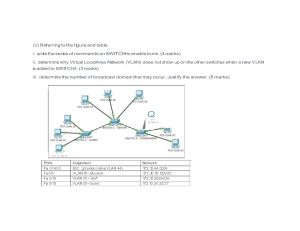
Assignment final: unit 2 Networking Network Design FPT University 63 pag. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Assignment name: Networking Infrastructure Student name: Tran Van Tien Student ID: BHAF180025 Tutor: Le Van Thuan Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Table of Contents Introduce ............................................................................................................................... 4 1, Check the network rules and their protocols ...................................................................... 4 1.1, Discuss the benefits and constraints of different network types and standards. .......... 4 1.1.1, Discuss the benefits and constraints of different types of networks ...................... 4 1.1.2, Discuss various network standards. ................................................................... 10 1.2, Explain the impact of network structure, communication and bandwidth requirements. ........................................................................................................................................ 14 1.2.1, Impact of network structure requirements........................................................... 14 1.2.2, Impact of communication and bandwidth............................................................ 18 1.3, Compare common network principles and how efficient protocols allow networked systems. .......................................................................................................................... 18 1.3.1, Compare common network principles ................................................................ 18 1.3.2, How protocols allow the efficiency of networked systems. .................................. 20 2, Explain devices and network activity ............................................................................... 22 2.1, Discuss the operating principles of network devices and server types. ..................... 22 2.1.1, Discuss the operating principles of network devices. .......................................... 22 2.1.2. Discuss the operational principles of server types. ............................................. 27 2.2. Explore a variety of server types and demonstrate server selection, considering a certain scenario regarding cost optimization and performance. ....................................... 31 2.2.1. Factors to consider when choosing a server ...................................................... 31 2.2.2. Select server for business .................................................................................. 32 2.3. Discuss the interdependence of workstation hardware with related network software. ........................................................................................................................................ 33 3, Network system design. .................................................................................................. 34 3.1, Design a networked system to meet a certain specification. ..................................... 34 3.1.1, Request. ............................................................................................................ 34 3.1.2, Design plan and expected cost. ......................................................................... 34 3.2, Check and evaluate the design to meet the requirements and analyze user feedback. ........................................................................................................................................ 37 3.2.1, Check and evaluate the design for requirements................................................ 37 3.2.2. Check and evaluate costs. ................................................................................. 38 3.3, Installing and configuring network services and applications. ................................... 45 3.3.1, Basic configuration. ............................................................................................ 45 3.3.2, VLAN. ................................................................................................................ 45 3.3.3, DHCP................................................................................................................. 46 3.3.4, Static routing. ..................................................................................................... 48 Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) 3.3.5, NAT.................................................................................................................... 48 3.3.6, ACL. ................................................................................................................... 49 4, Deploy and diagnose networked systems. ...................................................................... 49 4.1, Implement a network based on a prepared design. .................................................. 49 4.1.1, Basic configuration. ............................................................................................ 49 4.1.2, VLAN ................................................................................................................. 52 4.1.3, DHCP................................................................................................................. 54 4.1.4, Static routing. ..................................................................................................... 54 4.1.5, NAT.................................................................................................................... 55 4.1.6, ACL .................................................................................................................... 55 4.2, Analysis of test results compared with expected results ........................................... 56 a, Basic configuration. .................................................................................................. 56 b, VLAN. ...................................................................................................................... 56 c, DHCP. ...................................................................................................................... 57 d, Static routing and NAT ............................................................................................. 58 e, ACL.......................................................................................................................... 61 4.3, Proposing potential improvements for networked systems........................................ 63 4.3.1, Scaling up schools. ............................................................................................ 63 4.3.2, Redundant configuration for LAN. ...................................................................... 63 Conclude............................................................................................................................. 63 Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Introduce In this report, I will explain network principles, protocols and devices, including the benefits and limitations of network solutions, the impact of network topology, communication requirements and bandwidth, network system efficiency, operating principle of network equipment and server type and network software. In addition, I will design network systems and deploy and diagnose networked systems. 1, Check the network rules and their protocols 1.1, Discuss the benefits and constraints of different network types and standards. 1.1.1, Discuss the benefits and constraints of different types of networks Computer networks include two or more computers that are linked to share resources (such as printers and CDs), exchange files, or allow electronic communications. Computers on the network can be linked via cables, telephone lines, radio waves, satellites or infrared light rays. There are two very popular networks now: Internal network (LAN) Wide area network (WAN) 1.1.1.1, Internal network (LAN) LANs are often used in a business to provide Internet connectivity to all those in the same space with a single Internet connection. All Internet devices are capable of being configured as nodes on a LAN and can be connected to the Internet via a separate computer. The computers in the LAN are also used to connect office workstations to grant access to the printer. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) LAN network a, Advantages Share resources: All resources are attached to a network and if any computer needs any resources, it can be shared with the computer needed. Types of resources are DVD drives, printers, scanners, modems and hard drives. Therefore, there is no need to purchase separate resources for each computer and it saves money. Relationship between client and server: All data from the attached computers can be stored in a server. If any computer (client) needs data, that computer user only needs to log in and access data from the server. For example: Movies and songs can be stored on the server and can be accessed by any authorized user (client). Share on the internet: In offices and network cafes, we can see that an internet connection is shared between all computers. This is also the type of LAN technology in which the main internet cable is attached to a server and the computers are distributed by the operating system. