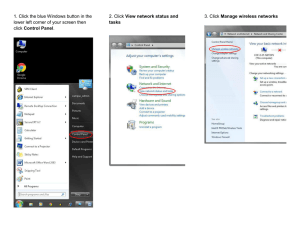
le>1 © llo..l3!.ol
Ci, AnyCoonect Profile Edit°'· N.iwortc Access Manager
Fil• Help
Netwarit Access Mariaoer
Networks
!.
Profile: Untitled
{Z)ClentPolcy
Authenllcation Poley
• Netwarits
1'NetwaritGr"'""
I SeaJnty Lewi
MedoT..,. =r -
Ol>e> Netwarit
Open networb have no 5eOllty, .1d •e open to.,ybody'Mthn r.ige.
sean type ofnetwork.
0 Aulhenllcabng Netwarit
AuthenbcilllnO netwarits provtde the
test level of S<Qlnty
n.is the least
.........
ComectlonT
ind••perfect for
ente"prise level networb. Authentialtion networks reoserd.lsservers, and other
network nfrastructu'e.
802.IXS.tlrlgs
illrll'l'eriod(5"C.)
star1Ponod (sec.) 3
30
hekl'<riod (sec.) 60
2
ma.Start
Port Aulhenllcation Ex«p- Poley
I
f'J
ENI.lie port
Alow data tnoffic befote outhenbcil..,.,
SeaJnty
o "'1:r# data traffic: after authentkation t'Yer'l If
Key Mana\Je'n<nt
M(A
MACSec:AES-GCM 128
Encrypbon
.
.''
p] EAP r.ls
./
EAPsucceedsbutkey-tfllls
I
I
Next
I I
c..al
I
Notice the 802.1X timers that are available for the administrator to tune. Also pay attention to
the Security section where Key Management can be turned on for Layer-2 MACSec encryption
between the supplicant and the switch. This provides AES-GCM-128-bit encryption over the
wire. Lastly, when enabled, the Port Authentication Exception Policy allows the supplicant to
control whether the client can send data immediately upon link (prior to an authentication) or
after the authentication with options about sending data even if EAP fails and even if MACSec
fails to negotiate. Environments, like certain government institutions, require such strict controls
that they demand the ability to deny traffic if it cannot be encrypted.
Clicking Next brings us to the Network Connection Type. The settings here should seem familiar
because they are asking for machine authentication, user authentication, or both. Selecting
Machine and User Connection adds four new tabs to the right side. Clicking Next opens the
Machine Auth tab.
Selecting the EAP method populates the lower portion of the tab. We have chosen EAP-FAST
for the tunneled EAP method, and you can see just how much control is given to the
administrator for customizing the behavior of the supplicant. The inner method is fully selectable
for EAP-MSCHAPv2 or EAP-GTC, or EAP-TLS (authenticate using a certificate).
0,=-=­---
"'"""
Hei-ttMINQeJ
Networks
Profll•: Untitled
McdllTp l
1('Nrtta\GrNll'
......
'
As an administrator builds the network profile, the wizard dynamically adds new tabs to the right
side. Selecting a wired (802.3) network adds a security level tab.
...
C. A.nyConncct Profile Editor ·Network Access MaNgcr
l.=J
F"1te Help
No-'<Acass-
"'°'"'-
Networks
I Untitled
Profile:
®
1 ,"°.".""_"',"'.'",*,"''tion'*'
.......,
j'\Notwmt.G<....,.
.
(auto1Jl'f'le'•tedl
lnVOl.C):
• In..
ModllTypo l
CorporateNetworl:
5«1.nNL<Yd l
(Qoboj)
0'°°5il!': Ytu Networt
o
meal!22.JlNe
5dect aww-ed rw:bwrlifthe endstationswl be CDl"l"leCtng
Ethemetcat:W:,
tD lhe network with a IJ"adbonal
Clicking Next will bring you to that next tab, or you can click the tab directly.
c:o 121
AnyConnect Profile Editor • Network Accos M.n.ger
-
ll
file- Hrip
Netwark Aaltss Manager
®°"'''*'
'",."._"",.",", "'""''*'
1J:N<twor1tG<-
Networks
Profile: Untitled
5«1.ntyl<Yd
OocnNctwor1t
Clper'I netwarb haw:no SKUTty, and •e open lD aiybody Nd'Wt
r-.. 1Ns sdieRst
Mcdo TSealltv Lewi I
ROH typeof networt.
Aulhenoaing Hl!twmt
Authentaono networb
!he Nrc#ltest levelorseo.nty .-.:Iarc oerfect for
enterprise lewtnetworb. Authenbt.nonnetworb rcradl.a serwn:,relother
netwark11hstrucvc.
Because we are talking about corporate networks and this is an exam about secure network
access, we will certainly be choosing the authenticating network option. As this option is
selected, notice the Connection Type tab that appears in the right margins. The Security Level
settings now that the profile is configured for an authenticating network.
