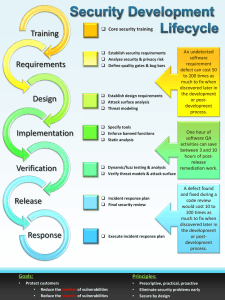
01- Comparing Security Roles and Security Controls 1.1- Compare and Contrast Information Security Roles Information Security Information Security Competencies Information Security Roles and Responsibilities Information Security Business Units 1.2- Compare and Contrast Security Control and Framework Types Security Control Categories Security Control Functional Types ISO and Cloud Frameworks 02- Explaining Threat Actors and Threat Intelligence 2.1- Explain Threat Actor Types and Attack Vectors Vulnerability, Threat, And Risk Attributes of Threat Actors Categories of Threat Actors State Actors and Advanced Persistent Threats Attack Vectors 2.2- Explain Threat Intelligence Source Threat Research Sources Threat Intelligence Providers 03- Performing Security Assessments 3.1- Assess Organizational Security with Network Reconnaissance Tools Ipconfig, Ping, And Arp Route and Traceroute Ip Scanners and Nmap Service Discovery and Nmap Netstat and Nslookup Other Reconnaissance and Discovery Tools Packet Capture and Tcpdump Packet Analysis and Wireshark Packet Injection and Replay Exploitation Frameworks Netcat 3.2- Explain Security Concerns with General Vulnerability Types Software Vulnerabilities and Patch Management Zero-Day and Legacy Platform Vulnerabilities Weak Host Configurations Weak Network Configurations Impacts from Vulnerabilities 3.3- Summarize Vulnerability Scanning Techniques Vulnerability Scan Types Common Vulnerabilities and Exposures Credentialed Versus Non-Credentialed Scanning 3.4- Explain Penetration Testing Concepts Penetration Testing Rules of Engagement Attack Profile Bug Bounty Exercise Types 04- Identifying Social Engineering and Malware 4.1- Compare and Contrast Social Engineering Social Engineering Impersonation Dumpster Diving and Tailgating Piggy Backing Identity Fraud Shoulder Surfing and Launchtime Attacks Phishing Spear Phishing Whaling and Vishing Spam and Hoaxes 4.2- Analyze Indicators of Malware-Based Attacks Malware Classification Malware Categories Computer Viruses Computer Worms Spyware, Keyloggers and Adware Backdoors and Remote Access Trojans (Rat) Rootkits Ransomware and Crypto-Malware Malware Indicators 05- Summarizing Basic Cryptographic Concepts Cryptographic Concepts Hashing Algorithms Encryption Ciphers and Keys Symmetric Encryption Asymmetric Encryption Public Key Cryptography Algorithms 06- Implementing Public Key Infrastructure. 6.1- Implement Certificates and Certificate Authorities Public and Private Key Usage Certificate Authorities PKI Trust Models Registration Authorities and CRSs Digital Certificates Certificate Attributes 6.2- Implement PKI Management Certificate and Key Management Certificate Expiration Certificate Revocation Lists OPENSSL 07- Implementing Authentication Controls 7.1- Summarize Authentication Design Concepts Identity and Access Management Authentication Factors Authentication Design Multifactor Authentication 7.2- Implement Knowledge-Based Authentication Local, Network, And Remote Authentication Windows Authentication Linux Authentication Single Sign-On (SSO) Kerberos Authentication Pap, Chap, And MS-Chap Authentication Password Attacks Brute-Force and Dictionary Attacks Dictionary and Rainbow Table Attacks Hybrid Attack Password Crackers 7.3- Summarize Biometrics Authentication Concepts Biometric Authentication Fingerprint Recognition Facial Recognition Behavioral Technologies 08- Implementing Identity and Account Management Controls 8.1- Implement Identity and Account Types Identity Management Controls Personnel Policies for Privilege Managements Offboarding Policies Security Account Types and Credential Management Security Group-Based Privileges Administrator/Root Accounts Service Accounts 8.2- Implement Account Policies Account Attributes and Access Policies Account Password Policy Settings Account Restrictions ACCOUNT AUDITS Account Lockout and Disablement 09- Implementing Secure Network Designs 9.1- Implement Secure Network Designs Secure Network Designs Network Appliances Routing and Switching Protocols Network Topology and Zones Demilitarized Zones (DMZ) 9.2- Implement Secure Switching and Routing Man-In-The-Middle and Layer 2 Attacks Physical Port Security and Mac Filtering Network Access Control Route Security 9.3- Implement Secure Wireless Infrastructure Wireless Network Installation Controller and Access Point Rogue Access Points and Evil Twins Jamming Attacks 9.4- Implement Load Balancers Distributed Denial of Service Attacks (DDOS) DDOS Attack Mitigation Load Balancing 10- Implementing Network Security Appliances 10.1- Implement Firewalls and Proxy Servers Packet Filtering Firewalls Stateful Inspection Firewalls Firewall Implementation Virtual Firewalls 10.2- Implement Network Security Monitoring Network-Based Intrusion Detection Systems Network-Based Intrusion Prevention Systems Signature-Based Detection Behavior and Anomaly-Based Detection Next-Generation Firewalls Unified Threat Management (UTM) Web Application Firewalls 10.3- Summarize The Use of SIEM Monitoring Services Security Information and Event Management (SIME) Security Orchestration, Automation, And Response (SOAR) 11- Implementing Secure Network Protocols 11.1- Implement Secure Network Operations Network Address Allocation Domain Name Resolution DNS Security 11.2- Implement Secure Application Protocols Hypertext Transfer Protocol (Http) Transport Layer Security File Transfer Services 11.3- Implement Secure Remote Access Protocols Remote Access Architecture Remote Desktop Secure Shell 12- Implementing Host Security Solutions 12.1- Implement Endpoint Security Hardening Patch Management Endpoint Protection 13- Implementing Secure Mobile Solutions 13.1- Implement Mobile Device Management Mobile Device Deployment Models Enterprise Mobility Management Mobile Access Control Systems Remote Wipe Full Device Encryption and External Media Location Services Rooting and Jailbreaking 14- Summarizing Secure Application Concepts 14.1- Analyze Indicators of Application Attacks Analyze Indicators of Application Attacks Application Attacks Overflow Vulnerabilities Memory Leaks and Resource Exhaustion DLL Injection 14.2- Analyze Indicators of Web Application Attacks Uniform Resource Locator Analysis Replay Attacks Session Hijacking Cross-Site Scripting (XSS) Structured Query Language (SQL) Injection 14.3- Summarize Secure Coding Practices Secure Coding Techniques 15- Implementing Secure Cloud Solutions 15.1- Summarize Secure Cloud and Virtualization Services Cloud Deployment Models Cloud Service Models Virtualization Technologies and Hypervisor Types Virtual Desktop Infrastructure and Thin Clients Container 15.2- Apply Cloud Security Solutions Cloud Security Controls High Availability 16- Explaining Data Privacy and Protection Concepts 16.1- Explain Privacy and Data Sensitivity Concepts Privacy and Sensitive Data Concepts Privacy Vs. Security Data Roles and Responsibilities Data Classifications Data Types Privacy Breaches and Data Breaches 16.2- Explain Privacy and Data Protection Controls Data Protection Data Exfiltration Data Loss Prevention 17- Performing Incident Response 17.1- Summarize Incident Response Procedures Incident Response Process Cyber Incident Response Team Incident Response Plan Cyber Kill Chain Attack Framework Other Attack Frameworks 17.2- Utilize Appropriate Data Sources for Incident Response Incident Identification Security Information and Event Management(SIME) SIME Dashboards Logging Platforms Network, Os, And Security Log Files Application Log Files 17.3- Apply Mitigation Controls Incident Containment Incident Eradication and Recovery Firewall Configuration Changes 18- Explaining Digital Forensics 18.1- Explain Key Aspects of Digital Forensics Documentation Key Aspects of Digital Forensics Digital Forensics Reports E-Discovery Video and Witness Interviews Timelines Event Logs and Network Traffic 19- Summarizing Risk Management Concepts 19.1- Explain Risk Management Processes and Concepts Risk Management Processes Risk Types Quantitative Risk Assessment Qualitative Risk Assessment Risk Avoidance Risk Transference and Risk Acceptance 19.2- Explain Business Impact Analysis (Bia) Concepts Business Impact Analysis Mission Essential Functions Single Points of Failure Disasters Disaster Recovery Plans 20- Implementing Cybersecurity Resilience 20.1- Implement Redundancy Strategies High Availability Power Redundancy Network Redundancy Disk Redundancy 20.2- Implement Backup Strategies Disk Redundancy Backup Types 21- Explaining Physical Security 21.1- Explain The Importance of Physical Site Security Controls Physical Security Controls Site Layout, Fencing, And Lighting Gateways and Locks Alarm Systems Security Guards and Cameras 21.2- Explain The Importance of Physical Host Security Controls Secure Areas Secure Data Destruction Data Sanitization Tools 01- Comparing Security Roles and Security Controls 1.1- Compare and Contrast Information Security Roles Information Security Information Security (or infosec): protection data resources from unauthorized access, attack, theft, or damage. Data may be vulnerable because of the way it is stored, transferred, or the way it is processed. Secure information has three properties (CIA Triad): - Confidentiality: only be known to certain people. - Integrity: only be modification by authorized people. - Availability: only be accessible by authorized people Non-repudiation: subject cannot deny doing something, such as creating sending …. Information Security Competencies Information Security Roles and responsibilities Security Policy: is a formalized statement that defines how security will be implemented within an organization. Information Security Business Units Security Operations Center (SOC): monitor and