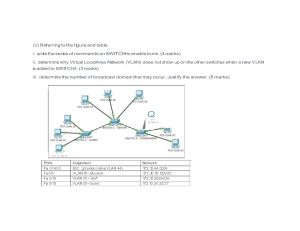
Presented by: Jelly Anne Lumactud • AVOID ACTIONS THAT CAN DISRUPT THE ONGOING SESSION. • TAKING DOWN NOTES IS HIGHLY APPRECIATED. • PARTICIPATE IN THE DISCUSSION BY ANSWERING ON-THE-SPOT QUESTIONS 01 02 03 Goals of Cybersecurity History and Timeline Dangers of Unsecured Networks 04 05 06 Securing A Network Implementations On the Spot Exercises NETWORK AND SECURITY SOFTWARE DEVELOPMENT Part-Time Cybersecurity Instructor Junior Support Project Manager Partner Services Assistant Part-Time Full Stack Web Development Instuctor Programmer Intern - VB.Net and Core PHP Confidentiality Prevents unauthorized use or disclosure of information. Integrity Availability Safeguards the accuracy and completeness of information. Authorized users have reliable and timely access to information S e c u r i t y • The Internet was initially designed for connectivity ⚬ Trust Assumed ⚬ We do more with the Internet nowadays ⚬ Security protocols are added on top of the TCP/IP • Fundamental aspects of information must be protected ⚬ Confidential data ⚬ Employee information ⚬ Business models ⚬ Protect identity and resources • We can’t keep ourselves isolated from the Internet ⚬ Most business communications are done online ⚬ We provide online services ⚬ We get services from third-party organizations online • It was first coined by US President Bill Clinton in 1996 as Critical Infrastructure. • He intends all necessary measures to swiftly eliminate any significant vulnerability to both physical and cyber attacks on our critical infrastructures, including especially our cyber systems. • 2013: Iranian hackers breached Bowman Avenue Dam in New York and gained control of the floodgates. • 2016: The attack on a Ukrainian power facility left 700,000 individuals without power in mid-December. • 2017: Triton was first seen in a Saudi petrochemical plant, allowing hackers to take over the plant's safety instrument system (SIS). • 2018: Hackers breached NASA's Jet Propulsion Laboratory's (JPL) IT network using Raspberry PI which had been connected for over a year undetected. • 2021: The Colonial pipeline was the target of a ransomware attack leaving upwards of 45% of the US East Coast gas, diesel, and jet fuel supplies offline. How many sectors are there in CIP? There are 16 sectors present in CIP. • Abbreviated as (Open Systems Interconnection) Model. • It was published in 1964 by International Standard Organization (ISO) when network computing was in its infancy. • It is a conceptual framework used to describe the functions of a networking system. The OSI model characterizes computing functions into a universal set of rules and requirements in order to support interoperability between different products and software. O S I L A Y E R S O • • • • • • • • • • Abbreviated as (Open Systems Interconnection) Model. • It was published in 1964 by International Standard Organization (ISO) when network computing was in its infancy. • It is a conceptual framework used to describe the functions of a networking system. The OSI model characterizes computing functions into a universal set of rules and requirements in order to support interoperability between different products and software. • It was designed to describe the functions of the communication system by dividing the communication procedure into smaller and simpler components. What OSI Layer/s use/s packet filtering? Select all that apply. A Application Layer B Network Layer C Switch Layer D Transport Layer Transport and Network Layer • Using Raspberry PI, hackers stole JPL's files about the Mars expedition using a shared network gateway. • The hacker also breached NASA's satellite dish network. • Suspect: APT10 - Elite hacking unit in China that is also known as Stone Panda or Red Apollo. • The investigation is still ongoing. • It is the process of identifying, preserving, analyzing, and documenting digital evidence. • Focuses on the recovery and investigation of material found in digital services related to cybercrime. • Failure to segment its internal network into smaller segments. • Failure to keep the Information Technology Security Database (ITSD) up-to-date. • Longer solution turnaround time and failure to fix any security-related issues. • Use VLAN to segment into smaller networks. • Update device inventory. • Quick response time and ensure that the solution is done within the required days. It is a method used to ensure accountability to IoT devices. A Device Accountability B Device Acknowledgement C Device Enrollment Device Enrollment is a method used to ensure accountability to IoT devices What type of VLAN is considered as untag? Native VLAN • VLANs are used to create virtual boundaries that only crossed to a router. This allows Network Engineers to easily arranged network connectivity to a specific VLAN. • Known Assets (computer, laptop) in the company can be placed in secured VLAN and connected to all other secured resources. • Also known as Dirty VLANS. • Common practices by companies to put new device connections. • VLAN Hopping - it is a well-known exploit allowing attackers to reside on a VLAN to gain access to network traffic through Switch Spoofing and Double Tagging. 