Notes on Modulation techniques
advertisement

Notes on Modulation techniques
by
Davide Micheli
1
Table of Contents
NOTES ON MODULATION TECHNIQUES.......................................................................................................... 1
TABLE OF CONTENTS ................................................................................................................................................2
1
CANNEL CAPACITY AND IDEAL COMMUNICATION SYSTEMS ...................................................... 6
1.1
2
CODING ........................................................................................................................................................... 14
2.1
2.2
3
CODE PERFORMANCE ................................................................................................................................14
SPECTRAL EFFICIENCY ..............................................................................................................................12
INTERSYMBOL INTERFERENCE ............................................................................................................. 19
3.1
3.2
3.3
3.4
4
CHANNEL CAPACITY DEFINITION .................................................................................................................6
SPECTRAL PROPERTY REMINDER (SQUARE WAVE SPECTRUM) ...................................................................22
EQUALIZING FILTER ..................................................................................................................................23
NYQUIST’S FIRST METHOD (ZERO ISI) .....................................................................................................25
RAISED COSINE-ROLLOFF NYQUIST FILTERING ........................................................................................28
BANDPASS SIGNALING............................................................................................................................... 32
4.1
COMPLEX ENVELOPE RAPPRESTNATION OF BANDPASS WAVEFORMS ................................32
4.1.1
Definitions: Baseband, Bandpass, and modulation ............................................................................. 32
4.1.2
Complex Envelope Representation ...................................................................................................... 33
4.1.3
Theorem............................................................................................................................................... 33
4.2
REPRESENTATION OF MODULATED SIGNALS..............................................................................35
4.3
SPECTRUM OF BANDPASS SIGNALS................................................................................................36
Theorem ............................................................................................................................................................. 36
5
AM, FM, PM MODULATED SYSETMS.................................................................................................... 37
5.1
DEFINITIONS .............................................................................................................................................37
5.2
AMPLITUDE MODULATION ...............................................................................................................37
5.2.1
Normalized AM average power ........................................................................................................... 39
5.2.2
Definition: The modulation efficiency ................................................................................................. 40
6
PHASE MODULATION AND FREQUENCY MODULATION................................................................ 41
6.1
6.1.1
6.2
6.2.1
6.3
6.3.1
6.4
6.4.1
6.4.2
6.5
7
REPRESENTATION OF PM AND FM SIGNALS .............................................................................................41
Definition for peak phase deviation and peak frequency deviaton. ..................................................... 45
SPECTRA OF ANGLE-MODULATED SIGNALS ..............................................................................................46
Spectrum of a PM or FM signal with Sinusoidal Modulation ............................................................. 47
NOISE AND FREQUENCY MODULATION ......................................................................................................51
Noise triangle ...................................................................................................................................... 51
PREEMPHASIS AND DEEMPHASIS IN ANGLE MODULATED SYSTEMS ...........................................................52
De-Emphasis response table................................................................................................................ 54
Why use “Roofed” Pre-Enhasis .......................................................................................................... 55
FREQUENCY DIVISION MULTIPLEXING .......................................................................................................55
OUTPUT SIGNAL-TO NOISE RATIOS FOR ANALOG SYSTEMS....................................................... 57
7.1
7.2
7.3
7.4
7.5
COMPARISON WITH BASEBAND SYSTEMS .................................................................................................58
AM SYSTEMS WITH PRODUCT DETECTION................................................................................................59
SSB SYSTEMS ............................................................................................................................................60
PM SYSTEMS .............................................................................................................................................60
FM SYSTEMS ............................................................................................................................................62
2
7.6
7.7
8
COMPARISON OF ANALOG SIGNALING SYSTEMS............................................................................ 67
8.1
9
FM SYSTEMS WITH THRESHOLD EXTENSION ............................................................................................63
FM SYSTEM WITH DE-EMPHASIS...............................................................................................................66
IDEAL SYSTEMS PERFORMANCE .................................................................................................................68
BINARY MODULATED BANDPASS SIGNALING................................................................................... 70
9.1
BINARY PHASE-SHIFT KEYING (BPSK) ....................................................................................................71
9.1.1
BPSK Generation ................................................................................................................................ 71
9.1.2
BPSK Detection by a Correlation Receiver......................................................................................... 78
9.1.3
With Noise ........................................................................................................................................... 80
9.2
MAXIMUM LIKELIHOOD DETECTION .........................................................................................................83
9.3
BIT ERRORS ..............................................................................................................................................83
9.3.1
Q-Function reminder ........................................................................................................................... 85
9.3.2
Bit Error Probability in terms of Eb and N0 ......................................................................................... 87
10
DIFFERENTIAL PHASE-SHIFT KEYING (DPSK)................................................................................... 89
10.1
11
FREQUENCY SHIFT KEYING (FSK)......................................................................................................... 91
11.1
11.2
11.3
12
QUADRATURE PHASE-SHIFT KEYNG (QPSK) AND M-ARY PHASE-SHIFT KEYNG (MPSK) .......................95
OQPSK AND π/4 QPSK ..........................................................................................................................102
QUADRATURE AMPLITUDE MODULATION (QAM)..................................................................................106
PSD FOR MPSK, QAM, OQPSK, AND π/4 QPSK WITHOUT PRE-MODULATION FILTERING ....................107
SPECTRAL EFFICIENCY FOR MPSK, QAM,OQPSK, AND π/4 QPSK WITH RAISED COSINE FILTERING ...109
RECEIVER QPSK, MSK AND PERFORMANCE ..........................................................................................117
FEHER-PATENTED QUADRATURE PHASE-SHIFT KEING.............................................................. 121
13.1
13.2
13.3
13.4
14
DISCONTINUOUS FSK ...............................................................................................................................91
CONTINUOUS FSK.....................................................................................................................................92
FSK DETECTION ........................................................................................................................................93
MULTILEVEL MODULATED BANDPASS SIGNALING ....................................................................... 95
12.1
12.2
12.3
12.4
12.5
12.6
13
DIFFERENTIAL CODING ..............................................................................................................................90
INTRODUCTION........................................................................................................................................121
SIGNAL MODEL FOR FQPSK ...................................................................................................................121
SIGNAL MODEL FOR FQPSK-B................................................................................................................131
SPECTRAL EFFICIENCY COMPARISON .......................................................................................................133
EFFICIENT MODULATION METHODS STUDY AT NASA/JPL ........................................................ 135
14.1
FQPSK-B MODULATION BIT-ERROR-RATE (BER) ................................................................................135
14.2
FQPSK-B MODULATION SPECTRA .........................................................................................................136
14.2.1
Hardware Spectrum Measurements.............................................................................................. 136
14.3
FQPSK-B MODULATION POWER CONTAINMENT ...................................................................................138
14.4
FQPSK-B MODULATION STUDY CONCLUSIONS .....................................................................................138
15
SUMMARY, CONCLUSIONS, AND RECOMMENDATIONS ............................................................... 140
15.1.1
SUMMARY.................................................................................................................................... 140
15.2
CONCLUSIONS ....................................................................................................................................144
15.2.1
Filtering Conclusions.................................................................................................................... 144
15.2.2
Loss Conclusions .......................................................................................................................... 145
15.2.3
Modulation Methods Conclusions ................................................................................................ 146
15.2.4
Spectrum Improvement Conclusions............................................................................................. 147
15.3
RECOMMENDATIONS .......................................................................................................................147
15.3.1
Mission Classification................................................................................................................... 147
16
8PSK MODULATION (EXAMPLE IMPLEMENTED IN MOBILE TELEPHONE NETWORK) ..... 151
16.1
16.2
INTRODUCTION........................................................................................................................................151
EDGE SIGNAL DESCRIPTION: MODULATING SYMBOL RATE AND SYMBOL MAPPING .............................153
3
16.3
SYMBOL ROTATION.................................................................................................................................158
16.4
(8PSK EDGE) MODULATION AM DISTORTION .......................................................................................165
16.4.1
First problem (ISI):....................................................................................................................... 165
16.4.2
Second problem (AM):.................................................................................................................. 166
16.5
USED GAUSSIAN EDGE FILTER ..............................................................................................................167
16.6
EFFECT DUE TO GAUSSIAN EDGE FILTERING IN 3Π/8 SHIFTED 8PSK .....................................................170
16.7
MODULATION..........................................................................................................................................173
16.8
CONCLUSION ...........................................................................................................................................173
17
EFFICIENT MODULATION METHODS STUDY AT NASA/JPL ........................................................ 174
17.1
17.2
17.3
17.4
17.5
18
PHASE SHIFT KEYED (8-PSK) MODULATION ...............................................................................174
PSK MODULATION BIT-ERROR-RATE (BER) .........................................................................................174
8-PSK MODULATION SPECTRA ...............................................................................................................175
PSK MODULATION POWER CONTAINMENT.............................................................................................177
PSK MODULATION STUDY CONCLUSIONS ..............................................................................................177
MINIMUM-SHIFT KEYNG (MSK) AND GMSK ..................................................................................... 178
18.1
GMSK ....................................................................................................................................................185
18.1.1
How to implement GMSK modulator............................................................................................ 190
18.1.2
How to implement GMSK demodulator ........................................................................................ 192
19
EFFICIENT MODULATION METHODS STUDY AT NASA/JPL ........................................................ 194
19.1
19.2
19.3
19.4
MSK AND GMSK MODULATION BIT-ERROR-RATE (BER) ....................................................................194
MSK AND GMSK MODULATION SPECTRA .............................................................................................194
MSK / GMSK MODULATION POWER CONTAINMENT .............................................................................196
MSK / GMSK MODULATION STUDY CONCLUSIONS ...............................................................................197
20
HISTORY OF SPECTRUM EFFICIENT MODULATION IN TELEMETRY APPLICATIONS....... 198
21
CORRELATED DETECTION .................................................................................................................... 201
22
INTRODUCTION TO CDMA ..................................................................................................................... 206
22.1
MULTIPLE ACCESS ..................................................................................................................................206
22.2
SPREAD SPECTRUM MODULATION ...........................................................................................................207
22.3
TOLERANCE TO NARROWBAND INTERFERENCE ......................................................................................210
22.4
DIRECT SEQUENCE SPREAD SPECTRUM SYSTEM .....................................................................................211
22.4.1
Channelization operation.............................................................................................................. 212
22.4.2
Scrambling operation.................................................................................................................... 214
22.5
ORTHOGONAL SEQUENCES REMINDER.....................................................................................................214
22.6
MODULATION AND TOLERANCE TO WIDEBAND INTERFERENCE .............................................................216
22.7
UPLINK MODULATION.............................................................................................................................219
22.7.1
One UL parallel channel .............................................................................................................. 223
22.7.2
Two UL parallel channel .............................................................................................................. 225
22.7.3
Three UL parallel channel............................................................................................................ 230
22.7.4
Filtering ........................................................................................................................................ 236
22.8
DOWNLINK SPREADING AND MODULATION ............................................................................................238
22.8.1
Downlink Spreading Codes........................................................................................................... 238
23
ORTHOGONAL FREQUENCY DIVISION MULTIPLEXING (OFDM) .............................................. 241
23.1
INTRODUCTION........................................................................................................................................241
23.2
DIGITAL AUDIO BROADCASTING.............................................................................................................242
23.3
DIGITAL VIDEO BROADCASTING .............................................................................................................243
23.4
BASIC PRINCIPLE OF OFDM ....................................................................................................................244
23.5
ORTHOGONALITY ....................................................................................................................................246
23.5.1
FREQUENCY DOMAIN ORTHOGONALITY.............................................................................. 249
23.6
OFDM GENERATION AND RECEPTION .....................................................................................................250
23.6.1
Serial To Parallel Conversion ...................................................................................................... 251
23.6.2
Subcarrier modulation and mapping ............................................................................................ 252
23.6.3
Frequency to time domain conversion .......................................................................................... 253
4
23.7
OFDM TRANSMITTER .............................................................................................................................254
23.8
FFT(LINE SPECRA FOR PERIODIC WAVEFORMS).....................................................................................256
23.8.1
Theorem ........................................................................................................................................ 256
23.8.2
Theorem ........................................................................................................................................ 258
24
APPENDIX..................................................................................................................................................... 267
24.1
24.2
25
CONVOLUTION PROCESS..........................................................................................................................267
DIRAC DELTA FUNCTION AND CONVOLUTION PROCESS ...........................................................................270
REFERENCE................................................................................................................................................. 271
5
1 CANNEL CAPACITY AND IDEAL COMMUNICATION
SYSTEMS
1.1 Channel capacity definition
Suppose the following transmission systems
Source
information
Transduction
Receiver
skay
NOISE
added
Transmitter
Transduction
Modulated
signal
Destination
Antenna and Receiver
NOISE added
figure 1
Let us define the channel capacity:
•
For digital systems, the optimum system might be defined as the system that
minimizes the probability of bit error at the system output. The variables are bit
error, signal bandwidth, transmitted energy and channel bandwidth.
The question is: is it possible to invent a system with non bit error at the output
even when we have noise introduced into the channel ? The answer is yes, under
certain assumption Shannon showed that (for the case of signal plus white
Gaussian noise) a channel capacity C(bits/s) could be calculated such that if the
rate information R(bits/s) was less then C, the probability of error would
approach to zero.
6
S⎞
⎛
C = B log 2 ⎜1 + ⎟
⎝ N⎠
eq 1
where B is the channel bandwidth in (Hz) and S/N is the signal-to-noise power
ratio(watts/watts, no dB) at the input to the digital receiver.
Shannon gives us a theoretical performance bound that we can strive to achieve
with practical communication systems. Systems that approach this bound usually
incorporate error correction coding.
•
In analog systems, in place of error probability, the optimum system might be
defined as the one that achieves the largest signal-to-noise ratio at the receiver
output, subject to design constraints such as channel bandwidth and transmitted
power.
In this case the question is: is it possible to design a system with infinite signal to
noise ratio at the output when noise is introduced to the channel ? The answerer
is no.
The law above, in the first equation, it was found considering that: if S is a continuous
signal between that varies s1 and s2 values and, if p(s) is the density of probability for S,
than p(s)⋅ds gives the probability for S of felling inside ds interval.
Therefore the information bits quantity related to S signal is
s2
q = ∫ p ( s ) log 2
s1
1
ds
p(s)
eq 2
1
is the number of bits needed to represent all values of signal S, each of
p(s)
which is multiplied by the density probability p(s) of the signal S
In a discrete case we easily have:
where log 2
N
q = ∑ Pn log 2
n=1
1
Pn
eq 3
where in case of equal probability Pn=1/N of the N symbols we had
N
q = ∑ Pn log 2
n=1
N
1
1
1
= ∑ log 2 N =
Pn n=1 N
N
N
∑ log
n =1
2
N = log 2 N
eq 4
7
As an example the representation of 8 states discrete signal, where all states are
supposed with the same probability, require 3 bits (each bit can assume 2 values high,
low so we using log2x) because
3 = log 2 8
eq 5
In the continuous scenario, if S is the average signal and σ2 is the variance, then it can
be shown that q (the number of bits needed to represent S) became maximum when
p(s) has a Gaussian distribution probability:
p( s) =
e
−
S2
2σ 2
eq 6
2πσ 2
In this case the bound of S are: s1=-∞ , s2=∞.
The corresponding quantity of information q (number of bits needed to represent S ) can
be obtained substituting this equation in the integral, above:
∞
q=
∫
−∞
1
p ( s ) log 2
e
−
S2
2σ 2
1
1
ds = log 2 (2π eS 2 ) 2 = log 2 (2π eS 2 )
2
bits/sample
eq 7
2πσ 2
here S2 is the average signal power.
Considering now the Shannon theorem which says that a signal of bandwidth B
requires at least 2B sample rate (samples/second). Therefore in a time interval t are
necessary 2B⋅t samples of the signal S, here each sample are univocally determined by
q bits. So the information quantity bit related to the sampled signal S with q bits
quantizing, on the time interval t is:
1
Q = 2 B ⋅ t ⋅ q = 2 Bt log 2 (2π eS 2 ) 2 = Bt log 2 (2π eS 2 )
bits
eq 8
The presence of noise corrupts the receiving information at the receiver input. The
relative information associated is:
1
QN = 2 B ⋅ t ⋅ q = 2 Bt log 2 (2π eS 2 ) 2 = Bt log 2 (2π eS 2 ) = 2 Bt log 2 (2π ePN ) bits
eq 9
where PN= S 2 is the average noise power .
Then at the input of the receiver we have the noise power PN along with the information
power signal PS:
8
QS + N = 2 B ⋅ t ⋅ qS + N = Bt{log 2 [2π e(PS + PN )]} bits
eq 10
where PS+PN =S2 is the total power of signal plus noise with Gaussian probability
density function
The uncorrupted quantity of information will be
Q = QS + N − QN = 2 B ⋅ t ⋅ qS + N = B ⋅ t{log 2 [2π e(PS + PN )] − log 2 [2π e(PN )]} =
= B ⋅ t log 2
⎛
2π e(PS + PN )
P ⎞
= B ⋅ t log 2 ⎜⎜1 + S ⎟⎟ bits
2π e(PN )
⎝ PN ⎠
eq 11
The bitrate Rb will be
⎛
P ⎞
Q
= B log 2 ⎜⎜1 + S ⎟⎟ = Rb bits/s
t
⎝ PN ⎠
eq 12
we can invert the equation to find PS/PN
Q
PS ⎛ B⋅t ⎞
= ⎜⎜ 2 − 1⎟⎟
PN ⎝
⎠
eq 13
where
PN = KTB
⇒
⎛ BQ⋅t ⎞
⎛ BQ⋅t ⎞
PS
⎜
⎟
= 2 − 1⎟ ⇒ PS = KTB⎜⎜ 2 − 1⎟⎟
KTB ⎜⎝
⎠
⎝
⎠
eq 14
This is the Hartely-Shannon law which contains the essential components of
transmission systems:
1.
2.
3.
4.
5.
bandwidth B
power of signal PS
power pf noise PN
duration of message t
temperature of reference T
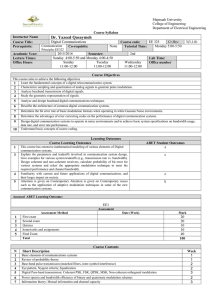
PS and PN power are reported in figure below as a function of the bandwidth, we have
fixed T=300 (K), Q=270833 (bit), K=1.38*10-23 (J/K) , t= 1 (s)
9
K
T
1.38E-23
tempo t (s)
300
Q (bit)
B (Hz)
Pn (w)
Ps (w)
1
270833
10000.0
4.1E-17
12500.0
5.2E-17
15625.0
6.5E-17
19531.3
8.1E-17
24414.1
1.0E-16
30517.6
1.3E-16
38147.0
1.6E-16
47683.7
2.0E-16
59604.6
2.5E-16
74505.8
3.1E-16
93132.3
3.9E-16
116415.3
4.8E-16
145519.2
6.0E-16
181898.9
7.5E-16
227373.7
9.4E-16
284217.1
1.2E-15
355271.4
1.5E-15
444089.2
1.8E-15
555111.5
2.3E-15
693889.4
2.9E-15
867361.7
3.6E-15
1084202.2
4.5E-15
1355252.7
5.6E-15
1694065.9
7.0E-15
2117582.4
8.8E-15
2646978.0
1.1E-14
3308722.5
1.4E-14
4135903.1
1.7E-14
5169878.8
2.1E-14
6462348.5
2.7E-14
5.9E-09
1.7E-10
1.1E-11
1.2E-12
2.2E-13
5.9E-14
2.2E-14
9.9E-15
5.5E-15
3.5E-15
2.5E-15
1.9E-15
1.6E-15
1.4E-15
1.2E-15
1.1E-15
1.0E-15
9.7E-16
9.2E-16
8.9E-16
8.7E-16
8.5E-16
8.3E-16
8.2E-16
8.1E-16
8.1E-16
8.0E-16
8.0E-16
7.9E-16
7.9E-16
bit rate Q/t
Pn (dBm)
Ps (dBm)
Ps/Pn (dB) (Kbit/sec)
-133.83
-52.30
82
270.833
-132.86
-67.64
65
270.833
-131.89
-79.71
52
270.833
-130.92
-89.18
42
270.833
-129.95
-96.56
33
270.833
-128.98
-102.28
27
270.833
-128.02
-106.67
21
270.833
-127.05
-110.03
17
270.833
-126.08
-112.59
13
270.833
-125.11
-114.53
11
270.833
-124.14
-116.01
8
270.833
-123.17
-117.13
6
270.833
-122.20
-118.00
4
270.833
-121.23
-118.66
3
270.833
-120.26
-119.18
1
270.833
-119.29
-119.58
0
270.833
-118.32
-119.90
-2
270.833
-117.36
-120.14
-3
270.833
-116.39
-120.34
-4
270.833
-115.42
-120.49
-5
270.833
-114.45
-120.62
-6
270.833
-113.48
-120.71
-7
270.833
-112.51
-120.79
-8
270.833
-111.54
-120.85
-9
270.833
-110.57
-120.90
-10
270.833
-109.60
-120.94
-11
270.833
-108.63
-120.97
-12
270.833
-107.66
-121.00
-13
270.833
-106.70
-121.02
-14
270.833
-105.73
-121.03
-15
270.833
-40.0
80
-45.0
75
-50.0
70
-55.0
65
-60.0
60
-65.0
55
-70.0
50
40
-80.0
35
-85.0
30
-90.0
25
-95.0
20
PS/PN=0 dB
and Q=B
-100.0
-105.0
-110.0
10
5
6462348.5
5169878.8
4135903.1
3308722.5
2646978.0
2117582.4
1694065.9
1355252.7
867361.7
1084202.2
693889.4
555111.5
444089.2
355271.4
284217.1
227373.7
181898.9
145519.2
93132.3
116415.3
74505.8
59604.6
47683.7
-20
38147.0
-15
-135.0
30517.6
-10
-130.0
24414.1
-5
-125.0
19531.3
0
-120.0
15625.0
Pn (dBm)
Ps (dBm)
Ps/Pn (dB)
15
-115.0
12500.0
Ps/Pn (dB)
45
-75.0
10000.0
Ps (dBm), Pn (dBm)
Singal power Ps (dBm), Noise Power Pn (dBm), Ps/Pn ratio (dB)
bandwidth (Hz)
figure 2
E:\documenti per
corsi\ELETTRONICA T
10
we can get some note:
•
•
By equation 11 we can observe that the information Q(n°bit) remains constant if
the product B⋅t is constant, the exchange between B and t is used in satellite
application. In fact the data can be collected, along the orbit, with low B and high
period of time t, the data are stored by using a memory device. After, the
transmission of data stored before, is possible only in a short period when the
satellite is flying above the Earth Station, by using a great bandwidth B.
