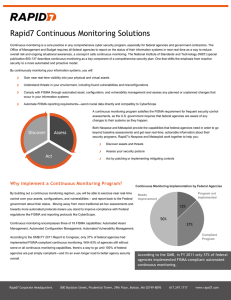
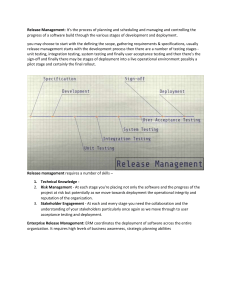
Enterprise Deployment Package Insight and integrated results through vulnerability management PRIMARY GOALS: • • • Create an automated and scalable vulnerability scanning method Leverage an existing vulnerability management solution Provide actionable insight and metrics to technical security team • Report consumable results to senior leadership and stakeholders • Measure program value and success over time Overview The Enterprise Deployment Package (EDP) is designed to drive maximum security-posture insight and consumable, integrated results through vulnerability management. The following methodology outlines the seven key steps to execution. Methodology STEP 1: Deploy A sound architecture will be the basis for all future discovery and scanning. This can have a large impact on the amount of time a scan takes as well as the impact to overall network bandwidth. Collaboratively, Rapid7 will develop a scalable architecture for deployment and facilitate efficient discovery and scanning of in-scope assets. If a product has already been implemented, Rapid7 will review the architecture, deployment, and configurations as input into the Nexpose solution architecture. STEP 2: Discover New assets are added every day and networks are constantly evolving in any enterprise environment. It is imperative to discover and include newly provisioned assets and networks as part of ongoing vulnerability scans. To facilitate this, Rapid7 will develop and implement an Active Reconnaissance (AR) strategy that will continuously discover newly provisioned assets and include them in ongoing scans. 1. Develop Active Reconnaissance (AR) strategy 2. Create Scripts to support AR and run without affecting future vulnerability scans 3. Integrate with IPAM or other asset / IP management solutions* | Rapid7.com Service Brief: Enterprise Deployment Package 01011011101010 10001011010100 STEP 3: Configure STEP 6: Monitor The configuration of Nexpose will be strategically customized to meet the needs of the business and associated operations. Scan templates, schedules and policy compliance will all be tailored to fit asset availability as well as frequency requirements. User accounts and access will be customized based on that user’s role and responsibilities. While reports are a great tool for point-in-time analysis, real-time monitoring is achieved through a customized dashboard comprised of impactful metrics and analytics with trending. Rapid7 will design and customize a dashboard to give realtime insight into key metrics and analytics around vulnerability management and program success. STEP 4: Report Real-Time Dashboard and Program Success Scorecard: Each organization has its own way of consuming data, and a successful product deployment means evaluating those needs, meeting those needs, and anticipating future needs. As part of this phase, reports will be developed, customized, and scheduled based on the “reader” with a focus on being actionable and consumable. • Organizational risk over time STEP 5: Integrate STEP 7: Train and Document To gain maximum insight, Nexpose needs to be effectively integrated into existing solutions and processes, such as GRC and SIEM.* Rapid7 will develop and define workflows while implementing, testing, and integrating with other existing technologies. All constituents will be trained to the appropriate level to support their respective duties and tasks associated with the program. Furthermore all information relative to the architecture, deployment and configuration will be documented in an as-built guide, including architecture, configuration, scanning profiles, report customizations and supporting workflows. • Monetary correlation with risk, remediation and program success • Number of assets in compliance • Remediation tracking and time-to- close for asset categorizations • Trend analysis over time for remedi- ation and vulnerabilities TRAINING OUTLINE • Administrator: Operate, administer and customize Nexpose, including scan scheduling, asset/ site creation, rights assignment, scan template creation and report template creation • Operator: Operate current scan schedules, ad-hoc scans and use appropriate scan and report templates • Asset / Business owner: View information relative to their in-scope assets, view dashboard information, run reports as-needed, interpret and consume relevant information for assets, vulnerabilities and remediation steps • Engineer: Customize and create custom reports, integrations, data exporting and usage of the API and Ruby GEM Ready to Get Started? Call: 866.7.RAPID7 Email: sales@rapid7.com Visit: www.rapid7.com/services *Standardized integrations can be found here: http://www.rapid7.com/company/partners/integration-partners.jsp | Rapid7.com Service Brief: Enterprise Deployment Package