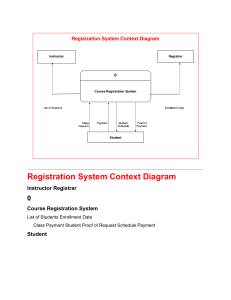
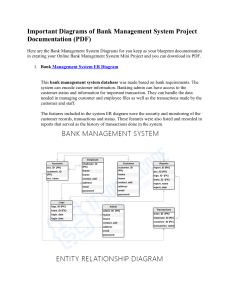
Development of House Renting System ...............................................A Practicum Report Submitted by MD. Tahmidur Rahman Tushar ID-20103257 In the Partial Fulfillment of the Requirements for the Award of Bachelor of Computer Science and Engineering (BCSE) Department of Computer Science and Engineering College of Engineering and Technology IUBAT – International University of Business Agriculture and Technology Fall 2023 Development of House Renting System MD. Tahmidur Rahman Tushar A Practicum report submitted in the Partial Fulfillment of the Requirements for the Award of Bachelor of Computer Science and Engineering (BCSE) The report has been examined and approved, ___________________________ Prof Dr. Utpal Kanti Das Chairman Dept. of Computer Science and Engineering IUBAT – International University of Business Agriculture and Technology ___________________________ Rashedul Islam Assistant Professor & Coordinator Dept. of Computer Science and Engineering IUBAT – International University of Business Agriculture and Technology ___________________________ Md. Nazir Ahmed Lecturer Dept. of Computer Science and Engineering IUBAT – International University of Business Agriculture and Technology Fall - 2023 iii LETTER OF TRANSMITTAL 15th December, 2023 The Chairman Practicum and Placement Board College of Engineering and Technology - CEAT IUBAT- International University of Business Agriculture and Technology 4 Embankment Drive Road, Sector- 10, Uttara Model Town Dhaka-1230, Bangladesh Subject: Letter of Transmittal. Sir, With due respect, I would like to inform you that it is a great pleasure and a great pleasure for me to submit this report entitled “Development of House Renting System” to complete my Practicum course. It was a great opportunity for me to work on this project to make my theoretical knowledge more realistic and I gained a lot of exposure to the business culture of a famous company. I now look forward to your kind commentary on this performance report. I will always be very grateful to you if you kindly go through this report and check my performance. Thanking you, ____________ MD. Tahmidur Rahman Tushar ID-20103257 iv STUDENT’S DECLARATION I am MD. Tahmidur Rahman Tushar, a student of the BCSE-Bachelor of Computer Science and Engineering program, under the College of Engineering and Technology (CEAT) of the International University of Business Agriculture and Technology (IUBAT) announcing, this report entitled ‘Development of House Renting System' has been prepared for the completion of the CSC 490 job training course, which is part of the Bachelor of Computer Science and engineering degree. The report and the project "Development of House Renting System" was edited by me. All modules and procedures for this project are done after proper testing and online information. It is not designed for other purposes, awards or presentations. _____________ MD. Tahmidur Rahman Tushar ID-20103257 v SUPERVISOR’S CERTIFICATION This is to ensure that the Practicum report on the “Development of House Renting System” is compiled by MD. Tahmidur Rahman Tushar, with ID-20103257, of IUBAT– International University of Business Agriculture and Technology, as part of the fulfillment of the required part of an effective defense course. The report has been prepared under my supervision and is a record of the work accomplished, successfully completed. To the best of my knowledge and as per his declaration, no portions of this report have been posted anywhere by any degree, diploma or certificate. You are now allowed to submit a report. I wish his every success in his future endeavors. Practicum Supervisor _______________________________ Md. Nazir Ahmed Lecturer Department of Computer Science and Engineering IUBAT–International University of Business Agriculture and Technology vi DEPARTMENT’S CERTIFICATION On behalf of the Department of Computer Science and Engineering, IUBAT-International University of Business Agriculture and Technology, I undersigned, confirm the performance report ‘Development of House Renting System for Bachelor of Computer Science and Engineering (BCSE) degrees was duly presented by MD. Tahmidur Rahman Tushar (ID20103257) and approved by the department. ___________________________ Md. Nazir Ahmed Supervisor, Lecturer Department of Computer Science and Engineering IUBAT- International University of Business Agriculture and Technology ___________________________ Rashedul Islam Assistant Professor & Coordinator Department of Computer Science and Engineering IUBAT- International University of Business Agriculture and Technology ___________________________ Prof. Dr. Utpal Kanti Das Chairman Department of Computer Science and Engineering IUBAT- International University of Business Agriculture and Technology vii ABSTRACT House renting system, developed using PHP, introduces a user-friendly interface allowing users to search for rental homes based on locations such as districts and local areas. Acknowledging the transformative impact of technology, the housing sector seeks innovative strategies for seamless rental house management. While distance vector routing protocols have proven efficient in current internet and wireless networks, their vulnerability to network routing-based attacks necessitates a new approach. We propose a rental house renting system that simplifies tasks for managers, enhancing efficiency and effectiveness. User input values are sent to the server for processing, where comprehensive management of rental house information takes place, addressing the challenges posed by the dynamic landscape of rental property management. The House Renting system is an online platform that will help to find the perfect house which process is easy, convenient, and affordable. viii ACKNOWLEDGMENTS I would like appreciate and acknowledge all the people who has encouraged and supported me through the entire journey and has played a great role the completion of my Practicum and the report on “Development of House Renting System”. First of all I would like to thank Almighty for uncountable and beyond to words reasons and for giving me the power to stay motivated all the time for completing any task. I would like to thank our Vice Chancellor, Chairman, Coordinator, Academic supervisor, Md. Nazir Ahmed, Lecturer of the Department of Computer Science and Engineering of IUBATInternational University of Business Agriculture and Technology, who has encouraged me throughout the entire time and has provided me with all the necessary guidelines and support that I needed. He was always there whenever I needed any help. He is a very humble and kind person and is always happy to be a helpful and supportive. I would also like to convey my special regards to my family. It was for them who encouraged and stayed beside me throughout my entire life. I wouldn’t have come this far if they were not there for me. I convey my thanks to my friends and ask for apologies from anyone and everyone whose name has not been mentioned. ix INTERNSHIP CERTIFICATE x TABLE OF CONTENTS Letter of Transmittal ....................................................................................................... iv Student’s Declaration ...................................................................................................... iv Supervisor’s Certification ............................................................................................... vi Department’s Certification ............................................................................................ vii Abstract .......................................................................................................................... viiii Acknowledgments ............................................................................................................ ix Internship Certificate ........................................................................................................x List of Figures .....................................................................................................................1 List of Tables ......................................................................................................................2 Chapter 1. Introduction ....................................................................................................4 1.1 Introduction ............................................................................................5 1.2 Project Overview ...................................................................................5 1.3 Background Study ..................................................................................6 1.4 Objectives ..............................................................................................6 1.4.1 Specific Objective ...................................................................6 1.5 Scope of the project ...............................................................................7 1.6 Methodology ..........................................................................................7 1.7 Limitation of the Project ........................................................................7 1.8 Process Model ........................................................................................8 1.8.1 Why