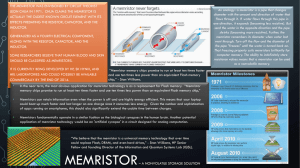
Publishing Journal Title Journal https:// Memristor and its Use in Physically Unclonable Functions Circuits Ludmil Petkov Computer Science Department, Oxford Brookes University, Oxford, United Kingdom E-mail: pl205306@gmail.com Received xxxxxx Accepted for publication xxxxxx Published xxxxxx Abstract This research investigates the possibility memristors to be used in the design of physical unclonable functions (PUFs) for cyber-security applications. LTSpice simulation software is used for better understanding of the processes and the results of the secure circuits. Keywords: PUF, CRP, LTSpice, TEAM information stream of bits (set of outputs or responses)(Joshi, Mohanty, & Kougianos, 2017). PUF are clearly object-related. This distinguishes them from biometric factors like fingerprints which relate to human beings. Nevertheless, some aspects are similar. The unavoidable variability in the physical world is taken advantage by the PUF for example different variations during process fabrication. It is impossible to make two identical integrated circuits (IC). Exactly these variations are useful for cyber-security applications where the size of the device is important. The physical world variability guarantees the unclonability. A valid challenge response pairs will not be produced. From Figure 1-1 It is evident that the challenge question is presented to the hardware circuit that generates the response, opposed to the traditional key storing in a non-volatile memory. 1. Physical Unclonable Functions The basic concept of Physical Unclonable Function (PUF) needs to be clearly defined and clarified for this research. It appeared not an easy task as the variety of circuits considered PUF is increasing. Some constructions are not recognised as PUFs because they were created before the name was created or their inventors were not aware that they can have cryptographic applications. It is attempted to class the constructions according to similarity and then the observed properties are reaffirmed. An analogy can be used and resemblance of the PUF can be found to fingerprint. It is inherent, expressing individualism and it is unclonable. Another human cannot be created with the same fingerprint, even the twins have different fingerprints. The main property of the PUF is that it cannot be reproduced. In general the natural properties of hardware devices (set of inputs or challenges) are mapped by a random function (PUF) to an exclusive xxxx-xxxx/xx/xxxxxx 1 © xxxx Publishing Ltd Journal Ludmil Petkov et al transistor. The transistor is not a fundamental circuit element. It is possible to write a Thevenin’s equivalent circuit for the transistor which has a source of energy and resistance in series connected to a load. In the 1960s at Berkeley University professor Leon Chua was the first person to put nonlinear circuit theory on a firm mathematical foundation. He is compared with his contribution to circuit theory to Albert Einstein’s theory of relativity. Professor Chua has a significant accomplishment as he has a mathematical system to prove whether a circuit is going to work or not. While working on his nonlinear circuit theory he noticed that there was something missing from the circuit equations. The four fundamental issues are the voltage, the charge, the current and the flux as shown on fig. 21. There are 6 equations of relating these elements but only three fundamental passive devices. He postulated based on his observations that there should be a fourth circuit element. It can be expressed as: M = dφ/dq. Figure 1-1 Traditional non-volatile memory key storage versus the concept of PUF (Joshi et al., 2017). Reverse engineering and cyber-attacks can be prevented efficiently by using PUFs. Some other applications include providing secure keys, random number generation, key management and generation, hw/sw binding, secure/trusted boot, trusty anchoring and root of trust. PUFs can be used as watchdogs for components with embedded chip. Figure 1-2 Smart card application. The card body is monitored by the chip. Courtesy of NXP. During the manufacture of the chip, the PUF’s environment critical parameters are measured and stored within the chip as exclusive parameter. The environment is authenticated by calling the stored metric. An attempt to reverse engineer the chip will change the environment and will fail the fingerprint check of the PUF(“Semiconductor Engineering .:. Physically Unclonable Functions - Semiconductor Engineering,” 2019). Figure 2-1 Showing the four fundamental circuit elements with two-terminals (Kavehei et al., 2010). 