Networking: Presentation & Application Layers, JPEG, HTTP, DNS
advertisement

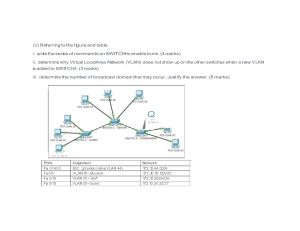
Module 5: Presentation Layer & Application Layer 2. Discuss the steps required for compressing an image using JPEG. JPEG (Joint Photographic Experts Group) is a popular image compression format that can reduce the size of digital images while maintaining acceptable image quality. Preprocessing: Preprocessing steps include color space conversion, downsampling, and other preprocessing steps to prepare images for compression. Divide the image into blocks: The most common size for images is 8x8 pixels, but other sizes are also possible. Apply the Discrete Cosine Transform (DCT): The DCT converts pixel values from the spatial domain to the frequency domain, allowing the JPEG algorithm to identify and discard high-frequency information that is less important for human perception. Quantization: The quantization table discards high-frequency information and can be adjusted to control compression and image quality. Entropy coding: Quantized frequency coefficients are encoded using entropy coding techniques such as Huffman coding or arithmetic coding, which reduce the size of the encoded data. Compress the image: The compressed image is then written to a file in the JPEG format. Decompression: Compression is necessary to view the compressed image, using the inverse of the above steps. Higher levels of compression and image quality can be controlled by adjusting the quantization table and other parameters in the JPEG algorithm, but higher levels of compression typically result in lower image quality. 3. Explain persistent HTTP with a neat diagram. Persistent HTTP (also known as HTTP keep-alive or HTTP connection reuse) is a feature of the HTTP protocol that allows multiple requests and responses to be sent over a single TCP connection. This reduces the overhead of establishing and tearing down connections for each request/response pair, leading to improved performance and reduced latency. Client Server | | | Request #1 (GET /) | |--------------------------------> | | | | Response #1 (HTML) | |<-------------------------------| | | | Request #2 (GET /image) | |--------------------------------> | | | | Response #2 (image) | |<-------------------------------| | | | ... | | | | Request #n (GET /) | |--------------------------------> | | | | Response #n (HTML) | |<-------------------------------| | | In this diagram, the client initiates multiple HTTP requests to the server over a single TCP connection. Each request is identified by a unique request/response pair. The client sends a request to the server to reuse an existing TCP connection, and the server acknowledges this request by including a "Connection: keep-alive" header in its response. The server sends a response back to the client, allowing the client to send additional requests without establishing a new connection. This process continues until either the client or server closes the connection or a timeout occurs. Persistent HTTP can improve performance by reducing the overhead of establishing and tearing down TCP connections, but it can also consume server resources and may not be appropriate for all requests. 4. Explain the two application layer paradigms in detail. Client-server and P2P are two application layer paradigms that involve communication between networked devices, but differ in how they interact and exchange information. Client-Server Paradigm: Client-server paradigm involves two types of networked devices: clients and servers. Clients initiate requests for services and resources, while servers provide them. The client-server paradigm is a hierarchical model of network communication where clients are end-user devices and servers provide services or resources to them. Communication is initiated by the client, who sends a request to the server using a standardized protocol. The server processes the request and sends a response back to the client, usually in the form of data or a service. The client-server paradigm offers several advantages, such as scalability, security, and reliability. Servers are more powerful than clients, allowing them to handle a large number of requests simultaneously. The hierarchical model also allows for centralized control and management of network resources, improving security and reliability. Peer-to-Peer (P2P) Paradigm: In the peer-to-peer paradigm, all networked devices are considered equal and can act as both clients and servers at the same time. Each device can initiate or respond to requests for services or resources. The P2P paradigm is a decentralized model of network communication, allowing for more flexible and dynamic network topologies where devices can join or leave the network at any time. In P2P networks, communication is initiated by a device that wants to share or access a resource. The device broadcasts a request to all other devices in the network, and any device that has the resource can respond to the request by providing it directly to the requesting device. P2P networks offer several advantages, such as scalability, fault-tolerance, and resilience. There is no centralized server, making them highly scalable and able to handle a large number of devices and resources. Fault-tolerance and resilience ensure the network can continue to function even if some devices or resources fail or leave the network. Client-server and P2P paradigms have their advantages and disadvantages, and the choice of one depends on the application or system being developed. 