Incremental Process Model ............................................8 1.9 Feasibility study .....................................................................................9 1.9.1 Technical Feasibility ...............................................................9 1.9.2 Economic Feasibility ............................................................10 1.9.3 Operational Feasibility ..........................................................10 Chapter 2. Organizational Overview ................................................................................11 2.1 Organization Introduction ....................................................................12 2.2 Organization Services ..........................................................................12 2.2.1 Web Development ................................................................12 2.2.2 Mobile Application ...............................................................12 2.2.3Digital Marketing ...................................................................13 xi 2.3 Organization Vision .............................................................................13 2.4 Organization Mission ...........................................................................13 2.5 Organization Location .........................................................................13 Chapter 3. Requirement Engineering ............................................................................14 3.1 Requiement Analysis ...........................................................................15 3.2 Requirement Engineering ....................................................................15 3.2.1 User and system Requirements .............................................15 3.2.2 Functional Requirements ......................................................16 3.2.3 Non Functional Requirements. .............................................17 3.3 Use Case Diagram................................................................................17 Chapter 4. System Planning ............................................................................................18 4.1 Function Description ............................................................................19 4.2 System Project Planning ......................................................................20 4.2.1 System Project Estimation. ...................................................21 4.2.2 Function Oriented Matrix. ....................................................21 4.2.3 Function Poin Estimation......................................................22 4.2.4 Task Scheduling. ...................................................................27 4.2.5 Project Schedule Chart. .........................................................28 4.2.6 Cost Estimation. ....................................................................28 Chapter 5. Risk Management .........................................................................................32 5.1 Risk Analysis .......................................................................................33 5.2 The RMMM Plan .................................................................................34 5.3 Project Risks ........................................................................................35 5.4 Technical Risk .....................................................................................36 5.5 Tool Risk..............................................................................................37 5.6 Requirement Risk.................................................................................38 Chapter 6. Analysis Modeling.........................................................................................39 6.1 Analysis Modeling ...............................................................................40 6.1.1 Objectives of Analysis Model. ..............................................40 6.2 Activity Diagram .................................................................................40 6.2.1 Activity Diagram For Admin. ..............................................41 xii 6.2.2 Activity Diagram For House Owner. . ..................................42 6.2.3 Activity Diagram For Tenant ................................................43 6.4 Entity Relationship Diagram (ERD) ....................................................43 6.5 Data Flow Diagram (DFD) ..................................................................44 6.5.1 Constext Level DFD. ............................................................45 6.5.2 Level 1 DFD. ........................................................................46 6.5.3 Level 2 DFD of Process 1. ....................................................47 6.5.4 Level 2 DFD of Process 2. ....................................................47 6.5.5 Level 2 DFD of Process 3. ....................................................48 6.5.6 Level 2 DFD of Process 4. ....................................................48 6.5.7 Level 2 DFD of Process 5. ....................................................49 6.5.8 Level 2 DFD of Process 6. ....................................................49 6.5.9 Level 2 DFD of Process 7. ....................................................50 Chapter 7. Designing .......................................................................................................51 7.1 Database Field Design .........................................................................52 7.2 Interface Design ...................................................................................54 Chapter 8. Qaulity Assurance .........................................................................................57 8.1 System Testing .....................................................................................58 8.1.1 System Testing Strategy. ......................................................59 8.2 System Testing Methodology ..............................................................59 8.3 Testing Design .....................................................................................60 Chapter 9. Conclusion .....................................................................................................63 9.1 Preface..................................................................................................64 9.1.1 Practicum ang its value. ........................................................64 9.2 Conclusion ...........................................................................................65 9.3 Limitations ...........................................................................................65 9.4 Future Plan ...........................................................................................66 References .........................................................................................................................67 xiii LIST OF FIGURES Figure 1.1 Incremental Process Model ..................................................................................... 9 Figure 3.1 Use Case Diagram. ................................................................................................ 17 Figure 6.2.1 Activity diagram for Admin. .............................................................................. 41 Figure 6.2.2 Activity diagram for House Owner.. .................................................................. 42 Figure 6.2.3 Activity diagram for Tenant.. ............................................................................. 43 Figure 6.3 ERD of House Renting System. ............................................................................ 44 Figure 6.4 Context Level DFD. .............................................................................................. 45 Figure 6.5 Level 1 DFD. ......................................................................................................... 46 Figure 6.6 Level 2 DFD processs 1. ....................................................................................... 47 Figure 6.7 Level 2 DFD processs 2. ....................................................................................... 47 Figure 6.8 Level 2 DFD processs 3. ....................................................................................... 48 Figure 6.9 Level 2 DFD processs 4. ....................................................................................... 48 Figure 6.10 Level 2 DFD processs 5. .................................................................................... 49 Figure 6.11 Level 2 DFD processs 6. ..................................................................................... 49 Figure 6.12 Level 2 DFD processs 7. ..................................................................................... 50 Figure 7.1 List of Tables in Database. ................................................................................... 52 Figure 7.2 User Table Structure. ............................................................................................ 52 Figure 7.3 House Table Structure. ......................................................................................... 52 Figure 7.4 Booking List Table Structure. .............................................................................. 53 Figure 7.5 Saved Property Table Structure. ........................................................................... 