The bit-rate Q/t (bit/s)
remain constant increasing the bandwidth and
simultaneously reducing the PS/PN ratio, this represent a possible application in
spread spectrum communication system, the greater the bandwidth the lower
PS/PN ratio. Anyway if we are increasing the bandwidth, then the power of the
signal PS will reduce to tend asymptotically to a constant while PN will increases
more. When
Q
PS ⎛⎜ B⋅t ⎞⎟
= ⎜ 2 − 1⎟ = 1
PN ⎝
⎠
eq 15
i.e. where
⎛
P ⎞
Q
= B log 2 ⎜⎜1 + S ⎟⎟ = B log 2 (1 + 1) = B = Rb
t
⎝ PN ⎠
bits/s
eq 16
Therefore when PS=PN, then the maximum transmission bandwidth (Hz) needed
for a correct received signal, is the same order of the channel capacity (bit/s).
Onboard of a satellite, one of the main problems concerns the heavy of the transmitter
systems, and the power required to transmission signaling. Therefore we are looking
for a system which can beneficial of exchanging between (PS/PN) and bandwidth
between input and output of the receiver.
In frequency modulation systems the bandwidth of the carrier channels are greater
than RX_output bandwidth channel, so at the input of the receiver can be used a
lower PS/PN. Anyway FM must work above FM C/N threshold and since the greater the
bandwidth, the greater the noise, then C/N threshold will increase with bandwidth. As a
consequence the Carrier power C will be affected by the same amount of growth too,
resulting in a bigger amplifier rather then a little amplifier as required.
As a conclusion, once we have been fixed PS/PN and the bit_rate Q/t, then we can
observe that the lower the PN, the lower PS. So the very important component of a
transmission design is trying to reducing the noise power PN.
11
1.2 Spectral Efficiency
The spectral efficiency η of a digital signal is given by the number of bits per second
of data that can be supported by each hertz of bandwidth, in other words is the bit rate
supported by the unit of bandwidth.
η=
R
(bits/s)/Hz
B
eq 17
In application in which the bandwidth is limited by physical constraints, the goal is to
choose a signaling technique that gives the highest spectral efficiency while achieving a
low probability of bit error at the system output. Moreover, the maximum possible
spectral efficiency is limited by the channel noise if the error is to be small, this
maximum spectral efficiency is given by Shannon’s capacity formula
η=
⎡ P ⎤
Rb
= log 2 ⎢1 + S ⎥
B
⎣ PN ⎦
(bits/s)/Hz
eq 18
All the binary codes have η ≤ 1. Multilevel signaling can be used to achieve much
greeter spectral efficiency.
12
The greater Ps/PN, the more is the spectral efficiency. Plotting this function we have the
following graph:
Spectral Efficiency as a function of SNR
9.00
300.00
8.00
250.00
7.00
200.00
5.00
150.00
4.00
3.00
SNR (Lineare)
Spectral efficiency
6.00
100.00
2.00
Spectral efficiency
50.00
SNR (lineare)
1.00
24.33
24.23
24.13
24.03
23.93
23.82
23.71
23.60
23.48
23.36
23.24
23.12
22.99
22.86
22.72
22.58
22.43
22.28
22.12
21.96
21.79
21.61
21.43
21.24
21.04
20.83
20.61
20.37
20.13
19.87
19.59
19.29
18.98
18.63
18.26
17.85
17.40
16.90
16.33
15.68
14.91
13.98
12.79
8.45
11.14
0.00
0.00
0.00
SNR (dB)
figure 3
E:\documenti per
corsi\ELETTRONICA T
13
2 CODING
If the data at the output of a digital communication system have errors that are too
frequent for the desired use, the errors can be often reduced by use either of two main
techniques:
•
•
Automatic repeat request (ARQ)
Forward error correction (FEC)
In an ARQ system, when a receiver circuit detects parity errors in a block of data, it
requests that the data block be retransmitted. In FEC system, the transmitted data are
encoded so that the receiver can correct, as well as detect errors. These procedures are
also classified as channel coding because they are used to correct errors caused by
channel noise. This is different from source coding, where the purpose of coding is to
extract the essential information from the source and encode it into digital form so that it
can be efficiently stored or transmitted using a digital techniques (example PCM)
The choice between using the ARQ or the FEC technique depends on the particular
application.
• ARQ is often used in computer communication systems because is relatively
inexpensive to implement and there is usually a duplex (two-way) channel so that
the receiving and can transmit back an acknowledgement (ACK) for correctly
received data or a requests for retransmission (NAC) when the data are received
in error.
• FEC is preferred on systems with large retransmission delays because if the
ARQ technique were used, the effective data rate would be small; the transmitter
would have long periods while waiting for the ACK/NAC indicator, which is
retarded by the long transmission delay.
2.1 Code performance
The improvement in the performance of a digital communication system can be
achieved by the use of coding as illustrated below:
14
figure 4
It is assumed that a digital signal plus channel noise is present at the receiver input. The
performance of a system that uses binary-phase-shift-keyed (BPSK) signaling is
shown both for the case when coding is used and for the case when there is no coding.
For the no coding case, the optimum (matched filter detector ) circuits is used at the
receiver. For the coded case a Golay code is used.
•
Pe is the probability of error-also called the Bit Error Rate (BER)- that is
measured at the receiver output.
•
Eb/N0 is the energy per-bit / noise-density ratio at the receiver input
•
The coding gain is defined as the reduction in Eb/N0 (in dB) that is achieved
when coding is used, when compared with required for the uncoded case at
some specific level of Pe. This improvement is significant in space
communication applications, where every decibel of improvement is valuable
since its possible to get the same Pe by using a lower Bit energy ( lower Power)
in transmission .
The figure also show noted that there is a coding threshold in the sense that the coded
system actually provides poorer performance than the uncoded system when Eb/N0 is
less than the threshold value.
15
For optimum coding, Shannon’s channel capacity theorem already seen, gives the
Eb/N0 required.
Channel
capacity
⎛
Q
P ⎞
= B log 2 ⎜⎜1 + S ⎟⎟ = Rb bits/s
eq 19
t
⎝ PN ⎠
That is, if the source rate is below the channel capacity Rb, the optimum code will
allow the source information to be decoded at the receiver with Pe→0. (i.e.10-∞) , even
though there is some noise in the channel.
We will now find the required Eb/N0 so that Pe→0 with the optimum (unknown) code.
Assume that the optimum encoded signal is not restricted in bandwidth, i.e. assuming
an optimum encoder formed by a sequence of infinite redundant bit such that in order
to transmit signal plus redundant coding bit, the required bandwidth became infinite.
Then from equation above where it has been posed C( as channel capacity), PS=S ( as
power signal) and PN=N (as Noise power):
S⎞
⎛
C = B log 2 ⎜1 + ⎟
N⎠
⎝
bit/s
⎧
⎧
⎛ E / T ⎞⎫
⎛
S [Watt ] ⎞⎫
C = lim ⎨ B log 2 ⎜⎜1 +
⎟⎟⎬ = lim ⎨ B log 2 ⎜⎜1 + b b ⎟⎟⎬ =
B →∞
N 0 B ⎠⎭
⎝ N [Watt ] ⎠⎭ B→∞ ⎩
⎝
⎩
1
if B = : ⇒
x
⎧
⎛
Eb ⎞ ⎫
x⎟⎪
⎪ log 2 ⎜⎜1 +
⎧1
N 0Tb ⎟⎠ ⎪
⎛ Eb / Tb ⎞⎫
⎪
⎝
C = lim⎨ log 2 ⎜⎜1 +
x ⎟⎟⎬ = lim⎨
⎬
x→0 x
N0
x
⎝
⎠⎭ x→0 ⎪
⎩
⎪
⎪
⎪
⎩
⎭
eq 20
eq 21
where :
Tb is the time needed to send one bit and N is the noise power that occurs within the
bandwidth of the signal:
N0
df = N 0 B
−B 2
N =∫
B
eq 22
where B is the signal bandwidth and N0/2 is the noise power spectral density (W/Hz).
16
L’ Hospital’s rule is used to evaluate this limit:
⎧∂ ⎡
⎛
⎞⎤ ⎫
E
⎪ ⎢log 2 ⎜⎜1 + b x ⎟⎟⎥ ⎪
N 0Tb ⎠⎦ ⎪
⎪ ∂x
⎝
C = lim⎨ ⎣
⎬=
x →0
∂
⎪
⎪
x
∂x
⎪
⎪
⎭
⎩
1
Eb
⎧
⎫
log 2 e ⎪
⎪⎛
⎞NT
E
⎪ ⎜⎜1 + b x ⎟⎟ 0 b
⎪
N 0Tb ⎠
E
E ⎛ ln e ⎞
E
1
⎪⎝
⎪
= lim⎨
= b (log 2 e ) = b ⎜
= b
⎟
⎬
x →0
1
N 0Tb ⎝ ln 2 ⎠ N 0Tb ln 2
⎪
⎪ N 0Tb
⎪
⎪
⎪
⎪
⎩
⎭
eq 23
where we have used the logarithm property of base changes
log a ( x ) =
log b ( x )
log b (a )
⇒
log 2 (e ) =
log e (e ) ln (e )
1
=
=
log b (2) ln (2 ) ln(2)
eq 24
and the derivative property of logarithm
d
du
1
log a (u ) =
dx
u ⋅ ln (a ) dx
⇒
⎧
⎪
⎛
E
⎪d ⎡
lim ⎨ ⎢log 2 ⎜⎜1 + b
x →0
N 0Tb
⎝
⎪ dx ⎣
⎪⎩
⇒
⎫
⎪
⎞⎤
Eb ⎪
Eb 1
1
⎟
x ⎟⎥ =
⎬=
⎠⎦ ⎛⎜1 + Eb x ⎞⎟ ln 2 N 0Tb ⎪ N 0Tb ln 2
⎜
⎪⎭
N 0Tb ⎟⎠
⎝
eq 25
If we signal at a rate, approaching the channel capacity, then Pe→0, and we have the
maximum information rate allowed for the Pe→0 (i.e. the optimum system). Thus
C=
1
Tb
where Tb = bit rate source
eq 26
E
1
1
= b
Tb N 0Tb ln 2
⇒
17
Eb
= ln 2 = −1,59 dB
N0
eq 27
This minimum value for Eb/N0 is -1.59 dB and is called Shannon limit.
That is, if the optimum coding/decoding is used at the transmitter and receiver, error
free data will be recovered at the receiver output, provided that the Eb/N0 at the receiver
input is larger than -1.59 dB, assuming that the ideal (unknown )code is used.
Any practical systems will perform worse than this ideal system described by Shannon’s
limit, thus the goal of digital system designer is to find practical codes that approach the
performance of Shannon’s limit.
The better code reported in figure above, achieves their coding gains at the expense of
bandwidth expansion. That is when redundant bits are added to provide coding gain, the
overall data rate and, consequently, the bandwidth of the signal are increased by a
multiplicative factor that is the reciprocal of the code rate. Thus, if the uncoded signal
takes up all the available bandwidth, coding cannot be added to reduce receivers errors,
because the coded signal would take up too much bandwidth.
18
3 INTERSYMBOL INTERFERENCE
The absolute bandwidth of rectangular multilevel pulses tend to infinity; on the contrary
the bandwidth available in communication system is always limited. Therefore in order
to limit the bandwidth and reducing the PSD (Power Spectral Density) of signaling we
needed some kind of filtering system for the binary pulses.
When these pulses are filtered improperly as they pass through a communication
system, they will spread in time, and the pulse for each symbol may be smeared into
adjacent time slot and cause intersymbol interference (ISI).
Input weaveform, win(t)
Individual pulse response
Received waveform, wout(t)
(sum of pulse responses)
T
0
1
0
0
0
s
t
t0
t0
t
t0
t
t
t0
t
Intersymbol interference
0
1
0
1
1
t0
Sampling points
(trasmitter clock)
t
t0
Sampling points
(receiver clock)
Sampling points
(receiver clock)
figure 5
Now, how do we can restrict the bandwidth and still not introduce ISI ? This problem
was first studied by Nyquist who discovered three different methods for pulse shaping
that could be used to eliminate/reducing ISI.
Let us consider a digital signaling system as shown below, in which the flat-topped
multilevel signal at the input is:
19
Trasmitting filter
HT(f)
Win(t)
Channel (filter)
charateristics
HC(f)
Wc(t)
Receiver filter
HR(f)
Flat top
pulses
Wout(t)
Recovered rounded
Pulse (to sampling
and decoding cicuits)
figure 6
Where at the input we have a series of flat-top impulse of a symbol rate D=1/Ts
(pulses/s):
win (t ) = ∑ an h(t − nTs )
eq 28
n
where an is the amplitude of multilevel signal (for a binary signal there are only two
levels permitted) and, where the shaping of a single flat top-impulse is
⎛ t
h(t) = ∏ ⎜⎜
⎝ TS
Ts ⎫
⎧
⎞ ⎪1, se t ≤ 2 ⎪
⎟⎟ ≡ ⎨
⎬
⎠ ⎪0, se t > Ts ⎪
2⎭
⎩
is a flat top inpulse (rectangular inpulse shaping) eq 29
1
0.8
0.6
1
2π/Ts
0.4
0.2
-Ts/2
Ts/2
t
0
-20
-15
-10
-5
0
5
10
15
-0.2
20
freq
-0.4
figure 7 : time domain
figure 8: frequency domain
20
The frequency domain of a single flat-top impulse is obtained by Fourier transform
H( f ) =
Ts / 2
∫1⋅ e
−Ts / 2
+ Ts / 2
T /2
− j ωt
⎡ e − jωt ⎤
1 s
e − jωTs / 2 − e + jωTs / 2
− j ωt
− jω ⋅e dt = ⎢
=
=
dt =
⎥
− jω −T∫s / 2
− jω
⎣ − jω ⎦ −T / 2
s
⎛ T ⎞
Ts
sen⎜ ω s ⎟
− jωTs / 2
+ jωTs / 2
+ jωTs / 2
− jωTs / 2
−e
−e
e
2Ts e
⎝ 2⎠
= 2
=
= Ts
Ts
T
− jω
Tsωs
2j
ω s
2
2
eq 30
The PSD of single flat top impulse is then obtained by :
Ts / 2
2
2
T /2
1 s
H ( f ) = ∫ 1 ⋅ e − jωt dt =
− jω ⋅ e − jωt dt =
∫
ω
j
−
−Ts / 2
−Ts / 2
2
2
⎡ 1 − j ωt ⎤
e jωTs / 2 − e − jωTs / 2 (Ts / 2)
e ⎥
=2
=
=⎢
(Ts / 2)
− 2 jω
⎣ − jω
⎦ −Ts / 2
Ts / 2
⎛ T ⎞
sen⎜ ω s ⎟
2
⎝ 2⎠
= Ts
T
ω s
2
2
eq 31
2
1
which is plotted in figure below
0.9
0.8
0.7
0.6
0.5
0.4
0.3
0.2
0.1
0
-20
-15
-10
-5
0
5
10
15
20
figure 9
21
3.1 Spectral property reminder (square wave spectrum)
Let us consider a square wave signal s (t ) as shown below
s(t)
-T/2
-∆t/2
t
∆t/2
T/2
figure 10
The relative s0 (t ) is shown in figure below where it is represented by a unitary
impulse s I (t )
s0(t) = sI(t)
-T/2
-∆t/2
∆t/2
t
T/2
figure 11
Then S 0 (ω ) has the shape reported below
S0(ω) = SI(ω)
ω
-4π/∆t
-2π/∆t
2π/∆t
4π/∆t
figure 12
22
As a consequence S (ω ) has the following shape
S(ω)
ω0=2π/T0
ω
-4π/∆t
-2π/∆t
2π/∆t
4π/∆t
Figura 1
3.2 Equalizing filter
Using the Dirac delta function and the convolved product we can also rewrite the
flat-top impulse series as:
⎡
⎤
win (t ) = ∑ an h(t − nTs ) = ∑ an h(t ) ∗ δ (t − nTs ) = ⎢∑ anδ (t − nTs )⎥ ∗ h(t )
n
n
⎣n
⎦
eq 32
The output of the linear system would be just the input impulse train convolved with the
equivalent impulse response of the overall system; that is
⎧⎡
⎫
⎤
wout (t ) = ⎨⎢∑ anδ (t − nTs )⎥ ∗ h(t )⎬ ∗ hT (t ) ∗ hC (t ) ∗ hR (t )
⎦
⎩⎣ n
⎭
eq 33
Calling the equivalent impulse response of the overall system as:
he (t ) = h(t ) ∗ hT (t ) ∗ hC (t ) ∗ hR (t )
eq 34
23
then
⎡
⎤
wout (t ) = ⎢∑ anδ (t − nTs )⎥ ∗ he (t ) = ∑ an he (t − nTs )
n
⎣n
⎦
eq 35
Note that he(t) is also the pulse shape that will appear at the output of the receiver filter
when a single Dirac pulse is fed into the transmitting filter.
The equivalent system transfer function is in frequency domain and it is represented by
the product of the corresponding Fourier transform of each single element:
H e ( f ) = H ( f )HT ( f )HC ( f )H R ( f )
eq 36
H(f) is the Fourier transform already seen that define the pulse shape
⎡ ⎛ Ts ⎞ ⎤
⎢ sen⎜ ωs 2 ⎟ ⎥
⎠⎥
H ( f ) = Ts ⎢ ⎝
T
⎢ ω s ⎥
s
⎢⎣
2 ⎥⎦
eq 37
Then the receiving filter is given by
HR( f ) =
He ( f )
H ( f )HT ( f )HC ( f )
eq 38
When He(f) is chosen to minimize the ISI, HR(f) is called an equalizing filter. The
equalizing filter characteristic depends on Hc(f), the channel frequency response, as
well as on the required He(f).
When the channel consists of dial-up telephone lines, the channel transfer function
changes from call to call and the equalizing filter may need to be an adaptive filter. In
this case, the equalizing filter adjusts itself to minimize the ISI. In some adaptive
schemes, each communication session is preceded by a test pattern that is used to
adapt the filter electronically for the maximum eye opening (minimum ISI). Such
sequence are called learning or training sequence and preambles.
As an example of training sequence we report those used in GSM mobile network
Um-Interface for a burst of 148 bits:
24
Normal burst (NB): TCH end other control channel, except. RACH, SCH e FACH
TB
3
Encrpted bits
57
1
Training sequence
26
0.577 ms
1
Encrpted bits
57
TB
3
GP
8.25
156.25 bit
Freq. correction burst (FB): Is equivalent to unmodulated carrier . I used to synchronize the
mobile in frequency
TB
3
Fixed bits
142
0.577 ms
TB
3
GP
8.25
156.25 bit
Synchronization burst (SB): Is used to temporally synchronize the mobile, it contains TDMA
frame number and and BSIC
TB
3
Encrpted bits
39
Synchronization sequence
64
0.577 ms
Encrpted bits
39
TB
3
GP
8.25
156.25 bit
figure 13
The pulse train at the output of the receiver filter is
wout (t ) = ∑ an he (t − nTs )
eq 39
n
The output pulse shape is affected by the input pulse shape (flat-topped in this
case), the transmitter filter, the channel filter, and the receiving filter. Because, in
practice, the channel filter is already specified, the problem is to determine the
transmitting filter and the receiving filter that will minimize the ISI on the rounded pulse
at the output of the receiving filter.
3.3 Nyquist’s First Method (Zero ISI)
Nyquist’s first method for eliminating ISI is to use an equivalent transfer function He(f),
such that the impulse response satisfies the condition
⎧C for k = 0 ⎫
he (kTs + τ ) = ⎨
⎬
⎩0 for k ≠ 0⎭
eq 40
where k is an integer, Ts is the symbol (sample) clocking period, τ is the offset in the
receiver sampling clock times due to propagation delay that should be compared with
the times of the input symbols, and C is a nonzero constant.
25
That is, for a single flat-top pulse of level a at the input to the transmitting filter at t=0,
the received pulse would be a⋅he(t) and it would have a value of a⋅C at t=τ (i.e. for
K=0) but it would not cause interference at any other sampling time because
he(kTs+τ)=0 when k≠0.
Input weaveform, win(t)
0
1
0
0
Individual Nyquist filter
pulse response is 0 in KTs
0
Ts
Received waveform, wout(t)
(sum of filter pulse responses)
Improper filtering with ISI
s
t
t0
t
t0
t0
t
t0
t
Ts
No Intersymbol interference
0
1
0
1
1
t
t0
Sampling points
(trasmitter clock)
t
t0
Sampling points
(receiver clock)
Sampling points
(receiver clock)
figure 14
Individual Nyquist filter pulse
response is 0 in KTs
NO ISI
Input weaveform, win(t)
0
1
0
1
Improper filtering with ISI
Tss
t
Ts
2Ts
3Ts
figure 15
26
A rectangular filter function can be used for this purpose, therefore suppose that we
chose a (sinx)/x function for he(t), in particular, let τ =0, and chose
he (t ) =
sin π f s t
π f st
KTs=0 KTs≠0
eq 41
f s = 1 / Ts
Then this impulse response satisfies zero ISI Nyquist’s first criterion because in t=KTs=0
we have max amplitude of the output function he(t) whereas in t=KTs≠0 we have zero
amplitude of function.
lim he (t ) = lim
t →0
t →0
sin π f s t 0
=
π f st
0
⇒
lim
t →0
− π f cos π f s t
d ⎡ sin π f s t ⎤
= −1 = 1
⎢
⎥ = lim
t
→
0
dt ⎣ π f s t ⎦
π fs
eq 42
Consequently, if the transmit and receive filters are designed so that the overall transfer
function is
He ( f ) =
1 ⎛ f ⎞
∏⎜ ⎟
f s ⎜⎝ f s ⎟⎠
−B=−
D
2
+B=
D
2
freq
eq 43
i.e. like a rectangular frequency response, there will be no ISI.
Furthermore, the absolute bandwidth of this transfer function is 2B=fs=D . This is the
optimum filtering method to produce a minimum bandwidth system. It will allow signaling
at a baud rate of D=1/Ts=2B (pulses/s), where B=D/2 is the absolute bandwidth of the
system. As an example, if D=271 ks/s then the bandwidth of filter is B=D/2=135.5 KHz.