protect critical information. Cyber Incident Response team (CIRT) or Computer Security Incident Response Team (CSIRT) or Computer Emergency Response Team (CERT): Single point-of-contact for the notification of security incidents 1.2- Compare and Contrast Security Control and Framework Types Security Control Categories Security Control: something designed to give a system or data asset the properties CIA. Controls can be divided representing the way the control is implemented: - Technical: implemented as a system for example, firewalls, antivirus OS access control models. - Operational: implemented primarily by people for example, security guards. - Managerial: oversight of the information system for example risk identification. Security Control Functional Types Controls can be classified representing according the goals or functions: - Preventive: preventative control operates before an attack can take place, Access - Detective: detective control operates during the progress of an attack. - Corrective: corrective control is used after an attack. Controls can be classified according other case: - Physical: alarms, gateways, locks, lighting, security cameras, and guards. - Deterrent: signs and warnings of legal penalties against trespass or intrusion. - Compensating: substitute for a principal control, as recommended by a security. ISO and Cloud Frameworks ISO 27001 or 27K: information security standards. - 27002: classifies security controls. - 27017 and 27018: reference cloud security. - 27701: focuses on personal data and privacy. ISO 31000 or 31K: establishes best practices for performing risk assessments. 02- Explaining Threat Actors and Threat Intelligence 2.1- Explain Threat Actor Types and Attack Vectors Vulnerability, Threat, and Risk Security Assessment: identify ways in which their systems could be attacked, these assessments involve: - Vulnerability: is a weakness that could be triggered accidentally or exploited. - Threat is the potential for someone or something to exploit a vulnerability and breach security. - Risk: is the likelihood and impact (or consequence) of an attacker exploiting vulnerability. Threat Actor or Threat Agent: The person or thing that poses the threat. Attributes of Threat Actors External: has no account or authorized access to the target system. Internal: has been granted permissions on the system. Intent: describes what an attacker hopes to achieve from the attack. Motivation: the reason for perpetrating the attack. Categories of Threat Actors Hackers: Hacker describes an individual who has the skills to gain access to computer systems - black hat (unauthorized) - white hat (authorized) - Gray hat (semi-authorized) - Script Kiddies: someone who uses hacker tools without necessarily understanding how they work. - Hacker Teams and Hacktivists: group of hacker work together. State Actors and Advanced Persistent Threats State Actors or Advanced Persistent Threat (APT): teams of hackers work for countries. Attack Vectors Attack Vector: The path or tool used by a malicious threat actor. Cloud be Direct access, Removable media, Email, Remote and wireless, Web and social media or Cloud. 2.2- Explain Threat Intelligence Source Threat Research Sources Threat research: gathering effort to attempt to discover the tactics, techniques, and procedures (TTPs) of modern cyber adversaries. honeynets to try to observe how hackers interact with vulnerable systems. Dark net: a network that prevent a third party from knowing about the existence of the network or analyzing any activity established such as The Onion Router (TOR), Freenet, or I2P Dark web: sites require registration, pages that block search indexing, unlinked pages, pages using nonstandard DNS, and content encoded in a nonstandard manner. Threat Intelligence Providers Closed/proprietary: the threat research is made available as a paid subscription. Vendor websites: proprietary threat intelligence is not always provided at cost. Public/private information sharing centers: set up to share threat intelligence and promote best practice. Open source intelligence (OSINT): some companies operate threat intelligence services on an open-source basis, earning income from consultancy rather than directly from the platform or research effort. 03- Explaining Threat Actors and Threat Intelligence 3.1- Assess Organizational Security with Network Reconnaissance Tools Ipconfig, Ping, and Arp Reconnaissance: the process of mapping out the attack surface. Topology discovery or Footprinting: means scanning for hosts, IP ranges, and routes between networks to map out the structure of the target network. ipconfig: show the configuration assigned to network interface(s) in Windows. ifconfig: show the configuration assigned to network interface(s) in Linux. ping: check the communication between to host using Internet Control Message Protocol (ICMP). arp: shows the MAC address with each IP address the local host has communicated with recently. (SY 0 Route and Traceroute route: view and configure the host's local routing table. tracert: uses ICMP to report the round trip time (RTT) for hops between the local host and a host on a remote network. traceroute: performs route discovery from a Linux host, traceroute uses UDP probes rather than ICMP, by default. pathping: provides statistics for latency and packet loss along a route over a longer measuring period, on Linux use mtr. Ip Scanners and Nmap Nmap Security Scanner: is one of the most popular open-source IP scanners. The default behavior of Nmap is to ping and send a TCP ACK packet to ports 80 and 443 to determine whether a host is present. It can be operated with a command line or via a GUI (Zenmap). Service Discovery and Nmap Service Discovery: work out which operating systems are in use, which network services each host is running, and, if possible, which application software is underpinning those services. Fingerprinting: The detailed analysis of services on a particular host. Banner Grabbing: scanning software to guess at the software name and version, without having any sort of privileged access to the host. Netstat and Nslookup Tools built into the Windows and Linux operating systems: - netstat: show the state of TCP/UDP ports on the local machine. - nslookup/dig—query name records using a particular DNS resolver under Windows (nslookup) or Linux (dig). Other Reconnaissance and Discovery Tools theHarvester: is a tool for gathering open-source intelligence (OSINT) for a particular domain or company name. dnsenum: packages a number of tests into a single query. Scanless: tools for Port and services scanning. curl tools: is command line client for performing data transfers over many types of protocol. Nessus: is one of the best-known commercial vulnerability scanners. Packet Capture and Tcpdump Packet and protocol analysis: tool to capture and decode the frames of data. Switched Port Analyzer ((SPAN) or Mirror Port): Capturing from a network segment. Test Access Port (TAP): device can perform capturing over a network cable segment. Tcpdump: is a command line packet capture utility for Linux. Packet Analysis and Wireshark Wireshark: is an open-source graphical packet capture and analysis utility. You can save the output to a (. pcap) file or load a file for analysis. Packet Injection and Replay There are also tools that allow for different kinds of packets to be crafted and manipulated: - Dsniff - Ettercap - Scapy - hping - tcpreplay Exploitation Frameworks Exploitation Framework: uses the vulnerabilities identified by an automated scanner and launches scripts or software to attempt to deliver matching exploits. Metasploit: The best-known exploit framework. Netcat Netcat: tool for testing connectivity. can be used for port scanning and fingerprinting. can be used to receive files. 3.2- Explain Security Concerns with General Vulnerability Types Software Vulnerabilities and Patch Management Software exploitation means an attack that targets a vulnerability in software code. Zero-Day and Legacy Platform Vulnerabilities Zero-Day: is a vulnerability that is exploited before the developer knows about it or can release a patch. legacy platform is one that is no longer supported with security patches by its developer or vendor. legacy platforms are unpatchable. Should be isolating them to networks that an attacker cannot physically connect to. Weak Host Configurations Default Settings. Unsecured Root Accounts. Open Permissions. Weak Network Configurations Open Ports and Services. Unsecure Protocols. Weak Encryption. Errors. Impacts from Vulnerabilities Data Breach: event is where confidential data is read, transferred, modified, or deleted without authorization. Data exfiltration: attacker transfers data without authorization from the victim's systems to an external network or media. Identity Theft Impacts. Financial and Reputation Impacts. 3.3- Summarize Vulnerability Scanning Techniques Vulnerability Scan Types Network Vulnerability Scanner: is designed to test network infrastructure, such as Tenable Nessus or OpenVAS. Application and Web Application Scanners: look for known web exploits, such as SQL injection and cross-site scripting (XSS), and may also analyze source code and database security to detect unsecure programming practices. such as Nikto. Common Vulnerabilities and Exposures Vulnerability Feed: An automated scanner needs to be kept up to date with information about known vulnerabilities. Nessus tool refers to these feeds as plug-ins, and OpenVAS refers to them as network vulnerability tests (NVTs). Secure Content Automation Protocol (SCAP): Many vulnerability scanners use it to obtain feed or plug-in updates. Common Vulnerabilities and Exposures (CVE): is a dictionary of vulnerabilities in published operating systems and applications software. Common Vulnerability Scoring System (CVSS): additional analysis plus fix information and generate metrics that a score from 0 to 10 based on characteristics of the vulnerability risk. Credentialed Versus Non-Credentialed Scanning Non-Credentialed Scan: proceeds to test packets at a host without being able to log on to the OS or application. Credentialed Scan proceeds to test packets at a host with login rights to the OS or application. 