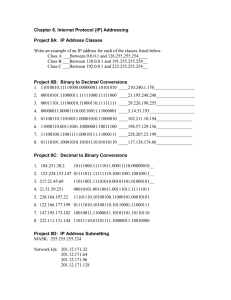
SCS 2205 Computer Networks I IP Addressing Communication - Communication is happening everywhere Plants communicate with each other Immune system Ant colony Communication Our Ancestors used - Pigeons Flags Light Sounds Communication Still we use those methods Importance of Communication - Global Village Computer Network - Connection between two or more computers for the purpose of sharing resources. OSI Model There are seven leyers Each layer has set of protocols Each layer has specific tasks Headers Important Refresh your knowledge in Computer System - Binary Numbers IP Addresses ● Structure of an IP address ● Classful IP addresses ● Limitations and problems with classful IP addresses ● Subnetting ● CIDR ● Supernetting ● NAT IP Addresses IP Addresses What is an IP Address? ● An IP address is a unique global address for a network interface ● Exceptions: ● ○ Dynamically assigned IP addresses ○ IP addresses in private networks An IP address: - is a 32 bit long identifier - encodes a network number (network prefix) and a host number Network prefix and host number ● The network prefix identifies a network and the host number identifies a specific host (actually, interface on the network). network prefix ● host number How do we know how long the network prefix is? ○ Before 1993: The network prefix is implicitly defined (see class-based addressing) or ○ After 1993: The network prefix is indicated by a netmask. Dotted Decimal Notation ● IP addresses are written in a so-called dotted decimal notation ● Each byte is identified by a decimal number in the range [0..255]: ● Example: 10000000 1st Byte = 128 10001111 2nd Byte = 143 10001001 3rd Byte = 137 128.143.137.144 10010000 4th Byte = 144 Select the correct IP addresses 198.168.255.10 198.256.20.45 198.2462.251.26 -198.256.20.10 xxxx xxxx. xxxx xxxx. xxxx xxxx. xxxx xxxx There are four sections and one section is between 0 - 255 Example ● Example: cs.virginia.edu 128.143 137.144 ● Network address is: ● Host number is: ● Netmask is: ● Prefix or CIDR notation: 128.143.137.144/16 ○ 128.143.0.0 (or 128.143) 137.144 255.255.0.0 (or ffff0000) Network prefix is 16 bits long Classful IP Addresses (Until 1993) ● When Internet addresses were standardized (early 1980s), the Internet address space was divided up into classes: ● ○ Class A: Network prefix is 8 bits long ○ Class B: Network prefix is 16 bits long ○ Class C: Network prefix is 24 bits long Each IP address contained a key which identifies the class: ○ Class A: IP address starts with “0” ○ Class B: IP address starts with “10” ○ Class C: IP address starts with “110” The old way: Internet Address Classes The old way: Internet Address Classes The old way: Internet Address Classes Problems with Classful IP Addresses ● By the early 1990s, the original classful address scheme had a number of problems ○ Flat address space. Routing tables on the backbone Internet need to have an entry for each network address. When Class C networks were widely used, this created a problem. By the 1993, the size of the routing tables started to outgrow the capacity of routers. Other problems: ○ Too few network addresses for large networks ■ Class A and Class B addresses were gone ○ Limited flexibility for network addresses: ■ Class A and B addresses are overkill (>64,000 addresses) ■ Class C address is insufficient (requires 40 Class C addresses) Allocation of Classful Addresses Special IP Addresses ● Reserved or (by convention) special addresses: Loopback interfaces ● all addresses 127.0.0.1-127.255.255.255 are reserved for loopback interfaces ● Most systems use 127.0.0.1 as loopback address ● loopback interface is associated with name “localhost” IP address of a network ● Host number is set to all zeros, e.g., 128.143.0.0 Broadcast address ● Host number is all ones, e.g., 128.143.255.255 ● Broadcast goes to all hosts on the network ● Often ignored due to security concerns ● Test / Experimental addresses (Private IPs) Certain address ranges are reserved for “experimental use”. Packets should get dropped if they contain this destination address (see RFC 1918): 10.0.0.0 - 10.255.255.255 