53 Figure 7.6 Review Table Structure. ....................................................................................... 53 Figure 7.7 User Registration Interface. .................................................................................. 54 Figure 7.8 User Login Interface. ............................................................................................ 54 Figure 7.9 Homepage Interface.............................................................................................. 54 Figure 7.10 User Profile Interface. ......................................................................................... 55 Figure 7.11 Admin panel User List Interface. ....................................................................... 55 1 LIST OF TABLES Table 4.1 Function Description DET and RET ...................................................................... 19 Table 4.2 Identifying Complexity (Transaction Function) ..................................................... 22 Table 4.3 Identifying Complexity (Data Function) ................................................................ 24 Table 4.4 Unadjusted Function Point Contribution (Transaction Function) .......................... 25 Table 4.5 Unadjusted Function Point Contribution (Data Function) ...................................... 25 Table 4.6 Total Degree of Influence ....................................................................................... 26 Table 4.7 Project Scheduling Chart ........................................................................................ 28 Table 4.8 Personal Cost .......................................................................................................... 29 Table 4.9 Hardware Cost ........................................................................................................ 30 Table 4.10 Software Cost ........................................................................................................ 31 Table 4.11 Other Cost ............................................................................................................. 31 Table 4.12 Total System Development Cost .......................................................................... 31 Table 5.1 Project Risk(PR1) ................................................................................................... 35 Table 5.2 Technical Risk ........................................................................................................ 36 Table 5.3 Technical Risk ........................................................................................................ 36 Table 5.4 Technical Risk ........................................................................................................ 37 Table 5.5 Tool Risk................................................................................................................. 37 Table 5.6 Requirement Risk ................................................................................................... 38 Table 5.7 Requirement Risk ................................................................................................... 38 Table 8.1 Testing Scenraio 1 .................................................................................................. 60 Table 8.2 Testing Scenraio 2 .................................................................................................. 61 Table 8.3 Testing Scenraio 3 .................................................................................................. 61 Table 8.4 Testing Scenraio 4 .................................................................................................. 62 Table 8.5 Testing Scenraio 5 .................................................................................................. 62 2 Chapter 1 Introduction 3 1.1 Introduction An internship is a way to put theoretical knowledge into practice and can be seen as a first step toward familiarizing oneself with a company and gaining the self-assurance necessary to launch a career. IUBAT—International University of Business Agricultural and Technology provides this opportunity by enabling us to complete an internship while we are enrolled students to develop competence through the most appropriate options. After graduation, the employment market is extremely competitive for everyone. The student is given the chance to use the knowledge and abilities they have learned in the classroom and in the real world during their undergraduate education. This report contains all the information and descriptions of the project created during my 12 weeks Web Development internship at Kodeeo Limited Bangladesh. The project titled “House Renting System” is assigned to me by my university supervisor for the fulfillment of the requirement of the Practicum course. The entire project was developed during the 12 weeks internship period at Kodeeo Limited. The project is solely developed for the sake of completion of the Practicum and it is not being used anywhere else. This report is generated to describe all the processes and works that have been done during the development of this project. This report contains all the details of the development phase of the project with proper illustration. 1.2 Project Overview Everyone is familiar with the concept of house renting websites in this modern day. Finding a house physically how much hassle we have to face everyone knows about that. It's messy and time-consuming to find a house by wandering the streets. This website helps you to find a perfect house. Finding your dream rental is as easy as a click with our state-of-the-art house renting system. With our site, renting becomes easy for both landlords and tenants. We've simplified the process, making it efficient and straightforward. For landlords, managing 4 property listings and connecting with potential tenants is a breeze. Tenants can easily find their ideal home, access detailed property information, and navigate a transparent leasing process. Our platform is designed to bring convenience to both parties, ensuring a smooth and hasslefree rental experience. Say goodbye to the complexities – our site is here to empower house owners and tenants alike, making the entire rental journey simple and accessible for everyone involved. 1.3 Background Study To create our user-friendly house renting system, we dug into the challenges faced by landlords and tenants in traditional renting time-consuming searches, opaque processes, and complex negotiations. These frustrations have driven us to a flowline the rental experience. Our system simplifies property management for house owners and enhances search for tenants, meeting the need for efficiency, transparency and convenience. Considering the trend of reliance on online services, we have adopted technology to make renting accessible and easy. In essence, our system is built on a solid background study, ensuring it caters to the real needs in today's ever-evolving rental landscape. The emphasis on security and transparency within our platform is a direct response to common concerns in the rental market, fostering trust between house owners and tenants. Features such as advanced search options and detailed property information are thoughtfully crafted based on a thorough analysis of user preferences and expectations. Ultimately, this website serves as the solid foundation for the development of the house renting system, ensuring that it not only acknowledges but effectively addresses the real needs of both house owners and tenants in the ever-evolving landscape of property rentals. It's our commitment to making the rental journey smoother, more transparent, and ultimately more satisfying for everyone involved. 1.4 Objectives Board Objective: The board objective of this project is to develop a software to maintain the track records of tenant, owner, monthly rent, maintenances and other related issues. Also is to use our educational experience in the real life working environment. 5 1.4.1 Specific Objective The specific objective of this project are listed below: ➢ Store and manage tenants and owners details. ➢ Build a web based Online House Renting System to fulfill requirements such as tenant management, owner management and user management. ➢ Well-designed database to store information. 1.5 Scope of the project Simplifying property listings and tenant interactions for house owners, making the rental management process more efficient. Enhancing the tenant experience with an easy-to-use platform, streamlined searches, and transparent leasing processes. Aligning with the growing trend of online service reliance, leveraging technology for accessibility in the competitive housing market. Emphasizing security and transparency features to establish trust between house owners and tenants, addressing common concerns in the rental market. Catering to the increasing demand for efficiency, transparency, and convenience in the rental market. Building a project adaptable to the evolving landscape of property rentals, ensuring responsiveness to emerging market needs and user expectations. 1.6 Methodology The development of House Renting System has been done with an incremental model. The system has been developed according to the structure described in Software Analysis and Design below. This study on ‘Development of House Renting System’ preliminary in nature. 