3.4- Explain Penetration Testing Concepts Penetration Testing A penetration test or pen test: uses authorized hacking techniques to discover exploitable weaknesses in the target's security systems, also referred to as ethical hacking. Rules of Engagement Rules of engagement: specify what activity is permitted or not permitted. These rules should be made explicit in contractual agreement. Attack Profile Black box or unknown environment: no privileged information about the network and its security systems. White box or known environment: the consultant is given complete access to information about the network. Gray box or partially known environment: the consultant is given some information. Bug Bounty Bug Bounty: is a program operated by a software vendor or website operator where rewards are given for reporting vulnerabilities. Exercise Types Red team: performs the offensive role. Blue team: performs the defensive role. 04- Identifying Social Engineering and Malware 4.1- Compare and Contrast Social Engineering Social Engineering Social engineering: refers to means of either eliciting information from someone or getting them to perform some action for the threat actor. also be referred to as hacking the human. Impersonation Impersonation: simply means pretending to be someone else. over the phone or via an email message. Dumpster Diving and Tailgating Dumpster Diving: search in garbage to try to find useful documents. Tailgating: entering a secure area by following close behind the person that has been allowed to open the door. Piggy Backing Piggy backing: the attacker enters a secure area with an employee's permission. Identity Fraud Identity fraud: is a specific type of impersonation where the attacker uses specific details of someone's identity. Shoulder Surfing and Launchtime Attacks Shoulder Surfing: attacker can learn a password or PIN by watching the user type it. Launchtime: If a user leaves a workstation unattended while logged on, an attacker can physically gain access to the system Phishing Phishing: is a combination of social engineering and spoofing Spear Phishing Spear Phishing: attack the specific person. Whaling and Vishing Whaling: attack important person in company like CEO. Vishing: attack through a voice channel (telephone or VoIP, for instance). Spam and Hoaxes Spam: attack through email. Hoaxes: attack by scam people. 4.2- Analyze Indicators of Malware-Based Attacks Malware Classification Malware is usually simply defined as software that does something bad, from the perspective of the system owner Malware Categories Viruses Worms Trojan Potentially unwanted programs (PUPs) Computer Viruses Virus: is executed only when the user performs an action such as downloading and running an infected executable process. Computer Worms Worm: is memory-resident malware that can run without user intervention and replicate over network resources. Spyware, Keyloggers and Adware Spyware Keylogger Adware: this is a class of PUP/grayware that performs browser reconfigurations. Backdoors and Remote Access Trojans (Rat) Backdoors: any type of access method to a host that circumvents the usual authentication method and gives the remote user administrative control. Remote Access Trojans (RAT): is backdoor malware that mimics the functionality of legitimate remote control programs. Bot: is an automated script or tool that performs some malicious activity. Botnet: group of bots that are all under the control of the same malware instance can be manipulated. Rootkits Rootkit: modifying files in the kernel of the operating system. Ransomware and Crypto-Malware Ransomware: this method of taking away your data and requiring you to pay to get that data back. Crypto-malware: is new form of ransomware uses cryptography to be able to encrypt all of your personal information. Malware Indicators Antivirus Notifications Sandbox Execution: analyze the suspect code in a sandboxed environment. sandbox is a system configured to be completely isolated from its host so that the malware cannot break out. LIKE Cuckoo. Resource Consumption: Indicators such as excessive and continuous CPU usage, memory leaks, disk read/write activity, and disk space. File System: A computer's file system stores a great deal of useful metadata about when files were created, accessed, or modified. 05- Summarizing Basic Cryptographic Concepts Cryptographic Concepts Cryptography: It is the art of making information secure by encoding it. Cryptanalysis: the art of cracking cryptographic systems. Plaintext or cleartext: an unencrypted message. Ciphertext: an encrypted message. Cipher: the process (or algorithm) used to encrypt and decrypt a message. Hashing Algorithms Hashing: is the simplest type of cryptographic operation. Cryptographic Hashing Algorithm: produces a fixed length string from an input plaintext that can be of any length. Checksum or Message Digest or Hash: can be referred the output. Hashing algorithm is used to prove integrity. Hash function can be used to prove the integrity of data, but it cannot be used to store or transmit data. The plaintext cannot be recovered from the digest. There are two popular implementations hash algorithms: - Secure Hash Algorithm (SHA) - Considered the strongest algorithm. - There are variants that produce different-sized outputs, with longer digests considered more secure. - The most popular variant is SHA-256, which produces a 256-bit digest. - Message Digest Algorithm #5 (MD5) - Produces a 128-bit digest. - is not considered to be as safe, but it might be required for compatibility between security products. Encryption Ciphers and Keys Encryption Algorithm: is a type of cryptographic process that encodes data so that it can be recovered or decrypted. Symmetric Encryption Symmetric Encryption: is also referred to as single key or private key or shared secret. Symmetric: is one in which encryption and decryption are both performed by the same secret key. If the key is lost or stolen, the security is breached. Symmetric encryption is used for confidentiality Symmetric encryption is very fast. It is used for bulk encryption of large amounts of data. The main problem is secure distribution and storage of the key. Asymmetric Encryption Asymmetric Encryption: two different key public and private to perform encryption and decryption. Asymmetric Encryption: can be used to prove identity. Asymmetric Encryption: is often referred to as public key cryptography. Public Key Cryptography Algorithms RSA algorithm: Many public key cryptography products are based on it. The RSA algorithm provides the mathematical properties for deriving key pairs and performing the encryption and decryption operations. This type of algorithm is called a trapdoor function, because it is easy to perform using the public key, but difficult to reverse without knowing the private key. Elliptic curve cryptography (ECC): is another type of trapdoor function that can be used in public key cryptography ciphers. 06- Implementing Public Key Infrastructure. 6.1- Implement Certificates and Certificate Authorities Public and Private Key Usage Public Key Cryptography solves the problem of distributing encryption keys when you want to communicate securely with others or authenticate a message that you send to others. When you want others to send you confidential messages, you give them your public key to use to encrypt the message, the message can then only be decrypted by your private key, which you keep known only to yourself. When you want to authenticate yourself to others, you create a signature and sign it by encrypting the signature with your private key, you give others your public key to use to decrypt the signature, as only you know the private key, everyone can be assured that only you could have created the signature. Public key infrastructure (PKI): aims to prove that the owners of public keys are who they say they are. Under PKI, anyone issuing public keys should obtain a digital certificate. The validity of the certificate is guaranteed by a certificate authority (CA). Certificate Authorities Certificate Authority (CA): is the entity responsible for issuing and guaranteeing certificates. Private CAs: can be set up within an organization for internal communications. PKI Trust Models Single CA: issues certificates to users; users trust certificates issued by that CA and no other. The problem If single CA server is compromised the whole PKI collapses. Hierarchical (Intermediate CA): also referred to as certificate chaining or a chain of trust In the hierarchical model, a single CA (called the root) issues certificates to several intermediate CAs. The root's certificate is self-signed. In the hierarchical model, the root is still a single point of failure. Online CA: is one that is available to accept and process certificate signing requests, publish certificate revocation lists, and perform other certificate management tasks. Offline CA: This means that it is disconnected from any network and usually kept in a powered-down state. Registration Authorities and CRSs Registration: process by which end users create an account with the CA and become authorized to request certificates. Certificate Signing Request (CSR): when a subject want to obtain a certificate. CSR: is a Base64 ASCII file containing the information that the subject wants to use in the certificate including its public key. Digital Certificates Digital Certificate: is essentially a wrapper for a subject's public key. The certificate is digitally signed to prove that it was issued to the subject by a particular CA. Digital certificates are based on the X.509 standard. Certificate Attributes The X.509 standard defines the fields or attributes that must be present in the certificate. 