IT(Information Technology) – A Level
2023-24 (9626)
Communication Technology
CONTENTS
1
Digital Currencies
1
Digital Currencies
2
Data Mining
2
Data Mining
3
Social Networking Services
3
Social Networking Services
4
The Impact of IT
4
The Impact of IT
5
Tech. Enhanced Learning
5
Tech. Enhanced Learning
Communication
Technology
NETWORK
What is Computer Network/Network?
A computer network is a set of inter-connected computers (nodes)
that sharing data and hardware resources located on or provided
by network nodes. Computers use common communication
protocols over digital interconnections to communicate with each
other.
Advantages of Computer Network:
➢ Can setup communication more effectively like using emails.
➢ Can share hardware resources and applications in better way.
➢ Can share data/file over the network in fastest rate with ease.
➢ Can access devices remotely.
NIC CARD
What is NIC (Network Interface CARD)?
A network interface card (NIC) is a hardware component without which a
computer cannot be connected over a network. It is a circuit board installed in a
computer that provides a dedicated network connection to the computer. It is
also called network interface controller, network adapter, or LAN adapter.
Purpose:
•NIC allows both wired and wireless communications.
•NIC allows communications between computers connected via local area
network (LAN) as well as communications over large-scale network through
Internet Protocol (IP).
•NIC is both a physical layer and a data link layer device, i.e. it provides the
necessary hardware circuitry so that the physical layer processes and some data
link layer processes can run on it.
IP ADDRESS
An IP address is a unique address (numerical label) that identifies a device on the internet or a local network.
IP stands for "Internet Protocol," which is the set of protocols (rules) governing the format of data sent via the
internet or local network.
Note: The IP address is a 32-bit number that uniquely identifies a network interface on a machine. An IP
address is typically written in decimal digits, formatted as four 8-bit fields separated by periods. Each 8-bit field
represents a byte of the IP address.
An IP address serves two main functions: network interface identification, and location addressing.
❑ It identifies the host, or more specifically its network interface, and it provides the location of the host in
the network, and thus the capability of establishing a path to that host.
❑ Its role has been characterized as follows: "A name indicates what we seek. An address indicates where it
is. A route indicates how to get there. "The header of each IP packet contains the IP address of the sending
host and that of the destination host.
MAC ADDRESS
What is MAC (Media Access Control) Address?
MAC Addresses are unique 48-bit (12 digit hexadecimal number) hardware number of a
computer, that is assigned into a network card (known as a Network Interface
Card during manufacturing. The MAC Address is also known as the Physical Address of a
network device.
Hyphen-Hexadecimal notation: 00-1s-99-f1-d2-4f
The first 24 bits (or three octets) are used as the Organization Unique Identifier (OUI),
and 24 bits are vendor-specific and assigned to and burned into the NIC.
For instance, here are the OUIs from a couple of popular vendors:
Cisco: CC:46:D6
Google: 3C:5A:B4
Hewlett Packard: 3C:D9:2B
Data Packets
Data packets: In networking, a packet is a small segment of a larger message. Data sent over computer networks, such as
the Internet, is divided into packets. These packets are then recombined by the computer or device that receives them.
Internet is a "packet switching" network. Packet switching refers to the ability of networking equipment to process packets
independently from each other.
What is a packet header?
A packet header is a "label" of sorts, which provides information about the packet’s contents (payload), origin (host), and
destination IP (version) address (IP address is like computer’s mailing address).
What is an IP packet?
IP (Internet Protocol) is a network layer protocol that has to do with routing. It is used to make sure packets arrive at the
correct destination. A packet with an IP header can be referred to as an "IP packet." An IP header contains important
information about where a packet is from (its source IP address), where it is going (destination IP address), how large the
packet is, and how long network routers should continue to forward the packet before dropping it.
HUB DEVICE
Hub is a device in a network, that plays a vital role in data transmission, and
broadcasting. Hub is a hardware device used at the physical layer to connect multiple
devices in the network. Hubs are widely used to connect LANs. A hub has multiple
ports and it is a non-intelligent device. A hub cannot filter the data, i.e. it cannot
identify the destination of the packet, so it broadcasts or send the message to each
port. This is why it is known as a non-intelligent or dumb device. Hub does not have
any routing table to store the data of ports and map destination addresses., the
routing table is used to send/broadcast information across all the ports.
Types of Network Hubs: Networks hubs are of the following three types:
Active Hub:
Passive Hub
Intelligent Hub:
REPEATER
What Does Repeater Mean?
A repeater is a network device that retransmits a received signal with
more power and to an extended geographical or topological network
boundary than what would be capable with the original signal.