2. Memristor The equations that describe this element are: The memristor is a device with different applications. It is the fourth fundamental passive circuit element. Generally, only three passive circuit elements were known before: the resistor, the capacitor and the inductor. All the electronics built was based on only these 3 devices and the most recent invention the 𝑣𝑣 = 𝑅𝑅(𝑤𝑤, 𝑖𝑖)𝑖𝑖 2 (2-1) Journal Ludmil Petkov et al 𝑑𝑑𝑑𝑑 (2-2) = 𝑓𝑓(𝑤𝑤, 𝑖𝑖) 𝑑𝑑𝑑𝑑 Where, f and R are the function of time, v and i are the voltage and current, w is the state variable of the device. It was named a memristor, because essentially it is a resistor with memory. The circuit element diagram that he invented looks like a changed a little bit resistor fig.22. Figure 2-2 The symbol of memristor. Figure 2-3 I-V characteristics of memristor “pinched hysteresis loop”. The memristor exists in order to relate the flux in a circuit to the charge. Professor Chua published a paper “Memristor-the missing circuit element” (Chua, 1971) where he mathematically proves that such an element exists and makes a complete set of the known circuit elements. It was difficult to the other scientists to figure out what physics could give rise to a coupling between flux and charge in a circuit. Sung-Mo (Steve) Kang a graduate student of professor Chua have realised that an important issue of the memristor is that it is a passive device with state (Chua & Kang, 1976). There is a memory within the memristor which essentially is represented by one or more state variables for the device. In fact, the memristor is not characterised by only one equation. Actually, to be completely characterised two equations are required. One equation essentially states that there is quasi-static relationship between voltage and current but the resistance in that equation depends upon the state of the device in any given point of time. Then the other equation is a time dependant equation which shows how the state variable evolves in time. The two equation are needed in order to put a model for the memristor into SPICE simulation to study it. These two equations don’t say anything about flux. Therefore, if there is a device that has a state issue that evolves in time it can be a memristor. It was predicted according to the two equations that the memristor has an I, V curve that looks like a bowtie. It was called by Leon Chua a pinched hysteresis loop. In his paper he stated that if you see a pinched hysteresis loop I, V curve probably this is a memristor. The memristor is a fundamental element because it is impossible a circuit to be designed with the other three elements, that will have the same I, V characteristic. It was proven mathematically by professor Leon Chua. Even before Chua there were publications showing pinched hysteresis loops, but the scientists did not know what they were. They were memristors but they couldn’t characterise them. They were dynamical devices that could be only characterised by two equations. The physical realisation took some time after the theoretical definition was announced. Hewlett-Packard research lab reported that has managed to create a simple device with two platinum electrodes on either side and a thin film of TiO2 in the middle (Strukov, Snider, Stewart, & Williams, 2008). The TiO2 is a semiconductor that is auto doped. If a little bit of oxygen is taken out from the TiO2 , this essentially is n-type doping of the material as shown in fig.2-4. The oxygen vacancies that are left inside the material are positively charged. Those vacancies are very slightly mobile. If a large electric field is applied on these vacancies, they can be pushed toward the left. So, this reduces the TiO2 film, that lowers the resistance. When the oxygen vacancies are pulled the other way, the resistance will increase. In principle this is a device that can be switched by voltages in a way that gives a pinched hysteresis loop. 3 Journal Ludmil Petkov et al Figure 2-4 Shows the Hewlett Packard’s ion model of memristor, where w is the doped region’s length and D is the length of the device’s channel (Strukov et al., 2008). Figure 2-7 Shows the equivalent circuit diagram with two resistances Ron and Roff (Amdapurkar & V, 2016). Equations 2-1 and 2-2 can be written as: v(t) = (𝑅𝑅𝑜𝑜𝑜𝑜 𝑤𝑤(𝑡𝑡) 𝑤𝑤(𝑡𝑡) + 𝑅𝑅𝑜𝑜𝑜𝑜𝑜𝑜 − ))𝑖𝑖(𝑡𝑡) 𝐷𝐷 𝐷𝐷 (2-3) 𝑑𝑑𝑑𝑑 𝑅𝑅𝑜𝑜𝑜𝑜 = 𝜇𝜇𝑣𝑣 𝑖𝑖(𝑡𝑡) 𝐷𝐷 𝑑𝑑𝑑𝑑 (2-4) 𝑅𝑅𝑜𝑜𝑜𝑜 𝑞𝑞(𝑡𝑡) 𝐷𝐷 (2-5) A linear ion drift model is used. It is assumed that the ions’ average mobility is the same equal to 𝜇𝜇𝑣𝑣 . The voltage/current relation is defined. The voltage v(t) is dependent on the current and resistance. The variable w(t) can take values between zero and D. Figure 2-5 Idealized representation of the switching behaviour in the TiO2 layer. After integrating 2-4 the state variable is: 𝑤𝑤(𝑡𝑡) = 𝜇𝜇𝑣𝑣 Figure 2-6 Crossbar array with TiO2 switch in the crossing point. This formula can be used to get the