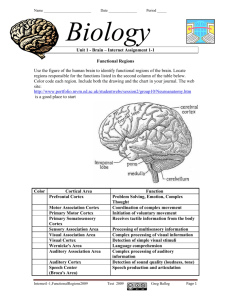
Creating Intelligent SOCs Cortex XSOAR Top Machine Learning Use Cases “Machine learning” is a term awash with both endless potential and considerable skepticism. As a security orchestration, automation, and response (SOAR) platform built from the ground up with a foundation of machine learning, Cortex® XSOAR brings customers verifiable benefits in their security operations centers (SOCs) across geographies, maturity, and scope of operations. The machine learning capabilities of Cortex XSOAR increase responder productivity, accelerate playbook development, and enable leaner, more efficient security operations. This paper presents a series of use cases that describe the challenges SOCs face, how Cortex XSOAR helps, and the benefits these capabilities provide. Cortex by Palo Alto Networks | Creating Intelligent SOCs | Use Case 1 Use Case 1: Incident Owner Recommendations Challenge As SOCs scale, they end up following a “whoever’s available” approach for assigning incident owners. This not only leads to uneven workloads for analysts who are already overburdened but also results in analyst expertise getting ignored with respect to assignments. Improperly assigned incidents will eventually lead to improperly handled incidents. Solution Whenever incident owners are to be assigned, Cortex XSOAR studies details of all past incidents in the system, including incident types and a variety of fields. Using machine learning, Cortex XSOAR cross-references this data with existing analyst loads to suggest the top three analysts best suited to own the incident. Figure 1: Intelligent analyst recommendations Cortex XSOAR studies incident fields and analyst loads b ­ efore recommending incident ownership. Benefit These suggestions ensure that workload is not the only ­criterion considered during incident assignment. By studying incident types and fields, Cortex XSOAR is able to suggest analysts who are best suited to own incidents with respect to both time and expertise. Cortex by Palo Alto Networks | Creating Intelligent SOCs | Use Case 2 Use Case 2: Security Expert Suggestions Challenge End-to-end handling of incident response is rarely an i­ solated process. Unfortunately, SOC analysts often operate in silos while performing investigations, oblivious to their colleagues’ specific skill sets that might come in handy for complex incidents. Junior analysts especially operate in the dark here, left to contend with incidents alone as senior analysts are occupied with other day-to-day operations. Solution Cortex XSOAR War Room enables collaborative investigations wherein analysts can invite their teammates to conduct joint investigations. Here, Cortex XSOAR uses machine learning to study the history of all closed incidents, specifically looking at manual actions performed by analysts in the past. After parsing this data, Cortex XSOAR suggests the top three analysts who can provide relevant assistance for a particular incident. Figure 2: Decisions based on historical analysis Cortex XSOAR looks at manual actions performed in the War Room and the history of closed ­incidents before­­recommending security experts to join the ­investigation. Benefit By both enabling joint investigations and facilitating intelligent team composition, Cortex XSOAR War Room heralds a consistent decrease in resolution times and increase in resolution quality. This feature also acts as a guiding hand for junior analysts by highlighting which experts can help them through ­specific incidents, thus reducing error rate and analyst anxiety. Cortex by Palo Alto Networks | Creating Intelligent SOCs | Use Case 3 Use Case 3: Commonly Used ­Security Commands Challenge While conducting real-time investigations after incident triage, analysts literally have hundreds of possible security a ­ ctions to choose from. As SOCs keep expanding their product stacks, there is an observed divergence in the type, order, and fidelity of security actions taken from analyst to analyst. This leads to varying resolution times and quality for similar incidents, which can negatively impact service-level agreements (SLAs) and metrics tracking. Solution When analysts begin to type in a security command in Cortex XSOAR War Room, the platform studies manual commands used for all incidents of that type in the past. This data enables recommendations on which security commands to run first. Even if analysts have already run some commands and are stuck in the middle of an investigation, these suggestions can set them on the right path with commands they might have missed. Figure 3: Intelligent command recommendations Cortex XSOAR looks at manual commands performed for particular incident types to recommend commonly used commands for that incident type. Benefit Security command suggestions move analysts toward standardized incident response and guarantee that no commonly used actions are missed for any isolated incident. U ­ ltimately, the Cortex XSOAR platform helps maintain and improve SOC SLA health by preventing rogue investigation processes that miss critical actions. This also aids in organic knowledge management and retaining expertise within the SOC. Cortex by Palo Alto Networks | Creating Intelligent SOCs | Use Case 4 Use Case 4: Visualizing ­Related Incidents Challenge The speed and intensity with which incidents crop up in the SOC frequently lead to analyst myopia. While concentrating on the incident at hand, analysts may fail to connect it to the bigger picture and draw patterns with similar incidents that have already occurred on the system. This results in redundant rework for response processes that are already stored—but untapped—in the platform. Solution For each Cortex XSOAR incident, the Related Incidents section presents a visual, time-based map of similar incidents that have occurred on the system. Cortex XSOAR studies the incident’s data and indicator details, identifies patterns and similarities, and visualizes that data in actionable form. Figure 4: Visualized, actionable data Cortex XSOAR