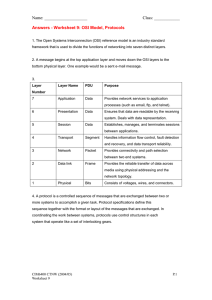
COMPUTER NETWORK : DEFINITION : A computer network is a system that connects numerous independent computers in order to share information (data) and resources. The integration of computers and other different devices allows users to communicate more easily. A network connection can be established using either cable or wireless media. Hardware and software are used to connect computers and tools in any network. A computer network consists of various kinds of nodes. Servers, networking hardware, personal computers, and other specialized or general-purpose hosts can all be nodes in a computer network. Criteria of good network: 1. Performance: It can be measured in many ways, including transmit time and response time. Transit time is the amount of time required for a message to travel from one device to another. Response time is the elapsed time between an inquiry and a response. The performance of the network depends on a number of factors, including the number of users, the type of medium & hardware 2. Reliability: In the addition to accuracy is measured by frequency of failure, the time it takes a link to recover from failure, and the network’s robustness in catastrophe. 3. Security: Network security issues include protecting data from unauthorized access, protecting data from damage and development, and implementing policies and procedures for recovery from breaches and data loss. Goal Of Networking: Programs do not have to execute on a single system because of resource and load sharing. Reduced costs – Multiple machines can share printers, tape drives, and other peripherals. Reliability – If one machine fails, another can take its place. Scalability (it’s simple to add more processors or computers) Communication and mail (people living apart can work together) Information Access (remote information access, access to the internet, e-mail, video conferencing, and online shopping) Entertainment that is interactive (online games, videos, etc.) Social Networking Types of Networks and its Classifications A computer network is a cluster of computers over a shared communication path that works for the purpose of sharing resources from one computer to another, provided by or located on the network nodes. Types of Computer Networks 1. Personal Area Network (PAN) 2. Local Area Network (LAN) 3. Wide Area Network (WAN) 4. Wireless Local Area Network (WLAN) 5. Metropolitan Area Network (MAN) 6. Virtual Private Network (VPN) 1. Personal Area Network (PAN) : PAN is the most basic type of computer network. This network is restrained to a single person, that is, communication between the computer devices is centred only to an individual’s work space. PAN offers a network range of 10 meters from a person to the device providing communication. Examples of PAN are USB, computer, phone, tablet, printer, PDA, etc. 2. Local Area Network (LAN) : LAN is the most frequently used network. A LAN is a computer network that connects computers together through a common communication path, contained within a limited area, that is, locally. A LAN encompasses two or more computers connected over a server. The two important technologies involved in this network are Ethernet and Wi-fi. Examples of LAN are networking in a home, school, library, laboratory, college, office, etc. 3. Wide Area Network (WAN) : WAN is a type of computer network that connects computers over a large geographical distance through a shared communication path. It is not restrained to a single location but extends over many locations. WAN can also be defined as a group of local area networks that communicate with each other. The most common example of WAN is the Internet. 4. Wireless Local Area Network (WLAN) : WLAN is a type of computer network that acts as a local area network but makes use of wireless network technology like Wi-Fi. This network doesn’t allow devices to communicate over physical cables like in LAN but allows devices to communicate wirelessly. The most common example of WLAN is Wi-Fi. 5. Metropolitan Area Network (MAN) : A MAN is larger than a LAN but smaller than a WAN. This is the type of computer network that connects computers over a geographical distance through a shared communication path over a city, town or metropolitan area. Examples of MAN are networking in towns, cities, a single large city, large area within multiple buildings, etc. . 6. Virtual Private Network (VPN) : A VPN is a type of computer network that extends a private network across the internet and lets the user send and receive data as if they were connected to a private network even though they are not. Through a virtual point-to-point connection users can access a private network remotely. VPN protects you from malicious sources by operating as a medium that gives you a protected network connection. Network Topology A Network Topology is the arrangement with which computer systems or network devices are connected to each other. Topologies may define both physical and logical aspect of the network. Both logical and physical topologies could be same or different in a same network. 1. Bus Topology: Every computer and network device is connected to a single cable in a bus topology network. Linear Bus topology is defined as having exactly two terminals. Advantages Installation is simple. Compared to mesh, star, and tree topologies, the bus utilizes less cabling. Disadvantages Difficulty in reconfiguring and isolating faults. A bus cable malfunction or break interrupts all communication. 