6.2- Implement PKI Management Certificate and Key Management Key Management: refers to operational considerations for the various stages in a key's life cycle. A key's life cycle may involve the following stages: - Key generation: creating a secure key pair of the required strength, using the chosen cipher. - Certificate generation. - Storage: the user must take steps to store the private key securely. Certificate Expiration Certificates are issued with a limited duration, as set by the CA policy for the certificate type. Root certificates might have long expiration dates (10+ years), whereas web server and user certificates might 1 year only. Certificate is renewed before it expires. Certificate Revocation Lists Certificate may be revoked or suspended by the owner or by the CA for many reasons. Revoked certificate: is no longer valid and cannot be "un-revoked" or reinstated. Suspended certificate: can be re-enabled. OpenSSL In a Windows environment, certificate infrastructure is installed and managed as Active Directory Certificate Services. There is a certutil tool for command line management, or you can use PowerShell. For Linux, CA services are typically implemented using the OpenSSL suite. 07- Implementing Authentication Controls 7.1- Summarize Authentication Design Concepts Identity and Access Management Access Control System: set of technical controls that govern how subjects may interact with objects. Subjects: users, devices, or software processes, or anything else that can request and be granted access to a resource. Objects: are the resources; these could be networks, servers, databases, files, and so on Identity and Access Management (IAM): system is usually described in terms of four main processes: - Identification: creating an account represents the user, device, or process on the network. - Authentication: proving that a subject is who or what it claims to be. - Authorization: determining what rights subjects should have on each resource. - Accounting: tracking authorized usage of a resource or use of rights by a subject. Authentication Factors Something You Know: Username and a password, PIN, Swipe patterns. Something You Have: smart card, fob, or wristband, hard tokens. Something You Are/Do: biometric factor such as a fingerprint, or behavioral identifiers, gait. Authentication Design Authentication design: refers to selecting a technology that meets requirements for CIA. Multifactor Authentication Multifactor authentication (MFA): combines the use of more than one type of knowledge, ownership, and biometric factor. Two-Factor Authentication (2FA). Three-factor authentication. 7.2- Implement Knowledge-Based Authentication Local, Network, And Remote Authentication Knowledge-based authentication relies on cryptographic hashes. When a user enters a password to log in, an authenticator converts what is typed into a hash and transmits that to an authority. The authority compares the submitted hash to the one in the database and authenticates the subject only if they match. Windows Authentication Windows local sign-in: The Local Security Authority (LSA) compares the submitted credential to a hash stored in the Security Accounts Manager (SAM) database, which is part of the registry. Windows network sign-in: the LSA can pass the credentials for authentication to a network service, The preferred system for network authentication is based on Kerberos, but legacy network applications might use NT LAN Manager (NTLM) authentication. Remote sign-in: if the user's device is not connected to the local network, authentication can take place over some type of virtual private network (VPN) or web portal. Linux Authentication local user account names are stored in /etc/passwd. When a user logs in to a local interactive shell, the password is checked against a hash stored in /etc/shadow. Interactive login over a network is typically accomplished using Secure Shell (SSH). Single Sign-On (SSO) Single Sign-On (SSO): system allows the user to authenticate once to a local device and be authenticated to compatible application servers without having to enter credentials again. In Windows, SSO is provided by the Kerberos framework. Kerberos Authentication Kerberos: is a single sign-on network authentication and authorization protocol used on many networks, notably as implemented by Microsoft's Active Directory (AD) service. Pap, Chap, And MS-Chap Authentication Password Authentication Protocol (PAP): used as the basic authentication mechanism in HTTP. Challenge Handshake Authentication Protocol (CHAP): encrypted challenge in a system called a three-way handshake. MS-CHAPv2: Microsoft's implementation of CHAP. Password Attacks Plaintext/Unencrypted Attacks: These protocols must not be used PAP, basic HTTP/FTP authentication, and Telnet. Online Attacks: threat actor interacts with the authentication service directly a web login form or VPN gateway. Offline Attack: means that the attacker has managed to obtain a database of password hashes. Brute-Force and Dictionary Attacks Brute-Force Attack: attempts every possible combination in the output space in order to match a captured hash and guess at the plaintext that generated it. Dictionary and Rainbow Table Attacks Dictionary attack: if there is a good chance of guessing the likely value of the plaintext, such as a non-complex password. The software generates hash values from a dictionary of plaintexts to try to match one to a captured hash. Rainbow table: the attacker uses a precomputed lookup table of all possible passwords and their matching hashes. The hash value of a stored password can then be looked up in the table and the corresponding plaintext discovered. Salt: add a random value to the stored plaintext helps to slow down rainbow table attacks. UNIX and Linux password storage mechanisms use salt, but Windows does not Hybrid Attack Hybrid Password Attack: uses a combination of attack methods when trying to crack a password. Like dictionary and brute force attacks. Password Crackers There are some Windows tools, including the infamous Cain and L0phtcrack (l0phtcrack.com) tools, most password crackers run primarily on Linux. For example, a tool such as Hashcat. 7.3- Summarize Biometrics Authentication Concepts Biometric Authentication The first step in setting up biometric authentication is enrollment. The chosen biometric information is scanned by a biometric reader and converted to binary information. Fingerprint Recognition Physiologic biometric features represent a something you are factor. Facial Recognition Facial recognition: records multiple indicators about the size and shape of the face, like the distance between each eye, or the width and length of the nose. Retinal Scan: one of the most accurate forms of biometrics. Iris Scanning: is the technology most likely to be rolled out for high-volume applications, such as airport security. Behavioral Technologies Voice Recognition: voice is also subject to impersonation. Gait Analysis: produces a template from human movement (locomotion). Signature Recognition. Typing. 08- Implementing Identity and Account Management Controls 8.1- Implement Identity and Account Types Identity Management Controls background check: determines that a person is who they say they are and are not concealing criminal activity, bankruptcy, or connections that would make them unsuitable or risky. Onboarding: IT and HR function will combine to create an account for the user to access the computer system, assign the appropriate privileges. NonDisclosure Agreement (NDA): when an employee signs an NDA, they are asserting that they will not share confidential information with a third party. Personnel Policies for Privilege Managements Separation of Duties: Duties and responsibilities should be divided among individuals to prevent ethical conflicts or abuse of powers. It can be compromised by insider threats. Least Privilege: means that a user is granted sufficient rights to perform his or her job and no more. Job Rotation: means that no one person is permitted to remain in the same job for an extended period. To ensure that it is not tied too firmly to any one individual also helps prevent abuse of power, reduces boredom, and enhances individuals professional skills. Mandatory Vacation: means that employees are forced to take their vacation time, help the corporate audit and security employees have time to investigate and discover any discrepancies in employee activity. Offboarding Policies Offboarding: process of ensuring that an employee leaves a company gracefully, disable the user account and privileges, retrieve mobile devices, keys, smart cards, USB media, wipe employee-owned devices of corporate data and application. Security Account Types and Credential Management Operating systems, network appliances, and network directory products use some standard account types as the basis of a privilege management system. These include standard user, administrative user, security group accounts, and service accounts and guest Accounts Security Group-Based Privileges Security Group Account: simplifies and centralizes the administrative process of assigning rights. Administrator/Root Accounts In Windows, this account is called Administrator; in Linux, it is called root. This type of account is also referred to as a superuser. Service Accounts Service Accounts: are used by scheduled processes and application server software, such as databases. Windows has several default service account types. These do not accept user interactive logons but can be used to run processes and background services: - System: has the most privileges of any Windows account, The local system account creates the host processes that start Windows before the user logs on, Any process created using the system account will have full privileges over the local computer. - Local Service: has the same privileges as the standard user account, It can only access network resources as an anonymous user. - Network Service: has the same privileges as the standard user account but can present the computer's account credentials when accessing network resources. 