1..,...,. , ,
B. AnyConnect Profile Editor·Ndo#ork Acan
"'.....
;.OWPoky
M e bllCW lc.A c: c.-Mlr'llQef'
AuehenllelbonPoley
' ,M
ttworts
:;r... ... ..._
AuthenUcaUon Polley
Profile: Untitled
r-Alow Anodlbon Modn
Mowed.tuhntiaobonModn
Mf>tnoM)
.f
.f Wecl.AIO..W
./ Opentioe"ICfl'OOCll'I
.f
./ Open (SC.llc\WP)
E>P. .,A S T
, . ...=
./ EJP.flol50W"y2.
"E>P·ns
./ Sl\ll'ed(WB')
./ Wf'APewnilTICIP
"E>P·ns
[{)'M'APelo'lll AES
.f EAP ·T l\ . S
.......,,
./ 'M'Al PW'tonll llCJP
./ EJP.flol50W"y2
.f Pl#(ltolcy)
--.1
.f WPA2 Pet.w AES
"""_.,)
MS0-1Ah1Cle9KY)
,......
./
,.....=
,PEN '
.f seectAI 1&112nNel
Q>ei(I02.IX)MP)
.f WPA EntBllrW AES
.f WPAEn llCJP
--
"E>P·ns
./ EJP.flol50W"y2
,""""
.f W9A2 llCJP
./ Wf'A2Enle'OriM:AfS
./ Op8'1ta
./ COM&i TICIP
.f l02.1Xoriy
./ c:c:>:M&iminr: AE5
./ I02. Jx1111111'1 MlcSec
LJ> ...
Networks
This view is where the administrator defines the corporate network and the security to use on
the corporate wired and wireless networks. There is a default network named wired .This default
network has all security disabled and is there to ensure that the supplicant will work in a
plainJane, non authenticating wired network.
- - r- -­
......
x ......
·· :.:::-
Networks
Profile:Untitled
....
..._
.Where things get interesting is when we click Add. Clicking this button starts a wizard that walks
the administrator through creating administratively defined networks.
The first section, Connection Settings, is similar to the single sign-on settings with the native
supplicant, where the administrator defines whether the supplicant performs authentication
before or after allowing the user to interact with the desktop.
The next section, Media, defines if end users should be able to use AnyConnect NAM and join
wired and wireless networks . Note that 3G broadband adapter cards must be Windows 7 logo
certified; otherwise, the 3G cards will be cards must be Windows 7 logo certified; otherwise , the
3G cards will be incompatible.
With the End User Control section, the administrator defines if the end user will be allowed to
perform certain functions. Disable Client allows end users to disable NAM and use the Windows
native supplicant. Display User Group makes user-created groups created from CSSC 5.x
visible and capable of a connection. Even though they do not correspond to administratordefined groups, they appear under the local group. User-created networks defined in
AnyConnect NAM will appear under here as well.
Specify a Script or Application to Run When Connected enables users to specify a script or an
application to run after the network connection is successfully established. The scripting settings
are specific to one user-configured network and allow the user to specify a local file (.exe, bat,
or .cmd) to run when that network gets to a connected state. Many enterprises use this to trigger
group policy object (GPO) refresh from Active Directory or to map network drives. Auto-Connect
allows NAM to automatically connect to administratively defined network connections without
user interaction.
Administrative Status has two sub-settings. If you disable Service Operation , the system can
use the native supplicant and connection manager when the device is not on an administrative
network, instead of having AnyConnect NAM take over as the connection manager and
supplicant for the entire system all the time. The FIPS Mode setting is for Federal Information
Processing Standard (FIPS 140-2 Level 1), which is a U.S. government standard that specifies
security requirements for cryptographic modules. If you enable FIPS mode, the NAM performs
cryptographic operations in a way that meets the government requirements.
Authentication Policy
This view is where an administrator can restrict which types of networks the end user is
permitted to connect to when not at the corporate location. Some organizations are very specific
about which security levels are required for their corporate owned assets, and this is one way of
controlling that. The settings on this tab let the administrator get very specific on the types of
wireless key management (WPA/WPA2) types to which an end user can connect, as well as
very specific on the EAP types that may be employed on those networks.
There are two main ways to configure the NAM supplicant. One is to use a standalone
AnyConnect Profile Editor for NAM. The other is to use the Profiler Editor on Cisco's ASA itself.
Let's walk through the configuration of AnyConnect NAM. The Standalone Profiler Editor
enables administrators to build configurations; the end user will never see these screens. The
editor contains the following views:
Client Policy-This view is for configuration options for connection, wired/wireless/3G mobile
broadband, and end user and administrative settings. Many of the items in this section will look
familiar as many of the options were also in the Windows native supplicant.
Authentication Policy-This view is for configuration options related to authentication
requirements for user-created networks. In other words, it is where an administrator can restrict
which types of networks the end user is permitted to connect to when not at the corporate
location.