Repeaters were introduced in wired data communication networks
due to the limitation of a signal in propagating over a longer distance
and now are a common installation in wireless networks for
expanding cell size. Repeaters are also known as signal boosters.
Note: This is necessary when long cable lengths are required
(typically over 100 m) and the signal would not be strong enough to
reach the destination on its own.
SWITCH DEVICE
The Switch is a network device that is used to segment the networks into different subnetworks
called subnets or LAN segments. It is responsible for filtering and forwarding the packets
between LAN segments based on MAC address. They connect devices in a network and use
packet switching to send, receive or forward data packets or data frames over the network.
Features of Network Switches
•It operates in Data Link Layer in OSI Model.
•It performs error checking before forwarding data.
•It transfers the data only to the device that has been addressed.
•It operates in full duplex mode.
•It allocates each LAN segment a limited bandwidth.
•It uses Unicast (one-to-one), multicast (one-to-many), and broadcast (one-to-all) transmission
modes.
•Packet Switching techniques are used to transfer data packets from source to destination.
•Switches have a more significant number of ports.
HUB Advantages and Disadvantages
Advantages of Hub
•It provides support for different types of Network Media.
•It can be used by anyone as it is very cheap.
•It can easily connect many different media types.
•The use of a hub does not impact on the network performance.
•Additionally, it can expand the total distance of the network.
Disadvantages of Hub
•It has no ability to choose the best path of the network.
•It does not include mechanisms such as collision detection.
•It does not operate in full-duplex mode and cannot be divided into the Segment.
•It cannot reduce the network traffic as it has no mechanism.
•It is not able to filter the information as it transmits packets to all the connected segments.
•Furthermore, it is not capable of connecting various network architectures like a ring, token, and ethernet, and
more
WAP (Wireless Access Point)
What is a wireless access point?
A wireless access point (wireless AP) is a network device that transmits and receives data over a wireless local
area network (WLAN), serving as the interconnection point between the WLAN and a fixed wire network
❑ It is simpler and easier to install WAPs to connect all the computers or devices in your network than to use
wires and cables.
❑ It uses radio waves at frequencies of 2.4GHz or 5 GHz to transmit data. A wireless access point is usually
connected to a switch by a cable, although it is possible in the home to have a combined wireless access
point/switch/router.
Why use a WAP to set up a wireless network?
Using a WAP lets you create a wireless network within your existing wired network, so you can accommodate
wireless devices.
WAP (Wireless access Point)
TASK
1.Write the differences between HUB and SWITCH.
2.Write Advantages and disadvantages of SWITCH.
ROUTER
What is a router?
A Router is a networking device that forwards data packets between computer
networks. It connects two or more packet-switched networks or subnetworks.
By sending data packets to their intended IP addresses, it manages traffic
between different networks and permits several devices to share an Internet
connection It serves two primary functions: managing traffic between these
networks by forwarding data packets to their intended IP addresses, and
allowing multiple devices to use the same Internet connection.
There
are
some
popular
companies
that
are Cisco, 3Com, HP, Juniper, D-Link, Nortel, etc.
develop
routers;
such
ROUTER
Working of Router:
Consider a router as an air traffic controller, and consider data packets as planes flying to various airports (or
networks). Each packet must be directed as quickly as possible to its destination, just as each plane has a distinct
destination and travels a distinct route. A router assists in guiding data packets to their intended IP address, just like an
air traffic controller ensures that aircraft reach their destinations without getting lost or experiencing significant
disruptions in a route.
An internal routing table, which is a list of routes to different network destinations, is used by a router to effectively
direct packets. In order to determine the destination of a packet, the router first scans its header. Then, it consults the
routing table. Forward packet to next packet.
Advantages of Router
Advantages:
❑ Eases connections: Sharing a single network connection among numerous machines is the router’s main job.
❑ Security: Undoubtedly, installing a router is the first step in securing a network connection.
❑ Supports dynamic routing: The router employs dynamic routing strategies to aid in network communication.
❑ Filtering Of Packets: Switching between packets and filtering packets are two more router services.
❑ Integrations: Routers can be integrated with modems to create a wireless access point for multiple devices in a
micro-environment. You can also install a VPN on your router for a more secure and private internet connection.
❑ Offers good backup plan: If one of your external network components fails, routers will use replacement
components to avoid traffic flow problems. This works well for large businesses where constant traffic is essential
for operation.
Disadvantages of Router
•Slower: Routers analyze multiple layers of information, from the physical layer to the network layer, which slows down
connections.
•High Cost: They are more expensive than some other tools for systems administration.
•Need for configuration: The router must be properly configured to work properly.
•Quality Issues: The time transitions are not always accurate.