8.2- Implement Account Policies Account Attributes and Access Policies Security Identifier (SID): each User Account defined as SID and each account is associated with a profile. Access Policies: determine the right to log on for users Group Policy Objects (GPOs): configured access policies rights for user/group/role accounts such as on a Windows Active Directory. Account Password Policy Settings Password length Password complexity Password aging Password reuse and history Account Restrictions Location-Based Policies: A user or device can have a logical network location, identified by an IP address, subnet, virtual LAN (VLAN), or organizational unit (OU). Geofencing: Refers to accepting or rejecting access requests based on location. ACCOUNT AUDITS Accounting and auditing processes: are used to detect whether an account has been compromised or is being misused Account Lockout and Disablement If account misuse is detected or suspected, the account can be manually disabled by setting an account property. An account lockout means that login is prevented for a period. 09- Implementing Secure Network Designs 9.1- Implement Secure Network Designs Secure Network Designs Typical weaknesses include: - Single Points of Failure: relying on a single hardware server or appliance or network channel. - Lack of Documentation and Change Control: leading to a lack of visibility into how the network is constituted. - Overdependence on Perimeter Security: if the network architecture is "flat" (that is, if any host can contact any other host), penetrating the network edge gives the attacker freedom of movement. Network Appliances Switches. Wireless access points. Routers. Firewalls. Load balancers. Routing and Switching Protocols The basic function of a network is to forward traffic from one node to another. The forwarding function takes place at two different layers: - Layer 2 forwarding: occurs between nodes on the same local network segment. each node is identified by the network interface's hardware or Media Access Control (MAC) address. - Layer 3 forwarding or routing: nodes are identified by an Internet Protocol (IP). Address Resolution Protocol (ARP): The Address Resolution Protocol (ARP) maps a network interface's hardware (MAC) address to an IP address. Internet Protocol (IP): provides the addressing mechanism for logical networks and subnets. Network Topology and Zones Topology: is a description of how a computer network is physically or logically organized. Zone: is an area of the network where the security configuration is the same for all hosts within it. Traffic between zones should be strictly controlled using a security device, typically a firewall. The main zones are as follows: - Intranet (private network): this is a network of trusted hosts owned and controlled by the organization. - Extranet: this is a network of semi-trusted hosts, typically representing business partners, suppliers. - Internet/guest: this is a zone permitting anonymous access (or perhaps a mix of anonymous and authenticated access). Demilitarized Zones (DMZ) DMZ is also referred to as a perimeter or edge network. The basic principle of a DMZ is that traffic cannot pass directly through it. DMZ enables external clients to access data on private systems, such as web servers. If communication is required between hosts on either side of a DMZ, a host within the DMZ acts as a proxy. DMZ can be established using one router/firewall appliance with three network interfaces. One interface is the public one, another is the DMZ, and the third connects to the LAN. 9.2- Implement Secure Switching and Routing Man-In-The-Middle and Layer 2 Attacks Man-in-the-Middle (MITM) or On-Path Attacks: Attackers can take advantage of the lack of security, threat actor gains a position between two hosts, and transparently captures, monitors, and relays all communication between the hosts. MAC cloning, or MAC address spoofing: changes the hardware address configured on an adapter interface or asserts the use of an arbitrary MAC address. MAC flooding: The intention of the attacker is to exhaust the memory used to store the switch's MAC address table. The switch uses the MAC address table to determine which port to use to forward unicast traffic to its correct destination. Physical Port Security and Mac Filtering MAC Filtering: creating a list of valid MAC addresses on a switch to defining which MAC addresses are allowed. MAC Limiting: specifying a limit to the number of permitted addresses. Network Access Control Port-Based Network Access Control (PNAC): switch uses an AAA server to authenticate the attached device before activating the port. Route Security Routes between networks and subnets can be configured manually, but most routers automatically discover routes by communicating with each other. It is important that this traffic be separated from channels used for other types of data. 9.3- Implement Secure Wireless Infrastructure Wireless Network Installation The access points forward traffic to and from the wired switched network. Each WAP is identified by its MAC address, also referred to as its basic service set identifier (BSSID). Each wireless network is identified by its name, or service set identifier (SSID). Wireless networks can operate in either the 2.4 GHz or 5 GHz radio band. Each radio band is divided into a number of channels, and each WAP must be configured to use a specific channel. Site Surveys and Heat Maps: are used to measure signal strength and channel usage throughout the area to cover. Site survey starts with an architectural map of the site, with features that can cause background interference marked. These features include solid walls, reflective surfaces, motors, microwave ovens, and so on. The survey is performed with a Wi-Fi-enabled laptop or mobile device with Wi-Fi analyzer software installed. Controller and Access Point Wireless Controllers: centralized management and monitoring. A controller can be a hardware or a software. Rogue Access Points and Evil Twins Rogue Access Point: is one that has been installed on the network without authorization. Evil Twin: might just have a similar name (SSID) to the legitimate. Jamming Attacks Jamming Attacks: disrupted by interference from other radio sources. 9.4- Implement Load Balancers Distributed Denial of Service Attacks (DDOS) Most denial of service (DOS) attacks against websites and gateways are distributed DOS (DDoS). This means that the attack is launched from multiple hosts simultaneously. DDOS Attack Mitigation Stateful firewall can detect a DDoS attack and automatically block the source. Load Balancing Load Balancer: distributes client requests across available server nodes in a farm or pool. It can provide mitigation against DDoS attacks. And also provides fault tolerance There are two main types of load balancers: - Layer 4 load balancer: basic load balancers make forwarding decisions on IP address and TCP/UDP port values. - Layer 7 load balancer (content switch): as web applications have become more complex, modern load balancers need to be able to make forwarding decisions based on application level data, such as a request for a particular URL or data types like video or audio streaming, this requires more complex logic, but the processing power of modern appliances is sufficient to deal with this 10- Implementing Network Security Appliances 10.1- Implement Firewalls and Proxy Servers Packet Filtering Firewalls Access Control Lists (ACLs): A packet filtering firewall is configured by specifying a group of rules. A packet filtering firewall can inspect the headers of IP packets. Rules can be based on the information found in those headers: - IP filtering: accepting or denying traffic on the basis of its source and/or destination IP address. - Protocol ID/type: (TCP, UDP, ICMP, routing protocols, and so on). - Port filtering/security: accepting or denying a packet on the basis of source and destination port numbers. Ability to block some types of ICMP (ping) traffic but not others, or the ability to filter by hardware (MAC) address. Stateless Operation: A basic packet filtering firewall. means that it does not preserve information about network sessions. e Stateful Inspection Firewalls Stateful inspection firewall: tracking information about the session established between two hosts, or blocking malicious attempts to start a bogus session. Session data is stored in a state table. Firewall Implementation Firewall Appliances: is a stand-alone hardware firewall deployed to monitor traffic. Firewall appliance can be deployed in two ways: - Routed (layer 3) - Bridged (layer 2) Virtual Firewalls Virtual firewall can be implemented in three different ways: - Hypervisor-based: this means that filtering functionality is built into the hypervisor or cloud provisioning tool, You can use the cloud's web app or application programming interface (API) to write access control lists (ACLs) for traffic