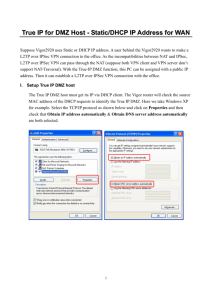
POTENTIAL IMPACT OF INCORRECT CONFIGURATION: FIREWALLS MISCONFIGURATION : • It depends on the person who config the setting or the. • Firewall misconfiguration example : an employee forget to close un used ports on the firewall, so unauthorized access happen here through the unused and opened port , opened and unused ports can do several attacks which can impact and do DOS attack the warmksan company network. VPN MISCONFIGURATION : • VPN used to remote access to the company by creating virtual private network. • VPN misconfiguration example: The engineer forget to select encrypt data choice which will impact in the data , so the C from CIA may be affected by the man in the middle for example HOW IMPLEMENTING DIFFERENT TECHNIQUES CAN BE USE FULL ? • DMZ : if we use this zone to save important things like database server it will be more secure than putting it in student or employees network , so DMZ create kind of secure area. • Static IP: it use-full to make the process to grow smoothly , for example if I give the admin IP access to the DMZ and then the admin IP changed , how will he access to the DMZ again , so we use the static IP to save access to important IP’s in the server. • NAT: adds more secure to the network by represent all users in the same IP when they go the internet which will make the users out of the attack and if some one attack he will attack the NAT IP not the user. NETWORK MONITORING SYSTEM • SNMP: Make us to monitor the network in one unit and save time and money of the fix problems • IPS: This prevents the malware to go inside the network by prevent him out. • IDS: if malware go inside the network , the IDS will detect him and then treat the problem PHYSICAL AND VIRTUAL SECURITY TO HELP INTEGRITY • Physical: -Doors or Access cards: help to save the data center and prevent unauthorized access in the company , and prevent the data change or edit which will save the integrity. • Virtual: -VPN encryption: This kind of security helps to transmit the data and no person on the line can see what is the data or open it so it helps to save the integrity.