Cybersecurity Lecture Notes: Attacks, Cryptography, Firewalls
advertisement
AmanVerma
Q.Diffrentiate Active and Passive Security Attacks
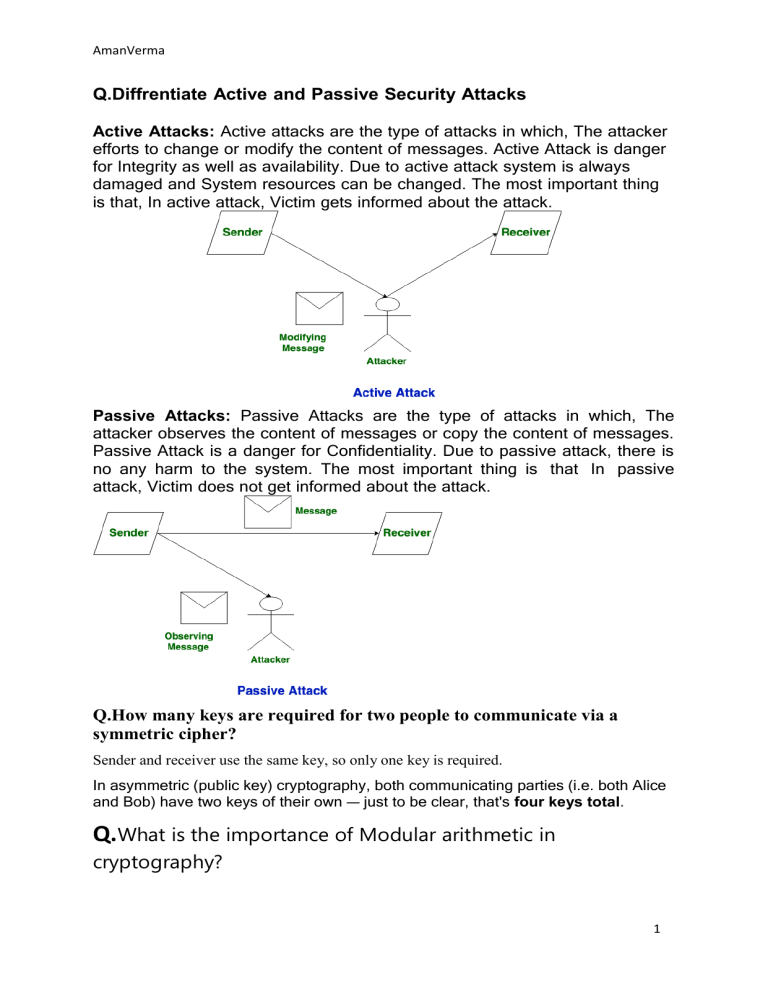
Active Attacks: Active attacks are the type of attacks in which, The attacker
efforts to change or modify the content of messages. Active Attack is danger
for Integrity as well as availability. Due to active attack system is always
damaged and System resources can be changed. The most important thing
is that, In active attack, Victim gets informed about the attack.
Passive Attacks: Passive Attacks are the type of attacks in which, The
attacker observes the content of messages or copy the content of messages.
Passive Attack is a danger for Confidentiality. Due to passive attack, there is
no any harm to the system. The most important thing is that In passive
attack, Victim does not get informed about the attack.
Q.How many keys are required for two people to communicate via a
symmetric cipher?
Sender and receiver use the same key, so only one key is required.
In asymmetric (public key) cryptography, both communicating parties (i.e. both Alice
and Bob) have two keys of their own — just to be clear, that's four keys total.
Q.What is the importance of Modular arithmetic in
cryptography?
1
AmanVerma
Modular arithmetic is a structure of arithmetic for integers, where numbers "wrap
around" upon reaching a specific value. Modular arithmetic enables us to simply
make groups, rings and fields which are the basic constructing piece of most
modern public-key cryptosystems.
For instance, Diffie-Hellman need the multiplicative group of integers modulo a
prime pp. There are different groups which can work. Modular or clock arithmetic is
arithmetic on a circle rather than a number line modulo N, it can use only the twelve
entire numbers from 0 through N-1.
Modular arithmetic is very well understood in method of algorithms for several basic
operations. That is one of the reason why it can use finite fields (AES) in symmetric
key cryptography. Cryptography needed complex problems. Some problems
develop into a hard with modular arithmetic.
For example, logarithms are simply to calculate over all integers but can become
hard to compute when it can introduce a modular reduction. Similarly with
discovering roots. Mod-arithmetic is the central mathematical terms in cryptography.
1. As mentioned, modular arithmetic allows groups. See @mikeazo's answer.
2. Cryptography requires hard problems. Some problems become hard with modular
arithmetic. For example, logarithms are easy to compute over all integers (and reals),
but can become hard to compute when you introduce a modular reduction. Similarly with
finding roots.
3. Cryptography is implemented digitally. It is nice if values can't be of arbitrary size. If you
work with modular arithmetic, you have guarantees about the largest value you will see and
can allocate the correct amount of space to hold values.
Q.Annote the technical details of Firewall and describe any three types
of Firewall with neat diagram
A firewall is a security tool that monitors incoming and/or outgoing network traffic to
detect and block malicious data packets based on predefined rules, allowing only
legitimate traffic to enter your private network. Implemented as hardware, software,
or both, firewalls are typically your first line of defense against malware, viruses, and
attackers trying to make it to your organization’s internal network and systems.
The major purpose of the network firewall is to protect an inner network by
separating it from the outer network. Inner Network can be simply called a
network created inside an organization and a network that is not in the range
of inner network can be considered as Outer Network.
Types of Network Firewall :
1. Packet Filters –
It is a technique used to control network access by monitoring outgoing
and incoming packets and allowing them to pass or halt based on the
source and destination Internet Protocol (IP) addresses, protocols, and
ports. This firewall is also known as a static firewall.