Networks-This view is where the administrator defines networks available to all groups or
specific groups. In other words, this is where the administrator would define the corporate
network and the security to use on the corporate wired and wireless networks.
Network Groups-This view is where defined network connections can be assigned to a
particular group, which enables easier management of network connections.
Client Policy
This view is for configuration options for connection , wired/wireless/3G mobile broadband , and
end user and administrative settings. Many of the items in this section will look familiar as many
of the options were also in the Windows native supplicant.
--,,..._1JllM'l.....,Mtd.
J
&lltillrlWIWl/IAllwlWlllll
o.faM:-.aann..: .tC..) I
·-
---
The computer starts with machine authentication, and then a user logging in to the system,
thereby causing a new authentication with user authentication. This concludes the section on
the Windows native supplicant, as well as the explanation of user and machine authentications.
Cisco AnyConnect NAM Supplicant
The Cisco AnyConnect Secure Mobility Client (also called AnyConnect) is another one of those
products that is really multiple products in one. Most people are familiar with it as Cisco's
premier VPN client, but it is actually more than that. The software itself is modularized with
several modules in existence today that can be installed on the system directly or even pushed
down in an update from a Cisco ASA to the software loaded on the Windows workstation.
The key modules that are of interest to Cisco ISE and this exam in particular are the
AnyConnect Network Access Manager (NAM) and the AnyConnect Diagnostics and Reporting
Tool (DART). To provide you with a little bit of history, many years ago in a galaxy far, far away
there was a product known as the Cisco Trust Agent. This product has since been announced
as end of life, so don't waste any time memorizing the name. The point of interest of this product
is that it contained a supplicant in it that was OEM'd from a company named Meeting House.
Since that time, Cisco has acquired Meeting House and packaged its supplicant as the Cisco
Secure Services Client (CSSC).
Why have you bothered to read that little tidbit of history that only this author finds interesting?
Because that CSSC client is one of the most widely deployed non-native supplicants for
Windows in the world, and Cisco used to charge around $50 per seat for it. Starting with
AnyConnect 3.1, that same enterprise class supplicant got integrated into the AnyConnect client
as the Network Access Module and is licensed at no charge.
Active Directory negotiates a password with a Windows workstation when it jo ins AD, which the
machine-state supplicant is able to use as the credential. Additionally, the computer maintains
its own system store for certificates that is separate from the users' certificate stores. Therefore,
machine authentication (also called computer authentication) is capable of using a computer
name and password (PEAP-MSCHAPv2) or a machine certificate (EAP-TLS, PEAP-EAPTLS ).
""J
Supplicant
.,..j Port Unauthorized I
Authenticator
A uthentication
Server
EAPol Start
I
I
I
I
I
I
.._
EAP·RequesVldenhly
I
EAP-Response/ldenlity
--
.._
•
:RADIUS Access Request
I
I
EAP Requesl/PEAP I .J
EAP Response/PEAP
I
I
•
Access Request
:(AVP EAP-Response PEAPJ
I
I
I .J
1
EAP Response/ldentity
'""'
j
Port Authorized
I
-
EAP·RequesVldenhty _.
-
I
-
IRADIUS
I
EAP·Requesl/PEAP
I
.J
EAP Resoonse/PEA P
IAVP: EAP Success
(AVP. VLAN 10 dACL
I
I
EAPol Start
RADIUS Access-Accepl
I
lj
I
1
-
IRADIUS
1
-User ogs In
Challenge­
>-Request
: Exchanges
1 PoSSlble
IAVP EAP-Roquesl PEAP)
I
CAP-Success
': Multiple
RADIUS Access-Challenge
--
I
I
Access Request
-
.._
RADIUS Access-Challenge
-
: Multiple
1 Challenge­
> ·Request
: Exchanges
(AVP EAP·Requesl PEAP)
RADIUS Access
EAP-Responee PEAPJ
I[AVP
I
.._
_.
_,1
I
I
Request
RADIUS Access-Accept
I -
.
EAP-Success 1 -
......
IAVP EAP Suc:cesi.1
(AVP. VLAN 10 dACL n1
I
I
I
,...4 Port Re-Authorized I
'
I
PoSSlble
I02.lX11t11ng1
This concludes our guided tour through the Windows native supplicant, and it is the perfect time
to introduce a new topic that is specific to Microsoft Windows operating systems: user
authentication versus computer authentication.
User Authentication
This is the normal authentication that one thinks of when discussing 802.1X and network access
control. It provides the identity credentials of the user to the authentication server , allowing for
role-based access control to the network. The buzz on the street with the 802.1X standard was
all about knowing who was accessing your network before allowing them onto the network.
User authentication on a Microsoft Windows device is able to use a username, password,
user-issued certificate, or even a smart card. With these Windows devices there is a separate
certificate store for user-issued certificates. Each user who logs in to a Windows workstation will
have her own certificate store, and therefore authenticate differently to the network.