However, the (sinx/x) type of overall pulse shape has two practical difficulties:
•
•
The overall amplitude transfer characteristic He(f) has to be flat over a bandwidth
–B<f<B and zero elsewhere. This is physically unrealizable (i.e. the impulse
response would be non casual and of infinite duration)
The synchronization of the clock in the decoding sampling circuit has to be
almost perfect, since the (sinx/x) pulse decays only as 1/x and is zero in
adjacent time slot only when is at the exactly correct sampling time. Thus,
inaccurate sync will cause ISI.
Because of these difficulties, we are forced to consider other pulse shapes that have a
slightly wider bandwidth then a rectangular –B<f<B.
27
The idea is to find pulse shapes that go through zero at adjacent sampling points and
yet have an envelope that decays much faster than 1/x so that clock jitter in the
sampling times KTs≠0 does not cause appreciable ISI. One solution for the equivalent
transfer function, which has many desirable future, is the raised cosine-rolloff Nyquist
filter.
3.4 Raised Cosine-Rolloff Nyquist Filtering
DEFINITION: the raised cosine-rolloff Nyquist filter has the transfer function:
⎧ 1,
⎪ ⎧
⎡ π ( f − f1 )⎤ ⎫⎪
⎪1⎪
H e ( f ) = ⎨ ⎨1 + cos ⎢
⎥ ⎬,
⎣ 2 f ∆ ⎦ ⎭⎪
⎪ 2 ⎪⎩
⎪0,
⎩
f < f1 ⎫
⎪
⎪
f1 < f < B ⎬
⎪
f > B ⎪⎭
eq 44
Where B is the absolute bandwidth and the parameters f∆ and f1 are
f∆ = B − f0
eq 45
f1 = f 0 − f ∆
f0 is the 6-dB Raised Cosine filter bandwidth
r=
f∆
f0
⇒
f ∆ = rf 0
eq 46
Where r is the rolloff factor of the filter.
Consequently
B = f 0 + f ∆ = f 0 + rf 0 = f 0 (1 + r )
eq 47
f1 = f 0 − f ∆ = f 0 − rf 0 = f 0 (1 − r )
The filter characteristics are illustrated in figure below:
28
He(f)
f∆
f∆
1.0
0.5
-B
-f0
-f1
f1
f0
B
Freq.
6-db bandwidth
figure 16
For several value of the rolloff factor r the corresponding required signaling transmission
bandwidth B are:
He(f)
1.0
r0=0, min bandwidth
0.5
f0=fB
r1=0.5
r2=1
Freq.
figure 17
For rolloff factors r=0 we have f∆=0 and we obtain the minimum-bandwidth required
case, where f0=B.
The corresponding impulse shape response is
29
⎛ sin (2πf 0t ) ⎞ ⎡ cos(2πf ∆ t ) ⎤
⎟⎟ ⎢
he (t ) = F −1 [H e ( f )] = 2 f 0 ⎜⎜
2⎥
f
t
2
π
0
⎠ ⎣1 − (4 f ∆ t ) ⎦
⎝
eq 48
when r = 0, the corresponding impulse pulse shape response became like (sinx/x):
⎛ sin (2πf 0t ) ⎞
⎛ sin (2πf 0t ) ⎞ ⎡ cos(0) ⎤
⎟⎟
⎟⎟ ⎢
he (t ) = F −1 [H e ( f )] = 2 f 0 ⎜⎜
= 2 f 0 ⎜⎜
2⎥
⎝ 2πf 0t ⎠
⎝ 2πf 0t ⎠ ⎣1 − (0 ) ⎦
Time Response for different rolloff factor: r=0
eq 49
r= 0.5 r=1
20
impulse responce
15
10
he_(r=0)
he_(r=0.5)
he_(r=1)
5
0.400
0.350
0.300
0.250
0.200
0.150
0.100
0.050
0.000
-0.050
-0.100
-0.150
-0.200
-0.250
-0.300
-0.350
-0.400
0
-5
Ts (symbol time)
figure 18
E:\documenti per
corsi\ELETTRONICA T
As the absolute bandwidth is increased (e.g. r=0, r=0.5 or r = 1.0) the filtering
requirements are relaxed, the clock timing requirements are relaxed too, since the
envelope of the impulse response decays faster than 1/t (on the order of 1/t3 for large
value of t).
30
Let us now develop a formula which gives the baud rate that the raised cosine-rolloff
system can support without ISI. From figure above, the zeros in the system impulse
response occur at t =n/2f0 where n≠0. Therefore, data pulses may be inserted at each
of these zero points without causing ISI. That is, referring to
⎧C for k = 0 ⎫
he (kTs + τ ) = ⎨
⎬
⎩0 for k ≠ 0⎭
eq 50
with τ =0, we see that the raised cosine-rolloff filter, satisfies Nyquist’s first criterion (for
the absence of ISI) if the symbol clock period is equal to Ts=1/(2f0). The
corresponding baud rate is
D=
1
= 2 f0
Ts
(Symbol / s )
⇒
f0 =
D
2
That is, the 6-dB bandwidth of the raised cosine-rolloff filter, f0, is designed to be half
the symbol (baud) rate.
D 2B − D
B − f0
2B − D
f
2 =
2
=
=
r= ∆ =
D
D
D
f0
f0
2
2
2B
⇒ D ⋅ r = 2B − D
⇒ D=
1+ r
B−
⇒
eq 51
where B is the absolute bandwidth of the system and r is the system rolloff factor.
B=
D
(1 + r )
2
eq 52
The greater r the grater B, and as a function of B and r we can aspect a maximum
value of symbol rate D.
Comparing to first criteria where B=D/2 now the bandwidth is increased when r≠0
31
4 BANDPASS SIGNALING
4.1 COMPLEX ENVELOPE RAPPRESTNATION OF BANDPASS
WAVEFORMS
4.1.1 Definitions: Baseband, Bandpass, and modulation
Definition. A baseband waveform has a spectral magnitude that is nonzero for
frequencies in the vicinity of the origin (i.e. f=0) and negligible elsewhere.
f0
f
figure 19
Definition. A bandpass waveform has a spectral magnitude that is non zero for
frequencies in some band concentrated about a frequency f =±fc, where fc>>0. the
spectral magnitude is negligible elsewhere. fc is called the carrier frequency.
f
-fC
+fC
figure 20
Definition. Modulation is the process of imparting the source information on to a
bandpass signal with a carrier frequency fc by the introduction of amplitude or phase
perturbations or both. This bandpass signal is called the modulated signal s(t), and the
baseband source signal is called the modulating signal m(t).
As the modulated signal passes through the channel, noise corrupts it. The result is a
bandpass signal-plus noise waveform that is available at the receiver input, r(t). (see
figure below) the receiver has the job of trying to recover the information that was sent
from the source; m* denote the corrupted version of m.
32
4.1.2 Complex Envelope Representation
All bandpass waveform, whether they arise from a modulated signal, interfering
signals, or noise, may be represented in a convenient form by the theorem that follows.
v(t) will be used to denote the bandpass waveform canonically; it can represent the
signal when s(t)=v(t), the noise when n(t)=v(t), the signal plus noise at the channel end
when r(t)=v(t).
m
Signal
processing
g(t)
Carrier
circuits
s(t)
Trasmission
medium
(channel)
r(t)
Carrier
circuits
g*(t)
Signal
processing
m*
Receiver
Trasmitter
Figure 21: communication system
4.1.3 Theorem
Any physical bandpass waveform can be represented by
{
}
v(t ) = Re g (t )e jωct = Re { g (t ) [ cos ωc t + j sin ωc t ]}
eq 53
here, Re(⋅) denotes the real part of (⋅), g(t) is called the complex envelope of v(t), and
fc is the associated carrier frequency (in Hertz) where ωc=2πfc is the radian frequency.
Furthermore, two other equivalent representations are
v(t ) = R (t ) cos [ωc t + θ (t )]
eq 54
and
v(t ) = x(t ) cos ωc t − y (t ) sin ωc t
eq 55
where
g (t ) = x(t ) + jy (t ) = g (t ) e j∠g (t ) = R(t )e jθ (t )
eq 56
33
x(t ) = Re { g (t )} = R (t ) cos θ (t )
eq 57
y (t ) = Im { g (t )} = R (t ) sin θ (t )
eq 58
R(t )
g (t ) = x 2 (t ) + y 2 (t )
eq 59
and
⎛ y (t ) ⎞
⎟
⎝ x(t ) ⎠
θ (t ) ∠g (t ) = tan −1 ⎜
eq 60
Consequently we obtain:
{
}
v(t ) = Re g (t )e jωct = Re { g (t ) [ cos ωc t + j sin ωc t ]} = Re {[ x(t ) + jy (t ) ][ cos ωc t + j sin ωc t ]} =
= Re { x(t ) cos ωct + jx(t ) sin ωc t + jy (t ) cos ωc t − y (t ) sin ωc t} =
= x(t ) cos ωc t − y (t ) sin ωc t
eq 61
In communication systems, the frequencies in the baseband signal g(t) are said to be
heterodyned up to fc.
The complex envelope, g(t), is usually a complex function of time, it is the baseband
equivalent of the bandpass signal v(t), and it is a generalization of the phasor concept.
In this case x(t) is said to be the in-phase modulation component also colled I(t), and
y(t) is said to be quadrature modulation component Q(t) associated with v(t).
Alternatively, the polar form of g(t) is represented by R(t) and θ(t); here R(t) is always
non negative and is said to be amplitude modulation (AM) on v(t), while θ(t) is said to
be the phase modulation (PM) on v(t).
34
4.2 REPRESENTATION OF MODULATED SIGNALS
Modulation is the process of encoding the source information m(t) (modulating signal)
into a bandpass signal s(t) (modulated signal). Consequently, the modulated signal is
just a special application of the bandpass representation. The modulated signal is
given by
{
s (t ) = Re g (t )e jωct
}
eq 62
where ωc=2πfc is the carrier frequency. The complex envelope g(t) is a function of
modulating signal m(t). That is,
g (t ) = g [m(t )]
eq 63
35
4.3 SPECTRUM OF BANDPASS SIGNALS
The spectrum of a bandpass signal is directly related to the spectrum of its complex
envelope.
Theorem.
If a bandpass waveform is represented by
{
v(t ) = Re g (t )e jωct
}
eq 64
than the Spectrum of the bandpass waveform is
V( f ) =
[
]
1
G ( f − f c ) + G * (− f − f c )
2
eq 65
where
G ( f ) = F [g (t )]
eq 66
is the Fourier transform of g(t)
the Power Spectral Density (PSD) of the waveform is
Pv ( f ) =
[
1
Pg ( f − f c ) + Pg (− f − f c )
4
]
eq 67
where
Pg ( f )
is the PSD of g(t)
G(f)
G(f)
G(-f-fc)
G(f-fc)
figure 22
36
5 AM, FM, PM MODULATED SYSETMS
5.1 Definitions
Amplitude Modulation (AM) is a system where the frequency of a carrier wave is held
constant while the amplitude is varied in sympathy with the voltage of the modulating
signal.
Frequency Modulation (FM) is a system where the amplitude of a carrier wave is held
constant while the frequency is varied in sympathy with the voltage of the modulating
signal.
Phase Modulation (PM) is a similar system where the phase of the carrier wave is
varied in sympathy with the voltage of the modulating signal, and as in frequency
modulation, the amplitude of a carrier is held constant.
Phase is the position of a rotating vector or phasor.
Angular Velocity is the rate of change of phase (usually expressed in radians per
second).
The Radian is a unit of angular displacement (as is degrees), there are 2*π radians in a
full circle (or 360°), so a radian is approximately 57°.
Frequency is a measure of the number of repetitions of a periodic waveform in unit time
(1 second). Frequency of a carrier wave is related to Angular Velocity, there are 2*π
radians in each cycle of a carrier wave, so the Angular Velocity is 2*π * frequency.
Pi is a numeric constant, it's value is approximately 3.1411592654. (You can
approximate it by using 22/7 - the error is less than 0.05%).
5.2 AMPLITUDE MODULATION
The complex envelope of an AM signal is given by
g (t ) = Ac [1 + m(t ) ]
eq 68
Where the constant Ac, has been included to specify the power level and m(t) is the
modulating signal (which may be analog or digital).
These equations reduce to the following representation for AM signal:
37
[
]
[
]
s (t ) = Re g (T )e jωct = Re Ac (1 + m(t ))e jωct =
eq 69
= Re[Ac (1 + m(t )) cos ωc t + jAc (1 + m(t )) sin ωc t ]
s (t ) = Ac [1 + m(t ) ] cos ωc t
eq 70
For convenience, it is assumed that the modulating signal m(t) is a sinusoid. The
modulating signal corresponds to the in-phase component x(t) of the complex envelope;
it also correspond to the real envelope g (t ) when m(t)≥-1 (the usual case).
If m(t ) = m cos(ωmt )
Then recalling that
eq 71
cos α cos β =
1
[cos(α + β ) + cos(α − β )]
2
we have
s (t ) = Ac [1 + m(t ) ] cos ωct = Ac [1 + m cos ωmt ] cos ωc t = Ac cos ωc t + Ac m cos ωmt cos ωc t =
= Ac cos ωc t +
1
1
Ac m cos (ωc + ωm ) t + Ac m cos (ωc − ωm ) t
2
2
eq 72
in figure below is shown a sinusoidal modulating wave and the resulting modulated AM
signal.
m(t)
envelope = information associated with modulating signal
g (t ) = Ac [1 + m(t ) ]
s(t )
Amin Ac
Amax
t
Tc
1/Tc=fc
figure 23
38
The overall modulation percentage is:
%modulation=
max [ m(t ) ] -min [ m(t ) ]
A max -A min
100 =
100
2Ac
2Ac
eq 73
5.2.1 Normalized AM average power
The normalized average power of an AM signal is:
1
2
g (t ) =
2
1
1
1
1
2
= Ac2 [1 + m(t )] = Ac2 1 + m 2 (t ) + 2m(t ) = Ac2 + Ac2 m(t ) + Ac2 m 2 (t )
2
2
2
2
s 2 (t ) =
eq 74
If modulation m(t) contains no dc level, then m(t ) = 0 and the normalized power of an
AM signal is
s 2 (t ) =
1 2 1 2 2
Ac + Ac m (t )
2
2
discrete
carrier
power
eq
sideband
power
The voltage magnitude spectrum of the AM signal is given by:
S( f ) =
Ac
[δ ( f − f c ) + M ( f − f c ) + δ ( f + f c ) + M ( f + f c )]
2
eq 76
39
M(f )
-B
f
B
a) Magnitude spectrum of modulation signal
S( f ) A
δ(f-fc)
Ac
2
-fc-B
-fc
Discrete carrier
term with
weight=1/2Ac
δ(f+fc)
Lower
sideband
-fc+B
fc-B
Upper
sideband
fc
fc+B
f
b) Magnitude spectrum of AM signal
figure 24
5.2.2 Definition: The modulation efficiency
The modulation efficiency is the percentage of the total power of the modulated signal
that conveys information.
In AM signal, only the sideband components conveys information, so the modulation
efficiency is
1 2 2
Ac m (t )
m 2 (t )
2
100 =
E=
100
2
1 2 1 2 2
1
(
)
+
m
t
Ac + Ac m (t )
2
2
eq 77
The highest efficiency that can be attained for a 100% AM signal would be 50%, (for
the case when square-wave modulation is used m=1).
40
6 PHASE MODULATION AND FREQUENCY MODULATION
6.1 Representation of PM and FM Signals
Phase Modulation (PM) and Frequency modulation (FM) are special cases of anglemodulated signaling. In this kind of signaling the complex envelope is
g (t ) = Ac e jθ (t )
eq 78
here θ(t) is a linear function of the modulating signal m(t), while g(t) is a non linear
function of the modulation.
The resulting angle-modulated signal is:
{
}
{
}
{
}
s (t ) = Re g (t )e jωct = Re Ac e jθ (t ) e jωct = Re Ac e j [θ (t )+ωct ] = Ac cos[ω c t + θ (t )]
eq 79
The relation between phase θ(t) and the instantaneous frequency fi is:
fi =
1 dθ (t )
2π dt
⇒
θ (t ) = 2π
t
∫ f dt
i
eq 80
−∞
1. for PM, the phase is directly proportional to the modulating signal m(t);
θ (t ) = D p m(t )
eq 81
Where the proportionally constant Dp is the phase sensitivity(phase deviation
constant) of the phase modulator, having units of radians per volt [assuming that
m(t) is a voltage waveform].
2. For FM, the phase is proportional to the integral of m(t), so that
t
θ (t ) = D f ∫ m(σ )dσ
eq 82
−∞
where the frequency deviation constant Df, has units of radians/volt-second.
41
We can develop an example for a PM first and FM later.
suppose
m(t ) = Am cos ωm t
•
eq 83
in the PM case we have
θ (t ) = D p m(t ) = D p Am cos ωmt = β p cos ωmt
eq 84
Where
β p = D p Am
•
is the phase modulation index
in the FM case we have
t
θ (t ) = D f ∫ m(σ )dσ = D f
−∞
t
∫A
m
1
cos ω mσ dσ = Am D f
ω
−∞
sin ω m t = β f sin ω m t
eq 85
Where
β f = Am D f
1
ωm
is the frequency modulation index
The complex envelope is:
g (t ) = Ac e jθ ( t ) = Ac e
jβ f sin ωmt
eq 86
Therefore the modulated bandpass signal is:
{
}
s (t ) = Re g (t )e jωct =
{
= Re Ac e
jβ f sin ωmt
}
{
e jωct = Re Ac e
[
j β f sin ω mt +ωc t
]
}= A cos[β
c
f
]
sin ω m t + ω c t =
eq 87
t
t
D f Am
⎤
⎡
⎤
⎡
cos ω m t ⎥
= Ac cos ⎢ω c t + ∫ β f cos ω m t ⎥ = Ac cos ⎢ω c t + ∫
ωm
−∞
−∞
⎦
⎣
⎦
⎣
42
[
the last term: cos ω c t + β f sin ω m t
]
can be studied by Bessels function
figure 25
Definition. If a bandpass signal is represented by
s (t ) = R (t ) cosψ (t ) = R (t ) cos[ωc t + θ (t )]
eq 88
then the instantaneous frequency (Hertz) of s(t) is [Boashash, 1992]
f i (t ) =
1
1 ⎡ dψ (t ) ⎤ 1 ⎡ d [ωc t + θ (t )]⎤
ωi (t ) =
=
⎥⎦ =
dt
2π
2π ⎢⎣ dt ⎥⎦ 2π ⎢⎣
1
1 dθ (t )
1 dθ (t )
=
ωc +
= fc +
2π
2π dt
2π dt
Therefore using θ (t ) = D f
eq 89
t
∫ m(σ )dσ
−∞
t
⎡
⎤
d ⎢ D f ∫ m(σ )dσ ⎥
1 dθ (t )
1 ⎣ −∞
⎦ = f + 1 D m(t )
f i (t ) = f c +
= fc +
c
f
2π dt
2π
dt
2π
eq 90
43
Of course, this is the reason for calling this type of signaling frequency modulation—
the instantaneous frequency varies about the assigned carrier frequency fc, in a manner
that is directly proportional to the modulating signal m(t).
vp
m(t)---sinusoidal modulating signal
fc+∆f
fi(t)---istantaneous frequency of the corresponding FM signal
fc
fc-∆f
s(t)---correspondign FM signal
s(t)---has constant amplitude
Ac
figure 26
figure above show how the instantaneous frequency varies when a sinusoidal
modulation (for illustrative purposes ) is used.
The frequency deviation from the carrier frequency is
f d (t ) = f i (t ) − f c =
1 d θ (t )
2π dt
eq 91
and the peak frequency deviation is
⎡ 1 d θ (t ) ⎤
∆ f = max [ f d (t ) ] = max ⎢
⎣ 2π dt ⎥⎦
eq 92
44
note that ∆f is a non negative number. In some applications, such as unipolar digital
modulation, the peak to peak deviation is used:
⎡ 1 dθ (t ) ⎤
⎡ 1 dθ (t ) ⎤
∆f pp = max ⎢
− min ⎢
⎥
⎣ 2π dt ⎥⎦
⎣ 2π dt ⎦
eq 93
For FM signaling, the peak frequency deviation is related to the peak modulating
voltage by:
1
⎡ 1 dθ (t ) ⎤
⎡ 1
⎤ 1
D f m(t )⎥ =
D f max[m(t )] =
D f Vp
∆f = max[ f d (t )] = max ⎢
= max ⎢
⎥
2π
⎣ 2π dt ⎦
⎣ 2π
⎦ 2π
eq 94
An increase in the amplitude of the modulation signal Vp will increase ∆f.
This in turn will increase the bandwidth of the FM signal, but will not affect the average
power level of the FM signal, which is AC2/2. As Vp is increased, spectral components
will appear farther and farther away from the carrier frequency, and the spectral
components near the carrier frequency will decrease in magnitude, since the total power
in the signal remains constant. This situation is distinctly different from AM signaling,
where the level of the modulation affects the power in the AM signal, but does not affect
its bandwidth.
In a similar way, the peak phase deviation may be defined by:
∆θ = max[θ (t )]
eq 95
which for PM, is related to the peak modulation voltage by
∆θ = D pV p = D p max[m(t )]
eq 96
6.1.1 Definition for peak phase deviation and peak frequency deviaton.
•
The phase modulation index is given by
β p = ∆θ
eq 97
where ∆θ is the peak phase deviation.
•
The frequency modulation index is given by:
45
βf =
∆F
B
eq 98
where ∆F is the peak frequency deviation and B is the bandwith of the modulating
signal, which, for the case of sinusoidal modulation, is fm, i.e the sinusoid sinusoid.
Using the deviation frequency expression found above we can rewrite:
1
D m(t ) D m(t ) D m(t )
∆F 2π f
f
f
=
=
=
βf =
ωm
fm
fm
2πf m
eq 99
Therefore the more greater m(t) the more greater βf, and the more greater ωm, the lower
βf. These facts have fundamental implication when we will speak about noise effect in
FM / PM modulation.
For digital signals, an alternative definition of modulation index is sometimes used and
is denoted by h in the literature. This digital index is:
h=
2∆θ
eq 100
π
where 2∆θ is the maximum peak to peak phase deviation change during the time that it
takes to send one symbol, Ts.
Strictly speaking, the FM index is different only for the case of single-tone (i.e.
sinusoidal) modulation.