2
AmanVerma
2. Stateful Inspection Firewalls –
It is also a type of packet filtering which is used to control how data
packets move through a firewall. It is also called dynamic packet filtering.
These firewalls can inspect that if the packet belongs to a particular
session or not. It only permits communication if and only if, the session is
perfectly established between two endpoints else it will block the
communication.
3. Application Layer Firewalls –
These firewalls can examine application layer (of OSI model) information
like an HTTP request. If finds some suspicious application that can be
responsible for harming our network or that is not safe for our network
then it gets blocked right away.
3
AmanVerma
4. Next-generation Firewalls –
These firewalls are called intelligent firewalls. These firewalls can perform
all the tasks that are performed by the other types of firewalls that we
learned previously but on top of that, it includes additional features like
application awareness and control, integrated intrusion prevention, and
cloud-delivered threat intelligence.
5. Circuit-level gateways –
A circuit-level gateway is a firewall that provides User Datagram Protocol
(UDP) and Transmission Control Protocol (TCP) connection security and
works between an Open Systems Interconnection (OSI) network model‘s
transport and application layers such as the session layer.
Working of Firewalls :
4
AmanVerma
Firewalls can control and monitor the amount of incoming or outgoing traffic
of our network. The data that comes to our network is in the forms of
packets(a small unit of data), it is tough to identify whether the packet is safe
for our network or not, this gives a great chance to the hackers and intruders
to bombard our networks with various viruses, malware, spam, etc.
How to prevent network?
A network firewall applies a certain set of rules on the incoming and outgoing
network traffic to examine whether they align with those rules or not.
If it matches – then the traffic will be allowed to pass through your
network.
If it doesn’t match– then the firewall will block the traffic.
This way, the network remains safe and secure.
Advantages of Network Firewall :
1. Monitors network traffic –
A network firewall monitors and analyzes traffic by inspecting whether the
traffic or packets passing through our network is safe for our network or
not. By doing so, it keeps our network away from any malicious content
that can harm our network.
2. Halt Hacking –
In a society where everyone is connected to technology, it becomes more
important to keep firewalls in our network and use the internet safely.
3. Stops viruses –
Viruses can come from anywhere, such as from an insecure website, from
a spam message, or any threat, so it becomes more important to have a
strong defense system (i.e. firewall in this case), a virus attack can easily
shut off a whole network. In such a situation, a firewall plays a vital role.
4. Better security –
If it is about monitoring and analyzing the network from time to time and
establishing a malware-free, virus-free, spam-free environment so
network firewall will provide better security to our network.
5. Increase privacy –
By protecting the network and providing better security, we get a network
that can be trusted.
Disadvantages of Network Firewall :
1. Cost –
Depending on the type of firewall, it can be costly, usually, the hardware
firewalls are more costly than the software ones.
2. Restricts User –
Restricting users can be a disadvantage for large organizations, because
of its tough security mechanism. A firewall can restrict the employees to
5
AmanVerma
do a certain operation even though it‘s a necessary operation.
3. Issues with the speed of the network –
Since the firewalls have to monitor every packet passing through the
network, this can slow down operations needed to be performed, or it can
simply lead to slowing down the network.
4. Maintenance –
Firewalls require continuous updates and maintenance with every change
in the networking technology. As the development of new viruses is
increasing continuously that can damage your system.
What is cryptanalysis?
Cryptanalysis is the study of ciphertext, ciphers and cryptosystems with the
aim of understanding how they work and finding and improving techniques
for defeating or weakening them. For example, cryptanalysts seek to
decrypt ciphertexts without knowledge of the plaintext source, encryption
key or the algorithm used to encrypt it; cryptanalysts also target
secure hashing, digital signatures and other cryptographic algorithms.
For example, a cipher with a 128 bit encryption key can have 2128 (or
340,282,366,920,938,463,463,374,607,431,768,211,456) unique keys; on average,
a brute force attack against that cipher will succeed only after trying half of those
unique keys. If cryptanalysis of the cipher reveals an attack that can reduce the
number of trials needed to 240 (or just 1,099,511,627,776) different keys, then the
algorithm has been weakened significantly, to the point that a brute-force attack
would be practical with commercial off-the-shelf systems.
What is cryptology?
Cryptology is the mathematics, such as number theory and the application
of formulas and algorithms, that underpin cryptography and cryptanalysis.
Cryptanalysis concepts are highly specialized and complex, so this
discussion will concentrate on some of the key mathematical concepts
behind cryptography, as well as modern examples of its use.
In order for data to be secured for storage or transmission, it must be
transformed in such a manner that it would be difficult for an unauthorized
6
AmanVerma
individual to be able to discover its true meaning. To do this, security
systems and software use certain mathematical equations that are very
difficult to solve unless strict criteria are met. The level of difficulty of
solving a given equation is known as its intractability. These equations form
the basis of cryptography
Modern cryptology examples
Symmetric-key cryptography. Symmetric-key cryptography, sometimes
referred to as secret-key cryptography, uses the same key to encrypt and
decrypt data. Encryption and decryption are inverse operations, meaning
the same key can be used for both steps. Symmetric-key cryptography's
most common form is a shared secret system, in which two parties have a
shared piece of information, such as a password or passphrase, that they
use as a key to encrypt and decrypt information to send to each other.
Public-key cryptography. Public-key cryptography is a cryptographic
application that involves two separate keys -- one private and one public.
While both keys are mathematically related to one another, only the public
key can be used to decrypt what has been encrypted with the private key.
The most well-known application of public-key cryptography is for digital
signatures, which allow users to prove the authenticity of digital messages
and documents. It also makes it possible to establish secure
communications over insecure channels.
