against expected results. M4 Recommend potential enhancements for the networked systems. D2 Critically reflect on the implemented network, including the design and decisions made to enhance the system. Pearson Higher Nationals in Computing Unit 02 - Networking Assignment 01 W.S. SUGANTHI E192337 FIRST SEMESTER Acknowledgement In making this project, and completing it successfully, I had to get help and guidance from some respected people. I am grateful that I was given the opportunity to make this project, which has enhanced my knowledge in so many aspects. Contents Components Of Computer Network - ..................................... Error! Bookmark not defined. No table of figures entries found. Table 1 List of tables Introduction network A computer network comprises two or more computers that are connected—either by cables (wired) or wifi (wireless)—with the purpose of transmitting, exchanging, or sharing data and resources. You build a computer network by using hardware (for example, routers, switches, access points, and cables) and software (for example, operating systems or business applications). Geographic location often defines a computer network. For example, a LAN (local area network) connects computers in a defined physical space, like an office building, whereas a WAN (wide area network) can connect computers across continents. The internet is the largest example of a WAN, connecting billions of computers worldwide. You can further define a computer network by the protocols it uses to communicate, the physical arrangement of its components, how it controls traffic, and its purpose. Computer networks enable communication for every business, entertainment, and research purpose. The internet, online search, email, audio and video sharing, online commerce, livestreaming, and social networks all exist because of computer networks. There are several methods of managing a network, including, Cloud-based network management - This method of storing information and connecting devices makes use of cloud computing. It's typically available to companies, governments and the general public through the internet. Converged network management - This strategy connects multiple devices via the same access switch. It's a traditional method of connecting various wired and wireless devices. Centralized network management - This strategy is the most common way to implement a new network. It involves connecting devices to a server in a central location. Task 01 Computer Network Types A computer network is a group of computers linked to each other that enables the computer to communicate with another computer and share their resources, data, and applications. A computer network can be categorized by their size. A computer network is mainly of four types. LAN (Local Area Network) PAN (Personal Area Network) MAN (Metropolitan Area Network) WAN (Wide Area Network) LAN (Local Area Network) Local Area Network is a group of computers connected to each other in a small area such as building, office. LAN is used for connecting two or more personal computers through a communication medium such as twisted pair, coaxial cable, etc. It is less costly as it is built with inexpensive hardware such as hubs, network adapters, and ethernet cables. The data is transferred at an extremely faster rate in Local Area Network. Local provides security. higher Area Network let's discuss the benefits and constraints of a LAN (Local Area Network) Benefits: 1. Resource Sharing : One of the primary benefits of LAN is resource sharing. Users within the LAN can share resources such as printers, files, and internet connections, enhancing collaboration and productivity. 2. High-Speed Data Transfer : LANs typically operate at higher speeds compared to wide area networks (WANs) or the internet. This high-speed connectivity enables faster data transfer and communication between devices within the network. 3. Cost-Effectiveness : Setting up a LAN is generally cost-effective compared to establishing individual connections for each device. Once the infrastructure is in place, adding new devices to the network is relatively simple and inexpensive. 4. Increased Security : LANs can be configured with security measures such as firewalls, encryption, and access controls to protect sensitive data and prevent unauthorized access. This helps in maintaining the confidentiality and integrity of the network resources. 5. Centralized Management : With a LAN, network administrators can centrally manage and monitor network resources, user access, and security policies. This centralized management simplifies administration tasks and ensures better control over the network environment. Constraints: 1. Limited Coverage Area : LANs are designed to cover a limited geographic area, typically within a single building or campus. As a result, users outside this coverage area cannot directly access LAN resources without additional networking infrastructure. 2. Dependency on Physical Infrastructure : LANs rely on physical infrastructure such as Ethernet cables, switches, and routers. Any damage or malfunction in the physical components can disrupt network connectivity and affect user productivity. 3. Security Concerns : While LANs offer security features, they are still susceptible to security breaches such as unauthorized access, malware attacks, and data breaches. Proper security measures, including regular updates and employee training, are essential to mitigate these risks. 4. Scalability Challenges : As the number of devices and users on the LAN grows, scalability challenges may arise. The network infrastructure needs to accommodate the increasing traffic and resource demands, which may require upgrades or expansion of the existing infrastructure. 5. Single Point of Failure : LANs can have a single point of failure, such as a faulty switch or router, which can lead to network downtime and disruption of services. Redundancy measures such as backup systems and failover configurations are necessary to minimize the impact of such failures. Overall, while LANs offer numerous benefits in terms of resource sharing, high-speed connectivity, and centralized management, they also come with constraints related to coverage limitations, infrastructure dependencies, security risks, scalability challenges, and potential points of failure. Addressing these constraints requires careful planning, implementation of best practices, and ongoing maintenance to ensure the efficient and secure operation of the LAN. PAN (Personal Area Network) Personal Area Network is a network arranged within an individual person, typically within a range of 10 meters. Personal Area Network is used for connecting the computer devices of personal use is known as Personal Area Network. Thomas Zimmerman was the first research scientist to bring the idea of the Personal Area Network. Personal Area Network covers an area of 30 feet. Personal computer devices that are used to develop the personal area network are the laptop, mobile phones, media player and play stations. There are two types of Personal Area Network - Wireless Personal Area Network - Wireless Personal Area Network is developed by simply using wireless technologies such as WiFi, Bluetooth. It is a low range network. Wired Personal Area Network - Wired Personal Area Network is created by using the USB. Examples Of Personal Area Network Body Area Network - Body Area Network is a network that moves with a person. For example, a mobile network moves with a person. Suppose a person establishes a network connection and then creates a connection with another device to share the information. Offline Network - An offline network can be created inside the home, so it is also known as a home network. A home network is designed to integrate the devices such as printers, computer, television but they are not connected to the internet. Small Home Office - It is used to connect a variety of devices to the internet and to a corporate network using a VPN Benefits: 1. Connectivity : PANs enable seamless connectivity between personal devices such as smartphones, tablets, laptops, wearable devices, and IoT (Internet of Things) gadgets. This interconnectedness allows for data sharing, synchronization, and collaboration among devices. 2. Convenience : PANs offer convenience by eliminating the need for physical connections like cables. Devices can communicate wirelessly using technologies such as Bluetooth, Wi-Fi Direct, or NFC (Near Field Communication), enhancing mobility and flexibility for users. 3. Integration : PANs facilitate the integration of various technologies and devices into a unified ecosystem. Users can easily integrate their smartphones with wearable devices, smart home appliances, and other gadgets to create personalized and interconnected experiences. 4. Portability : PANs are designed for portability, allowing users to carry their personal devices and networks with them wherever they go. This portability enables seamless connectivity and communication regardless of the user's location or environment. 5. Privacy : Since PANs are typically limited to a small area around the individual, they offer enhanced privacy and security compared to larger networks like LANs or WANs. Users have greater control over the devices and data within their PAN, reducing the risk of unauthorized access or data breaches. Constraints: 1. Limited Range : The primary constraint of a PAN is its limited range, typically ranging from a few meters to a few tens of meters depending on the wireless technology used. This limited range restricts communication to devices within close proximity, making PANs unsuitable for long-distance communication. 2. Interference : Wireless communication technologies used in PANs, such as Bluetooth and Wi-Fi, may experience interference from other electronic devices or networks operating in the same frequency band. This interference can degrade signal quality and affect the performance of connected devices. 3. Security Risks : PANs are susceptible to security risks such as unauthorized access, data interception, and device tampering. Users need to implement security measures such as encryption, authentication, and access controls to protect their devices and data from malicious attacks. 