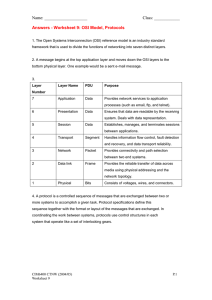
Network system It includes creating a network of computers (workstations, PCs, and supercomputers), getting them running properly, and then maintaining them functioning despite user actions that frequently lead to system failure. (Burgess, 2004). Moreover, a computer network is a combination of several independent computing elements that are linked together in different ways in order to exchange information using protocols, or standardized rules, via a common communication channel. Benefits of computer system It is worth of examine the benefits, when discussing about a computer system. Main benefits are, o In information sharing Authorized users can access and exchange information and data on other computers which linked to the network. This includes special group works, projects and databases etc. o In hardware sharing One device connected to a network, such as a printer or scanner, can be shared by many users o Software sharing Instead of purchasing and installing a software program on each computer, it can be installed on the server. All of the users can then access the program from a single location o Collaborative environment Users can work together as a team on a group project by combining the power and capabilities of diverse equipment. Other than that computer networks are used in, o Business applications (as a communication medium, in resource sharing in the business) o Home applications o Mobile users (S.Tanenbaum, 2003) Risks of computer system As well as the benefits, the security of a computer system is challenged in today by; o Equipment malfunction o System failures o Computer hackers o Virus attacks Network models Computer networks can logically be classified into two models as, Peer to Peer network ▪ In a peer-to-peer network, many workstations are linked together to share data. ▪ The workstations are considered as being equal in value. ▪ There are no dedicated servers exist in a peer-to-peer network. ▪ This network is perfect for small networks, such as home networks and small business networks, that don't require a dedicated server. Figure 1 peer to peer network (computer hope) Client server network ▪ This is a server-based network and the server is the central location where users share and access network resources. ▪ Each network that connects to the network is called a client computer. ▪ When several client computers access server-based resources, server operating systems are built to handle the strain. Figure 2 client server network (computer hope) Network types There are several kinds of network systems, which each is having special characteristics. It can be classified based on purpose or size. They are namely, (LAN, PAN, MAN, WAN) Local Area Network (LAN) ▪ Basically, a Local Area Network spreads across a small geographic area compared to other network types. ▪ ▪ LANs are limited to one building or a group of buildings. ▪ Ethernet is the most common type of Local Area Network. Advantages of a Local Area Network; Centralized management, Quick and efficient access to shared databases, Provides high data rates ▪ Disadvantages of Local Area Network; limited geographic area, may need special hardware and software Figure 3 LAN (computer hope) Wide Area Network (WAN) ▪ This network type covers a very large geographical area such as a country, continent or even the world ▪ Provides long distance communication of data ▪ Operation speed is low compared to LANs. ▪ advantages of a Wide Area Network; Operate over large geographical area, allow access over serial interfaces operating at lower speeds, connect devices separated over wide ▪ disadvantages of a Wide Area Network; The deployment and design of be challenging and require specialized knowledge and abilities, might not be as fast as LANs Figure 4 WAN (computer hope) ▪ Moreover, WANs can be further classified as, ✓ Metropolitan Area Network (MAN) : This provides high speed connectivity for internet through DSL/ADSL lines and other services such as cable TV. : advantages of MAN; Efficient Data Transfer, localized service, cost effective : disadvantages of MAN; limited coverage, maintenance complexity, scalability changes Figure 5 MAN (computer hope) ✓ Virtual Private Network (VPN) : VPN is a network that uses a public telecommunication infrastructure, such as internet to provide remote offices or individual users with secure access to their organization’s network. : advantages of a Virtual Private Network; o The internet is used as the backbone for VPNs o Employees can access the network (internet) from remote locations o Scalability : disadvantages of a Virtual Private Network; security risk, cost, reliability, potential for misuse Figure 6 VPN (computer hope) ✓ Storage Area Networks (SAN) : Storage Area Network is a high-speed special purpose network that interconnects different kinds of data storage devices with associated data servers. : advantages of SAN; Simplifies storage administration, Adds flexibility, High performance : disadvantages of SAN; cost, complexity, single point of failure, risk of data loss Figure 7 SAN (computer hope) ✓ Controller Area Network (CAN) : A controller area network (CAN) bus is a high-integrity serial bus system for networking intelligent devices. : Devices and CAN buses are frequently found in industrial and automotive systems. : advantages of CAN; real time performance, flexibility, high reliability : disadvantages of CAN; limited data rate, distance limitations, lack of security features Figure 9 CAN (computer hope) Figure 8 CAN (computer hope) Other types of networks, ➢ Intranet An intranet is a private LAN designed to use by everyone within an organization. Figure 10 INTRANET ➢ Extranet This is a network that links members of your firm with those outside the organization. Figure 11 EXTRANET What is Cloud computing? ➢ Cloud computing is