Q.Genranalize the security services classification and security
mechanism in detail
Network Security is field in computer technology that deals with
ensuring security of computer network infrastructure. As the network is
very necessary for sharing of information whether it is at hardware
level such as printer, scanner, or at software level. Therefore security
mechanism can also be termed as is set of processes that deal with
recovery from security attack. Various mechanisms are designed to
recover from these specific attacks at various protocol layers.
7
AmanVerma
Types of Security Mechanism are :
1. Encipherment :
This security mechanism deals with hiding and covering of data which
helps data to become confidential. It is achieved by applying
mathematical calculations or algorithms which reconstruct information into
not readable form. It is achieved by two famous techniques named
Cryptography and Encipherment. Level of data encryption is dependent
on the algorithm used for encipherment.
2. Access Control :
This mechanism is used to stop unattended access to data which you are
sending. It can be achieved by various techniques such as applying
passwords, using firewall, or just by adding PIN to data.
3. Notarization :
This security mechanism involves use of trusted third party in
communication. It acts as mediator between sender and receiver so that if
any chance of conflict is reduced. This mediator keeps record of requests
made by sender to receiver for later denied.
4. Data Integrity :
This security mechanism is used by appending value to data to which is
created by data itself. It is similar to sending packet of information known
to both sending and receiving parties and checked before and after data
is received. When this packet or data which is appended is checked and
is the same while sending and receiving data integrity is maintained.
5. Authentication exchange :
This security mechanism deals with identity to be known in
communication. This is achieved at the TCP/IP layer where two-way
handshaking mechanism is used to ensure data is sent or not
6. Bit stuffing :
This security mechanism is used to add some extra bits into data which is
being transmitted. It helps data to be checked at the receiving end and is
achieved by Even parity or Odd Parity.
7. Digital Signature :
This security mechanism is achieved by adding digital data that is not
visible to eyes. It is form of electronic signature which is added by sender
which is checked by receiver electronically. This mechanism is used to
preserve data which is not more confidential but sender‘s identity is to be
notified.
8
AmanVerma
Security services
Authentication: assures recipient that the message is from the source that
it claims to be from.
Access Control: controls who can have access to resource under
what condition
Availability: available to authorized entities for 24/7.
Confidentiality: information is not made available to unauthorized individual
Integrity: assurance that the message is unaltered
Non-Repudiation: protection against denial of sending or receiving in the
communication
Q.What is confidentiality an important principle of
security?
Confidentiality measures are designed to protect against unauthorized
disclosure of information. The objective of the confidentiality principle is to ensure
that private information remains private and that it can only be viewed or accessed
by individuals who need that information in order to complete their job duties
For example, examples of Confidentiality can be found in various access control methods,
like two-factor authentication, passwordless sign-on, and other access controls, but it's not
just about letting authorized users in, it's also about keeping certain files inaccessible.
9
AmanVerma
Q.What is CIA in Cyber Security?
The CIA Triad is an information security model, which is widely popular. It guides an
organization‘s efforts towards ensuring data security. The three principles—
confidentiality, integrity, and availability which is also the full for CIA in cybersecurity,
form the cornerstone of a security infrastructure. In fact, it is ideal to apply these
principles to any security program.
Confidentiality makes sure that only authorized personnel are given access or
permission to modify data
Integrity helps maintain the trustworthiness of data by having it in the correct state
and immune to any improper modifications
Availability means that the authorized users should be able to access data
whenever required
The CIA Triad is so elementary to information security that anytime data violation or
any number of other security incidents occur, it is definitely due to one or more of
these principles being compromised. So, the CIA Triad is always on top of the
priority list for any infosec professional.
Security experts assess threats and vulnerabilities thinking about the impact that
they might have on the CIA of an organization‘s assets. Based on that assessment,
the security team enforces a specific set of security controls to minimize the risks
within that environment.
Knowing the CIA is a must for Cyber Security. But to learn more than this,
enroll in Cyber Security Course in Bangalore now.
10
AmanVerma
Examples of CIA Triad
To have a better understanding of how the CIA Triad works in practice, consider an
ATM that allows users to access bank balances and other information. An ATM
incorporates measures to cover the principles of the triad:
The two-factor authentication (debit card with the PIN code)
provides confidentiality before authorizing access to sensitive data.
The ATM and bank software ensure data integrity by maintaining all transfer and
withdrawal records made via the ATM in the user‘s bank accounting.
The ATM provides availability as it is for public use and is accessible at all times
Q.Substitution cipher technique and Transposition cipher
technique are the types of Traditional cipher which are used to convert
the plain text into cipher text.
Substitution Cipher Technique:
In Substitution Cipher Technique plain text characters are replaced
with other characters, numbers and symbols as well as in substitution
Cipher Technique, character‘s identity is changed while its position
remains unchanged.
Transposition Cipher Technique:
Transposition Cipher Technique rearranges the position of the plain
text‘s characters. In transposition Cipher Technique, The position of
the character is changed but character‘s identity is not changed.
11
AmanVerma
12
AmanVerma
Q.Data encryption standard (DES) has been found vulnerable to
very powerful attacks and therefore, the popularity of DES has been found
slightly on the decline. DES is a block cipher and encrypts data in blocks of
size of 64 bits each, which means 64 bits of plain text go as the input to
DES, which produces 64 bits of ciphertext. The same algorithm and key are
used for encryption and decryption, with minor differences. The key length
is 56 bits. The basic idea is shown in the figure
Q.What Is Steganography?
A steganography technique involves hiding sensitive information within an ordinary,
non-secret file or message, so that it will not be detected. The sensitive information
13
AmanVerma
will then be extracted from the ordinary file or message at its destination, thus
avoiding detection. Steganography is an additional step that can be used in
conjunction with encryption in order to conceal or protect data.