1.7 Limitation of the Project This project has some limitations those we have planned to develop in future. The limitations are: ❖ Renters (tenants) cannot pay monthly rent separately. ❖ Embedded account management and some other module is needed to be implemented. ❖ Here renters (tenants) will not get any mobile SMS notifications. 6 1.8 Process Model I chose incremental process model for the development of the system. The incremental model is a developed version of the waterfall model. This product is designed, implemented, integrated and tested as a series of incremental builds. The reasons for which I have selected the Incremental Process model are as follows, • The incremental model prioritizes requirements of the system and then implements them in groups. • Develop high-risk or major functions first • Each release delivers an operational product • Customer can respond to each build • Lowers initial delivery cost • Initial product delivery is faster • Customers get important functionality early 1.8.1 Why Incremental Process Model • This model can be used when the requirements of the complete system are clearly defined and understood. • Major requirements must be defined; however, some details can evolve with time. • There is a need to get a product to the market early. • A new technology is being used • There are some high risk features and goals. • Construct a partial implementation of a total system. • Then slowly add increased functionality. • The incremental model prioritizes requirements of the system and then implements them in group. 7 • Each subsequent release of the system adds functions to the previous release, until all designed functionality has been implemented. Figure 1.1 Incremental Process Model 1.9 Feasibility study A feasibility study is an analysis of how successfully a project can be completed; accounting for factors that affect it such as economic, technological, legal and scheduling factors. Feasibility study determines whether that solution is feasible or achievable for the organization. There are three major areas of feasibility study: • Technical feasibility • Economic feasibility • Operational feasibility 1.9.1 Technical Feasibility A technical feasibility study is a complete study of a project regarding inputs, processes, outputs, areas, programs and procedures. This is a very effective tool for long term planning and troubleshooting. Basically, the technical feasibility study should support the financial information of the organization. A technical feasibility assessment focuses on understanding the current technical resources of the organization and the applicability of the proposed system to the anticipated requirements. This is an evaluation of the hardware and software and how they meet the needs of the proposed system. 8 Hardware Requirements • Computer (Desktop/Laptop/Equivalent) • Proper electricity Support • Adequate system memory and secondary memory Software Requirements • Operating System (Windows 8.1 or equivalent) with any web browser • PHP • XAMPP Server (MySQL) 1.9.2 Economic Feasibility The purpose of an economic feasibility assessment is to determine the positive economic benefits that a proposed system will have for an organization. Our system is economically viable because using the proposed system, many jobs can be done in a short time that cannot be done simultaneously by humans. The system also reduces the personnel required to maintain products, order details, customer information and payment details. So, if the current system requires many employees, they have to pay less, and they pay more. It can be said that it is economically profitable. 1.9.3 Operational Feasibility Operational feasibility addresses concerns about user acceptance, management support, and the requirements of entities and factors in the organizations external environment. It’s easy to insert inventory products and easy to create stocks. If the stuff of the organization has the basic to computer knowledge they could operate the software easily. Every features and the activity that are combined within the system is designed and developed belongs to previous format they had used with a more attractive user interface. The proposed system is designed from a client‘s point of view. So, all of the features are included only to benefit the portal‘s users. And this system supports them all. 9 Chapter 2 Organizational Overview 10 2.1 Organization Introduction Kodeeo Company Limited is a Bangladeshi company providing complete web solutions, software development, mobile applications, graphics and multimedia services, domain hosting and digital marketing. Its core consists of highly skilled designers and developers with over 5 years of experience in a variety of complex designs and developments. With services including website design and development, mobile application design and development, software development, SEO and social media design and development, Kodeeo Ltd. satisfy your customers. In all areas of our operations, we work hard to understand customer requirements and provide solutions Kodeeo Ltd. We strongly believe in the philosophy “Our vision is to help every young person become competent and employable”. We pride ourselves on our team of highly qualified, knowledgeable and motivated professionals who are encouraged for leadership, innovation and excellence. Our team is comprised of leading experts who share a common vision and passion, providing clients with the information and guidance needed to succeed in today's competitive environment. We believe in providing expert and excellent services through our experience and providing the best possible service utilization to our customers. (Kodeeo Company Limited). 2.2 Organization Services Kodeeo Company Limited is a leading provider of IT services, including all types of creative and professional software, enterprise software integration, management information systems, e-commerce, game development Play and develop Web and mobile application solutions. 2.2.1 Web Development At Kodeeo Ltd, we focus on creating interactive, search engine friendly website designs. It is a known fact that to build a strong web presence and ensure the countless marketing opportunities available on the Internet, it is mandatory to have a good website, thereby triggering a race in web design . While designing and developing your website, our experts keep in mind key factors such as ease of navigation, overall consistency and quality of content, stipulated deadlines and budgets as well as auxiliary support. 2.2.2 Mobile Application We have a strong mobile application developer team of professional engineers who are experienced in creating versatile mobile applications for various industries. All our expert engineers work on Android and iOS platforms for more than 5 years. We work on stock Android, delivering faster app response and quality assurance. We can design, build, prototype and execute your ideas through planning, construction, testing and deployment. 1 2.2.3 Digital Marketing Kodeeo Ltd offers different types of packages to help your business perform at its best in the internet world. Digital marketing involves promoting products or brands that are essential to the success of a business. It increases your web visibility among your potential customers. The more exposure you get, the closer you get to your business goals. This is the most important strategy to grow your business. Kodeeo Ltd is a full-service digital agency with clients ranging from well-known businesses to innovative startups. (Kodeeo Company Limited). 2.3 Organization Vision Kodeeo Ltd's vision. is to empower youth and build successful IT businesses in digital Bangladesh. Their mission is to become one of the leading IT companies in Bangladesh. Through the innovative use of technology, Kodeeo Ltd. gain competitive advantage and increase operational effectiveness and efficiency. 2.4 Organization Mission Kodeeo Ltd. was established as a one-stop shop for a skills development platform. Client needs are satisfied in respect to their attributes thanks to their services and the excellent staff behind them. My position in this organization I am a development intern in this organization. I am guided by a supervisor in this organization. It was very helpful and informative. I really learned a lot from him. I completed my project on time. This was only possible thanks to the advice of my supervisor. It was also a great experience for me to maintain working time at the office. I also followed other organizing instructions. I am happy to be a part of this office. It definitely helped prepare me for the start of my career. 2.5 Organization Location House 15 Road-10 A, Sector 11, Dhaka 1230 Phone: 01854969657 Email: info@kodeeo.com Web: www.kodeeo.com 12 Chapter 3 Requirement Engineering 13 3.1 Requirement Analysis The software designer can use requirement analysis to translate data, architectural, interface, and component level designs into information, function, and behavior. During the task phases, which are listed below in this chapter, the requirement analysis was finished. 