2. Ring Topology: The topology is named ring topology because one computer is connected to another, with the final one being connected to the first. Exactly two neighbors for each device. A signal is passed along the ring in one direction. Each ring incorporates a repeater. Advantages Data transmission is relatively straightforward because packets only move in one direction. There is no requirement for a central controller to manage communication between nodes. Easy installation & Reconfiguration Simplified Faulty connections Disadvantages In a Unidirectional Ring, a data packet must traverse through all nodes. All computers must be turned on in order for them to connect with one another. 3.Star Topology: Each device in a star topology has a dedicated point-to-point link to a central controller, which is commonly referred to as the HUB. There is no direct connection between the devices. Traffic between the devices is not allowed in this topology. Advantages When attaching or disconnecting devices, there are no network interruptions. It’s simple to set up and configure. Identifying and isolating faults is simple. Less Expensive than mesh Easy to install & configure Disadvantages Nodes attached to the hub, switch, or concentrator is failed if they fail. Because of the expense of the hubs, it is more expensive than linear bus topologies. More cable required compared to bus or ring Too much dependency on Hub 4.Mesh Topology: Every device in a mesh topology has dedicated point-to-point connectivity to every other device. The term “dedicated” refers to the fact that the link exclusively transports data between the two devices it links. Advantages Data can be sent from multiple devices at the same time. This topology can handle a lot of traffic. Even if one of the connections fails, a backup is always available. As a result, data transit is unaffected. Physical boundaries prevent other users from gaining access to messages Point to Point links make fault transmission & fault isolation easy Disadvantages The amount of cabling and the number of I/O ports that are necessary. The sheer bulk of wiring can be greater than the available space can accommodate. It is difficult to install and reconfigure. 5.Tree Topology : The topology of a tree is similar to that of a star. Nodes in a tree, like those in a star, are connected to a central hub that manages network traffic. It has a root node, which is connected to all other nodes, producing a hierarchy. Hierarchical topology is another name for it. Advantages Network expansion is both possible and simple. We partition the entire network into pieces (star networks) that are easier to manage and maintain. Other segments are unaffected if one segment is damaged. Disadvantages Tree topology relies largely on the main bus cable because of its basic structure, and if it fails, the entire network is handicapped. Maintenance becomes more challenging when more nodes and segments are added. Serial number Network Internet 1. A network is a collection of two or more computer systems. The internet, on the other hand, is the interconnection of a few networks. 2. Low hardware devices required as compared to internet. More hardware devices required as compared to network. 3. Geographically constrained (small – area wise) Geographically extensive (large – area wise) 4. As cover small area, low error rate As covers large area, higher error rate 5. Lower communication cost High communication cost Computer Network Components Computer network components are the major parts which are needed to install the software. Some important network components are NIC, switch, cable, hub, router, and modem. Depending on the type of network that we need to install, some network components can also be removed. For example, the wireless network does not require a cable. Following are the major components required to install a network: NIC o NIC stands for network interface card. o NIC is a hardware component used to connect a computer with another computer onto a network o It can support a transfer rate of 10,100 to 1000 Mb/s. o The MAC address or physical address is encoded on the network card chip which is assigned by the IEEE to identify a network card uniquely. The MAC address is stored in the PROM (Programmable readonly memory). There are two types of NIC: Wired NIC and Wireless NIC Wired NIC: The Wired NIC is present inside the motherboard. Cables and connectors are used with wired NIC to transfer data. Wireless NIC: The wireless NIC contains the antenna to obtain the connection over the wireless network. For example, laptop computer contains the wireless NIC. Hub A Hub is a hardware device that divides the network connection among multiple devices. When computer requests for some information from a network, it first sends the request to the Hub through cable. Hub will broadcast this request to the entire network. All the devices will check whether the request belongs to them or not. If not, the request will be dropped. The process used by the Hub consumes more bandwidth and limits the amount of communication. Nowadays, the use of hub is obsolete, and it is replaced by more advanced computer network components such as Switches, Routers. Switch A switch is a hardware device that connects multiple devices on a computer network. A Switch contains more advanced features than Hub. The Switch contains the updated table that decides where the data is transmitted or not. Switch delivers the message to the correct destination based on the physical address present in the incoming message. A