4. Compatibility Issues : Devices within a PAN may use different communication protocols or standards, leading to compatibility issues. Ensuring interoperability between devices and maintaining compatibility with evolving technologies can be challenging for users managing a PAN. 5. Limited Scalability : PANs are typically designed for personal use and may not support scalability to accommodate a large number of devices or users. As the number of devices in the PAN grows, managing connectivity and ensuring optimal performance can become more complex. Despite these constraints, PANs offer significant benefits in terms of connectivity, convenience, integration, portability, and privacy, making them ideal for personal and localized communication needs. By addressing security concerns, ensuring compatibility, and managing interference, users can maximize the advantages of PANs while minimizing their limitations. MAN (Metropolitan Area Network) A metropolitan area network is a network that covers a larger geographic area by interconnecting a different LAN to form a larger network. Government agencies use MAN to connect to the citizens and private industries. In MAN, various LANs are connected to each other through a telephone exchange line. The most widely used protocols in MAN are RS-232, Frame Relay, ATM, ISDN, OC-3, ADSL, etc. It has a higher range than Local Area Network(LAN). Uses Of Metropolitan Area Network MAN is used in communication between the banks in a city. It can be used in an Airline Reservation. It can be used in a college within a city. It can also be used for communication in the military. A MAN (Metropolitan Area Network) is a type of network that covers a larger geographic area than a LAN but smaller than a WAN, typically spanning across a city or metropolitan area. Let's explore the benefits and constraints of a MAN network: Benefits: 1. Coverage : One of the primary benefits of a MAN network is its extended coverage over a metropolitan area. It allows organizations and businesses within the city to connect their various locations, branches, or campuses seamlessly. 2. High-Speed Connectivity : MAN networks often utilize high-speed technologies such as fiber optics or Ethernet to provide fast and reliable connectivity. This enables efficient data transfer and communication between different sites or users within the metropolitan area. 3. Scalability : MAN networks are designed to accommodate the growing needs of businesses and organizations within the metropolitan area. They can easily scale up to support additional users, devices, and network services as required, making them suitable for evolving business requirements. 4. Cost-Effectiveness : Compared to wide area networks (WANs), MAN networks are generally more cost-effective to deploy and maintain, especially for organizations operating within a single metropolitan area. They offer a balance between the coverage of WANs and the cost-effectiveness of LANs. 5. Centralized Management : MAN networks allow for centralized management and administration of network resources, services, and security policies. This centralized management simplifies network operations, troubleshooting, and maintenance across multiple locations within the metropolitan area. Constraints: 1. Infrastructure Investment : Establishing a MAN network requires significant investment in infrastructure, including laying fiber optic cables, deploying network equipment, and ensuring connectivity across the metropolitan area. This initial investment can be a barrier for smaller organizations or municipalities. 2. Complexity : MAN networks can be complex to design, deploy, and manage due to the diverse range of technologies, protocols, and services involved. Network administrators need specialized knowledge and expertise to ensure optimal performance and reliability across the network. 3. Security Concerns : MAN networks are vulnerable to security threats such as unauthorized access, data breaches, and cyber attacks. With multiple sites and users interconnected within the metropolitan area, ensuring robust security measures such as encryption, access controls, and intrusion detection systems is essential. 4. Interference and Signal Degradation : In densely populated metropolitan areas, MAN networks may experience interference and signal degradation due to electromagnetic interference, physical obstacles, or environmental factors. This can impact the reliability and performance of the network, especially for wireless technologies. 5. Regulatory Compliance : MAN networks may be subject to regulatory requirements and compliance standards imposed by government authorities or industry regulations. Ensuring compliance with these regulations, such as data privacy laws or network neutrality regulations, can add complexity and cost to MAN network operations. Despite these constraints, MAN networks offer significant benefits in terms of coverage, highspeed connectivity, scalability, cost-effectiveness, and centralized management for organizations and businesses operating within a metropolitan area. By addressing the challenges associated with infrastructure investment, complexity, security, interference, and regulatory compliance, organizations can leverage the advantages of MAN networks to support their communication and networking needs effectively. WAN (Wide Area Network) A Wide Area Network is a network that extends over a large geographical area such as states or countries. A Wide Area Network is quite bigger network than the LAN. A Wide Area Network is not limited to a single location, but it spans over a large geographical area through a telephone line, fibre optic cable or satellite links. The internet is one of the biggest WAN in the world. A Wide Area Network is widely used in the field of Business, government, and education. Examples Of Wide Area Network Mobile Broadband - A 4G network is widely used across a region or country. Last mile - A telecom company is used to provide the internet services to the customers in hundreds of cities by connecting their home with fiber. private network - A bank provides a private network that connects the 44 offices. This network is made by using the telephone leased line provided by the telecom company. Benefits: 1. Geographic Reach : One of the primary benefits of a WAN network is its extensive geographic reach. It enables organizations to connect their remote offices, branches, and facilities located in different cities, countries, or continents, facilitating seamless communication and collaboration. 2. Scalability : WAN networks are designed to scale up and accommodate the growing needs of organizations, regardless of their geographic spread. As businesses expand or add new locations, WANs can easily adapt to support additional users, devices, and network services. 3. Centralized Management : WAN networks allow for centralized management and administration of network resources, services, and policies across multiple locations. This centralized management simplifies network operations, troubleshooting, and maintenance, leading to improved efficiency and cost savings. 4. Redundancy and Resilience : WAN networks often incorporate redundancy and resilience features to ensure high availability and reliability of network services. Technologies such as multipath routing, link aggregation, and failover configurations help mitigate the impact of network failures or outages. 5. Global Connectivity : WAN networks provide global connectivity, enabling organizations to access resources, data, and services from anywhere in the world. This global reach fosters international collaboration, expands market opportunities, and supports remote work initiatives. Constraints: 1. Cost : Establishing and maintaining a WAN network can be costly, especially for organizations with extensive geographic coverage and bandwidth requirements. Expenses include infrastructure investment, leased lines, network equipment, and ongoing operational costs such as maintenance and bandwidth fees. 2. Complexity : WAN networks are inherently complex due to their large scale, diverse technologies, and distributed nature. Designing, deploying, and managing a WAN network requires specialized knowledge and expertise, as well as coordination across multiple locations and teams. 3. Security Risks : WAN networks are vulnerable to various security threats such as unauthorized access, data breaches, malware attacks, and distributed denial-of-service (DDoS) attacks. Securing a WAN network requires implementing robust security measures such as encryption, firewalls, intrusion detection systems, and access controls. 4. Latency and Performance : WAN networks may experience latency and performance issues, especially for applications requiring real-time data transmission or high-bandwidth requirements. Factors such as network congestion, distance, and routing inefficiencies can impact the responsiveness and throughput of the network. 5. Dependency on Service Providers : WAN networks often rely on third-party service providers for connectivity, bandwidth, and infrastructure. Organizations must carefully select and manage their service providers to ensure quality of service, reliability, and compliance with service level agreements (SLAs). Despite these constraints, WAN networks offer significant benefits in terms of geographic reach, scalability, centralized management, redundancy, resilience, and global connectivity for organizations operating across distributed locations. By addressing the challenges associated with cost, complexity, security, performance, and service provider management, organizations can leverage the advantages of WAN networks to support their communication, collaboration, and business needs effectively. IEEE IEEE stands for the Institute of Electrical and Electronics Engineers. It is a professional association and standards organization dedicated to advancing technology for the benefit of humanity. IEEE develops and publishes technical standards for various industries, including electrical and electronics engineering, telecommunications, information technology, and more. IEEE standards cover a wide range of topics, including networking, wireless communication, power systems, software engineering, and biomedical technology. These standards are developed through a consensus-based process involving experts from academia, industry, and government. Some well-known IEEE standards include: 1. IEEE 802.3: Defines the standards for Ethernet networks, including wired LAN technologies like Ethernet and Wi-Fi. 2. IEEE 802.11: Specifies the standards for wireless LAN (Wi-Fi) technologies, including protocols for wireless communication and network security. 3. IEEE 802.1: Covers standards for network architecture, including protocols for bridging and network management. 4. IEEE 754: Defines standards for floating-point arithmetic in computer systems, including formats for representing and manipulating floating-point numbers. 5. IEEE 754-2008: Revised version of the IEEE 754 standard, incorporating updates and clarifications. 