172.16.0.0 - 172.31.255.255 192.168.0.0 - 192.168.255.255 ● Convention (but not a reserved address) Default gateway has host number set to ‘first’ or ‘last’ number: 192.0.1.1 or 192.0.1.254 Subnetting ● Problem: Organizations have multiple networks which are independently managed ○ Solution 1: Allocate a separate network address for each network ■ Difficult to manage ■ From the outside of the organization, each network must be addressable. ○ Solution 2: Add another level of University Network Engineeri ng School Medical School Library hierarchy to the IP addressing structure Subnetting Address assignment with subnetting ● Each part of the organization is allocated a range of IP addresses (subnets or subnetworks) ● Addresses in each subnet can be administered locally 128.143.0.0/16 University Network 128.143.71.0/24 128.143.136.0/24 Engineeri ng School Medical School 128.143.56.0/24 Library 128.143.121.0/24 Basic Idea of Subnetting ● Split the host number portion of an IP address into a (smaller) host number. ● Result is a 3-layer hierarchy network prefix ● Then: ■ ■ ■ subnet number and a host number subnet host number number Subnets can be freely assigned within the organization extended network prefix Internally, subnets are treated as separate networks Subnet structure is not visible outside the organization network prefix Subnetmask ● Routers and hosts use an extended network prefix (subnetmask) to identify the start of the host numbers Advantages of Subnetting ● ● With subnetting, IP addresses use a 3-layer hierarchy: ○ Network ○ Subnet ○ Host Reduces router complexity. Since external routers do not know about subnetting, the complexity of routing tables at external routers is reduced. ● Note: Length of the subnet mask need not be identical at all subnetworks. Example: Subnetmask ● 128.143.0.0/16 is the IP address of the network ● 128.143.137.0/24 is the IP address of the subnet ● 128.143.137.144 is the IP address of the host ● 255.255.255.0 is the subnetmask of the host ● When subnetting is used, one generally speaks of a “subnetmask” (instead of a netmask) and a “subnet” (instead of a network) ● Use of subnetting or length of the subnetmask if decided by the network administrator ● Consistency of subnetmasks is responsibility of administrator No Subnetting ● All hosts think that the other hosts are on the same network With Subnetting ● Hosts with same extended network prefix belong to the same network With Subnetting ● Different subnetmasks lead to different views of the size of the scope of the network CIDR - Classless Interdomain Routing ● IP backbone routers have one routing table entry for each network address: ○ With subnetting, a backbone router only needs to know one entry for each Class A, B, or C networks ○ This is acceptable for Class A and Class B networks ■ 27 = 128 Class A networks ■ 214 = 16,384 Class B networks ○ But this is not acceptable for Class C networks 21 ■2 ● ● = 2,097,152 Class C networks In 1993, the size of the routing tables started to outgrow the capacity of routers Consequence: The Class-based assignment of IP addresses had to be abandoned CIDR - Classless Interdomain Routing ● ● Goals: ○ New interpretation of the IP address space ○ Restructure IP address assignments to increase efficiency ○ Permits route aggregation to minimize route table entries CIDR (Classless Interdomain routing) ○ abandons the notion of classes ○ Key Concept: The length of the network prefix in the IP addresses is kept arbitrary ○ Consequence: Size of the network prefix must be provided with an IP address CIDR Notation ● CIDR notation of an IP address: 192.0.2.0/18 ■ "18" is the prefix length. It states that the first 18 bits are the network prefix of the address (and 14 bits are available for specific host addresses) ● CIDR notation can replace the use of subnetmasks (but is more general) ○ IP address 128.143.137.144 and subnetmask 255.255.255.0 becomes 128.143.137.144/24 ● CIDR notation allows to drop traling zeros of network addresses: 192.0.2.0/18 can be written as 192.0.2/18 Why do people still talk about ● CIDR eliminates the concept of class A, B, and C networks and replaces it