2 Methods • Switch Spoofing - attacking host imitates the trunk switch. • Double Tagging - attacker adds/modifies tags on the instructional bits of information switch protocols use to direct traffic called Ethernet frames to allow sending the packets through to any VLAN. It is the process of logically segmenting a group of stations into smaller networks VLAN (Virtual Local Area Network) It is a term used to describe the method of attacking a network by gaining access to packets to a port that is not normally accessible from a given system to an existing location. A Data Spoofing B Data Tagging C VLAN Spoofing D VLAN Hopping VLAN Hopping Which OSI Layer do VLANs function? Data Link Layer because VLANs function on Switches • North-to-South Traffic - Any communication between components of a data center and another system, which is physically out of the boundary of the data center, is referred to as north-south traffic. • North-south traffic usually includes queries, commands, and data in general, being requested from a data center or stored in one. • East-to-West Traffic - Any communication between two or more components of a data center, or even communication between different data centers, is referred to as east-west traffic. • It occurs when routers within a data center exchange table information, or when a LAN client communicates with a server in the data center. • It has grown extensively because organizations now prefer private cloud infrastructure East to West infections are when malware spreads spreads to devices on the same? A Subnet B WAN C Latitude Subnets • It provides total network security to an organization. • It can be deployed either on Layer 2 or Layer 3 in an OSI model. This varies because it still depends on the organization's needs. WHICH OSI Layer talks about Layer 2 and Layer 3? Data Link and Network Layer • It interacts with the flow of data representing a device's hardware information like MAC Address. • MAC (Media Access Control) Access is also known as "Physical Address" or "Hardware Address". It is a unique, 12-character alphanumeric attribute that is used to identify individual electronic devices on a network. • Open CMD > enter ipconfig /all • It routes traffic with logical or interchangeable assignments such as IP Addresses. • IP Address is a unique numerical identifier for every device or network that connects to the internet. • Open CMD > enter ipconfig • Identify and authorize devices • Protect resources • Separate user access • Quarantined compromised devices. • Genian NAC Policy Server - Provides instant visibility of all active nodes on any network regardless of network infrastructure. Rapidly deploy AWS Cloud Policy Server via AMI and provision associated On-Prem network Sensor in minutes. • Microsoft Intune - NAC Integration IEEE’s 802.1x Framework • IEEE stands for Institute of Electrical and Electronics Engineers • Framework for passing authentication over wired or wireless LAN. • Credentials are sent to a specified server (RADIUS) which handles the actual user's verification IEEE’s 802.1x Framework RADIUS Framework • RADIUS stands for Remote Authentication Dial-In User Service. • It acts as a broker between a centralized database (e.g. Active Directory) and the endpoint that needs to be authenticated. • It promotes an additional level of administrative delegation by using AAA framework (Authentication, Authorization, and Accounting. RADIUS Framework RADIUS AAA Fingerprinting • It is used to identify endpoints. • It can analyze the device operating system, the type of version of web browser being used, and what resources the device is trying to connect to. Fingerprinting Captive Portals • It is used to combat unauthorized access by using a quality network access control system that can redirect unrecognized devices. Captive Portal Configurations on a Secured Network • Monitoring settings • User login sources • Apply Access Control List (ACL). These are set of rules that assign network access to newly connected devices, configurable IPs, and port access availability on endpoint. Custom Policy Check • User experience customization to suit the organization's needs • Example: BYOD (Bring Your Own Device) will be redirected to portal registration. • Acquire requirements for cybersecurity. Ex: PCI Compliance and HIPAA Compliance. • It is applicable to non-compliant devices. • It is enforced on L2 and L3 in OSI Model • Real-time compliance checks to consume live feeds. • Scrut - is a compliance automation platform that monitors and collects evidence of an organization's security controls. • It brings ISO 27001, SOC 2, GDPR, PCI DSS, CCPA, and HIPAA compliance into a singleplatform. It helps you get real-time monitoring and updates to ensure controls are fully operational. • Hyperproof - It is a security assurance and compliance operations platform that empowers the organization to be compliant with regulatory requirements. • It optimizes your compliance management and security to organize, standardize, and automate the work. • The compliance framework includes SOC2, ISO 27001, NIST 800-53, NIST CSF, NIST privacy, PCI, SOX, and many more. Additionally, it allows you to upload custom frameworks and manage them on the platform. • It is a combination of Network frameworks. • Gather directories, RADIUS accounting logs, DHCP server, NetFlow and SFlow collectors, and device fingerprinting to maintain share awareness of connected devices and create smarter security enrollment • NAC Integrations that benefit from shared endpoint data include bandwidth managers, firewalls, identity access managers, endpoint security systems, secure gateways, content filters, SIEM, and RADIUS Accounting. • IDP/IPS, ATP • Patterned by Cyber Kill Chain Frameworks • WireShark - It trace connections, view the contents of suspect network transactions and identify bursts of network traffic. • Nmap - also known as Network Mapper. It is a free and open-source tool used for vulnerability checking, port scanning, and, of course, network mapping. • Neesus - it discovers weaknesses within your attack surface to pinpoint where to pen test and decrease your cyber risk. • MENTOR: G.L Jackson, PhD • Christopher Marquez • Former Students • Future Students Create your IDEAL Secured Network Design that you can think of that may help the company's daily operation. This will help to manifest your goals towards adding new skills in Cybersecurity. https://clintonwhitehouse4.archives.gov/WH/EOP/NSC/html/docume nts/NSCDoc3.html https://climbtheladder.com/10-vlan-numbering-best-practices/ https://www.forbes.com/sites/emilsayegh/2023/02/21/spotlight-onapt10/?sh=343d60a6491e