arriving or leaving a virtual host or virtual network. - Virtual appliance: this refers to deploying a vendor firewall appliance instance using virtualization, in the same way you might deploy a Windows or Linux guest OS. - Multiple context: this refers to multiple virtual firewall instances running on a hardware firewall appliance, Each context has a separate interface and can perform a distinct filtering role. 10.2- Implement Network Security Monitoring Network-Based Intrusion Detection Systems Intrusion Detection System (IDS): provide real-time analysis of either network traffic or system and application logs. Network-based IDS (NIDS): captures traffic and analyzes the packets to identify malicious traffic and displays alerts. A NIDS, such as Snort (snort.org), Suricata (suricata-ids.org), or Zeek/Bro (zeek.org) performs passive detection. Network-Based Intrusion Prevention Systems Intrusion Prevention System (IPS): can provide an active response to any network threats that it matches. There are several methods of formulating the ruleset. - Signature-based detection. - Behavioral-based detection. Signature-Based Detection Signature-based detection (or pattern-matching): means that the engine is loaded with a database of attack patterns or signatures. If traffic matches a pattern, then the engine generates an incident. The signatures and rules (often called plugins or feeds). Behavior and Anomaly-Based Detection Behavioral-based detection: means that the engine is trained to recognize baseline "normal" traffic or events. Anything that deviates from this baseline (outside a defined level of tolerance) generates an incident. The idea is that the software will be able to identify zero day attacks, insider threats, and other malicious activity for which there is no signature. This type of detection was provided by network behavior and anomaly detection (NBAD) products. NBAD: engine uses heuristics to generate a statistical model of what baseline normal traffic looks like. False Positive: is where legitimate behavior generates an alert. False Negative is: where malicious activity is not alerted. Next-Generation Firewalls Next-Generation Firewall (NGFW): combined application-aware filtering with user account-based filtering and the ability to act as an intrusion prevention system (IPS). Unified Threat Management (UTM) Unified threat management (UTM): refers to a security product that centralizes many types of security controls—firewall, anti-malware, network intrusion prevention, spam filtering, content filtering, data loss prevention, VPN, cloud access gateway into a single appliance. This means that you can monitor and manage the controls from a single console. Web Application Firewalls Web Application Firewall (WAF): is designed specifically to protect software running on web servers and their back-end databases from code injection and DOS attacks. WAF may be deployed as an appliance or as plug-in software for a web server platform. 10.3- Summarize The Use of SIEM Monitoring Services Packet Capture: Data captured from network sensors/sniffers plus netflow sources. Network Monitors: collects data about network appliances, such as switches, access points, routers, firewalls, and servers. This is used to monitor load status for CPU/memory, disk capacity, fan speeds/temperature, network link utilization/error. Another important function is a heartbeat message to indicate availability. This data might be collected using the Simple Network Management Protocol (SNMP) or proprietary management system. Logs: Logs are one of the most valuable sources of security information. Security Information and Event Management (SIME) Software designed to assist with managing security data inputs and provide reporting and alerting. The core function of a SIEM tool is to aggregate traffic data and logs. Security Orchestration, Automation, And Response (SOAR) The basis of SOAR is to scan the organization's store of security and threat intelligence, analyze it using machine/deep learning techniques, and then use that data to automate and provide data enrichment for the workflows that drive incident response and threat hunting. 11- Implementing Secure Network Protocols 11.1- Implement Secure Network Operations Network Address Allocation Dynamic Host Configuration Protocol (DHCP): provides an automatic method for network address allocation. DHCP starvation: is a type of DOS attack where a rogue client repeatedly requests new IP addresses using spoofed MAC addresses, with the aim of exhausting the IP address pool. Enabling the DHCP snooping port security feature on a switch can mitigate rogue DHCP attacks. Domain Name Resolution Domain Name System (DNS): resolves fully qualified domain names (FQDNs) to IP addresses. DNS poisoning: attack that compromises the process by which clients query name servers to locate the IP address for a FQDN. There are several ways that a DNS poisoning attack can be perpetrated: - Man in the Middle: attacker can use ARP poisoning to impersonate a legitimate DNS server and respond to DNS queries - DNS Client Cache Poisoning. - DNS Server Cache Poisoning. DNS Security DNS Security Extensions (DNSSEC): Help to mitigate against spoofing and poisoning attacks by providing a validation process for DNS responses. 11.2- Implement Secure Application Protocols Hypertext Transfer Protocol (HTTP) HTTP enables clients to request resources from an HTTP server. Transport Layer Security Secure Sockets Layer (SSL): the new version is Transport Layer Security (TLS) communications are secured. File Transfer Services File Transfer Protocol (FTP): file transfer but has no security mechanisms. SFTP: secure link is created between the client and server using Secure Shell (SSH) over TCP port 22. 11.3- Implement Secure Remote Access Protocols Remote Access Architecture most remote access is implemented as a virtual private network (VPN), running over the Internet. A VPN can also be deployed in a site-to-site model to connect two or more private networks. Remote Desktop Remote Desktop Protocol (RDP) can be used to access a physical machine on a one-to-one basis. Secure Shell Secure Shell (SSH) is the principal means of obtaining secure remote access to a command line terminal. The main uses of SSH are for remote administration and secure file transfer (SFTP). 12- Implementing Host Security Solutions 12.1- Implement Endpoint Security Hardening Hardening: process of putting an operating system or application in a secure configuration. Patch Management Automated vulnerability scanners can be effective at discovering missing patches for the operating system, plus a wide range of third-party software apps and devices. Endpoint Protection Antivirus (A-V)/Anti-Malware. Host-Based Intrusion Detection/Prevention (HIDS/HIPS). Endpoint Protection Platform (EPP): is a single agent performing multiple security tasks, including malware/intrusion detection and prevention. (say one for A-V, one for HIDS, another for host-based firewall, and so on). Data Loss Prevention (DLP): Many EPPs include a data loss prevention (DLP) agent. This is configured with policies to identify privileged files and strings that should be kept private or confidential, such as credit card numbers. The agent enforces the policy to prevent data from being copied or attached to a message without authorization. 13- Implementing Secure Mobile Solutions 13.1- Implement Mobile Device Management Mobile Device Deployment Models Bring your own device (BYOD): The mobile will have to meet whatever profile is required by the company and the employee will have to agree on the installation of corporate apps and to some level of oversight and auditing. Corporate owned, business only (COBO): property of the company and may only be used for company business. Corporate owned, personally-enabled (COPE): The employee may use it to access personal email and social media accounts. Choose your own device (CYOD): Much the same as COPE but the employee is given a choice of device from a list. Enterprise Mobility Management Enterprise Mobility Management (EMM): is a class of management software designed to apply security policies to the use of mobile devices and apps in the enterprise. There are two main functions of an EMM product suite: - Mobile Device Management (MDM)—sets device policies for authentication, feature use (camera and microphone), and connectivity, MDM can also allow device resets and remote wipes. - Mobile Application Management (MAM)—sets policies for apps that can process corporate data, and prevents data transfer to personal apps, This type of solution configures an enterprise-managed container or workspace Mobile Access Control Systems Remote Wipe Remote Wipe or Kill Switch: means that if the handset is stolen it can be set to the factory defaults or cleared of any personal data (sanitization). or wipe any plug-in memory cards too. Thief can prevent a remote wipe by ensuring the phone cannot connect to the network, then hacking the phone and disabling the security. Full Device Encryption and External Media All but the early versions of mobile device OSes for smartphones and tablets provide full device encryption. Location Services Geolocation: is the use of network attributes to identify (or estimate) the physical position of a device. Location services can make use of two systems: - Global Positioning System (GPS): a means of determining the device's latitude and longitude based on information received from satellites via a GPS sensor. - Indoor Positioning System (IPS): works out a device's location by triangulating its proximity to other radio sources, such as cell towers, Wi-Fi access points, and Bluetooth/RFID beacons. Rooting and Jailbreaking Rooting: some vendors provide authorized mechanisms for users to access the root account on their device Jailbreaking: term "jailbreaking" became popular for exploits that enabled the user to obtain root privileges Carrier unlocking: for either iOS or Android, this means removing the restrictions that lock a device to a single carrier. 