6. IEEE 1613: Specifies standards for environmental and testing requirements for networking equipment used in electric power substations. Overall, IEEE plays a crucial role in promoting technological innovation and interoperability by developing and maintaining standards that facilitate the development and deployment of advanced technologies across various industries. 1.1 Main IEEE Ethernet Standards IEEE 802.3 Ethernet - 1. Standard for Wired Ethernet Networks - IEEE 802.3 Ethernet defines the standard for wired Ethernet networks, specifying the rules and protocols for data transmission over Ethernet cables. It outlines the frame format, data encoding methods, and collision detection mechanisms used in Ethernet networks. 2. Supports Various Media Types - Ethernet supports various media types for network connectivity, including twisted pair, fiber optic, and coaxial cable. This versatility allows organizations to choose the most suitable media type based on factors such as distance, bandwidth requirements, and environmental conditions. 3. Options for Different Data Rates - IEEE 802.3 Ethernet provides options for different data rates, ranging from 10 Mbps (Ethernet) to 100 Gbps (Ethernet). This flexibility enables organizations to scale their network bandwidth according to their requirements, whether it's for small office networks or high-performance data centers. IEEE 802.11 Wireless LAN - 1. Standard for Wireless LANs - IEEE 802.11 Wireless LAN specifies the standards for wireless local area networks (LANs), defining protocols for medium access control (MAC) and physical layer (PHY). It governs how wireless devices communicate with each other within a WLAN. 2. Offers Different Variants - IEEE 802.11 offers various variants such as 802.11a, 802.11b, 802.11g, 802.11n, 802.11ac, and 802.11ax. Each variant operates on different frequency bands and supports different data rates, allowing organizations to choose the most suitable option based on their specific requirements and environmental conditions. 3. Supports Security and QoS Features - IEEE 802.11 WLANs support features like encryption, authentication, and quality of service (QoS) to ensure secure and reliable wireless communication. These features help protect sensitive data transmitted over the wireless network and prioritize certain types of traffic for better performance. Benefits and Constraints of LAN and WLAN for Matara Branch - - LAN Benefits - Provides high-speed connectivity within the branch, facilitating efficient communication between departments. - Allows for the separation of departments with unique subnets, meeting management's requirement for organizational structure. - Simplifies network management and troubleshooting, as all devices are connected through a wired infrastructure. - WLAN Benefits - Equipping areas like the reception and customer services with Wi-Fi facilities offers flexibility and mobility for employees and guests. - Facilitates connectivity for wireless devices such as laptops, smartphones, and tablets, enhancing productivity and collaboration. Constraints - The limited range of LAN may require additional infrastructure for connectivity between the head office and the Matara branch, such as dedicated leased lines or VPN connections. - WLAN may be susceptible to interference and security vulnerabilities, necessitating proper network design and security measures such as encryption and access control. Conclusion Implementing a combination of LAN and WLAN at the Matara branch ensures efficient connectivity and meets the company's requirements for departmental separation and Wi-Fi access. Utilizing IEEE Ethernet standards ensures compatibility and reliability in network communication, providing a solid foundation for the branch's networking infrastructure. P2 Network topology, communication, and bandwidth requirements are crucial aspects of designing and managing a network. Let's explore their impact: 1. Network Topology : Network topology refers to the physical or logical layout of interconnected devices and nodes in a network. Different network topologies, such as star, mesh, bus, ring, or hybrid, have distinct characteristics that influence network performance, scalability, and fault tolerance. - Impact : The choice of network topology can significantly impact network performance, reliability, and scalability: - Performance : The topology affects data transmission speed, latency, and efficiency. For example, a star topology with centralized connectivity offers fast data transfer and easy troubleshooting, while a mesh topology with redundant paths provides fault tolerance and resilience. - Scalability : Some topologies are more scalable than others. For instance, a bus topology may become congested as more devices are added, while a mesh or hybrid topology can accommodate growth more effectively by adding new connections or nodes. - Reliability : The topology influences network reliability and fault tolerance. Redundant paths in mesh or ring topologies can prevent single points of failure and ensure uninterrupted connectivity, whereas a failure in a single point in a bus topology can disrupt the entire network. - Complexity : Different topologies vary in complexity, affecting network management, troubleshooting, and maintenance. For example, a mesh topology with numerous connections may require more configuration and management efforts compared to a star or bus topology. 2. Communication : Communication refers to the exchange of data and information between devices and nodes within a network. Efficient communication protocols, addressing schemes, and routing algorithms are essential for establishing and maintaining effective communication within the network. - Impact : Effective communication is vital for network performance, reliability, and security: - Performance : Communication protocols and routing algorithms impact data transmission speed, latency, and efficiency. Well-designed protocols can optimize network traffic and minimize delays, improving overall performance. - Reliability : Reliable communication protocols ensure accurate data transmission and error detection/correction mechanisms. Robust routing algorithms can dynamically adapt to network changes, ensuring data reaches its destination reliably. - Security : Secure communication protocols and encryption mechanisms protect sensitive data from interception, tampering, or unauthorized access. Secure communication is essential for maintaining data confidentiality, integrity, and privacy within the network. 3. Bandwidth Requirements : Bandwidth refers to the maximum rate of data transfer across a network, typically measured in bits per second (bps) or megabits per second (Mbps). Bandwidth requirements vary based on the volume of data traffic, the number of users/devices, and the type of applications/services running on the network. - Impact : Bandwidth requirements affect network performance, scalability, and user experience: - Performance : Inadequate bandwidth can lead to network congestion, slow data transfer speeds, and increased latency. Sufficient bandwidth ensures smooth and responsive network performance, especially for bandwidth-intensive applications like video streaming or VoIP. - Scalability : Network bandwidth must scale to accommodate growing data traffic and user demands. Scalable bandwidth options, such as fiber optics or high-speed Ethernet, allow for expansion and accommodate increased bandwidth requirements over time. - User Experience : Bandwidth availability directly impacts user experience and productivity. Insufficient bandwidth can result in slow application performance, buffering during multimedia streaming, and degraded quality of service, leading to user frustration and dissatisfaction. In summary, network topology, communication, and bandwidth requirements play integral roles in shaping network performance, reliability, scalability, and user experience. By carefully considering these factors during network design, implementation, and management, organizations can build robust, efficient, and resilient networks that meet their communication needs effectively. M1 Common networking principles serve as foundational concepts that guide the design, implementation, and management of networked systems. These principles, along with networking protocols, play crucial roles in enabling the effectiveness of networked systems. Let's assess some common networking principles and their relationship with protocols: 1. Interoperability : - Principle : Interoperability refers to the ability of different systems, devices, or applications to communicate and work together seamlessly, regardless of their underlying technologies or manufacturers. - Protocols : Networking protocols define standardized rules and conventions for communication between devices and systems. Protocols such as TCP/IP (Transmission Control Protocol/Internet Protocol) ensure interoperability by establishing common communication standards used across the internet and other networks. 2. Scalability : - Principle : Scalability refers to the ability of a network to accommodate growth in terms of the number of users, devices, or data traffic without sacrificing performance or reliability. - Protocols : Scalable protocols, such as BGP (Border Gateway Protocol) for routing or DHCP (Dynamic Host Configuration Protocol) for IP address assignment, enable networks to adapt to changes in size and demand dynamically. These protocols support features like load balancing, route aggregation, and automatic address allocation to scale network resources efficiently. 3. Reliability : - Principle : Reliability ensures that networked systems consistently deliver data accurately and without errors, even in the face of network disruptions, failures, or adverse conditions. - Protocols : Reliable protocols, such as TCP (Transmission Control Protocol), provide mechanisms for error detection, retransmission of lost packets, and flow control to ensure data integrity and delivery. These protocols enhance network reliability by mitigating the impact of packet loss, congestion, or network errors. 4. Security : - Principle : Security involves protecting networked systems, data, and resources from unauthorized access, malicious attacks, and data breaches. - Protocols : Security protocols, such as SSL/TLS (Secure Sockets Layer/Transport Layer Security) for encrypted communication or IPsec (Internet Protocol Security) for secure IP layer communication, establish secure connections and encryption mechanisms to safeguard data confidentiality, integrity, and authenticity. These protocols authenticate users, encrypt data transmissions, and enforce access controls to prevent unauthorized access and protect sensitive information. 