•Bandwidth shortages: It consuming a lot of bandwidth. This leads to a bandwidth shortage that significantly slows down
the internet connection between connected devices.
•Frequent disconnections: A major problem that most router users face is frequent disconnections, To keep your router in
good working order, you also need to update its firmware and settings regularly.
Gateway
•A gateway is a network node that forms a passage between two networks operating with
different transmission protocols. Gateways The most common type of gateways, the
network gateway operates at layer 3, i.e. network layer of the OSI (open systems
interconnection) model. However, depending upon the functionality, a gateway can operate
at any of the seven layers of OSI model. It acts as the entry – exit point for a network since
all traffic that flows across the networks should pass through the gateway. Only the internal
traffic between the nodes of a LAN does not pass through the gateway.
Features of Gateway:
❖ Gateway is located at the boundary of a network and manages all data that inflows or
outflows from that network.
❖ It forms a passage between two different networks operating with different transmission
protocols.
❖ A gateway operates as a protocol converter, providing compatibility between the
different protocols used in the two different networks.
❖ It uses packet switching technique to transmit data across the networks.
Gateway
Difference Between Router and Gateway
It is capable of dynamic routing.
It's a piece of hardware that's in charge of receiving,
processing, and forwarding data packets to other
networks.
The OSI model's layer 3 and layer 4 are used by routers.
It is not capable of dynamic routing.
It is a gadget that allows networks with various protocols
to communicate with one another.
The OSI model's layer 5 is where a gateway functions.
A router's primary job is to transport traffic from one A gateway's primary role is to convert one protocol to
network to another.
It is only available in specialized applications.
A router's main function is to store routing information
for various networks and route traffic based on the
destination.
another.
Dedicated apps, physical servers, or virtual applications
are used to host it.
A gateway's main function is to distinguish between what
is within and what is outside the network.
Bridge Device
Bridge in Computer Network:
A bridge in a computer network is a device used to connect multiple LANs together with
a larger Local Area Network (LAN). The mechanism of network aggregation is known as
bridging. The bridge is a physical or hardware device but operates at the OSI model’s
data link layer and is also known as a layer of two switches.
Basically, a bridge in computer networks is used to divide network connections into
sections, now each section has separate bandwidth and a separate collision domain.
Here bridge is used to improve network performance.
Functions of Bridges
❖ Store MAC address in PC that is used in the network for reducing network traffic.
❖ Divide local area networks into multiple segments.
❖ Connects multiple networks to ensure communication between them.
❖ Connects LAN segments into a single network.
❖ Recognizes areas where data is to be sent and on which device it will be sent.
❖ Maintains MAC address table to discover new segments.
❖ Used in load filtering of network traffic by separating it into segments or packets.
Bridge
Advantages:
•Bridges can be used as a network extension like they can connect two network topologies together.
•It has a separate collision domain, which results in increased bandwidth.
•It can create a buffer when different MAC protocols are there for different segments.
•Highly reliable and maintainable. The network can be divided into multiple LAN segments.
•Simple installation, no requirement of any extra hardware or software except the bridge itself.
•Protocol transparency is higher as compared to other protocols.
Disadvantages:
•Expensive as compared to hubs and repeaters.
•Slow in speed.
•Poor performance as additional processing is required to view the MAC address of the device on the network.
•As the traffic received is in bulk or is broadcasted traffic, individual filtering of data is not possible.
•During the broadcasting of data, the network has high broadcast traffic and broadcast storms can be formed.
A bridge in a computer network is a device used to connect
multiple LANs together with a larger Local Area Network (LAN).
The mechanism of network aggregation is known as bridging.
The bridge is a physical or hardware device but operates at the
OSI model's data link layer and is also known as a layer of two
switches.
Firewall in Computer Network
A Firewall is a network security device that monitors and filters incoming and outgoing
network traffic based on an organization's previously established security policies. At its most
basic, a firewall is essentially the barrier that sits between a private internal network and the
public Internet.
Firewall prevents external users gaining un authorized access to a computer system. Itis
usually positioned at the gateway to a network and will examine all incoming data to
determine if it should be allowed. Data that is not allowed will be prevented from gaining
access to the network. A firewall can also prevent certain types of data from exiting a
network. As well as preventing unauthorized users from gaining access, a firewall can
prevent malicious data packets from causing disruption to a computer system such as a
denial of service (DOS) attack A proxy server would sit between the gateway and the LAN so
that data cannot passthrough to the network without being examined by its firewall software.
Firewall software can also be installed on individual computers in order to prevent any
unauthorized access or malicious attack from within a network.