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Share the software program: Software programs can also be shared on the LAN. You can use only licensed software and any user can use this software in the network. It's costly to buy a license for each user in the network so it's easy and cost-effective to share software programs. Data security: Keep data on the server more secure. And if you want to change or delete any data, you can do it easily on a server computer and other computers can access the updated data. You can also grant access or revoke access to specific users so that only authorized users can access data in the network. Communicate easily, quickly and save time: LAN computers can exchange data and messages easily and quickly. It also saves time and makes our work fast. All users can share messages and data with any other user on the LAN. Users can log in from any computer on the network and access the same data placed on the server. Computer identification: Each computer is provided with a MAC address and stored temporarily in the switch or router during communication. All computers in the LAN are identified by the MAC addresses used to send and receive messages and data. Note that the MAC address is stored in the network adapter installed in the motherboard of each computer. In older computers, the network adapter is not integrated with the motherboard, but in modern computers, they are integrated with the motherboard. Centralized data: Data of all network users can be saved on the computer's hard disk. This will help users to use any network workstation to access their data. Because data is not stored on the local workstation. But it is stored on a server computer. Users will access their own data by logging into their account from any client in the network. Easy and cheap: The biggest advantage of a local area network is that it is easy to set up and also cheap compared to other options and therefore, if the company is trying to set up a network at a lower cost and easier than a local area network is the answer. Such companies. b, Disadvantages Limited area: The biggest drawback of LAN is that it can only be used in a limited area and once the computer goes out of the network, the local area network is not used. Therefore, Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) to put it simply, if the area of local area deployment is larger than setting up a LAN in that area, it cannot and is not feasible for the company. Share data from outside: Another limitation of LAN is that if a person wants to share data from outside the network, it is difficult because people cannot run mobile devices such as hard drives and CDs easily on all network computers. . Therefore, if you have done some work at home and want to bring that job to the office, you have to send that job by email and if the data is big, even the email option is not feasible and people will have problems carrying data from home to office. Data security issues: If the server computer is not properly set up and there is a leak of security, unauthorized users can also access the data. Therefore, a security policy and rules are set up correctly on the server. Server problems can affect all computers: If any files on the server are corrupted or the hard drive fails, all attached computers have problems with the operation. 1.1.1.2, Wide area network (WAN) When the LAN has coverage in a very small range in just one building, the WAN can cover a large geographic area, crossing national or international borders. A WAN is made using a subscriber line provided by a service provider or by using switching network packets for data transmission. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) WAN network a, Advantages Include a large geographic area: WAN has a geographical area of 1000 km or more. If your office is in different cities or countries, you can connect your branch offices through WAN. ISP (Internet Service Provider) can provide you with separate links so you can connect different branch offices together. Centralized data: Your company does not need to purchase email, files and backup servers, all of which can be located at the headquarters. All branch offices can share data through the headquarters server. You can back up, share other useful data from headquarters and all this data is synchronized with all other office branches. Receive files and updated data: Software companies work on servers directly to exchange updated files. Therefore, all programmers and office staff receive updated versions of files within seconds. Many applications for exchanging messages: With IOT (Internet of thing) and new LAN technologies, messages are being transmitted quickly. A lot of web apps are available like Facebook messenger, Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) WhatsApp, Skype that you can communicate with friends via text, voice and video chat. Share software and resources: Like LAN, we can share software applications and other resources such as hard drives and RAM with other users on the internet. In web hosting, we can share computer resources between multiple websites. Global business: Now everyone with computer skills can do business on the internet and expand their business globally. There are many types of businesses such as: E-commerce, Buy and sell stocks, etc. High frequency band: If you receive a leased line for your company, it gives higher bandwidth than a normal bandwidth connection. You can get high data transfer rates, which can increase your company productivity. Distribute workload and reduce travel costs: Another benefit of a wide area network is that you can distribute your work to other locations. For example, if you have an office in the US, you can hire people from any other country and contact them easily over the WAN. It also reduces your travel costs when you can track your group activities online. a, Disadvantages Security issue: WAN has more security issues than LAN. WANs with many technologies combined can create security holes. Requires firewall and antivirus software: Because data transmitted on the internet can be accessed and changed by hackers, the firewall needs to be turned on in the computer. Some people may also inject a virus into a computer to install antivirus software. Other security software also needs to be installed on different points in the WAN. High set up cost: Setting up the LAN for the first time at the office costs more. It may involve buying routers, switches and additional security software. Troubleshoot: Because LAN covers so many areas, it is very difficult to fix the problem. Most WAN wires go to the sea and sometimes the wires are broken. It involves a lot of Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) resources to repair the sea currents. In ISP headquarters, many internet connections, routers are mixed in the rooms and troubleshooting incidents on the internet requires a full-time employee. Server issue and disconnection: In some areas, ISPs face problems due to power supply or bad line structure. Customers often face connectivity problems or slow Internet speed problems. The solution to this problem is to buy a dedicated line from ISP. * Internet network or Computer network is a special case of WAN, it provides global services such as Mail, Web, Chat ... Free internet for everyone. Internet Other types of networks include: ▪ Urban area network (MAN) ▪ Wireless LAN (WLAN) ▪ Storage area network (SAN) 1.1.2, Discuss various network standards. 1.1.2.1, OSI Model Open System Interconnection - OSI model developed by International Standards Organization (ISO). Model of dividing network communication into 7 classes. Grades 1-4 are common low-level classes that perform data migration tasks. Grades 5-7 are high-level classes that contain application-level data. The way the network operates is in a general rule, that is to transfer data. Each class will perform specific tasks and then move the data to the next layer. OSI reference model is divided into seven classes with the following functions: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) OSI model + Application: (application): interface between application and network (Level 7) + Presentation: (presentation): data exchange format agreement (6th floor) + Session: (session): allows users to set up connections (5th floor) + Transport: (transport): ensure communication between two systems. (4th floor) + NetWork: (network): oriented data transmission in inter-network (3rd floor) + Data Link: (data link): determines access to the device. (2nd Floor) + Physical: (physical): convert data into bits and transmit. (1st floor) a, Advantages Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) It is a general model. And it is considered a standard model in computer networks. Classes in the OSI model architecture are distinguished by services, interfaces, and protocols. Because protocols are hidden, any protocol can be implemented in this model. So it is a common model. It has all the flexibility to adapt to many protocols. It supports connection orientation as well as disconnected services. So we can use connection-oriented models when we need reliability and service without connection when we need to transfer data faster over the internet. It follows the division and conquest technique. All services are distinguished in different classes. Therefore, administration and maintenance for this OSI model architecture is simple and easy. This class architecture follows the principle of abstraction. Changes in a class do not have much impact on other classes. It is safer and more adaptable than having all the services wrapped in one class. It is a class model. It is possible to change a class without affecting other classes. It clearly distinguishes services, interfaces and protocols. Therefore, it is flexible in nature. The protocols in each layer can be conveniently replaced depending on the nature of the network. It supports both connection-oriented and disconnected services. b, Disadvantages It is purely a theoretical model that does not consider the availability of appropriate technology. This limits its practical implementation. The launch time of this model is not suitable. When OSI appeared, the TCP / IP protocols were deployed. So companies were initially reluctant to use it. OSI model is very complicated. The original implementation was bulky, slow and expensive. Although there are many layers, some classes such as Session Layer and Presentation Layer have very few functions when practically deployed. There are duplicates of services in different classes. Services such as addressing, flow control and error control are provided by multiple layers. The standards of the OSI model are theoretical and do not provide an appropriate solution for actual network deployment. 