5. Performance Optimization : - Principle : Performance optimization aims to maximize network efficiency, throughput, and responsiveness to meet user requirements and application demands. - Protocols : Performance-enhancing protocols, such as UDP (User Datagram Protocol) for low-latency communication or ICMP (Internet Control Message Protocol) for network diagnostics, optimize network performance by minimizing overhead, reducing latency, and prioritizing traffic. These protocols support features like Quality of Service (QoS), traffic prioritization, and congestion control to optimize network resources and improve user experience. 6. Simplicity : - Principle : Simplicity emphasizes the importance of keeping network designs, configurations, and operations straightforward and manageable to reduce complexity and minimize potential points of failure. - Protocols : Simple and standardized protocols, such as Ethernet for LAN connectivity or DNS (Domain Name System) for name resolution, promote simplicity by providing clear and well-defined communication mechanisms. These protocols facilitate easy configuration, troubleshooting, and maintenance of networked systems, leading to more robust and reliable networks. In summary, common networking principles provide guiding principles for building effective networked systems, while protocols serve as the implementation mechanisms that enable these principles to be realized in practice. By adhering to these principles and leveraging appropriate protocols, organizations can design, deploy, and manage resilient, scalable, secure, and highperformance networks that meet their communication needs effectively. 1.2 Network topologies play a crucial role in determining how devices are connected and communicate within a network. The choice of network topology can significantly impact factors such as scalability, performance, fault tolerance, and ease of management. Additionally, selecting the appropriate network protocols ensures efficient and reliable data transmission across the network. Let's discuss the importance and impact of network topologies and network protocol suites in the context of Alliance Health's expansion to the Matara branch - Importance of Network Topologies - 1. Scalability - The network topology should support the growth of the organization, allowing for easy expansion and addition of new devices or departments. A scalable topology ensures that the network can accommodate future requirements without significant redesign. 2. Performance - The topology affects the performance of the network in terms of data transfer speeds, latency, and throughput. A well-designed topology minimizes bottlenecks and ensures optimal performance for critical applications and services. 3. Fault Tolerance - Redundancy and fault tolerance are essential for ensuring network reliability and minimizing downtime. Topologies with built-in redundancy mechanisms, such as ring or mesh topologies, can automatically reroute traffic in case of link failures, ensuring continuous operation. 4. Ease of Management - The topology should be easy to manage and troubleshoot. Simplified topologies, such as star or hierarchical designs, offer centralized management points, making it easier to monitor and maintain the network infrastructure. Impact of Network Protocol Suites - 1. TCP/IP Protocol Suite - TCP/IP is the standard protocol suite used in modern networks, providing reliable and connection-oriented communication. It comprises several protocols, including IP, TCP, UDP, and ICMP, each serving different functions such as addressing, routing, and error detection. 2. Ethernet - Ethernet is the most widely used LAN protocol, defining the standards for wired communication. It ensures data integrity, frame formatting, and collision detection, making it suitable for local network communication within the branches. 3. Wireless Protocols (e.g., IEEE 802.11) - Wireless protocols are essential for providing Wi-Fi connectivity within the branches. IEEE 802.11 standards govern wireless LAN communication, specifying protocols for medium access control (MAC) and physical layer (PHY). These standards ensure interoperability and compatibility among Wi-Fi-enabled devices. Recommendation for Network Topology and Protocols - For the Alliance Health Matara branch, a hierarchical network topology combined with TCP/IP protocol suite and Ethernet/Wi-Fi protocols would be suitable - 1. Hierarchical Topology - Implementing a hierarchical topology with core, distribution, and access layers allows for efficient network management and scalability. Core switches at the head office and Matara branch ensure inter-branch connectivity, while distribution and access switches within each branch facilitate departmental segmentation and connectivity. 2. TCP/IP Protocol Suite - Leveraging the TCP/IP protocol suite ensures reliable and standardized communication across the network. IP addresses can be assigned to each department using subnetting, meeting the requirement for unique subnets. 3. Ethernet/Wi-Fi Protocols - Ethernet protocols (IEEE 802.3) can be used for wired connectivity within the branches, providing high-speed and reliable communication. Wi-Fi protocols (IEEE 802.11) enable wireless connectivity in areas like the reception and customer services, enhancing mobility and flexibility for employees and guests. Efficient Utilization of the Networking System - - The hierarchical topology ensures efficient traffic management and scalability by dividing the network into logical layers. - TCP/IP protocol suite ensures seamless communication and compatibility across different devices and network segments. - Ethernet and Wi-Fi protocols offer reliable wired and wireless connectivity, meeting the diverse communication needs of the organization. - Departmental segmentation with unique subnets enhances security and network performance by isolating traffic and reducing broadcast domains. Overall, the recommended network topology and protocols ensure efficient utilization of the networking system at the Matara branch, meeting Alliance Health's requirements for connectivity, scalability, and reliability. TASK 02 Operating Principles of Network Devices In simple terms, a network device is a physical device that is used to connect other physical devices on a network. In some cases, their role is to simply forward packets of information to a destination. In other cases, it might be to serve as a translator or to block suspicious network traffic. The most common types of network devices include hubs, switches, routers, bridges, gateways, modems, repeaters, and access points. 1. Router Routers operate at the network layer (Layer 3) of the OSI model and are responsible for forwarding data packets between different networks. They use routing tables to determine the best path for packet forwarding based on destination IP addresses. Routers provide segmentation and isolation of network traffic, allowing for efficient communication between different subnets or VLANs. They support features such as NAT (Network Address Translation), DHCP (Dynamic Host Configuration Protocol), and firewall capabilities for network security. 2. Switch Switches operate at the data link layer (Layer 2) of the OSI model and are responsible for forwarding data frames within the same network segment or VLAN. They use MAC addresses to forward frames to the appropriate ports based on the destination MAC address. Switches provide high-speed and dedicated connections between devices within the same network segment, eliminating collisions and improving network performance. They support features such as VLANs (Virtual Local Area Networks), QoS (Quality of Service), and port security for network segmentation and traffic prioritization. Hub Hubs are used to connect multiple network devices together. They can be used to transmit both digital and analog information. Digital information is transmitted as packets, whereas analog information is transmitted as a signal. Hubs also act as a repeater, which amplifies signals that have weakened after being transmitted across a long distance. Hubs operate at the Physical layer of the Open Systems Interconnection (OSI) model. bridge A bridge is used to connect hosts or network segments together. As with routers, they can be used to divide larger networks into smaller ones, by sitting between network devices and regulating the flow of traffic. A bridge also has the ability to filter packets of data, known as frames, before they are forwarded. Bridges are not as popular as they once were, and are now being replaced by switches, which provide better functionality. Gateway A gateway device is used to facilitate interoperability between different technologies such as Open System Interconnection (OSI) and Transmission Control Protocol/Internet Protocol (TCP/IP). In other words, they translate each other’s messages. You could think of a gateway as a router, but with added translation functionality. Recommended Servers for the Scenario Servers Servers are dedicated computers or hardware devices that provide services or resources to other computers, known as clients, over a network. There are various types of servers available in the market, including, File Servers: Store and manage files and data for users within the network. Application Servers: Host and manage applications that are accessed by users over the network. Database Servers: Store, manage, and provide access to databases and data management services. Web Servers: Host websites and web applications, serving web content to clients over HTTP. Mail Servers: Manage email communication, including sending, receiving, and storing emails. In the scenario, servers will be deployed in the server room to host critical applications, databases, and services required by different departments, such as HR, Accounting & Finance, and IT. Recommendation for Servers Based on the requirements and scale of Alliance Health's operations, the following servers are recommended for deployment: File Server Specification: Dual-core processor, 8GB RAM, RAID storage with at least 1TB capacity. Justification: This server will store and manage files and data for different departments, ensuring centralized access and data management. Application Server Specification: Quad-core processor, 16GB RAM, SSD storage with at least 500GB capacity. Justification: This server will host and manage critical applications used by various departments, such as HR management software, accounting software, and business intelligence tools. Database Server Specification: Hexa-core processor, 32GB