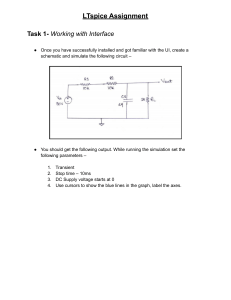
Binary, Hex, Floating Point, Logic, Data Structures Reference
advertisement

Name Binary Hexadecim al Converting Hex Sign of Magnitude Two’s Complimen t Subtracting with 2’s complimen t Floating Points Numbers (FPN) in Binary Addition of FPN Subtractio n of FPN Normalisat ion Bitwise Manipulati on Masks Description Method Example Can represent up to Uses the 128 64 32 16 8 4 2 1 table to convert binary into denary 00010111 = 23 256 Uses letters and numbers to represent values 0 1 2 3 4 5 6 7 8 9 A B C D E F = 0-15 B2 = 10110010 = 178 Split digits into a nibble and then combine the nibbles Split into hex digits, then convert hex to decimal, then decimal do binary nibbles then combine them B2 = B 2 = 11 2 =1011 0010 = 10110010 =178 Positive = 01 To convert from SoM to Decimal, identify the sign and Normal 15 = & Negative = 11 discard the leading bit. Then convert normally and add 1111 the sign (either + or -) SoM +15 = 01111 SoM -15 = 11111 Flip all the bits and add 1. Make the most significant bit negative, and then flip the 7= 00000111 bits and add one using binary addition rules. flip 7= 11111000 add 1= 11111001 Subtracting a number from Organize the addition in a top-heavy order, remember Sub 12 from 8 another = adding a negative that the most significant number is negative. Then 08 = 01000 number. perform a binary addition and convert to denary if -12 = 10100 needed. = 11100 = -16 +8 +4 = -4 First bit is the sign, then 0 = positive & 1 = negative in both the mantissa and Sign = 0 = + you have the mantissa exponent. The binary point (decimal point) is found after Mantissa = and the exponent. the first bit of the mantissa. Next convert the exponent to 1100100111 = With a positive decimal. Then move the binary point the number of times 1.100100111 exponent jump to the stated by the exponent. Finally convert it to binary, any Exponent = 000101 = right. Whilst with a numbers after the binary point are below 0 e.g. .5, .25, 5 negative exponent jump .125, .0625… Jump = 5 to the left. When jumping left you can pad the jumps with 0’s. 110010.0111 = 50.4375 Exponents Once exponents are the same, to e.g. MUST be the add, add the mantissas and 0 000100 0011 same in order normalise the result if required. If 0 000101 0010 to perform exponents are not the same, one First mantissa is shifted by 3 and the second by 2. calculations. must be modified to match the other 0 001000 0010 by shifting one or both exponents. 0 000101 0010 Once exponents are the same, a Addition = binary addition on the mantissas can 001101 be carried out. Finally the results still Normalise by shifting the M by 1 bit to the left and needs to be normalised by shifting decrease the E by 1 = 0 011010 0001 the mantissa. Similarly, exponents Firstly, exponents must be the same. Next the mantissa of the number being must be the same. subtracted from must be converted to 2’s complement (by flipping all and +1). Now binary addition is carried out before normalising the results. Adjust Mantissa (M) First split number into M and E. Next adjust M for positive or Whole number = so a positive binary negative. With positive move all the bits to the left until 01 or 00011010 0101 starts with 01 and a 10 and then pad the ending with 0’s. By increasing M, E must be Adjust M to + or negative with 10. reduced by the same number of shifts e.g from 5 jumps to 3. 01101000 0011 Binary shifts, Shifts move all bits in a specific direction, can be done by adding a number leading or trailing left and right of 0’s. e.g. Performing a left shift on 10010110 = 10010110000 Left shift = Multiplication & Right Shift = Division. Binary number + Logic gate AND, OR and XOR apply their rules to and operation e.g. ---> Character Sets Array, Record Lists Tuples Linked lists Graphs Stacks Queues Trees Hash Tables Logic gates Karnaugh Maps De Morgan’s Law Distributio n ASCII ASCII = American Standard Code for Information Interchange. ASCII uses 7 bits which can represent and up to 128 different symbols. A-Z = 65-90/ a-z = 97-122/ 0-9 = 48-57/ . = 46/ space = 32. Extended Unicode ASCII uses 8 bits = 256 characters. Unicode = Uses a varying number of bits, allows for over 1 million characters of different languages. Array is an ordered, finite set Array, 1D = Linear array, 2D Table (down the rows and across columns), 3D of elements of a single type. database (array num, row, column number). It’s a just like a row in a file Records are used in a database Consists of a list of number of ordered items where items can occur more than once and are stored noncontiguously, which means they are not stored next to each other in memory. More than 1 data can be stored. An ordered set of values of any type. It is immutable (cannot be changed) once is created. Dynamic data structure used to hold and ordered sequence not necessarily contiguous. Each item is called a node and contains a data field named a link/ pointer. They store the first pointer and the next free space. Set of nodes connected by Advantages of Matrix are convenient to work due to quicker access time + is edges. CPU’s transverse using easy to add nodes. an adjacency list or matrix Advantages of List is that It is more efficient for large sparse networks. Last in First Out (LIFO) data structure. Items can be Stacks can be static or dynamic, where the max manipulated from the top of the stack. They are often used size is required must be known in advance. to reverse an action. First in First Out (FIFO) data structure where There are different types of queues, linear where it acts items are added to the end of the queue. similarly to an array, items are added onto the list, starting Often used in printers and simulators. from the front. A circular queue allow for looping, provided it is empty. Have a root node at top, connected to other nodes using branches with children and leaves of nodes. A binary tree can have a max of 2 children. Easy to search and represent with left and right pointers. 