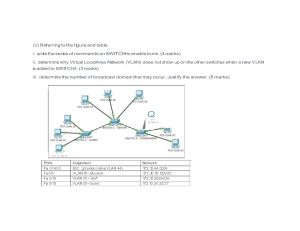
VIRTUAL LANS CSE2008 – NETWORK SECURITY OVERVIEW What is a LAN and What is a Virtual LAN? Types of Virtual LANs VLAN Operations Security Vulnerability in VLANs WHAT IS A LAN? LAN1 Client server client Bridge client Client server LAN – Single broadcast domain – subnet No routing between of a LAN Routing Required between LANs Router LAN 2 client client WHAT IS A VIRTUAL-LAN Engineering VLAN Marketing VLAN Accounting VLAN A VLAN is a way to partition a single switch into multiple switches Through VLANs, a group of devices on one or more LANs can be configured to communicate as if they were attached to the same wire. Switch Floor 3 Switch Floor 2 Router It logically segment switched networks based on the functions, project teams, or applications of the organization regardless of the physical location or connection to the network All workstations and servers used by a particular workgroup share the same VLAN, regardless of the physical connection or location. Switch Floor 1 VLAN INTRODUCTION A workstation in a VLAN group is restricted to communicating with file servers in the same VLAN group. A group of ports or users in same broadcast domain Can be used on port ID, MAC address, protocol or application LAN switched and network management software provide a mechanism to create VLANS Frame tagged with VLAN ID. Engineering VLAN VLAN INTRODUCTION VLANs function by logically segmenting the network into different broadcast domains so that packets are only switched between ports that are designated for the same VLAN in VLAN topologies provide broadcast filtering, security, and traffic flow management. Marketing VLAN Accounting VLAN Switch Floor 3 Switch Floor 2 Router Routers Switch Floor 1 VLAN WHY? Virtual is Better than Real Location-independent Marketing LAN can be all over the building Users can move but not change LAN Traffic between LANs is routed Better to keep all traffic on one LAN Switch when you can, route when you must Do not VLAN over expensive WAN links Better Security BROADCAST DOMAINS WITH VLANS AND ROUTERS A VLAN is a broadcast domain created by one or more switches. BROADCAST DOMAINS WITH VLANS AND ROUTERS Layer 3 routing allows the router to send packets to the three different broadcast domains. BROADCAST DOMAINS WITH VLANS AND ROUTERS Implementing VLANs on a switch causes the following to occur: The switch maintains a separate bridging table for each VLAN. If the frame comes in on a port in VLAN 1, the switch searches the bridging table for VLAN 1. When the frame is received, the switch adds the source address to the bridging table if it is currently unknown. The destination is checked so a forwarding decision can be made. For learning and forwarding the search is made against the address table for that VLAN only. VLAN OPERATION Each switch port could be assigned to a different VLAN. Ports assigned to the same VLAN share broadcasts. Ports that do not belong to that VLAN do not share these broadcasts. VLAN OPERATION Users attached to the same shared segment, share the bandwidth of that segment. Each additional user attached to the shared medium means less bandwidth and deterioration of network performance. VLANs offer more bandwidth to users than a shared network. The default VLAN for every port in the switch is the management VLAN. The management VLAN is always VLAN 1 and may not be deleted. All other ports on the switch may be reassigned to alternate VLANs. VLAN OPERATION Dynamic VLANs allow for membership based on the MAC address of the device connected to the switch port. As a device enters the network, it queries a database within the switch for a VLAN membership. VLAN OPERATION In port-based or port-centric VLAN membership, the port is assigned to a specific VLAN membership independent of the user or system attached to the port. All users of the same port must be in the same VLAN. VLAN OPERATION Network administrators are responsible for configuring VLANs both manually and statically. BENEFITS OF VLANS The key benefit of VLANs is that they permit the network administrator to organize the LAN logically instead of physically. VLAN TYPES Port-based VLANs MAC address based VLANs Protocol based VLANs MEMBERSHIP BY PORT MEMBERSHIP BY MAC-ADDRESSES VLAN TYPES The number of VLANs in a switch vary depending on several factors: Traffic patterns Types of applications Network management needs Group commonality VLAN TYPES An important consideration in defining the size of the switch and the number of VLANs is the IP addressing scheme. Because a one-to-one correspondence between VLANs and IP subnets is strongly recommended, there can be no more than 254 devices in any one VLAN. It is further recommended that VLANs should not extend outside of the Layer 2 domain of the distribution switch. VLAN TYPES There are two major methods of frame tagging, Inter-Switch Link (ISL) and 802.1Q. ISL used to be the most common, but is now being replaced by 802.1Q frame tagging. SECURITY VULNERABILITIES IN VLAN There are several known applications (dsniff, macof, yersinia) that provide potential attackers with the tools to penetrate VLANS. Applications show how badly configured networks and physical weakness in the LAN, which lead them to launch VLAN attack. VLAN are implemented at layer 2 (data link layer) of the OSI network model. Attack in layer 2 exploits the inability of a switch to track an attacker, change network path without detection etc. SECURITY VULNERABILITIES IN VLAN CAM Table Overflow / Media Access Control (MAC) attack Address Resolution Protocol (ARP) Attack Switch Spoofing/ VLAN Hopping Attack Double Tagging/ Double encapsulation Hopping Attack VLAN Management Policy Server (VMPS)/ VLAN Query Protocol (VQP) attack Cisco Discovery Protocol Attack Multicast Brute Force Attack Random Frame Stress Attack Private VLAN (PVLAN) Attack Spanning Tree Protocol (STP) Attack CAM TABLE OVERFLOW / MEDIA ACCESS CONTROL (MAC) ATTACK This attack focuses on the Content Addressable Memory (CAM) table, which stores information such as MAC addresses on a physical port along with the associated VLAN parameters. Buffer overflow attack, the aim is to fill this table up and attacker sits on a physical port and