1.1.2.2, TCP / IP model TCP / IP stands for Transmission Control Protocol (TCP) and Internet Protocol (IP), a protocol known as the communication setup protocol, the protocol stack that most Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) computer networks today run on it. This set of protocols is named after two protocols, the transport control protocol and the inter-network protocol. These are the first two protocols in the world to be defined. TCP / IP model consists of 4 layers: TCP/IP model + Class / 4th floor: Application. + Class / 3rd floor: Transport. + Class / 2nd floor: Internet. + Class / 1st floor: Network Access. a, Advantages This is an industry standard model that can be effectively implemented in real network problems. It is interactive, that is, it allows cross-platform communication between heterogeneous networks. It is an open protocol suite. It is not owned by any particular institute and can therefore be used by any individual or organization. It is a client architecture - the server can expand. This allows networks to be added without disrupting existing services. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) It assigns an IP address to each computer on the network, thus making each device identifiable over the network. It assigns each site a domain name. It provides name and address resolution service. b, Disadvantages It is not general in nature. Therefore, it cannot represent any protocol stack other than TCP / IP. For example, it cannot describe Bluetooth connectivity. It does not clearly separate the concepts of services, interfaces and protocols. Therefore, it is not suitable to describe new technologies in new networks. It does not distinguish between data link and physical layers, which have very different functions. Data link layer should be concerned with frame transmission. On the other hand, the physical layer should lie down to the physical characteristics of the transmission. An appropriate model should separate the two classes. It was originally designed and deployed for wide area networks. It is not optimized for small networks like LAN (Local Area Network) and PAN (Personal Area Network). 1.2, Explain the impact of network structure, communication and bandwidth requirements. 1.2.1, Impact of network structure requirements Network topology refers to the physical layout or logic of the network. It defines how different nodes are placed and linked. Alternatively, the network topology may describe how data is transmitted between these nodes. There are two types of network topology: physics and logic. + Physical Topology refers to the topology of the Local Area Network (LAN). The method used to connect physical devices on the network to cables and cables is used, all forming the physical topology. + Logical Topology describes the communication signal performance of the network and how it exchanges distributed data. The logical topology determines how data is transmitted. 1.2.1.1, Physical Topology The network topology is a spatial geometrical structure that is in fact the element layout of the network as well as how to connect them. Common networks have three types of structures: Star Topology, Ring Topology and Linear Bus Topology. 1.2.1.1.1, Star Topology Star-shaped networks include a center and information nodes. Information nodes are terminal stations, computers and other network devices. The center of the network that coordinates all activities in the network with basic functions is: - Identify pairs of addresses to send and receive permission to occupy information lines and communicate with each other. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) -Allow to monitor and mishandle in the process of information exchange. -Notify the status of the network ... Star Topology a, Positive Network format is the fastest way o When the network cable is broken, it will reward you for disconnecting one machine, while others will still work normally. When an error occurs, it is easy to check and fix. The network can be expanded according to user needs. b, Negative Network scalability depends on the capabilities of the center. When the center encounters a problem, the whole network is down. The network requires independent connection of each device separately at information nodes to the center. The distance from the machine to the center is very limited (100 m). Costs of network and intermediate devices are costly In general, the image network allows to connect computers to a centralized unit (HUB) with a twisted cable, this solution allows to directly connect the computer to the HUB Need to go through the Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) BUS axis, avoid the factors causing the network stagnation. Recently, along with the development of switching hubs, this model has become increasingly popular and accounts for the majority of newly installed networks. 1.2.1.1.2, Ring Topology This form network, arranged in a circular form, is designed to be a closed loop, the signal running around in a certain direction. The buttons that communicate each other at a time are only one button. The transmitted data must be accompanied by the specific address of each receiving station. Ring Topology a, Positive The ring-type network has the advantage of being able to extend far away, the total line needed is less, thus saving the cable wire, the speed is faster than the type of BUS. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) b, Negative The downside of this network is that the speed is still slow When there is a problem on the cable road, the entire network will stop working When there is a problem, it is difficult to check error detection. Because this network has many disadvantages, it is rarely used 1.2.1.1.3, Bus topology According to the road corridor layout as shown, the server (host) as well as all other computers (workstations) or nodes (nodes) are connected together on a main cable line to convey signal. All nodes use this same main cable. The two ends of the cable are covered by a device called a terminator. Signals and packets when moving up or down in cables carry the address of the destination. Bus topology a, Positive This type of network uses the least cable, easy to install, thus saving installation costs b, Negative However, there are also disadvantages that there will be traffic congestion when moving data with large traffic. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) When there is a failure at some stage it is difficult to detect, a stop on the line to repair will stop the whole system. * In addition to the three types of configurations above, there are some other forms that can be modified from these three types of tree networks, star-shaped networks rings, mixed networks, etc. 1.2.1.2, Logical Topology Logical Topology of the network is the way that hosts communicate through the transmission environment with two common logical topologies, Broadcast and Token passing. -Broadcast: simply means that each host sends its data to all other hosts on the medium. There is no registration of the next station using the transmission medium, instead of first serving first. This logical topology uses a very popular CSMA / CD access method in Ethernet networks. -Token passing: controls network access with a sequential token to each host. When a host receives a token, it means that the host can transmit data to the network, if the host does not have data to transmit it will transfer the token to the next host and this process is repeated in the network. 1.2.2, Impact of communication and bandwidth. The bandwidth can be understood as the maximum speed that can be transmitted in 1 second. We often encounter fiber optic network speeds, copy speed of USB ... In this sense, Bandwidth is understood as Broadband. In the field of website hosting, the term "bandwidth" is often used to describe the maximum amount of data including upload and download back and forth between the website (or server) and users in a unit of time ( usually months). In short, bandwidth is the parameter that indicates the maximum amount of traffic your website can circulate each month. In this sense, we understand bandwidth is the sum of 1-month traffic. Another way of understanding Bandwidth is "Broadband" is the size of the transmission line. If the Broadband has a high index, it is possible to serve multiple people online at a time quickly. 1.3, Compare common network principles and how efficient protocols allow networked systems. 