RAM, RAID storage with at least 2TB capacity. Justification: This server will store, manage, and provide access to databases containing important healthcare industry data and revenue cycle information. Web Server Specification: Quad-core processor, 16GB RAM, SSD storage with at least 500GB capacity. Justification: This server will host the company's website and web-based applications, providing access to clients and employees for information and services. Mail Server Specification: Quad-core processor, 16GB RAM, RAID storage with at least 1TB capacity. Justification: This server will manage email communication for the company, ensuring reliable and efficient email services for employees. By deploying these servers with appropriate specifications, Alliance Health can ensure reliable, scalable, and efficient network services to support its business operations at both the head office in Colombo and the branch in Matara. Compare server types Server type Function Typical specifications Main use cases File server Stores and manages Dual-core processor, Centralized file files and data for 8GB RAM, RAID storage and sharing network users storage (1TB capacity) Application server Hosts and manages Quad-core processor, Hosting applications business for 16GB RAM, SSD applications network users storage and (500GB tools capacity) Web server Hosts websites web- Quad-core processor, Serving web content based applications 16GB RAM, SSD to clients storage (500GB capacity) Mail server Manage email Quad-core processor, Sending, receiving, communication the organization for 16GB storage RAM,SSD and storing emails (500GB capacity) Database server Stores, manages, and Hexa-core processor, Storing provides access to 32GB RAM, RAID managing databases storage and critical (2TB business data capacity) Each type of server serves a distinct purpose within a network infrastructure, providing essential services to support the organization's operations. The specifications listed are typical for each server type and may vary depending on the specific requirements and scale of the organization. When selecting a server for a given scenario, it's essential to consider factors such as the specific requirements of the workload, anticipated performance needs, scalability requirements, budget constraints, and long-term maintenance costs. By carefully evaluating these factors and choosing the appropriate server type, organizations can optimize both cost and performance to meet their business objectives effectively. 2.2 The inter-dependence of workstation hardware and networking software is crucial for the effective functioning of a network. Workstation hardware refers to the physical components of computers or devices used by employees, while networking software includes the programs and protocols that enable communication and data exchange over the network. Here's how workstation hardware and networking software are inter-dependent: 1. Network Interface Cards (NICs) and Drivers: Workstation hardware: NICs are physical network adapters installed in computers to connect them to the network. Networking software: NIC drivers are software components that enable the operating system to communicate with the NIC and establish network connections. Example - Ethernet drivers for wired connections or Wi-Fi drivers for wireless connections. 2. Operating Systems (OS): Workstation hardware - The OS is installed on computers and manages hardware resources, including network interfaces. Networking software - The OS includes networking protocols and services for communication over the network. Example - Windows, Linux, macOS, which provide built-in networking support for TCP/IP, DHCP, DNS, etc. 3. Network Protocols and Services: Workstation hardware - Workstations utilize network protocols for data transmission and network services for various functionalities. Networking software - Network protocols and services handle tasks such as addressing, routing, and data transfer between workstations and servers. Example - TCP/IP, UDP, HTTP, FTP, DNS, DHCP, which enable communication and resource sharing across the network. 4. Firewalls and Security Software Workstation hardware: Firewalls may be implemented as hardware appliances or software applications to protect workstations from unauthorized access. Networking software - Firewall software monitors and filters network traffic to enforce security policies and prevent malicious activities. Example - Windows Firewall, third-party firewall software, antivirus programs, which safeguard workstations from network threats. 5. Remote Desktop Software Workstation hardware - Workstations can access and control remote computers or servers over the network. Networking software: Remote desktop software facilitates remote access and administration of workstations or servers. Example - Remote Desktop Protocol (RDP), VNC (Virtual Network Computing), TeamViewer, which enable remote management and troubleshooting. The selection and configuration of networking software depend on the hardware capabilities of workstations and the specific requirements of the network infrastructure. Compatibility between workstation hardware and networking software ensures seamless communication and efficient network operations. D1 For the given scenario, the most suitable network topology protocol would be a combination of a hierarchical topology for the internal network within each office and a point-to-point connection for inter-branch connectivity. Hierarchical Topology : A hierarchical topology divides the network into multiple layers, such as core, distribution, and access layers, to provide scalability, flexibility, and efficient resource utilization. This topology is well-suited for large organizations with multiple departments and offices. Point-to-Point Connection : For inter-branch connectivity between the head office in Colombo and the branch in Matara, a point-to-point connection, such as a leased line or a dedicated VPN connection, would be appropriate. This type of connection ensures reliable and secure communication between the two locations, enabling seamless access to shared resources and services. Network Architectural Design : Based on the requirements provided by Alliance Health and the given floor plans, here is a proposed network architectural design: 1. Head Office in Colombo : - Floor 1 : - Reception Area - Sales & Marketing Department (10 employees) - Customer Services Area with Wi-Fi - Floor 2 : - Administration Department (30 employees) - HR Department (20 employees) - Accounting & Finance Department (15 employees) - Audit Department (5 employees) - Business Development Department (5 employees) - Floor 3 : - Video Conferencing Room - IT Department (60 employees) - Server Room 2. Branch Office in Matara : - Floor 1 : - Reception Area - Customer Services Area with Wi-Fi - Floor 2 : - Administration Department (10 employees) - HR Department (7 employees) - Accounting & Finance Department (8 employees) - IT Department (50 employees) Network Implementation : 1. Assigning Unique Subnets: - Each department in both offices will be assigned a unique subnet, ensuring network segregation and security. - Assumption: Use of Class B private IP addressing scheme (e.g., 172.16.0.0/16) to provide enough address space for each department. 2. Wi-Fi Connectivity: - Wi-Fi access points will be installed in the reception areas and customer services areas of both offices. - VLANs will be configured to segregate Wi-Fi traffic from the wired network. 3. Inter-Branch Connectivity: - A point-to-point VPN connection will be established between the head office and the branch office. - Assumption: Use of IPsec VPN for secure communication. 4. Server Room: - Assign the subnet 10.254.10.0/24 for the server room in the head office. - Install 10 servers in the server room with static IPs assigned from the subnet. 5. Sales and Marketing Team: - Provide Wi-Fi access to the Sales and Marketing Department in the head office. - Configure VLANs to separate Sales and Marketing Department traffic from other departments. Justification : - Hierarchical topology ensures efficient resource allocation, scalability, and ease of management. - Point-to-point connection between branches ensures secure and reliable inter-branch communication. - Unique subnets for each department provide network segmentation, improving security and performance. - Use of VLANs for Wi-Fi connectivity ensures segregation of traffic and efficient utilization of network resources. - Assignment of static IPs for servers in the server room facilitates easy management and access control. By implementing this network design, Alliance Health can meet its requirements for departmental segregation, Wi-Fi connectivity, inter-branch communication, and server management, while optimizing cost and performance. Network Design Plan 1. Network Overview: - The network design will encompass both the head office in Colombo and the branch in Matara. - Each department will have its own subnet to ensure network segmentation and security. - Wi-Fi facilities will be provided in the reception area and Customer Services Areas at both locations. - Connectivity between the two branches will enable intra-branch communication between departments. - IP address classes and ranges will be assigned based on the requirements, excluding the server room which will use the 10.254.10.0/24 subnet. 2. Hardware and Infrastructure: - Switches: Managed switches will be deployed to provide VLAN segmentation and optimize network traffic. - Routers: Router devices will be utilized for inter-branch connectivity and routing between subnets. - Wireless Access Points (APs): APs will be strategically placed to ensure optimal coverage for Wi-Fi connectivity. - Cabling: Cat6 Ethernet cabling will be used for wired connections, ensuring high-speed data transmission. - Servers: Server hardware will be deployed in the server room to host critical applications and services. 3. Network Security: - Firewall: Firewalls will be implemented to protect the network from external threats and unauthorized access. - Access Control: Role-based access control mechanisms will be enforced to restrict access to sensitive data and resources. - Encryption: Data encryption protocols will be employed to secure data transmission over the network, especially for wireless connections. - Security Policies: Comprehensive security policies will be established to govern network usage and compliance. 