generates a vast number of MAC entries. When the CAM table fills up and has no room left, traffic without a CAM entry is sent out on all ports of the VLAN in question. Traffic with a CAM entry is not affected, but adjacent switches can be. Depending on the switch in question, this type of attack can be mitigated by: • Specifying the MAC addresses that are allowed to communicate through the physical port • Limiting the number of MAC addresses for a port. ADDRESS RESOLUTION PROTOCOL (ARP) ATTACK ARP protocol has a simple belief that everyone is friendly and responses can be taken at face value. If a host broadcasts an ARP request to the network, it expects only the relevant host to respond. Similarly, if a host announces its presence by sending out a gratuitous ARP, other hosts expect that it is telling the truth and believe what it broadcasts. If a malicious host is present, anything from a legitimate host will be routed through the malicious host as the default gateway. Attacker broadcast all host in LAN, all incoming packets received by attacker before transmitting to receiver. To migitate, “Man in the Middle” attacks is to use Private VLANs SWITCH SPOOFING/ VLAN HOPPING ATTACK A VLAN trunk has been configured to allow the two sites to communicate. A malicious host now presents itself to router 1 as another router and attempts to connect by using the appropriate tagging and trunking protocols. If successful, then the attacker can see the traffic on all the VLANs and can contact hosts on any of the VLANs. To mitigate, organizations should ensure that ports are not set to negotiate trunks automatically and that ports, which are not meant to be trunks, are configured as access ports. DOUBLE TAGGING/ DOUBLE ENCAPSULATION HOPPING ATTACK In Communication, first router strips off the first header and sends it on to router 2. Router 2 strips the second header and send the packet to the destination. This attack sends a packet in only one direction, but still gives the attacker access to hosts that should not be accessible. It only works if the trunk has the same native VLAN as the attacker. To mitigate this attack, auto-trunking should be disabled and a dedicated VLAN ID should be used for all trunk ports. VLAN MANAGEMENT POLICY SERVER (VMPS)/ VLAN QUERY PROTOCOL (VQP) ATTACK VMPS allows VLANs to be assigned based on the MAC address of the host and these relationships are stored in a database. This database is usually downloaded to the VMPS and then queried using VQP, an unauthenticated protocol that uses UDP (User Datagram Protocol), making it very easy to manipulate by an attacker. The mitigation is to either monitor the network for misbehavior, send VQP queries out of band or to disable it the protocol. CISCO DISCOVERY PROTOCOL (CDP) ATTACK CDP is a feature that allows Cisco devices to exchange information and configure the network to work smoothly together. The information being sent is sensitive, such as IP addresses, router models, software versions and so on. It is all sent in clear text so any attacker sniffing the network is able to see this information and, as it is unauthenticated, it is possible to impersonate another device. To mitigate disable CDP. MULTICAST BRUTE FORCE ATTACK A multicast brute-force attack searches for failings in the switch software. The attacker tries to exploit any potential vulnerability in a switch, by storming it with multicast frames. This type of attack is pretty speculative as it looks for the switch to mishandle multicast frames. The switch should contain all the frames within their appropriate broadcast domain and an attack of this nature should not be possible. RANDOM FRAME STRESS ATTACK A large number of packets is generated, randomly varying several fields within each packet and leaving only the source and destination addresses untouched. The aim is to see how the switch software copes with meaningless or unexpected values in packet fields. This type of attack should fail, but obviously bugs do occur which may allow for unexpected access to other VLANs or give rise to denial of service (DoS) attacks. RANDOM FRAME STRESS ATTACK PVLANs are used to further divide up groups of hosts at layer 2. For instance a demilitarised zone (DMZ) might have web servers that are accessed by the outside world and a SFTP(Secure File Transfer Protocol) server providing download facilities for staff in the field. There is no reason for these servers to talk to each other and PVLANs will prevent this from happening. PVLANs are not intended or designed to protect against a layer 3 attack. An attacker would create a frame with the destination MAC address set to that of the router; the source address can be that of the host he or she is on. At layer 3, the frame has the IP address of the intended victim. The switch will pass this frame to the router as the destination MAC address is that of the router. The router will then forward the frame to the victim as the IP address is valid. With this attack, packets can only be sent. The return frames will have the correct addressing and will be blocked. An attack can be mitigated by the using the right ACLs (Access Control List) on the. SPANNING TREE PROTOCOL (STP) ATTACKS STP is used to maintain loop free network topologies and use Bridge Protocol Data Units (BPDU) which are very simple packets with no payload. By using BPDUs, a switch is chosen as the Root Bridge which then defines how traffic is routed round the network. In such an exchange, an attacker has two options. One is to repeatedly send Topology Change Notification (TCN) messages to disrupt the system’s current understanding of the network and force renegotiation of the Root Bridge, resulting in a DoS attack. An alternative is to send a specially crafted BPDU to try and become the Root Bridge. Prevention of STP attacks can be achieved by using features like BPDU guard on Cisco products, which enforce the selection of the Root Bridge. https://www.cs.ucf.edu/~czou/CNT3004-11/ch15.ppt http://ce.sc.edu/cyberinfra/workshops/wast_june_2021_WS2/Day%205-lab6- VLAN%20trunking%20in%20Open%20vSwitch.pptx blob:resource://pdf.js/a38be009-037a-4652-9991-3e03379c558f https://www.redscan.com/news/ten-top-threats-to-vlan-security/