with a network prefix ● Existing classful network addresses are converted to CIDR addresses: 128.143.0.0 🡪 128.143.0.0/16 ● The change has not affected many (previously existing) enterprise networks ○ Many network administrators (especially on university campuses) have not noticed the change (and still talk about (Note: CIDR was introduced with the role-out of BGPv4 as interdomain routing protocol. ) CIDR address blocks ● ● CIDR notation can nicely express blocks of addresses Blocks are used when allocating IP addresses for a company and for routing tables (route aggregation) CIDR Block Prefix /27 /26 /25 /24 /23 /22 /21 /20 /19 /18 /17 /16 /15 /14 /13 32 64 128 256 512 1,024 2,048 4,096 8,192 16,384 32,768 65,536 131,072 262,144 524,288 # of Host Addresses CIDR and Address assignments ● Backbone ISPs obtain large block of IP addresses space and then reallocate portions of their address blocks to their customers. Example: ● Assume that an ISP owns the address block 206.0.64.0/18, which represents 16,384 (214) IP addresses ● Suppose a client requires 800 host addresses ● With classful addresses: need to assign a class B address (and waste ~64,700 addresses) or four individual Class Cs (and introducing 4 new routes into the global Internet routing tables) ● With CIDR: Assign a /22 block, e.g., 206.0.68.0/22, and allocated a block of 1,024 (210) IP addresses. Subnetting Consider a class “C” IP address : 200.10.15.x Default (subnet) mask (SM): 255.255.255.0 Borrowing 2 bits: SM 255.255.255.192 /26 → 4 subnets @ 62 hosts Borrowing 3 bits: SM 255.255.255.224 /27 → 8 subnets @ 30 hosts Borrowing 4 bits: SM 255.255.255.240 /28 → 16 subnets @ 14 hosts Borrowing 5 bits: SM 255.255.255.248 /29 → 32 subnets @ 6 hosts Borrowing 6 bits: SM 255.255.255.252 /30 → 64 subnets @ 2 hosts Ex. 1. Find the SM for 192.168.2.0/24 that specifies 5 bits of sub-netting? 2. Divide the IP address 172.10.0.0/16 into 100 sub-nets 3. What is the network ID of the following: IP=192.234.34.32 SM=255.255.255.240? 4. How SMs are used to determine the network ID? Another Example Take the 192.168.1.0 class C network but now we’ll chop it into four pieces so we get 4 “blocks”: Another Example We have the same set of questions to answer: ● ● ● ● What are the network addresses? What are the broadcast addresses? What is the subnet mask? What are the usable host IP addresses? The subnet mask is 255.255.255.192 Another Example ● ● Subnet 1: ○ network address: 192.168.1.0 ○ first host: 192.168.1.1 ○ last host: 192.168.1.62 ○ broadcast address: 192.168.1.63 Subnet 2: ○ network address: 192.168.1.64 ○ first host: 192.168.1.65 ○ last host: 192.168.1.126 ○ broadcast address: 192.168.1.127 Another Example ● ● Subnet 3: ○ network address: 192.168.1.128 ○ first host: 192.168.1.129 ○ last host: 192.168.1.190 ○ broadcast address: 192.168.1.191 Subnet 4: ○ network address: 192.168.1.192 ○ first host: 192.168.1.193 ○ last host: 192.168.1.254 ○ broadcast address: 192.168.1.255 Variable Length Subnet Mask (VLSM) In previous subnetting lessons all subnets had a “fixed size”. Each subnet had the same size. For example we took a class C network 192.168.1.0 and divided it 4 blocks: Variable Length Subnet Mask (VLSM) Let’s say I would have the following requirements: ● ● ● ● One subnet for 12 hosts. One subnet for 44 hosts. One subnet for 2 hosts (point-to-point links are a good example where you only need 2 IP host addresses). One subnet for 24 hosts. IP 192.168.1.0 I have 4 subnets so it’s no problem, but I’m still wasting a lot of IP addresses. If we use a block of 64 for our subnet where I only need 2 IP addresses I’m throwing 60 IP addresses away (Network IP, Broadcast IP and 2 IP for host computers. 60 IP wasting). Variable Length Subnet Mask (VLSM) What kind of subnets would we need to fit in these hosts? Let’s see: ● ● ● ● 12 hosts, the smallest subnet would be a block of 16. 44 hosts, the smallest subnet would be a block of 64. 2 hosts, the smallest subnet would be a block of 4. 