14- Summarizing Secure Application Concepts 14.1- Analyze Indicators of Application Attacks Analyze Indicators of Application Attacks You must be able to identify indicators of arbitrary code execution and privilege escalation from your host monitoring and logging systems. Application Attacks Application attack targets a vulnerability in OS or application software. Privilege Escalation. Error Handling. Improper Input Handling. Overflow Vulnerabilities Overflow Attack: the threat actor submits input that is too large to be stored in a variable assigned by the application. Buffer Overflow: the attacker passes data that deliberately overfills the buffer. Buffer: is an area of memory that the application reserves to store expected data. One of the most common vulnerabilities is a stack overflow. Stack: is an area of memory used by a program subroutine. Memory Leaks and Resource Exhaustion Memory leaks: are particularly serious in service/background applications, consume memory over an extended period. Memory leak may itself be a sign of a malicious or corrupted process. Less memory is available to other processes and the system could crash. DLL Injection Dynamic link library (DLL): is a binary package that implements some sort of standard functionality, such as establishing a network connection or performing cryptography. DLL injection: is a vulnerability in the way the operating system allows one process to attach to another. 14.2- Analyze Indicators of Web Application Attacks Uniform Resource Locator Analysis Uniform Resource Locator (URL): can encode some action or data to submit to the server host. This is a common vector for malicious activity. Replay Attacks Token: The server normally gives it to the client. Cookie: new version of token, it created when the server sends an HTTP response header with the cookie data. Replay Attack: works by sniffing or guessing the token value and then submitting it to re-establish the session illegitimately. Session Hijacking Attackers can sniff network traffic to obtain session cookies sent over an unsecured network. Cross-Site Scripting (XSS) Run scripts within the user input fields on that device. This might be in a search field, or some other input field on the web page. Structured Query Language (SQL) Injection Threat actor modifies one or more functions by adding code to some input accepted by the app, causing it to execute the attacker's own set of SQL queries or parameters. 14.3- Summarize Secure Coding Practices Secure Coding Techniques Input Validation Secure Cookies 15- Implementing Secure Cloud Solutions 15.1- Summarize Secure Cloud and Virtualization Services Cloud Deployment Models Public. Private. Community. Cloud Service Models Infrastructure as a service (IaaS): is a means of provisioning IT resources such as servers, load balancers, and storage area. Software as a service (SaaS): is a different model of provisioning software applications. Platform as a service (PaaS): provides resources somewhere between SaaS and IaaS. Virtualization Technologies and Hypervisor Types Virtualization means that multiple operating systems can be installed and run simultaneously on a single computer. A virtual platform requires at least three components: - Host hardware: the platform that will host the virtual environment - Hypervisor/Virtual Machine Monitor (VMM): manages the virtual machine environment and facilitates interaction with the computer hardware and network. - Guest operating systems, Virtual Machines (VM), or instances: operating systems installed under the virtual environment. Virtual Desktop Infrastructure and Thin Clients Virtual desktop infrastructure (VDI): refers to using a VM as a means of provisioning corporate desktops. In a typical VDI, desktop computers are replaced by low-spec, low-power thin client computers. Virtual desktop environment(VDE): All application processing and data storage in the is performed by the server VDI. Container Container: new version of virtualization that have same idea of a hypervisor and but without need to install all resource of operating system. One of the best-known container virtualization products is Docker (docker.com). 15.2- Apply Cloud Security Solutions Cloud Security Controls Clouds use the same types of security controls as on-premises networks. High Availability One of the benefits of the cloud is the potential for providing services that are resilient to failures at different levels, such as component, server, local network, site, data center, and wide area network. High Availability (HA): refers to storage provisioned with a guarantee of 99.99% uptime or better. 16- Explaining Data Privacy and Protection Concepts 16.1- Explain Privacy and Data Sensitivity Concepts Privacy and Sensitive Data Concepts It is important not to solely judge how secretly it might need to be kept, but how the data is used within workflows. Data must be kept securely within a processing and storage system that enforces CIA attributes. Privacy Vs. Security Privacy: is a data governance requirement that arises when collecting and processing personal data. Security: controls of focus on the CIA attributes of the processing system. Data Governance Policy: describes the security controls that will be applied to protect data at each stage of its life cycle Data Roles and Responsibilities Data owner: a senior (executive) role with ultimate responsibility for maintaining CIA. Data steward : responsible for data quality, like ensuring data is labeled and identified with appropriate metadata. Data custodian: responsibility for enforcing access control, encryption, and backup/recovery measures. Data Privacy Officer (DPO): responsible for oversight of any personally identifiable information (PII). Data Classifications Data Classification: schema is a decision tree for applying one or more tags or labels to each data asset. Many data classification schemas are based on the degree of confidentiality required: - Public (unclassified): there are no restrictions on viewing the data. - Confidential (secret): the information is highly sensitive, for viewing only by approved persons within the owner. - Critical (top secret): the information is too valuable to allow any risk of its capture, Viewing is severely restricted. Another type of classification schema identifies the kind of information asset: - Proprietary: information created and owned by the company. - Private/personal data: information that relates to an individual identity. - Sensitive: Privacy-sensitive information about a person could harm them if made public. Data Types Personally Identifiable Information (PII): is data that can be used to identify, contact, or locate an individual. Social Security Number (SSN): is a good example of PII, date of birth, email address, telephone number Personal health information (PHI): refers to medical and insurance, plus associated hospital and laboratory test results. Financial Information: refers to data bank and investment accounts, plus information such as payroll and tax returns. The Payment Card Industry Data Security Standard (PCI DSS): defines the safe handling and storage of this information Government Data. Privacy Breaches and Data Breaches Data Breach: occurs when information is read, modified, or deleted without authorization. 16.2- Explain Privacy and Data Protection Controls Data Protection Data at rest: This state means that the data is in some sort of persistent storage media. Data in transit (or data in motion): This is the state when data is transmitted over a network. Data in use (or data in processing): present in volatile memory, such as system RAM or CPU. Data Exfiltration Data exfiltration: attackers retrieve valuable data, such as personally identifiable information (PII) or payment information. Data Loss Prevention Data loss prevention (DLP): enforce rules so that data is not viewed or transferred without authorization. 17- Performing Incident Response 17.1- Summarize Incident Response Procedures Incident Response Process Incident Response Policy: sets the resources, processes, and guidelines for dealing with security incidents. Incident management is vital to mitigating risk. The following are the principal stages in an incident response life cycle: - Preparation: hardening systems, writing policies and procedures, and setting up confidential lines of communication, It also implies creating incident response resources and procedures. - Identification: determine whether an incident has taken place, assess how severe it might be (triage), and notify stakeholders. - Containment: limit the scope and magnitude of the incident, the principal aim of incident response is to secure data while limiting the immediate impact on customers and business partners. - Eradication—once the incident is contained, remove the cause and restore the affected system to a secure state by applying secure configuration settings and installing patches. - Recovery: restoration of data from backup and security testing, Systems must be monitored more closely for a period to detect and prevent any reoccurrence of the attack. - Lessons learned: analyze the incident and responses to identify whether procedures or systems could be improved, it is imperative to document the incident. Cyber Incident Response Team Preparing for incident response means establishing the policies and procedures for dealing with security breaches and the personnel and resources to implement those policies. One of the first challenges lies in defining and categorizing types of incidents. Incident Response Plan incident response plan (IRP): lists the procedures, contacts, and resources available to responders for various incident categories. The CSIRT should develop profiles or scenarios of typical incidents (DDoS attack, virus/worm). Playbook (or Runbooks): is a data-driven standard operating procedure (SOP) to assist junior analysts in detecting and responding to specific cyber threat scenarios, such as phishing attempts, SQL injection data exfiltration. Cyber Kill Chain Attack Framework Threat Intelligence: Threat research provides insight into adversary tactics, techniques, and procedures (TTPs). Cyber Kill Chain: model of framework to understand the attackers steps and have 7 phases: 1- Reconnaissance 2- Weaponization 3- Delivery 4- Exploitation 5- Installation 6- Command and control (C2 or C&C 7- Actions on objectives Other Attack Frameworks MITRE ATT&CK: Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK), provide access to a database of known TTPs. Diamond Model of Intrusion Analysis: suggests a framework to analyze an intrusion event by exploring the relationships between four core features: adversary, capability, infrastructure, and victim. 