3-way s to traverse, Pre-order, in-order, and Post-order. A hash table is an array which is paired with a hash function. The hash function takes in a data (a key) and releases an output (the hash). The role of a hash function is to map the key to an index in the hash table. Each piece of data is mapped to a unique value using a hash function. Collision is when 2 inputs result in the same hashed value, a good hashing algorithm has low collisions. To deal with them the item is typically placed in the next available location. AND = Conjunction, ^ / OR = Disjunction, V / NOT = Negation, ¬ / XOR = Exclusive Disjunction V Group with even numbers, 2,4,8,16…., use wraparounds, groups can overlap. Involves a breaking a negation and changing the operator between two literals. They are used when a negation applies to the whole of an operator between 2 literals. and result in 2 negated literals Applies to conjunctions over disjunction as well as disjunction of Conjunction over Disjunction: conjunction Disjunction of conjunction: Association Involves the addition or removal of brackets and reordering of literals in a Boolean expression. Commutati on Laws of commutation show that the order of literals around an operator does not matter. Double Negation If you negate a literal twice, you can remove both negations and retain the same truth value. NOT NOT A is the same as A. D-Type Flip Flops Type of logic circuit which can store the value of 1 bit. It has 2 inputs, a control signal, and a clock input. A clock pulse rises and falls as shown in the diagram, with edges labelled rising or falling. The output of a D-type flip flop can only change at a rising edge, the start of a clock tick. These use a NAND gates. Adders An adder is a logic circuit which adds together the number of inputs which are true, and outputs that number in binary. There are two adder circuits you need to know: half and full. Half Adder A half adder has two inputs, A and B, and two outputs, Sum and Carry. The circuit is formed from just two logic gates: AND and XOR. Full Adder A full adder is similar to a half adder, but has an additional input, allowing for a carry in to be represented. The full adder logic circuit is formed from two XOR gates, two AND gates and an OR gate as shown in the diagram. Because the full adder has a carry input, the circuits can be chained together to form what’s known as a ripple adder. At each stage, B and Cin can be connected to the previous adder’s S and Cout, and a new input can be attached to A. Time Complexity It is how much time it requires to solve a particular problem. It shows the effectiveness of the algorithm. It shows an upper limit for the amount of time taken relative to the number of data elements given as an input. This is good because it allows you to predict the amount of time it takes for an algorithm to finish given the number of data elements. Big O Notation Linear Search Algorithm A linear search algorithm is an algorithm which traverses through every item one at a time until it finds the item its searching for, below is the pseudocode for the linear search algorithm. The Big-O notation for a linear search algorithm is O(n). Bubble Sort Algorithm The bubble sort algorithm passes through the list evaluating pairs of items and ensuring the larger value is above the smaller value. It has a polynomial Big-O notation, O(n2 ). Breadth First Insertion Sort Merge Sort Dijkstra’s Algorithm A* Algorithm Starting from the left, breadth-first visits all children of the start node. It places elements into a sorted sequence. In the ith iteration of the algorithm, the first i elements of the array are sorted. It starts at the second element in the input and compares it to the element to its left. If the two elements are in the wrong order, the smaller element is placed in the lowest position. The third element in the input is then selected. It is inserted into the correct position in the sorted portion of the input to its left Divide and Conquer, . Merge Sort divides its input into two parts and recursively calls Merge Sort on each of those two parts until they are of length 1 at which point Merge is called. Merge puts groups of elements back together in a special way, ensuring that the final group produced is sorted. Merge Sort is a more efficient algorithm than bubble sort and insertion sort, with a worst-case time complexity of O(n logn). Regardless of the scenario, complexity, or size of the graph, it finds the shortest path between two nodes in a weighted graph. Step 1: Starting from root node (A) add the distances to all adjacent neighbouring nodes to the priority queue. All nodes that can’t be reached are labelled by (infinite symbol). Step 2: Remove the first node from the front of the queue once all options have been visited. Now traverse the rest of the nodes starting from the closest to the root node. Step 3: Continue repeating Step 2 until the goal node has been reached. As we have now visited all the nodes on the graph, we can confirm by tracing back through the table the shortest path The A* Algorithm is a general path-finding algorithm which is an improvement of Dijkstra’s algorithm and has two cost functions: 1) The first cost function is the actual cost between two nodes. This is the same cost as is measured in Dijkstra’s algorithm. 2) The second cost function is an approximate cost from node x to the final node. This is called a heuristic and aims to make the shortest path finding process more efficient. The approximate cost might be an estimate of the length between x and the final node, calculated using trigonometry. When calculating the distance between two nodes using the A* algorithm, the approximate cost is added onto the actual cost. This is used to determine which node is visited next. This differs from Dijkstra’s algorithm as a node with a lower actual cost may be rejected in favour of a node with a lower total cost. This is meant to reduce the total time taken to find the shortest path Step 1: When working out the shortest distance using the A* algorithm, an extra column is required to store the heuristic. The heuristic cost is added onto the actual cost to calculate the total cost. Step 2: The node with the least estimated time of traversal is then selected. This process is then repeated until it achieves its destination. The heuristics used here allow the shortest path to be found much quicker than when using Dijkstra’s algorithm. How effective the A* algorithm is, however, depends largely on the accuracy of the heuristics used.