Machine Authentication (a.k.a. Computer Authentication)
Microsoft Windows workstations have a very powerful management system, Microsoft Windows
workstations have a very powerful management system, known as Active Directory. Maybe
you've heard of it? Well, AD needs to remain in contact with the computers it manages for policy
updates and other management tasks. The IEEE 802.1X standard came out, and with no user
logged in to the computer, no network access was granted. This concept broke the
communication between the AD managed computer, as well as not allowing the user's Kerberos
authentication to reach Active Directory, which didn't allow the credentials to be passed down to
the supplicant itself-especially in the instances where the user's password was expired.
This should sound an awful lot like a denial of service (DoS) because it truly was. Microsoft
(quite brilliantly) designed a way to solve this problem and prevent this chicken-and-egg
scenario.They created multiple states for their supplicant: a machine state and a user state.
Whenever there was no interactive user logged in to the workstation (that is, no one had
pressed CTRL-ALT-DEL and logged in to the computer), the machine was able to log in to the
network with its own credentials. As soon as a user interactively logged in to the system, the
supplicant would send a new EAPoL_Start message into the network, triggering a whole new
authentication of the user's credentials.
The only remaining option to cover is the Additional Settings button.This is where the supplicant
has some additional authentication options related to mode and sign-on timing.
Click the Additional Settings button.
./ Soeofy........IKlnlN:ldit
J
m.outsaufleMtallOll ..
s...
flw'tf wt
[)llM!p.,p.
•t-llQOl"I
&\lbtit ..191.w1bh11ttwM
Pwfar, _....,
i.lr.,.._.,
""'*-- ......
Let us cover these settings in reverse order, starting with Enable Single Sign On for This
Network first. This setting enables the administrator to allow or disallow the logging in to the
workstation before the 802.1X authentication occurs. Selecting Perform Immediately Before
User Logan sends the EAPoL_Start message and allows the supplicant to perform the EAP
exchange before allowing the user to interact with the workstation interface (that is, before the
start button and desktop are displayed to the end user). The maximum delay setting puts a timer
on how long the supplicant should wait for success before allowing the user to interact with the
desktop or logging the user off.
The Perform Immediate After User Logan option enables the user to interact with the desktop
immediately, which could include the ability to respond to prompts where the supplicant is
asking the user to enter the username and password.One last choice on the bottom half of this
tab is This Network Uses password. One last choice on the bottom half of this tab is This
Network Uses Separate Virtual LANs for Machine and User Authentication. This option will
make more sense after you have read the next section, but ultimately it forces the supplicant to
do an IP release/renew and attempt to get a new IP address when the user logs in.
Now, let's return to the first item of note in the Advanced settings tab, which is the Specify
Authentication Mode check box. The options under this check box are User or Computer
Authentication, Computer Authentication, User Authentication , and Guest Authentication.
"
"
ICRMZFNNT-R>I
ICI AAIZWTIN
K£DICOM ....
N:HlB
I
-c...&ao J
0onatPl'flll'Cll..-IO r..-or-..8dClltllalion
Just like the outer method of PEAP, this inner method of (EAP-TLS) has the options to validate
server certificates , specify specific servers to trust, allow the administrator to select trusted root
certificate authorities, and control the prompting to trust new servers. There is even an ability to
specify a different username for this connection (inner identity).
Click OK or Cancel to return to the Protected EAP Properties page.
Return the Select Authentication Method to the default of Secured Password.
The only other relevant setting in the Protected EAP properties page is the Enable Identity
Privacy check box. This option allows the administrator to set the outer identity. Leaving this
unchecked causes the outer identity to be set to anonymous.
Click Cancel to return to the Authenticati on tab
.........
..._.
it.Elhemaldlpt•
./ &i.bl91EEE I02_1X
°'°°"•,,....,.
a.chetticltlon IMd'od
I-
EAPEAP>
·I
·
Disabling this setting turns off that level of authentication and the supplicant would form a tunnel
and send EAP credentials to any RADIUS server.
An option to specify the servers that are allowed is available, as well as which certificates to
trust. This setting provides even more strict security control over which RADIUS servers are
allowed to receive security control over which RADIUS servers are allowed to receive the
supplicant's credentials, although it is rarely used because of the ever-changing environments
of customers.
In the Trusted Root Certificate Authorities area, the administrator is able to select which specific
root CAs are trusted for authentication. The next check box is to not prompt a user to authorize
new servers or trusted certificate authorities. By leaving this check box disabled, a user will not
be prompted to trust a certificate that is not explicitly trusted in the list above the check box.
In the Select Authentication Method area of the properties page, the administrator is provided
with an option to select the inner method for PEAP, which can be either Secured Password
(EAP-MSCHAPv2) or Smart Card or Other Certificate (which will use EAP-TLS as the inner
method for certificate authentication).
Click Configure for Secured Password (EAP-MSCHAPv2) to bring up the properties page.