Steganography is a means of concealing secret information within (or even on top of)
an otherwise mundane, non-secret document or other media to avoid detection. It
comes from the Greek words steganos, which means ―covered‖ or ―hidden,‖ and
graph, which means ―to write.‖ Hence, ―hidden writing.‖
You can use steganography to hide text, video, images, or even audio data. It‘s a
helpful bit of knowledge, limited only by the type of medium and the author‘s
imagination.
Steganography Techniques Explained
Now that we have a better grasp on what steganography is, what forms it comes in,
and who uses it, let‘s take a closer look at a sample of the available techniques.
Secure Cover Selection
Secure Cover Selection involves finding the correct block image to carry malware.
Then, hackers compare their chosen image medium with the malware blocks. If an
image block matches the malware, the hackers fit it into the carrier image, creating
an identical image infected with the malware. This image subsequently passes
quickly through threat detection methods.
Least Significant Bit
That phrase almost sounds like a put-down, doesn‘t it? However, in this case, it
refers to pixels. Grayscale image pixels are broken into eight bits, and the last bit,
the eighth one, is called the Least Significant Bit. Hackers use this bit to embed
malicious code because the overall pixel value will be reduced by only one, and the
human eye can‘t detect the difference in the image. So, no one is even aware that
anything is amiss, and that the image is carrying something dangerous within.
Palette-Based Technique
Like the Least Significant Bit technique, the Palette-Based Technique also relies on
images. Hackers embed their message in palette-based images such as GIF files,
making it difficult for cybersecurity threat hunters or ethical hackers to detect the
attack.
14
AmanVerma
Q.Explain block diagram of fiestel cypher
Q.Block Cipher modes of Operation
Electronic Code Book (ECB) –
Electronic code book is the easiest block cipher mode of functioning. It is
easier because of direct encryption of each block of input plaintext and
output is in form of blocks of encrypted ciphertext. Generally, if a message is
larger than b bits in size, it can be broken down into a bunch of blocks and
the procedure is repeated.
Procedure of ECB is illustrated below:
15
AmanVerma
Advantages of using ECB –
Parallel encryption of blocks of bits is possible, thus it is a faster way of
encryption.
Simple way of the block cipher.
Disadvantages of using ECB –
Prone to cryptanalysis since there is a direct relationship between
plaintext and ciphertext.
Cipher Block Chaining –
Cipher block chaining or CBC is an advancement made on ECB since ECB
compromises some security requirements. In CBC, the previous cipher block
is given as input to the next encryption algorithm after XOR with the original
plaintext block. In a nutshell here, a cipher block is produced by encrypting
an XOR output of the previous cipher block and present plaintext block.
The process is illustrated here:
16
AmanVerma
Advantages of CBC –
CBC works well for input greater than b bits.
CBC is a good authentication mechanism.
Better resistive nature towards cryptanalysis than ECB.
Disadvantages of CBC –
Parallel encryption is not possible since every encryption requires a
previous cipher.
Cipher Feedback Mode (CFB) –
In this mode the cipher is given as feedback to the next block of encryption
with some new specifications: first, an initial vector IV is used for first
encryption and output bits are divided as a set of s and b-s bits.The left-hand
side s bits are selected along with plaintext bits to which an XOR operation is
applied. The result is given as input to a shift register having b-s bits to lhs,s
bits to rhs and the process continues. The encryption and decryption process
for the same is shown below, both of them use encryption algorithms.
Advantages of CFB –
Since, there is some data loss due to the use of shift register, thus it is
difficult for applying cryptanalysis.
Disadvantages of using ECB –
The drawbacks of CFB are the same as those of CBC mode. Both block
losses and concurrent encryption of several blocks are not supported by
the encryption. Decryption, however, is parallelizable and loss-tolerant.
Output Feedback Mode –
The output feedback mode follows nearly the same process as the Cipher
17
AmanVerma
Feedback mode except that it sends the encrypted output as feedback
instead of the actual cipher which is XOR output. In this output feedback
mode, all bits of the block are sent instead of sending selected s bits. The
Output Feedback mode of block cipher holds great resistance towards bit
transmission errors. It also decreases the dependency or relationship of the
cipher on the plaintext.
Advantages of OFB –
In the case of CFB, a single bit error in a block is propagated to all
subsequent blocks. This problem is solved by OFB as it is free from bit
errors in the plaintext block.
Disadvantages of OFB The drawback of OFB is that, because to its operational modes, it is more
susceptible to a message stream modification attack than CFB.
Counter Mode –
The Counter Mode or CTR is a simple counter-based block cipher
implementation. Every time a counter-initiated value is encrypted and given
as input to XOR with plaintext which results in ciphertext block. The CTR
mode is independent of feedback use and thus can be implemented in
parallel.
Its simple implementation is shown below:
18
AmanVerma
Advantages of Counter –
Since there is a different counter value for each block, the direct plaintext
and ciphertext relationship is avoided. This means that the same plain
text can map to different ciphertext.
Parallel execution of encryption is possible as outputs from previous
stages are not chained as in the case of CBC.
Disadvantages of Counter The fact that CTR mode requires a synchronous counter at both the
transmitter and the receiver is a severe drawback. The recovery of
plaintext is erroneous when synchronisation is lost.
Q.describe the digital signature algorithm and for how
signing and verification is done using DSS
A digital signature is a mathematical technique used to validate the authenticity
and integrity of a message, software or digital document. It's the digital equivalent
of a handwritten signature or stamped seal, but it offers far more inherent security.
A digital signature is intended to solve the problem of tampering and
impersonation in digital communications.
Digital signatures can provide evidence of origin, identity and status of electronic
documents, transactions or digital messages. Signers can also use them to
acknowledge informed consent.