However, it is often used for other waveshapes, where B is chosen to be the highest
frequency or the dominant frequency in the modulating waveform.
6.2 Spectra of Angle-Modulated signals
We found that the spectrum of an angle modulated signal is given by
S( f ) =
1
[G( f − f c ) + G * (− f − f c )]
2
eq 101
where
[
]
[
G ( f ) = F [g (t )] = F Ac e jθ (t ) = F Ac e j [ f ( m (t ) ]
]
eq 102
46
Since g(t) is a non linear function of m(t) a general formula relating G(f) cannot be
obtained, that is G(f) must be evaluated case by case basis for the particular
modulating waveshape of interest, furthermore superposition does not hold, and the FM
spectrum for the sum of two modulating waveshapes is not the same as summing the
FM spectra that were obtained when the individual waveshapes were used.
The evaluation into a closed form is not easy, one often has to use a numerical
techniques to approximate the Fourier transform integral. An example for the case of
sinusoidal waveshape will now be worked out.
6.2.1 Spectrum of a PM or FM signal with Sinusoidal Modulation
Let us assume as an example
t
θ (t ) = D f ∫ m(σ )dσ = D f
−∞
t
∫A
m
cos ω mσ dσ = Am D f
−∞
1
ω
sin ω m t = β f sin ω m t
eq 103
then the complex envelope is
g (t ) = Ac e jθ ( t ) = Ac e jβ sin ωmt
eq 104
which is periodic with period
Tm =
1 2π
=
f m ωm
eq 105
consequently g(t) could be represented by a Fourier series that is valid over all time
(-∞<t<∞);
∞
g (t ) =
∑c e
n= −∞
n
jnωmt
eq 106
where:
1
cn =
Tm
+
Tm
2
1
− jnω t
∫T g (t )e m dt = Tm
m
−
2
+
Tm
2
∫ [A e
c
T
− m
2
jβ sin ωmt
]
A
e − jnωmt dt = c
Tm
+
Tm
2
∫ [e
j ( β sin ωmt −nωmt )
]dt
eq 107
T
− m
2
Calling:
47
ϑ = ωmt
eq 108
⎛ Tm ⎞ 2π ⎛ Tm ⎞
⎜ − ⎟ = −π
⎟=
⎝ 2 ⎠ Tm ⎝ 2 ⎠
⎛ T ⎞ 2π ⎛ Tm ⎞
ϑ2 = ω m ⎜ + m ⎟ =
⎜ − ⎟ = +π
⎝ 2 ⎠ Tm ⎝ 2 ⎠
eq 109
ϑ1 = ωm ⎜ −
2π
dt
Tm
dϑ = ωm dt =
⇒
dt =
Tm
dϑ
2π
eq 110
Substituting we obtain
cn =
Ac
Tm
+
Tm
2
(
∫ [e
j β sin ωmt − nωmt )
T
− m
2
⎧1
cn = Ac ⎨
⎩ 2π
]dt = TA
c
m
ϑ =π
[e
∫
ϑ π
j ( β sin ϑ − nϑ )
2π ⎛ Tm ⎞
⎜
⎟
Tm ⎝ 2 ⎠
j ( β sin ϑ − nϑ )
∫ [e
2π ⎛ T ⎞
ϑ= ⎜ − m ⎟
Tm ⎝ 2 ⎠
] 2Tπ dϑ = TA
m
c
m
]dϑ ⎫⎬ = A J (β )
⎭
=−
ϑ=
c
Tm
2π
ϑ =π
∫ [e
ϑ π
j ( β sin ϑ − nϑ )
]dϑ
eq 111
=−
eq 112
n
This integral [ known as the Bessel function of the first kind of the nth order, Jn(β) ]
cannot be evaluated in closed form, but it has been evaluated numerically.
Taking the Fourier transform of g(t) we obtain:
G ( f ) = F [g (t )] =
n= +∞
n = +∞
n= −∞
n = −∞
∑ cnδ ( f − nf m ) = Ac
∑ J (β )δ ( f − nf )
n
m
eq 113
The spectrum is a series of Dirac-impulse spaced by nfm and multiplied by the
amplitude of Bessel function.
Therefore the discrete carrier term (at f=fc) is proportional to J 0 ( β ) ; consequently, the
level (magnitude) of the discrete carrier depends on the modulation index, it will be zero
if J 0 ( β ) = 0 .
The bandwidth of the bandpass angle-modulated signal depend on β and fm. In fact it
can be shown that 98% of the power is approximately contained in the bandwidth
48
BT = 2( β + 1) B
eq 114
where β is either the phase modulation index or the frequency modulation index
and B is the bandwidth of the modulating signal (which is fm for sinusoidal
modulation).
This formula is called Carson’s rule.
Using this result, we get the spectrum of FM or PM with sinusoidal modulation for
various modulation indexes as reported in figure below.
Fig below shows the spectral distribution of an FM wave, The column labelled fc is the
carrier and the other columns are the nth sidebands. Note the increasing in large
number of sidebands and the simultaneously carrier amplitude decreasing (in the centre
of the diagram) close to zero, when β change up to β =2, we can see how most of the
FM wave energy is in the sidebands.
The values of Bessel functions are commonly published in tables as in Table below. In
the table, mf is the modulation index and J0..Jn are the amplitude coefficients for the
carrier and sidebands
mf
J0
J1
J2
J3
0.00
1.000
0.000
0.000
0.000
0.05
0.999
0.025
0.000
0.000
0.50
0.938
0.242
0.031
0.003
1.00
0.765
0.440
0.115
0.020
1.50
0.512
0.558
0.232
0.061
2.00
0.224
0.577
0.353
0.129
2.50
-0.048
0.497
0.446
0.217
3.00
-0.260
0.339
0.486
0.309
4.00
-0.397
-0.066
0.364
0.430
Table 1
The greater mf the lower j0.
49
⎛
⎞
⎜ S( f ) ⎟
⎜
⎟
⎜ 1A ⎟
⎜
c ⎟
⎝ 2
⎠
J0(0,2)
1.0
J1(0,2)
f
fc
β=0,2
BT
⎛
⎞
⎜ S( f ) ⎟
⎜
⎟
⎜ 1A ⎟
⎜
c ⎟
⎝ 2
⎠
J0(1)
J1(1)
1.0
J2(1)
f
fc
β=1
fc+fm
fc+2fm
BT
⎛
⎞
⎜ S( f ) ⎟
⎜
⎟
⎜ 1A ⎟
⎜
c ⎟
⎝ 2
⎠
J0(2)
J1(2)
1.0
J2(2)
J2(2)
f
fc
β=2
fc+fm
fc+3fm
BT
⎛
⎞
⎜ S( f ) ⎟
⎜
⎟
⎜ 1A ⎟
⎜
c ⎟
⎝ 2
⎠
β=5
1.0
J0(5)
J1(5)
J2(5)
J3(5)
J4(5)
J5(5) J (5)
6
f
fc
fc+fm
fc+6fm
BT
figure 27
50
6.3 Noise and frequency modulation
6.3.1 Noise triangle
To understand the effect of noise on an FM signal, it helps to consider a single noise
frequency vector added to the FM signal vector Ec (see figure below). Since it is at a
different frequency, the noise vector will rotate about it with an angular velocity equal to
the difference between the noise frequency and the carrier frequency. This will produce
a variation in amplitude and phase of the resultant vector. The amplitude variation can
be largely eliminated in a limiter stage, but the phase variation (shown as Ø) remains
Resulting Vector
figure 28 : Effect of a noise phasor on an FM carrier phasor
The modulation index due to the noise voltage is constant, whereas the modulation
index for the desired modulation signal decreases with the increasing of the modulating
frequency fm or with the band B of the modulating signal (for FM).
β f = D f Am
1
ωm
=
∆f ∆f
≅
B
fm
eq 115
Or the similar expression already found
1
D m(t ) D m(t ) D m(t )
∆f 2π f
f
f
=
=
=
βf =
2πf m
ωm
fm
fm
eq 116
Consequently the lower the βf, the lower the phase variation θ(t) and the lower the
deviation frequency ∆f:
t
θ (t ) = D f ∫ m(σ )dσ = D f
−∞
t
∫A
m
−∞
cos ω mσ dσ = Am D f
1
ω
sin ω m t = β f sin ω m t
eq 117
This means that the noise degrades the Signal-to-Noise Ratio for an FM / PM
modulation more at higher modulating frequencies than at lower modulating frequency.
51
A plot of the noise vs frequency has a triangular shape, hence the term noise triangle
noise
AM noise rectangular
FM noise triangle
fc
f
figure 29: FM noise sideband distribution (mf=1).
Figure above shows the distribution of noise sidebands compared with the AM case.
6.4 Preemphasis and Deemphasis in angle modulated Systems
As described, with FM reception, noise contributes more to the high frequency portions
of the spectrum than to the lower frequency portions. The higher frequency portions
therefore tend to have a lower Signal-to-Noise Ratio than the lower frequency portions.
The noise contribution of the high frequency region can be reduced by transmitting the
highs at increased relative levels and then reducing the level by the same amount at the
receiver. This boosting of the highs at the transmitter is known as Pre-emphasis and
the reduction of the highs at the receiver is called De-emphasis.
For realistic reproduction, the amount of de-emphasis at the receiver must equal the
pre-emphasis at the transmitter. Simple networks are utilized to achieve this. The
networks are typically a single RC filter stage, and are characterised by the time
constant of the filter section
In a modulator the audio modulating signal is boosted with Pre-emphasis prior to
modulation. In the receiver, De-emphasis is used after demodulation to recover a flat
audio frequency response. This results in a much improved Signal-to-Noise Ratio for
any given FM transmission system. This gives an overall baseband frequency response
that is flat, while improving the signal to noise ratio at the receiver output.
52
Modulating
Input signal
vin
Pre-emphasis
filter
mf
FM
trasmitter
s(t)
Trasmission
medium
(channel)
r(t)
FM
receiver
Trasmitter
g*(t)
De-emphasis
filter
m*
Receiver
figure 30
The standard in the USA for FM Radio is
τ
=75 microseconds. Be aware that some
countries have standardized on τ =25 or τ =50 microseconds and International
Satellites use what is called the J-17 standard as well as others.
C
Bode plot Pre-enphasis
Log H p ( f )
R1
R2
Pre-enphasis filter
Hp( f ) = K
1 + j ( f / f1 )
1 + j( f / f 2 )
f1 =
1
2πτ 1
Log H p ( f )
=
1
2τR1C
Log(f)
R + R2
1
f2 =
= 1
2πτ 2 2τR1 R2C
Bode plot De-enphasis
R1
C
De-enphasis filter
Log(f)
f1
Hp( f ) =
1
1 + j ( f / f1 )
f1 =
1
2πτ 1
=
f2
1
2τR1C
figure 31
53
6.4.1 De-Emphasis response table
--
75 MICROSECOND RESPONSE TABLE for broadcasting FM
FREQUENCY
UNLIMITED
75uS
26 dB
75uS (roofed)
26 dB
25uS (roofed)
50 Hz
100 Hz
500 Hz
1 KHz
2 KHz
3 KHz
4 KHz
5 KHz
6 KHz
7 KHz
8 KHz
9 KHz
10 KHz
11 KHz
12 KHz
13 KHz
14 KHz
15 KHz
16 KHz
17 KHz
18 KHz
19 KHz
20 KHz
100 KHz
1 MHz
-0.00 dB
-0.01 dB
-0.23 dB
-0.87 dB
-2.76 dB
-4.77 dB
-6.58 dB
-8.16 dB
-9.54 dB
-10.75 dB
-11.82 dB
-12.78 dB
-13.66 dB
-14.45 dB
-15.18 dB
-15.86 dB
-16.49 dB
-17.07 dB
-17.62 dB
-18.14 dB
-18.63 dB
-19.09 dB
-19.53 dB
-33.47 dB
-53.47 dB
-0.00 dB
-0.01 dB
-0.23 dB
-0.87 dB
-2.75 dB
-4.75 dB
-6.55 dB
-8.11 dB
-9.46 dB
-10.64 dB
-11.68 dB
-12.60 dB
-13.43 dB
-14.17 dB
-14.85 dB
-15.47 dB
-16.04 dB
-16.56 dB
-17.05 dB
-17.50 dB
-17.91 dB
-18.30 dB
-18.66 dB
-25.27 dB
-25.97 dB
-0.00 dB
-0.00 dB
-0.03 dB
-0.11 dB
-0.41 dB
-0.87 dB
-1.44 dB
-2.08 dB
-2.75 dB
-3.43 dB
-4.10 dB
-4.75 dB
-5.37 dB
-5.97 dB
-6.54 dB
-7.09 dB
-7.61 dB
-8.10 dB
-8.58 dB
-8.95 dB
-9.45 dB
-9.86 dB
-10.26 dB
-21.85 dB
-25.95 dB
table 2
--
J-17 RESPONSE TABLE for Satellite
FREQUENCY
J-17
1.00
50.00
200.00
400.00
800.00
1.42
2.00
4.00
6.40
8.00
10.00
100.00
+9.38
+9.32
+8.68
+7.10
+3.72
+0.00
-2.40
-6.28
-7.89
-8.37
-8.70
-9.38
Hz
Hz
Hz
Hz
Hz
KHz
KHz
KHz
KHz
KHz
KHz
KHz
table 3
Note that all the losses shown on the De-emphasis tables would become gains for the
Pre-emphasis network within any FM modulator
54
6.4.2 Why use “Roofed” Pre-Enhasis
The higher audio frequencies are boosted in the pre-emphasis network. Out-of-band RF
signals entering with the audio program would also be boosted if they were not limited.
Observe that an unlimited 75 microsecond pre-emphasis network would boost a 1 MHz
spurious signal by 53.47 dB while the 26 dB "Roofed" 75 microsecond pre-emphasis
network would only boost the spurious signal by 25.97 dB. Higher spurious signals
would be boosted without limit in an unlimited pre-emphasis network while the "roofed"
pre-emphasis network would limit at 26 dB.
6.5 Frequency division multiplexing
Frequency-Division multiplexing (FDM) is a technique for transmitting multiple
messages simultaneously over a wideband channel by first modulating the message
signals on to several subcarriers and forming a composite baseband signal that consists
of the sum of these modulated subcarriers.
This composite signal may then be modulated onto the main carrier as shown in figure
below
m1(t)
Subcarrier modulator
fSC1
Ssc1(t)
m2(t)
Subcarrier modulator
fSC2
Ssc1(t)
Σ
m3(t)
Subcarrier modulator
fSCN
SscN(t)
mb(t)
Transmitter
s(t)=FDM
fC
Composite baseband modulating
signal
Transmitter
figure 32
55
Any type of modulation, such as AM, DSB, SSB, PM, FM, and so on, can be used. The
types of modulation used on the subcarriers, as well as the type of modulation used on
the main carrier, may be different.
However, as shown in figure below the composite signal spectrum must consists of
modulated signal that do not have overlapping spectra; otherwise, crosstalk will occur
between the message signals at the receiver output.
The composite baseband signal then modulates a main transmitter to produce the FDM
signal that is transmitted over the wideband channel.
Mb( f )
0
fSC1
fSC2
fSC3
fSCN
BSC1
BSC2
BSC3
BSC
f (Hz)
B
figure 33
The received FDM signal, is first demodulated to reproduce the composite baseband
signal that is passed through filters to separate the individual modulated subcarriers.
Then the subcarriers are demodulated to reproduce the message signals m1(t), m2(t),
and so on.
56
Composite
baseband signal
Badnpass filter
fSC1
Badnpass filter
fSC2
s(t)=FDM Main
receiver
Badnpass filter
fSCN
Ssc1(t)
Demodulator
fSC1
Ssc2(t)
Demodulator
fSC2
Ssc3(t)
Demodulator
fSCN
m1(t)
m2(t)
mN(t)
Receiver
figure 34
7 OUTPUT SIGNAL-TO NOISE RATIOS FOR ANALOG
SYSTEMS
For systems with additive noise channels the input to the receiver is
r (t ) = s (t ) + n(t )
eq 118
for bandpass communication systems having a transmission bandwidth of BT
{
}
{
}
{
}
{
r (t ) = Re g s (t )e j (ωct +θc ) + Re g n (t )e j (ωct +θc ) = Re [g s (t ) + g n (t )]e j (ωct +θc )
}
eq 119
or
r (t ) = Re gT (t )e j (ωct +θc )
eq 120
where
57
g T (t ) = g s (t ) + g n (t ) =
= [xs (t ) + xn (t )] + j[ y s (t ) + y n (t )] =
eq 121
= xT (t ) + jyT (t ) =
= RT (t )e jθT
RT (t ) = g s (t ) + g n (t )
eq 122
gT(t) denotes the total (i.e. composite) complex envelope at the receiver input; it
consists of the complex envelope of the signal plus complex envelope of the noise.
7.1 Comparison with Baseband Systems
The noise performance of various types of bandpass systems is examined by evaluating
the signal-to-noise power ratio at the receiver output, (S/N)out, when a modulated signal
plus noise is present at the receiver input. We would like to see if (S/N)out is larger for an
AM system or an FM system. To compare these SNRs, the power of the modulated
signals at the inputs of the receivers is set to the same value and the PSD of the input
noise is N0/2. (that is , the input noise is white with a spectral level set to N0/2).
To compare the output signal to noise ratio (S/N)out for various bandpass
systems we need a common measurement criterion for the receiver input. For analog
systems, the criterion is the received signal power Ps, divided by the amount of the
power in the white noise that is contained in a bandwidth equal to the message
(modulating) bandwidth B of the baseband signal. This is equivalent to the (S/N)out of a
baseband transmission system, as illustrated in figure below.
n(t)
PN=N0/2
s(t)
PN=2BxN0/2= N0B
Σ
(S/N)in
Lowpass filter
Bandwidth =B
2B= bandwidth of modulated
s(t) signal
r(t)=s(t)+n(t)
(S / N )in = (S / N )baseband
{
r (t ) = Re g T (t )e j (ωct +θc )
Receiver
=
Ps
N0 B
}
figure 35 : Baseband system
where:
58
P
⎛S⎞
= s
⎜ ⎟
⎝ N ⎠baseband N 0 B
eq 123
We can compare the performance of different modulated systems by evaluating (S/N)out
P
for each system as a function of (S / N )baseband = s , where Ps, is the power of AM or FM
N0 B
signal at the receiver input, B is chosen to be the bandwidth of the baseband
(modulating) signal where the same baseband modulating signal is used for all cases
so that the same basis of comparison will be realized.
7.2 AM Systems with Product Detection
Figure Below illustrates the receiver for an AM system with coherent detection
(correlator receiver).
{
r (t ) = s (t ) + n(t ) = Re gT (t )e j (ω c t +θ c )
}
Product detector
(S / N )in = (S / N )baseband
Lowpass filter
Bandwidth =B
IF filter
r(t) = Modulated signal
plus noise in
m * (t ) = Re{gT (t )}
(S / N )out
2 cos(ωct + θ c )
figure 36 : Coherent receiver
it can be shown that
(S / N )out
(S / N )baseband
=
m *2
1 + m *2
eq 124
for 100% sine-wave modulation, m *2 = 1 / 2 therefore
59
(S / N )out
(S / N )baseband
1
1
= 2 =
1 3
1+
2
eq 125
This illustrates that AM system is worse than a baseband system that uses the same
amount of signal power, because of the additional power in the discrete AM carrier that
does not contribute to the information ability of the signal but permits AM receivers to
use economical envelope detectors
7.3 SSB systems
it can be shown that
(S / N )out
(S / N )baseband
=1
eq 126
7.4 PM systems
The modulation on a PM signal is recovered by a receiver that uses a (coherent) phase
detector.
{
r (t ) = s (t ) + n(t ) = Re gT (t )e j (ω c t +θ c )
IF filter
}
Detector
(PM or FM)
⎫
⎧
⎪r0 (t ) = ∠g T (t ) for PM ⎪
⎪
⎪
⎬
⎨
⎪
⎪
d
⎪r0 (t ) = [∠g T (t )] for FM ⎪
dt
⎭
⎩
m * (t ) = Re{gT (t )}
Lowpass filter
Bandwidth =B
(S / N )out
Modulated signal
plus noise in
figure 37 : Receiver for angle-modulated-signal
The PM signal has a complex envelope of
60
g s (t ) = Ac e jθ s ( t )
eq 127
where
θ s (t ) = D p m(t )
eq 128
the complex envelope of the complex signal plus noise at the detector inputs is
gT (t ) = gT (t ) e jθ ( t ) = [g s (t ) + g n (t )] = Ac e jθ s (t ) + Rn (t )e jθ n (t )
eq 129
Imaginary
g n (t ) = Rn (t )e jθ n (t )
g s (t ) = Ac e jθ s (t )
θT
θs
Rn sin(θ n − θ s )
Rn
θn
AC
Real
figure 38 : vector diagram for angle modulation (S/N)in>1
it can be shown that
(S / N )out
(S / N )baseband
⎛m⎞
=β ⎜ ⎟
⎜V ⎟
⎝ p⎠
2
2
p
eq 130
where:
βp is the PM modulation index and Vp is the peak value of m(t).
61
This equation shows that the improvement of a PM system over a baseband signalling
system depends on amount of phase deviation that is used; the larger the phase
deviation, the better the signal-to-noise-ratio.
It seems to indicate that we can make the improvement as large as we wish simply by
increasing βp. This depends on the types of circuits used. If the peak phase deviation
exceed π radians, special “phase unwrapping” techniques have to be used in some
circuits to obtain the true value (as compared to the relative value) of the phase output.
Thus the maximum value of
β p m(t )
Vp
= D p m(t ) might be taken to be π. For sinusoidal
2
⎡ β pm ⎤
π2
2
≅ 6.9 dB over
modulation, this would provide an improvement of ⎢
⎥ = Dp m =
2
⎣⎢ V p ⎦⎥
baseband signaling.
[
]
It is emphasized that the results obtained previously for (S/N)out are valid only when the
input signal is above the threshold [i.e. when (S/N)in>1]
7.5 FM Systems
The procedure that we will use to evaluate the output SNR for FM systems is essentially
the same as that used for PM systems, except that the output for the FM detector is
proportional to dθ(t)/dt, whereas the output of the PM detector is proportional to θ(t).
assuming that (S/N)in>1 then we can find
(S / N )out
(S / N )baseband
⎛m⎞
= 3β ⎜ ⎟
⎜V ⎟
⎝ p⎠
2
2
f
eq 131
2
⎛m⎞
1
for the case of sinusoidal modulation ⎜ ⎟ = we have
⎜V ⎟
2
⎝ p⎠
(S / N )out = 3 β 2
(S / N )baseband 2 f
At first glance, these results seem to indicate that the performance of FM systems can
be increased without limit simply by increasing the FM index βf. However, as βf is
increased, the transmission bandwidth increases, and consequently, (S/N)in decreases.
