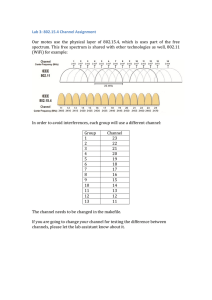
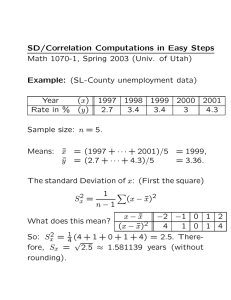
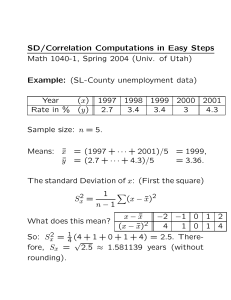
A New Relay-Assisted Spectrum Sharing - LabUnix
advertisement

The Tenth International Symposium on Wireless Communication Systems 2013
A New Relay-Assisted Spectrum Sharing Scheme
for Bidirectional Communication
Hela Hakim1,2 , Wessam Ajib1 and Hatem Boujemaa2
of Computer Sciences, Université de Québec à Montréal, Canada
2 Carthage University, Higher School of Communication of Tunis, Tunisia
Emails: ajib.wessam@uqam.ca and {hakim.hela,boujemaa.hatem}@supcom.rnu.tn
1 Department
Abstract—In this paper, we propose a new relay-assisted
spectrum sharing protocol where a pair of secondary users
and a pair of primary users bidirectionally communicate. A
secondary relay is deployed to assist the secondary transmissions
and improve the secondary access to the spectrum. We employ
a time division access technique to make primary and secondary
users communicate with no interference. The proposed scheme
is then compared to the axiomatic and simple scheme where
the secondary users communicate in an underlay mode with the
assistance of the relay . We study and compare the performances
of the two schemes in terms of outage probability. Our simulation
results show that the proposed scheme significantly outperforms
the underlay spectrum sharing scheme while in both schemes,
the primary outage probability is kept identical to the case where
secondary users are absent.
I. I NTRODUCTION
Cognitive radio has emerged as an efficient way to improve
the spectrum exploitation [1]-[2]. It consists in allowing secondary users access the spectrum licensed to primary users
under the constraint that secondary transmissions result in
limited interference to primary users [3].
Three main forms of spectrum sharing have been proposed
in literature [1]: (i) interweave paradigm employs efficient
spectrum sensing algorithms to detect the holes in the spectrum
licensed to primary users and exploits it for its own transmissions when primary user is silent; (ii) underlay paradigm
allows secondary users to transmit concurrently with primary
users, under the constraint that the induced interference power
at primary receiver is kept below a certain threshold, known as
interference temperature and (iii) an overlay paradigm where
the primary users cede the spectrum for the secondary users
during a fraction of time. The secondary users access the
ceded spectrum and devote a fraction of its transmit power
to cooperates with the primary users and the rest of transmit
power is used for secondary transmissions.
Recently, a great interest on designing and investigating new
spectrum sharing schemes has been raised. Several works in
literature have proposed various schemes to allow secondary
users access the primary spectrum [4]-[12]. Exploiting multiple antennas has been proposed in [4] to allow secondary
transmissions in the presence of multiple primary receivers.
In [5], an opportunistic spectrum sharing approach is proposed to maximize the downlink throughput of the cognitive
radio system and limit the interference perceived by the PU
where communications exist between a cognitive base station
and multiple SUs. In [6], authors have exploited cooperative
Orthogonal Frequency Division Multiplexing (OFDM) relays
to relay the primary signal on a fraction of the subcarriers
and use the rest of subcarriers to transmit secondary data.
In [7], the SUs gain spectrum access by overhearing and
exploiting limited channel state information (CSI) from PUs.