Note: Firewalls have existed since the late 1980’s and started out as packet filters, which were
networks set up to examine packets, or bytes, transferred between computers.
SWITCHING TECHNIQUES
Switching techniques
❑ In large networks, there can be multiple paths from sender to receiver. The switching technique will decide the best
route for data transmission.
❑ It is the process of exchanging information between two communication devices.
❑ Switching technique is used to connect the systems for making one-to-one communication.
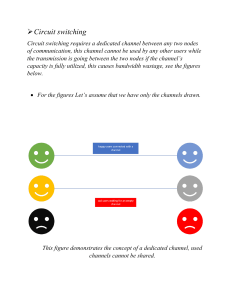
CIRCUIT SWITCHING
❑ Circuit Switching is a connection-oriented service that uses a dedicated path from the
sender to the receiver. Before sending any data from the source to the destination, it
needs to set up an end-to-end path.
❑ Circuit switching has the minimum chance of data loss due to the dedicated circuit
path, but a lot of bandwidth is wasted as a path cannot be used by other senders
during a congestion.
❑ A complete end-to-end path must exist before the communication takes place.
❑ In case of circuit switching technique, when any user wants to send the data, voice,
video, a request signal is sent to the receiver then the receiver sends back the
acknowledgment to ensure the availability of the dedicated path. After receiving the
acknowledgment, dedicated path transfers the data.
❑ Circuit switching is used in public telephone network. It is used for voice transmission.
Terms: Dedicated connections, Contiguous flow, Out of Flow (in-order), No headers
Efficiency less (resources reserved), delay less
Not suitable for computer network like to work on sending email, data etc.
Telephone system network is one of the example of Circuit switching.
CIRCUIT SWITCHING
Circuit switching has 3 phases:
❑ Circuit Establishment − A dedicated circuit is established between the two end-devices or from the source to the destination
using the number of intermediate switching center offices. The sender from the source side and the receiver from the destination
side transmit communication signals to request and ACK of circuit’s establishment.
❑ Data Transfer − After a dedicated connection is established from the source to the destination. Data and voice are traveled from
the source to the destination. This connection remains till the communication is the end.
❑ Disconnect the circuit − when the data transfer is completed, the circuit disconnects the connection.
Following are the advantages of using circuit switching −
❑ Circuit switching uses a dedicated path exists for the data to travel from source to destination.
❑ It has no waiting time at any switch and the data is transmitted without any delay.
❑ Data always reaches the other end in order means reordering not required.
Following are the disadvantages of using circuit switching −
❑ The channel is blocked after the communication is ended.
❑ It needs a long time to establish the connection from the source to the destination.
❑ More bandwidth is required for the dedicated channels.
CIRCUIT SWITCHING
1.
A local telephone network is an example of a _____________network.
a) Packet switched
b) Circuit switched
c) Bit switched
d) Line switched
2. The required resources for communication between end systems are reserved for the duration of the session between end
systems in ________ method.
a) Packet switching
b) Circuit switching
c) Line switching
d) Frequency switching
PACKET SWITCHING
❑ The packet switching is a switching technique in which the message is sent in
one go, but it is divided into smaller pieces, and they are sent individually.
❑ The message splits into smaller pieces known as packets and packets are
given a unique number to identify their order at the receiving end.
❑ Every packet contains some information in its headers such as source
address, destination address and sequence number.
❑ Packets will travel across the network, taking the shortest path as possible.
❑ All the packets are reassembled at the receiving end in correct order.
❑ If any packet is missing or corrupted, then the message will be sent to resend
the message.
❑ If the correct order of the packets is reached, then the acknowledgment
message will be sent.
Terms: Data Link Layer, Network Layer, store and forward, Pipelining used,
Efficiency, Delay
MESSAGE SWITCHING
Message Switching
❑ Message Switching is a switching technique in which a message is transferred as a
complete unit and routed through intermediate nodes at which it is stored and
forwarded.
❑ In Message Switching technique, there is no establishment of a dedicated path between
the sender and receiver.
❑ The destination address is appended to the message. Message Switching provides a
dynamic routing as the message is routed through the intermediate nodes based on the
information available in the message.
❑ Message switches are programmed in such a way so that they can provide the most
efficient routes.
❑ Each and every node stores the entire message and then forward it to the next node.
This type of network is known as store and forward network.
❑ Message switching treats each message as an independent entity.
MESSAGE SWITCHING
Advantages Of Message Switching
❑ In message switching, the data channels are shared by the network devices.
❑ It makes traffic management efficient by assigning priorities to the messages.
❑ Because the messages are delivered via a store and forward method, it is possible to include
priority in them.