These equations for (S/N)out are valid only when (S/N)in >>1 (i.e. when the input signal
power is above the threshold), so (S/N)out does not increase to an excessively large
value simply by increasing the FM index βf. Figure below, by dashed line, show a plot of
the preceding equation.
62
figure 39 : noise performance of an FM discriminator for a sinusoidal modulated FM signal plus Gaussian noise (no
deemphasis)
A generalized expression to describe S/N near the threshold, for the case of sinusoidal
modulation is plotted by the solid line.
Figure illustrates that the FM noise performance can be substantially better than
baseband performance, particularly when βf increases.
7.6 FM Systems with Threshold Extension
A PLL FM detector could be used to extend the threshold below that provided by an
FM discriminator. However, when the input SNR is Large, all the FM receiving
techniques provide the same performance.
An FM receiver with feedback (FMFB) is shown below.
e * (t )
e(t )
vin (t )
IF Filter
FM
Discriminator
( S / N ) in
FM Signal in
Demodulated
output
m * (t ) = Re{gT (t )}
( S / N ) out
v0 (t )
VCO
figure 40
63
the FMFB receiver provides threshold extension by lowering the modulation index
for the FM signal that is applied to the discriminator input. That is, the modulation
index of e*(t) is smaller than that for vin(t) (that in a normal case would have been
applied to the discriminator input).
the FM signal at the receiver input is
vin (t ) = Ac cos[ωc t + θ i (t )]
eq 132
where
t
θ i (t ) = ∫ D f m(σ )dσ
eq 133
−∞
the output of the VCO is
v0 (t ) = A0 cos[ω0t + θ 0 (t )]
eq 134
where
t
θ 0 (t ) = ∫ Dv m * (σ )dσ
eq 135
−∞
With these representations for vin(t) e v0(t), the output of multiplier (mixer) is:
e(t ) = A0 Ac cos[ωc t + θ i (t )]cos[ω0 t + θ 0 (t )] =
=
1
1
A0 Ac cos[(ωc − ω 0 )t + (θ i (t ) − θ 0 (t ) )] + A0 Ac cos[(ωc + ω0 )t + (θ i (t ) + θ 0 (t ) )]
2
2
eq 136
If the IF filter is tuned to pass the band of frequencies centered about f IF ≡ f c − f 0 , the
IF filter output is
e * (t ) =
1
1
A0 Ac cos[(ωc − ω 0 )t + (θ i (t ) − θ 0 (t ) )] = A0 Ac cos[ω IF t + (θ i (t ) − θ 0 (t ) )]
2
2
eq 137
or
64
e * (t ) =
t
⎡
⎤
1
A0 Ac cos ⎢ωif t + ∫ D f m(σ ) − Dv m * (σ ) dσ ⎥
2
−∞
⎣
⎦
[
]
eq 138
the FM discriminator output is proportional to the derivative of the phase deviation
⎧t
⎫
d ⎨ ∫ D f m(σ ) − Dv m * (σ ) dσ ⎬
K ⎩−∞
⎭
m * (t ) =
dt
2π
[
]
eq 139
Evaluating the derivative and solving the resulting equation for m*(t), we obtain
[
]
K
K
K
D f m(t ) − Dv m * (t ) =
D f m(t ) −
Dv m * (t )
2π
2π
2π
K
K
m * (t ) +
Dv m * (t ) =
D f m(t )
2π
2π
K
D f m(t )
KD f m(t )
K
K
⎡
⎤
m * (t ) ⎢1 +
Dv ⎥ =
D f m(t ) ⇒ m * (t ) = 2π
=
K
⎡
⎤ [2π + KDv ]
⎣ 2π ⎦ 2π
⎢⎣1 + 2π Dv ⎥⎦
m * (t ) =
⎛ KD f ⎞
⎟⎟m(t )
m * (t ) = ⎜⎜
⎝ 2π + KDv ⎠
eq 140
eq 141
Substituting this expression for m*(t) we get
e * (t ) =
=
t
⎡
⎡
⎛ KD f
1
A0 Ac cos ⎢ω IF t + ∫ ⎢ D f m(σ ) − Dv ⎜⎜
2
⎝ 2π + KDv
−∞⎣
⎣⎢
⎤ ⎤
⎞
⎟⎟m(σ )⎥ dσ ⎥
⎠
⎦ ⎦⎥
t
⎡
⎡ 2πD f m(σ ) + KDv m(σ ) − Dv KD f m(σ ) ⎤ ⎤
1
A0 Ac cos ⎢ω IF t + ∫ ⎢
⎥ dσ ⎥
2
2π + KDv
⎦ ⎦
−∞⎣
⎣
eq 142
⎡
⎤
⎛
⎞
⎜
⎟t
⎢
⎥
1
1
⎟ D m(σ )dσ ⎥
= A0 Ac cos ⎢ω IF t + ⎜
⎜ ⎛ k ⎞ ⎟∫ f
2
⎢
⎥
⎟ Dv ⎟ −∞
⎜1+ ⎜
⎢
⎥
⎝ ⎝ 2π ⎠ ⎠
⎣
⎦
65
This demonstrates that the modulation index of e*(t) (i.e of the signal in input to the
⎛
⎞
1
⎟⎟ of the modulation index of vin(t).
discriminator), is exactly ⎜⎜
⎝ 1 + (k / 2π )Dv ⎠
Since β f = D f Am
1
ωm
, the lower the modulation index Df the lower the β, then once,
the lower will be the needed
(S / N )out
(S / N )baseband
=
3 2
βf .
2
The threshold extension provided by the FMFB receiver is on the order of 5 dB,
whereas that of PLL receiver is on the order of 3 dB (when both are compared with the
threshold of an FM discriminator). Although this is not a fantastic improvement, it can
be quite significant for systems that operate near the threshold, such as satellite
communication systems. A System that uses a threshold extension receiver instead of a
conventional receiver may be much less expensive than the system that requires a
double-sized antenna to provide the 3-dB signal gain.
7.7 FM System with De-emphasis
The noise performance of the FM system can be improved by preemphasizing the
higher frequencies of the modulation signal at the transmitter input and deemphasizing
the output of the receiver. This improvement occurs because the PSD of the noise at
the output of the FM detector has a parabolic shape as a function of the frequency.
The improvement when a sinusoidal test tone is transmitted over this FM system is
(S / N )out
(S / N )baseband
=
1 2⎛ B ⎞
βf ⎜ ⎟
2 ⎜⎝ f1 ⎟⎠
eq 143
of course, each of these results is valid only when the FM signal at the receiver input is
above the threshold.
66
figure 41
8 COMPARISON OF ANALOG SIGNALING SYSTEMS
Table below compares the analog systems that were analyzed in the previous sections.
It has been seen that the non linear modulation systems (FM and PM) provide
significant improvement in the noise performance, provided that the input signal is
above the threshold. Of course, the improvement in the noise performance is obtained
at the expense of having to use a wider transmission bandwidth.
If the input SNR is very low, the linear systems outperform (AM)are better than non
linear systems.
SSB is best in terms of a small bandwidth, and it has one of the best noise
characteristics at low input SNR.
The selection of a particular system depends on the transmission bandwidth that is
allowed and the available receiver input SNR. For the non linear systems a bandwidth
spreading ratio of BT/B=12 is chosen for systems comparisons. This corresponds to a
βf=5 for FM systems cited in the figure below and corresponds to commercial FM
broadcasting.
67
Of course, when operating above the threshold, all the non linear modulation systems
have better SNR performance than the linear modulation systems, because the non
linear systems have larger transmission bandwidths.
8.1 Ideal systems performance
What is the best noise performance that is theoretically possible? How can wide
transmission bandwidth be used to gain improved noise performance? The answer is
given by Shannon’s channel capacity theorem.
The ideal system is defined as one that does not lose channel capacity in the detection
process.
Cin = Cout
eq 144
where Cin is the bandpass channel capacity and Cout is the channel capacity after
detection.
The equation for channel capacity is
S⎞
⎛
C = B log 2 ⎜1 + ⎟
⎝ N⎠
eq 145
using this equation in the preceding equation we get:
⎡ ⎛S⎞ ⎤
⎡ ⎛S⎞ ⎤
BT log 2 ⎢1 + ⎜ ⎟ ⎥ = B log 2 ⎢1 + ⎜ ⎟ ⎥
⎣ ⎝ N ⎠ out ⎦
⎣ ⎝ N ⎠in ⎦
eq 146
where BT is the transmission bandwidth of the bandpass signal at the receiver input
and B is the bandwidth of the baseband signal at the receiver output. Solving for
(S/N)out , we get
⎡ ⎛S⎞ ⎤
⎢1 + ⎜ ⎟ ⎥
⎣ ⎝ N ⎠ in ⎦
⎛S⎞
⎜ ⎟
⎝ N ⎠ out
BT
⎡ ⎛S⎞ ⎤
= ⎢1 + ⎜ ⎟ ⎥
⎣ ⎝ N ⎠ out ⎦
B
⇒
⎡ ⎛S⎞ ⎤
⎢1 + ⎜ ⎟ ⎥
⎣ ⎝ N ⎠ in ⎦
BT
B
⎛S⎞
= 1+ ⎜ ⎟
⎝ N ⎠ out
eq 147
BT
⎡ ⎛S ⎞ ⎤B
= ⎢1 + ⎜ ⎟ ⎥ − 1
⎣ ⎝ N ⎠in ⎦
eq 148
but
68
⎛ P
P
⎛S⎞
⎜ ⎟ = s = ⎜⎜ s
⎝ N ⎠in N 0 BT ⎝ N 0 B
⎞⎛ B
⎟⎜
⎟⎜ BT
⎠⎝
⎞ ⎛ B
⎟⎟ = ⎜⎜
⎠ ⎝ BT
⎞⎛ S ⎞
⎟⎟⎜ ⎟
⎠⎝ N ⎠baseband
eq 149
thus equation (S/N)out becomes
⎡ ⎛ B
⎛S⎞
⎜ ⎟ = ⎢1 + ⎜⎜
⎝ N ⎠ out ⎣ ⎝ BT
BT
⎤B
⎞⎛ S ⎞
⎟⎟⎜ ⎟
⎥ −1
⎠⎝ N ⎠baseband ⎦
eq 150
equation above, which describes the ideal system performance, is plotted in figure
below for the case of BT/B=12. As expected, none of the practical signalling systems
equals the performance of the ideal system. However, some of the non linear systems
(near the threshold) approach the performance of the ideal systems.
figure 42
69
9 BINARY MODULATED BANDPASS SIGNALING
For digital modulated signals, the modulating signal m(t) is a digital signal given by the
binary or multilevel line codes. The most common binary bandpass signalling
techniques are illustrated as follows:
•
On-off keing (OOK) also called Amplitude Shift Keying (ASK), which consists
of keying (switching) a carrier sinusoid on and off with a unipolar binary signal.
Morse code radio transmission is an example of this technique.
figure 43
•
Binary phase-shift keying (BPSK), which consists of shifting the phase of
sinusoidal carrier 0° or 180° with a unipolar binary signal. BPSK is equivalent to
PM signalling with a digital waveform.
figure 44
70
•
Frequency shift keying (FSK) which consists of shifting the frequency of
sinusoidal carrier from a mark frequency (corresponding, for example, to sending
a binary 1) to a space frequency (corresponding to sending a binary 0) according
to the baseband digital signal. FSK is identical to modulating an FM carrier with a
binary digital signal
figure 45
9.1 Binary Phase-Shift Keying (BPSK)
9.1.1 BPSK Generation
A PSK bandpass modulated signal is generally represented by
{
}
{
}
{
}
s (t ) = Re g (t )e jωct = Re Ac e jθ (t ) e jωct = Re Ac e j [θ (t )+ωct ] = Ac cos[ωc t + θ (t )] =
[
= Ac cos ωc t + D p m(t )
]
eq 151
Where
θ (t ) = D p m(t )
eq 152
In BPSK m(t) is a polar baseband data signal. For convenience, let m(t) have a peak
values of ±1 and a rectangular pulse shape.
We now show that BPSK is also a form of AM-type signalling, in fact expanding the
preceding equation we get
cos(a + b) = cos a cos b − sin a sin b
eq 153
71
s (t ) = Ac cos(ωc t ) cos(D p m(t ) ) − Ac sin (ωc t )sin (D p m(t ) )
[
]
[
eq 154
]
s (t ) = {Ac cos D p m(t ) }cos(ωc t ) − {Ac sin D p m(t ) }sin (ωc t )
eq 155
From equation above we can see that it corresponds to a quadrature modulation
scheme.
Accos[Dpm(t)]
cosωct
+
s(t)
sinωct
Acsin[Dpm(t)]
-
figure 46
Now recalling that m(t)= ±1 and that cos(x) and sin(x) are even and odd functions of
x we get:
cos[Dp ⋅ (+ 1)] = cos[Dp ⋅ (− 1)] = cos[Dp ]
sin[Dp ⋅ (+ 1)] = − sin[Dp ⋅ (− 1)]
eq 156
we see that the representation of BPSK signal reduces to:
s (t ) = Ac cos(ω c t )cos(D p ) − Ac sin (ω c t )sin (D p )⋅ m(t ) =
[
]
[
]
= Ac cos(D p ) cos(ω c t ) − Ac sin (D p ) m(t ) sin (ω c t )
Pilot Carrier Term,
m(t) is not present
eq 157
Data Term: m(t) is
present
72
The level of the pilot carrier term is set by the value of the peak phase deviation
constant, ∆θ=Dp.
For digital angle-modulated signals, the digital modulation index h is defined by
h=
2 ∆ϑ
π
=
2D p
eq 158
π
where 2∆θ =2Dp is the maximum peak-to-peak phase deviation (radians) during the
time required to send one symbol, Ts.
h
2∆θ=2Dp
2
1
2π
π
For binary signaling, the symbol time is equal to the bit time (Ts=Tb).
The level of the pilot carrier term is set by the value of the peak deviation, which is
∆θ=Dp for m(t)=±1. The value of m is determined by the input data bit stream converted
in NRZ for example.
If Dp is small, the pilot carrier term has a relatively large amplitude compared to the
data term; consequently, there is a very little power in the data term (which contains
the source information). To maximize the signaling efficiency (so that there is a low
probability of error), the power in the data term needs to be maximized. This is
accomplished by letting ∆θ=Dp=π/2 radians, which corresponds to a digital modulation
index of h=1.
For this optimum case of h=1, the BPSK signal becomes
s (t ) = − Ac m(t ) sin ωc t
eq 159
73
The baseband complex envelope for this BPSK signalling is:
g (t ) = jAc m(t )
Imaginary
eq 160
g1(t)
Real
g2(t)
Therefore the modulated signal is
[
]
[
]
s (t ) = Re g (t )e jωct = Re jAc m(t )e jωct = Re[ jAc m(t ) cos ω c t − Ac m(t ) sin ω c t ]
eq 161
= − Ac m(t ) sin ω c t
s1 (t ) = − Ac sin ωc t
m(t ) = +1
s 2 (t ) = + Ac sin ω c t
m(t ) = −1
To simplify the explanation, suppose now to 90° rotate all constellation then we can
obtain the simulation like as obtained by using WINIQ software as shown below.
This means that
g (t ) = Ac m(t )
eq 162
Consequently
[
]
[
]
s (t ) = Re g (t )e jωct = Re Ac m(t )e jωct = Re[Ac m(t ) cos ωc t + jAc m(t ) sin ω c t ]
= + Ac m(t ) cos ω c t
eq 163
In figure below are reported the phase i(t)=±1 and quadrature q(t)=0 components of the
baseband modulating signal g(t) plus the constellation diagram.
g1(t)
g2(t)
74
g1(t)
figure 47:
left i(t)=±1 and q(t)=0,
g2(t)
right constellation diagram of baseband i(t) ,q(t) signal
When the modulating wave shape is rectangular and the symbol 0,1 are equally
probable, the Power Spectral Density (PSD) for the baseband complex envelope is
⎛ sin π f Tb ⎞
⎟⎟
Pg ( f ) = A T ⎜⎜
⎝ π f Tb ⎠
2
2
c b
eq 164
The resulting FFT of the bandpass digital signals s(t) can be obtained by WienerKhintchine theorem:
[
]
A 2Tb
1
PSD[ s (t )] = Pg ( f − f c ) + Pg ( f + f c ) =
4
4
=
{
⎧⎪⎡ sin (π ( f − f )T ) ⎤ 2 ⎡ sin (π ( f + f )T ) ⎤ 2 ⎫⎪
c
b
c
b
⎨⎢
⎥ +⎢
⎥ ⎬=
⎪⎩⎣ π ( f − f c )Tb ⎦ ⎣ π ( f + f c )Tb ⎦ ⎪⎭
A 2Tb
[sin c(π ( f − f c )Tb )]2 + [sin c(π ( f + f c )Tb )] 2
4
A2T b
Pg ( f − f c )
4
}
A 2T b
Pg ( f + f c )
4
figure 48
75
Considering the positive frequency only, we can have the FFT reported on figure below:
figure 49
To have an easier BPSK model, we can eliminate the minus sign by a 90° rotation of all
signals s(t):
s (t ) = − Ac m(t ) sin(ω c t −
π
2
) = − Ac m(t )[− cos ω c t ] = Ac m(t ) cos ω c t
eq 165
The symbols, s1(t) and s2(t) representing the ones and zeros respectively, are then,
s1 (t ) = + Ac cos ω c t
when m = +1
s 2 (t ) = − Ac cos ω c t
when m = −1
Using the duplication formula
1 + cos 2 x
2
1
cos
2x
−
sin 2 x =
2
cos 2 x =
the energy transmitted during one bit period Tb =
eq 166
2π
ωb
is :
76
2π
⎡
⎤
ωb
⎥
1 − cos(2 ωc t )
1
2
2
2
2
2 ⎢ Tb
Eb =ˆ ∫ s(t ) dt = ∫ Ac sen (ωc t ) dt =Ac ∫
dt =Ac ⎢ − ∫ cos(2 ωc t ) dt ⎥ =
2
0
0
0
⎢2 2 0
⎥
⎣
⎦
⎡ ⎛
⎤
2π ⎞
2π
⎟⎟
sen⎜⎜ 2 ωc
⎢
⎥
ωb
ωb ⎠ ⎥ Ac2
⎝
2 Tb
2 1 ⎡ sen(2 ωc t ) ⎤
2 Tb
2 1 ⎢
−0 =
− Ac ⎢
− Ac
Ac
T
⎥ = Ac
⎥ 2 b
2
2 ⎣ 2ωc ⎦ 0
2
2⎢
2ωc
⎢
⎥
⎣⎢
⎦⎥
Tb
Tb
where s(t ) = Ac sen(ωc t ) ,
Tb
Tb =
2π
ωb
,
ωc = nωb with n = 1,2,3,4.......
eq 167
Therefore the carrier power, C, during a bit period Tb is:
C=
Eb Ac2
=
2
Tb
[W ]
eq 168
The value AC of the carrier is given by:
Ac =
2 Eb
Tb
[V]
eq 169
Substituting this value of Ac into equation of s(t) we get:
s1 (t ) = Ac m(t ) cos ω c t = + Eb
2
cos ωc t
Tb
when m = +1
s 2 (t ) = Ac m(t ) cos ω c t = − Eb
2
cos ω c t
Tb
when m = −1
eq 170
This form of BPSK is referred to as phase-reversal keying since the two carrier signals
representing the logic ones and zeros are exactly 180° out of the phase i.e. the phase
modulation index h=1. A more general form of BPSK occurs when the phase difference
between the two signals is other than 180°. This creates a residual carrier term that
allows carrier tracking by a phase-lock loop (PLL). Unless stated otherwise, BPSK will
refer to 180° mode.
77
A method of generating BPSK is shown in figure below. A bit sequence represented by
±Ac is applied to a balanced modulator, resulting in an output of ±Accos(ωct) which is a
BPSK.
±Accos (ωct)
BPSK signal s(t)
±A c
cos ωct
figure 50: BPSK modulator
9.1.2 BPSK Detection by a Correlation Receiver
When binary PSK modulation is used at the transmission end, then a receiver
employing coherent demodulation must be employed since the information is
contained in the carrier phase.
A correlation receiver performs coherent demodulation. Correlation, C(t), of two
signals, r(t) and s(t), over a period, T, is defined mathematically as:
t
C (t ) = ∫ r (t ) s (t )dt
0<t <T
eq 171
0
Correlation is implemented in hardware by a multiplier and an integrator, as shown in
figure below:
Low-pass Filter
t
∫ s(t )r (t )dt
0
s(t)
r(t)
figure 51:hardware implementation of correlation
78
A BPSK correlation receiver is shown in figure below, with each block of hardware
labeled with its functional purpose.
Receiver
Bit synchronizer
em(t)
Low-pass Filter
Or Matched
Filter
a(t )
t
∫ r (t )s(t )dt
Sam
ple &
Hold
Z
Threshold
device
S/H
0
si(t)=
BPSK
Output of the
receiver and
input to the bit
synchronizer
2
cos ωc t
Tb
Output of the bit
synchronizer
figure 52
The correlation receiver is so called because it correlates the received signal, composed
of signal plus noise, with a replica of the signal. For the correlation to be achieved, it is
necessary for the receiver to be phase locked to the carrier as discussed earlier.
The purpose of the correlation receiver is to reduce the received symbol to a single
point or statistic that will be used by the decision device to determine which symbol has
been transmitted. In practice, the single point is a fixed voltage obtained by a S/H
device. The decision device is a voltage comparator that is set such that if the voltage
point is above a certain level, the comparator indicates a one is received; if the voltage
is below this level, a received zero is indicated, the case for no noise will be treated first.
Functionally and conceptually, the correlation receiver is composed of the receiver and
bit synchronizer.
The correlation receiver and the matched filter are equivalent. Specifically, the integrator
and the S/H, at t=Tb, are equivalent to a matched filter, sampled at the output.