3.2 Requirement Engineering Requirements engineering, as its name suggests, is a subfield of engineering that is concerned with developing software systems and recognizing user requirements. There are several definitions of requirements engineering, but they all agree that it involves understanding what users anticipate from a computer system and what their requirements mean for the design. Requirements engineering is closely related to software engineering, which is primarily focused on the method of building the system that customers want. The following are the results of the requirement engineering for this project: • User requirements • System requirements • Functional requirements • Non-Functional requirements 3.2.1 User and System Requirements The House Renting System has 3 types of users, 1. Admin 2. Tenant 3. House Owner The user and system requirements of the project House Renting System are as follows, 1. Every role needs to registration. 1.1 System needs related information like phone number or email, password for registration. 14 2. User (property owner or manager) should be able to easily list their available properties for rent, including details such as property type, location, rent amount. 2.1 System should have user friendly interface. 2.2 System should have property details form. 2.3 Allow users to upload high quality photos images of the property. 3. Tenants should be able to submit rental applications online, providing their personal information, rental history, and references. 3.1 Develop a user-friendly tenants can easily book houses. 3.2 Allow tenants to enter their employment details, including employer names, income, and references if applicable. 3.3 Ensure that tenant data is collected and stored securely. 3.4 Provide tenants with a confirmation message or notify after successfully submitting their rental application. 4. User, as tenant, can see the details of houses, other owners, tenants and book houses. 4.1 System needs information of houses, owner id, owner name, email, occupation for the see the details of houses and owners. 4.2 System needs owner id, house id, booking date, period, price, and agreement to book the houses. 5. Tenants should be able to make p..ayments online through various payment methods. 5.1 Provide tenants with the option to make payments using various payment methods, including credit/debit cards, bank transfers, and mobile payment services (Bkash, Rocket, DBBL, Nagad). 3.2.2 Functional Requirements 1. Here any user can sign up as owner or tenant and can give their details. 2. After registration user can sign in as owner or tenant on their own platform. 3. User can see the information of houses as view house and can see the list of rating. 4. Owner can add the detail of houses and can see the tenants list. 5. Tenant can see the information of houses and can book the houses. 6. Tenant can see the information of owners and other tenant’s information. 7. Owners and tenants can log out from their own platform. 15 3.2.3 Non-Functional Requirements • Security Requirements: Transaction Record, General Users and Admin must be Authorized • Reliability Requirements: The System should be consistent and should give the desired results. • Efficiency Requirements: The Software should be efficient enough to take less memory of the computer System; there should not be any performance degradation. • Usability Requirements: The System should be easily usable by the Actors. 3.3 Use Case Diagram Figure 3.1 Use Case Diagram 16 Chapter 4. System Planning 17 4.1 Function Description Function description descriptive the function in details. It concerns on three factors: what is the possible input, possible output for a particular function and which table of the database uses by that function. Table 4.1 Function Description : DET and RET Functionality Input Output User can register as tenant or Click sign in Name, Email, Password, Mobile No, owner by clicking on the sign Role up. Owner can sign in fore Click sign in Email, Password, sign in as owner. entering in their own platform. Owner can see the details of Click see details below House ID, Owner ID, No. of houses. the houses & then they bedrooms, no of bathroom, Address, can add houses. City, State, Description, flat and floor number, Photos of the houses. Owner can see the details of all Click see details below Owner ID, Name, Email, Mobile No, Owners. the owners. Occupation, No. of houses owned, Address, City, State, Country. Owner can see the details of all Click see details below Tenant ID, First Name, Last Name, bookings. the booking and they Email, Mobile No, Occupation. can book houses also. Tenant can sign in for entering Click sign in Email, Password, sign in as tenant. in their own platform. Tenant can see the details of Click see details below House ID, Owner ID, No. of houses. the houses. bedrooms, No. of bathroom, Address, City, State, Flat and floor 18 number, Description, Rate for rent, Photos of the houses. Tenant can see the details of Click see details below Owner ID, Name, Email, Mobile No, Owners. the owners. Occupation, No. of houses owned, Address, City, State. Tenant can see the details of Click see details below Tenant ID, First Name, Last Name, alternates. the tenants then they Email, Mobile No, Occupation. can add members and rating to houses. Tenant can see the details of Click see the details Tenant ID, House ID, Booking Date, all booking. below the Booking, Period, Price, House type. Then they can book house. 4.2 System Project Planning Before starting any project, it is compulsory to estimate the work to be done, the resources that will be required, the time that will elapse from start to finish and to analyze the project to determine whether it is feasible or not. The following activities of software project planning that have followed in this project are: ➢ System Project Estimation ➢ Function Oriented Metrics ➢ Process Based Estimation ➢ Effort Distribution 19 ➢ Task Scheduling ➢ Project Schedule Chart ➢ Cost Estimation 4.2.1 System Project Estimation The accuracy of a software project estimate predicated based on a number of things: • Properly estimated the size of the product to build. • The ability to translate the size estimation into human effort, calendar time and money. • The degree to which the project plan reflects the abilities of the software team or engineer. • The stability of the product requirements and the environment that supports the software engineering effort. Software size estimation is the most important matter that I had to consider during the software project. If the software size not calculated properly, then various problems such as scheduling problems, budget problem etc may arise. As the project goes on before estimating the software size, I had to confirm that software scope is bounded. 4.2.2 Function Oriented Metrics Function point-based estimation focuses on information domain values rather that software values. Function points are computed by comparing five information domain characteristics. The information domain values are as follows Data Functions • Internal Logical File • External Interface File Transaction Functions • External Inputs • External Outputs • External Inquires 20 Number of external outputs – Each user output that provides application-oriented information to the user is counted. Number of external inquires – An inquiry defined as an on-line input those results in the generation of some immediate software response in the form of an on-line output. Each distinct inquiry counted. Number of Internal Logical files – Each logical internal file is a logical grouping of data that resides within the application‘s boundary and is maintained via external inputs. Numbers of external interfaces – All machine-readable interfaces that used to transmit information to another system counted. 4.2.3 Function Point Estimation Identifying Complexity (Transaction Function) Table 4.2 Identifying Complexity (Transaction Function) Transaction Functions Fields/File involvement FTRS sign up (EI) Fields-Name, Email, Password, Mobile No, 1 DETS 6 Role, Address. File- house-rental Houses (EI) Fields-Owner ID, No of bedrooms, No of 1 13 washrooms, Flat number, Floor number, House type, Rent amount, Upload Pictures, Country, state, city, Address, Description File- house-rental Display houses (EQ) Fields-House ID, Owner ID, No of rooms, 1 10 Address, City, state, Country, Description, Rent amount, Pics of the house File -house-rental Owners (EI) Fields-Owner ID, Name, Email, Mobile No, 1 occupation, No. of houses owned, Address, City, State, Country file- house rental 21 10 Display Owners (EQ) Fields-Owner ID, Name, Email, Mobile No, 1 9 Occupation, No of houses owned, Address, City, State, Country. File- house rental Tenants (EI) Fields-t-id, phone no, name, email, gender, 1 6 dob File house rental Display Tenants (EQ) Fields-Tenant ID, Name, Image, Email, 1 6 Mobile No, Dob File-house rental Booking (EI) Fields-Booking ID, House ID, Booking Date, 1 6 House Name, Price, House Owner Name File-house rental. Rating (EI) Fields-Name, Profession/role, Rating, 1 4 profession/role, Rating, 1 4 Content File- house rental Display Rating (EQ) Fields-Name, Content File- house rental Identifying Complexity (Data Function) Table 4.3 Identifying Complexity (Data Function) Transaction Functions Fields/File involvement RETS Favorite (ILF) Favorite id, house id, house name, 1 house owner name, rent amount, house type, house description 22 address, DETS 8 house-rental (ILF) Fields-booking, houses, Logs, 1 7 member, owner, rating, tenant Payment (ILF) Payment id, status, date, amount, 1 5 name Unadjusted Function Point Contribution (Transaction Function) Table 4.4 Unadjusted Function Point Contributions (Transaction Function) Transaction functions FTRS DTES Complexity UFP Sign Up (EI) 1 6 Low 3 Houses (EI) 1 13 Low 3 Display houses (EQ) 1 10 Low 3 Owners (EI) 1 10 Low 3 Display Owners (EQ) 1 9 Low 3 Tenants (EI) 1 6 Low 3 Display Tenants (EQ) 1 6 Low 3 Booking (EI) 1 6 Low 3 Review and rating (EI) 1 4 Low 3 Display Rating (EQ) 1 4 Low 3 Total 30 23 Unadjusted Function Point Contribution (Data Function) Table 4.5 Unadjusted Function Point Contribution (Data Function) Data Functions DETS Complexity UFP rental 1 7 Low 7 Favorite 1 8 Low 7 Payment 1 5 Low 7 house RETS (ILF) Total 21 Total Degree of Influence Table 4.6 Total Degree of Influence GSC DI 1: Data Communications 2 2: Distributed Data Processing 3 3: Performance 4 4: Heavily used Configuration 2 5: Transaction Pate 0 6: Online Data Entry 4 7: End User Efficiency 2 8: Online Update 4 9: Complex Processing 2 10: Reusability 4 24 11: Installation fare 0 12: Operational fare 1 13: Multiple Sites. 