Switch does not broadcast the message to the entire network like the Hub. It determines the device to whom the message is to be transmitted. Therefore, we can say that switch provides a direct connection between the source and destination. It increases the speed of the network. Router o A router is a hardware device which is used to connect a LAN with an internet connection. It is used to receive, analyze and forward the incoming packets to another network. o A router works in a Layer 3 (Network layer) of the OSI Reference model. o A router forwards the packet based on the information available in the routing table. o It determines the best path from the available paths for the transmission of the packet. Advantages Of Router: o Security: The information which is transmitted to the network will traverse the entire cable, but the only specified device which has been addressed can read the data. o Reliability: If the server has stopped functioning, the network goes down, but no other networks are affected that are served by the router. o Performance: Router enhances the overall performance of the network. Suppose there are 24 workstations in a network generates a same amount of traffic. This increases the traffic load on the network. Router splits the single network into two networks of 12 workstations each, reduces the traffic load by half. o Network range Modem o A modem is a hardware device that allows the computer to connect to the internet over the existing telephone line. o A modem is not integrated with the motherboard rather than it is installed on the PCI slot found on the motherboard. o It stands for Modulator/Demodulator. It converts the digital data into an analog signal over the telephone lines. Based on the differences in speed and transmission rate, a modem can be classified in the following categories: o Standard PC modem or Dial-up modem o Cellular Modem o Cable modem Cables and Connectors Cable is a transmission media used for transmitting a signal. There are three types of cables used in transmission: o Twisted pair cable o Coaxial cable o Fibre-optic cable Coaxial cables Coaxial cables are metallic cables most often used to carry television signals and connect video equipment. They provide protection from electromagnetic interference, allowing signals with low power to be transmitted over longer distances. Sometimes called “coax,” they often carry infrared (IR or remote) control signals, eliminating the need for a separate IR network. While no longer installed for the purpose, coax was among the first Ethernet network cable types FIBER OPTIC CABLES Fiber optic cables use glass or plastic threads to transmit data quickly and efficiently using pulses of light rather than electrical signals. Apart from connecting components in home theaters, they are not as readily available for residential use as are coax and CAT5e. They transmit data at higher rates than coaxial or twisted-pair cables. TWISTED PAIR CABLES The pair of twisted is the simplest transmission medium. it consists of one or more pairs of electrical son arranged spiral. This type of support is suitable for transmission both analog and digital. The twisted pairs may be shielded, metal sheath surrounding completely metallic pairs or unshielded. They can also be “unscreened”. In this case, a metal tape around the son. A twisted pair consists of two copper wires about 1 mm thick. Purpose of twisting the wire is to reduce the electrical interference from the similar pairs in surroundings. The performance of the wire improves with the increase in the number of twist per foot. CABLE CONNECTORS :Fiber Optic cable connector , USB connector , Coaxial Cable Connectors , ETHERNET Cable Connectors. Computer Network Architecture Computer Network Architecture is defined as the physical and logical design of the software, hardware, protocols, and media of the transmission of data. Simply we can say that how computers are organized and how tasks are allocated to the computer. The two types of network architectures are used: o Peer-To-Peer network o Client/Server network Peer-To-Peer network o Peer-To-Peer network is a network in which all the computers are linked together with equal privilege and responsibilities for processing the data. o Peer-To-Peer network is useful for small environments, usually up to 10 computers. o Peer-To-Peer network has no dedicated server. o Special permissions are assigned to each computer for sharing the resources, but this can lead to a problem if the computer with the resource is down. Advantages Of Peer-To-Peer Network: o It is less costly as it does not contain any dedicated server. o If one computer stops working but, other computers will not stop working. o It is easy to set up and maintain as each computer manages itself. Disadvantages Of Peer-To-Peer Network: o In the case of Peer-To-Peer network, it does not contain the centralized system . Therefore, it cannot back up the data as the data is different in different locations. o It has a security issue as the device is managed itself. Client/Server Network o Client/Server network is a network model designed for the end users called clients, to access the resources such as songs, video, etc. from a central computer known as Server. o The central controller is known as a server while all other computers in the network are called clients. o A server performs all the major operations such as security and network management. o A server is responsible for managing all the resources such as files, directories, printer, etc. o