1.3.1, Compare common network principles Application Bus topology - Good for small networks and networks with low traffic and low data traffic. Ring Topology - Good for cases where the network has a few stations operating at high speed, not far apart or the network has Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Star Topology - Currently the star network is the best way for the case of data and signal integration. Public Complexity Efficiency Cost Defect Ability of extension unevenly distributed data. - Requiring relatively complex installation. networks have this structure. - Not complicated. - The complexity depends on the central device, which is generally easy. - Very good under - Effective in the case - Good for medium low load can reduce of high traffic volume load case however performance very and is quite stable size and ability, quickly when due to the increase deduce the network loading increases. of delay time and performance degradation depends directly on compared to other the power of the networks. central device. - Relatively low, - Must have doubled - The total cost is especially because the resources or very high when doing many devices have have an alternative the task of the central been fully developed method when a device, the central and sold in the button does not work device, although not market. Channel if you still want the used for other things. redundancy is network to operate The number of recommended to normally, very high private wires is also reduce the risk of cost high. network incidents. - A broken station - A faulty station can - The reliability of the does not affect the affect the whole system depends on whole network. system because the the central device, Except for incidents stations depend on the network only fails on the line. each other. Difficult when the central to find broken device fails. network button. - Adding and - Relatively easy to - Network expansion reshaping this add and subtract is quite easy network is easy. workstations without depending on the However, it is connecting much for capacity of the difficult to connect each change Cost for central device. between different change is relatively computers and low. devices because they must be able to receive the same address and data. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) 1.3.2, How protocols allow the efficiency of networked systems. 1.3.2.1, TCP TCP is the most commonly used protocol on the Internet. When you request a web page in the browser, the computer sends TCP packets to the web server's address, asking it to resend the site. The web server responded by sending a stream of TCP packets, which your web browser combined to form the web page. When you click on a link, log in, post a comment or do anything else, your web browser sends TCP packets to the server and the server sends the packets back to TCP. The TCP protocol is highly reliable, packets sent by TCP will be monitored so that data will not be lost or damaged during transport. That is why the download file is not corrupted even if the network has a problem. Of course, if the recipient is completely offline, your computer will give up and you will see a write error message that it cannot communicate with the remote host. The TCP protocol achieves this in two ways. First, it requests packets by numbering them. Second, it checks for errors by asking the recipient to send feedback received to the sender. If the sender does not receive the correct response, it can resend the packet to ensure the recipient receives them correctly. Process Explorer and other system utilities can display the connection type that the process creates. Here we can see the Chrome browser with TCP connections open to many different web servers: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) TCP connections on chrome 1.3.2.2, UDP UDP stands for User Datagram Protocol - a packet similar to a packet of information. UDP protocol works similar to TCP, but it includes all the checked and error-free things. When using UDP, the packet is only sent to the receiver. The sender will not wait to make sure the receiver has received the packets - it will continue to send the next packet. If you are a recipient and you miss some UDP packets because it's too bad you can't request those packets again. There is nothing to guarantee you are getting all the packages and there is no way to request a package again if you miss it, but in return, the computers can communicate more quickly. . UDP is used when speed is desired and error correction is not required. For example, UDP is often used for live broadcasts and online games. For example, suppose you are viewing live video images. Broadcast Live Stream usually uses UDP instead of TCP. The server only needs to send a stream of UDP packets to the computer to view. If you lose the connection for a few seconds, the video will freeze for a moment and then move to the current bit of TV, ignoring the Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) bits you have missed. Video or audio may be distorted for a while and the video continues to play without data loss. This works similarly in online games - if you miss some UDP packets, the player character may appear shifted on the map when you receive newer UDP packets. There is no point in requesting old packages if you lose them, and the game is continued without you. All the problems are what's happening right now on the game server - not what happened a few seconds. 1.3.2.3, Other protocols POP3 and SMTP (simple mail transfer protocols) are protocols used for both sending and receiving email. Basically, SMTP is used to send mail while the protocol used to receive mail is called the postal protocol (POP) and because it uses its latest version of 3, the name is POP3; but both of these protocols have different server addresses and it uses TCP to send and receive mail over the internet including sending reports. Hypertext transfer protocol (HTTP) is used to open a page on the web built by the HTML language which is hypertext markup language. This protocol uses both IP and TCP to manage the transmission. FTP (file transfer protocol) is used to share or copy or even send files over the web from one computer to another. But now, this protocol not only manages sharing and transferring files, but also helps download and upload files on the web (Zhang 2011). 2, Explain devices and network activity 2.1, Discuss the operating principles of network devices and server types. 2.1.1, Discuss the operating principles of network devices. To connect Internet connection from home to home and office electronic devices, it is inevitable that network devices such as Repeater, Switch, Router, Bridge or Hub. These devices share the same function in connecting and transmitting internet signals, but they have different characteristics. a, Repeaters For a LAN, the cap usually has a limit of 100m because the signal will be reduced on the line so it cannot go further. Therefore, in order to connect to remote devices, the network needs to have devices to amplify and reset the signal, so that the signal can travel far beyond this limit. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Repeater And the repeater is a device designed to serve as an amplification of the physical signal at the input and provide power to the output signal to continue to the next route in the network. This is also an essential device in the use of telegrams and telephones because they need to traditionally travel far away through fiber optics. Repeater is a device in class 1 (Physic Layer) in OSI model. When we use Repeater, the physical signal at the input will be amplified, thereby providing a more stable and powerful signal for the output, to be able to reach further locations. b, Hubs Hub is a device used for signal amplification, and is considered as a multi-port repeater. When a port on the hub receives information, the other ports will receive the information immediately. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Hub There are 2 types of Hub lung that are Active Hub and smarthub - Active Hub, this type of Hub is often used much more commonly, it needs to be powered when operating. Active Hub is used to amplify the incoming signal and divide the remaining ports to ensure the necessary signal speed when using. - Smart Hub, also known as Intelligent Hub, also has the same function as Active Hub, but it has integrated chip that automatically detects errors on the network. c, Bridges If the Repeater is the first layer in the OSI model, the Bridge is the second layer in this model (Data Link Layer). This tool is used to connect between two networks to form a large network, such as a bridge between two Ethernet networks. When there is a computer that transmits signals to another machine with two completely different networks, Bridge will copy the packet and send it to the destination network. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Bridge Thus, although different network computers can still transmit signals to each other without knowing the appearance of Bridge, because it works transparently. A Bridge can handle multiple network traffic as well as IP addresses at the same time. However, Bridge only connects networks of the same type and uses them for highspeed networks that will be more difficult if they are located far away from each other. d, Switches Switches are sometimes described as a multi-port bridge. While a Bridge has only two ports to connect two network segments together, the Switch is able to connect multiple segments together depending on the number of ports on the Switch. Like Bridge, the Switch also "learns" the information of the network through the packets it receives from computers on the network. The switch uses this information to build up the Switch panel, which provides information to help the packets arrive at the correct address. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Switch e, Router Layer 1 Repeater, Layer 2 Bridge and Router are Layer 3 network devices of the OSI model, it is capable of connecting two or more IP networks together. The feature of this network is that every computer connected to the network can communicate with the Router, while other networks and computers must be aware of the existence and participation of the Router. Router Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) f. Gateways Gateway lets you join two types of protocols together. For example, if your network uses IP protocol and someone's network uses IPX, Novell, DECnet, SNA ... or a protocol, Gateway will switch from one protocol to another. Gateway Through Gateway, computers in networks using different protocols can easily "talk" to each other. Gateway not only distinguishes protocols but can also distinguish applications like how you send e-mail from one network to another, convert a remote session ... g. Other devices In addition to the 6 listed devices, some other network devices are used. 2.1.2. Discuss the operational principles of server types. Server is a computer program that provides services for other computer programs (and for users). In data centers, physical computers that run server programs are also often referred to as a server. This computer can be a dedicated server or can be used for other purposes. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Server ( illustration ) In the client / server programming model, a server program will wait to receive and respond to requests from the client program. This client can run on the same computer as the server or run on another computer. A specific application in a computer that can act as a client with service requests from other or similar programs can also run as a server. a. Web Server Web Server is a computer on which to install web server software, sometimes it is called the web server itself. All web servers understand and run *.htm and *.html files. However, each web server serves a number of specialized file types such as Microsoft llS for *.asp, *.aspx ...; Apache for *.php ...; Sun Java system web server of SUN for *.jsp ... At the core of the web server is a web service that serves static content to a browser by downloading a file from the disk and transferring it to the network, to a web browser user. This complete exchange is done indirectly through a browser and a server connects to another device using HTTP. Any computer can go into a web service by installing service software and connecting to the internet. There are a lot of web application software on the net, including domain name software from NCSA and Apache, and commercial software from Microsoft, Netscape and many others. b. Applications Server It is also known as AppServer. A program that controls all application activities between users and end-layer applications of a business organization or databases. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Typical application services are typically used for basic transaction-matching applications. To support high demand, an application service must have internal redundancy, control for high availability, high-level presentation, application service delivery, and support for link access. database. c. Printer Server Print service is installed on a network to route print requests from the network computers of that network. The control server prints the required file and sends the file to the requested printer - A print service that allows multiple users to use the same printer on the network. d. Proxy Server It is a server that stands between an application, as a web browser, and a real server. It blocks all requests to the real server if it is able to fully respond to requests, otherwise it will forward requests to the real server. Proxy servers have two main purposes: It is possible to increase the flexibility of user group activities, because it stores the results of all requests for a certain amount of time. Proxy servers also require filtering to lock or not allow a particular connection to request to or from the server. e. Database Server Database Server is a computer on which the Database Management System software is installed. We have database management system such as: SQL server, MySQL, Oracle ... A database service is a basic application on the server / workstation architecture model. The application is divided into two parts. a part runs on a workstation (where users accumulate and display database information) and the rest runs on the server, which is supposed to be a data connection and store - made show. f. FTP Server FTP server: FTP (short for File Transfer Protocol translated as "File Transfer Protocol") is often used to exchange files over TCP / IP communication network (such as Internet - network external - or intranet - intranet). Operation of FTP requires two computers, a server and a client). The FTP server, running software that provides FTP services, is called a server, listening to the service requests of other computers on the network. The client running the FTP software is for the user of the service, called the client, and initiates a link to the server. An FTP service is a software application that runs file transfer protocols, which exchange files over the internet. FTP works similarly to the way HTTP makes and transmits web pages from a server to a browser user, and SMTP for sending e-mail via the internet. Like these technologies, FTP uses the Internet's TCP / IP protocol to transfer data. FTP is widely used to download a file from a server using the internet or vice versa (eg uploading a website to the server). Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) g. DNS Server DNS Server is a domain resolution server. Every computer, network device connected to the Internet is connected to each other by IP address (Internet Protocol). To facilitate the use and easy to remember, we use the name (domain name) to identify the device. Domain Name System DNS (Domain Name System) is used to map domain names to IP addresses. h, DHCP Server DHCP server: DHCP (Dynamic Host Configuration Protocol) is an automatic configuration protocol for IP addresses. The computer is configured automatically, thus reducing interference in the network. DHCP server is a server with DHCP service installed, it functions to manage the allocation of dynamic IP addresses and TCP / IP configuration data. There is also an answering task when the DHCP Client has a subscription contract. i.Virtual Private Server - VPS VPS is a server type separated from the above physical server by using virtualization technology. From a separate server, it is possible to split into many different virtual servers that function as physical servers and share resources on the original physical server. Virtual Private Server - VPS k. Cloud Server Cloud Server is a server that combines a lot of different physical servers together with SAN storage system with outstanding access speed, which helps the server to operate quickly, stably and limit the downtime of downtime. Cloud server is built on Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) cloud computing technology so it is easy to upgrade each part of the device during use without disrupting the process of using the server. l. SMTP server SMTP server: SMTP (Simple Mail Transfer Protocol) is a standard for e-mail transmission over the Internet. SMTP server is a server that helps you send mail to other email addresses on the internet. Most web and mail services transfer and store mail on the network and send it over the internet. Today most people think that mail service is an abbreviation of the internet. However, mail services are developed primarily on the basis of the internet. (LANs and WANs). 2.2. Explore a variety of server types and demonstrate server selection, considering a certain scenario regarding cost optimization and performance. There are many factors to consider when choosing a server, including virtual machines (VMs) and unified containers. When choosing a server, pay attention to the importance of some features depending on the use case. Remember, security is also extremely important, in addition to the need for additional protection, detection, warning and recovery features, including encryption of the original data to protect data on the move and The data is stored, updating the event log continuously to prevent duplicates that cannot be deleted. If the server uses internal memory, selecting disk type and capacity is equally important as it may significantly affect input / output (I / O) and resilience. 2.2.1. Factors to consider when choosing a server Select the server that meets the main needs: If you want to improve email usage in your business, an email server is a priority. Or if your business needs to manage a large volume of documents, choose a dedicated server to share data immediately. Appropriate budget: You should set a budget right from the start and based on that budget to have an appropriate plan. The server market is quite diverse and you can have more than 3-4 options for a budget level. Select brand: After deciding which type of server to buy, you need to choose a provider that is known for that type of server. This ensures you will buy a server from a reputable, well-known brand and is fully supported during use. Select operating system: Just like when buying personal computers, the operating system plays a very important role in ensuring smooth operation of applications. Similarly, the server Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) needs an appropriate operating system as a platform to handle thousands of different user commands from the entire user of the system. Ability of extension: The server is invested for long-term use, so the level of expansion of the system should be considered. Usually the hard drive and memory will be concerned about how much can be extended. Using RAID settings will also ensure that the business does not lose data when any hard drive in the system fails Support and maintenance: Most small businesses have no IT department available, so they often have to outsource. But if you buy a server from a reputable provider, you will always be offered the maintenance package included. Virtualization capability: Using virtualization will increase operational efficiency for server systems and is often concerned by small and medium enterprises to save costs. This feature is also increasingly popular to help businesses create new servers based on available hardware based on software. So you need to consider whether the processor and the hard drive can meet the requirements or not. 2.2.2. Select server for business a. For small and medium enterprises The basic needs of a business such as enterprise information storage, website hosting, software running can be solved with simple technologies such as hosting. However, when the demand at maintaining a stable system, beautiful website, stable speed that meets a traffic of 100-700 times a day, the choice of server is enough to ensure the effective business capacity. fruit. Besides, for higher demands such as storing large amounts of information or needing to exchange data back and forth, server use can be considered mandatory. b.For big business The server for large businesses is a necessity because the demand for management capacity and operating speed are always top priorities. Some of the needs that server helps solve for this business object include: - Save and manage a large amount of business information, manage project information ... - Run the software: management, finance ... - Backup, data backup - Safe and secure data protection - Anti-local attack Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) - Managing and operating remote systems - Increase processing capability, enabling powerful processing capability during peak periods, the need for resources such as RAM, CPU, high speed transmission ... 