19
AmanVerma
In many countries, including the United States, digital signatures are considered
legally binding in the same way as traditional handwritten document signatures.
How do digital signatures work?
Digital signatures are based on public key cryptography, also known
as asymmetric cryptography. Using a public key algorithm, such as RSA
(Rivest-Shamir-Adleman), two keys are generated, creating a
mathematically linked pair of keys, one private and one public.
Digital signatures work through public key cryptography's two mutually
authenticating cryptographic keys. The individual who creates the digital
signature uses a private key to encrypt signature-related data, while the
only way to decrypt that data is with the signer's public key.
If the recipient can't open the document with the signer's public key, that's a
sign there's a problem with the document or the signature. This is how
digital signatures are authenticated.
Digital signature technology requires all parties trust that the individual
creating the signature has kept the private key secret. If someone else has
access to the private signing key, that party could create fraudulent digital
signatures in the name of the private key holder.
20
AmanVerma
users A and B use the Diffie-Hellman key,exchange technique with a
common prime q=71and a primitive root as a=74)If user has private key
xA=5,what isA's public key YA?5) If user B has private key XB=12, what
isB's public key YB?6) What is the shared secret key?
Answer:
a. If user A has private key XA=5, what is A’s public key YA?
Ya =7^5 mod 71 = 51
b. If user B has private key XB=12, what is B’s public key YB?
Yb = 7^12 mod 71 = 4
c.What is the shared secret key?
YK = 4^5 mod 71 = 30
21
AmanVerma
Question 10.1:
Alice and Bob use the Diffie–Hellman key exchange technique with a common
prime
q = 1 5 7 and a primitive root a = 5.
a. If Alice has a private key XA = 15, find her public key YA.
b. If Bob has a private key XB = 27, find his public key YB.
c. What is the shared secret key between Alice and Bob?
Solution:
We are given that q= 157 and a primitive rot a=5.
1. If Alice has a private key XA=15, find her public key YA.
So, public key for Alice will be given as
YA= (a) xa Mod (q)
= (5)15 mod (157)
= 79
1. If Bob has a private key XB = 27, find his public key YB.
So, public key for Bob will be given as
YB= (a) xb mod (q)
= (5)27 mod (157)
= 65
1. What is the shared secret key between Alice and Bob.
Shared key (for Alice) = (YB) xa mod (157)
= (65)15 mod (157)
= 78
Shared key (for bob) = (YA) xb mod (q)
= (79)27 mod (157)
= 78
22
AmanVerma
Thus, shared secret key between Alice and Bob is 78.
Question 10.2:
Alice and Bob use the Diffie-Hellman key exchange technique with a common
prime q = 2 3 and a primitive root a = 5 . a. If Bob has a public key YB = 1 0 ,
what is Bob’s private key YB? b. If Alice has a public key YA = 8 , what is the
shared key K with Bob? c. Show that 5 is a primitive root of 23.
Solution:
1. If Bob has a public key YB = 1 0 , what is Bob‘s private key YB.
Given common prime q = 23
Primitive root a = 5
Bob has a public key YB= 10
Bob‘s private key BX = ?
YB = aXB (mod 23)
YB = 5XB (mod 23) (∴ q=23)
10 = 5XB (mod 23)
∴51 mod 23 = 5
52 mod 23 = 25 mod 23 = 2
53 mod 23 = 125 mod 23 = 10
∴ 53(mod 23) = 5XB (mod23)
= XB = 3
∴ Bob‘s private key XB = 3
1. If Alice has a public key YA = 8 , what is the shared key K with Bob.
Alice has a public key YA= 8
The shared key K with Bob = ?
K= YAXB(mod q)
23
AmanVerma
K = 83(mod23)
K= 512(mod23)
K= 6(mod 23)
∴ K=6 is the shared key with Bob.
In order to check whether 5 is a primitive root of 23 we need to construct a table for it
as shown below:
∴ 522 = 54 x 54 x 54 x 54 x 54 x 52
= (4x 4 x 4 x 4 x 4 x 2) (mod 23)
= 16 x 16 x 8 (256 x 8) (mod23)
= 24 (mod 23)
=1
Thus 5 is a primitive root of 23.
Q.What is public key cryptography?
Public key cryptography definition: Public key cryptography is a type of encryption technique
that employs two keys that are mathematically related but not identical – one private or secret
and one public.
24
AmanVerma
In layman’s terms, it is a method of cryptography that requires two separate keys. One private for
decrypting the data and one public for encrypting the data in order to protect it from unauthorized
access or use.
Public key cryptography example
An HR representative (Rashmi) from Naukri.com wishes to send Aquib an encrypted email.
Rashmi encrypts the message using Aquib’s public key, and when Aquib receives it, he uses his
private key to decrypt the message from Rashmi.
Although attackers may attempt to compromise the server in order to read the message, they will
be unable to do so because they lack the private key required to decrypt the message. Because he
is the only one with the private key, only Aquib will be able to decrypt the message. Aquib
simply repeats the process when he wishes to respond, encrypting her message with Rasmi’s
public key.
25
AmanVerma
Applications of public key cryptography
There are various public key cryptography applications, and some of the most common ones are
digital signatures and encryption.
Digital signatures: A digital signature confirms the signer’s identity and ensures that the
documents transmitted are not forged or tampered with. Digital signatures function similarly to
electronic ―fingerprints.‖ Some of the benefits of using digital signatures are:
Speed: First and foremost, signing documents digitally is not the same as signing them on
paper in terms of time management and ease of use. The administrative burden can hamper the
sale and, in some cases, force it to be terminated. Using electronic signatures in your business
could save you money.
User Experience: Improving the user experience is a second overlooked benefit. Opening a
signing email request simplifies printing, signing, and scanning a document to return it.
Security: Identification and authentication checks provide a high level of protection for
document access and signing capabilities.