5. Elaborate the process of E-Mail transfer. The process of email transfer involves several steps, which are as follows: Compose the Email: The first step is to compose an email, which involves writing the message, adding attachments, and specifying the recipient's email address. Sender's Mail Server: The sender's mail server is responsible for sending the email to the recipient's mail server. DNS Resolution: The sender's mail server needs to resolve the recipient's mail server's domain name before sending an email. This is done by querying the Domain Name System (DNS) to obtain the recipient's IP address. Sender's Mail Server Sends the Email: The sender's mail server establishes a connection with the recipient's mail server to send an email. Recipient's Mail Server: The recipient's mail server stores the email in its mail transfer agent (MTA) queue. Email Delivery: The recipient's mail server delivers the email to the recipient's mailbox or forwards it to another mail server if it is not hosted on the recipient's server. Recipient's Email Client: The recipient's email is downloaded from the mail server to their device when they open their email client or webmail account. Email Read and Response: The recipient can read, reply, forward, or delete an email. The process of email transfer usually takes only a few seconds, but can take longer if there are issues with the sender's or recipient's mail servers or if the email is large or contains many attachments. Simple Mail Transfer Protocol (SMTP) is a standard protocol for email transmission over the Internet, which ensures reliable and secure delivery. 6. Write a note on the Domain Name System. The Domain Name System (DNS) is a hierarchical and distributed naming system used to map human-readable domain names to numerical IP addresses that identify networked devices on the Internet. It serves as the phone book of the Internet, allowing users to access websites and other resources by their domain name, rather than having to remember the IP address. DNS uses a hierarchical tree-like structure of domain names, with each domain name consisting of one or more labels separated by dots. Top-level domains (TLDs) are located at the root of the tree, and include generic TLDs such as .com, .org, and .net, as well as country-code TLDs. DNS is a system of servers that resolve domain names to IP addresses, consisting of three main types. Root servers: Top-level DNS servers provide information about TLDs and serve as the starting point for DNS queries. Authoritative servers: TDNS servers store and provide information about a domain name, including its IP address. Recursive servers: DNS servers process DNS queries and query other servers to resolve the requested domain name. When a user types a domain name into a web browser or other application, their device sends a DNS query to a recursive server, which then queries other DNS servers to resolve the domain name to its corresponding IP address. The IP address is then returned to the device, which uses it to establish a connection with the server hosting the requested resource. The Domain Name System (DNS) is an important part of the Internet, allowing users to access websites and resources using human-readable domain names rather than numerical IP addresses. It is hierarchical and distributed, and relies on a system of DNS servers to resolve domain names to IP addresses. Module 6: Network Design Concepts 1. Compare the concepts of collision domain and broadcast domains. Collision domain and broadcast domain are concepts in computer networking that describe how network traffic flows and is managed. Network collisions occur when two or more devices on the same network try to transmit data at the same time, causing the data to become garbled and requiring retransmission. A collision domain is the portion of a network where network collisions can occur, and all devices connected to the same segment are part of the same collision domain. Broadcast traffic is traffic that is sent to all devices on a network, rather than to a specific device. It is used for tasks such as network discovery, address resolution, and network management. Devices connected to the same network segment are part of the same broadcast domain, meaning they will all receive broadcast traffic sent on that segment. Collision domain and broadcast domain are related concepts, but they refer to different aspects of network behavior and are not interchangeable. Collision domain refers to the portion of a network where network collisions can occur, while broadcast domain is the portion of the network where broadcast traffic is forwarded. 