4. Network Monitoring and Management: - Network Monitoring Tools: Network monitoring software will be used to monitor network performance, detect anomalies, and troubleshoot issues proactively. - Configuration Management: Configuration management tools will be employed to maintain consistency and integrity across network devices and configurations. - Regular Audits: Periodic network audits will be conducted to assess security posture, identify vulnerabilities, and ensure compliance with industry standards. 5. User Training and Support: - User Training: Training sessions will be conducted to educate employees on network usage, security best practices, and troubleshooting procedures. - Helpdesk Support: A dedicated helpdesk team will provide technical assistance and support to users for network-related issues and inquiries. Blueprint:  Testing and Evaluation: User feedback will be collected through surveys, interviews, and observations to assess the usability, performance, and effectiveness of the network design. - Analyzing user feedback will help identify areas for improvement and optimization, such as network performance, user experience, and security concerns. - Iterative testing and evaluation will be conducted to refine the network design and address any issues or shortcomings identified during the testing phase. By incorporating user feedback and continuously optimizing the network design, we aim to ensure that the network infrastructure meets the needs of Alliance Health's expanding business operations in both Colombo and Matara, while maintaining security, reliability, and efficiency. TASK 03 Network Design Plan: 2nd floor Matara branch 1. VLAN and IP Subnetting Scheme: Head Office in Colombo: - VLAN 10: Reception area (192.168.10.0/24) - VLAN 20: Sales & Marketing Department (192.168.20.0/24) - VLAN 30: Customer Services Area (192.168.30.0/24) - VLAN 40: Administration Department (192.168.40.0/24) - VLAN 50: HR Department (192.168.50.0/24) - VLAN 60: Accounting & Finance Department (192.168.60.0/24) - VLAN 70: Audit Department (192.168.70.0/24) - VLAN 80: Business Development Department (192.168.80.0/24) - VLAN 90: Video Conferencing Room (192.168.90.0/24) - VLAN 100: IT Department (192.168.100.0/24) - VLAN 110: Server Room (10.254.10.0/24 - Static IPs) Branch Office in Matara: - VLAN 120: Reception area (192.168.120.0/24) - VLAN 130: Customer Services Area (192.168.130.0/24) - VLAN 140: Administration Department (192.168.140.0/24) - VLAN 150: HR Department (192.168.150.0/24) - VLAN 160: Accounting & Finance Department (192.168.160.0/24) - VLAN 170: IT Department (192.168.170.0/24) 2. List of Devices and Network Components: - Layer 3 Switches (for inter-VLAN routing) - Access Points (for Wi-Fi connectivity) - Routers (for inter-branch connectivity) - Firewall/UTM (for security) - Ethernet Cables - Patch Panels - Network Switches - Network Printers - Network Attached Storage (NAS) - Server Rack - Power Distribution Units (PDUs) 3. Software Used: - Cisco IOS for Switches and Routers - Cisco Packet Tracer for Network Simulation - Microsoft Visio for Network Diagrams - Wireshark for Network Traffic Analysis - Active Directory for User Authentication - DHCP Server for IP Address Management - DNS Server for Domain Name Resolution - Proxy Server for Internet Access Control Configuration Scripts: Below are the configuration scripts for VLANs and inter-VLAN routing on Layer 3 switches: ``` ! Configuration script for VLANs on Layer 3 Switches vlan 10 name Reception vlan 20 name Sales_Marketing vlan 30 name Customer_Services vlan 40 name Administration vlan 50 name HR vlan 60 name Accounting_Finance vlan 70 name Audit vlan 80 name Business_Development vlan 90 name Video_Conferencing vlan 100 name IT vlan 110 name Server_Room vlan 120 name Reception_Matara vlan 130 name Customer_Services_Matara vlan 140 name Administration_Matara vlan 150 name HR_Matara vlan 160 name Accounting_Finance_Matara vlan 170 name IT_Matara Configuration script for Inter-VLAN Routing interface vlan 10 ip address 192.168.10.1 255.255.255.0 interface vlan 20 ip address 192.168.20.1 255.255.255.0 ! Repeat for all VLANs ip routing ``` Maintenance Schedule: - Weekly: Check and update firewall/UTM rules, review network performance metrics. - Monthly: Perform firmware updates for switches, routers, and access points. Review and update VLAN configurations as needed. - Quarterly: Conduct security audits and vulnerability assessments. Review and update network documentation. - Annually: Perform comprehensive network assessment and optimization. Review disaster recovery and backup procedures. Test and Evaluation: - Conducted network connectivity tests to ensure VLAN separation and inter-branch connectivity. - Tested Wi-Fi connectivity in designated areas and optimized access point placement for coverage. - Analyzed network traffic using Wireshark to identify any bottlenecks or anomalies. - Gathered user feedback to address any usability issues and optimize network performance. Optimization and Improvement: - Implemented VLAN-based network segmentation to enhance security and optimize network traffic. - Upgraded firmware for network devices to ensure compatibility and improve performance. - Fine-tuned firewall/UTM configurations to strengthen network security and mitigate threats. - Enhanced Wi-Fi coverage and performance through access point optimization and channel selection. Conclusion: By following the network design plan, installing and configuring network services, devices, and applications, and conducting thorough testing and evaluation, Alliance Health can ensure a robust and efficient network infrastructure that meets the company's requirements and supports its business operations effectively. Regular maintenance and optimization will be essential to sustain network performance and security over time. P5 Based on the requirements provided by Alliance Health, I'll design a networked system for both the head office in Colombo and the branch office in Matara. Here's the proposed network architecture: Assumptions : 1. Use of Class B private IP addressing scheme (e.g., 172.16.0.0/16) for internal network addressing. 2. Each department will have its own subnet for network segregation. 3. Implementation of Wi-Fi access points for the reception areas and customer services areas in both offices. 4. Connectivity between branches will be established using VPN for intra-branch communication. 5. The server room in Colombo will be assigned the subnet 10.254.10.0/24 for server allocation. 6. Sales and Marketing Department in the head office requires Wi-Fi connectivity. 7. Each office will have its own DHCP server for IP address assignment. Network Design: Head Office in Colombo: - Floor 1 : - Subnet: 172.16.1.0/24 - Reception area - Sales & Marketing Department (Wi-Fi enabled) - Customer Services Area (Wi-Fi enabled) - Floor 2 : - Subnet: 172.16.2.0/24 - Administration Department - HR Department - Accounting & Finance Department - Audit Department - Business Development Department - Floor 3 : - Subnet: 172.16.3.0/24 - Video conferencing room - IT Department - Server Room (10 servers with static IPs from 10.254.10.0/24 subnet) Branch Office in Matara: - Floor 1 : - Subnet: 172.16.4.0/24 - Reception area - Customer Services Area (Wi-Fi enabled) - Floor 2 : - Subnet: 172.16.5.0/24 - Administration Department - HR Department - Accounting & Finance Department - IT Department Network Implementation: 1. Configure VLANs for each department on each floor to ensure network segregation and security. 2. Install Wi-Fi access points in the reception areas and customer services areas on both floors of both offices. 3. Implement VPN connections between the head office in Colombo and the branch office in Matara to facilitate inter-branch communication. 4. Assign static IP addresses from the 10.254.10.0/24 subnet to the servers in the server room in Colombo. 5. Enable Wi-Fi connectivity for the Sales and Marketing Department in the head office. 6. Configure DHCP servers in both offices to assign IP addresses dynamically to client devices. Justification: - Using VLANs and separate subnets for each department ensures network segregation, security, and efficient resource allocation. - Implementation of Wi-Fi access points in key areas enhances mobility and accessibility for employees and visitors. - VPN connections between branches enable secure and reliable inter-branch communication. - Assigning static IPs to servers simplifies management and ensures consistent access to server resources. - Enabling Wi-Fi connectivity for the Sales and Marketing Department enhances productivity and flexibility for employees. By implementing this network architecture, Alliance Health can effectively meet their requirements for network segregation, Wi-Fi connectivity, inter-branch communication, and server management, while ensuring scalability, security, and performance optimization for their expanding business operations. P6 To support the networked system for Alliance Health effectively, a maintenance schedule should be established to ensure the network remains secure, reliable, and optimized. Here's a proposed maintenance schedule: 1. Regular Software Updates and Patch Management : - Schedule regular software updates and patches for network devices, including routers, switches, access points, and servers. - Implement a patch management system to automate the process of deploying updates and patches. - Ensure that updates are applied during scheduled maintenance windows to minimize disruption to network operations. 2. Network Monitoring and Performance Tuning : - Deploy network monitoring tools to continuously monitor network performance, traffic patterns, and device health. - Establish baseline performance metrics and thresholds to identify potential issues and proactively address them. - Conduct regular performance tuning to optimize network resources, bandwidth utilization, and response times. 3. Security Audits and Vulnerability Assessments : - Perform regular security audits and vulnerability assessments to identify potential security risks and weaknesses in the network infrastructure. - Implement intrusion detection and prevention systems (IDS/IPS) to detect and mitigate security threats in real-time. - Conduct penetration testing to simulate cyber-attacks and assess the effectiveness of security measures. 4. Backup and Disaster Recovery Planning : - Implement regular data backups for critical network resources, including servers, databases, and configuration files. - Test backup and disaster recovery procedures regularly to ensure data integrity and rapid recovery in the event of a network outage or data loss. - Store backup data securely offsite or in the cloud to mitigate the risk of data loss due to physical damage or theft. 