2.3. Discuss the interdependence of workstation hardware with related network software. Network hardware - This is a single component of the data transfer network and facilitates computer functions. Although it contains many hardware components, there are many different types that make up the total functionality of the network. Router - it is a device that is connected to multiple channels for different networks. It works with the help of the interface. It is in the network's layers that create a path to transmit information to routers that act as processing units. It sets up some rules and uses protocols to identify information packets to its final destination. Gateway - it works with different protocols. It is in the network node and interfaces with another network. Switch contains more intelligent centers. It is capable of checking data, identifying sources and forwarding data. It performs better than the center. The switches are mainly active. Bridges - it allows a large network area into a smaller, more efficient segment. They make the data updated and create connections on both sides. It transmits information to the correct location. It maintains optimal work on both sides of the network. Modems - it converts data into between similar forms. It is capable of implementing some advanced network features. File server - network file server is a computer system used for the purpose of managing file systems, network printers, handling network communication and other functions. A server that can be reserved is such a case, its entire processing power is allocated to the network function or it may not be dedicated, which means that part of the server functions are Allocate as a workstation or DOS-based system. Network operating system - it is loaded into the server's hard disk along with system management tools and user utilities. When the system is started, the NOS starts and the other server is under its control. Workstations - workstations or nodes are attached to the server via network interface cards and cables; Workstations are usually smart systems, such as IBM computers. But the DUMV terminal is used in mainframe computers. The concept of distributed processes depends on the fact that the personal computer attached to the network performs its own processing after downloading the program and data from the server. Therefore, a workstation is called an active device on the network. After processing, the files are stored back on the server where other workstations can use them. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Network interface card - all devices connected to the LAN need a network interface card to plug into the LAN. For example, a PC needs to have an Ethernet card installed in it to connect to Ethernet LAN. Network cabling - when the server, workstation and network interface card are set, the network cable is used to connect everything together. The most common type of network cable: + Twisted twisted wire + Coaxial cable + Optical cable. These are interdependent to implement the network properly. This is the basic process of complete connection. This is a suitable system for insurance industries to apply this process to operate effectively and efficiently. 3, Network system design. 3.1, Design a networked system to meet a certain specification. 3.1.1, Request. I was recruited to be a network engineer by a high-tech network solution development organization and working on a project for a local educational institution (Specifically, I will act as a network engineer for BTEC FPT International College). I will need to analyze the specification from the organization below to complete this project within a certain time frame with the requirements set out as follows: People: 200 students, 15 teachers, 12 marketing and administration staff, 5 higher managers including academic manager and program manager, 3 computer network administrators Resources: 50 student lab computers, 35 computer staff, 3 printers Building: 3 floors, all computers and printers are on the ground floor outside the IT lab - a laboratory is located on the first floor and another is on the second floor. 3.1.2, Design plan and expected cost. 3.1.2.1, Design plan. At the request of the lesson, the building consists of 3 floors: - On the ground floor, teachers and staff at the school will be designed here. Besides, there are rooms for network administrators and managers. The printer is also designed on the ground floor. In addition, I also propose to add some servers to use as File Server and Web Server. We can also use virtualization technology to save costs (Virtual Private Server). - Level 1 and 2 are labs. With 50 computers for students, we divided into 2 laboratories, 1 room on the 1st floor and 1 room on the 2nd floor. The number of computers for students per floor is 25 units. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Let's see the physical diagram illustrating the above proposal: Network physical diagram of the building 3.1.2.1.1. Design plan on ground floor. Network physical model on the ground floor Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) a, Management Department. In this room, we will have 5 computers for 5 senior managers, including the academic manager and program manager. b, Computer network administrator room. With 3 computers, 3 network administrators will manage the entire network in the school such as switch and router management, server management, security for the intranet, ... c, Teachers and staff rooms in the school. Teachers and staff will also be supported by the school and printers to work. These devices are arranged on the ground floor. d, Equipment department. This is the room used to place devices such as switches, routers and servers (as mentioned above, I would suggest installing one or more servers to work internally even though the threads are not required). 3.1.2.1.2. 1st and 2nd floor. Network physical model of LAB On these two floors there will be the same layout because they are all arranged in a lab for students. With 50 computers divided into 2 labs, each room will have 25 computers. Besides, each room will have 1 computer for teachers to use for teaching as well as to manage students. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) 3.2, Check and evaluate the design to meet the requirements and analyze user feedback. 3.2.1, Check and evaluate the design for requirements. Network system of British College BTEC FPT is a network system used for learning purposes and helps improve the quality of school teaching. Since the deployment network must meet some of the following requirements: Operability: The first criterion is that it must work, the network must meet the user's work requirements, must provide the ability to connect among users, between users and the application at a speed and Acceptable reliability. Can be managed: The network must be designed to be easy to monitor and administer to ensure smooth operation of the features. Exchange data quickly and safely: The exchange of information and data between teachers in the school, between the central office and schools is carried out quickly and safely, high speed of information transmission, meeting operational needs of school. Ability to manage centralized data information: Building a centralized management model, all data is gathered in one place to both keep information confidential and convenient for managing and backing up data. Simultaneously with centralized management from the central office can easily manage remote offices through the support of application programs. Remote administration and administration capabilities: The school can operate its operations remotely through the network. Therefore, saving travel costs and improving the effectiveness of teaching management of the school. Ability of extension: The network must be expanded, the original design must be expanded without causing a major change in the overall design. Compatibility: The network must be designed with a pair of faces that are always oriented towards new technology and must ensure that it does not prevent the introduction of new technologies in the future. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) 3.2.2. Check and evaluate costs. 