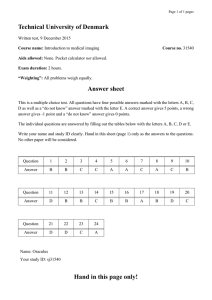
lOMoARcPSD|17716303 Cyber sec mcqs ca2 Cybersecurity (Richfield Graduate Institute of Technology) Studocu is not sponsored or endorsed by any college or university Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Skip to main content 1 CYBER SECURITY 700(2022S1CBS700) Dashboard My courses CYBER SECURITY 700(2022S1CBS700) Welcome to Cyber Security 700 - BSC IT_YEAR 3 2022_REVIEW QUESTION Started on State Wednesday, 25 May 2022, 7:22 PM Finished Completed on Wednesday, 25 May 2022, 7:23 PM Time taken 54 secs Marks 0.00/50.00 Grade 0.00 out of 100.00 Question 1 Not answered Marked out of 1.00 Not flaggedFlag question Question text ___________ refers to the extent to which staff understands the importance of information security. Select one: a. Security awareness b. Security culture c. Security policy Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 d. Secuirty behaviour Feedback The correct answer is: Security awareness Question 2 Not answered Marked out of 1.00 Not flaggedFlag question Question text An act which involves leaking sensitive information to other employees or competitors is an example of which type of behaviour? Select one: a. Malicious behaviour b. Non-accidental behaviour c. Negligent behaviour d. Accidental behaviour Feedback The correct answer is: Malicious behaviour Question 3 Not answered Marked out of 1.00 Not flaggedFlag question Question text In documentation and records management, the life cycle of records is distinguished into three stages. These are ___________ Select one: a. Completed, Semi Completed and Inactive. Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 b. Active, Semi Active and Dormant. c. Active, Semi Active and Inactive. d. Completed, Semi Completed and Dormant. Feedback The correct answer is: Active, Semi Active and Inactive. Question 4 Not answered Marked out of 1.00 Not flaggedFlag question Question text According to the European Union Agency for Network and Information Security (ENISA), the three main processes in the development of an information security awareness program are ______________________ Select one: a. Design and Develop; Implement and Monitor; Analyse and Change b. Plan, Assess and Design; Execute and Manage; Evaluate and Adjust c. Assess and Design; Execute and Manage; Analyse and Change d. Plan, Design and Develop; Execute and Manage; Evaluate and Adjust Feedback The correct answer is: Plan, Assess and Design; Execute and Manage; Evaluate and Adjust Question 5 Not answered Marked out of 1.00 Not flaggedFlag question Question text The acronym “BYOD” as an IT strategy/ policy in organisations stands for ___________ Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Select one: a. Bring your own Data b. Bring your own Dungle c. Bring your organisation Device d. Bring your own Device Feedback The correct answer is: Bring your own Device Question 6 Not answered Marked out of 1.00 Not flaggedFlag question Question text As a cyber security consultant for a company that handles a lot of documentation and communication, which tools would you reccomend for broader information management? Select one: a. Management Information System and Decision information system b. File servers and databases. c. Document management system or a Records management system d. Databases and management information system Feedback The correct answer is: Document management system or a Records management system Question 7 Not answered Marked out of 1.00 Not flaggedFlag question Question text Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Internal staff may also cause security problems to the organisation. These can be categorised as ___________ Select one: a. Negligent and accidental. b. Malicious and non-malicious. c. Accidental and non-malicious. d. Negligent and malicious. Feedback The correct answer is: Malicious and non-malicious. Question 8 Not answered Marked out of 1.00 Not flaggedFlag question Question text A behaviour that does not involve a motive to cause harm but does involve a conscious decision to act inappropriately is called ___________ Select one: a. Accidental behaviour b. Non-accidental behaviour c. Negligent behaviour d. Malicious behaviour Feedback The correct answer is: Negligent behaviour Question 9 Not answered Marked out of 1.00 Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Not flaggedFlag question Question text The human resource department has just informed you about the termination of employment of an employee. As the Information security manager, which of the following action should you take with immediate effect? Select one: a. Check the CCTV footage for any suspcious activity. b. Revoke access to all authorised applications and software. c. Compile a report about what the employee has been up to. d. Invite the employee to hand over anything that belongs to the I.T department. Feedback The correct answer is: Revoke access to all authorised applications and software. Question 10 Not answered Marked out of 1.00 Not flaggedFlag question Question text As an information security manager, one of your security officers comes to you complaining about an application that the company uses, but is blocked by the security tools you have recently implemented. Which of the option below will be the best course of action to take? Select one: a. Whitelisting the application. b. Turning off the new security tools. c. Blacklisting the application. d. Acquire a new application that won’t be blocked by the new system. Feedback The correct answer is: Whitelisting the application. Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Question 11 Not answered Marked out of 1.00 Not flaggedFlag question Question text Which of the following is concerned with monitoring and controlling access to computer networks and access to all or part of the network management information obtained from the network nodes. Select one: a. Accounting management b. Fault management c. Configuration management d. Security management Feedback The correct answer is: Security management Question 12 Not answered Marked out of 1.00 Not flaggedFlag question Question text As the I.T technical officer of a security sensitive company, you receive a call that everyone at your busiest branch in town cannot access the company’s multi million-dollar application, what are the four steps that you should take to fix the problem? Select one: a. Isolate location from the rest, reconfigure or modify to minimise damage, repair or replace, and finally inform your supervisor. b. Inform your supervisor about the problem, determine fault location, isolate location from the rest and finally assign best person to fix the problem. Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 c. Inform your supervisor about the problem, ask those affected, and fix the problem. d. Determine fault location, isolate location from the rest, reconfigure or modify to minimise damage and finally repair or replace. Feedback The correct answer is: Determine fault location, isolate location from the rest, reconfigure or modify to minimise damage and finally repair or replace. Question 13 Not answered Marked out of 1.00 Not flaggedFlag question Question text The acronym “VPN” stands for ________________ Select one: a. Virtualised private network. b. Virtualised public network. c. Virtual public network. d. Virtual private network. Feedback The correct answer is: Virtual private network. Question 14 Not answered Marked out of 1.00 Not flaggedFlag question Question text ________________ is a term used when two or more devices have the same IP Address on the same network Select one: Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 a. IP Duplicate b. IP Same c. IP Conflict d. IP Equal Feedback The correct answer is: IP Conflict Question 15 Not answered Marked out of 1.00 Not flaggedFlag question Question text According to ISO in Cyber Security Network Management, which of the following has the five correct functional areas? Select one: a. Fault management, Accounting management, Configuration management, Perfomance management and Security management. b. Installation management, Networking management, Configuration management, Monitoring management and Security management. c. Fault management, Design management, Configuration management, Networking management and Security management. d. Installation management, Networking management, Configuration management, Perfomance management and Security management. Feedback The correct answer is: Fault management, Accounting management, Configuration management, Perfomance management and Security management. Question 16 Not answered Marked out of 1.00 Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Not flaggedFlag question Question text ________________ is concerned with initialising a network and gracefully shutting down part or all of the network. Select one: a. Security management b. Performance management c. Configuration management d. Fault management Feedback The correct answer is: Configuration management Question 17 Not answered Marked out of 1.00 Not flaggedFlag question Question text DNS stands for ________________ Select one: a. Dynamic Name Server b. Domain Name System c. Dynamic Name System d. Domain Name Source Feedback The correct answer is: Domain Name System Question 18 Not answered Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Marked out of 1.00 Not flaggedFlag question Question text A private network that is configured within a public network in order to take advantage of the economies of scale and management facilities of large networks is called ________________ Select one: a. APN b. CPN c. VPN d. BPN Feedback The correct answer is: VPN Question 19 Not answered Marked out of 1.00 Not flaggedFlag question Question text The Acronym “IP” in IP address stands for ________________ Select one: a. International protocol b. Internal protocol c. Internet protocol d. Intranet protocol Feedback The correct answer is: Internet protocol Question 20 Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Not answered Marked out of 1.00 Not flaggedFlag question Question text The facilities that enable the detection, isolation and correction of abnormal operation of the OSI environment is ________________ Select one: a. Security management b. Accounting management c. Fault management d. Configuration management Feedback The correct answer is: Fault management Question 21 Not answered Marked out of 1.00 Not flaggedFlag question Question text A DoS attack in which multiple systems are used to flood servers with traffic in an attempt to overwhelm available resources making them unavailable to respond to legitimate users is known as ……………………. Select one: a. CDoS Attack b. BDoS Attack c. DDoS Attack d. DSoS Attack Feedback Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 The correct answer is: DDoS Attack Question 22 Not answered Marked out of 1.00 Not flaggedFlag question Question text A management technique that monitors local network traffic to identify applications (and, in some cases, operating systems) that are in need of patching is ……………………. Select one: a. Agent-based scanning b. Agentless Scanning c. Passive networking monitoring d. None of the options listed Feedback The correct answer is: Passive networking monitoring Question 23 Not answered Marked out of 1.00 Not flaggedFlag question Question text ________is a network attack in which an unauthorized person gains access to a network and stays there, undetected, for a long period of time. Select one: a. Worms b. Social Engineering attack c. Advanced Persistent threat Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 d. Botnet attack Feedback The correct answer is: Advanced Persistent