In [8], authors propose to devote a fraction of the transmit
power of an SU to relay the primary signal and transmit the
secondary signal using the rest of the transmit power. Spectrum
sharing with two way relaying have attracted a considerable
attention [9]-[11]. In [9], the authors considered a cognitive
radio network where two secondary users can communicate
with each other via the help of a PU. In addition, applying
network coding to a spectrum sharing system with two-way
relaying by using a decode-and-forward (DF) protocol was
considered in [10]. In [11], a pair of PUs bidirectionally
communicate and the SU gains spectrum access by devoting
a part of its power to perform two way relaying for PUs
and use the rest of its power to transmit secondary data.
In [12], primary and secondary bidirectional communications
between a pair of secondary users and a pair of primary
users is conducted with the help of a single-antenna relay.
The transmissions are done in two phases: a relay receiving
phase and a relay transmitting phase. The communications are
always performed only via the relay.
In this paper, we propose an efficient and simple spectrum
sharing technique to conduct one secondary and one primary
bidirectional communications with the assistance of a relay. In
[12], in a first phase, the primary and secondary transmitters
send their data to the relay. Then, in the second phase, the
relay forwards the data to the primary and secondary receivers.
Unlike [12], in this paper each transmitter communicates with
its correspondent receiver while the relay overhears. If the
data rate of the primary and/or secondary users are below
the required values, the relay intervenes to help the user(s)
in outage reach the required data rate values. Moreover,
we propose a time division access technique so that each
user transmits in a fraction of time without getting disturbed
by interference from other users. We compare the proposed
scheme with the axiomatic scheme where secondary users
transmit and the relay cooperates with them in an underlay
mode. Our Simulation results prove that our proposed scheme
outperforms the simple underlay spectrum sharing without
affecting the primary outage probability.
The rest of this paper is organized as follows. In section
,6%1
9'(9(5/$**0%+ā%HUOLQā2IIHQEDFK*HUPDQ\
239
The Tenth International Symposium on Wireless Communication Systems 2013
II, we present our system model while in section III we
describe the proposed spectrum sharing scheme. For comparison purposes, we present the underlay scheme in section
IV. Simulation results are presented in section V. Finally,
concluding remarks and a summary of our findings are given
in section VI.
Notations:
Let y ∈ {1, 2}, y = {1, 2} \ {y}, x ∈ {1, 2} and
x = {1, 2} \ {x}. The channel gain between PUy and PUy ,
SUx and SUx , SR and SUx , PUy and SUx are denoted by
hyy , gxx , frx and hps
yx , respectively; . denotes the 2-norm;
[.]H denotes the transpose conjugate operator; [.]t denotes the
transpose operator; [.]−1 denotes the inverse of the matrix;
CN ×M denotes all the N ×M matrices; |.| denotes the modulo
operator; E(.) is the expectation operator;, IM denotes the
identity matrix of size M .
II. S YSTEM M ODEL
We consider a cognitive radio network composed of two
SUs (SU1 and SU2 ), two PUs (PU1 and PU2 ) and a secondary
relay denoted by SR as depicted in Fig.1. All nodes are
assumed to be half duplex.
PU1
Rp and Rs , denotes the primary and secondary required data
rate, respectively.
At the beginning of each time slot, the data rate of PUs as
if SUs are absent, denoted by Rabs is computed as follows
P |h |2
Rabs = 12 log2 (1 + p Nyy
), where PP denotes the transmit
0
power of PUs. We suppose that PUs transmit only if Rabs is
below Rp . This helps PUs save energy since their transmissions are in outage even if SUs are silent. If Rabs is higher
than Rp , then to allow SUs access the spectrum and perform
their transmissions, we propose the following time division
access. In the first eighth of time slot, PUy transmits data to
PUy . If the data rate at PUy is below Rp , then during the
second eighth of time slot, SR forwards the received signal to
PUy to reach out the required value Rp . In the third eighth
of time slot, SUx transmits data to SUx with a power Psx , so
that the data rate at SUx be equal to the required value Rs .
As SUx has a maximum available power Psmax , the transmit
power Psx can be given by
x
Psx = min(Psmax , Preq
),
(1)
x
is the power required to have Rs at SUx , given
where Preq
8Rs
−1)N 0
x
x
= (2 |gx,x
> Psmax , then the data rate
. If Preq
by Preq
|2
at SUx is below Rs and hence SR will forward the received
signal from SUx to help SUx reach the required data rate Rs .