5. Documentation and Change Management : - Maintain comprehensive documentation of the network architecture, configuration settings, and hardware inventory. - Implement a change management process to track and manage changes to the network infrastructure, including configuration changes, upgrades, and additions. - Ensure that changes are properly documented, tested, and approved before implementation to minimize the risk of disruptions or errors. 6. User Training and Support : - Provide regular training and support for network users to ensure they understand how to use network resources securely and effectively. - Establish a helpdesk or support system to assist users with network-related issues and troubleshoot problems promptly. - Encourage users to report any suspected security incidents or unusual network activity to the IT department for investigation. 7. Review and Planning : - Conduct periodic reviews of the network infrastructure to identify areas for improvement, upgrades, or expansion. - Develop long-term strategic plans for network growth and scalability, taking into account business requirements and technological advancements. - Collaborate with stakeholders to prioritize projects and investments that will enhance the overall performance and reliability of the network. By implementing and adhering to this maintenance schedule, Alliance Health can ensure that their networked system remains secure, reliable, and optimized to support their business operations effectively. Regular maintenance and proactive monitoring will help prevent downtime, minimize security risks, and maximize the performance of the network infrastructure. M3 To analyze user feedback on the network architectural design provided earlier, let's consider potential areas for optimization and efficiency improvement based on user input: 1. Ease of Use and Accessibility : - Users may provide feedback on the ease of accessing network resources, such as file shares, printers, and applications. Optimizing network configuration and access controls to ensure seamless access to resources can enhance user satisfaction and productivity. 2. Network Performance : - Users may report any network performance issues, such as slow connectivity, network congestion, or latency. Conducting performance monitoring and analysis to identify and address bottlenecks or network inefficiencies can improve overall network performance and user experience. 3. Security and Data Protection : - Users may express concerns about network security and data protection measures. Enhancing security protocols, implementing encryption technologies, and enforcing access controls can help address user security concerns and safeguard sensitive data. 4. Reliability and Availability : - Users may provide feedback on network reliability and availability, particularly during peak usage periods or in the event of network failures. Implementing redundancy, failover mechanisms, and disaster recovery plans can enhance network reliability and minimize downtime. 5. Scalability and Flexibility : - Users may request additional network resources or scalability options to support growing business needs. Designing the network architecture with scalability in mind, such as using modular hardware, cloud-based services, or virtualization technologies, can accommodate future growth and evolving business requirements. 6. User Training and Support : - Providing ongoing user training and support can address user feedback related to network usage, troubleshooting, and technical assistance. Offering comprehensive training programs, documentation, and responsive helpdesk support can empower users to maximize their productivity and effectively utilize network resources. 7. Feedback Collection and Improvement Process : - Establishing channels for collecting user feedback and implementing a continuous improvement process can ensure that user concerns and suggestions are addressed promptly. Regularly soliciting feedback through surveys, user forums, or direct communication channels can foster a culture of collaboration and responsiveness within the organization. By analyzing user feedback and implementing optimizations based on their input, the network architecture can be refined to better meet user needs, improve efficiency, and enhance overall satisfaction with the networked system. Regularly monitoring user feedback and iterating on the design can ensure that the network remains aligned with business objectives and user expectations over time. D2 After designing and implementing the network architecture for Alliance Health's head office in Colombo and their branch office in Matara, it's important to critically reflect on the implemented network to evaluate its effectiveness and identify areas for improvement: 1. Network Segmentation : The decision to assign unique subnets to each department ensures network segmentation, which enhances security and facilitates efficient resource allocation. This design choice aligns with industry best practices and helps prevent unauthorized access to sensitive data. 2. Wi-Fi Connectivity : Equipping the conferencing rooms and customer services areas with Wi-Fi connections improves accessibility and flexibility for employees and visitors. However, the Wi-Fi network should be adequately secured to prevent unauthorized access and protect sensitive information. 3. Inter-Branch Connectivity : Enabling connectivity between the head office and the branch office allows for intra-branch communication between departments, which promotes collaboration and seamless operations. While the use of VPN is not compulsory, it may be advisable to implement VPN connections to ensure secure data transmission between locations, especially when dealing with sensitive healthcare data. 4. IP Addressing : The decision to use the 10.254.10.0/24 subnet for the server room and assign static IPs to servers simplifies management and ensures consistent access to server resources. However, careful consideration should be given to IP address allocation to avoid IP conflicts and ensure efficient use of available address space. 5. Wireless Access for Sales and Marketing Team : Providing Wi-Fi connectivity for the Sales and Marketing Department improves their accessibility to network resources and supports their mobility. However, proper security measures should be implemented to protect the network from potential security threats associated with wireless access. 6. Scalability and Future Expansion : The network architecture should be designed with scalability in mind to accommodate future growth and evolving business needs. Regular reviews and assessments should be conducted to identify opportunities for optimization and expansion as the company continues to grow. 7. Documentation and Training : Comprehensive documentation of the network architecture, configuration settings, and procedures is essential for effective management and troubleshooting. Additionally, providing ongoing training and support for network users ensures they are equipped to utilize network resources effectively and securely. In conclusion, while the implemented network design for Alliance Health meets the immediate requirements and supports their business operations, continuous monitoring, evaluation, and refinement are necessary to ensure optimal performance, security, and scalability. Regular updates and adjustments should be made based on evolving business needs, technological advancements, and feedback from users and stakeholders. TASK 04 P7 Based on the provided requirements, here is the network architectural design for Alliance Health's head office in Colombo and their branch office in Matara: Head Office in Colombo: - Floor 1: - Subnet: 192.168.1.0/24 - Reception area - Sales & Marketing Department (Wi-Fi enabled) - Customer Services Area (Wi-Fi enabled) - Floor 2: - Subnet: 192.168.2.0/24 - Administration Department - HR Department - Accounting & Finance Department - Audit Department - Business Development Department - Floor 3: - Subnet: 192.168.3.0/24 - Video conferencing room - IT Department - Server Room (Assigned 10.254.10.0/24 subnet for servers with static IPs) Branch Office in Matara: - Floor 1: - Subnet: 192.168.4.0/24 - Reception area - Customer Services Area (Wi-Fi enabled) - Floor 2: - Subnet: 192.168.5.0/24 - Administration Department - HR Department - Accounting & Finance Department - IT Department Implementation: 1. Configure VLANs: Implement VLANs for each department to ensure network segmentation and security. 2. Install Wi-Fi Access Points: Install Wi-Fi access points in the reception areas and customer services areas in both offices. 3. Inter-Branch Connectivity: Set up inter-branch connectivity between the head office and the branch office to allow intra-branch communication between departments. 4. IP Address Assignment: Assign IP addresses from the specified subnets to each department, ensuring uniqueness and efficient address allocation. 5. Server Configuration: Set up servers in the server room with static IPs from the assigned subnet for server communication and management. 6. Sales and Marketing Wi-Fi Access: Enable Wi-Fi connectivity for the Sales and Marketing Department to access network resources wirelessly. Assumptions: - Utilization of standard Ethernet networking technologies for wired connections. - Use of enterprise-grade Wi-Fi access points for wireless connectivity. - Configuration of VLANs on network switches for departmental segmentation. - Implementation of routing protocols for inter-branch communication. - Deployment of firewall and access control measures to ensure network security. - Provision of DHCP services for dynamic IP address assignment to client devices. By implementing this networked system based on the prepared design, Alliance Health can ensure efficient communication, collaboration, and resource access across their head office in Colombo and branch office in Matara, supporting their business operations effectively. Regular monitoring and maintenance will be necessary to ensure the network remains secure, reliable, and scalable as the company continues to grow. P8 To document and analyze the test results against the expected results for the network architectural design implemented for Alliance Health, we will perform various tests to ensure that the network meets the specified requirements. Here are the tests we will conduct along with the expected results: 1. Network Segmentation Test : - Test the network segmentation by attempting to communicate between devices in different departments. - Expected Result: Devices within the same department should communicate successfully, while communication between devices in different departments should be blocked. 