3.2.2.1, Equipment cost. 3.2.2.1.1, 85 computers. a, Tower. Tower: is the main part of the computer. That is the part containing the necessary hardware. In this case I will choose Tower ACER ASPIRE ATC-780: Tower ACER ASPIRE ATC-780 Here are a few specifications: Model: Producer: Origin: ASPIRE ATC-780 DT.B59SV.002 Acer China Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) CPU: CPU type: CPU speed: Caching: RAM type: RAM capacity: Bus speed: Hard drive type: Hard disk capacity: Optical disc type: Graphics processor: Graphics card chipset: Graphics card capacity: Sound technology: Audio standard: WiFi standard: LAN Standard: OS Size: Weight (kg): Intel Core-i3 6100 3.70 GHz 3 MB Cache SDRAM DDR3 4 GB 1600 MHz SATA 1 TB SuperMulti DVD Integrated Intel HD Graphics Intel HD Graphics 530 Share High Definition High Definition Audio IEEE 802.11 b/g/n 10 / 100 / 1000 Mbps Windows 10 Home SL 175x426x382 mm 10 kg It sells for $ 350 (at the time the network is being designed). b, Monitor. Monitor: if there is no screen, you will not be able to view this website or any other program. I will propose a 21.5-inch HP N220 computer screen (Y6P09AA): Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Computer screen Some basic parameters: 21.5 inch FHD IPS screen 21.5-inch large screen size, 16: 9, N220 ratio allows easier handling of work. The screen's resolution is FHD (1920 x 1080p) and the wide viewing angle IPS 178º technology allows easy viewing of content at different angles while ensuring sharp quality. A common VGA and HDMI connection The screen is equipped with common connectors such as VGA and HDMI. Screen adjustment buttons are located on the right side on the back. Solid base with elegant silver color, can fold the screen to the front and back to suit the sitting posture. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) The back of the screen High-end display technology Optimized by HP's high-end display technology, the N220 screen gives a comfortable viewing experience, without eye fatigue even at night thanks to the extremely low level of blue light. The selected screen allows the blue light to be turned off if desired. N220 has extremely low power consumption, saving maximum cost of use. The screen meets ENERGY STAR 7.0 and EPEAT Silver standards, and uses environmentally friendly materials. With the above configuration, it will cost about 100 USD. c, Mouse and keyboard. Currently on the market there are many different types of mice and keyboards, which are diverse in types, so I will not recommend specific equipment. The cost for both the keyboard and the keyboard will be about 50 USD. So for a set of computers we will (including Tower, Monitor, mouse and keyboard) we will spend 500 USD. At the request of the lesson, the school will have 85 computers, so the expected cost is 42 500 USD (500 * 85 = 42 500 USD). Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) 3.2.2.1.2, Printer. At a cost of about 100 USD, we can choose LASER printer CANON IMAGECLASS LBP6230DN: Compact design Canon Laser ImageClass LBP6230DN laser printer in white color combined with black color gives an elegant, neat design with rounded edges that look a lot like the LBP6030W but slightly larger because the paper tray is upgraded to 250 sheets. Canon printer Fast printing speed Canon laser printer ImageClass LBP6230DN helps improve work efficiency. With a resolution of 600 x 600 dpi, fast printing capability of 25 pages / minute and automatic 2-sided printing, you can easily get quality prints in short time. 250-sheet paper tray The printer is equipped with a paper tray that can hold up to 250 sheets, you do not need to add paper regularly, which helps ensure continuous printing capability. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Canon printer Automatic shutdown mode In addition, Canon laser printers are programmed with sleep mode and automatic shutdown if not working for a certain period of time, saving you electricity costs. With 3 numbers, we will spend 300 USD to buy a printer. 3.2.2.1.3, Server Since this is a small LAN, I will choose the Server for about 1500 USD. The IBM System server x3500 M4 (7383C2A) will be the right choice in this case: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) IBM server Some specifications: Type of CPU used Number of CPUs Caching Main memory RAM Memory type BUS speed of RAM Storage HDD communication type Optical drive PSU Intel Xeon E5-262 1 CPU 15MB 8GB DDR3 1333MHz SATA DVD-ROM 750W With 2 server machines, we will spend about 3000 USD. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) 3.2.2.1.4, Switch. With 3-storey building, we will use 3 Switch layer 2 and 1 Switch Core. Switch layer 2 will cost 500 USD / unit, Switch Core will be more expensive and cost about 1000 USD. Thus, we will spend 2500 USD to buy Switch. 3.2.2.1.5, Router. For a small network, I would suggest a Router device that costs $ 100 and just one device is enough. Thus, the cost for the device will be 48 400 USD. 3.2.2.2, Other costs. In addition to the cost to buy the equipment, we can also mention some other costs such as initial installation costs, operating costs, ... In order for the network to run smoothly, it will take about 50 000 USD. 3.3, Installing and configuring network services and applications. 3.3.1, Basic configuration. Set hostname for router and switch: Each device needs a name that is easy to manage. Set IP: Each device needs an IP to easily manage and identify. Set password: In order to improve security, switches and routers should use access passwords, as well as limit the number of visits for some authorized users. Besides setting a password, we can use SSH remote access method to improve security. SSH configuration: Besides improving security more than Telnet, SSH helps network administrators easily manage devices. 3.3.2, VLAN. VLAN stands for Virtual Local Area Network or virtual LAN. A VLAN is defined as a logical group of network devices and is set up based on factors such as functions, parts, applications ... of the company. Technically, VLANs are a broadcast domain created by switches. Normally, the router plays the role of creating the broadcast domain. For VLANs, switches can create broadcast domains. Benefits of VLANs: • Bandwidth savings of the network: VLAN divides the LAN into several small segments, each of which is a broadcast domain. When there is a broadcast, it is Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) transmitted only in the corresponding VLAN. Therefore, dividing VLANs saves network bandwidth. • Increased security: Because devices on different VLANs cannot access each other (unless you use a router that connects VLANs). As in the above example, computers in VLAN accounting can only communicate with each other. The machine in VLAN accounting cannot be connected to the computer at VLAN engineer (Engineering). • Easily add or remove computers to VLANs: Adding a computer to the VLAN is simple, just configure the port for that machine to the desired VLAN. • Great network flexibility: VLANs can easily move devices. Suppose in the above example, after a period of use the company decided to leave each part on a separate floor. With VLANs, you only need to reconfigure switch ports and place them on the required VLANs. VLANs can be configured static or dynamic. In a static configuration, the network administrator must configure each port of each switch. Then, assign it to a VLAN. In the dynamic configuration, each switch port can configure its VLAN based on the MAC address of the connected device. Trunk port: • When a link between two switches or between a router and a switch conveys the traffic of multiple VLANs, that port is called trunk port. • The trunk port must run special communication protocols. The protocol used may be Cisco's proprietary ISL protocol or IEEE 802.1q standard. 3.3.3, DHCP. DHCP is an acronym for Dynamic Host Configuration Protocol (Dynamic Host Configuration Protocol). It is a protocol for allocating IP addresses for devices on a network. DHCP is essential to determine the number of devices that can connect to a network. It ensures that all devices on the network have an IP address and no device has the same IP. Without DHCP, devices on the network may experience IP conflict errors, making network administration difficult. Manually assign IP addresses, IP conflict resolution is a tedious, time-consuming task even on small network systems. For larger networks, it is almost impossible. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) DHCP Server and DHCP on Router Basically, DHCP allows network administrators to automate the process of allocating IP addresses and because these addresses are dynamic addresses, you'll rarely see a device on the network. granted IP address. This allows an almost unlimited number of devices to connect to the network. There are three components within the DHCP architecture, including DHCP clients, DHCP servers, and DHCP relay agents. The DHCP client is any device that can connect to the network, and can communicate with the DHCP server. It could be a phone, a computer, but it could be a network printer, a server, etc. DHCP server is a device that allocates an IP address. DHCP relay agents are intermediate devices that relay requests between a DHCP client and a DHCP server. They are not an essential component of a normal network. However, when working with large, complex networks, they become very necessary. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) DHCP relay agents 3.3.4, Static routing. For static routing the route information must be entered by the network administrator for the router. When the network structure has any changes, it is the network administrator who has to delete or add path information to the router. Such types of routes are called fixed paths. For large networks, the maintenance of the routing network for the router like this takes a lot of time. Also for small networks, there is little change. This work is less costly. Because static routing requires network administrators to configure all route information for the router, it does not have the flexibility of dynamic routing. In large networks, Static routing is often used in conjunction with dynamic routing protocols for some special purposes. 