❑ Unlike circuit switching, it does not necessitate the actual connection of source and destination
devices.
Disadvantages of Message Switching:
❑ Message switching cannot be used for real-time applications as storing messages causes delay.
❑ In message switching, the message has to be stored for which every intermediate device in the
network requires a large storing capacity.
❑ There is uncertainty whether or not messages are correctly conveyed. This could cause
problems in social relationships.
❑ The type of message switching does not create a dedicated path between the devices. It is not
dependable communication because there is no direct relationship between sender and
receiver.
SERVER TYPES
Servers: A server is a computer on a network which provides resources that can be
used by client devices. Individual servers or groups of servers can perform a variety of
functions depending on how they are configured.
❑ File Server: A file server's role is to make files available for users on the network.
These files might be for individuals who have access to their own user area for file
storage or they may be files that are shared between groups of users depending on
the permissions given to each user or group of users, files can be created, read,
modified and deleted.
❑ Print Server: Print server deals with all the print jobs on a network each time a
client computer sends a request for printing, it will be added to the queue on the
print server. The print server will then deliver each print job in turn to the printer.
There may be several printers that are managed by the print server. Some client
computers or users may be given priority and so may be able to jump the queue. t's
also possible for the print server to charge users for each print Job, which is usually
done by reducing the number of print credits available to the user.
Bandwidth
Network bandwidth is a measurement indicating the maximum capacity of a wired or
wireless communications link to transmit data over a network connection in a given
amount of time. Typically, bandwidth is represented in the number of bits, kilobits,
megabits or gigabits that can be transmitted in 1 second.
Bandwidth measures the range of frequencies available on a communications channel.
This defines its capacity. Bandwidth is measured as a frequency range in
kilohertz(kHz) or as a transmission rate in bits per second bps. Although the
bandwidth is often thought of a5 a speed, it’s actually the number of bits per second
that the line is capable of transmitting, rather than the actual speed of transmission. It
is therefore the maximum possible speed of data transfer. The transmission speed is
often referred to as the bit rate
Bit Streaming
A Bit stream is a series of bits which represent a stream of data transmitted at one time. Although it
usually refers to communications, it can also apply to data in memory or storage. In networking, streaming
takes place when video or audio files are sent to a receiving device for viewing or listening to without
downloading a file to save in storage. With a video, the first few seconds consisting of several frames will be
sent to it a buffer (a temporary area of storage) which can then be watched at the receiving device. As the
frames within the buffer are viewed, they are removed so that more frames can be added to the buffer to
keep it full. A buffer is used to keep the video running smoothly. Without a buffer, any data congestion
would be noticed by the video pausing, missing out frames or pixelating until the full transmission rate was
available again, even if it was only for a split second. It's still possible that a buffer could be fully used during
data congestion but it is much less likely than if a buffer was not present. Data congestion can be caused by
devices on the same network using up so much bandwidth that there isn’t enough eft for the full video
transmission or a similar situation at the sending end of the transmission. The same situation regarding
buffering applies to audio streaming as t does to video streaming, This is not just used for video and audio
streamed on demand but also when streamed live, for example when watching a sporting event or live news.
This means that live events that are streamed are actually delayed by the size of the buffer. This is why you
could be watching a rugby match on television and see try being scored before you see it on a live stream
Optical Fibre Cable
A fiber optic cable is a network cable that contains strands of glass fibers inside an insulated
casing. They're designed for long-distance, high-performance data networking, and
telecommunications. Compared to wired cables, fiber optic cables provide higher bandwidth
and transmit data over longer distances. Fiber optic cables support much of the world's internet,
cable television, and telephone systems.
Because they suffer hardly any degradation of signal, they can be used over large distances,
including in LANs where copper cable limits are typically 100m. They are also used n aircraft
where weight is an important factor, because the yare lighter than copper cables. The lack of
degradation of signal means that they are suitable for passing data across the globe as well as
throughout towns and cities. ISPs often use a method called fibre to the cabinet (FTTC) to provide
internet connectivity to homes. With FTTC, fibre optics are used to connect a communications
exchange to a cabinet in the street and the last portion of the connection to the house is by
copper cable. In the UK in 2015, Virgin Media were able to offer bandwidths of200Mbps using this
method.
Note: Fiber optic cables carry communication signals using pulses of light generated by small
lasers or light-emitting diodes.
Infrared
Infrared is the communication method used by most remote control devices. It is cheap to produce and a well
recognized standard method of transmitting simple commands. It works by transmitting electromagnetic radiation
that is just past the red end of the visible light spectrum, so it cannot be seen by the human eye. It does not have a
very high bandwidth and so only suitable for transmitting small amounts of data. It can also be affected by sunlight,
meaning that the transmission of data is not always successful. Infrared requires line of sight between the sending
and receiving devices so it cannot bend around corners but it can reflect off light surfaces. Infrared will only work for
short distances. Infrared can also be used by mobile phone devices to act as a remote control and is used within
active sensors.