EAP MSCHAPvZ Properties
The only configurable option for this inner method is to automatically use the Windows logon
credentials, also called single sign-on.
Click OK to close the EAP-MSCHAPv2 Properties window.
Change the Select Authentication Method to Smart Card or Other Certificate, and click the
Configure button to bring up the properties window.
The properties window gives the administrator the option to select the use of a smart card or a
certificate that is stored on the local computer. Along with that choice is a selection for simple
certificate selection. A windows machine might be storing many different certificates that have
multiple purposes. By enabling simple certificate selection, the list of certificates will be filtered
down to only identity certificates, thereby simplifying the experience of choosing the correct
certificate.
W...,Aw>Config
--
Gaw.e l l.JMIOn 1 ---1
,_,,,...
The Wnd
1'.toCorlig (DOTlS'tQ.....a.
o w9.aekloc.llS,S
,_-1w,,.._,,,1EEE802.1X
C :\
.......
5
w..d.tw.C<riig
,...,
......,............
.... ,....1..
ttlltl:mm6aa m:.a
.i. a . i -. oplaltoptO'l'lde
n.twa'k lor
./ &llb'e!EEE ICl2,IX
...love
,-.
,,_,,..
-
--
(loal Compuwj
.
-11-
--
O il
r.,·=·et•
I!!' . !
Fle r d f
J
o-.,,,..............ln9Ctt0d
1-
............tPEAPJ ·l
l•s tlft lg f orMlamalt
·
PtuocalV.....,(TtPllPri)
..._...,.Pn::ieoc:dV«.oi'l•CTCPllFY4)
I!i,! ....
ll ......, I
.A. lri:.U,..Tccdogro.ocrw.,..._.,.l.I0°"'9'
•li*.U,.TopcilogJ
..........
Y a
u
l!Pldytt.Prt psmidnlhlltAilrwhwi)'l:l'.I Atlhl .....a
I
I
0.0
The last check box is to Fallback to Unauthorized Network Access. This setting basically states
that if the network device is not an authenticator (that is, it does not send EAP identity requests),
the network connection should still work . If this setting was unchecked and the user plugs into a
non-802.1X-enabled switch, the connection would be treated as if the authentication failed and
the user would not have network access. It's a good idea to leave this setting enabled to ensure
positive user experience.
There are two more areas for additional settings. The first is the Settings button for the selected
network authentication method.
Click the Settings button. The Protected EAP Properties page opens. The first thing in the
Protected EAP Properties page that should stand out is the check box for Validate Server
Certificate. With this setting enabled, the supplicant is required to trust the certificate from the
RADIUS server (802.1X authentication server) before it will form the secure TLS tunnel.
Windows Native Supplicant
The single most common supplicant in wired networks is the Windows native supplicant. One
reason this supplicant is so popular is that it is built into the most common business desktop
operating system in the world. Besides that, it offers one truly beneficial feature that no other
supplicant has been able to compete with: It is fully controllable from a central Active Directory
group policy. That fact alone has made the supplicant appear very attractive to desktop
managers of corporations all over the world.
To use the Windows native supplicant, the service must first be started. It is unintuitively named
Wired AutoConfig , and the default state of the service is manual. This will need to be changed
to Automatic for the supplicant to be enabled at each boot. There is also a WLAN AutoConfig
service for the wireless supplicant, which is set to automatic by default.
Fde Adton
Vtew
He:lp
... 12)
n,
:!.- Computer M110.gunent (local
• fl Syslem Tools
(9 Task:Schuln
IiEvent\/' .,
Ill.I
Sh1redFok:lm
Loni Use:n and Groups
@) Puformann
Q DevtceMMYgu
Stor.ge
Oislc Mlnagemeit
it St:rvlcts and Appiiuibons
s..w:..
.._ WMIConttot
• II I
N.,,,.
St•rtup Type.
log On As
Windows BIOf'netri< Sefvtce
TheWindo...
Manual
Windows CardS:p.ace
Stturdyen._
M&nual
local Syste.LocalSyste.-
Dua1pt1on
SlltUJ
ThtWnPlu-.
Y/indowf. Connect Now· Config Re.- WCNCSVC ,.
Prottct1on a...
Windawi Odtnd«r
Wlftdowl Offl-er-F041ftd.uon • Ustr- Ctt1tts1nd...
WWldCWll'S Color System
Wondows En0< Repomng SeMce
W.ndows Ewnt Coiltctor
Wandows Event log
Windows Fw'ewa.11
W.ndow.s Font Cat.he Serv.c:e
YftndOW'S ltNge Acqut.Stbon (YM)
Wtndows Jmt.lta
Manual
Manual
loclf Service
Manu.t
loal5ysl<locol Syslt-.
localSyste..
M1nu1I
Allows error•.•
Manual
ThlSStMCt. .
Manu.J
ThlSSCt ...