All the clients communicate with each other through a server. For example, if client1 wants to send some data to client 2, then it first sends the request to the server for the permission. The server sends the response to the client 1 to initiate its communication with the client 2. Advantages Of Client/Server network: o A Client/Server network contains the centralized system. Therefore we can back up the data easily. o A Client/Server network has a dedicated server that improves the overall performance of the whole system. o Security is better in Client/Server network as a single server administers the shared resources. o It also increases the speed of the sharing resources. Disadvantages Of Client/Server network: o Client/Server network is expensive as it requires the server with large memory. o A server has a Network Operating System(NOS) to provide the resources to the clients, but the cost of NOS is very high. o It requires a dedicated network administrator to manage all the resources. Layered Architecture o The main aim of the layered architecture is to divide the design into small pieces. o Each lower layer adds its services to the higher layer to provide a full set of services to manage communications and run the applications. o It provides modularity and clear interfaces, i.e., provides interaction between subsystems. o It ensures the independence between layers by providing the services from lower to higher layer without defining how the services are implemented. Therefore, any modification in a layer will not affect the other layers. o The number of layers, functions, contents of each layer will vary from network to network. However, the purpose of each layer is to provide the service from lower to a higher layer and hiding the details from the layers of how the services are implemented. o The basic elements of layered architecture are services, protocols, and interfaces. o Service: It is a set of actions that a layer provides to the higher layer. o Protocol: It defines a set of rules that a layer uses to exchange the information with peer entity. These rules mainly concern about both the contents and order of the messages used. o Interface: It is a way through which the message is transferred from one layer to another layer. o In a layer n architecture, layer n on one machine will have a communication with the layer n on another machine and the rules used in a conversation are known as a layer-n protocol. Let's take an example of the five-layered architecture. Why do we require Layered architecture? o Divide-and-conquer approach: Divide-and-conquer approach makes a design process in such a way that the unmanageable tasks are divided into small and manageable tasks. In short, we can say that this approach reduces the complexity of the design. o Modularity: Layered architecture is more modular. Modularity provides the independence of layers, which is easier to understand and implement. o Easy to modify: It ensures the independence of layers so that implementation in one layer can be changed without affecting other layers. o Easy to test: Each layer of the layered architecture can be analyzed and tested individually. Design Issues for the Layers of Computer Networks o A number of design issues exist for the layer to layer approach of computer networks. Some of the main design issues are as follows − o o Reliability o o Scalability o o Addressing o o Error Control o o Flow Control o o Resource Allocation o o Statistical Multiplexing Network channels and components may be unreliable, resulting in loss of bits while data transfer. So, an important design issue is to make sure that the information transferred is not distorted. Networks are continuously evolving. The sizes are continually increasing leading to congestion. Also, when new technologies are applied to the added components, it may lead to incompatibility issues. Hence, the design should be done so that the networks are scalable and can accommodate such additions and alterations. At a particular time, innumerable messages are being transferred between large numbers of computers. So, a naming or addressing system should exist so that each layer can identify the sender and receivers of each message. Unreliable channels introduce a number of errors in the data streams that are communicated. So, the layers need to agree upon common error detection and error correction methods so as to protect data packets while they are transferred. If the rate at which data is produced by the sender is higher than the rate at which data is received by the receiver, there are chances of overflowing the receiver. So, a proper flow control mechanism needs to be implemented. Computer networks provide services in the form of network resources to the end users. The main design issue is to allocate and deallocate resources to processes. The allocation/deallocation should occur so that minimal interference among the hosts occurs and there is optimal usage of the resources. It is not feasible to allocate a dedicated path for each message while it is being transferred from the source to the destination. So, the data channel needs to be multiplexed, so as to allocate a fraction of the bandwidth or time to each host. o o Routing o o Security There may be multiple paths from the source to the destination. Routing involves choosing an optimal path among all possible paths, in terms of cost and time. There are several routing algorithms that are used in network systems. A major factor of data communication is to defend it against