device’s steering property. A linear dependency is shown of w(t) from q(t). This results in simple linear drift of dopants model of first order (Batas & Fiedler, 2011). Equivalent circuit diagram can be created with two variable resistors in series with each other. One represents the TiO2 when is stoichiometric (undoped) and the other one when it has oxygen vacancies (doped) in it. The idea is that a dividing line can be pushed or pulled of the end state between the oxygen vacancies and the stoichiometric part so that the resistance of the total device can be varied fig.2-7. One equation can be written that shows that the voltage is a function of the current and resistance which depends on the state variable. The state variable is the position of the dividing line between the doped and undoped material of the system. The other equation is the dynamical state equation of the device. It shows that the velocity of the dividing line (drift) is equal to the electric field multiplied by the current through the device. An equation can be derived for memristance. In this simple model of linear conduction, the drift is inversely proportional to the width of the device. It 4 Journal Ludmil Petkov et al Response is the output of the XOR which is dependent on the Challenge and the random output of the memory cell. The chance of guessing the result is 50%, when logic “1” is the output of the memory cell (Rose, McDonald, Yan, Wysocki, et al., 2013). shows that the memristance is more important at the nano scale than the micron scale and at the millimetre scale is completely unobservable. This explains that the hysteresis is typical for nano circuits and this is memristance. Very high fields cause atoms to move. Memristance is the coupled motion of atoms and electrons in a device. 3.Memeristor Architecture Based PUF Hardware Security is an important area of research. It helps to resolve issues related to side channel attacks, counterfeiting and piracy. Due to the scaling of the technology to a nanometre regime the memristor became a feasible choice to protect integrated circuits. Memristors are interesting components to be used in the design of PUFs because they are compatible to the CMOS manufacturing standards and their sensitivity to process variations can be controlled. The variation of the memristor’s thickness D creates different write times. Figure 3-2 A one bit PUF based on filament growth (Rose, McDonald, Yan, Wysocki, et al., 2013). From fig.3-2 can be noticed that the Challenge is externally supplied and through it one of the outputs of the memristors can be selected. The output or the Response bit will be the hardware explicit part of the security key. The memristive device keys and values will not be able to be read because of the requirement of a forming step without alerting the mechanism for tamper detection. There is probability an attacker in theory to influence the unpredictability of the suggested circuits. For example, if a voltage potential is applied to a specific device the time for writing can be successfully reduced. The protections against such an attack are the required formation step and multiple reset conditions return the memristor to a normal state and attempts to overhaul the memristor are annulled. (Gao, Ranasinghe, Al-Sarawi, Kavehei, & Abbott, 2015) are investigating highly secure physical unclonable functions (PUFs). They are using a nanocrossbar exploiting the existing high density of information. The novel design benefits from reliability, uniqueness, great number of challenge-response pairs (CRPs) and further desirable characteristics typical for strong PUFs. Further differently to the existing PUFs it can be reconfigured (rPUF). Figure 3-1 Variations in the memristor’s write times are used in a 1-bit PUF (Rose, McDonald, Yan, Wysocki, & Xu, 2013). Fig.3-1 shows implemented a single bit memristive memory-based PUF cell. Writing or reading of the � /W). For the circuit is determined by 2 control signals (𝑹𝑹 polarity of the writing (𝑵𝑵𝑵𝑵𝑵𝑵) is used. To work as a PUF the circuit first carries out RESET of the memristor � /W=1 and 𝑹𝑹 NEG=1 for a long enough period to guarantee that the memristor is in the high resistance state (HRS). After that NEXT is pulsed out for the write � /W=1). nominal time which is 𝒕𝒕𝒘𝒘𝒘𝒘,𝒎𝒎𝒎𝒎𝒎𝒎 (NEG=0 and 𝑹𝑹 Following the SET operation, the memristor can be read � /W=0. at the output by applying 𝑹𝑹 The input of an XOR function is used for the Challenge and the other input is the output of the memristor. The 5 Journal Ludmil Petkov et al reprogramming to revive CRPs of mrSPUF to convert it into a new PUF instance. In distinction to the programming control circuit, left analogue multiplexers block and the top decoder block, counters and CM-ROs enable the