3 14: facilitate Change 3 Total Degree of Influence (TDI) (Range 0 to 70 - influence size by ±35%) 34 Final Calculation Total UFP = UFP (TF) + UFP (DF) = 30 + 21 =51 Value adjustment factor (VAF) = (0.65+ (0.01* TDI)) = (0.65+ (0.01* 34)) = 0.99 Adjusted Function Point (AFP) = Total UFP * VAF =51*0.99 = 50.49 Effort for PHP = 53.33 * 50.49 = 2692.63 Person Hours = 2692.63 / 8 Person Days (Working 8 Hours in a day) = 336.57 Person Days = 336.57 / 25 Man Months (25 working days in a month) = 13.46 Man Months =13.46 / 4 = 3.36 Approximately 3.4 months required for 4 persons to finish the project. 4.2.4 Task Scheduling Project scheduling is an activity of distributing the estimated efforts within the planned project duration. There are some basic rules for project scheduling. They are as follows, Compartmentalization – The project must compartmentalize into a number of manageable activities and tasks. 25 Interdependency – The interdependency of each compartmentalized activity or task must be determined. Some tasks must occur in sequence while others can occur in parallel. Time allocation – Each task to be scheduled must allocated some number of work units. Effort validation – Every project has a defined number of staff members. It should ensure that no more than the allocated number of people has scheduled at any given time. Defined responsibilities – Every task that is scheduled should assign to a specific team member. Defined outcomes – Every task that is scheduled should have a defined outcome. The outcome is normally a work product or a part of a work product. 4.2.5 Project Schedule Chart Total system development is a combination of set of tasks. These set of tasks should done sequentially and timely. Project schedule works as the guideline of the system developer. The following is the schedule chart of this project: Table 4.7 Project Scheduling Chart Weeks Category 1 2 3 4 5 6 7 CC Planning Analysis Design Coding Testing Implement 26 8 9 10 11 12 13 14 15 4.2.6. Cost Estimation The approximation of the cost of a program is cost estimation. In this project, there are five factors to analyze and calculate the cost. Given bellow, • Personnel cost • Software cost • Hardware cost • Other cost Personnel cost: • Number of days in a year = 365 • Number of government holidays in a year = 24 • Number of weekly holidays in a year = 52 • Total number of working days to develop the project =365-(52+24) =289 days • Total number of working days per months to develop the project = 289/12 =24.083 days • Organization working hours per day = 8 hours • Organization working hours per month= 24.083*8 = 192.66 hours Type No. of Month Salary Members s (Taka) System Analyst 1 2 30,000 System Designer and 2 2 50,000 1 2 30,000 Coder System Tester Total 1,10,000 Taka Table 4.8 Personal Cost 27 Hardware Cost: Machin Quant e ity Deskt 1 op Parts Quantit Pric y Motherboa e 1 Depreciation Cost Tot al (Tak Cos a) t 5500 rd Compu Depreciation (5500/12)* 1,833 4 Processor 1 4500 ter (4500/12)* 1,500 4 Core i3 1 3500 2GB RAM (3500/12)* 1,167 9,050 4 500GB 1 4000 1,333 4 HDD Monitor (4000/12)* 1 9000 (9000/12)* 3,000 4 Keyboard 1 400 (400/12)*4 1 3 3 Mouse 1 250 (250/12)*4 8 4 Printer 1 Printer 1 1050 0 (10500/12) 3,500 3,500 *4 Total=12,550 Taka • Computer life = 1 years • Computer usage= 16 weeks = 4 months Table 4.9 Hardware cost 28 Software Cost: Table 4.10 Software cost Price Name MS Office 2010 1,566.40 Windows 10 1,333.00 Notepad++ 0.00 Xampp Server 0.00 Total=2899.40 Other Cost: Table 4.11 Other cost Name Price Transport 1800 House rent 2500 Electric bill 700 Extra 1500 Total=6,500 Total System Development Cost: Table 4.12 Total system Development Cost Purpose Amount Salary 1,10,000 Software cost 2,899.40 Hardware cost 12,550 Other cost 6,500 Total=1,31,949.5 Taka 29 Chapter 5 Risk Management 30 5.1 Risk Analysis A series of documents that assist a system development team in comprehending and managing uncertainty is known as risk analysis and management. While developing a system, numerous issues may arise. A risk is a problem that could happen or not. Analyzing and controlling risks requires several steps. The identification of risks is the first step. After that, each risk is looked at to see how likely it is to happen and how much damage it will cause if it does. Risks are noted once this information is established. Finally, a strategy for dealing with high-impact risks is developed. There are different stages of risk. They are, 1. Risk identification: The process of gathering data to identify potential dangers or risks is known as risk identification. There are a variety of tools and methods for collecting and manipulating data. The team is beginning to identify potential threats to Web resources and is collecting data using both automated and manual methods. One effective method for gathering information about the state of Web pages and websites is web crawling. 2. Risk Classification: The process of creating a structured model to classify risk and incorporating observable risk attributes and events into the model is known as risk classification. To characterize, the team employs both quantitative and qualitative methods. 3. Risk Assessment: The process of determining the likelihood of specific risk scenarios—or sequences of events—that could cause damage or loss—is known as risk assessment. Risk assessment is the focus of many sources. "Transparent, coherent, consistent, complete, comprehensive, impartial, uniform, balanced, defensible, sustainable, flexible, and accompanied by suitable and sufficient guidance" are Rosenthal's descriptions of the characteristics of a generic standard for risk assessment. 4. Risk Analysis: Risk analysis determines the potential impact of risk patterns or scenarios, the possible extent of loss, and the direct and indirect costs of recovery. This step identifies vulnerabilities, considers the willingness of the organization to accept risk given potential consequences, and develops mitigation responses. 31 5. Risk Management Implementation: Policies, procedures, and mechanisms for managing and responding to identified risks are defined in Risk Management Implementation. The program's implementation should strike a balance between the direct and indirect costs of preventing or recovering from damage or loss and the value of assets. There are different categories of risk that should be considered during the development of any project. They are, 1. Project risks: The project plan is in danger from these risks. It is likely that the project schedule will be pushed back and costs will rise if these risks materialize. Potential issues with the software project's budget, schedule, personnel, resources, customers, and requirements are known as project risks. 2. Technical risks: The software that will be produced is in jeopardy because of these risks. Implementation may become difficult or impossible if a technical risk is realized. Potential issues with design, implementation, interface, verification, and maintenance are identified by technical risks. Additionally, technical obsolescence, technical ambiguity, and specification ambiguity are risk factors. 3. Business risks: The software that is going to be made is in jeopardy because of these risks. Building a system that no one really wants is one of the business risks that can be market risks. Building a system that no longer fits the company's overall business strategy are strategic risks. Due to a shift in focus or personnel, management runs the risk of losing support from senior management. 5.2 The RMMM Plan The RMMM plan mainly implies project Mitigation, Project Monitoring, Project Management along with the Impact and probability of any risk to occur. They are described below, • Risk Mitigation: Proactive planning for risk avoidance. 32 • Risk Monitoring: Assessing whether predicted risks occur or not, ensuring preventive steps are being properly applied, collect information for future risk analysis, attempt to determine which risks caused which problem. • Risk Management: Actions to be taken in the event that mitigation steps have failed and the risk has become a live problem. • Type of Impact: Catastrophic (1), Marginal (2), Tolerable (3), Critical (4). • Type of Probability: very low (<10%), low (10–25%), moderate (25–50%), high (50– 75%), very high (>75%). 