Automaltc
Windows Fi.•
Automauc
Opt.iminsp.•
Autom.hC
Manual
Manual
Providesim.•.
modi .. St•rttd
Windows M.tn.gtmtnt lnsttumtnllt... PrOVldH 1c... SC.rttd
W.ndows Mtd1•Centu Recf:Wtt Ser- Windows M...
Windows Mtdi• Cmtu Schtdulu Se... St.lrts ind st..
Adds.
Automeoc:
Mtnwil
Windows Prtsf:nlltton Foundation F- Opllm11es p•••
Manual
Manual
Manual
Manual
Yf1ndowsRt:mo.te Mlnagement (WS... Windows R..•
Manutl
Wmdows Medi• Plf)'t:r NttworkShar ... ShartsWin...
Windows Modules lnruilltt
Wtndows Sutch
SUrttd
Enables mst... Started
PtOVlda
co... Sttntd
M•1nt•1nsd...
En•blu the ... St1rttd
WanHTIP WHI Proxy Auto--Otscovtt - WinHnP 1.. St1rttd
WlAN AutoConfHJ
WMI Pt'lfomw.Me Adliptet
Wotbt:won
WWAN AutoCOftfig
&tendtd
SU....,d
TheWlANS...
PtOVldes pe.••
Cre1tt11nd.•. St1rttd
ThlS UMU ...
loal S8vtce
Nd:wo<l<S...
local SeMc:e
lonlServtce
local Serw:e
loal Setvtc:e
locol Sysl<locll5yslt-.
NotworlcS...
N-S...
N-S...
local Syste...
LocllSeMct
NotworlcS...
AutomabC(O... locll Sys!<Manual
locllStM<:t
AutomatK fO- locll Sys!<Manual
Loc:ll ScrvKe
Mmu1t
M1nual
Autom1tJC
M.nutt
loc1I Syste.-
loc:MSyste.Netwo<l<S...
lootXMU
·1 !ieM<6
Mort Acbons
Wotd AutoConfHJ
MOftAcllons:
Network Access Devices
Cisco ISE refers to the authenticator role as a network access device (NAD). The NAD serves
multiple roles. Yes, it is an authenticator for 802.1X and will proxy EAP communications from a
supplicant to the authentication server. The NAD is also what is commonly referred to as a
policy enforcement point (PEP). The NAD is responsible for enforcing whatever authorization
result it receives from the authentication server (Cisco ISE in this case).
In simple terms, a NAD is the Access Layer device but can be any device that is going to send
RADIUS authentication requests to Cisco ISE. Common NAD types include
Wired Ethernet switches
Wireless LAN Controllers
Cisco adaptive security appliances (ASAa)
Enforcement types are covered in more detail, but to provide a little color to this subject,
common enforcement types include the following:
Dynamic VLAN (dVLAN) assignment
Downloadable access control lists (dACLs)
Security group tags (SGTs)
Airespace ACL names (for use with Wireless LAN Controllers)
URL redirections
Network access devices are an incredibly important part within the authentication system known
as secure access. It is doing so much more than simply passing frames at Layer-2. These
devices are the security enforcement devices; they apply the policy to the end user. These
devices are doing functionality that used to be available only in overlay appliances, such as URL
functionality that used to be available only in overlay appliances, such as URL redirection and
enabling agent discovery of the active posture server. These topics are covered in much more
depth; however, it is important to stress just how key these devices actually are to the success
of an 802.1X deployment. Intelligence at the edge is an absolute requirement to ensure
success .
Supplicant Options
The bulk of this chapter is about 802.1X itself. That would never be complete without discussing
the client side of the authentication flow, the supplicant. As described earlier in the chapter, a
supplicant is the software on an endpoint that understands how to communicate with EAP on
the LAN. A supplicant must be configured to use credentials , either stored credentials (such as
a certificate) or with the user's username and password.
Summary of EAP Authentication Types
EAP-PEAP
EAP-TLS
EAP-FAST
Client-side
certs required
No
Yes.
No.
Server-side
certs required
Yes
Yes.
No.
Security
High
High
High
Protects EAP
• methods:
• Authentication
occurs automari-
• Crypro-binding
between inner and
• TLS runnel erearion for EAP
packers
• Message
authentication
• Message
encryption
cally, no intervenrion by user.
outer methods prevents MITM attacks.
ro passive
dependency on
• No
• Immunity
user password.
dictionary attacks.
certs
• Use of preshared
• Digital
provide strong
keys (PAC files} ro
authentication.
Message exchange is
of •
• Auchentication
protected with pubserver ro client
Lie key encryption.
construct tunnel
through use of symmetric cryptography
(optional).
EAP Authentication Type Identity Store Comparison Chart
Selecting the appropriate EAP type is dependent on the operating system, 802.1X supplicant,
and supported back-end credential database or identity store.