threat Question 24 Not answered Marked out of 1.00 Not flaggedFlag question Question text A category of threat that occurs as a result of Individuals, groups, organizations, or states that seek to exploit the organization’s dependence on cyber resources can be categorized as ……………. Select one: a. Adversarial b. Accidental c. Structural d. Environmental Feedback The correct answer is: Adversarial Question 25 Not answered Marked out of 1.00 Not flaggedFlag question Question text DDoS Attack stands for______ Select one: a. Distributed denial of system attack b. Distributed denial of service attack Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 c. Distributed denial of server attack d. Distributed denial of software attack Feedback The correct answer is: Distributed denial of service attack Question 26 Not answered Marked out of 1.00 Not flaggedFlag question Question text The acronym URL stands for ……………. Select one: a. Uniform resource locator b. Uniform resourceful locator c. Uniform resource location d. Universal resource locator Feedback The correct answer is: Uniform resource locator Question 27 Not answered Marked out of 1.00 Not flaggedFlag question Question text _________is a service on a computer system (usually a server) that delays incoming connections for as long as possible Select one: a. Tarpit Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 b. IPS c. IDS d. HIDS Feedback The correct answer is: Tarpit Question 28 Not answered Marked out of 1.00 Not flaggedFlag question Question text The knowledge established as a result of analyzing information about potential or current attacks that threaten an organization is called ………………………. Select one: a. Threat analysis b. Threat intelligence c. Threat information d. None of the options listed Feedback The correct answer is: Threat intelligence Question 29 Not answered Marked out of 1.00 Not flaggedFlag question Question text A category of threat that occurs as a result of failures of equipment, environmental controls, or software due to aging, resource depletion, or other circumstances that exceed expected operating parameters falls under which category? Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Select one: a. Adversarial b. Accidental c. Environmental d. Structural Feedback The correct answer is: Structural Question 30 Not answered Marked out of 1.00 Not flaggedFlag question Question text IPS stands for________ Select one: a. Intrusion Prevention system b. Intrusion prevention software c. Intrusion prevention service d. Intrusion prevention signal Feedback The correct answer is: Intrusion Prevention system Question 31 Not answered Marked out of 1.00 Not flaggedFlag question Question text Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Which of the options below relates to security policies and the mechanisms and procedures used to enforce that policy. Select one: a. Security inspection b. Security check c. Security gathering d. Security audit Feedback The correct answer is: Security audit Question 32 Not answered Marked out of 1.00 Not flaggedFlag question Question text Which of the following trail records user interactions with the system, such as commands issued, identification and authentication attempts, and files and resources accessed Select one: a. User-level audit trail b. Design-level audit trail c. Unit-level audit trail d. System-level audit trail Feedback The correct answer is: User-level audit trail Question 33 Not answered Marked out of 1.00 Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Not flaggedFlag question Question text The process by which you verify an information when conducting a security investigation is referred to as …………. Select one: a. Access control b. Non repudiation c. Authentication d. Integrity Feedback The correct answer is: Authentication Question 34 Not answered Marked out of 1.00 Not flaggedFlag question Question text ________is/are used to detect security violations in an application or to detect flaws in the application’s interaction with the system Select one: a. Intelligence gathering trail b. System-level audit trail c. Application-level audit trail d. Security-level audit trail Feedback The correct answer is: Application-level audit trail Question 35 Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Not answered Marked out of 1.00 Not flaggedFlag question Question text Which of the option below is used to trace the activity of an individual user over time Select one: a. Unit-level audit trail b. User-level audit trail c. Design-level audit trail d. System-level audit trail Feedback The correct answer is: User-level audit trail Question 36 Not answered Marked out of 1.00 Not flaggedFlag question Question text The protocol TCP stands for ………………… Select one: a. Transfer control protocol b. Transmission control protocol c. Transmit control protocol d. Transreceiver control protocol Feedback The correct answer is: Transmission control protocol Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Question 37 Not answered Marked out of 1.00 Not flaggedFlag question Question text The process that ensures that data or information has not been altered during transmission is called …………. Select one: a. Authentication b. Integrity c. Authorisation d. Access control Feedback The correct answer is: Integrity Question 38 Not answered Marked out of 1.00 Not flaggedFlag question Question text Which of the following is a process that produces information systems reports that address threats, capabilities, vulnerabilities, and inherent risk changes? Select one: a. Risk identification b. Risk reporting c. Risk Information gathering d. Risk assessing Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Feedback The correct answer is: Risk reporting Question 39 Not answered Marked out of 1.00 Not flaggedFlag question Question text An audit trails that