5. 3 Project Risks: The Project Risks threaten the project plan. In my system, the bellow mentioned projects risks Ineeded manage. Table 5.1: Project Risk Project Risk (PR1) Name Changes the requirements Probability Low (25%) Impact Marginal (2) Description Customer may change their requirements Mitigation & Monitoring Requirements are redefined by the company due to time or business needs. Meeting will be held with the company regularly. This ensures that the product we are producing solves a problem. Management Emergency meeting between both parties to identify new project requirements and goals. Status Not occur. 33 5.4 Technical Risk Technical hazard: threaten the schedule's timeliness and product quality. Because this is my practicum project, it is necessary to properly manage these kinds of risks. Table 5.2: Technical Risk Technical Risk(1) Name Software reusability Probability Moderate (30%) Impact Critical (4) Description Reusable software components contain defects that mean they cannot be reused as planned Mitigation & Monitoring Management Status Replace potential defected software Managing reusable software Solved Table 5.3: Technical Risk Technical Risk(2) Name Database performance. Probability Moderate (40%) Impact Critical (4) Description The database used in the system cannot process as many transactions per second an expected. Mitigation & Monitoring Investigate the possibility of getting better performance database Management Expected database is managed Status Solved 34 Table 5.4: Technical Risk Technical Risk (TR3) Name Poor Training Skill in Team Members. Probability Moderate (30%) Impact Catastrophic (1) Description Poor Training Skill in Team Members to Train the Client. Mitigation & Monitoring The training team should have a clear knowledge about the entire functionality of the software. System analyst need to ensure and monitor it while training session start. Management We should arrange a meeting with the train team and come to a point to solve this problem. We have not encountered such issue yet Status 5.5 Tool Risk Table 5.5 Tool Risk Tool Risk (TR1) Name Software tools coordination Probability Moderate (30%) Impact Tolerable (3) Description Software tools cannot work integrated together in an way Mitigation & Monitoring Management Replace potential defected component By replacing potential defected component tools coordination managed. Status Solved 35 5.6 Requirement Risk Table 5.6: Requirement Risk Requirement Risk (1) Name Changes of Requirements Probability Moderate Impact serious Description Client may change the requirements Mitigation & Monitoring We will call a meeting then will discuss about the problems Management Manage the requirement changes Status Solved Table 5.7: Requirement Risk Requirement Risk (2) Name After changes requirement fail to understand Probability Moderate Impact Tolerable Description Client may fail to understand after changes the requirements Mitigation & Monitoring We will call a meeting then will discuss about the problems Management If this problem occurs, we will able to make them understand Status Not occur 36 Chapter 6. Analysis Modeling 37 6.1 Analysis Modeling Analysis modeling depicts requirements for data, function, and behavior in a manner that is relatively simple to comprehend and, more importantly, simple to review for correctness, completeness, and consistency using a combination of text and diagrammatic forms. Resources for UML as well as those for conventional and object-oriented analysis (OOA) methods are provided in this section. 6.1.1 Objectives of analysis model The Objectives of analysis model are as follows, • Domain Analysis • Describe what the client requires • Establish a basis for the creation of a software design • Define a set of requirements that can be validated once the software is built. 6.2 Activity Diagram With support for choice, iteration, and concurrency, activity diagrams are graphical representations of workflows that consist of stepwise activities and actions. Activity diagrams are used to model both organizational and computational processes in the Unified Modeling Language. Activity diagrams depict the overall control flow. 38 6.2.1 Activity diagram for Admin Figure 6.1 Activity diagram for Admin 6.2.2 Activity diagram House Owner Figure 6.2 Activity diagram for House Owner 39 6.2.3 Activity diagram Tenant Figure 6.3 Activity diagram for Tenant 6.4 Entity Relationship Diagram (ERD) An entity relationship diagram (ERD), also known as an entity relationship model, is a graphical representation of relationships between individuals, things, locations, concepts, or events within an information technology (IT) system. An ERD makes use of data modeling strategies in order to establish business procedures and lay the groundwork for a relational database. 40 Figure 6.3 ERD of House Renting System 6.5 Data Flow Diagram (DFD) By graphically depicting the "flow" of data through an information system, a data flow diagram (DFD) models the process features of the system. A DFD is often used as a starting point to create a system overview that can be further developed later. Data processing visualization is another application for DFDs. 41 6.5.1 Context Level DFD Figure 6.4 Context Level DFD 42 6.5.2 Level 1 DFD Figure 6.5 Level 1 DFD 6.5.3 Level 2 DFD of Process 1 Figure 6.6 Level 2 DFD of Process 1 43 6.5.4 Level 2 DFD of Process 2 Figure 6.7 Level 2 DFD of Process 2 6.5.5 Level 2 DFD of Process 3 Figure 6.8 Level 2 DFD of Process 3 44 6.5.6 Level 2 DFD of Process 4 Figure 6.9 Level 2 DFD of Process 4 6.5.7 Level 2 DFD of Process 5 Figure 6.10 Level 2 DFD of Process 5 45 6.5.8 Level 1 DFD of Process 6 Figure 6.11 Level 2 DFD of Process 6 6.5.8 Level 2 DFD of Process 7 Figure 6.12 Level 2 DFD of Process 7 46 Chapter 7. Designing 47 7.1 Database Field Design Table List Figure 7.1 List of tables in Database Users Table Figure 7.2 Users table structure House Table Figure 7.3 House table structure 48 Booking Table Figure 7.4 Booking table structure Saved Property Table Figure 7.5 Saved property table structure Review Table Figure 7.6 Review table structure 49 7.2 Interface Design Figure 7.7 User Registration interface Figure 7.8 User Login interface Figure 7.9 Homepage 50 Figure 7.10 User Profile interface Figure 7.11 Admin Panel User list Figure 7.12 Admin House list interface 51 Chapter 8. Quality Assurance 52 8.1 System Testing Software testing is the process of evaluation a software item to detect differences between given input and expected output. Also, to assess the feature of A software item. Testing assesses the quality of the product. Software testing is a process that should be done during the development process. In other words, software testing is a verification and validation process. Verification: Verification is the process to make sure the product satisfies the conditions imposed at the start of the development phase. In other words, to make sure the product behaves the way we want it to. Validation: Validation is the process to make sure the product satisfies the specified requirements at the end of the development phase. In other words, to make sure the product is built as per customer requirements. The objectives of software testing are: • Testing is a process of executing a program with the intent of finding an error. • A good test case is one that has a high probability of finding an as-yet-undiscovered error. • A successful test is one that uncovers an as-yet-undiscovered error. The design of tests for software can be challenging as the initial design of the product itself. Software can be tested in one of two ways: • Knowing the specified function that the software has been designed to perform, tests can be conducted that demonstrate each function fully while at the same time searching for errors in each function. This approach is known as black-box testing. • Knowing the internal workings of software, tests can be conducted to ensure that internal operations are performed according to specifications and all internal components have been adequately exercised. This approach is known as white-box testing. 53 8.1.1 Software Testing Strategy A strategy for software testing integrates software test case design methods into a well-planned series of steps that result in the successful construction of a software. The strategy provides a road map that describes the steps to be conducted as part of testing. Testing strategy that will be followed in this software project – • Unit testing • Integration testing • Validation testing The first step in software testing is unit testing. Unit testing concentrates on each unit of the software as implemented in source code. Unit testing focuses on each component individually. The unit test is white-box oriented. Thus, unit testing of this library software will be done after completion of every module or component. The next step is integration testing. Integration testing is a systematic technique for constructing the program structure while at the same time conducting tests to uncover errors associated with interfacing. The objective of integration testing is to take unit tested components and build a program structure that has been dictated by design. The integration testing strategy that has been chosen for this project is top down testing. Blackbox testing method is the most prevalent for integration testing. Top down integration strategy will be used to perform integration testing. Top down integration will be done by breadth-first manner. Breadth-first integration incorporates all components directly subordinate at each level, moving across the structure horizontally. After the software has been integrated, a set of high order tests am conducted. Hence, the validation criteria that have been mentioned in requirements engineering should be tested. Validation testing provides final assurance that software meets all functional, behavioral and performance requirements. The black-box testing method is exclusively used in validation. 