threats like eavesdropping and surreptitious alteration of messages. So, there should be adequate mechanisms to prevent unauthorized access to data through authentication and cryptography. Interfaces and Services Generally a network service is an application which runs at application layer and above and is used in computer networking. Network service provides data Storage, manipulation, presentation, communication. This is implemented using client-server architecture or peer-to-peer architecture. Service Interface is used to implement a Service-Oriented Architecture (SOA). This is implemented to achieve interoperability among the applications among various technologies. The basis of functions of each and every layered structure is to provide a service to the layer above it. Types of interface’s services The types of interface’s services are as follows − Entities and peer entities An entity is an active element in each and every layer, It can be either a software entity or hardware entity. Example of software entity − Process. Example of hardware entity − I/O chip's. Services provider and services user The entities and layer n implement services for the (n+1) which is above the nth layer to layer n which provides services is called services provider and layer (n+1) which takes these services is called as services user. Services Access Points They are available at the interfaces of n and n+1 layer. Services are available at SAP’s that means the layer n SAPs are those placed at the interfaces where layer n+1 access the service being offered. Interface Data Unit (IDU) For the successful exchange of information between two layers, a set of rules about the interfaces should be presented, the layer (n+1) entity passes an IDU to the layer and entity through the SAP. IDU contains mainly two parts: ICI and SDU. SDU − Services Data Unit is a part of IDU, The SDU is the information which is passed across two networks from peer network to peer entity and then goes to the help layer (n+1). ICI − ICI contains the control information which is necessary to help the lower layer n to do the necessary job. Protocol data unit In order to transfer the SDU the layer n entity has to divide into many smaller pieces. Each pieces in given header is buying the entities to their peer protocol as shown in below figure Layer n entities exchanging PDU their layer n protocol The relationship between layer and interfaces is shown in the diagram below − Both Connection-oriented service and Connection-less service are used for the connection establishment between two or more two devices. These types of services are offered by the network layer. Connection-oriented service is related to the telephone system. It includes connection establishment and connection termination. In a connection-oriented service, the Handshake method is used to establish the connection between sender and receiver. Connection-less service is related to the postal system. It does not include any connection establishment and connection termination. Connection-less Service does not give a guarantee of reliability. In this, Packets do not follow the same path to reach their destination. Difference between Connection-oriented and Connection-less Services: S.NO Connection-oriented Service Connection-less Service 1. Connection-oriented service is related to the telephone system. Connection-less service is related to the postal system. 2. Connection-oriented service is preferred by long and steady communication. Connection-less Service is preferred by bursty communication. 3. Connection-oriented Service is necessary. Connection-less Service is not compulsory. 4. Connection-oriented Service is feasible. Connection-less Service is not feasible. 5. In connection-oriented Service, Congestion is not possible. In connection-less Service, Congestion is possible. 6. Connection-oriented Service gives the guarantee of reliability. Connection-less Service does not give a guarantee of reliability. 7. In connection-oriented Service, Packets follow the same route. In connection-less Service, Packets do not follow the same route. 8. Connection-oriented services require a bandwidth of a high range. Connection-less Service requires a bandwidth of low range. 9. Ex: TCP (Transmission Control Protocol) Ex: UDP (User Datagram Protocol) 10. Connection-oriented requires authentication. Connection-less Service does not require authentication. SERVICE PRIMITIVES Service generally includes set of various primitives. A primitive simply means Operations. A Service is specified by set of primitives that are available and given to user or other various entities to access the service. All these primitives simply tell the service to perform some action or to report on action that is taken by peer entity. Each of the protocol that communicates in layered architecture also communicates in peer-to-peer manner with some of its remote protocol entity. Classification of Service Primitives : Primitive Request Meaning It represent entity that wants or request service to perform some action or do some work (requesting for connection to remote computer). It represent entity that is to be informed about event (receiver Indication just have received request of connection). Response It represents entity that is responding to event (receiver is simply sending the permission or allowing to connect). Confirm It represent entity that acknowledges the response to earlier request that has come back (sender just acknowledge the permission to get connected to the remote host). Primitives of