Since there is no discrete carrier term in the ideal BPSK signal, a PLL may be used to
extract the carrier reference only if a low level pilot carrier is transmitted together with
the BPSK signal otherwise is needed a coherent detection.
However, the 180° phase ambiguity must be resolved, this can be accomplished by
using differential coding at the transmitter input and differential decoding at the
receiver output.
79
9.1.2.1 No Noise
An exact replica of the carrier multiplies the received symbol, and the output of the
multiplier is applied to an integrator. The output of the multiplier is given by:
em (t ) = ± Eb
2
2
cos ω c t ×
cos ωc t =
Tb
Tb
2 ⎡1 1
2
2 ⎡1 + cos 2ω c t ⎤
⎤
= ± Eb cos 2 ω c t = ± Eb
= ± Eb
+ cos 2ωc t ⎥
⎢
⎥
⎢
2
Tb
Tb ⎣
Tb ⎣ 2 2
⎦
⎦
eq 172
The output of the multiplier, em(t), is applied to integrator. The integrator will integrate
the double frequency term over an integer number of cycles therefore deleting this term.
In practice, a low pass filter follows the integrator to ensure that this term is deleted from
the output. The output a(t), is:
a(t = Tb ) = Eb
t
a (t ) = ± Eb
2 ⎡1 1
1
⎤
+ cos 2ω c t ⎥ dt = ± Eb t
∫
⎢
Tb 0 ⎣ 2 2
Tb
⎦
eq 173
t=Tb
This is the output of the correlator is either a positive- or negative-going ramp function
(triangular function).
The S/H device is usually set to sample the ramp whenever it reaches a maximum
value, which ideally occurs whenever t=Tb. the upper limit of the integrator is also set to
Tb. For the no noise case, the output of the integrator a t=Tb is:
T
2 b ⎡1 1
1
⎤
a (t = Tb ) = ± Eb
+ cos 2ω c t ⎥ dt = ± Eb Tb = ± Eb
∫
⎢
Tb 0 ⎣ 2 2
Tb
⎦
eq 174
The S/H device is clocked to sample the output of the integrator whenever the maximum
voltage is expected. For this case, the S/H samples at t=Tb and the output voltage
± Eb is applied to the threshold device, which normally triggers out a crisp waveform
representing a one if the voltage is greater than zero or a zero if the voltage is less than
zero.
9.1.3 With Noise
The case when the received signal is contaminated with additive white Gaussian
Noise (AWGN) is now considered. Let the white noise have a power spectral density
(PSD) given by N0/2. The received modulated baseband signal in input to the
correlator receiver is now given by
80
s (t ) = ± Eb
2
cos ωc t + n(t )
Tb
eq 175
Where n(t) is white Gaussian noise.
The output of the integrator at t=Tb due to the signal part of s(t) will be the same as
before, ±a. For the low-noise case, the output of the integrator might look similar to the
ramp shown in figure below on the left; and for the high-noise case, the ramp on the
right figure is indicative about what the output might look like.
t
T
t
T
figure 53: Integrator output of a correlation receiver: (left) low noise, and (right) high noise.
Let the baseband sampled voltage outgoing by the integrator at t=T, can be
represented by z, then
z = ± Eb + N
eq 176
It can be shown that N is a Gaussian random variable with zero mean µ and variance
σ2 given by:
σ 2 = N0 / 2
eq 177
Therefore, the output random variable voltage, z, outgoing from the integrator is also
a Gaussian random variable. Then z will have a variance of N0/2 and a mean of
a = ± Eb , depending upon which symbol has been received.
Letting
a = Eb
eq 178
81
The conditional probability density function for z, gives an information about the
correspondence of symbol with ±a. Precisely it gives an indication if a one or a zero
has been transmitted:
p( z | + a) =
p( z | −a) =
1
2πσ 2
1
2πσ 2
e
e
1 ⎛ z − Eb
− ⎜
2 ⎜⎝ σ
⎞
⎟
⎟
⎠
2
1 ⎛ z + Eb
− ⎜
2 ⎜⎝ σ
⎞
⎟
⎟
⎠
2
eq 179
eq 180
Maximum value for p(z|a) function, is reached when z=a.
The plot for these two functions is shown in figure below, this figure shows that the
sampled output voltage z will fall somewhere along the x axis. Points ±a represents the
more density probability places for z
max p(z | -a)
max p(z | +a)
-a
+a
Figure 54: Conditional probability density functions, gives if a “one” or a “zero” has been transmitted
The baseband signal constellation for a BPSK is shown below, we can observe the
jitter around ±a points due to the noise presence.
φ(t)
-a
+a
figure 55: BPSK signal constellation
82
9.2 Maximum Likelihood Detection
At the end of each symbol period when the integrator output voltage is sampled, the
receiver must decide which symbol was sent based on the sampled voltage z. For
maximum likelihood detection, conceptually, the statistic z is substituted into
conditional probability density function already seen, and the function with the largest
value indicates which symbol have the maximum possibility to have been transmitted.
The test is implemented by forming a ratio between two densities, such as:
1
p ( z | + a ) p ( z | + Eb )
=
=
λ=
p ( z | − a ) p ( z | − Eb )
2πσ
2
1
2πσ 2
e
e
1 ⎛ z − Eb
− ⎜
2 ⎜⎝ σ
1 ⎛ z + Eb
− ⎜
2 ⎜⎝ σ
⎞
⎟
⎟
⎠
⎞
⎟
⎟
⎠
2
=
2
1
2πσ 2
e
⎡ ⎛ z+ E
b
⎢ 1⎜
⎢ 2⎜ σ
⎣⎢ ⎝
2
⎞ 1 ⎛ z − Eb
⎟ − ⎜
⎟ 2⎜ σ
⎠
⎝
⎞
⎟
⎟
⎠
2⎤
⎥
⎥
⎦⎥
eq 181
Assuming each symbol is equally likely and the cost of all errors is the same, the
received point z is substituted as Gaussian random variable. Therefore a value for
λ>1, choose the symbol corresponding to +a;
λ<1, choose the symbol corresponding to -a.
Fundamentally, this test computes the value for each conditional probability density
function at instant and selects the density with the largest value in that time instant.
9.3 Bit Errors
A bit error is made if a zero is transmitted and the sampled voltage, z, falls above zero.
The probability which this error can happen is the area (i.e. the integral) beneath the
Gaussian density function curve, with mean –a. The integral of the probability density
function is made starting the integration, from zero toward infinity and is given by
p(z | -a)
p(z | +a)
-a
0
+a
figure 56
83
∞
∞
P (a | − a) = ∫ P ( z | − a )dz = ∫
0
0
1
2πσ 2
e
1 ⎡ z −( − a ) ⎤
− ⎢
2 ⎣ σ ⎥⎦
2
dz =
∞
1
∫e
2πσ 2
1 ⎡ z −( − a ) ⎤
− ⎢
2 ⎣ σ ⎥⎦
2
eq 182
0
calling
x=
z+a
dz = σ dx
then
σ
eq 183
Therefore when z=0 then x=a/σ and when z=∞
P(a | −a) =
1
2πσ 2
∞
∫e
−
1 2
(x)
2
∞
1
dz =
2πσ 2
0
∫e
−
1 2
(x)
2
σ dx =
a /σ
then x=∞
1
2π
∞
∫e
−
1 2
(x)
2
dx = Q(a / σ )
eq 184
a /σ
By the symmetry, a bit error is made if a one is transmitted and the sampled voltage, Z,
falls under zero. The probability of this occurrences is the area beneath the Gaussian
curve, with mean +a, from zero to -infinity, the probability of mistaking –a for +a is
P(−a | a) =
x=
z−a
1
2πσ 2
then
σ
P(−a | a) =
1
2πσ 2
−∞ − 1 ⎡ z −(+ a ) ⎤
2 ⎢⎣ σ ⎥⎦
∫e
2
dz
eq 185
0
dz = σ dx
0
∫e
−
1 2
(x)
2
−∞
dz =
eq 186
1
2πσ 2
−a /σ
∫
−∞
e
−
1 2
(x)
2
σ dx =
1
2π
−a /σ
∫
e
−
1 2
(x)
2
dx = Q(a / σ ) eq 187
−∞
Considering that P(a)=P(-a)=1/2 then the total error probability is, for the Bayes
theorem:
1
1
Pe = P(a | − a) P(− a) + P(− a | a) P(a) = P (a | −a) + P(− a | a)
2
2
eq 188
1
1
Pe = Q(a / σ ) + Q(a / σ ) = Q(a / σ )
2
2
eq 189
Since
a = Eb
⎛
⎜
⎛ Eb ⎞
⎜
⎟
Pe = Q
= Q⎜
⎜
⎜ σ ⎟
⎝
⎠
⎜
⎝
then
⎞
⎟
⎛
Eb ⎟
E ⎞
= Q⎜⎜ 2 b ⎟⎟
⎟
N0 ⎠
N0
⎝
⎟
2 ⎠
eq 190
84
9.3.1 Q-Function reminder
We say that X is a normal or gaussian variable with mean µ =X and variance σ 2 if its
conditional probability density function is:
− ( x − µ )2
1
f x (x | µ ) =
2πσ
2σ 2
e
2
eq 191
One example for Gaussian probability Density function is plotted below:
Probability Density
f(X)
0.004
0.0035
0.003
f(x)
0.0025
0.002
0.0015
0.001
0.0005
0
-250
-200
-150
-100
-50
0
50
100
150
200
250
x
figure 57: Probability density for a Gaussian random variable
The curve is symmetric around the parameter µ and the relative probability
distribution function referred to an interval within -∞ to x is given by
Fx ( x ) =
x
x
∫ f ( y )dy = ∫
x
−∞
−∞
1
2πσ 2
Using the substitution: z =
x
F ( x) =
∫
−∞
1
2πσ 2
e
dy =
2σ
e
2
x
dy =
∫
−∞
y−µ
σ
z=
− ( y − µ )2
2σ 2
− ( y − µ )2
∫
−∞
2πσ 2
e
1 ⎡ y−µ ⎤
− ⎢
2 ⎣ σ ⎥⎦
2
dy
eq 192
then y = σ z + µ ⇒ dy = σ dz consequently
x−µ
σ
1
1
2πσ 2
e
−z2
2
σ dz =
z
∫
−∞
1
e
2π
−z2
2
⎛x−µ⎞
dz = Q( z ) = Q⎜
⎟ eq 193
⎝ σ ⎠
85
The resulting function is that more often tabulated
Q(z ) =
z
∫
−∞
1
e
2π
− z2
2
dz
eq 194
One example of cumulative distribution function F(X) relative to a Gaussian density
function f(x), is plotted below
Distribution F(X)
F(X)
1.2
1
F(X)
0.8
0.6
0.4
0.2
0
-250
-200
-150
-100
-50
0
50
100
150
200
250
X
figure 58: cumulative distribution of a Gaussian density
The constant 2πσ 2 is a normalization factor which maintain the area under the F(x)
unitary within the interval -∞, +∞
When µ=0 then the Q function is defined as:
Q( Z ) = Q(a / σ ) =
1
2π
∞
∫σe
−
y2
2
dy
where σ 2 = variance of density function
eq 195
a/
i.e. the probability value F(x) computed within an interval starting from a/σ to +∞
That is, for a Gaussian distribution with mean equal to zero and variance σ2=1, Q(a/σ)
i.e. Q(a), is the area beneath the tail of the curve from a to +∞.
86
9.3.2 Bit Error Probability in terms of Eb and N0
Because white noise (AWGN) is presented, it can be shown that the variance of the
noise is given by
σ2 =
•
N0
2
eq 196
N0 = one-sided power spectral density (PSD) of the white noise going into the
IF bandwidth measured in [W/Hz].
Calling:
•
Eb= bit energy [J]
Eb is a variable that occurs in the theoretical analysis of digital systems, but it is
equivalent to the carrier power, C, at the receiver that is measured or determined by
link analysis ad is a function of antenna gain, path loss distance. transmitted power, and
losses.
Eb = CTb =
C
Rb
eq 197
Where:
•
•
•
Tb = bit period = 1/Rb where Rb = bit rate [bit/s]
C = carrier power at the receiver [W]
BIF= bandwidth of the IF [Hz]
The noise power within the IF bandwidth is
N p = N 0 BIF
eq 198
These parameters can be related as follows:
E R
E R
C
= b b = b b
N p N 0 BIF N 0 BIF
eq 199
The greater the Rb, the greater the C/Np needed at the receiver side, whereas the
greater the bandwidth B, the lower will be the S/N ratio required.
87
C/Np is the carrier-to-noise ratio in the IF, which is determined by link analysis, the
BER may be predicted based on this engineering parameter.
Consequently :
Eb
C BIF
=
N 0 N p Rb
eq 200
Under the ideal condition and NRZ data format, the assumption is that BIF ≅ Rb ( this is
usually not the case unless raised cosine filtering is used);
In fact using a RRC filter the since for a BPSK the Symbol rate D is equal to the bit
rate Rb, then we can write:
B=
D
Rb
(r + 1) =
(r + 1) ≈ Rb
2
2
when
r →1
eq 201
then the remaining relationship is
Eb
C
≅
N0 N p
eq 202
Then using the above relationship, the error probability Pe (BER) may be written as
⎛
⎜
⎛ Eb ⎞
⎜
⎟
= Q⎜
Pe = Q
⎜ σ ⎟
⎜
⎝
⎠
⎜
⎝
Eb
N0
2
⎞
⎟
⎛
⎞
⎛
⎞
⎟ = Q⎜ 2 Eb ⎟ ≅ Q⎜ 2 C ⎟
⎜
⎜
⎟
N 0 ⎟⎠
N p ⎟⎠
⎝
⎝
⎟
⎠
eq 203
This is an important equation that relates the BER to the carrier-to-noise ratio, (C/Np)
in the IF bandwidth, which is determined by link analysis.
88
10 Differential Phase-Shift Keying (DPSK)
Phase-shift-keyed signals cannot be detected incoherently. However, a partially
coherent detection technique can be used to extract the phase reference for the
present signalling interval. This is provided by a delayed version of the signal occurred
during the previous signalling interval. This is illustrated below where differential
coding is provided by (one-bit) delay and the multiplier. If a BPSK signal (no noise)
were applied to the receiver input, the output of the Sample-and-Hold circuit, says, r0(t0),
would be positive (binary 1) if the present data bit and the previous data bit were of the
same sense; while r0(t0) would be negative (binary 0) if the two data bits were different.
Consequently, if the data on the BPSK signal are differentially encoded, the decoded
data sequence will be recovered at the output of the receiver. This technique consisting
of transmitting a differentially encoded BPSK signal is known as DPSK.
In practise, DPSK is often used instead of BPSK, because the DPSK receiver does not
require a carrier synchronizer circuit. An example is the Bell212 A modem (1200 bits/s)
DPSK
in
Bandpass filter
Low-pass Filter
integrator
H(f) BT
-fc
S&H
Threshold
r0(t0) device
t0
Binary
output
∫ (..)dt
+fc
t 0 −T
f
One-bit
Delay, Tb
r0(t0),Bit
sync
From bit sync
i it
figure 59 : (partially Coherent detection of DPSK)
The BER of an optimum DPSK receiver is:
⎛ Eb ⎞
1 −⎜⎜ N ⎟⎟
Pe = e ⎝ 0 ⎠
2
eq 204
89
10.1 Differential coding
When serial data are passed through many circuits along a communication channel, the
waveform is often unintentionally inverted (i.e. data complemented). This result can
occur in a twisted-pair transmission line channel just by switching the two leads at a
connection point where a polar line code is used. (note that such switching would non
affect the data on a bipolar signal). To ameliorate the problem, Differential Coding is
often employed. The encoded differential data are generated by
en = d n ⊕ en −1
eq 205
Modulo 2 adder
(EX-OR)
dn
en
Data
in
en-1
Line
Encoder
circuit
Channel
Line
Decoder
circuit
One-bit
Delay, Tb
Modulo 2 adder
(EX-OR)
dn
en
Data
out
One-bit
Delay, Tb
Differential Encoder
en-1
Differential Decoder
figure 60 : differential coding system
The received encoded data are decoded by:
d n = en ⊕ en−1
eq 206
where ⊕ is a modulo 2 adder or an exclusive-OR gate (XOR) operation.
Each digit in the encoded sequence is obtained by comparing the present input bit with
the past encoded bit. A binary 1 is encoded if the present input bit and the past encoded
bit are of opposite state, and a binary 0 is encoded if the state are the same (XOR
operation)
Differential encoding present a great advantage when the waveform is passed through
thousand of circuits in a communication system and the positive sense of the output is
lost or changes occasionally as the network changes.
90
11 FREQUENCY SHIFT KEYING (FSK)
The FSK signal can be characterized as one of two different types, depending on the
used to generate it.
11.1 Discontinuous FSK
One type is generated by switching the transmitter output line between two deferent
oscillators.
This type generates an output waveform that is discontinuous at the switching times, it
is called discontinuous phase FSK, because θ(t) is discontinuous at the switching
times. It can be represented by:
⎧ A cos[ω1t + θ1 ] when binary 1 is sent ⎫
s (t ) = Ac cos[ω c t + θ (t )] = ⎨ c
⎬
⎩ Ac cos[ω 2 t + θ 2 ] when binary 0 is sent ⎭
eq 207
And where θ1 and θ1 are the start-up phases of the two oscillators.
Oscillator
Freq=f1
Electronic
switch
Discontinuous
FSK output
Oscillator
Freq=f2
Control line
Bynary data input
m(t)
figure 61
91
11.2 Continuous FSK
The continuous FSK signal is generated by feeding the data signal into a frequency
modulator.
Frequency
modulator
(carrier freq.=fc)
Bynary data input
m(t)
Continuous
FSK output
figure 62
The FSK signal is represented by:
t
⎡
⎤
s (t ) = Ac cos[ω c t + θ (t )] = Ac cos ⎢ω c t + D f ∫ m(λ )dλ ⎥ = Re g (t )e jωct
−∞
⎣
⎦
[
]
eq 208
Where m(t) is a baseband digital modulating signal.
Although m(t) is discontinuous at the switching time, the phase function θ(t) is
proportional to the integral of m(t).
Using the digital modulation index h=2*∆f/ fb then we can rewrite the equation above:
t
⎡
⎤
s (t ) = Ac cos[ω c t + θ (t )] = Ac cos ⎢2πf c t + 2π h ∫ m(λ )dλ ⎥ = Re g (t )e jωct
−∞
⎣
⎦
[
]
If the serial data input waveform is binary, such as polar baseband signal, m(t)=±1, the
resulting FSK signal is called a binary FSK (BFSK) signal.
t
In this case the overall phase 2πf c t + 2π h ∫ m(λ )dλ will be like as
−∞
t
t
−∞
−∞
y = 2πf c t + 2π h ∫ m(λ )dλ = 2πf c t + 2π h ∫ 1dλ = 2πf c t + 2π ht = 2π ( f c + h)t
eq 209
Which is the equation of rect line where the angular coefficient is 2π ( f c + h)
Of course, a multilevel input signal would produce a multilevel FSK signal.
In general, the spectra of FSK signals are difficult to evaluate since the complex
envelope g(t), is a non linear function of m(t).
The approximate transmission bandwidth BT for FSK signal is given by Carson’s rule:
92
⎡ ∆f
⎤
BT = 2( β + 1) B = 2 ⎢ + 1⎥ B = 2∆f + 2 B
B
⎣
⎦
eq 210
Where B is the bandwidth of the signal (e.g. square wave) modulation waveform.
If the Bandwidth B is equal to the Bit Rate R i.e. B=R, then BT became:
⎡ ∆f
⎤
BT = 2( β + 1) B = 2⎢ + 1⎥ B = 2∆f + 2 B = 2∆f + 2 R = 2(∆f + R )
⎣B
⎦
eq 211
Using a raised-cosine-rolloff premodulation filter and since in a binary signaling D=R
then the transmission bandwidth of the FSK signal became:
BT = 2∆f + 2 B = 2∆f + 2
D(1 + r )
R (1 + r )
= 2∆f + 2
= 2∆f + R (1 + r )
2
2
eq 212
11.3 FSK detection
FSk can be detected by using either a frequency (noncoherent) detector or two product
detectors (coherent detection). In order to obtain the lowest BER when the FSK signal is
corrupted by AWGN, coherent detection with matched filter processing and threshold
device (comparator) is required.
Low-pass
filter
cos(ω1t)
Binary out
FSK in
∑
cos(ω2t)
Low-pass
filter
figure 63: coherent (synchronous) detection
93
FSK in
Frequency
detector
Binary out
figure 64: Noncoherent detection
94
12 MULTILEVEL MODULATED BANDPASS SIGNALING
With multilevel signalling, digital inputs with more than two levels are allowed on the
transmitter input. This technique is illustrated in figure below, which show how multilevel
signals can be generated from a serial binary input stream by using a digital-to-analog
converter(DAC). For example, suppose that an L=2-bit/symbol DAC is used. Then the
number of levels in the multilevel signal is M=2L.
The symbol rate (baud) of the multilevel signal is D=R/L where R=1/Tb
is the bit rate bits/s.
Binary input
R bits / sec
Digital-to-Analog
converter L bits
M=2L -level
digital signal
Transmitter
Modulated output
D(symbol/sec)=R/L
figure 65: multilevel digital transmission system
12.1 Quadrature Phase-shift Keyng (QPSK) and M-ary Phase-Shift
Keyng (MPSK)
If the transmitter is a PM transmitter with a M=4-level digital modulation signal, M-ary
phase-shift keing (MPSK) is generated at the transmitter output. Assuming
rectangular-shaped data pulses, a plot of the permitted values of the complex envelope,
g(t)=Acejθ(t), would contain four points, one value of g(t) (a complex number in general)
for each of the four multilevel values, which correspond to the four phase θ permitted. A
plot of two possible sets of g(t) is shown in figure below (constellation point).
g(t)
g(t)
Imaginary
(Quadrature)
Imaginary
(Quadrature)
θi
θi
Real
(in Phase)
QPSK
Real
(in Phase)
QPSK
figure 66
95
The signal constellation are essentially the same, except for a shift in the carrier-shiftkeyed (QPSK) signalling. A constellation is an N-dimensional plot for the possible
signal vectors corresponding to the possible diagram signals as reported in figure
below.
figure 67
For instance, suppose that the permitted multilevel values at the DAC are -3,-1,+1,+3 V;
then these multilevel values might correspond to PSK phase of 0°,90°,180°,270°,
respectively.