The proposed time division access is depicted in Fig. 2 below.
SR
SU1
SU2
PUy →PUy
PUy →PUy
TS
(a)
1/2 TS
PUy →PUy
SR→PUy
SUx →SUx
SR→SUx
1/8 TS
PU2
Fig. 1.
PUy →PUy
SR→PUy
SUx →SUx
SR→SUx
(b)
Fig. 2. (a) Time division access in the absence of SUs. (b) Time division
access in the presence of SUs.
System Model.
The channel between two nodes k and
l is assumed to
−α
have (i) a pathloss component (a = dkl 2 ), where dkl is the
distance between k and l and α is the path loss exponent
and (ii) an independent fading effect component modeled as
a circular symmetric complex Gaussian random variable with
variance 1. The noise is modeled as additive white gaussian
noise (AWGN) with zero mean and N0 variance. We assume
that the state of the channels are invariant during one time
slot and may change independently each time slot. We assume
a bidirectional communication between SUs. Also, a bidirectional communication between PUs exists where PUy starts the
transmission with a probability 12 . The entire communication
time is one time slot (TSl).
In this case, the data rate at SUx can be written as
1
P x |gxx |2
Pr |frx |2
prop
Rsec,x
= log2 (1 + s
+
),
8
N0
N0
P x |g
|2
8Rs
0
− 1 − s Nxx
)) and
where Pr = min(Prmax , |fN
2 (2
rx |
0
Prmax is the maximum available power for SR.
If the data rate at PUy is higher than Rp , then SUx transmits
7
of time slot. If the data rate at SUx is
data to SUx during 16
7
below Rs , then during the next 16
of time slot, SR forwards
the received signal from SUx to help SUx reach the required
data rate Rs . Otherwise, if the data rate at SUx is higher than
7
of time
Rs , SUx continues to transmit data during the next 16
slot. Fig. 3 illustrates the described time division access.
PUy →PUy
III. T HE PROPOSED S PECTRUM S HARING S CHEME
Without loss of generality, we suppose that PUy starts to
transmit. In the absence of secondary network, the time slot is
divided into two sub-slots ( 12 time slot). During the first subslot, PUy transmits data to PUy . Then, in the second sub-slot,
PUy transmits data to PUy . This is depicted in Fig.2 (a). Let
(2)
1/8 TS
Fig. 3.
SUx →SUx
SR→SUx
PUy →PUy
SUx →SUx
SR→SUx
7/16 TS
Time division access if PUs are not in outage.
If Rabs is below Rp , as mentioned earlier PUs remain silent.
Hence SUs are free to use the spectrum. The proposed time
,6%1
9'(9(5/$**0%+ā%HUOLQā2IIHQEDFK*HUPDQ\
240
The Tenth International Symposium on Wireless Communication Systems 2013
division access in this case is as follows. SUx transmits data
to SUx during the first quarter of time slot. If the data rate
at SUx is below Rs , then during the second quarter of time
slot, SR forwards the received signal to SUx in order to help
it reach the required data rate Rs . If the data rate at SUx is
higher than Rs , then SUx continues to transmit data to SUx
during the second quarter of time slot. In the second half of
time slot, SUx and SUx substitutes rules and SR helps SUx
only if it is needed. This is also depicted in Fig. 4.
SUx →SUx
SUx →SUx
SR→SUx
PUy →PUy
PUy →PUy
TS
1/2 TS
SUx →SUx
SUx →SUx
SR→SUx
SR→SUx
1/4 TS
SR→SUx
Fig. 5.
(a)
1/4 TS
4Rs
−1)N0
x
where Preq
= (2 |gxx
, is the required power to have a
|2
data rate equal to Rs at SUx . If Rabs < Rp , PUs will not
transmit and SUs use the power as in (1).
Underlay spectrum sharing scheme time division access.