Laser
Laser is an intense beam of light that can be used to transmit data. Like infrared, line of sight is
necessary, but, unlike infrared, laser beams can cover large distances. Laser still travels at the speed
of light, built does not require a physical connection like fiber optics. Lasers can be used to connect
LAN between buildings. They are suitable for this because very few data packets are lost as there is
little interference in normal atmospheric conditions, although adverse condition scan cause some
interference. Laser communications are quick to set up and can be portable, making them suitable for
live events such as sports and music concerts, The military use lasers to transmit live video from aircraft
because the video feed will arrive n real time because itis travelling at the speed of light. Laser beams
tend to be secure because they are narrow and aimed directly from sender to receiver, meaning that to
intercept the transmission would mean interrupting it, which would alert the sender and receiver.
Wireless communication/transmission Methods
Bluetooth is a wireless communication method used for the transfer of data between devices. It uses wireless frequencies
between 2402 and 2480 MHz. Bluetooth splits transmission data into packets which can be transmitted on 1 of 79 channels, each
with a bandwidth of 1MHz. It is typically used within mobile phone devices to connect to a range of equipment including:
❑ A cars audio system for handsfree communication
❑ A headset for hands-free communication.
❑ Communicating with a Bluetooth enabled smart watches, so that some of the phone's features can be used on the watch
❑ Sending and receiving data to and from devices that measure biometric data, such as heart rates.
❑ Streaming videos to a larger display screen.
❑ Streaming music to Bluetooth speakers.
❑ Transferring files from one phone to another phone or other Bluetooth connected device.
Bluetooth can also be used to network devices together in a small area as long as a high bandwidth is not required.
Wireless communication/transmission Methods
Wi-Fi is a wireless communication method. It operates in the 2.4 GHz and 5GHz frequencies. There have been many Wi-Fi
standards that have evolved over the years and they are all referred to by the number 802.11 followed by a letter. These letters
have included a, b, n and, in 2015, ac was introduced. Devices supporting aversion are backwardly compatible with devices that
support previous versions, but the communication will be limited to the highest common version the two devices support. The
802.11ac standard supports speeds of up to 1.3Gbps,compared to just 450 Mbps (045 Gbps) on the previous802.11n standard,
These are theoretical maximums and don't reflect the actual maximum speeds that are experienced in practice, which were around
150 Mbps and 300 Mbps respectively. Another big advantage of 802.11 ac over 802.11n is that it uses the 5 GHz wireless spectrum
rather than the 2.4 GHz spectrum used by802.110. The 24 GHz spectrum was very crowded because in urban areas there can be
several wireless access points overlapping, as well as other wireless devices such as baby monitors, smart home equipment and even
microwaves which cause interference and therefore reduce the connection speed.
Wireless communication/transmission Methods
Wi-Fi is used for a range of applications including
❑ Connection of portable devices such as laptops, tablets and mobile phones to a network, which could be a corporate LAN, a home LAN or a wireless
hotspot.
❑ Smart’ televisions which use services from the internet and so require a connection to a LAN that is connected to the internet
❑ Printers that can be located anywhere in a room, without that having to run additional cables.
❑ Casting of a devices screen to another device wirelessly. Typically this could be casting a laptop's display to a projector or casting a mobile phone's
display to a television
❑ Smart home devices.
The main advantage of Wi-Fi is that devices can connect to a LAN without the need for cables which can be costly to install, unsightly and a potential
hazard. This means devices can use any location where Wi-Fi access is available. Line of sight is not required and the international Wi-Fi standards
mean that any compatible device can connect. Mobile phones which usually rely on fourth generation (46)for data can connect to Wi-Fi networks for
internet access, which will save the user money and allow for larger amounts of data to be downloaded. Connection speeds are not massively smaller
than wired connections, meaning that data can be transferred quickly. However, the range offered by Wi-Fi is restricted by distance and objects. The
connection speed is dependent on the bandwidth available and the number of devices that are using the Wi-Fi connection at the same time. Security is
a potential issue because a hacker does not need to make a physical connection to a network in order to gain access and so it is necessary to ensure
that sufficient encryption is in place with a secure key.