24 hosts, the smallest subnet would be a block of 32. Variable Length Subnet Mask (VLSM) Because we have different subnet sizes, we need to calculate the subnet mask for each subnet. To find the subnet mask you can use this trick: 256 – subnet size = subnet mask ● ● ● ● Subnet 1: 256 – 64 = 192 so the subnet mask is 255.255.255.192 Subnet 2: 256 – 32 = 224 so the subnet mask is 255.255.255.224 Subnet 3: 256 – 16 = 240 so the subnet mask is 255.255.255.240 Subnet 4: 256 – 4 = 252 so the subnet mask is 255.255.255.252 When using VLSM, make sure you start with the biggest subnet first or you will have overlapping address space. Variable Length Subnet Mask (VLSM) ● ● Subnet 1: (size of 64) ○ network address: 192.168.1.0 ○ first host: 192.168.1.1 ○ last host: 192.168.1.62 ○ broadcast address: 192.168.1.63 Subnet 2: (size of 32) ○ network address: 192.168.1.64 ○ first host: 192.168.1.65 ○ last host: 192.168.1.94 ○ broadcast address: 192.168.1.95 Variable Length Subnet Mask (VLSM) ● ● Subnet 3: (size of 16) ○ network address: 192.168.1.96 ○ first host: 192.168.1.97 ○ last host: 192.168.1.110 ○ broadcast address: 192.168.1.111 Subnet 4: (size of 4) ○ network address: 192.168.1.112 ○ first host: 192.168.1.113 ○ last host: 192.168.1.114 ○ broadcast address: 192.168.1.115 Variable Length SM (VLSM) is the process by which we take a major network address and use different subnet masks at different points. A fixed length mask has the advantage of simplicity. It will be easy for the network staff/users to remember the SM. However, if we have to keep the subnet mask the same we encounter severe problems concerning addressing space. Some useful tips on VLSM: Use as few different masks as possible Keep lookup table to figure out the masks for a given subnet Make sure not to overlap subnets with VLSM When do we need to use different subnet masks? Variable Length SM (VLSM) E1 E2 R R Leased Line Colombo Head Office 100 users Kandy Branch Office 50 users Variable Length SM (VLSM) E1 E2 R R Colombo Head Office 100 users Subnet 1 Subnet 2 Kandy Branch Office 50 users Subnet 3 Variable Length SM (VLSM) E1 100 E2 1 R 1 1 R 1 50 Kandy Branch Office 50 users Colombo Head Office 100 users No of IP Addresses Required 100+50+1+1+1+1 = 154 Variable Length SM (VLSM) For the serial link – needs only 2 IPs SM – 255.255.255.252 IPs – 200.10.15.5 /30 and 200.10.15.6 /30 For Kandy subnet – needs 51 IPs SM – 255.255.255.192 IPs – 200.10.15.65 /26 → E2 and 200.10.15.66 /26 to 200.10.15.110 /26 (m/c) For Colombo subnet – needs 101 IPs SM – 255.255.255.128 IPs – 200.10.15.129 /25 → E1 and 200.10.15.130 /25 to 200.10.15.230 /25 (m/c) When can VLSM be used? VLSM can only be used with a classless routing protocol. Classless routing protocols: RIP Version 2, OSPF Colombo Head Office 100 users 200.10.15.130 – 200.10.15.230/25 E2 200.10.15.65/26 R 200.10.15.6/30 200.10.15.129/25 E1 200.10.15.5/30 Variable Length SM (VLSM) R Kandy Branch Office 50 users 200.10.15.66 – 200.10.15.110 /26 An approach to assigning subnets with VLSMs is documented in RFC 1219. CIDR and Routing ● So what is IP Address Aggregation? Quite simply, IP Address Aggregation means that several networks can be spanned by a single routing entry. Consider the following case: ● Our router needs to route traffic for eight separate networks through the same gateway (ip address 194.1.1.1): ● ip route 66.100.50.0 255.255.255.224 194.1.1.1 ● ip route 66.100.50.32 255.255.255.224 194.1.1.1 ● ip route 66.100.50.64 255.255.255.224 194.1.1.1 ● ip route 66.100.50.96 255.255.255.224 194.1.1.1 ● ip route 66.100.50.128 255.255.255.224 194.1.1.1 ● ip route 66.100.50.160 255.255.255.224 194.1.1.1 ● ip route 66.100.50.192 255.255.255.224 194.1.1.1 ● ip route 66.100.50.224 255.255.255.224 194.1.1.1 ○ ip route 66.100.50.0 255.255.255.0 194.1.1.1 Route Summarization (Aggregation) /18 CIDR and Routing ● Aggregation of routing table entries: ○ 128.142.0.0/16 and 128.143.0.0/16 are represented as 128.142.0.0/15 (142=10001110) ● Longest prefix match: Routing table lookup finds the routing entry that matches the longest prefix For example, consider this routing table: 192.168.20.16/28 192.168.0.0/16 ● When the address 192.168.20.19 needs to be looked up, both entries in the routing table "match". That is, both entries contain the looked up address. In this