SUx →SUx
SUx →SUx
PUy →PUy
1/2 TS
PUy →PUy
(b)
TS
Fig. 4. Time division access for SUs when Rabs < Rp . (a) Cooperation is
needed (b) Cooperation is not needed.
Note that when the data rate at PUy is below Rp , SR
must forward the signal received from PUy with the following
transmit power
Prprim =
N0
Pp |hyy |2
(28Rp − 1 −
).
2
|fry |
N0
Prprim
Prmax ,
(3)
If
is higher than
SR can not help PUy and the
spectrum sharing becomes impossible. Hence, at the beginning
of each time slot, the SR verifies if Prprim is within its power
budget and informs PUs and SUs that spectrum sharing is
possible. Otherwise, SUs remain silent.
1/2 TS
(a)
SUx →SUx
1/2 TS
SUx →SUx
(b)
Fig. 6. Underlay spectrum sharing scheme time division access when PUs
are silent.
The data rate at SUx using the underlay spectrum sharing
scheme is as follows
Ps x |gxx |2
1
Pr |frx |2
= log2 (1 +
),
ps 2 +
2
4
N0 + Pp |hyx |
N0 + Pp |hps
yx |
(6)
where Pr is given by
underlay
Rsec,x
Pr =
IV. U NDERLAY SPECTRUM SHARING SCHEME
2
2
In this scheme, each time slot is divided into two half time min(P max , N0 (24Rs − 1 − |gxx | ), 1 ( Pp |hyy | − N )).
0
r
|frx |2
N0
|fry |2 22Rp − 1
slots. Each half time slot is further divided into four sub(7)
slots. In the first sub-slot, SUx transmits data to SUx and
PUy transmits data to PUy , simultaneously. In the second subslot, if the data rate at SUx is below Rs , then SR forwards
V. S IMULATION R ESULTS
the signal received during the first sub-slot to SUx in order
In this section, some simulation results are presented to
to reach out the data rate to Rs . Otherwise, if the data rate
study the performance of our proposed spectrum sharing
at SUx is higher than Rs , SUx continues to transmit data to
scheme. We assume BPSK modulation. We consider a system
SUx during the second sub-slot. In the third sub-slot, SUx and
topology in a 2-D X-Y plane, where SU1 , SU2 , PU1 and
SUx substitutes roles and the same process described above
PU2 are located at points (0, 0) and (1, 0), (0, 3) and (1, 3),
is executed in the fourth sub-slot. The same transmissions are
respectively. Relay position is randomly distributed in a square
repeated in the second half of time slot. The proposed time
1 × 1. Numerical results are averaged over many random relay
division access for the underlay spectrum sharing scheme is
positions and path loss exponent is set to 3.5.
depicted in Fig. 5. As explained earlier, PUs transmit only if
In Fig. 7, we present the secondary and primary average
they estimate that Rabs is higher than Rp . If Rabs ≥ Rp , SUs
outage probabilities versus primary transmit SNR for Rp = 1
may access the spectrum simultaneously with PUs by adapting
and Rs = 0.5 bits/s/Hz. The secondary transmit SNR is fixed
their power so that the data rate at the primary receiver be Rp .
to 20 dB. The maximum available power for SR, Prmax is
For example, if SUx wants to transmit, it is authorized to use
fixed to 30 dB. We observe that the proposed spectrum sharthe following power to not cause a harmful interference to
ing scheme outperforms significantly the underlay spectrum
PUs
2
sharing scheme. This proves the robustness of our proposed
1
Pp |hyy |
Pauth =
.