Connection-Oriented Service : Primitive Meaning Listen When server is ready to accept request of incoming connection, it simply put this primitive into action. Listen primitive simply waiting for incoming connection request. Connect This primitive is used to connect the server simply by creating or establishing connection with waiting peer. Accept This primitive simply accepts incoming connection form peer. Receive These primitive afterwards block the server. Receive primitive simply waits for incoming message. Send This primitive is put into action by the client to transmit its request that is followed by putting receive primitive into action to get the reply. Send primitive simply sends or transfer the message to the peer. This primitive is simply used to terminate or end the connection Disconnect after which no one will be able to send any of the message. Primitives of Connectionless Service : Primitive Meaning Unitdata Unitdata primitive is simply required to send packet of data or information. Facility, Report This primitive is required for getting details about the performance and working of the network such as delivery statistics or report. OSI Model o OSI stands for Open System Interconnection is a reference model that describes how information from a software application in one computer moves through a physical medium to the software application in another computer. o OSI consists of seven layers, and each layer performs a particular network function. o OSI model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications. o OSI model divides the whole task into seven smaller and manageable tasks. Each layer is assigned a particular task. o Each layer is self-contained, so that task assigned to each layer can be performed independently. Characteristics of OSI Model: o The OSI model is divided into two layers: upper layers and lower layers. o The upper layer of the OSI model mainly deals with the application related issues, and they are implemented only in the software. The application layer is closest to the end user. Both the end user and the application layer interact with the software applications. An upper layer refers to the layer just above another layer. o The lower layer of the OSI model deals with the data transport issues. The data link layer and the physical layer are implemented in hardware and software. The physical layer is the lowest layer of the OSI model and is closest to the physical medium. The physical layer is mainly responsible for placing the information on the physical medium. 7 Layers of OSI Model There are the seven OSI layers. Each layer has different functions. A list of seven layers are given below: 1. Physical Layer 2. Data-Link Layer 3. Network Layer 4. Transport Layer 5. Session Layer 6. Presentation Layer 7. Application Layer TCP/IP MODEL The OSI Model we just looked at is just a reference/logical model. It was designed to describe the functions of the communication system by dividing the communication procedure into smaller and simpler components. But when we talk about the TCP/IP model, it was designed and developed based on standard protocols. It stands for Transmission Control Protocol/Internet Protocol. The TCP/IP model is a concise version of the OSI model. It contains four layers, unlike seven layers in the OSI model. The layers are: 1. Process/Application Layer 2. Host-to-Host/Transport Layer 3. Internet Layer 4. Network Access/Link Layer The diagrammatic comparison of the TCP/IP and OSI model is as follows : Difference between TCP/IP and OSI Model: TCP/IP OSI TCP refers to Transmission Control Protocol. OSI refers to Open Systems Interconnection. TCP/IP has 4 layers. OSI has 7 layers. TCP/IP is more reliable OSI is less reliable TCP/IP does not have very strict boundaries. OSI has strict boundaries TCP/IP follow a horizontal approach. OSI follows a vertical approach. TCP/IP uses both session and presentation layer in the application layer itself. OSI uses different session and presentation layers. TCP/IP developed protocols then model. OSI developed model then protocol. Transport layer in TCP/IP does not provide assurance delivery of packets. In OSI model, transport layer provides assurance delivery of packets. TCP/IP model network layer only provides connection less services. Connection less and connection oriented both services are provided by network layer in OSI model. Protocols cannot be replaced easily in TCP/IP model. While in OSI model, Protocols are better covered and is easy to replace with the change in technology. The first layer is the Process layer on the behalf of the sender and Network Access layer on the behalf of the receiver. During this article, we will be talking on the behalf of the receiver. 1. Network Access Layer – This layer corresponds to the combination of Data Link Layer and Physical Layer of the OSI model. It looks out for hardware addressing and the protocols present in this layer allows for the physical transmission of data. 2. Internet Layer – This layer parallels the functions of OSI’s Network layer. It defines the protocols which are responsible for logical transmission of data over the entire network. The main protocols residing at this layer are : 1. IP – stands for Internet Protocol and it is responsible for delivering packets from the source host to the destination host by looking at the IP addresses in the packet headers. IP has 2 versions: IPv4 and IPv6. IPv4 is the one that most of the websites are using currently. But IPv6 is growing as the number of IPv4 addresses are limited in number when compared to the number of users. 