Fewer errors: By automating the digital signature process, the financial consequences of
human errors, such as signing errors or document loss, can be reduced.
For more information, you can also explore: What is a digital signature?
Encryption: Encryption is a method of concealing information by transforming it into what
appears to be random data. Some of the benefits of using encryption are:
Confidentiality: Because the content is encrypted using the sender’s public key, it can only be
decrypted using the recipient’s private key, ensuring that only the receiving party can decrypt
the content.
26
AmanVerma
Integrity: Even the slightest change to the original content will cause the decryption process to
fail, ensuring the content’s integrity.
Advantages of using public key cryptography
There are various advantages of this type of cryptography, and some of those advantages are:
Authentication: Because public key cryptography allows for digital signatures, message
recipients can confirm that messages are truly coming from a specific sender.
Convenience: This type of cryptography addresses the issue of distributing encryption keys by
having everyone publish their public keys while keeping private keys private.
Non-repudiation: Digitally signed messages function similarly to physically signed
documents. It is essentially the same as admitting a message; thus, the sender cannot deny it.
Tampering detection: Message recipients can detect tampering using digital signatures in
public key encryption.
Disadvantages of using public key cryptography
As almost everything has its advantages and disadvantages, public key cryptography also has
some disadvantages of its own, such as:
Security: If an attacker discovers your private key, he or she can read all of your messages.
Possibility of losing a private key: If your private key is lost, you will not be able to decrypt
the received messages.
Slow working: Because this method is slower than symmetric cryptography, it is unsuitable
for decrypting bulk messages.
Public keys are not authenticated: No one knows for certain that a public key belongs to the
individual it specifies, so users must verify that their public keys truly belong to them.
27
AmanVerma
verma
2022-12-24 00:07:10
-------------------------------------------video save kiya hai outube me or pahle ka 14
haianswer galat diya hai
Q.list for general characteristics of Schema for
the distribution of public key
In cryptography, it is a very tedious task to distribute the public and private
keys between sender and receiver. If the key is known to the third party
(forger/eavesdropper) then the whole security mechanism becomes
worthless. So, there comes the need to secure the exchange of keys.
There are two aspects for Key Management:
1. Distribution of public keys.
2. Use of public-key encryption to distribute secrets.
Distribution of Public Key:
The public key can be distributed in four ways:
1. Public announcement
2. Publicly available directory
3. Public-key authority
4. Public-key certificates.
These are explained as following below:
1. Public Announcement: Here the public key is broadcasted to everyone.
The major weakness of this method is a forgery. Anyone can create a key
claiming to be someone else and broadcast it. Until forgery is discovered can
masquerade as claimed user.
28
AmanVerma
2. Publicly Available Directory: In this type, the public key is stored in a
public directory. Directories are trusted here, with properties like Participant
Registration, access and allow to modify values at any time, contains entries
like {name, public-key}. Directories can be accessed electronically still
vulnerable to forgery or tampering.
3. Public Key Authority: It is similar to the directory but, improves security
by tightening control over the distribution of keys from the directory. It
requires users to know the public key for the directory. Whenever the keys
are needed, real-time access to the directory is made by the user to obtain
any desired public key securely.
4. Public Certification: This time authority provides a certificate (which
binds an identity to the public key) to allow key exchange without real-time
access to the public authority each time. The certificate is accompanied by
some other info such as period of validity, rights of use, etc. All of this
content is signed by the private key of the certificate authority and it can be
verified by anyone possessing the authority‘s public key.
First sender and receiver both request CA for a certificate which contains a
public key and other information and then they can exchange these
certificates and can start communication.
Q.describe the roles of the different servers in kerberos protocol
how does the user get authenticated to the different servers
Kerberos provides a centralized authentication server whose function
is to authenticate users to servers and servers to users. In Kerberos
Authentication server and database is used for client authentication.
Kerberos runs as a third-party trusted server known as the Key Distribution
Center (KDC). Each user and service on the network is a principal.
29
AmanVerma
The main components of Kerberos are:
Authentication Server (AS):
The Authentication Server performs the initial authentication and ticket for
Ticket Granting Service.
Database:
The Authentication Server verifies the access rights of users in the
database.
Ticket Granting Server (TGS):
The Ticket Granting Server issues the ticket for the Server
Kerberos Overview:
Step-1:
User login and request services on the host. Thus user requests for ticketgranting service.
Step-2:
Authentication Server verifies user‘s access right using database and
then gives ticket-granting-ticket and session key. Results are encrypted
using the Password of the user.
Step-3:
The decryption of the message is done using the password then send the
ticket to Ticket Granting Server. The Ticket contains authenticators like
user names and network addresses.
30
AmanVerma
Step-4:
Ticket Granting Server decrypts the ticket sent by User and authenticator
verifies the request then creates the ticket for requesting services from
the Server.
Step-5:
The user sends the Ticket and Authenticator to the Server.
Step-6:
The server verifies the Ticket and authenticators then generate access to
the service. After this User can access the services.
Kerberos Limitations
Each network service must be modified individually for use with Kerberos
It doesn‘t work well in a timeshare environment
Secured Kerberos Server
Requires an always-on Kerberos server
Stores all passwords are encrypted with a single key
Assumes workstations are secure
May result in cascading loss of trust.
Scalability
Data is prone to various attacks. One of these attacks includes message
authentication. This threat arises when the user does not have any
information about the originator of the message. Message authentication can
be achieved using cryptographic methods which further make use of keys.
Authentication Requirements:
Revelation: It means releasing the content of the message to someone
who does not have an appropriate cryptographic key.
Analysis of Traffic: Determination of the pattern of traffic through the
duration of connection and frequency of connections between different
parties.
