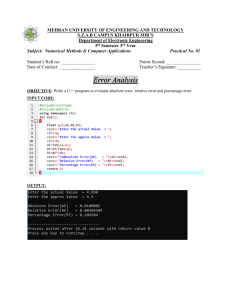
professional-ethics-multiple-choice-questions-and-answers-converted
advertisement

Professional Ethics Multiple Choice Questions & Answers Pdf 1: Computer ethics has its roots in the work of ___ during World War II. (A) Hermen Horllerith (B) Norbert Wiener (C) Blaise Pascal (D) Charles Babbage Ans: B Norbert Wiener 2:____ is a self- replicating program that can cause damage to data and files stored on your computer. (A) Virus (B) Freeware (C) Piracy (D) None of the given Ans: A Virus 3:Making and using duplicate hardware and software is called ___ (A) Piracy (B) Free copy (C) Copy right (D) None of these Ans: A Piracy 4: The protection of hardware, facilities magnetic disks, and other illegally accessed, stolen, damaged or destroyed items refers to ____ (A) Physical security (B) Personal security (C) Personnel security (D) None of the given Ans: A Physical security 5:____ refers to software setups that permit only authorized access to the system. (A) Personnel security (B) Personal security (C) Physical security (D) None of these Ans: B Personal security 6:General guidelines of computer ethics are needed for ____ (A) Cracking (B) Computer crime (C) Protection of personal data (D) All the above Ans: D All the above 7:“Cracking” comes under ____ (A) Website Service (B) Transcription (C) Computer Crime (D) Data Security Ans: C Computer Crime 8:____ is the illegal access to the network or computer system. (A) Security (B) Cracking (C) Virus (D) Piracy Ans: B Cracking 9:____ is a set of rules for determining moral standards or socially acceptable behaviour. (A) Protocol (B) Standard (C) Ethics (D) None of the given Ans: C Ethics 10:Running other software on idle computer without the knowledge of the organization is called theft of ____ (A) Software (B) Computer (C) Computer time (D) Use Ans: C Computer time 11:_____ refers to protecting data and computer system against dishonesty or negligence of employees. (A) Personnel security (B) Personal security (C) Physical security (D) None of these Ans: A Personnel security 12:Which of the following is not a way of protection? (A) Physical Security (B) Personal Security (C) Piracy (D) Personnel security Ans: C Piracy 13:Who among the following began to examine unethical and illegal uses of computers by computer professionals in mid 1960s Menlo Park, California? (A) Charles Babbage (B) Bill Gates (C) Norbert Wiener (D) Donn Parker Ans:D Donn Parker 14: You can protect sensitive data from prying eyes using (A) File permissions (B) File locks (C) Passwords (D) Encryption Ans: A File permissions 15:A hacker contacts your phone or E-mail and attempts to acquire your password is called (A) Spamming (B) Spoofing (C) Phishing (D) None of these Ans: C Phishing Question: 11 _____ refers to protecting data and computer system against dishonesty or negligence of employees. (A) Personnel security (B) Personal security (C) Physical security (D) None of these Ans: A Personnel security Question: 12 Which of the following is not a way of protection? (A) Physical Security (B) Personal Security (C) Piracy (D) Personnel security Ans: C Piracy Question: 13 Who among the following began to examine unethical and illegal uses of computers by computer professionals in mid 1960s Menlo Park, California? (A) Charles Babbage (B) Bill Gates (C) Norbert Wiener (D) Donn Parker Ans:D Donn Parker Question: 14 You can protect sensitive data from prying eyes using (A) File permissions (B) File locks (C) Passwords (D) Encryption Ans: A File permissions Question: 15 A hacker contacts your phone or E-mail and attempts to acquire your password is called (A) Spamming (B) Spoofing (C) Phishing (D) None of these Ans: C Phishing