2. ARP – stands for Address Resolution Protocol. Its job is to find the hardware address of a host from a known IP address. ARP has several types: Reverse ARP, Proxy ARP, Gratuitous ARP and Inverse ARP. 3. Host-to-Host Layer – This layer is analogous to the transport layer of the OSI model. It is responsible for end-to-end communication and error-free delivery of data. It shields the upper-layer applications from the complexities of data. The two main protocols present in this layer are : 1. Transmission Control Protocol (TCP) – It is known to provide reliable and error-free communication between end systems. It performs sequencing and segmentation of data. It also has acknowledgment feature and controls the flow of the data through flow control mechanism. It is a very effective protocol but has a lot of overhead due to such features. Increased overhead leads to increased cost. 2. User Datagram Protocol (UDP) – On the other hand does not provide any such features. It is the goto protocol if your application does not require reliable transport as it is very cost-effective. Unlike TCP, which is connection-oriented protocol, UDP is connectionless. 4. Application Layer – This layer performs the functions of top three layers of the OSI model: Application, Presentation and Session Layer. It is responsible for node-to-node communication and controls user-interface specifications. Some of the protocols present in this layer are: HTTP, HTTPS, FTP, TFTP, Telnet, SSH, SMTP, SNMP, NTP, DNS, DHCP, NFS. Physical layer Physical layer in the OSI model is the lowest layer of the OSI reference model. It is responsible for sending raw bits from one computer to another computer over a network. It does not deal with the data of these bits and is majorly concerned with the setup of physical connection to the network. It plays the role of interacting with actual hardware and signaling mechanisms. Functions of OSI Model Physical Layer Following are some important and basic functions that are performed by the physical layer in the OSI model : 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. Physical Layer maintains the data rate (how many bits a sender can send per second). It performs Synchronization of bits. It helps in Transmission Medium decision (direction of data transfer). It helps in Physical Topology (Mesh, Star, Bus, Ring) decision (Topology through which we can connect the devices with each other). It helps in providing Physical Medium and Interface decisions. It provides two types of configuration Point to Point configuration and Multi-Point configuration. It provides an interface between devices (like PC’s or computers) and transmission medium. It has a protocol data unit in bits. Hubs, Ethernet, etc. device is used in this layer. This layer comes under the category of Hardware Layers (since the hardware layer is responsible for all the physical connection establishment and processing too). It provides an important aspect called Modulation, which is the process of converting the data into radio waves by adding the information to an electrical or optical nerve signal. It also provides Switching mechanism wherein data packets can be forward from one port (sender port) to the leading destination port. MODULATION Modulation is defined as the process of superimposing a low-frequency signal on a high-frequency carrier signal. To involve data information or speech information, another wave has to be imposed known as an input signal above the carrier wave. This process of imposing an input signal on a carrier wave is known as modulation. Types of Modulation There are three types of modulation, namely: Frequency Modulation Amplitude Modulation Phase Modulation Amplitude Modulation It is a kind of modulation where the amplitude of the carrier signal is changed in proportion to the message signal while the phase and frequency are kept constant. Phase Modulation In this type of modulation, the phase of the carrier signal is altered according to the low frequency of the message signal and hence it is called phase modulation. Frequency Modulation In this modulation the frequency of the carrier signal is altered in proportion to the message signal while the phase and amplitude are kept constant is called frequency modulation. Modulation mechanisms can also be digital or analogue. An analogue modulation scheme has an input wave that continuously changes like a sine wave, but it is a bit more complicated when it comes to digital. The voice sample is considered at some rate and then compressed into a bit (the stream of zeros and ones). This, in turn, is made into a specific type of wave that is superimposed on the carrier. What is Demodulation? Demodulation is defined as extracting the original information-carrying signal from a modulated carrier wave. A demodulator is an electronic circuit that is mainly used to recover the information content from the modulated carrier wave. There are different types of modulation, and so are demodulators. The output signal via a demodulator may describe the sound, images, or binary data. Difference Between Modulation and Demodulation Modulation is the process of influencing data information on the carrier, while demodulation is the recovery of original information at the distant end of the carrier. A modem is an equipment that performs both modulation and demodulation. Both processes aim to achieve transfer information with the minimum distortion, minimum loss, and efficient utilisation of the spectrum.