(4)
−
N
0
spectrum sharing scheme. Moreover, we observe that the
2R
2
|gxx |
2 p −1
outage probability performance of the proposed scheme is
Given that SUx has a maximum available power Psmax and
almost constant versus the primary transmit SNR. This is
the data rate at SUx must be equal to Rs , then the used power
because our proposed spectrum sharing scheme is designed so
by SUx can be written as
that the interference from the PUs is avoided. So whatever is
x
Ps x = min(Psmax , Pauth , Preq
),
(5) the power used by the PUs, the performance of our secondary
,6%1
9'(9(5/$**0%+ā%HUOLQā2IIHQEDFK*HUPDQ\
241
The Tenth International Symposium on Wireless Communication Systems 2013
í
3ULPDU\XVHUV
3ULPDU\XVHUVLQDEVHQFHRIVHFRQGDU\XVHUV
8QGHUOD\VSHFWUXPVKDULQJVFKHPH
3URSRVHGVSHFWUXPVKDULQJVFKHPH
8QGHUOD\VSHFWUXPVKDULQJVFKHPH
3URSRVHGVSHFWUXPVKDULQJVFKHPH
2XWDJHSUREDELOLW\
2XWDJHSUREDELOLW\
í
í
í
í
3ULPDU\7UDQVPLW615G%
3ULPDU\XVHUV
3ULPDU\XVHUVLQDEVHQFHRIVHFRQGDU\XVHUV
8QGHUOD\VSHFWUXPVKDULQJVFKHPH
3URSRVHGVSHFWUXPVKDULQJVFKHPH
2XWDJHSUREDELOLW\
í
í
í
6HFRQGDU\7UDQVPLW615G%
U
0D[LPXPSRZHURI653PD[G%
Fig. 7. Average outage probability versus primary transmit SNR, Rp = 1
and Rs = 0.5 bits/s/Hz.
í
Fig. 8. Average outage probability versus secondary maximum SNR, Rp = 1
and Rs = 0.5 bits/s/Hz.
network will not be affected. We observe that for low primary
transmit SNR, the outage probability of the secondary network
is slightly better than the medium range of the primary transmit
SNR. This is because when the primary transmit SNR is low,
Rabs is often lower than Rp . Hence, PUs will not transmit
and will leave the spectrum for the SUs. This ameliorates the
performance of the secondary network. As far as for the high
transmit primary SNR, the PUs will not need the help of SR
and hence SUs find larger time to transmit. Observe that the
primary outage probability in the absence of SUs and when
our proposed spectrum sharing scheme is applied are identical.
This proves that our proposed spectrum sharing scheme allows
SUs to access spectrum and perform their transmission without
affecting the performance of the primary network and offers
a secondary outage probability performance much better than
that of the underlay spectrum sharing scheme.
In Fig. 8, we present the outage probability of the proposed
scheme and the underlay spectrum sharing scheme versus the
secondary transmit SNR. The primary transmit SNR and Prmax
are fixed to 20 and 30 dB, respectively. We observe that
the outage probability performance of the underlay spectrum
sharing scheme decreases as the secondary transmit SNR
increases. This is because when the secondary transmit SNR
Fig. 9. Average outage probability versus secondary maximum SNR, Rp = 1
and Rs = 0.5 bits/s/Hz.
increases, the maximum power available for SUs increases and
hence SUs can use higher power to satisfy their required data
rate as long as this do not harm the PUs. We observe that the
performance of the outage probability of the proposed spectrum sharing scheme is almost invariant versus the secondary
transmit SNR. This is because the relay SR is designed to
hide the power insufficiency of SUs. In other words, if the
available power of SUs is insufficient to reach the required
value Rs , then SR will dispense its power to cooperate with
the transmitting SU to make the data rate at the receiving
SU be equal to the required value. Moreover SR is free to
use the sufficient power as long as this is within its power
budget because SR do not have any interference constraint
toward PUs. In Fig. 9, we present the outage probability
performances of the underlay and the proposed spectrum
sharing scheme versus the maximum available power of SR,
Prmax . We set the primary and secondary transmit SNR to 20
dB. We observe that the outage probability performance of the
underlay spectrum sharing scheme is invariant versus Prmax .
This is because the SR has an interference constraint toward
the PUs and even if it has an extra power range, it can not
use it since its transmit power is controlled by the interference
constraint imposed by PUs. For the proposed spectrum sharing
scheme, as we have designed a time division access so that
SUs and SR transmit with no interference constraints, we
observe that when Prmax increases, the outage probability
decreases. This is because, in the proposed scheme, SR is free
to use the power sufficient to satisfy the data rate constraint
of SUs as long as this power is within its power budget. To
conclude, the available power of the SR is a key parameter that
influences the outage probability performance of the secondary
network.