This example of M-ary PSK where M=4 is called quadrature phase-shift-keyed
(QPSK) signalling.
MPSK can also be generated by using two quadrature carriers modulated by the x and
y components of the complex envelope (instead of using a phase modulator); in that
case,
g (t ) = Ac e jθ (t ) = x(t ) + jy (t )
eq 213
Where the permitted values x and y are
x(t ) = Ac cos θ i
y (t ) = Ac sin θ i
eq 214
and where the permitted phase angles are θI , i=1,2,….,M of the MPSK signal.
96
The output modulated signal v(t)=s(t) is:
{
}
v(t ) = Re g (t )e jωct = Re { g (t ) [ cos ωc t + j sin ωc t ]} = Re {[ x(t ) + jy (t ) ][ cos ωc t + j sin ωc t ]} =
= Re { x(t ) cos ωct + jx(t ) sin ωc t + jy (t ) cos ωc t − y (t ) sin ωc t} =
eq215
= x(t ) cos ωc t − y (t ) sin ωc t
This situation is illustrated in figure below
Baseband processing
Binary
input
R
bits/s
Digital-toanalog
converter
L-bits
Multilevel
digital signal
Signal
processing
L
x(t)
cos(ωct)
QAM
signal out
s(t)
Σ
y(t)
M=2 level
D=R/L
symbols / sec
sin(ωct)
Oscillator
f=fc
-90° phase
shift
figure 68: modulator for generalized signal constellation
g(t)=x(t)+jy(t)
L
M=2 point constellation
D=R/L symbol/sec
Baseband processing
Binary
input
R
bits/s
2-bit
serial-toparallel
converter
d1(t)
R/2 bits/sec
L/2 bit
DAC
x(t)
cos(ωct)
d2(t)
R/2 bits/sec
L/2 bit
DAC
y(t)
Σ
QAM
signal out
s(t)=Re[g(t)ejωt]
sin(ωct)
Multilevel
digital signal
Oscillator
f=fc
-90° phase
shift
figure 69: Modulator for Rectangular Signal Constellation
97
For rectangular-shaped data pulses, the envelope of the QPSK signal is constant.
That is, there is no AM (Amplitude Modulation) on the signal, even during the
transmission times when there is a 180° phase shift, since the data switches value
(say, from +1 to -1) instantaneously.
Phase shift:
180°
0°
-90°
180°
QPSK
figure 70
As an instance by winiq software simulator, generating a random binary input we can
observe the (I,Q) baseband signal diagram and (s(t),ϕ(t)) output modulated signal
diagram.
From (s(t),ϕ(t)) diagram its possible to see that the module of s(t) is constant.
This case is reported as an example in figure below
s(t) with constant amplitude
s(t) phase shift
figure 71
98
The rectangular-shaped data pulse produce a (sinx/x) -type power spectrum for the
QPSK signal that has large undesirable spectral sidelobes.
figure 72
These undesirable sidelobes can be eliminated if the data pulses are filtered by a
pulse shaping filter corresponding for example to a raised cosine rolloff filter.
Unfortunately this produces AM on the resulting QPSK signal, because the filtered data
waveform cannot change instantaneously from one peak to another when 180° phase
transition occur.
On figure below it possible to observe how the spectrum changes, when a raised
cosine rolloff filter is used
figure 73
99
Although filtering solves the problem of poor spectral sidelobes, it creates another one:
AM on the QPSK signal, see figure below:
s(t) with no constant amplitude
s(t) phase shift
figure 74
On figure below are reported the constellation diagram and the vector diagram at the
output of the transmitter. We can observe how shape filtering causes a constellation
point position dispersion around the expected position symbol.
Constellation point
position dispersion
figure 75
Due to this AM, low-efficiency linear (Class A or B) amplifiers, instead of high-efficiency
nonlinear (Class C) amplifiers, are required for amplifying the QPSK signal without
distortion. In portable communication application, these amplifiers increase the battery
capacity requirements by as much as 50%. A possible solution to the dilemma is to use
Offset QPSK (OQPSK) or π/4 QPSK, each of which has a lower amount of AM.
For a QPSK in order to represent the modulated bandpass signal we can use also the
following equation where the square of 2 is used as a normalization factor, and π/4 is an
initial phase shift on both axes:
100
s (t ) = cos[2πf c t + θ (t )] =
π
π
1
1
d I (t ) cos(2πf c t + ) +
d Q (t ) sin( 2πf c t + )
4
4
2
2
Where
d I = d 0 , d 2 , d 4 ......(bit
even)
d Q = d1 , d 3 , d 5 ......(bit
odd )
figure 76
In other word, as we have already seen a QPSK signal can be represented as the
superposition of two BPSK signal with carrier in quadrature. Each signal is
characterized by a 2Tb symbol time, i.e. double time length with respect to original
modulating signal.
101
12.2 OQPSK and π/4 QPSK
Offset Quadrature Phase-Shift keying (OQPSK) is M=4 PSK in which the allowed
data transition times for I and Q components are offset by ½ symbol (i.e. by 1 bit)
interval.
This offset provides an advantage when nonrectangular (i.e. filtered) data pulses are
used, because the offset greatly reduces the AM on the OQPSK signal compared to the
AM on the corresponding QPSK signal. The AM is reduced because a maximum phase
transition of only 90° occurs for OQPSK signalling (as opposed to 180° for QPSK),
since the I and Q data cannot change simultaneously, because the data are offset.
g(t)=x(t)+jy(t)
M=2l point constellation
D=R/l symbol/sec
x(t)
Ts/2
delay
cos(ωct)
Σ
y(t)
QAM
signal out
s(t)=Re[g(t)ejωt]
sin(ωct)
Oscillator
f=fc
-90° phase
shift
figure 77
In mathematical form we have:
M = 2l = 2 2 = 4
eq 216
D = symbol _ rate =
Symbol _ delay =
•
1
BitRate
R
=
=
Ts number _ of _ bit _ per _ symbol l
Ts
2
eq 217
eq 218
in a usual QAM the I and Q component are:
102
n⎞
⎛
x(t ) = ∑ xn hl ⎜ t − ⎟
⎝ D⎠
n
eq 219
n⎞
⎛
y (t ) = ∑ yn hl ⎜ t − ⎟
⎝ D⎠
n
eq 220
where: (xn,yn) denotes one of the permitted (xi,yi) value during the symbol time that is
centred on t=nTs=n/D (s) (it takes Ts (s) to send each symbol), hl(t) is the pulse shape
that is used for each symbol. If the bandwidth of the QAM signal doesn’t need to be
restricted, the pulse shape will be rectangular and of Ts (s) duration.
•
In OQPSK the timing between the x(t) and y(t) components is offset by
Ts/2=(1/2D) (s). that is
n⎞
⎛
x(t ) = ∑ xn hl ⎜ t − ⎟
⎝ D⎠
n
eq 221
n T ⎞
n
1 ⎞
⎛
⎛
y (t ) = ∑ yn hl ⎜ t − − s ⎟ = ∑ yn hl ⎜ t − −
⎟
⎝ D 2⎠ n
⎝ D 2D ⎠
n
eq 222
In Figure Below is reported a comparison between the QPSK and OQPSK (I,Q) signal
QPSK
Shift=0
Tsymbol
O-QPSK
Shift=1/2
Tsymbol
I
Ts
Q
figure 78
103
In the other figure is shown a comparison between QPSK and OQPSK vector
constellation, note that in OQPSK case there is no zero crossing by the modulating
vector.
180°
90°
O-QPSK
QPSK
figure 79
At the output of the QPSK and OQPSK transmitter the modulated signal s(t) could be
as shown in example below:
S(t)
QPSK
Max phase
shift
180°
OQPSK
Max phase
shift
90°
figure 80
104
From mathematical point of view the only difference between QPSK and OQPSK is a
shift/delay of Ts/2 on Q branches, so for OQPSK we can use the representation
reported below:
s (t ) = cos[2πf c t + θ (t )] =
π
π T
1
1
d I (t ) cos(2πf c t + ) +
d Q (t ) sin( 2πf c t + − s ) eq 223
4
4 2
2
2
Where
d I = d 0 , d 2 , d 4 ......(bit
even)
d Q = d1 , d 3 , d 5 ......(bit
odd )
This equation is very similar to that used for QPSK which is reported as a reminder:
s (t ) = cos[2πf c t + θ (t )] =
π
π
1
1
d I (t ) cos(2πf c t + ) +
d Q (t ) sin( 2πf c t + )
4
4
2
2
eq 224
Using rectangular modulating signal, we must observe that there are no difference
between QPSK and OQPSK signal spectrum. This can be explained observing that
while the OQPSK amplitude phase shift is only half with respect to QPSK, the
transitions can occur more frequently (in each period of 2Tb for aQPSK and in each
period of Tb of OQPSK)
Anyway thanks to a lower phase transition OQPSK induces lower AM modulation
amount when the signal is filtered prior to modulation.
Both modulation techniques QPSK and OQPSK, are used in order to reduce BPSK
bandwidth to 1/2, and the staggering doesn’t modify the properties.
figure 81
105
12.3 Quadrature Amplitude Modulation (QAM)
In general, QAM signal constellation is not restricted to having permitted signalling point
only on a unique circle (of radius Ac, as was for the case of MPSK). The general QAM
signal is
s (t ) = x(t ) cos ωc t − y (t ) sin ωc t
eq 225
g (t ) = x(t ) + jy (t ) = R (t )e jϑ ( t )
For example, a popular 16-symbol (M= 16 levels) QAM constellation is shown in figure
below, where the relationship between (Ri,θi) and (xi,yi) can readily be evaluated for
each of the 16 signal values permitted. This type of signaling is used by 2400-bit/s V.22
modem.
figure 82
The spectrum of the output transmitted signal s(t) and the I,Q modulating signal can be
evaluated for a random rectangular binary input signal:
figure 83
106
12.4 PSD for MPSK, QAM, OQPSK, and π/4 QPSK without premodulation filtering
The PSD for MPSK and QAM signals for the case of rectangular bit-shape signaling is
the same of the BPSK, provided that proper frequency scaling is used.
13,5 dB
f(Hz)=R/l=1/Ts
figure 84
The PSD for the complex envelope of MPSK and QAM signals with data modulation of
rectangular bit shape is:
⎛ sin πf lTb ⎞
⎟⎟
Pg ( f ) = K ⎜⎜
⎝ πf lTb ⎠
2
K = ClTb
eq 226
R = 1 / Tb
M = 2l
C=power (watts)
For L=1 we have the BPSK PSD,
QPSK PSD.
L=2 (M=4 symbols) describe QPSK, OQPSK, π/4
107
It is also realized that the PSD for the complex envelope of bandpass signals (i.e.
envelope of the modulated signal), is essentially the same as the PSD for baseband
multilevel signals (i.e. envelope of the modulated signal) when any filtering method is
used.
From figure above, we can see that the null-to-null transmission bandwidth of MPSK
or QAM when rectangular data pulses are used is
BT = 2 R / l = 2(1 / Ts ) = 2 DS
eq 227
Therefore ones BT it is fixed we can observe that an increasing of L has as a
consequence an increasing of bit rate R. In the same way once R is fixed the an
increasing of L produce a decreasing of BT.
The spectral efficiency of MPSK or QAM signaling with rectangular pulses is
η=
⎡ bit/s ⎤
⎢⎣ Hz ⎥⎦
R
R
l
=
=
R
BT 2
2
l
eq 228
As a consequence if:
•
•
•
L=2
L=4
L=8
then
then
then
R=B
R=2B
R=4B
One way to define the transmission bandwidth efficiency for a waveform encoding is the
Out-Of-Band-Power (POB), which is defined as:
−f
POB( f ) =
∫ S( f )
2
−∞
+∞
∞
df + ∫ S ( f ) df
∫ S( f )
−∞
f
2
∞
2
df
=
∫ S( f )
2
∫ S( f )
2
f
∞
df
eq 229
df
0
Where S(f)=PSD (Power Spectral Density).
This method gives the contribution of the PSD, S(f), above a certain frequency, f, when
compared with the total PSD for the signal on entire bandwidth.
If one wanted a 99% power for the signal, which is a common requirement for regulatory
measures, one would find the frequency that gives a POB of 1%.
108
12.5 Spectral efficiency for MPSK, QAM,OQPSK, and π/4 QPSK with
Raised Cosine Filtering
The spectrum shown above was obtained for the case of rectangular symbol pulses
shaping, and the spectral side lobes was terrible. The first side lobe is attenuated only
by ≅ 13.5 dB.
13,5 dB
figure 85
The high side lobes can be eliminated if raised cosine filtering is used (since the
raised cosine filter has an absolutely band limited frequency response).
We should select the 6-dB bandwidth f0 of the raised cosine filter, for the baseband
signal, equal to half of the symbol (baud) rate in order for o avoid ISI. That is
f0 =
1
1R 1 1
=
D=
2
2 l 2 Ts
eq 230
In practise, a square root raised cosine SRRC frequency response characteristic is
often used at the transmitter, along with another SRRC filter at the receiver, in order to
simultaneously prevent ISI on the received filtered pulses and minimize the bit errors
due to channel noise.
However the SRRC filter also introduces AM on the transmitted signal.
If the overall pulse shape satisfies the raised cosine-rolloff filter characteristic, then, the
absolute bandwidth of the M-level modulating baseband signal signal is
109
B=
1
[(1 + r )D] Hz
2
or
eq 231
⎛ 2B ⎞ R
symbol/s
D=⎜
⎟=
⎝1+ r ⎠ l
r is the characteristic of the filter called rolloff factor.
From AM study modulation we know that the transmission bandwidth BT is related to
the modulation bandwidth B by
BT = 2 B
eq 232
so the overall absolute transmission bandwidth of the QAM signal with raised
cosine filtered pulses is:
BT = 2 B = 2
1
[(1 + r )D] = [(1 + r )D] = ⎡⎢(1 + r ) R ⎤⎥ Hz
2
l⎦
⎣
eq 233
R
of rectangular pulse
l
shaping i.e. without SRRC filter). We can see that the greeter the r , the greeter the BT,
when r=1 then we have again the maximum bandwidth such as we used the rectangular
filter shape.
This bandwidth can be compared to a null bandwidth BT = 2
On table below are reported some values of the parameter related to the above
equations supposing a fixed bit-rate R=812 Kbit/s.
Note that when the rolloff factor of the SRRC filter tend to 1 then the bandwidth BT
become the same as found for rectangular filter data pulse shape.
110
figure 86
Transmission Bandwidth Bt as a function of rolloff factor r for SRRC and Rectangular pulse shape
filter
1800.0
l=1-bit
1600.0
1400.0
Bt KHz
1200.0
1000.0
l=2-bit
800.0
l=3-bit
600.0
BT (KHz) SRRC
BT (KHz) rectang
BT (KHz) SRRC
BT (KHz) rectang
BT (KHz) SRRC
BT (KHz) rectang
400.0
200.0
R=812,499 Kbit/s
0.0
0
0.1
0.2
0.4
0.6
0.8
1
Rolloff factor r
figure 87
E:\documenti per
corsi\ELETTRONICA T
111
Transmission Bandwidth Bt as a function of rolloff factor r for SRRC and Rectangular pulse shape
filter
0
0.1
0.2
0.4
0.6
0.8
1
1800.0
1600.0
1400.0
l=1-bit
Bt KHz
1200.0
l=2-bit
1000.0
800.0
l=3-bit
600.0
400.0
200.0
0.0
BT (KHz) SRRC
BT (KHz) rectang
BT (KHz) SRRC
BT (KHz) rectang
BT (KHz) SRRC
BT (KHz) rectang
Bandwidth with SRRC and rectangular pulse filter shape
figure 88
Because
M = 2l
eq 234
which implies
l = Log 2 M =
ln M
ln 2
eq 235
Then the spectral efficiency of QAM-type signaling with raised cosine filtering is
ln M
l
ln M
R
R
η=
=
= ln 2 =
=
1 + r 1 + r (1 + r ) ln 2
BT ⎛ 1 + r ⎞
⎜
⎟R
⎝ l ⎠
bit/s
Hz
eq 236
112
The above equation can be compared with the rectangular data pulse shape filter
efficiency already seen
η=
l
R
R
=
=
BT 2 R 2
l
⎡ bit/s ⎤
⎢⎣ Hz ⎥⎦
eq 237
we can see that ηSRRC is greater than ηrectang if r < 1.
This result is important because tell us how fast we can signaling for a prescribed
bandwidth. The result also holds for MPSK, since it is a special case of QAM.
For example, suppose that we want to signal over a communications satellite that has
an available bandwidth of BT=2.4 MHz.
•
If we used BPSK (M=2) with a r=50% rolloff factor, we could signal at rate of
R = BT ×η = 2.4 × 0.677 = 1.60 Mbit / s
•
eq 238
If we used QPSK (M=4) with a r=25% rolloff factor, we could signal at a rate of
R = BT ×η = 2.4 × 1.6 = 3.84
Mbit / s
eq 239
Table below illustrates the allowable bit rate per hertz of transmission bandwidth for
a QAM signalling
Size of DAC
E:\documenti per
corsi\ELETTRONICA T
Rolloff factor r
Number ofLevels
l bit per symbol
M symbols
1
2
3
4
5
2
4
8
16
32
0
1.00
2.00
3.00
4.00
5.00
0.1
0.91
1.82
2.73
3.64
4.55
0.25
0.80
1.60
2.40
3.20
4.00
0.5
0.67
1.33
2.00
2.67
3.33
0.75
0.57
1.14
1.71
2.29
2.86
1
0.50
1.00
1.50
2.00
2.50
figure 89
113
Spectral efficiency for QAM signaling with Raised Cosine-Rolloff Pulse Shaping filtering
6
efficiency=R/Bt ((bit/s)/Hz))
5
ln M
l
ln M
R
R
=
=
= ln 2 =
η=
1 + r 1 + r (1 + r ) ln 2
BT ⎛ 1 + r ⎞
⎜
⎟R
l
⎝
⎠
bit/s
Hz
4
0
0.1
0.25
0.5
0.75
1
3
2
1
0
1
2
3
4
5
l - bit per symbol
figure 90
In order to conserve more bandwidth, the number of levels M cannot be increased too
much, since for a given peak envelope power (PEP) the spacing between the signal
points on the signal constellation will decrease and noise on the received signal will
cause errors (Noise moves the received signal vector to a new location that might
correspond to a different signal level.) However, we know that R certainly has to be less
than C, the channel capacity, if the errors are to be kept small.
η < η max
eq 240
⎛
⎝
η max = Log 2 ⎜1 +
S⎞
⎟
N⎠
114
24.33
24.23
24.13
24.03
23.93
23.82
23.71
23.60
2.00
23.48
23.36
23.24
23.12
22.99
22.86
22.72
22.58
22.43
22.28
22.12
21.96
21.79
21.61
21.43
21.24
21.04
20.83
20.61
20.37
20.13
19.87
19.59
19.29
18.98
18.63
18.26
17.85
17.40
16.90
16.33
15.68
14.91
13.98
12.79
11.14
8.45
0.00
Spectral efficiency
9.00
6.00
5.00
4.00
150.00
3.00
Spectral efficiency
SNR (lineare)
0.00
SNR (Lineare)
Spectral Efficiency as a function of SNR
300.00
8.00
7.00
250.00
200.00
100.00
1.00
50.00
0.00
SNR (dB)
figure 91
115
As an example related to the effect of rolloff factor value on the constellation dispersion
and on the PSD, we can consider a QPSK modulation at the transmitter output side. Let
us consider two cases: Rectangular filter pulse shaping and SRRC filter pulse
shaping. In this last case are being considered the value of rolloff factor: r = 0.5
QPSK constellation
With rectangular pulse shaping
figure 92
QPSK constellation
With SRRC pulse shaping and
rolloff factor r = 0.5
figure 93
The difference on side lobe decaying its clear !!
116
12.6 Receiver QPSK, MSK and performance
QPSK is a multilevel signalling technique that uses L=4 levels per symbol. Thus, 2 bits
are transmitted during each signalling interval (T seconds). The QPSK signal may be
represented by
s (t ) = (± A)cos(ω c t + θ c ) − (± A)sin(ω c t + θ c )
0<t ≤T
eq 241
Where the (±A) on the cosine carrier is one bit of data and the (±A) factor on the sine
carrier is another bit of data.
The relevant input noise is represented by
n(t ) = x(t ) cos(ω c t + θ n ) − y (t ) sin(ω c t + θ n )
eq 242
Total input power it will be given by adding signal and noise: after the demodulation we
have ±A+x(t) and ±A+y(t) as input to the integrator.
The QPSK signal is equivalent to two BPSK signals-one using a cosine carrier and the
other using a sine carrier. The QPSK signal is detected by using a coherent receiver
shown in figure below:
± A+x(t)
Matched Filter:
integrator
t0
QPSK
signal +
noise
∫ (..)dt
2cos(ωct+θc)
S
&
H
Threshold
device
t0 −T
+90°
phase
shift
Carrier sync f=fc
(form carrier sync
circuits)
Bit sync (from
bit sync circuitry)
Matched Filter:
integrator
-2sin(ωct+θc)
± A+y(t)
Carrier recovery
t0
∫ (..)dt
S
&
H
R/2 bits/sec
Parallel
To serial
converter
Threshold
device
R/2 bits/sec
t0 −T
figure 94 : Coherent/Matched filter detection of QPSK
Because both the upper and lower channels of the receiver are BPSK receivers, the
BER is the same as that for BPSK system. Thus the BER for the QPSK receiver is:
117
Digital
output
⎛
E ⎞
Pe = Q⎜⎜ 2 b ⎟⎟
N0 ⎠
⎝
eq 243
figure 95 : Comparison of the probability of bit error for several digital signaling schemes
Except for the curves describing the non coherent detection cases, all of these results
assume that the optimum filter-the matched filter- is used in the receiver.
Comparing the various bandpass signaling techniques, we see that QPSK and MSK
give the best overall performance in terms of the minimum bandwidth required for a
given signaling rate and one of the smallest Pe for a given Eb/N0. However QPSK is
relatively expensive to implement, since it requires coherent detection.
Channel coding can be used to reduce the Pe below values given above.
The BERs for BPSK and QPSK signaling are identical. But for the same bit rate R, the
bandwidth of the QPSK is exactly one-half the bandwidth of the BPSK, i.e. the same
information but in half bandwidth.