case, the longest prefix of the candidate routes is 192.168.20.16/28, since its subnet mask (/28) is higher than the other entry's mask (/16), making the route more specific. Network Address Translation (NAT) 60 Private Network ● Private IP network is an IP network that is not directly connected to the Internet ● IP addresses in a private network can be assigned arbitrarily. ○ ● Not registered and not guaranteed to be globally unique Generally, private networks use addresses from the following experimental address ranges (non-routable addresses): ○ 10.0.0.0 – 10.255.255.255 ○ 172.16.0.0 – 172.31.255.255 ○ 192.168.0.0 – 192.168.255.255 61 Network Address Translation (NAT) ● NAT is a router function where IP addresses (and possibly port numbers) of IP datagrams are replaced at the boundary of a private network ● NAT is a method that enables hosts on private networks to communicate with hosts on the Internet ● NAT is run on routers that connect private networks to the public Internet, to replace the IP address-port pair of an IP packet with another IP address-port pair. 62 Main uses of NAT ● Pooling of IP addresses ● Supporting migration between network service providers ● IP masquerading ● Load balancing of servers 63 Pooling of IP addresses ● Scenario: Corporate network has many hosts but only a small number of public IP addresses ● NAT solution: ○ Corporate network is managed with a private address space ○ NAT device, located at the boundary between the corporate network and the public Internet, manages a pool of public IP addresses ○ When a host from the corporate network sends an IP datagram to a host in the public Internet, the NAT device picks a public IP address from the address pool, and binds this address to the private address of the host 64 Pooling of IP addresses 65 Supporting migration between network service providers ● Scenario: In CIDR, the IP addresses in a corporate network are obtained from the service provider. Changing the service provider requires changing all IP addresses in the network. ● NAT solution: ○ Assign private addresses to the hosts of the corporate network ○ NAT device has static address translation entries which bind the private address of a host to the public address. ○ Migration to a new network service provider merely requires an update of the NAT device. The migration is not noticeable to the hosts on the network. Note: ○ The difference to the use of NAT with IP address pooling is that the mapping of public and private IP addresses is static. 66 Supporting migration between network service providers 67 IP masquerading ● Also called: Network address and port translation (NAPT), port address translation (PAT). ● Scenario: Single public IP address is mapped to multiple hosts in a private network. ● NAT solution: ○ Assign private addresses to the hosts of the corporate network ○ NAT device modifies the port numbers for outgoing traffic 68 IP masquerading 69 Load balancing of servers ● Scenario: Balance the load on a set of identical servers, which are accessible from a single IP address ● NAT solution: ○ ○ ○ ○ Here, the servers are assigned private addresses NAT device acts as a proxy for requests to the server from the public network The NAT device changes the destination IP address of arriving packets to one of the private addresses for a server A sensible strategy for balancing the load of the servers is to assign the addresses of the servers in a round-robin fashion. 70 Load balancing of servers 71 Concerns about NAT ● Performance: ○ Modifying the IP header by changing the IP address requires that NAT boxes recalculate the IP header checksum ○ ● Modifying port number requires that NAT boxes recalculate TCP checksum Fragmentation ○ Care must be taken that a datagram that is fragmented before it reaches the NAT device, is not assigned a different IP address or different port numbers for each of the fragments. 72 Concerns about NAT ● End-to-end connectivity: ○ NAT destroys universal end-to-end reachability of hosts on the Internet. ○ A host in the public Internet often cannot initiate communication to a host in a private network. 73 End of Lecture Any Questions?