VI. C ONCLUSION
In this paper, we have considered a bidirectional communications between a pair of secondary users and a pair of
primary users. We have investigated a new spectrum sharing
scheme that provides the secondary users with a better access
to the spectrum with the help of a secondary relay. We have
compared the outage probability performance of our proposed
,6%1
9'(9(5/$**0%+ā%HUOLQā2IIHQEDFK*HUPDQ\
242
The Tenth International Symposium on Wireless Communication Systems 2013
scheme to that of the axiomatic scheme where secondary users
communicate with each other in an underlay mode with the
assistance of the relay. Our results showed that the proposed
scheme significantly outperforms the underlay scheme while
the primary outage probability is kept the same as if secondary
users were absent.
R EFERENCES
[1] A. Goldsmith, S. Jafar, I. Maric, and S. Srinivasa, “Breaking spectrum
gridlock with cognitive radios: An information theoretic perspective,”
Proceedings of the IEEE, vol. 97, no. 5, pp. 894–914, May 2009.
[2] S. Haykin, “Cognitive radio: brain-empowered wireless communications,” IEEE J. Select. Areas Commun., vol. 23, no. 2, pp. 201–220,
Feb. 2005.
[3] Y. Xing, C. Mathur, M. Haleem, R. Chandramouli, and K. Subbalakshmi, “Dynamic spectrum access with qos and interference temperature
constraints,” IEEE Trans. Mobile Comput., vol. 6, no. 4, pp. 423–433,
Apr. 2007.
[4] R. Zhang and Y. Liang, “Exploiting multi-antennas for opportunistic
spectrum sharing in cognitive radio networks,” IEEE J. Select. Areas
Signal Processing., vol. 2, no. 1, pp. 88–102, Feb. 2008.
[5] K. Hamdi, W. Zhang, and K. Letaief, “Opportunistic spectrum sharing
in cognitive mimo wireless networks,” IEEE Trans. Wireless Commun.,
vol. 8, no. 8, pp. 4098–4109, Aug. 2009.
[6] W. Lu, Y. Gong, S. Ting, X. Wu, and N. Zhang, “Cooperative ofdm relaying for opportunistic spectrum sharing: Protocol design and resource
allocation,” IEEE Trans. Wireless Commun., vol. 11, no. 6, pp. 2126–
2135, Jun. 2012.
[7] J. Li, W. Zhang, and J. Yuan, “Opportunistic spectrum sharing in
cognitive radio networks based on primary limited feedback,” IEEE
Trans. Commun., no. 99, pp. 1–6, Dec. 2011.
[8] Y. Han, A. Pandharipande, and S. Ting, “Cooperative decode-andforward relaying for secondary spectrum access,” IEEE Trans. Wireless
Commun., vol. 8, no. 10, pp. 4945–4950, 2009.
[9] W. Zhong, M. Tao, and Y. Xu, “A spectrum access game in bidirectional
cognitive relay networks,” in Proc. International Conference on Wireless
Communications and Signal Processing (WCSP). IEEE, 2010, pp. 1–6.
[10] Q. Li, S. Ting, A. Pandharipande, and Y. Han, “Cognitive spectrum
sharing with two-way relaying systems,” IEEE Trans. Veh. Technol.,
vol. 60, no. 3, pp. 1233–1240, Mar. 2011.
[11] L. Yang, M.-S. Alouini, and K. Qaraqe, “On the performance of spectrum sharing systems with two-way relaying and multiuser diversity,”
IEEE Commun. Lett., vol. 16, no. 8, pp. 1240–1243, Aug. 2012.
[12] C. Gong, G. Yue, and X. Wang, “A transmission protocol for a
cognitive bidirectional shared relay system,” IEEE J. Select. Areas Signal
Processing, vol. 5, no. 1, pp. 160–170, Feb. 2011.
,6%1
9'(9(5/$**0%+ā%HUOLQā2IIHQEDFK*HUPDQ\
243