a technology that enables entities to access and use different computing services and resources over the internet. ➢ Benefits of cloud computing o Low cost o High speed o More productivity o Reliability Transmission media Communication channel, In order to send data from one computer to another computer it requires some type of link through which the data can be transmitted. This link is simply known an communication channel. Transmission medium, To send data through the channel it requires some type of transmission media. I may be physical or wireless. Types of transmission media, We can classify transmission media into 2 as; Guided media (wired) ▪ Cabling Computers in a network are usually physically connected to each other using cables. There are several types of cables as; o Twisted pair cable This is the most commonly used cable in today’s world. This also known as its official designation 10BaseT. Features – Inexpensive Requires two conductors Plastic sheath Two types as Unshielded Twisted Pair (UTP) and Shielded Twisted Pair (STP) ❖ Unshielded Twisted Pair (UTP) UTP is made up of two copper wires that have been wrapped in insulation. This cable has interference suppression capabilities and doesn't need a physical shield. It is used for telephonic applications. ✓ Advantages of UTP The cheapest Simple to install Capacity for high-speed ✓ Disadvantages of UTP Vulnerable to interference from outside Less performant and with a lower capacity than STP ❖ Shielded Twisted Pair (STP) This cable type has a protective jacket to prevent outside interference. ✓ Advantages of STP reduces echoing Better performance Comparatively faster ✓ Disadvantages of STP Quite difficult to install and produce More expensive Figure 12 CABLES (IJRTI) o Coaxial cable This also known as its official designation 10Base2. Features – higher bandwidth Less susceptible to noise Center conductor wire Encased in a protective sheath ✓ Advantages of coaxial cable A large bandwidth Improved noise resistance ✓ Disadvantages of coaxial cable To avoid interference, the system must be grounded. A coaxial cable's numerous layers, which add bulk. Figure 13 COAXIAL CABLE (IJRTI) ▪ Fiber Optic Cable This is good for very high speed, high-capacity data transmission because of the lack of attenuation and the purity of the signal. Optical fibers carry digital data signals in the form of modulated pulses of light. ✓ Advantages of Fiber Optic Cable Increased bandwidth and capacity Lightweight Less attenuation of the signal Protection against electromagnetic interference ✓ Disadvantages Install and maintain difficult High price Figure 14 FIBER OPTIC CABLE (IJRTI) Unguided media (wireless) It is also known as wireless transmission media or unbounded transmission media. Electromagnetic signals may be transmitted without a physical medium. There are 3 types of Signals transmitted through unguided media; Microwave system – Transmit data via high frequency radio signals through the atmosphere Figure 15 MICROWAVE SYS (IJRTI) Infrared technology – transmit data as infrared light waves from one device to another, providing wireless links between PCs and peripherals Figure 16 INFRARED Satellite system – Receive transmitted signals, amplify them, and then transmit the signals to the appropriate locations Figure 17 SATALITE SYS(IJRTI) Cellular technology – Uses antennae resembling telephone towers to pick up radio signals with a specific area Figure 18 CELLULAR TECH ✓ Advantages of using unguided media The signal is broadcasted through free space. Portable service ✓ Disadvantages of using unguided media Data security is in risk as signals can be hacked. Transmission of data may be affected by weather condition. Signal interference if there exist many wireless signals. ❖ Factors to be considered when selecting transmission media Transmission rate Distance Cost and ease of installation Resistance to environment conditions Network topologies Network topology refers to the way computers and peripherals are configured to form networks. We can identify them as logical topology and physical topology. Physical topology Here, the network laid out physically. There are different types of physical topologies as; Bus topology In the bus topology all devices share single communication line or cable. Bus topology may have problems while multiple hosts sending data at the same time. As a solution for that either uses CSMA/CD technology or recognizes one host as bus master. Importance and impact of bus topology o Being simple and requires minimal cabling o Cost effectiveness o Expansion of the network being easy Figure 19 bus topology (computer hope) Mesh topology Here the host is connected to one or more multiple hosts. The host may be connected in point to point with every other host or may also have hosts which are in point-to-point connection to few hosts only. Comes in two types as, full mesh and partial mesh Importance and Impact of Mesh Topology o Reducing redundancy o High data transfer speed o Flexibility o Isolation of Network Traffic Figure 20 MESH TOPOLOGY (computer hope) Star topology Here, every node connects to a central device. (Hub, switch, computer). The central device act as a server and the other devices acts as clients. (computer hope, 2023) Importance and Impact of star Topology o Centralized control o Being easy to add or remove devices without disrupting the entire network o Ease of management o Being a user-friendly network Figure 21 STAR TOPOLOGY (computer hope) Ring topology Here, the network is created by connecting each host machine with exactly two other machines. So, the data is transmitted from one device to another until it reaches the destination. Importance and Impact of ring topology o Easy to set up o Prevent data collisions o No central point of failure o Minimal delay Figure 22 RING TOPOLOGY (computer hope) Tree topology