stimulation by a challenge and the extraction of a corresponding response. A challenge set as a vector of binary values (bits) provides the address bits for both the analogue multiplexers block and the decoder block. (d) CM-RO. Each current mirror serves only an inverter in the RO structure, where the bias memristor for each current mirror, Mi, is carefully chosen from the nanocrossbar array. Though difference in the oscillation frequency of each RO is insignificantly inclined by the threshold voltage difference in the CMOS transistor combining the starved inverter and current mirror structures, the complete difference in the oscillation frequency is mainly determined by the differences in the memresistance of 𝑴𝑴𝒊𝒊 if the supply voltage,𝑽𝑽𝑫𝑫𝑫𝑫 , is kept constant (Gao et al., 2015). Figure 3-3 (a) Memristive devices in a nanocrossbar. (b) Bottom and top electrodes. (c) Principle of operation of memristive devices. (d) Model of interconnection of one memristive device , 𝒓𝒓𝒘𝒘 is the nanowire segment resistance 𝑹𝑹𝒊𝒊𝒊𝒊 is the memristive device resistance at j-th top and i-th bottom conductor. (e) Reading scheme. To the designated word line, a reading voltage is applied and the current passing through it is sensed to determine the state of the memristive device. Throughout the reading there are some not obvious path currents (purple dashed line) besides the desired read current (green dashed line) (Gao et al., 2015). For the mrSPUF two Current Mirrors – Ring Oscillators (CM-RO) were used. The nanocrossbar complements them which helps with reducing the area. The reading is faster, and the reduced output frequency eases the precision of the counting. Different to the memristorbased PUF in (Koeberl, Kocabaş, & Sadeghi, 2013) where the goal was the value of the resistance to be sensed. This determined the binary value (in ROFF or RON state) of the targeted memristor in nanocrossbar array. The memristance analogue value was decoded (here only RON state was used) into a frequency over CM-RO. The advantages of this design include: 1) Significantly smaller number of Ros were used and only i inverter stages to build each RO. 2) Much improved number of CRPs were created. 3) The Response bit was generated using different structure. This mitigated some of the undesirable Response variations triggered by power supply and temperature fluctuations 4) Compared to the design in (Koeberl et al., 2013) complex circuitry wasn’t needed a memory cell to be readout. A full physical information (memory’s binary value) of the all nanocrossbar’s array junctions was not directly unprotected. These observations are shown in table 3-1. The memristors are randomly programmed in 𝑅𝑅𝑜𝑜𝑜𝑜 and 𝑅𝑅𝑜𝑜𝑜𝑜𝑜𝑜 state. Figure 3-4 Memristive device based strong Physical Unclonable Function (mrSPUF) architecture. (a) Basic mrSPUF construction. Very memristor is in the ON state. The shaded programming control circuit includes the row programming control circuitry in (b) and column programming control circuitry in (c) which is working to program memristors in nanocrossbar arrangement before it performs as a PUF and enables reconfigurability of mrSPUF by successive 6 Journal Ludmil Petkov et al Table 3-1Shows how other memristor PUFs compare with mrSPUF (Gao et al., 2015). (Koebe rl et al., 2013) Uniqueness ≈ 50% ≈ 50% Uniformity Number CRPs (Rose, mrSPUF McDo Fig.2-12 nald, Yan, & Wysoc ki, 2013) N/A of Use of Nanocrossbar Security Analysis MxN ≈ 50% M 50.07% 50.76% 𝑁𝑁 × �𝑀𝑀 � × �𝑀𝑀−𝑖𝑖 � 1 𝑖𝑖 2 Figure 4-2 some traces of analysing the TEAM single memristor model. Kvatinsky introduced a simple and general model of a memristor, which corresponds to the Simmons model with an acceptable error. This simplified model is based on several assumptions. Provisions to simplify the analysis and facilitate the calculation process. He assumes the absence of changes in the model variable parameters in a certain threshold and uses the polynomial dependence of the current of the memristor and the thickness of the tunnel barrier instead of the exponential. The dependent of the derivative of the thickness of the tunnelling barrier on the current is divided by multiplying two functions, one of which is a function of the current, and the other depends on the variable x. Strong PUF Reconfigurabl e PUF Figure 4-1 The single TEAM model of a memristor used by the researchers at Oxford Brookes University. 