17.2- Utilize Appropriate Data Sources for Incident Response Incident Identification Identification: is the process of collating events and determining whether any of them should be managed as incidents. Security Information and Event Management(SIME) SIEM: parses network traffic and log data from multiple sensors, appliances, and hosts and normalizes the information to standard field types. SIME Dashboards SIEM dashboard provides a console to work from for day-to-day incident response Logging Platforms Syslog: provides an open format, protocol, and server software for logging event messages. Journalctl: In Linux, text-based log files of the sort managed by syslog can be viewed using commands. NXlog: is an open-source log normalization tool. Network, Os, And Security Log Files System and Security Logs. Network Logs Authentication Logs Vulnerability Scan Output Application Log Files DNS Event Logs Web/HTTP Access Logs 17.3- Apply Mitigation Controls Incident Containment Containment techniques can be classed: 1- isolation-based: - Physical disconnect the host from the network completely (air gap). - Isolated using VLAN. - Disable user account. 2- Segmentation-based - DMZ. - Subnet. Incident Eradication and Recovery After an incident has been contained, you can apply mitigation techniques and controls to eradicate the intrusion tools and unauthorized configuration changes from your systems. you should also consider a recovery phase. Firewall Configuration Changes configuration change may mean the deployment of a new type of security control, or altering the settings of an existing control to make it more effective. 18- Explaining Digital Forensics 18.1- Explain Key Aspects of Digital Forensics Documentation Key Aspects of Digital Forensics Digital forensics: practice of collecting evidence from computer systems to a standard that will be accepted in a court of law. Latent: means that the evidence cannot be seen with the naked eye; rather, it must be interpreted using a machine or process. Digital Forensics Reports Digital Forensics Report: summarizes the significant contents of the digital data and the conclusions from the investigator's analysis. E-Discovery E-discovery: is a means of filtering the relevant evidence produced from all the data gathered by a forensic examination and storing it in a database in a format such that it can be used as evidence in a trial. Video and Witness Interviews Timelines Timeline: The visual representation of events happening in chronological order. Event Logs and Network Traffic 19- Summarizing Risk Management Concepts 19.1- Explain Risk Management Processes and Concepts Risk Management Processes Risk management: is a process for identifying, assessing, and mitigating vulnerabilities and threats to the essential functions that a business must perform to serve its customers. process as being performed over five phases: 1. Identify 2. Identify vulnerabilities 3. Identify threats 4. Analyze business impacts 5. Identify risk response Risk Types External: such as fire. Internal: such as assets and workflows that are owned and managed by your organization. Multiparty: such as supplier relationships. Intellectual Property (IP) Theft Software Compliance/Licensing Legacy Systems There are methods to performing risk analysis to evaluate likelihood and impact: quantitative and qualitative Quantitative Risk Assessment Quantitative: risk assessment aims to assign concrete values to each risk factor. - Single Loss Expectancy (SLE): the amount that would be lost in a single occurrence of the risk factor, This is determined by multiplying the value of the asset by an Exposure Factor (EF), EF is the percentage of the asset value that would be lost. - Annualized Rate of Occurrence (ARO): how many times of occurrence in a year. - Annualized Loss Expectancy (ALE): the amount that would be lost over the course of a year. This is determined by multiplying the SLE by the ARO Qualitative Risk Assessment Qualitative: risk assessment focused on identifying significant risk factors. Risk Avoidance + Risk Transference and Risk Acceptance Avoidance: Means that you stop doing the activity that is risk-bearing. For Example: a company may develop an in-house application for managing inventory and then try to sell it. Transference (or sharing): Means assigning risk to a third party, such as an insurance company or a contract with a supplier that defines liabilities. Risk Acceptance(or tolerance): means that no countermeasures are put in place either because the level of risk does not justify the cost or because there will be unavoidable delay before the countermeasures are deployed. 19.2- Explain Business Impact Analysis (Bia) Concepts Business Impact Analysis Business impact analysis (BIA): Is the process of assessing what losses might occur for a range of threat scenarios. for example: The likelihood of a DOS attack can be assessed on an annualized basis to determine annualized impact, in terms of costs. Mission Essential Functions Maximum tolerable downtime (MTD): Is the longest period of time that a business function outage may occur for without causing irrecoverable business failure. Recovery time objective (RTO): Is the period following a disaster that an individual IT system may remain offline. Work Recovery Time (WRT): Following systems recovery, there may be additional work to reintegrate different systems. Single Points of Failure Single Points of Failure (SPOF): one firewall, one server, one hard disk. should be use redundancy. Mean time to failure (MTTF): determine if the assets are non-repairable. Mean time between failures (MTBF): determine if the assets are repairable. Mean time to repair (MTTR): measure of the time taken to correct a fault so that the system is restored to full operation. Disasters Disaster: is an event that could threaten mission essential functions. Disaster Recovery Plans Disaster recovery plans (DRPs): describe the specific procedures to follow to recover a system or site to a working state following a disaster-level event. The DRP should accomplish the following: 1. Identify scenarios for natural and non-natural disaster and options for protecting systems. 2. Identify tasks, resources, and responsibilities for responding to a disaster. 3. Train staff in the disaster planning procedures and how to react well to change 20- Implementing Cybersecurity Resilience 20.1- Implement Redundancy Strategies High Availability High Availability: One of the key properties of a resilient system. Availability: is the percentage of time that the system is online, measured over the defined period, typically one year Power Redundancy All types of computer systems require a stable power supply to operate. Network Redundancy Network Interface Card (NIC) Teaming or adapter teaming: means that the server is installed with multiple NICs, or NICs with multiple ports, or both. Load Balancers: A load balancing switch distributes workloads between available servers. Disk Redundancy When a storage system is configured as a Redundant Array of Independent Disks (RAID), many disks can act as backups for each other to increase reliability and fault tolerance. 20.2- Implement Backup Strategies Backups Backups are kept back to certain points in time. Backup Types Full: full back up. Incremental: backup only includes files changed during the full back up. Differential: backup includes all files changed since the last full backup. 21- Explaining Physical Security 21.1- Explain The Importance of Physical Site Security Controls Physical Security Controls Physical Access Controls: are security measures that restrict and monitor access to specific physical areas or assets. Site Layout, Fencing, And Lighting Barricades and Entry/Exit Points. Fencing. Lighting Gateways and Locks Secure Gateway will normally be self-closing and self-locking, rather than depending on the user to close and lock it. Lock types can be categorized as follows: - Physical - Electronic - Mantraps Alarm Systems Circuit alarm Motion detection alarm Noise detection alarm Security Guards and Cameras Human security guards armed or unarmed, can be placed in front of and around a location to protect it. CCTV (closed circuit television) is a cheaper means of providing surveillance than maintaining separate guards at each gateway or zone. 21.2- Explain The Importance of Physical Host Security Controls Secure Areas safe vault Secure Data Destruction Data Sanitization Tools Overwriting: The standard method of sanitizing an HDD.