3.3.5, NAT. Network Address Translation (NAT) is like a router, forwarding packets between different network layers on a large network. NAT translates or changes one or both addresses inside a packet when the packet goes through a Router, or some other device. Usually NAT usually changes the address is usually the private address (Private IP) of a network connection to a public address (IP Public). NAT can also be considered a basic firewall. NAT maintains a table of information about each packet sent. When a network computer connects to a website on the Internet header, the source IP address is replaced with a public address that is preconfigured on the NAT server, after having a packet returned to NAT based on the record it has saved. About packets, change the destination IP address to the PC's address in the network and forward it. Through that mechanism, network administrators can filter packets sent to or sent from an IP address and allow or prevent access to a specific port. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) 3.3.6, ACL. ACLs (Access control lists) are also known as access lists, which are a sequential list of statements called ACEs (Access control entries), applied on a certain Interface, and on input or output buffers, Router control rejects or forwards packets based on information in IP header or TCP / UDP header. Purpose of using ACL: Limit network traffic to increase network performance Provide control of communication flow by limiting delivery updates. Provides basic security level for network access. Terms of communication are allowed to be forwarded or rejected by the Router. Ability to control user access Activities of ACLs: When the packet arrives at the Router, the serial device checks against ACEs in the ACLs to decide whether to allow the packet to go through Interface or reject. The ACEs in the ACLs are checked sequentially from the first ACE to the last ACE. If certain ACE conditions are met, then ACEs need to be checked. At the end of the ACLs is an implicit ACE that refuses to allow the packet to pass. Therefore, if the packet does not meet the conditions for the above ACEs, the packet will be dropped. 4, Deploy and diagnose networked systems. 4.1, Implement a network based on a prepared design. 4.1.1, Basic configuration. a, Set hostname for devices. On the router, we proceed to configure terminal terminal and name it: Set hostname for Router Similar to Switch Core, Ground floor switch, 1st and 2nd floor: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Set hostname for Switch Core b, Set IP. The outside of the router will have a public IP address of 200.200.1.1 and the inside surface will be the 172.17.0.0/16 network range Internet (demo) On the router, we will go to the gateway to connect to the network and the port connected to the Switch Core to set the IP: Set IP for interface s2/0 on Router Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Similarly on the Switch Core, at the port connected to the Route we will set the IP to 172.17.0.254 Set IP on Switch Core On the Switch on the ground floor, the first floor and the second floor we enter vlan 1 to set them IP to 172.17.1.1 (SW1), 172.17.1.2 (SW2), 172.17.1.3 (SW3) and their default gateway for 172.17.1.254 , point to Switch Core. c, Set password. Setting passwords on routers and switches is the same. We set up the password console one by one, enable password and encrypt all password types to MD7: Set password on Switch Core d, SSH configuration. Here, I create 3 usernames, u1, u2 and u3, respectively for 3 network administrators in the school: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) SSH configuration on Switch Core Similarly, configure the router and other switches one after another. 4.1.2, VLAN a, Create VLANs. I will create the following VLANs in turn: VLAN 1 (172.17.1.0/24): Default for switches VLAN 10 (172.17.10.0/24): Management VLAN 21 (172.17.21.0/24): Employee VLAN 22 (172.17.22.0/24): Teacher VLAN 31 (172.17.31.0/24): Student in Lab 1 VLAN 32 (172.17.32.0/24): Student in Lab 2 VLAN 41 (172.17.41.0/24): Vlan is used when testing for Lab 1 VLAN 42 (172.17.42.0/24): Vlan is used when testing for Lab 2 VLAN 50 (172.17.50.0/24): Client network VLAN 97 (172.17.97.0/24): Printer VLAN 98 (172.17.98.0/24): Server VLAN 99 (172.17.99.0/24): IT b, VTP configuration. - Help synchronize information of VLANs on all Switches together. - Asynchronous port because the switch has different port numbers. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) - Conditions for obtaining VTP: • The lines between the Switches must be trunk: Configuring trunking Configure VTP mode server on switch core: Configure VTP mode server on switch core Configure VTP mode client on switch ground floor, 1st and 2nd floor: Configure VTP mode client on switch ground floor, 1st and 2nd floor c, Routing between VLANs After the created VLANs, there is a problem that other VLANs cannot communicate with. In order for them to communicate, we configure routing between VLANs. On SW-L3 configuring routing images between Vlans ensures that other VLAN PCs communicate with each other: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) VLANs in the intranet system 4.1.3, DHCP. On Switch Core, DHCP configuration grants dynamic IP to VLANs: DHCP configuration on the switch core In addition to providing dynamic IP for VLAN 10, I also reserve the first 10 IPs of the range to use when needed. For the remaining VLANs, we perform the same configuration. 4.1.4, Static routing. Configuring on the router (200.200.1.2 is the IP gateway connected to the network): Static routing on router And on the switch: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Static routing on switch core 4.1.5, NAT. Mechanism of 2-way NAT processing. • NAT processing packets from inside a LAN going outside the internet (outside) • NAT processes packets from outside the internet (outside) to the local network (LAN) Configure NAT on the router I created an ACL that banned IP ranges of VLAN 41 (172.17.41.0/24) and VLAN 42 (172.17.42.0/24) out of the internet for the purpose of using these two IP ranges for testing. In addition, I also allow machines from outside the Internet to access Web Server through ports 80 and 443 (172.17.98.80 is the IP of the Web Server). 4.1.6, ACL a, Prohibit VLAN test1 and VLAN test2 internet access. As mentioned in Section 4.1.5, I have created ACL 1 that prohibits these IP ranges from accessing the internet for exams at two labs. b, Only allow VLAN it ssh to switch and router. On the router, I do the following: Configure ACL to SSH Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Similar to switch. 4.2, Analysis of test results compared with expected results. a, Basic configuration. IT department machines can access switches and routers via SSH protocol: IT computer SSH to the Router b, VLAN. After creating VLANs, computers belonging to the same VLAN can communicate with each other. And after routing between VLANs on Switch Core, other VLAN devices can also ping each other. Example of a VLAN 22 computer (teacher) pings to VLAN 32 (student2 in Lab 2): Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) The teacher's computer pings to the student's computer All 4 packets were sent successfully. c, DHCP. After configuring DHCP on the core switch, the devices in the network are completely provided with a free IP corresponding to each VLAN, which reduces the effort for network administrators, no need to install manually. Example of automatic receipt of an IPv4 of a computer in VLAN 99 (IT): Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Computer under VLAN 99 receives dynamic IP We can also apply for a different IP address. d, Static routing and NAT Configuring static routing and NAT helps devices access the internet: Example of a computer in VLAN 31 (student1) that accesses Google DNS: DNS Google And access is completely successful: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Successful Google DNS access But for VLAN 41 (test1) - VLAN for the exam, it is completely inaccessible. This avoids cheating of students: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) The VLAN for the exam does not access the internet And when we try to ping Google DNS: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) The VLAN for the exam does not access the internet e, ACL Configuring ACL only allows VLAN IT to access the router and switch, preventing any unauthorized access. On a VLAN IT computer we can use the SSH protocol: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) IT computer SSH to Router successfully For other VLAN computers, it will not be possible to SSH into the router and switch: Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com) Computer does not belong to VLAN IT then it fails SSH to the router 4.3, Proposing potential improvements for networked systems. 4.3.1, Scaling up schools. We can completely open another Lab for students. With the target of 25 students and 1 student machine, the new Lab room will be invested 13,000 USD. There is also a lab management switch installed. 4.3.2, Redundant configuration for LAN. In case the network connection with ISP FPT has trouble, the whole LAN will not access the Internet. In this case, we will hire an additional line and a public IP to build a redundant network path. Conclude In the above reports, I have presented the following main ideas: Check their network rules and protocols. Explain devices and network activity. Effective network design. Deploy and diagnose networked systems. Document shared on www.docsity.com Downloaded by: King786 (deadlyshaz786@gmail.com)