correlates indicators and incident data to present a real-time radial map of related ­incidents for each case. Benefit Rather than reduce MTTR or alert fatigue—which are ­standard SOAR benefits—the Related Incidents feature goes a step further and increases analysts’ investigative c ­ apabilities by providing them with visual tools to better understand the broader picture of the SOC and how incidents are related across a host of factors. Cortex by Palo Alto Networks | Creating Intelligent SOCs | Use Case 5 Use Case 5: Simplifying ­Playbook Task Creation Challenge After playbooks make the initial journey from paper (or the analysts’ minds) onto SOAR platforms, they facilitate automated response but may not undergo any further measurement and review. Unless analysts capture better knowledge from elsewhere and feed it into the platform, the benefits of these playbooks plateau eventually. Solution Cortex XSOAR not only facilitates creation of custom playbook tasks but also uses machine learning to accelerate conception of verifiably relevant tasks. While creating playbook tasks and selecting inputs, analysts can see suggestions for arguments and parameters that fit best with those inputs. Figure 5: Best-fit input recommendations Cortex XSOAR digs across playbook tasks to study commonly used automation arguments and recommends these inputs during the creation of new playbook tasks. Benefit Rather than stopping at alert fatigue reduction and quicker incident triage, Cortex XSOAR playbooks use machine learning to always traverse the path of improvement through more efficient tasks. This helps tackle the eventual stagnation in efficacy of static playbooks. Cortex by Palo Alto Networks | Creating Intelligent SOCs | Use Case 6 Use Case 6: Extracting ­Duplicate Incidents Challenge High alert volume usually leads to a high occurrence of ­duplicates as well. However, due to varying attack vectors, different target endpoints, or subtle morphing, these incidents register independently on the SOC’s security i­ nformation and event management (SIEM) or SOAR platform. This leads to tiresome, repetitive work for the analysts as they comb through duplicate incidents. Solution Cortex XSOAR users can take advantage of out-of-the-box automation to generate a list of duplicate incidents, either as a playbook task or interactively in the War Room. Cortex XSOAR machine learning studies both predefined data and customer environments, looks for similar labels, email labels (relevant for phishing incidents), incident occurrence times, and common indicators to generate this list. Figure 6: Automation to identify duplicate incidents Cortex XSOAR builds a duplicate incident list by comparing labels, time stamps and other ­common traits among incidents. Benefit Easy identification and documentation of duplicate incidents eliminate huge chunks of menial work for analysts, freeing them to concentrate on more critical problem-solving and meaningful tasks. Cortex by Palo Alto Networks | Creating Intelligent SOCs | Use Case 7 Use Case 7: Automate Phishing Response Challenge Reviewing potential phishing incidents consumes a significant portion of time for many SOC teams. ­Analysts spend an exorbitant amount of time and energy manually investigating potential phishing ­attacks, using various tools and services that provide enriched data on indicators found within the emails to see if any proof of malice exists. Such a high volume of phishing attack incidents usually requires a ­manual review step, in which many of the suspected phishing incidents turn out to be false positives. Solution Cortex XSOAR’s machine learning (ML) model capabilities can solve this manual review process with a high degree of accuracy and efficiency using the phishing classifier feature. The phishing classifier is a deep learning model that enables Cortex XSOAR to analyze and predict behavior through incident types and fields. Machine learning models are used mainly for phishing incidents and can be trained to automatically recognize, for example, phishing emails or URL information that is legitimate or contains spam and predicts if there is a potential phishing attack. Figure 7: Sample phishing classifier model results Cortex XSOAR provides detailed evaluations and enables analysts to get a sense of how the model should perform from different aspects to better understand the expected implications of applying it in a certain way. Benefit Cortex XSOAR enables users to leverage ML effectively in the investigation process of phishing incidents. In a few short steps, SOCs can configure the ML model training using either out-of-the-box or custom models and scripts to identify and analyze specific indicators, get a detailed analysis of the results, and receive a recommendation for using it in production. It is yet another step in the SOC automation journey that eliminates unnecessary manual work. Cortex by Palo Alto Networks | Creating Intelligent SOCs | Use Case 8 Conclusion For Cortex XSOAR, automation is just one of many means to an end: an attack-proof SOC. By harmonizing actions across products, managing incidents within the platform, collaborating in real time, and learning from all the data at your disposal, you can truly extract the greatest value for your SOC. Staying true to the “learning” half of machine learning, Cortex XSOAR is always searching for new avenues to leverage its ML base and advance a platform that gets smarter with each incident, in turn making the SOC smarter as well. Want to See Cortex XSOAR in A ­ ction? Schedule a demo. Sign up for Cortex XSOAR Free Edition. 3000 Tannery Way Santa Clara, CA 95054 Main: Sales: +1.408.753.4000 +1.866.320.4788 Support: +1.866.898.9087 www.paloaltonetworks.com © 2022 Palo Alto Networks, Inc. Palo Alto Networks is a registered ­ trademark of Palo Alto Networks. A list of our trademarks can be found at https://www.paloaltonetworks.com/company/trademarks.html. All other marks mentioned herein may be trademarks of their respective companies. cortex_creating-intelligent-socs_uc_032222