Cyber Protection Team 175
Candidate Questionnaire
2/24/2024
FOUO
1
Candidate Information
Name: Rainwater, Brian
Rank: SPC / E – 4
Current MOS: 88N
Email Address: Brianrainwater@gmail.com
Phone #: 256 – 226 - 3570
Current Unit POC and Phone #:
School Attended (i.e. university, military academy, etc. put N/A if not applicable): The
University of Alabama
Degree Awarded: Bachelor of Science (BS) in Commerce and Business Administration
Graduation Date: DEC 2024
Certifications (i.e. Security +, CEH, CISSP, CCNA, ect.): ITIL 4, CompTia A+, Google
Cybersecurity
Resume (attach with CPT questionnaire):
2/24/2024
FOUO
2
Clearance Information
Do you currently hold a clearance? Yes or No? Yes
If so what is your current level of access?
TOP SECRET / SCI
Interim TOP SECRET
SECRET
X
Interim SECRET
Public Trust
None
2/24/2024
FOUO
3
Questionnaire
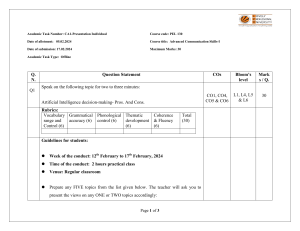
What qualifies you to be a Cyber Professional? Include any special skills you have?
I am a diligent, analytical, and determined to be a cybersecurity professional, wholly
committed to the safeguarding of digital assets and the protection of organizations, private
citizens, and the USFG sensitive information from malicious cyber threats. With a strong
grounding in cybersecurity foundational principles and an unwavering dedication to
ongoing learning, I am poised to contribute my skills and knowledge to fortifying,
upholding, and securing digital environments effectively.
2/24/2024
4
Questionnaire
List three of your goals as a Cyber Professional:
Long term
Have a high ranking job in the federal government
Mid term
Have a job at Redstone Arsenal or the new FBI building there
Short term
Graduate UA with a double major in Cybersecurity and Entrepreneurship and pass 17C
school
2/24/2024
5
Questionnaire
List any internships or industry experience:
I am creating my own SaaS business. I am taking certifications online to bolster my
programming skills.
I spent some time at Naval Computer and Telecommunications Station, Far East. I learned
firsthand of proper responses to ensure safety of data.
I have experience with WindowsOS, macOS, Kali Linux, SQL, HTML, JS, RSA,
Kleopatra, VPN, GUI, CLI, Bash, Metasploit, Magnet Axiom, Python, C#, Ruby, SQL
2/24/2024
6
Questionnaire
What is the hardest technical problem that you have solved?
I have faced many tasks. I have put together my computer and troubleshot it as problems
arose. I was also an electrician on MH-60S. I helped solve a large number of electrical
issues during my stint in the navy.
2/24/2024
7
Questionnaire
Please rate your level of proficiency in the following areas on a scale of 1-5.
1 being least familiar and 5 being very comfortable. Do not mark any if you have no experience.
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
Linux OS/UNIX, to include derivatives
such as BSD, Mac OSX, Ubuntu
Windows OS
Forensics (disk, memory, netork)
Software Analysis & Malware reversal
Assembly
FORTRAN
C++
Java
Python
Penetration Testing
Binary Analysis
BASIC
C
SQL
JavaScript
Perl
Other ________C#______
Other ______________
2/24/2024
USER ____3______
USER _____4_____
USER _____2_____
USER _____2_____
USER __________
USER __________
USER __________
USER __________
USER ______3____
USER ____2______
USER __________
USER __________
USER __________
USER ____2______
USER __________
USER __________
USER _____2_____
USER __________
ADMIN ___2______
ADMIN ____4_____
ADMIN ____2_____
ADMIN _____2____
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
ADMIN _________
8
Scenario 1
Your in a lab environment with multiple computer assets and tools. You are working on a
person’s computer that is suspected to be infected with a virus. The operating system is
Windows 7. What steps would you take in analyzing this computer?
2/24/2024
9
Scenario 1 Cont’d
Provide answer below:
• Isolate the computer
• Enter into safe mode
• Back up important data
• Use a reliable antivirus
• System Restore
• Malware scans
• Update and patch
• Clean install
• change all passwords and monitor accounts and systems for any signs of unauthorized
access or lingering issues.
2/24/2024
10
Scenario 2
A piece of malware is running on a Windows 7 machine via process injection, so it does not
show up in a process list. What remote forensic technique could be used to discover the
malware that is running under the contents of a specific process?
2/24/2024
11
Scenario 2 Cont’d
Provide answer below:
I would then use antivirus to scan and see if it could find any any abnormalities first. I
would try Process Monitor from Sysinternals and then cross reference with process explorer
and wireshark to see if there is any unusual activity going out of my computer. If still not
rectified, I would use live activities such as KAPE to see if I could root out the issue that
way.
2/24/2024
12
Scenario 3
Describe a corporate network infrastructure design with which you’re familiar and define
the critical areas that need to be secured. What vulnerabilities exist and what are methods
for mitigation? Prioritize what needs to be secured and what the potential impacts would be
if not secured properly.
2/24/2024
13
Scenario 3 Cont’d
Provide answer below:
Physical access and digital access. Locked doors behind pin codes and key cards and
security systems manned by watch personnel to ensure the unauthorized personnel cannot
gain access to areas to which they are not allowed. Security cameras to ensure that only
authorized personnel would be allowed entry.
For digital access, I would say ID cards like the military CAC. Authorizing by email and
digital pin to access accounts and regular trainings to ensure user error is at a minimum.
2/24/2024
14
Scenario 4
Given the following program, explain the specifics of what is being done.
int fact(int n)
{
if (n < = 1) // base case
return 1;
else
return n*fact(n-1);
}
2/24/2024
15
Scenario 4 Cont’d
Provide answer below:
It is a function calling integer “n”. The process of the function is a factorial of what ever
number “n” is set to. When the function reaches 1 in the if statement, it will print out the
final number of the factorial. Else if a number is less than 1, it would just print 1.
2/24/2024
16
Recommendation for Approval
• CPT 175 Mission Element Lead (CW2/1LT or above):
• Date of interview:
• Recommend for approval (include justification):
2/24/2024
FOUO
17