4. Simulation Using LTSpice Memristors have great potential for use in various areas of electronics and hardware cryptography. Therefore, there is a need to create their qualitative models for the analysis, design and creation of schematics based on their newly found properties. Except the model, provided by the HP lab other mathematical models of memristors exist. A ThrEshold Adaptive Memristor model (TEAM) was used as it was already chosen by the University’s research group and they have created a working model. It is flexible and can be used for any practical memristive device and also was further improved using a new window function (Kvatinsky, Friedman, Kolodny, & Weiser, 2013),(Zayer, 2018). Figure 4-3 Shows Memristive Memory PUF circuit drawn on LTSpice. And gates were used instead of the original design multiplexers as they have similar function. 7 Journal Ludmil Petkov et al and a new approach for magnetic flux-controlled memristor modeling. IEEE Transactions on Nanotechnology, 10(2), 250–255. https://doi.org/10.1109/TNANO.2009.2038051 5. Discussion and Conclusion Chua, L. O. (1971). Memristor—The Missing Circuit Element. IEEE Transactions on Circuit Theory, 18(5), 507–519. https://doi.org/10.1109/TCT.1971.1083337 This research showed that the memristors and the memristive devices are sensible candidates for applied PUFs. Some circuits are analysed that use completely different characteristics of the device. One circuit exploits the set time of the memristor. It is good that the noise margin is low for an analogue device. A satisfactory separation is given between larger noise margins and memristance states. The second PUF throughout relies on the ability two devices to be scanned and written to crosswise. The mrSPUF compared very well with the other designs and had some unique features. For more thorough understanding of the theoretical explanations and the simulations of the small circuits, more real experimental work is needed. This is the only way the initial findings to be verified against protypes and manufactured chips, circuits and modules. Circuit designers can work closer with physicists, device engineers and cyber-security specialist for the creations of working and verified industrial designs. Reliability, repeatability, cost, ruggedness, device aging are factors that will need to be considered for the future projects. The availability of memristors is still inadequate and the memristor-based circuits for cyber-security remain mostly speculative. Chua, L. O., & Kang, S. M. (1976). Memristive Devices and Systems. Proceedings of the IEEE, 64(2), 209–223. https://doi.org/10.1109/PROC.1976.10092 Gao, Y., Ranasinghe, D. C., Al-Sarawi, S. F., Kavehei, O., & Abbott, D. (2015). Memristive crypto primitive for building highly secure physical unclonable functions. Scientific Reports, 5, 1– 14. https://doi.org/10.1038/srep12785 Joshi, S., Mohanty, S. P., & Kougianos, E. (2017). Everything You Wanted to Know about PUFs. IEEE Potentials, 36(6), 38–46. https://doi.org/10.1109/MPOT.2015.2490261 Kavehei, O., Iqbal, A., Kim, Y. S., Eshraghian, K., Al-Sarawi, S. F., & Abbott, D. (2010). The fourth element: Characteristics, modelling and electromagnetic Theory of the memristor. Proceedings of the Royal Society A: Mathematical, Physical and Engineering Sciences, 466(2120), 2175–2202. https://doi.org/10.1098/rspa.2009.0553 Koeberl, P., Kocabaş, Ü., & Sadeghi, A. R. (2013). Memristor PUFs: A new generation of memory-based physically unclonable functions. Proceedings -Design, Automation and Test in Europe, DATE, 428–431. Kvatinsky, S., Friedman, E. G., Kolodny, A., & Weiser, U. C. (2013). TEAM: Threshold adaptive memristor model. IEEE Transactions on Circuits and Systems I: Regular Papers, 60(1), 211–221. https://doi.org/10.1109/TCSI.2012.2215714 Rose, G. S., McDonald, N., Yan, L. K., & Wysocki, B. (2013). A write-time based memristive PUF for hardware security applications. IEEE/ACM International Conference on Computer-Aided Design, Digest of Technical Papers, ICCAD, 830–833. https://doi.org/10.1109/ICCAD.2013.6691209 Rose, G. S., McDonald, N., Yan, L. K., Wysocki, B., & Xu, K. (2013). Foundations of memristor based PUF architectures. Proceedings of the 2013 IEEE/ACM International Symposium on Nanoscale Architectures, NANOARCH 2013, 52–57. https://doi.org/10.1109/NanoArch.2013.6623044 Semiconductor Engineering .:. Physically Unclonable Functions Semiconductor Engineering. (2019). Retrieved September 26, 2019, from file:///G:/MSc Thesis Cyber Security/Semiconductor Engineering - Physically Unclonable Functions.html Acknowledgements I would like to thank Dr Abusaleh Jabir and Mr Saurabh Khandelwal for their help with the research. Strukov, D. B., Snider, G. S., Stewart, D. R., & Williams, R. S. (2008). The missing memristor found. Nature, 453(7191), 80– 83. https://doi.org/10.1038/nature06932 References Zayer, F. (2018). Improved TiCh TEAM Model Using a New Window Function. (Icm), 236–239. Amdapurkar, A., & V, P. R. (2016). Design and Development of Memristor Based Combinational Circuits . (March), 554–557. Batas, D., & Fiedler, H. (2011). A memristor SPICE implementation 8