Cyber Security
As critical infrastructure networks become
smarter, automated and more connected,
they are also more susceptible than ever to
cyber threats. Communication networks of
power grids, water systems, public transportation,
and oil rigs are subjected to hundreds, sometimes
thousands of cyber attacks per day.
RAD’s secure-by-design Service Assured Networking
solutions ensure that your operational network
remains reliable and protected at all times.
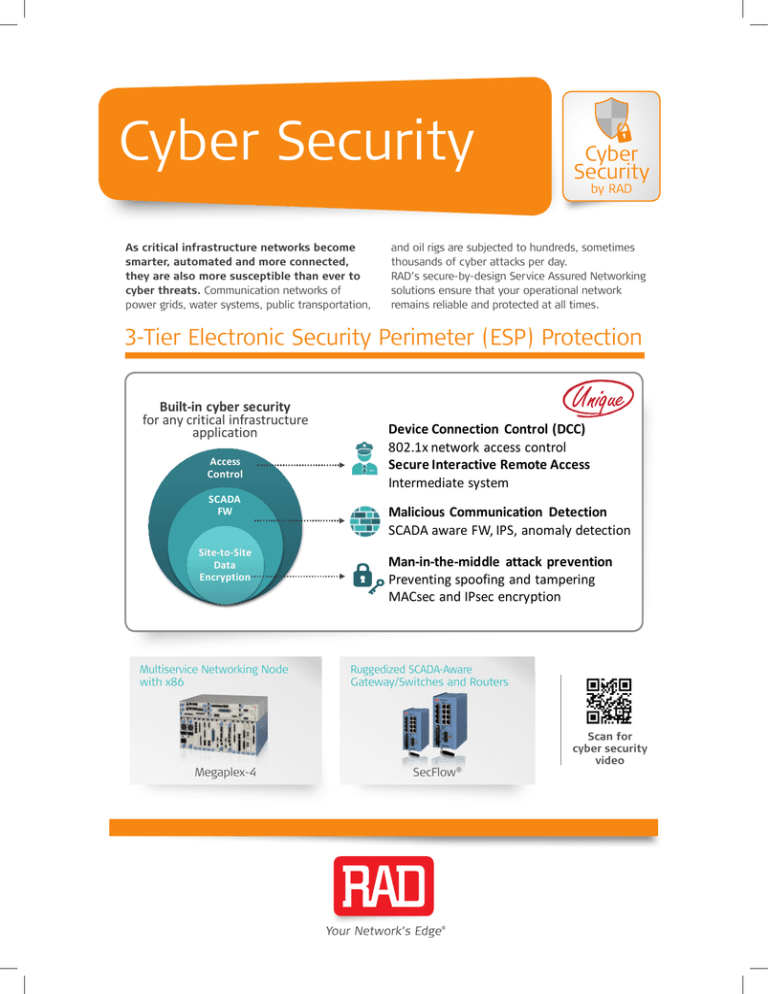
3-Tier Electronic Security Perimeter (ESP) Protection
Built-in cyber security
for any critical infrastructure
application
Access
Control
SCADA
FW
Site-to-Site
Data
Encryption
Multiservice Networking Node
with x86
Megaplex-4
Device Connection Control (DCC)
802.1x network access control
Secure Interactive Remote Access
Intermediate system
Malicious Communication Detection
SCADA aware FW, IPS, anomaly detection
Man-in-the-middle attack prevention
Preventing spoofing and tampering
Phase 2
MACsec and IPsec encryption
Ruggedized SCADA-Aware
Gateway/Switches and Routers
SecFlow®
Scan for
cyber security
video
>>> Boosting NERC-CIP Compliance
RAD’s SAN solutions are in line with recent North American Electric Reliability Corporation Critical
Infrastructure Protection (NERC-CIP) directives to boost your cyber security and compliance levels:
• Encryption and integrity for all communications outside ESP
• Application (SCADA) aware firewall
• Record/monitor all device connections in substations
High Voltage/Medium Voltage (HV/MV)
Substation Electronic Security Perimeter
Access
point
Operational
WAN
Phase 2
Megaplex/SecFlow
Multi-Layer
Security-by-Design
•• Strategically located to securely manage all
electronic access to the substation’s ESP, and to
protect the cyber assets within it from external and
internal attacks:
•• Device connection control (DCC) using IEEE 802.1x
Network Access Control to ensure authenticated
and authorized internal substation connections
•• SCADA-aware security layer, including firewall,
intrusion prevention, anomaly detection, and more
•• Boost compliance level with NERC-CIP requirements
for bulk electric systems (BES) protection
•• Layered security approach addresses all vulnerability
points including integrity, confidentiality
(encryption), authentication, authorization,
and auditing
•• Access control, user authentication and privilegelevel associations for local and remote access using
Secure Shell (SSH), TACACS or RADIUS
•• IEEE 802.1AE (MACsec) and IPsec encryption
and data integrity verification to prevent sourcespoofing, session hijacking, Man in the Middle and Distributed Denial of Service (DDoS) attacks
www.rad.com
Specifications are subject to change without prior notification. The RAD name, logo and logotype are registered trademarks of RAD Data Communications Ltd.
RAD product names are trademarks of RAD Data Communications Ltd. ©2016 RAD Data Communications. All rights reserved. Catalog number 802715, Version 4/16
Your Network’s Edge