8.2 System Testing Methodology • Black-box Testing 54 Black-box testing which is also known as behavioral testing focuses on the functional requirements of the software. It enables the software engineer to derive sets of input conditions that will fully exercise all functional requirements for a program. Black-box testing method will be applied to test the modules of LMS. • White-box Testing White-box testing, which also known as glass-box testing, is a test case design method that uses the control structure of the procedural design to derived test cases. Using white-box testing methods, software engineer can derive test cases that, 1. Guarantee that all independent paths within a module have been exercised at least once 2. Exercise all logical decisions on their true and false sides 3. Execute all loops at their boundaries and within their operational bounds 4. Exercise internal data structures to ensure their validity. The modules that contain some complex calculations or decision making code such as check the availability of the library item will be tested using white-box method. 8.3 Testing Design Table 8.1 Testing Scenario 1 Testing Scenario No:1 Scenario Owner and tenant log in testing scenario of our system. Input Desired Output Email, Password of owner or tenant for log in. When enter E-mail, password then get access level defines. Actual Output’s For login my system works correctly. Verdict Getting result from Desired Output’s and Actual Output’s decided this system is successful for login. 55 Table 8.2 Testing Scenario 2 Testing Scenario No:2 Scenario Owner can add houses. Input Submit all the house’s information. Desired Output Save the information into the system. Actual Output For showing all records my system works correctly. Verdict The process is worked correctly and successfully. Table 8.3 Testing Scenario 3 Testing Scenario No:3 Scenario Tenant can book houses, rate houses. Input Submit all the booking and rating information. Desired Output Save the information into the system. Actual Output For showing all records my system works correctly. Verdict The process is worked correctly and successfully. 56 Table 8.4 Testing Scenario 4 Testing Scenario No:4 Scenario Payment testing scenario of the system Input User will insert Payment Details After registration Desired Output User will be notified and will be sent to pending list Actual Output After testing I got the desired output. So, this is successful. Verdict The system is worked correctly and successfully. Table 8.5 Testing Scenario 5 Testing Scenario No:5 Scenario Report Generation testing scenario of the system. Input Admin Will generate report by clicking “Site Report” Desired Output Actual Output Report generation with all data The report was generated perfectly with all data elements. So, this is successful. Verdict The system successfully. 57 is worked correctly and Chapter 9. Conclusion 58 9.1 Preface Today is the age of modern science and information and online communication, which is critical to development of more effective operational and management process. To provide better and uninterrupted services to the employee of Kodeeo Limited Bangladesh a group of Software specialist working together to keep the service all time. I was fortunate and blessed to get this lucky break to work some of these efficient hard working friendly engineers. My earnest thanks, gratitude and salutations to these wonderful people from the deep down inside my heart. 9.1.1 Practicum and Its Value In your career development as with most life issues there is direct relationship between effort and reward. To me, practicum can be as a transition from engineering college study life to a real world workplace through hands on experience of engineering practices. The four years of undergraduate engineering studies gives a student theoretical and practical knowledge. Using that knowledge and observing live operational system, the practicum program clarifies those subject matters to another level blessed with practical working skills. Considering this fact, it gives us an immense pleasure to say that my practicum was a successful event. Practical work experience doesn’t have any other alternatives. Before getting into the job student should have a real world work experiences in a major field of study. Now-a-day’s recruiter no longer considers just high grades, good communication skill, part time work experiences. They highly consider the work experiences of an applicant. Students with better work experiences are getting the better job opportunities. Kodeeo Limited Bangladesh gives us the opportunity of working in a professional working environment. During the internship period I have tried my level best to make my system efficient. I followed the lessons, methods, tools and techniques that I have learned during my study period at IUBAT. Successful software development is a blend of standard development practices, proper theoretical knowledge and the developer’s creativity. Student of College of Engineering and Technology (CEAT) at IUBAT go for this practicum program carrying 6 credit hours weight, which goes for a semester long and usually after the 59 completion of the course work. A report submitted after the completion of the practicum followed by a presentation and a comprehensive examination on the overall four years education. 9.2 Conclusion My internship period at Kodeeo Limited Bangladesh has been an amazing experience. I have learnt so much within this 12 weeks which will impact greatly and positively in my future career goals. During this 12 weeks internship time I was assigned to complete a project named “House Renting System”. This report contains all the details of the project and also of the development phases and strategies of the project. Our project is only a humble venture to satisfy the needs in Development of House Rental System. Here we have tried to show how user, tenant & owner uses a website for their house rent purpose. Maybe there is some works or some other module we can add, but we tried our best level for our project. During the development of this project there many problems that I had to face. Time constraint was the biggest issue that I had to face during the development of this project. Because of the time constraint there are many limitations of this project. If I am given a chance to work further with this system I have all the future plans to make the system a perfect house rental system. 9.3 Limitations This project has some limitations those we have planned to develop in future. The limitations are: ❖ Renters (tenants) cannot pay monthly rent separately. ❖ Embedded account management and some other module is needed to be implemented. ❖ Here renters (tenants) will not get any mobile SMS notifications 60 9.4 Future plan If I am given a chance to work further with this project I have plans made to make the system more efficient for the users. The followings are the future plan for the “House Renting System”. 1. A process to verify the identification of the user will be implemented by including a NID verification method. 2. An option for chatting will be included so that the tenants can chat with owner. 3. A password recovery system through email will be implemented. 4. Mobile Banking options will be implemented. 61 References Kendall, E. & Kendall. (1999). System Analysis and Design. 4th Ed. New Delhi: PrenticeHall. Kushal. S, (2007, Mar 14). Calculating Function Points. (Accessed on 20 March, 2019) Retrieve from https://www.codeproject.com/articles/18024/calculating-function-points Longstreet, David. (2005). Fundamentals of Function Point Analysis. (Accessed on 19 March, 2019)Retrieve from http://www.softwfaremetrics.com/fpafund.html. Meyer, Bertrand. (1997), OOSC2: The Use Case Principle. (Accessed on 18 March, 2019)Retrieve From http://www.elj.com/elj/v1/n2/bm/usecases. Pressman, Roger S. (2004). Software Engineering: A Practitioner’s Approach. 5th ed. Boston: McGraw Hill. Silberschattz, Abraham, Korth, Henry F., &Sudrashan S. (2002). Database System Concepts. 4th ed. Boston: McGraw Hill. Function Point Overview. (Accessed on 20 November, 2022) Retrieve from http://www.csee.umbc.edu/~mgrass2/cmsc645/function_point.html How to calculate function points. (Accessed on 27 November, 2022) Retrieve from http://stackoverflow.com/questions/34473698/how-to-calculate-functionpoints The RMMM Plan. url: http://www.tutorialride.com/software-engineering/risk-managementinsoftware-engineering.html(Accessed on 2 December, 2022) Methods of System quality testing. url: https://en.wikipedia.org/wiki/Software_testing (Accessed on 5 December, 2022) System quality assurance. url: https://en.wikipedia.org/wiki/Software_quality_assurance (Accessed on 09 December, 2022) 1