2. Write a note on Virtual LAN. A Virtual Local Area Network (VLAN) is a logical grouping of devices in a computer network that behave as if they are on the same physical LAN, even though they may be located on different network segments or physical switches. VLANs are used to group devices based on function, department, or other criteria and allow network administrators to better manage network traffic and security. In a traditional LAN, all devices connected to the same physical switch are part of the same broadcast domain, creating security risks and network congestion. By creating VLANs, network administrators can partition a physical switch into multiple virtual switches, each with its own set of devices and its own broadcast domain. This allows devices on different VLANs to communicate with each other, but not with devices on other VLANs unless routing is specifically enabled. VLANs are typically configured on network switches and can be created based on port, MAC address, or protocol type. They can be used to control network traffic by applying different security policies, Quality of Service (QoS) settings, and other parameters to each VLAN. For example, a network administrator might create a VLAN for all devices in the marketing department or create one specifically for VoIP traffic. VLANs can improve network security and traffic management, as well as improve network performance by reducing the size of broadcast domains and enabling more efficient use of network resources. Network administrators can use VLANs to create flexible and scalable networks that can adapt to changing business needs. Virtual LANs are an important tool for network administrators to manage network traffic, security, and performance. They partition a physical network into multiple virtual networks with their own devices and security policies, allowing for more efficient use of network resources. 3. Write a note on Virtual Private Networks. VPNs are a technology that allows users to establish a secure and encrypted connection between their device and a remote network over the internet. They are often used to provide remote access to corporate networks or to encrypt and secure internet traffic when accessing the internet from public or untrusted networks. A VPN is used to create a private and secure connection over a public network, such as the internet. It uses encryption and tunneling protocols to ensure that data sent over the VPN is protected from eavesdropping, tampering, and interception. When a user connects to a VPN, their device establishes a secure and encrypted tunnel to the VPN server, which is located on the remote network. All data sent and received by the user's device is then transmitted through this tunnel and protected by the encryption provided by the VPN. VPNs provide remote access to corporate networks, allowing employees to securely access resources from anywhere in the world. They can also be used to bypass internet censorship or access geo-restricted content. VPNs are used to connect multiple remote networks together over the internet, while remote access VPNs provide individual users with secure remote access to a network. Virtual Private Networks (VPNs) are an important technology for providing secure and private connections over the internet. They are used to provide remote access to corporate networks or to encrypt and secure internet traffic when accessing the internet from public or untrusted networks. They use encryption and tunneling protocols to ensure data transmitted over the VPN is protected from eavesdropping, tampering, and interception. 4. Draw and explain IEEE 802.1Q frame format. The IEEE 802.1Q is a standard for VLAN tagging in Ethernet frames. It allows network administrators to create and manage VLANs by inserting VLAN tags into Ethernet frames. The VLAN tag consists of a 4-byte header inserted between the Source MAC Address and the EtherType fields in the Ethernet frame. Preamble | Destination MAC Address | Source MAC Address | VLAN Tag | EtherType | Payload | Frame Check Sequence The fields in the IEEE 802.1Q VLAN tag are as follows: Tag Protocol Identifier (TPID): A 2-byte field that identifies the IEEE 802.1Q tagging protocol. It has a fixed value of 0x8100. Priority Code Point (PCP): A 3-bit field that is used to assign priority to Ethernet frames. It is used to support Quality of Service (QoS) in VLANs. Drop Eligible Indicator (DEI): A 1-bit field that is used to indicate whether an Ethernet frame is eligible to be dropped in the event of network congestion. VLAN Identifier (VID): A 12-bit field that identifies the VLAN that the Ethernet frame belongs to. It allows network administrators to create and manage VLANs. The IEEE 802.1Q VLAN tag is inserted between the Source MAC Address and the EtherType fields in the Ethernet frame to identify the VLAN that the frame belongs to. When a switch receives an Ethernet frame with an IEEE 802.1Q VLAN tag, it uses the VID field to determine which VLAN it belongs to. This allows network administrators to control network traffic and improve network security. The IEEE 802.1Q frame format is a standard for VLAN tagging in Ethernet frames. It allows network administrators to create and manage VLANs by inserting VLAN tags into Ethernet frames. The VLAN tag consists of a 4-byte header between the Source MAC Address and the EtherType fields in the Ethernet frame. It includes fields for assigning priority to Ethernet frames, indicating whether frames are eligible to be dropped, and identifying the VLAN that the frame belongs to.