include security-related data generated by firewalls, virtual private network managers, and IPsec traffic can be categorized as ………….. Select one: a. Physical-Access level audit trails b. Network-Level Audit Trails c. Systems-level audit trails d. User-level audit trails Feedback The correct answer is: Network-Level Audit Trails Question 40 Not answered Marked out of 1.00 Not flaggedFlag question Question text Which one of the following is an objective of Internal Audit? Select one: a. It identifies security weaknesses b. All of the options listed c. It provides management with information about the status of security Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 d. It provides an opportunity to improve the information security management system Feedback The correct answer is: All of the options listed Question 41 Not answered Marked out of 1.00 Not flaggedFlag question Question text The process of attempting to trick someone into revealing information falls under which of the following attack? Select one: a. Botnet Attack b. Zero-day threat c. Social Engineering d. Advanced Persistent threat Feedback The correct answer is: Social Engineering Question 42 Not answered Marked out of 1.00 Not flaggedFlag question Question text __________is a process that involves extracting and categorizing qualitative and quantitative data to identify and analyze onsite and offsite patterns and trends. Select one: a. Trend analytic Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 b. Web analytics c. Data analytics d. Pattern analytics Feedback The correct answer is: Web analytics Question 43 Not answered Marked out of 1.00 Not flaggedFlag question Question text ________is an occurrence considered by an organization to have potential security implications to a system or its environment. Select one: a. Security incident b. Security policy c. Security damage d. Security event Feedback The correct answer is: Security event Question 44 Not answered Marked out of 1.00 Not flaggedFlag question Question text A category of threat that occurs as a result of erroneous actions taken by individuals in the course of executing their everyday responsibilities can be categorised as …………….. Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Select one: a. Accidental b. Physical c. Environmental d. Structural Feedback The correct answer is: Accidental Question 45 Not answered Marked out of 1.00 Not flaggedFlag question Question text A branch of technology that appears to emulate human performance, typically by learning, coming to its own conclusions, appearing to understand complex content, engaging in natural dialogs with people, enhancing human cognitive performance is_________ Select one: a. Artificial Intelligence b. Machine Intelligence c. Computer Intelligence d. System intelligence Feedback The correct answer is: Artificial Intelligence Question 46 Not answered Marked out of 1.00 Not flaggedFlag question Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Question text HIDS stands for_______ Select one: a. Host-based intrusion detection server b. Host-based intrusion detection software c. Host-based intrusion detection systems d. Host-based intrusion detection service Feedback The correct answer is: Host-based intrusion detection systems Question 47 Not answered Marked out of 1.00 Not flaggedFlag question Question text 1The process for generating, transmitting, storing, analyzing, archiving, and disposing of log data is called ………………… Select one: a. Log Service b. Log management c. Log information d. Log event Feedback The correct answer is: Log management Question 48 Not answered Marked out of 1.00 Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Not flaggedFlag question Question text A type of patch management technique that requires an agent to be running on each host to be patched, with one or more servers managing the patching process and coordinating with the agents is referred to as_________. Select one: a. Agentless Scanning b. Computer Scanning c. Agent-based scanning d. Passive Networking Monitoring Feedback The correct answer is: Agent-based scanning Question 49 Not answered Marked out of 1.00 Not flaggedFlag question Question text A category of threat that occurs as a result of natural disasters and failures of critical infrastructures on which the organization depends, but which are outside the control of the organization falls under which category below? Select one: a. Environmental b. Adversarial c. Structural d. Accidental Feedback The correct answer is: Environmental Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Question 50 Not answered Marked out of 1.00 Not flaggedFlag question Question text In which of the following does the system captures traffic allowed through firewall, traffic blocked by firewall; bytes transferred; protocol usage; and detected attack activity? Select one: a. Network device log b. Web server log c. Computer log d. Operating system logs Feedback The correct answer is: Network device log Finish review Jump to... Jump to... Skip <span id="mod_quiz_navblock_title">Quiz navigation</span> Quiz navigation Show one page at a time Finish review You are logged in as PRAYER MALUKA (Log out) 2022S1CBS700 Search Modules Higher Education and Training (HET) Technical, Vocational, Education and Training (TVET) Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com) lOMoARcPSD|17716303 Short Learning Program (SLP) Misc Staff Resources Email How to Log in to Microsoft Office 365 PressReader eLibraries Digital Library User Guide Springer eBooks Conferences & Events Code of conduct Work Readiness Program (WRP) Distinguished Speaker (Muhammad Sijmee) Video Bursaries and Graduate Programme Standard Bank Youth Development and Employment Programmes Get the mobile app Switch to the standard theme Downloaded by Kgothatso Selepe (mkayselepe27.com@gmail.com)