Deception: Adding out of context messages from a fraudulent source into
a communication network. This will lead to mistrust between the parties
communicating and may also cause loss of critical data.
Modification in the Content: Changing the content of a message. This
includes inserting new information or deleting/changing the existing one.
Modification in the sequence: Changing the order of messages
between parties. This includes insertion, deletion, and reordering of
messages.
31
AmanVerma
Modification in the Timings: This includes replay and delay of
messages sent between different parties. This way session tracking is
also disrupted.
Source Refusal: When the source denies being the originator of a
message.
Destination refusal: When the receiver of the message denies the
reception.
Q.give the classification of authentication
function in detail
Message Authentication Functions:
All message authentication and digital signature mechanisms are based on
two functionality levels:
Lower level: At this level, there is a need for a function that produces an
authenticator, which is the value that will further help in the authentication
of a message.
Higher-level: The lower level function is used here in order to help
receivers verify the authenticity of messages.
These message authentication functions are divided into three classes:
Message encryption: While sending data over the internet, there is
always a risk of a Man in the middle(MITM) attack. A possible solution for
this is to use message encryption. In message encryption, the data is first
converted to a ciphertext and then sent any further. Message encryption
can be done in two ways:
Symmetric Encryption: Say we have to send the message M from a
source P to destination Q. This message M can be encrypted using a
secret key K that both P and Q share. Without this key K, no other person
can get the plain text from the ciphertext. This maintains confidentiality.
Further, Q can be sure that P has sent the message. This is because
other than Q, P is the only party who possesses the key K and thus the
ciphertext can be decrypted only by Q and no one else. This maintains
authenticity. At a very basic level, symmetric encryption looks like this:
32
AmanVerma
Public key Encryption: Public key encryption is not as advanced as
symmetric encryption as it provides confidentiality but not authentication.
To provide both authentication and confidentiality, the private key is
used.
Message authentication code (MAC): A message authentication code is
a security code that the user of a computer has to type in order to access
any account or portal. These codes are recognized by the system so that
it can grant access to the right user. These codes help in maintaining
information integrity. It also confirms the authenticity of the message.
Hash function: A hash function is nothing but a mathematical function
that can convert a numeric value into another numeric value that is
compressed. The input to this hash function can be of any length but the
output is always of fixed length. The values that a hash function returns
are called the message digest or hash values.
Measures to deal with these attacks:
Each of the above attacks has to be dealt with differently.
Message Confidentiality: To prevent the messages from being revealed,
care must be taken during the transmission of messages. For this, the
message should be encrypted before it is sent over the network.
33
AmanVerma
Message Authentication: To deal with the analysis of traffic and
deception issues, message authentication is helpful. Here, the receiver
can be sure of the real sender and his identity. To do this, these methods
can be incorporated:
Parties should share secret codes that can be used at the time
of identity authentication.
Digital signatures are helpful in the authentication.
A third party can be relied upon for verifying the authenticity of
parties.
Digital Signatures: Digital signatures provide help against a majority of
these issues. With the help of digital signatures, content, sequence, and
timing of the messages can be easily monitored. Moreover, it also
prevents denial of message transmission by the source.
Combination of protocols with Digital Signatures: This is needed to
deal with the denial of messages received. Here, the use of digital
signature is not sufficient and it additionally needs protocols to support its
monitoring.
Q.What Does Smurfing Mean?
In an IT context, smurfing is a type of denial-of-service attack that relies
on flooding a network with a large volume of traffic through the
manipulation of IP addresses in that network. This type of attack can
result in a high volume of excess activity, which can overwhelm a server
or IT setup.
A Smurf attack is a distributed denial-of-service (DDoS) attack in which an attacker
floods a victim’s server with spoofed Internet Protocol (IP) and Internet Control
Message Protocol (ICMP) packets. As a result, the target’s system is rendered
34
AmanVerma
inoperable. This type of attack gets its name from a DDoS.Smurf malware tool that
was widely used in the 1990s. The small ICMP packet generated by the malware
tool can cause significant damage to a victim’s system, hence the name Smurf.
How Does a Smurf Attack Work?
Smurf attacks are similar to a form of denial-of-service (DoS) attacks called ping
floods, since they’re accomplished by flooding a victim’s computer with ICMP Echo
Requests. The steps in a Smurf attack are as follows:
1. Attacker locates the target’s IP address: An attacker identifies the target victim’s
IP address.
2. Attacker creates spoofed data packet: Smurf malware is used to create a spoofed
data packet, or ICMP Echo Request, that has its source address set to the real IP
address of the victim.
3. Attacker sends ICMP Echo Requests: The attacker deploys ICMP Echo Requests
to the victim’s network, causing all connected devices within the network to respond
to the ping via ICMP Echo Reply packets.
4. Victim is flooded with ICMP replies: The victim then receives a flood of ICMP Echo
Reply packets, resulting in a denial-of-service to legitimate traffic.
5. Victim’s server becomes overloaded: With enough ICMP Reply packets
forwarded, the victim’s server is overloaded and potentially rendered inoperable.
6. A SYN flood, also known as a TCP SYN flood, is a type of denial-ofservice (DoS) or distributed denial-of-service (DDoS) attack that sends
massive numbers of SYN requests to a server to overwhelm it with open
connections.
Q.What Is a SYN Flood?
A SYN flood, sometimes known as a half-open attack, is a network-tier attack that
bombards a server with connection requests without responding to the
corresponding acknowledgements. The large numbers of open TCP connections that
result consume the server’s resources to essentially crowd out legitimate traffic,
making it impossible to open new legitimate connections and difficult or impossible
for the server to function correctly for authorized users who are already connected.
Q.What Is a Ping of Death Attack?