Identity
Store
EAP/
TLS
PEAP/
TLS
PEAP/
MSCHAPv2
PEAP/
GTC
EAP-FAST/
MSCHAPv2
EAP-FAST/
GTC
EAP-FAST/
TLS
MS-AD
Yes*
Yes*
Yes
Yes
Yes
Yes
Yes*
LDAP
Yes*
Yes*
No
Yes
No
Yes
Yes*
Token
Server
No
No
No
Yes
No
No
No
RSA
No
No
No
Yes
No
Yes
No
*TLS authentication is validating only the certificate; however, the authorization function may use these
identity scores.
EAP-MSCHAPv2- Using this inner method, the client's credentials are sent to the server
encrypted within an MSCHAPv2 session. This is the most common inner method because it
allows for simple transmission of username and password, or even computer name and
computer password, to the RADIUS server, which in turn authenticates them to Active Directory.
EAP-GTC-This inner method was created by Cisco as an alternative to MSCHAPv2
and enables generic authentications to virtually any identity store, including OTP token servers,
LDAP, Novell E-Directory, and more.
EAP-TLS-While rarely used, and not widely known, PEAP is capable of using EAP-TLS
as an inner method.
EAP-FAST-Flexible Authentication via Secure Tunnel (FAST) is similar to PEAP. FAST was
created by Cisco Systems as an alternative to PEAP that enables faster re authentications and
supports faster wireless roaming. Just like PEAP, FAST forms a TLS outer tunnel and then
transmits the client credentials within that TLS tunnel. Where FAST differs from the PEAP is the
ability to use protected access credentials (PACs). A PAC can be thought of like a secure
"cookie," stored locally on the host as proof of a successful authentication.
EAP-MSCHAPv2- Using this inner method, the client's credentials are sent to the server
encrypted within an MSCHAPv2 session. This is the most common inner method because it
allows for simple transmission of username and password, or even computer name and
computer password to the RADIUS server, which in turn authenticates them to Active Directory.
EAP-GTC-This inner method was created by Cisco as an alternative to MSCHAPv2
that enables generic authentications to virtually any identity store, including OTP token servers,
LDAP, Novell E-Directory, and more.
EAP-TLS-EAP-FAST is capable of using EAP-TLS as an inner method. This has
become quite popular with EAP chaining.
With tunneled EAPs, there is a concept of inner and outer identities. The inner identity is easiest
to explain. It is the user's or device's actual identity credentials sent with the native EAP
protocol. The outer identity is typically set to "anonymous." It's the identity that is used between
the supplicant and the authentication server for the initial TLS tunnel setup.
Cisco ISE is able to read that outer identity and use it to help make identity store selection
decisions. Put simply, that outer identity can contain information (such as domain name) that
tells Cisco ISE to submit the credentials to Active Directory, LDAP, or some other identity store.
Most supplicants hide this option from the end user, and only administrators see the outer
identity.
Native EAP Types (Nontunneled EAP)
Native EAP types include the following:
EAP-MD5-Uses a message digest algorithm to hide the credentials in a HASH. The
HASH is sent to the server where it is compared to a local hash to see whether the credentials
were accurate. However, EAP-MD5 does not have a mechanism for mutual authentication. That
means the server is validating the client, but the client does not authenticate the server (that is,
it does not check to see whether it should trust the server). EAPMD5 is common on IP phones,
and it is also possible that some switches will send MAC authentication bypass (MAB) requests
using EAP-MD5.
EAP-TLS-An EAP type that uses TLS to provide the secure identity transaction. This is
similar to SSL and the way encryption is formed between your web browser and a secure
website. EAP-TLS has the benefit of being an open IETF standard and is considered to be
universally supported. EAP-TLS uses X.509 certificates and provides the ability to support
mutual authentication, where the client must trust the server's certificate, and vice versa. It is
considered among the most secure EAP types because password capture is not an option; the
endpoint must still have the private key.
EAP-MSCHAPv2-An EAP type in which the client's credentials are sent to the server
encrypted within an MSCHAPv2 session. This allows for simple transmission of username and
password, or even computer name and computer passwords , to the RADIUS server, which in
turn authenticates them to Active Directory (AD).
EAP-GTC-EAP-Generic Token Card (GTC) was created by Cisco as an alternative to
MSCHAPv2 that allows generic authentications to virtually any identity store, including OTP
token servers, LDAP, Novell EDirectory, and more.
Tunneled EAP Types
The previously mentioned native EAP types send their credentials immediately, while tunneled
EAP types form an encrypted tunnel first and then transmit the credentials within that tunnel.
PEAP-Protected EAP (PEAP) was originally proposed by Microsoft and is an EAP tunnel type
that has quickly become the most popular and widely deployed EAP method in the world. PEAP
forms a potentially encrypted TLS tunnel between the client and server using the x.509
certificate on the server in much the same way the SSL tunnel is established between a web
browser and a secure website. After the tunnel has been formed, PEAP uses another EAP type
as an "inner method," authenticating the client using EAP within the outer tunnel.