Wireless communication/transmission Methods
The importance of bandwidth and bit rate when transmitting data
The importance of bandwidth and bit rate when transmitting data:
Bandwidth governs the maximum speed that data can be transferred; the bit rate is the actual transmission speed. They
are therefore important to consider when large amounts of data need to be transferred in a short amount of time. There
are two main scenarios when bandwidth is important
❑ Accessing content within a time limit
❑ Accessing content in real time
If a user wants to download a large file then the higher the bandwidth the quicker it will be to download. However,
bandwidth and bit rate are only important if it is important to download that file within a specific time limit for example,
if a user needs to download 50 Mb high quality photograph but doesn't need to view it until several minutes later, then
bandwidth may not be a major issue. However, if that user needs to examine the photograph within a couple of minutes,
then itis important the user has a higher bit rate and sufficient bandwidth, when a user needs to access streamed or live
content in real time {or with a short buffer delay) its essential that there is sufficient bandwidth to stream the content
without the buffer emptying at any point. If the buffer empties due to the content not being streamed quickly enough,
then the user will experience pauses, pixilation or missing video or sound.
Different types of communication/transmission media govern bandwidth.
Cables: Copper cables are the main method used for connecting devices in a LAN. The
most common form of copper cable is unshielded twisted pair (UTP), which is also
known as an Ethernet cable. The cables consist of four twisted pairs of cables and are
protected by plastic tubes, but there is no earth wire, which can result in lost data
packets a high frequencies. Copper cables are suitable over distances up-to 100 meters
but beyond this the signal weakens. The bandwidth available is governed by the
frequencies that the copper cable can accommodate, and electrical interference which
can result in lost data packets that which affect the transmission rate. When higher
bandwidths are required, shielded twisted pair (STP) cables can be used. They include
a metal shield around each twisted pair and an earth wire.
Different types of communication/transmission media govern bandwidth.
Wireless:
❑ Less frequencies are available to wireless communication methods than to copper cable, which means there is less
bandwidth available.
❑ Wireless transmission is also susceptible to interference from other wireless devices, including conflicting wireless
access points, baby monitors and even microwave ovens. This interference causes lost data packets which reduces
the transmission rate.
❑ Obstacles such as walls and ceilings can reduce the strength of a wireless signal, which means there is even less
bandwidth available the further away a device is from a wireless access point.
Optical: As fiber optics are not susceptible to electrical interference, they are less likely that data packets will be lost,
meaning that the total bandwidth available is considerably higher than with copper cables.
Protocols and their types
What is a protocol and different types of protocols:
A communication protocol is a set of rules that ensures that data is transferred between devices correctly. These rules are required so that a
variety of devices and applications can communicate together successfully. A protocol defines the method of addressing to use the type of error
checking to be used, how sending devices will indicate the start and end of a message, how receiving device will confirm that is received a message
and any data compression methods to be used.
Abstraction Layers: The International Organization or Standardization (ISO) published a layered model in 1883 known as the Open Systems
Interconnection (OSI) model. This defined a frame work that put protocols into seven different layers with each layer being an abstraction of
communication.
Seven Layers of OSI Model
❑ The physical layer of communication deals with electrical and mechanical operations.
❑ The data link layer deals with data packets.
❑ The network layer deals with how data is switched, outed and addressed.
❑ The transport layer ensures data lows correctly without errors,
❑ The session layer defines protocols between applications during a communication session.
❑ The presentation layer ensures that data is in a format that can be recognized such as types of image, types of
video files and the text encoding method to use.
❑ The application layer deals with specific types of communication application such as file transfer or email
OSI MODEL
OSI MODEL WITH PROTOCOL
TCP/IP PROTOCOL
TCP/IP (Transmission Control Protocol / Internet Protocol ): is the basic communication protocol used on the Internet
and in most LANs and WANs. TCP/IP consists of two layers i.e. Transport layer and Network layer. TCP deals with
breaking a message down into small data packets that are transmitted and then reassembled at the receiving end. IP
deals with the address to ensure that each packet reaches the correct destination. The address will be checked each
time a packet reaches a gateway and routed towards the destination. The IP protocol uses IP addresses which consist of
four numbers between 0 and 255 separated by dots. Some of these are addresses used for private networks which start
with 10, 172 or 192(ex. 192.168.0.0) but most are for external networks (ex. 212.58.246.90). There are approximately 4
billion of these addresses but they started to run out in 2011. Therefore,1P v6 was introduced which has the potential
for over334 x 1038 addresses.
POP(Post Office Protocol)
The Post Office Protocol (POP) service is a network server by which client-based
e-mail programs are connected to access a user's e-mail on a central server. POP
servers appear commonly on an Internet service provider's (ISP's) network, to
provide e-mail delivery to customers. It defines the rules for email-client
software to retrieve emails. The main method that is applied is to connect to an
email server, download all messages and store them on the client computer and
then delete the messages from the server. POP also supports encrypted
transmission of emails. POP is part of the application layer of the OSI model.