The ping of death is a form of denial-of-service (DoS) attack that occurs when an attacker
crashes, destabilizes, or freezes computers or services by targeting them with oversized data
packets. This form of DoS attack typically targets and exploits legacy weaknesses that
organizations may have patched.
Unpatched systems are also at risk from ping floods, which target systems by overloading them
with Internet Control Message Protocol (ICMP) ping messages.
35
AmanVerma
Q.What Is Trojan Horse?
A Trojan horse (or simply known as Trojan) is defined as a software
package containing malicious code that appears to be legitimate,
similar to the ancient Greek myth of the Odyssey that caused severe
damage to Troy despite having a harmless exterior.
Trojans are malicious code or software that infiltrate a computer while
impersonating a genuine program and eventually take over the system
without the user or IT administrator noticing. Technically, Trojans are not
viruses – instead, they are a sort of malware. Although this is incorrect, the
terms Trojan malware and Trojan virus are frequently used
interchangeably. Viruses can execute and replicate themselves. A Trojan,
however, cannot and must be executed by the user.
How to identify a Trojan horse
Since Trojan horses frequently appear disguised as legitimate system files,
they are often very hard to find and destroy with conventional virus and
malware scanners. Specialized software tools are often necessary for the
identification and removal of discrete Trojan horses.
However, it's possible to identify the presence a Trojan horse through
unusual behaviors displayed by a computer. The quirks could include:
A change in the computer's screen, including changing color
andresolution or an unnecessary flip upside down.
Excessive amounts of pop-up ads appear, offering solutions to various
errors which might prompt the end user to click on the ad.
The computer mouse may start moving by itself or freezing up
completely and the functions of the mouse buttons may reverse.
The browser's homepage may change or the browser will consistently
redirect the user to a different website than the one they are requesting.
This redirected website will often contain an offer that users can click on
or download which will, in turn, install more malware.
36
AmanVerma
The computer's antivirus and antimalware programs will be disabled and
the necessary steps to remove malware will be inaccessible.
Mysterious messages and abnormal graphic displays may start
appearing.
Unrecognized programs will be running in the task manager.
The taskbar will either change in appearance or completely disappear.
The computer's desktop wallpaper may change as well as the format of
desktop icons and applications.
The user's personal email service may start sending spam messages to
all or some of the addresses in the contact list that frequently contain
malware and a persuasive tactic to get recipients to open and download
the attack, thus spreading the Trojan horse to other computers.
How to Protect yourself from Trojans?
A mix of good network safety practices and utilizing a Trojan scanner regularly are demonstrated
approaches to ensure against Trojan assaults. Observe these means to shield yourself and your framework
from being attacked.
1. Do not download from untrusted sources: Never download or introduce any product program from
a site or source that you don't completely trust.
2. Avoid phishing assaults: Do not open a connection or snap a connection in an email that was
simply shipped off you from an arbitrary individual.
3. Update your Operating framework and any introduced security conventions: Regularly update
your OS to ensure that the product is progressively equipped for battling off dangers. Updates
normally incorporate security patches on the most recent dangers.
4. Do not visit dangerous sites: Be watching out for any sites that don't have security testaments –
their URL ought to incorporate https://rather than HTTP://. The 's' represents secure and there
ought to likewise be a lock close to the URL in the location bar.
5. Do not click spring up or flag from the web: Do not click any new, untrusted popups because they
might contain incredible Trojan ponies.
6. Protect records with perplexing, interesting passwords. A solid secret key isn't difficult to figure
and is undeniably comprised of a blend of upper-and lower-case letters, extraordinary characters,
and numbers. Try not to utilize a similar secret word in all cases and change your secret key
consistently. A secret phrase administrator apparatus is a magnificent method to deal with your
passwords.
37
AmanVerma
7. Keep your data protected with firewalls. Firewalls screen information that enters your gadget from
the web. While most working frameworks accompany an inherent firewall, it's additionally a
smart thought to utilize an equipment firewall for complete security.
8. Back up consistently. While backing up your documents will not shield you from downloading a
Trojan, it will help you ought to a malware assault cause you to lose anything significant.
Q.A virus
is a fragment of code embedded in a legitimate program.
Viruses are self-replicating and are designed to infect other programs. They
can wreak havoc in a system by modifying or destroying files causing system
crashes and program malfunctions. On reaching the target machine a virus
dropper(usually a trojan horse) inserts the virus into the system.
For more details, refer to this.
Various types of viruses :
File Virus:
This type of virus infects the system by appending itself to the end of a
file. It changes the start of a program so that the control jumps to its code.
After the execution of its code, the control returns back to the main
program. Its execution is not even noticed. It is also called a Parasitic
virus because it leaves no file intact but also leaves the host functional.
Boot sector Virus:
It infects the boot sector of the system, executing every time system is
booted and before the operating system is loaded. It infects other
bootable media like floppy disks. These are also known as memory
viruses as they do not infect the file systems.
38
AmanVerma
Macro Virus:
Unlike most viruses which are written in a low-level language(like C or
assembly language), these are written in a
high-level language like
Visual Basic. These viruses are triggered when a program capable of
executing a macro is run. For example, the macro viruses can be
contained in spreadsheet files.
Source code Virus:
It looks for source code and modifies it to include virus and to help spread
it.
Polymorphic Virus:
A virus signature is a pattern that can identify a virus(a series of bytes
that make up virus code). So in order to avoid detection by antivirus a
polymorphic virus changes each time it is installed. The functionality of
the virus remains the same but its signature is changed.
Encrypted Virus:
In order to avoid detection by antivirus, this type of virus exists in
encrypted form. It carries a decryption algorithm along with it. So the virus
first decrypts and then executes.
Stealth Virus:
It is a very tricky virus as it changes the code that can be used to detect it.
Hence, the detection of viruses becomes very difficult. For example, it can
39
AmanVerma
40