The authentication can be initiated by either the authenticator or the supplicant. The
authenticator initiates authentication when the link state changes from down to up or periodically
as long as the port remains up and unauthenticated. The switch sends an EAP request/identity
frame to the endpoint to request its identity. Upon receipt of the frame , the client's supplicant
responds with an EAP response/identity frame. However, enhancements were made to allow
the supplicant to trigger the authenticator to request an identity by sending an EAPoL_Start
message at any time. This enhancement provided for a much better end-user experience with
802.1X.
EAP Types
There are many EAP types, and each one has its own benefit and downside. The EAP type
defines the authentication mechanism to be used with EAP, which is usually self-evident in its
name. Most EAP types are not discussed in this book, due to lack of adoption or lack of
inclusion in the exam blueprint, such as EAP-Kerberos.
The EAP types can be broken down into two categories: native EAP types and tunneled EAP
types. A tunneled EAP type simply uses a nontunneled EAP inside a Transport Layer Security
(TLS) tunnel between the supplicant and the authenticator.
RADIUS
EAP Authentication
EAP Types:
• EAP-TLS
• EAP-MD5
Figure 4-3 Na tive EAP methods.
,,,_.,
RADIUS
EAP Authentication
(inner method)
EAP Tunnels:
·PEAP
• EAP-FAST
Inner Methods:
• EAP-TLS
• EAP-MsCHAPv2
• EAP-GTC
Component Name
Description
Supplicanr
Sofrware on rhe endpoim (also called a peer in TETF) char
comrnunicareswith EAP ar Layer-2. This sofrware responds ro
rhe aurhenticaror and provides rhe identity credentialswirh rhe
EAP comrnunicarion.
Aurhenticaror
The nerwork device char controls physical access ro rhe
nerwork based on rhe aurhenricarion srafUs of rhe endpoint.
The aurhenticaror aces as rhe middleman raking Layer-2 EAP
communicarion from rhe supplicanr and encapsulating ir in
RADfUS direcred ar the active authenricarion server. The mosr
common aurhenticarors wirh a Cisco TSE deployment are LAN
swirches and Wireless LAN Controllers(WLCs). Cisco ISE
refers ro these auchenticacors generically as necwork access
device (NADs).
Aurhentication Server
The server char is performing rhe actual authentication of
the client. The aurhentication server validares the identiry of
rhe endpoinr and provides the aurhenricator wirh a resulr,
such as accept or deny. Cisco ldenriry Services Engine is an
authenrication server.
The actual EAP identity exchange and authentication is occurring between the supplicant and
the authentication server. The switch or WLC has no idea of which EAP type is in use or
whether the user's credentials are valid. It simply takes the unmodified EAP frame and
encapsulates it within the RADIUS packet sent to the authentication server and authorizes the
port if the authentication server tells it to.
Supplicant
Layer 2
Layer 3
Link
Link
Authenticator
.....J Port Unauthorized I
I
I
I
I
I
I
-,.
EAPol Slart
Start
Authentication
Server
EAP-Requesl/ldentity
EAP Response/ldentity
-
1
,.I RADIUS Access Requesl
EAP Requesl/PEAP
Middle
EAP·Resoonse/PEAP
--
I
EAP Success
'
'
·-
RADIUS Access-Accept
IAVP EAP 5uccoNI
(AVP VI.AN 10.dACL·nJ
.1
I
Challenge­
:>-Aequest
: Exchanges
Possible
Port Authorized
I
,.
1 AVP EAP·AespoMe: PEAP)
r
: Multiple
IAVP. EAP·Aoquest PEAPJ
I
I
•
RADIUS Access-Challenge
:RADIUS Access Request
I
End
I
I
I
1
EAP Over LAN (Also Known As 802.1X)
Back in the early 2000s the IEEE standardized a solution for port-based network access control,
known as 802.1X. It was predicted to revolutionize networking as we knew it, and no device
would be able to plug in and communicate on a network without the user identifying himself and
being authorized again. Well, here we are a decade later and 802.1X is really starting to catch
on.
The three fundamental components of 802.1X are the supplicant, the authenticator, and the
authentication server. This chapter explains those components, along with critical elements to
an 802.1X solution, such as the various EAP types that can be used.
Extensible Authentication Protocol
an authentication framework that defines the transport and usage of identity credentials. EAP
encapsulates the usernames, passwords, certificates, tokens, one-time password (OTPs), and
so on that a client is sending for purposes of authentication.
EAP has become the de facto standard of authentication protocols. It is used for many
authentication methods including VPN, but most importantly IEEE 802.1X is a ratified standard
for using EAP over LAN (EAPoL).
EAP over LAN (802.1X)
IEEE 802.1X (commonly referred to as Dot1x) is defined as a standard for "port based network
access control" for local area and metropolitan area networks. The standardization of a
network-based authentication framework was the catalyst for all identity-based networking that
we see today. The three main components to 802.1X are the supplicant, the authenticator, and
the authentication server;
Layer 2
Layer 3
Link
Link
Authenticator
Supplicant
Authentication
Server