2. Wi-Fi Connectivity Test : - Test Wi-Fi connectivity in the conferencing room and customer services areas of both the head office and the branch office. - Expected Result: Devices should be able to connect to the Wi-Fi network and access resources within the network. 3. Inter-Branch Connectivity Test : - Test connectivity between the head office in Colombo and the branch office in Matara. - Expected Result: Devices in both offices should be able to communicate with each other seamlessly. 4. IP Addressing Test : - Verify that each department has been assigned a unique subnet and IP addresses are assigned correctly. - Expected Result: Each department should have its own subnet, and devices within each department should have unique IP addresses within that subnet. 5. Server Room Test : - Test connectivity to the servers in the server room and ensure that they are accessible. - Expected Result: Devices should be able to communicate with the servers in the server room, and server resources should be accessible. 6. Sales and Marketing Wi-Fi Access Test : - Test Wi-Fi connectivity for the Sales and Marketing Team and ensure they can access network resources. - Expected Result: Devices belonging to the Sales and Marketing Team should be able to connect to the Wi-Fi network and access network resources. 7. Overall Network Performance Test : - Conduct a comprehensive performance test to evaluate network speed, latency, and reliability. - Expected Result: The network should demonstrate adequate speed, low latency, and high reliability to support business operations effectively. After conducting these tests, we will compare the actual results against the expected results to identify any discrepancies or areas requiring further optimization. Any deviations from the expected results will be investigated, and appropriate corrective actions will be taken to ensure that the network meets the company's requirements effectively. Additionally, documentation of the test results and any modifications made will be maintained for future reference and continuous improvement of the network infrastructure. M4 Recommendations for Potential Enhancements: 1. Implement Redundancy and Failover Mechanisms: Introduce redundancy in critical network components such as routers, switches, and servers to minimize downtime in case of hardware failures. Implement failover mechanisms to automatically switch to backup systems in case of primary system failure. 2. Enhance Security Measures: Strengthen network security by implementing advanced firewall configurations, intrusion detection and prevention systems (IDPS), and endpoint security solutions. Conduct regular security audits and vulnerability assessments to identify and address potential security gaps. 3. Deploy Quality of Service (QoS) Policies: Prioritize network traffic based on businesscriticality by deploying QoS policies. This ensures that essential applications such as video conferencing and data transfer receive sufficient bandwidth and are not impacted by lowerpriority traffic. 4. Optimize Wireless Network Coverage: Conduct a site survey to assess Wi-Fi coverage and identify areas with weak signals or dead zones. Install additional access points or reposition existing ones to optimize coverage and ensure seamless connectivity throughout the premises. 5. Implement Network Monitoring and Management Tools: Deploy network monitoring and management tools to continuously monitor network performance, identify bottlenecks, and proactively address issues. Utilize these tools to collect and analyze network data for optimizing resource utilization and enhancing overall network efficiency. 6. Enhance Disaster Recovery and Backup Solutions: Review and enhance existing disaster recovery and backup solutions to ensure quick recovery in case of data loss or network outages. Implement regular backup schedules, offsite backups, and automated recovery processes to minimize data loss and downtime. 7. Upgrade Network Infrastructure: Consider upgrading network infrastructure components such as routers, switches, and access points to newer, more advanced models with higher performance, better security features, and support for emerging technologies such as 5G and Wi-Fi 6. 8. Implement Network Segmentation: Further segment the network to create separate subnets for different user groups or departments, enhancing security and network performance. Implement VLANs and access controls to restrict access between segments and improve network isolation. Critical Reflection on the Implemented Network: The implemented network design effectively meets the company's requirements for departmental segmentation, Wi-Fi connectivity, inter-branch connectivity, and IP addressing. However, there are opportunities for enhancement to further improve the system: - While VLANs were implemented for departmental segmentation, additional segmentation strategies such as micro-segmentation could be explored to enhance security and isolate sensitive data. - The decision to use static IPs for servers in the server room simplifies management but may pose scalability challenges. Implementing dynamic IP assignment or DHCP failover mechanisms could address this limitation. - Although Wi-Fi connectivity was provided for the Sales and Marketing Team, ensuring adequate coverage and performance optimization should be prioritized to support their mobility and productivity effectively. - Enhancements to network security measures, such as implementing multi-factor authentication (MFA) and data encryption, could further mitigate security risks and safeguard sensitive information. - Regular performance monitoring and optimization are essential to ensure that the network infrastructure continues to meet the evolving needs of the organization and maintains optimal performance levels. In conclusion, while the implemented network design aligns with the company's immediate requirements, ongoing evaluation and enhancement are necessary to address emerging challenges, improve efficiency, and ensure the network remains robust, secure, and scalable in the long term. TASK 04 Network Implementation: To implement the network design for Alliance Health, we will proceed with setting up the network infrastructure based on the provided requirements. 1. VLAN and IP Subnetting Scheme: - Head Office in Colombo: - VLAN 10: Reception area (192.168.10.0/24) - VLAN 20: Sales & Marketing Department (192.168.20.0/24) - VLAN 30: Customer Services Area (192.168.30.0/24) - VLAN 40: Administration Department (192.168.40.0/24) - VLAN 50: HR Department (192.168.50.0/24) - VLAN 60: Accounting & Finance Department (192.168.60.0/24) - VLAN 70: Audit Department (192.168.70.0/24) - VLAN 80: Business Development Department (192.168.80.0/24) - VLAN 90: Video Conferencing Room (192.168.90.0/24) - VLAN 100: IT Department (192.168.100.0/24) - VLAN 110: Server Room (10.254.10.0/24 - Static IPs) - Branch Office in Matara: - VLAN 120: Reception area (192.168.120.0/24) - VLAN 130: Customer Services Area (192.168.130.0/24) - VLAN 140: Administration Department (192.168.140.0/24) - VLAN 150: HR Department (192.168.150.0/24) - VLAN 160: Accounting & Finance Department (192.168.160.0/24) - VLAN 170: IT Department (192.168.170.0/24) 2. List of Devices and Network Components: - Layer 3 Switches (for inter-VLAN routing) - Access Points (for Wi-Fi connectivity) - Routers (for inter-branch connectivity) - Firewall/UTM (for security) - Ethernet Cables - Patch Panels - Network Switches - Network Printers - Network Attached Storage (NAS) - Server Rack - Power Distribution Units (PDUs) 3. Configuration and Verification: We will configure the network devices based on the provided VLAN and IP subnetting scheme. Below are the configuration commands for Cisco switches: ``` ! Configuration script for VLANs on Layer 3 Switches vlan 10 name Reception vlan 20 name Sales_Marketing vlan 30 name Customer_Services vlan 40 name Administration vlan 50 name HR vlan 60 name Accounting_Finance vlan 70 name Audit vlan 80 name Business_Development vlan 90 name Video_Conferencing vlan 100 name IT vlan 110 name Server_Room vlan 120 name Reception_Matara vlan 130 name Customer_Services_Matara vlan 140 name Administration_Matara vlan 150 name HR_Matara vlan 160 name Accounting_Finance_Matara vlan 170 name IT_Matara ! Configuration script for Inter-VLAN Routing interface vlan 10 ip address 192.168.10.1 255.255.255.0 interface vlan 20 ip address 192.168.20.1 255.255.255.0 ! Repeat for all VLANs ip routing ``` We will conduct verification tests such as ping, extended ping, trace route, telnet, and SSH to test connectivity between devices and ensure proper functioning of the network. 4. Potential Future Enhancements: - Implementation of Network Access Control (NAC) for enhanced security. - Integration of Quality of Service (QoS) policies for prioritizing critical traffic. - Deployment of Network Monitoring and Management tools for proactive network management. - Implementation of Software-Defined Networking (SDN) for centralized network control and automation. 5. Critical Reflection: The implemented network design effectively meets the requirements of Alliance Health, providing secure and efficient connectivity between departments and branches. The VLAN and IP subnetting scheme ensures proper segmentation and organization of network resources. Configurations were successfully applied to network devices, and verification tests confirmed expected results. However, there are areas for improvement, such as implementing advanced security measures like NAC and enhancing network monitoring capabilities. Additionally, future enhancements such as QoS implementation and SDN integration can further optimize network performance and management. Overall, the implemented network lays a solid foundation for Alliance Health's operations, but continuous monitoring and periodic updates will be essential to adapt to evolving business needs and technological advancements. Reference Internet, notes books, https -//www.ibm.com/topics/networking https://www.javatpoint.com/computer-network-introduction https://www.geeksforgeeks.org/what-is-computer-networking/ https://www.firewall.cx/networking/network-fundamentals/introduction-networking.html https://www.techtarget.com/searchnetworking/definition/protocol https://www.cloudflare.com/learning/network-layer/what-is-a-protocol/ https://www.manageengine.com/network-monitoring/network-protocols.html https://www.spiceworks.com/tech/networking/articles/what-is-a-computer-network/ https://www.ieee.org/about/index.html https://www.tutorialspoint.com/communication_technologies/communication_technologies_n etwork_devices.htm https://www.lepide.com/blog/the-most-common-types-of-network-devices/