Tree topology is seeming like a tree. Here, it divides the network in to multiple levels. All neighboring hosts have point to point connection between them. Importance and Impact of tree topology o Easy to manage the network connection s o Centralized management o Network traffic can be controlled o Being suitable for large organizations Figure 23 TREE TOPOLOGY (computer hope) Impact of physical topologies Physical topology explains how devices and cables are physically arranged and can be modified based on needs. The physical topology of a network can impact its reliability, scalability, ease of management, and overall performance. Logical topology This means the logical pathway where data travels in a computer network. Ethernet o Widely developed LAN technology. o Invented by bob Metcalfe. o It was standardized in IEEE 802.3 o Ethernet share media. Fast ethernet o Ethernet was extended as fast ethernet. o It can run on UTP, optical fiber, and wirelessly too. o IEEE standard is IEEE 803.2 Giga ethernet o After introducing fast ethernet, after 3 years giga ethernet was introduced. o IEEE 802.3ab standardized giga ethernet over UTP using Cat-5, Cat-5e and cat-6 cables. o IEEE 802.3ah defines giga ethernet over fiber. VLAN VLAN divides a single broadcast domain into multiple broadcast domains. Host in one VLAN cannot speak to another host. By default, all hosts are placed into the same VLAN. Token ring Token ring operates at the network access layer of the TCP/IP model. It is using IBM connectors and cables. This is physically a star topology. Impact of logical topologies Logical topology explains how all the devices in a network communicate with each other. Basically, logical topologies are different from physical topologies. Logical topologies focus on how data flows, while physical topologies focus on how devices are wired together. Figure 25 logical vs physical (DNSstuff) Networking standards Networking standards are the set of guidelines which outlines the best practices, specifications, or requirements for a particular technology, product, or service. Standards are basically developed by organizations such as the International Organization for Standardization (ISO) or the Institute of Electrical and Electronics Engineers (IEEE). Standards help to ensure that products and services are safe, of high quality, and can work together seamlessly. IEEE standards In 1985, the computer society of IEE has started the “project 802” in order to set standards and to enable inter communication among equipment from a variety of manufactures. So, this can specify the functions of the physical layer and the data link layer of major LAN protocols. Example; IEEE 802.x – this is deal with LAN and MAN. And also, these are restricted to networks carrying variable size packets. The services and protocols which used this standard are map in the lower two layers of the OSI networking referral model. IEEE 802.3 (ethernet) – this defines the physical layer and data link layer’s media access control (MAC) of wired ethernet. This is generally, a LAN technology with some WAN applications. IEEE 802.11 (Wi-Fi) – this specifically devoted for WLANs with a character to develop a MAC protocol and physical medium specification. IEEE 802.1Q (VoIP (Voice over Internet Protocol)) – this standard helps ensure that voice calls and other data can share the same network without interfering with each other Benefits of standards Compatibility Provide a foundation for new technologies and innovations to build Networks being reliable and stable Global adoption constraints of standards Rapid Technological Changes Limitation of Choice Complexity Protocols Protocols means a set of rules and procedures for transmitting data between two or more devices. It specifies the structure, timing, order, and error checking involved in data transmission between devices. Examples for protocols; TCP, IP, UDP, POP further discussed in page 39-43. Network models In order to understand and manage the computers we are using network models. It helps to describe how the networks work. There are different models, each with its own rules and standards for sharing data. Some popular models are OSI, TCP/IP, and hybrid models. These models make dealing with networks easier and more organized for everyone involved. There are two types of network models as, o ISO OSI Model o TCP/IP Model ISO/OSI Model For data to travel smoothly across countries and the world, we need systems that can talk to each other. ISO, which stands for International Organization of Standardization, made a set of rules called the OSI model. There are 7 layers. This model helps different systems work together, like speaking a common language, making global communication possible. (studytonight, n.d.) Benefits of OSI model are; ▪ ▪ ▪ ▪ Reduces complexity Standardizes interfaces Facilitates modular engineering Accelerates evolution Figure 26 OSI model Physical layer The lowest layer of OSI model is physical layer. This layer creates the actual connection between all physical devices and media involved in data exchange. Data link layer ▪ This is the second layer of OSI model. ▪ Messages are delivered from node to node by this. ▪ The data link layer is in charge of using the host's MAC address to transmit messages when they are received by. ▪ We can classify two sub layers as; 1. logical link control 2. MAC, or media access control ARP (address resolution protocol) is used to encapsulate the receiver's MAC address in the data connection layer. Network layer This is the third layer of OSI model. Network layer facilitates the transfer of data between the network nodes. The process used by the network layer to add the sender's and receiver's IP addresses to the header is refer as the logical addressing. Transport layer This is the fourth layer of OSI model. Transport layer is responsible