IMAP (Internet message access protocol)
IMAP (Internet message access protocol) is an alternative method for email
client software to retrieve emails. Instead of downloading the email and then
deleting it from the server, its default mode is to leave the email on the server
and download a copy to the client. This means the emails can still be accessed
from a remote location. IMAP also supports multiple folders on a server whereas
POP only supports a single folder on the server. IMAP is part of the application
layer of the OSI model
FTP (File Transfer Protocol)
FTP (File transfer protocol (FTP) is part of the TCP/IP suite and is used to define
how computer files should be transferred rom one location to another . FTP allows
for users to be authenticated by username and password but also has an option for
anonymous connectivity. This protocol sets the rule for how a server should
respond using ASCII codes, the data format to use (e.g ASCII, binary, EBCDIC) and
the mode of data transfer (stream, block or compressed). FTP is part of the
application layer of the OSI model. There are three components of the FTP Client:
the user interface, control process, and data transfer process. It supports different
IP protocols such as SSH, FTPS (FTP over SSL), FXP (Site2site transfer), etc.
FTP (File Transfer Protocol) Client Software
FTP (File Transfer Protocol) Client Software
Advantages of FTP Client
1.It allows for transferring multiple data as well as directories.
2.If the download fails, you can resume that downloading with the help of FTP client software.
3.It allows us to add the data to a queue to be upload or download.
4.It can transfer data to a specific schedule.
5.It provides fast speed than HTTP.
6.There is no size limitation on a single transfer.
7.FTP client is very useful for those people whose internet speed is very slow.
8.In this, several clients have scripting abilities via the CMD (command line).
Disadvantages of FTP Client
1.It does not send the data in encrypted form.
2.It is difficult to filter the active FTP connection on the local device (passive is preferred).
3.It is complex to scripts job.
4.The server can be malformed to send the file to random ports on unexpected devices.
HTTP (Hyper Test Transfer Protocol)
HTTP (Hypertext transfer protocol ) is also part of the TCP/IP suite and is used by web browsers to send requests to a web
server to view a web page. When the request is received by the web server it sends the web page information back to the
web browser. HTTP is in secure and so HTTPS is a secure version that encrypts the transmissions. HTTP is part of the
transport layer of the 0SI model.
Network Security
Unauthorized access Commonly known as hacking, unauthorized access takes place when a person or device gains access
to a computer network without permission. Hackers can guess usernames and passwords to gain access to a network,
particularly when users set up weak passwords. Once a hacker has access, they can read data on the system. This data may
be confidential to people or to the organization. The hacker may also make changes to the data, such as changing payment
details, or the hacker might destroy data deliberately to cause harm to the organization or individual.
Malware
Malware is a word used to describe any software that is designed to cause damage. In relation to networks, the main
problems are viruses and spyware. Viruses copy themselves automatically to other devices and so the connectivity of a
network makes the spread of viruses more likely. Viruses are designed to cause damage to data or cause problems to the
operation of a computer system. Parasitic viruses attach themselves to files on a computer system and are triggered by
certain events such as a date and time. Macro viruses attach themselves to macros that are part of macro-enabled
documents. Email viruses arrive as attachments to emails and are triggered by the user opening the attachment. Unique
to networks are worms which spread automatically through networks. Worms don’t require files to attach to as they create
their own executable file. Trojan horses are malicious programs that disguise themselves as normal software, but if they
are run they will actually cause damage. Trojans are often found on websites when a user tries to download some illegal
musicor films and they end up downloading a Trojan instead.
Denial of Service (DoS)
A denial of service (DoS) attack is designed to send more requests to a server than it can deal with. These are easy to
launch and difficult to track. They are carried out to cause disruption to an organization's network or website and often
result in users not being able to use the network and customers not being able to access the website. Website attacks
are measured in requests per second (RPS) and it can only take around SORPS to cripple a website. Network attacks are
measured in gigabits per second (Gbps) and it can only take around 20 Gbps of data to make a network unusable. DoS
attacks are not designed to gain access to data, but purely to cause disruption. A DoS attack can last for hours, days or
weeks. DoS attacks involve the perpetrator using a single internet connection to overload the target, but distributed
denial of service (DDoS) attacks use multiple connections distributed across the internet. These are much more difficult
to defend because they are coming from so many different locations. The motivations of perpetrators of DoS attacks can
be pure vandalism (cyber vandalism) or it could be as part of an activist campaign (hacktivism) to express criticism of, or
displeasure with, an organization.
Security Methods
Thank You