for end to end communication over a network. The transport layer provides an access to both the session layer and the network layer. Session layer This is the fifth layer of OSI model. This session layer provides the mechanism for opening, closing and managing a session end user application process. Presentation layer This is the sixth layer of OSI model. This layer explains how data is presented to the user. Data encryption is also a function of presentation layer to ensure data security. Application layer This is the last layer of OSI model. The function of this layer is to present data to user by enabling direct interaction between user and software applications. TCP/IP Model The Department of Defense created and developed TCP/IP, which is based on standard protocols, in the 1960s. TCP/IP stands for “Transmission Control Protocol/Internet Protocol”. Compared to the OSI model's seven layers, TCP/IP model has four layers. (geeksforgeeks, 21 Jul, 2023) There are 4 layers of this model as; o Application Layer o Transport Layer o Internet Layer o Network Access layer/Link Layer Figure 27 TCP MODEL Network access layer ▪ This is the first layer of TCP/IP model. It controls the hardware devices and media that make up the network. ▪ Examples for protocols; ethernet, frame relay Internet layer ▪ This is the second layer of TCP/IP model. It determines the best path through the network. ▪ Examples for protocols in internet layer; ➢ IP An IP address is a special code for devices on the Internet or a network. These addresses help devices talk to each other by showing where they are. Just like homes have different addresses, devices have different IP addresses. It is important for the Internet to know which device is which. ➢ ICMP Internet Control Message Protocol (ICMP) uses an error control method to identify communication problems. Since there is no built-in method for transmitting error and control messages in IP. Error control is provided through ICMP. ➢ ARP & RARP ARP used to get the physical address of destination machine. Transport layer ▪ The transport layer of the ISO OSI model and this layer operate in parallel. The function is to support communication between diverse devices across diverse networks. ▪ Examples for protocols in transport layer; ➢ Transmission Layer Protocol (TCP) TCP is a tool that ensures data is sent smoothly between apps. It guarantees that the data is complete, in the right order, and reaches its destination without issues. (IBM, 2021) ➢ User Datagram Protocol (UDP) UDP is a part of IP and must be implemented by every IP module. It provides full transport layer service to applications. Application layer ▪ This is the final layer of TCP/IP model. ▪ The Application, Presentation, and Session Layers of the OSI model are performed by this layer. ▪ Examples for protocols in transport layer; ➢ File Transfer Protocol (FTP) File Transfer Protocol (FTP) is a special way to transfer files between computers on the internet. FTP used to be like talking between two devices, but now it's often used to store files safely online in the cloud. (Mitchell, 2023) Figure 28 FTP ➢ Simple Mail Transfer Protocol (SMTP) Simple Mail Transfer Protocol (SMTP) is an internet standard communication protocol for electronic mail transmission. Figure 29 SMTP Telnet Telnet allows you to connect to remote computers over a TCP network. DNS-Domain Name Server It is used to resolve human readable host names into machine readable IP addresses. Hypertext Transfer Protocol (HTTP) Hypertext Transfer Protocol (HTTP) used to access the data on the World Wide Web (www). It can be used to transfer the data in the form of plain text, hypertext, audio and video. HTTP is similar to SMTP as the data is transferred between client and server. Figure 30 HTTP ➢ Hypertext Transfer Protocol secure (HTTPS) HTTPS used to secure socket layer or transport layer security as a sub later under regular HTTP application layering. Figure 31 OSI VS TCP/IP Impact of bandwidth requirements bandwidth means amount of data that can be carried from one point to another in a given period of time. Bandwidth is expressed in bits per second. The advantages of high bandwidth are; faster data transfer, high user experience, efficiency. The disadvantages of high bandwidth are; poor transmission speed, user dissatisfaction. Common networking principles and how the protocols enable the effectiveness of networked systems Networking principles are the main foundation that is under the design, implementation and management of a network. Networks should be reliable. Networks should be dependable and should work consistently. Another principle is security. Ensuring the security of a network is must needed. The network should perform well. That is another principle. One of the main principles is standardization. In a network, we should use common protocols and standards to ensure the efficiency of the network. With the help of these principles, the effectiveness and efficiency of a system is determined. Then below is how protocols enable the effectiveness of a network system. The network protocols are more likely to special codes with helps the devices to talk with each device. Protocols make sure that where the message should go in safely and accurately. Without protocols, devices cannot understand each other when communicating. Different protocols have specific roles. Some focus on verifying data integrity to make sure nothing gets corrupted during transmission. Others manage data flow to prevent congestion on the network. Some protocols handle security, ensuring that data remains private and protected. In conclusion protocols are the reason behind the reliability of the communication on the Internet. They create a common ground, allowing devices to understand and work with each other, which is crucial for the smooth operation of networked systems