118
When rectangular data pulses is used, the null-to-null transmission bandwidth is:
BT =
2R
l
⇒
BT ( BPSK ) = R
BT (QPSK ) =
1
R
2
eq 244
The spectral efficiency is
l ⋅ BT
R
l
η=
= 2 =
BT
BT
2
⇒
η ( BPSK ) = 1
η (QPSK ) = 2
eq 245
The bandwidth of π/4 QPSK is identical to that for QPSK.
For the same BER, the differentially detected π/4 QPSK requires about 3 dB more
Eb/N0 than that for QPSK, but coherently detected π/4 QPSK has the same BER
performance as QPSK.
The MSK is essentially equivalent to QPSK, except that the data on the x(t) and y(t)
quadrature modulation components are normally offset and their equivalent data pulse
shape is a positive part of a cosine function instead of rectangular pulse (this gives a
PSD for MSK that rolls off faster than that for QPSK). Consequently, because the
MSK and QPSK signal representations and the optimum receiver structures are
identical except for the pulse shape, the probability of bit error for MSK and QPSK is
identical.
119
TYPE OF DIGITAL
SIGNALING
MINIMUM
TRANSMISSION
BANDWIDTH
REQUIRED
ERROR PERFORMANCE
(R is the bit rate)
Baseband Signalling
Unipolar
1
R
2
⎡ Eb ⎤
Q⎢
⎥
⎢⎣ N 0 ⎥⎦
Polar
1
R
2
⎡ E ⎤
Q⎢ 2 b ⎥
⎣⎢ N 0 ⎥⎦
Bipolar
1
R
2
3 ⎡ Eb ⎤
Q⎢ 2
⎥
2 ⎣⎢ N 0 ⎥⎦
Bandpass Signalling
Coherent detection
Non coherent detection
1 −⎜⎜⎝ 2 N 0 ⎟⎟⎠
e
2
OOK (On Off Keing)
R
⎡ Eb ⎤
Q⎢
⎥
⎢⎣ N 0 ⎥⎦
BPSK
R
⎡ E ⎤
Q⎢ 2 b ⎥
⎢⎣ N 0 ⎥⎦
PCM/FM
R
1 −⎜⎜⎝ 2 N0 ⎟⎟⎠
e
2
FSK
2∆f + R
⎛ 1 Eb ⎞
Eb 1
>
N0 4
Requires coherent
detection
⎛ 1 Eb ⎞
where
∆f = f 2 − f1 =frequency
shift
⎡ Eb ⎤
Q⎢
⎥
⎢⎣ N 0 ⎥⎦
⎛ 1 Eb ⎞
1 −⎜⎜⎝ 2 N 0 ⎟⎟⎠
e
2
DPSK
R
Not used in practise
1 −⎜⎜⎝ N 0 ⎟⎟⎠
e
2
QPSK
1
R
2
⎡ E ⎤
Q⎢ 2 b ⎥
⎣⎢ N 0 ⎥⎦
Requires coherent
detection
MSK
1,5 R (null bandwidth )
⎡ E ⎤
Q⎢ 2 b ⎥
⎣⎢ N 0 ⎥⎦
⎛ Eb ⎞
⎛ 1 Eb ⎞
1 −⎜⎜⎝ 2 N 0 ⎟⎟⎠
e
2
120
13 Feher-Patented Quadrature Phase-Shift Keing
13.1 Introduction
The Feher-patented Quadrature-phase-shift Keying, type B (FQPSK-B) modulation
scheme is a proprietary bandwidth-efficient modulation technique invented by Dr.Kamilo
Feher. FQPSK-B is a variant of the cross-correlated FQPSK scheme (originally
referred to as XPSK) which in turn was derived from a previous modulation scheme also
invented by Dr. Feher known as Inter-symbol-interference and Jitter-Free (IJF)
QPSK, which has a 3-dB envelope fluctuation. With FQPSK as well as FQPSK-B,
there is an intentional controlled amount of cross-correlation between the In-phase (Ik)
and Quadrature-phase (Qk) channels which allows for a quasi-constant envelope,
reducing the envelope fluctuation to 0 dB. This cross-correlation was applied to the
IJF-QPSK baseband signals prior to modulation onto In-phase (Ik)
and
Quadrature-phase (Qk) carriers. This transformation was initially implemented by
mapping, in each half symbol, the 16 possible combinations of the (Ik) and (Qk)
baseband waveforms present in the IJF-QPSK onto a new set of 16 waveform
combinations.
Here SI(t) and SQ(t) are the I- and Q-channel baseband signals.
These new waveforms were chosen in such a way that the baseband signals are time
continuous and the envelope is constant.
FQPSK-B improves spectral efficiency over FQPSK because low-pass filtering is
applied to the baseband I- and Q-channel waveforms.
When properly designed and specified, a system using FQPSK-B is interoperable with
other modulation schemes such as OQPSK, GMSK, and MSK.
13.2 Signal model for FQPSK
The FQPSK signal (or XPSK signal) can be realized using either a
half-symbol cross-correlation mapping or a full-symbol mapping. In this section, the
full-symbol cross-correlation mapping is described instead of the half-symbol mapping
because the full-symbol mapping facilitates the interpretation of the FQPSK as a TCM
(Trellis Code Modulation).
The waveform of each baseband signal in a TS symbol interval is chosen from a set of
16 waveforms {si(t) | 0 ≤ i ≤ 15} defined as follows:
Typically
A= 2
Eb
≅ 1/ 2
Tb
eq 246
And:
121
eq 247
122
123
Example of quasi constant envelope modulation si(t) and sQ(t)
124
Note that for any value of A other then unity, s5(t) and s6(t) as well as their negatives,
s13(t) and s14(t), will have a discontinuous slope at their midpoints (i.e., at t = 0),
whereas the remaining 12 waveforms all have a continuous slope throughout their
defining intervals. Also note that all 16 waveforms have zero slope at their end points
and, thus, concatenation of any pair of these will not result in a slope discontinuity.
The wavelets are numbered according to a Trellis mapping rule that determines which
wavelet is transmitted. Specifically, the mapping rule specifies that during the n-th
channel symbol interval, [(n - [1/2])Ts] ≤ t ≤ [(n + [1/2])Ts], the baseband I- and Qchannel waveforms Ik and QK are assigned wavelets sI(t)=si and sQ(t)=sj respectively,
where the indices i and j are given by:
i = I 3 × 2 3 + I 2 × 2 2 + I1 × 21 + I 0 × 2 0
j = Q3 × 2 3 + Q2 × 2 2 + Q1 × 21 + Q0 × 2 0
eq 248
with
I 0 = d Q ,n ⊕ d Q ,n−1
Q0 = d I ,n+1 ⊕ d I ,n1
I1 = d Q ,n−1 ⊕ d Q ,n−2
Q1 = d I ,n ⊕ d I ,n−1 = I 2
I 2 = d I ,n ⊕ d I ,n−1
Q2 = d Q ,n ⊕ d Q ,n−1 = I 0
I 3 = d I ,n
Q3 = d Q ,n
Where d I ,n and d Q ,n ∈ {0,1}
eq 249
are the n-th I- and Q- channel inputs to the modulator
respectively
The particular sI(t) and sQ(t) waveforms chosen for any particular Ts signalling interval
on each channel depend on the most recent data transition on that channel, as well as
the two most recent successive transition on the other channel.
Next, define the following mapping function for the baseband I-channel transmitted
waveform [yI (t)=sI (t) ] in the n-th signalling interval [(n - [1/2])Ts] ≤ t ≤[(n + [1/2])Ts]
in terms of the transition properties of the I and Q data symbol sequences dIn and dQn,
respectively.
125
Making use of the signal properties of eq above, the mapping conditions in (1) through
(4) for the I-channel baseband output can be summarized in a concise form described
by Table 1. A similar construction for the baseband Q-channel transmitted waveform
[yQ(t)=sQ(t-Ts/2) ] in the n-th signalling interval nTs ≤ t ≤ (n + 1)Ts in terms of the
transition properties of the I and Q data symbol sequences, dIn and dQn, respectively,
126
can be obtained analogously to (1) through (4) above. The results can once again be
summarized in the form of a table, as in Table 2.
Tables below specify the details where dIK is the data sequence on the I channel, and
dQK the data sequence for the Q channel.
127
A block diagram of a FQPSK transmitter based on the reformulation by Simon and Yan
is shown in figure below:
figure 96 : The conceptual block diagram of FQPSK(SPSK)
FQPSK-B Transmitter and Receiver schemes are reported below:
I seq. Logic
And switch
si(t)
Ik
cos(ωct+θc)
Digital
source
Encoder
Qin=2
Bin=1/Tb
Qout=4
Bout= Bin /2
Ts=2Tb
+
cos = [π t / 2Ts ]
I and Q
Comb
logic
sin = [π t / 2Ts ]
+
sin (ωct+θc)
Qk
Delay
=Tb
=Ts/2
SFQPSK(t)
Modulated
signal
Q seq. Logic
And switch
sQ(t-T/2)
QPSK Modulator
figure 97 : FQPSK transmitter
128
Ik
Delay
=Tb
=Ts/2
Decision r1
unit
Tb
∫ (.)dt
0
cos(ωct+θc)
Digital
sink
ei
Decoder
mk
I and Q
Decision
logic
r(t)=
SFQPSK(t)
Decision mapping
+ 1 ← r1 > 0
− 1 ← r1 < 0
Received
Modulated
signal
sin (ωct+θc)
Qk
Decision r
2
unit
Tb
∫ (.)dt
0
Correlator
Decision mapping
+ 1 ← r2 > 0
− 1 ← r2 < 0
figure 98: coherent FQPSK receiver
The FQPSK signal obtained by transmitter can be represented by:
S XPSK (t ) = S FQPSK (t ) = sI (t ) sin(2πf c t + θ c ) + sQ (t −
Ts
) cos(2πf c t + θ c )
2
eq 250
Where sI(t) and sQ(t) are the combined cross-correlator output.
These are obtained, as we have seen so far, by cross-correlating (i.e. mapping) the
sequence dI and dQ baseband-data represented by IK and QK
The value of IK and QK depend on the encoder output state k as given by equation
below, and is a function of two consecutive encoder inputs bits as specified in table
below.
Ik = +
Qk = −
2 Es
π⎤
⎡
cos ⎢(2k − 1) ⎥
Ts
4⎦
⎣
2Es
π⎤
⎡
sin ⎢(2k − 1) ⎥
Ts
4⎦
⎣
Encoder
Input
Encoder
Input
Encoder
Output
I logic
Q logic
Ej-1
0
0
1
1
Ej
0
1
0
1
k
0
1
2
3
IK
+1
+1
-1
-1
QK
+1
-1
-1
+1
figure 99
129
As an example for Ik and Qk which in turn are the dI e dQ data flow on I and Q channels,
we have:
I0 =
2 Es
2Es
π⎤
⎡
⎡ π⎤
cos ⎢(0 − 1) ⎥ =
cos ⎢− ⎥ =
4⎦
Ts
Ts
⎣
⎣ 4⎦
2 Es 2
=
Ts 2
Es
= +1
Ts
I1 =
2 Es
2Es
π⎤
⎡ π⎤
⎡
cos ⎢(2 − 1) ⎥ =
cos ⎢
=
4⎦
Ts
Ts
⎣ 4 ⎥⎦
⎣
2Es 2
=
Ts 2
Es
= +1
Ts
I2 =
2 Es
2Es
2Es 2
E
π⎤
⎡ π⎤
⎡
cos ⎢(4 − 1) ⎥ =
cos ⎢3 ⎥ = −
= − s = −1
4⎦
Ts
Ts
Ts 2
Ts
⎣ 4⎦
⎣
I3 =
E
2 Es
2Es
2 Es 2
π⎤
⎡ π⎤
⎡
cos ⎢(6 − 1) ⎥ =
cos ⎢5 ⎥ = −
= − s = −1
Ts
Ts
Ts 2
Ts
4⎦
⎣ 4⎦
⎣
eq 251
Q0 = −
2 Es
2Es
π⎤
⎡
⎡ π⎤
sin ⎢(0 − 1) ⎥ = −
sin ⎢− ⎥ =
4⎦
Ts
Ts
⎣
⎣ 4⎦
2Es 2
=
Ts 2
Q1 = −
2 Es
2Es
π⎤
⎡ π⎤
⎡
sin ⎢(2 − 1) ⎥ = −
sin ⎢
=
4⎦
Ts
Ts
⎣ 4 ⎥⎦
⎣
2 Es 2
E
= − s = −1
Ts 2
Ts
Q2 = −
2 Es
2Es
2Es 2
E
π⎤
⎡ π⎤
⎡
sin ⎢(4 − 1) ⎥ = −
sin ⎢3 ⎥ = −
= − s = −1
4⎦
Ts
Ts
Ts 2
Ts
⎣ 4⎦
⎣
Q3 = −
2 Es
2Es
π⎤
⎡ π⎤
⎡
sin ⎢(6 − 1) ⎥ = −
sin ⎢5 ⎥ =
Ts
Ts
4⎦
⎣ 4⎦
⎣
2 Es 2
=
Ts 2
Es
= +1
Ts
Es
= +1
Ts
eq 252
Consecutive values of Ik and Qk assume A=±1 values, and are then nonlinearity filtered
by the I sequential logic and switch, and by the Q sequential logic and switch
respectively. The switch outputs are defined in table 1 and table 2. Note that the
switch output is determined by three consecutive inputs, and thus has memory.
This is in contrast to OQPSK, which is memory less.
130
13.3 Signal model for FQPSK-B
The FQPSK-B signal obtained by transmitter can be represented by:
T
S XPSK (t ) = S FQPSK − B (t ) = ~
sI (t ) sin(2πf c t + θ c ) + ~
sQ (t − s ) cos(2πf c t + θ c )
2
eq 253
where the filtered signals
t
~
sI (t ) = ∫ s I (t )h(t − τ )dτ
−∞
~
sQ (t ) =
eq 254
t
∫s
Q
(t )h(t − τ )dτ
−∞
are the low pass filtered version of the sI(t) and sQ(t) seen so far in FQPSK form, and
h(t) is the impulse response of the low-pass filter.
The functional block diagram below depicts full-symbol cross-correlation mapping
followed by the transmission filter and an Offset-QPSK (OQPSK) modulator.
sI(t)
SQ(t)
figure 100 : FQPSK-B modulator
Figure below shows the phasor diagrams and the eye diagrams of both FQPSK and
FQPSK-B baseband signals.
131
figure 101: phasor diagrams FQPSK (left) FQPSK-B (right)
figure 102: transmitter eye figure for FQPSK (top) and FQPSK-B (bottom)
132
13.4 Spectral efficiency comparison
Required bit rates in range telemetry are increasing dramatically, resulting in research to
develop modulation techniques that have greater spectral efficiency than 35-year-old
workhorse fo the telemetry industry, NRZ, PCM/FM.
In figure below is presented a comparison between several type of modulation
techniques.
figure 103
133
figure 104
•
•
The 99.99% bandwidths of filtered FQPSK-B are approximately one-half of the
corresponding bandwidth of optimized PCM/FM, even when the signal is non
linearly amplified.
The EB/N0 required for a BER of 1x10-5 for non optimized FQPSK-S is
approximately 12 dB, which is approximately the same as the limiter discriminator
detected PCM/FM
134
14 EFFICIENT MODULATION METHODS STUDY AT NASA/JPL
CCSDS (RF and Modulation) became aware of a new modulation type at its Spring
1997 meeting. Named FQPSK for its inventor, Dr. Kamilo Feher, it was reported to have
a very narrow RF spectrum and only minimal end-to-end system losses. Test data
provided by Dr. Feher showed a spectrum narrower than that of GMSK using a
BTS = 0.50 filter. Sideband attenuations were tabulated for the several modulation types
studied and it was concluded that FQPSK-B could be a very attractive modulation
method.
FQPSK-B, a specific version of FQPSK, was simulated using SPW. Additionally, Mr.
Eugene Law of the Naval Air Warfare Center Weapons Division at Point Mugu obtained
an FQPSK-B modulator-demodulator (modem) for hardware tests. NASA witnessed
these spectrum tests and obtained copies of the spectra. Note: This is the only modulation
type covered in this report for which there are actual hardware verification tests. These tests
confirm the simulation results reported here.
•
•
FQPSK-B modulation is a form of OQPSK modulation in which one of 16
wavelets [waveforms] is selected for transmission on the I-channel and another is
chosen for transmission on the Q-channel.
Wavelet determination depends on the present and previous data bit pair values
for the I and Q channels. There is a ½-symbol-time offset between I and Q
transmissions.
FQPSK-B modulates and filters at baseband. There after, the signal is translated
to an i.f. frequency and then translated again to the transmitted RF frequency.
14.1 FQPSK-B Modulation Bit-Error-Rate (BER)
Simulations of FQPSK-B were conducted at JPL with the assistance of Dr. Feher.
Figure below shows the Bit-Error-Rate (BER) performance. Like MSK and GMSK
modulation, existing transmitting and receiving equipment simulation models were
unsuitable for FQPSK-B. However, BER performance was measured using ESA’s
power amplifier operating in full saturation.
Comparing FQPSK-B to ideal BPSK/NRZ shows that an additional EB / N0 of 1.7 dB is
required to achieve a 1 x 10-3 BER. This is 0.3 dB greater than GMSK with a BTS = 0.5.
Dr. Feher commented that additional system optimization might reduce these losses.
His suggestions included adding hard limiters to the transmitting system and improving
the receiver filter’s phase performance.
Supporting his position, Dr. Feher points to BER measurements made at Point Mugu
using actual hardware. Dr. Feher’s modem, operating with a 1 Watt SSPA in full
saturation, produced a 1 x 10-3 BER at an EB / N0 of 8 dB, about 1.3 dB more than ideal
BPSK/NRZ and 0.1 dB less than GMSK with a BTS = 0.5. Further BER tests will be
required to verify the better EB / N0 performance using a modulator capable of a 60 dB
sideband attenuation.
135
figure 105: FQPSK-B mosulation Bit Error Rate
14.2 FQPSK-B Modulation Spectra
Figure below FQPSK-B spectra obtained by simulations. Spectra are obtained using
ESA’s 10 Watt SSPA operating in full saturation. However, as with the MSK and GMSK
simulations, an ideal modulator and receiver were simulated.
FQPSK-B spectra do not have discrete components, giving it a distinct advantage over
filtered phase modulation schemes. Sideband attenuation does tend to reach a floor at
approximately 75 dB below the peak amplitude where spectral broadening is clearly
evident in Figure below. Unlike most of the phase modulation schemes, spectral
broadening in the vicinity of fC does not occur. Rather, Figure shows the spectrum width
around fC to be significantly narrower than BPSK/NRZ.
FQPSK-B has a very compact, bandwidth-efficient spectrum. Simulations show it to be
slightly better than GMSK reaching a level 50 dB below the peak sideband amplitude at
a bandwidth of 1.7 RB rather than at 1.9 RB for GMSK with a BTS = 0.5. At a sideband
attenuation of 60 dB, FQPSK-B and GMSK are within 0.1 RB of one another.
14.2.1
Hardware Spectrum Measurements
FQPSK-B is the only modulation type in the Phase 3 Efficient Modulation Methods Study
for which there are actual hardware measurements. On 1 July 1997 FQPSK-B hardware
tests were conducted at the Naval Air Warfare Center at Point Mugu. Dr. Feher
contributed a laboratory model of his FQPSK-B modulator. The test configuration
included: a random data generator producing 1 Mb/s, Dr. Feher’s FQPSK-B modulator,
a Hewlett Packard (HP) Model 8780A Vector Signal Generator for QPSK modulation, a
frequency translator, a 1-Watt SSPA, and an HP spectrum analyzer.
136
Tests were run with the SSPA in full saturation at 2.44 GHz and frequency spectra were
plotted by the HP spectrum analyzer. Figure reproduces the HP analyzer’s plot on the
same scale as that used for the Fine Detail spectra shown in Figure. Separate figures
are provided because the spectrum plotted in Figure is virtually indistinguishable from
the FQPSK-B curve in Figure, down to a level 55 dB below the peak sideband
amplitude. Below the -55 dB point, the hardware generated spectrum in Figure
becomes wider than the SPW computed spectrum in Figure. Readers should
understand that no attempt was made to optimize the hardware test configuration at Point
Mugu. The test bed was constructed using hardware elements designed for a variety of
other uses.
These measurements confirm the bandwidth efficiency of FQPSK-B modulation, as
predicted by SPW. Neither a 2 GHz receiver nor an FQPSK-B demodulator-symbol
synchronizer were available to measure Bit-Error-Rate. Therefore, system losses
calculated by SPW could not be confirmed using this test configuration.
Additional hardware tests were conducted using an FQPSK-B modem provided by Dr.
Feher. The test configuration operated at 70 MHZ. This inexpensive commercially
available modem was designed to operate over a more restrictive set of signal levels
than the laboratory modulator described above. It did not provide sideband attenuations
much below 40 dB.
figure 106: fc=±10 Rb
137
figure 107: Broadband spectra (fc=±250 Rb)
14.3 FQPSK-B Modulation Power Containment
FQPSK-B frequency spectrum efficiency is so high that two power containment plots are
required.
First figure is plotted using a 0 - 20 RB scale for consistency with the other modulation
methods.
However, virtually all of the transmitted power is contained in such a small bandwidth
that a second figure is added. Its scale of 0 - 2 RB clearly shows the occupied bandwidth
to be only 0.8 RB. This is significantly better than the 1.0 RB found with GMSK using a
filter bandwidth of BTS = 0.5.
14.4 FQPSK-B Modulation Study Conclusions
Although FQPSK-B modulation was only recently added to the Efficient Modulation
Methods Study, it appears to be one of the most bandwidth-efficient modulation method
considered. Because of its proprietary nature, some of its parameters are not apparent
from published documents. Whether this proprietary nature would serve as an
impediment to universal application by space agencies is also not clear.
What is clear is that FQPSK-B modulation must be seriously considered for high and
very high data rate missions. With RF spectra valued in the Unites States at several
hundred dollars per Hertz, NASA, and probably all space agencies, have a duty to
investigate this modulation type further.
138
figure 108: FQPSK-B Power containment (0-20 Rb)
139
figure 109: FQPSK-B Power containment (0-2 Rb)
15 SUMMARY, CONCLUSIONS, AND RECOMMENDATIONS
The CCSDS - SFCG Efficient Modulation Methods Study measured the RF spectrum’s width
and end-to-end system performance using computer simulations. In compliance with the
SFCG’s request, the conclusions identify those modulation schemes that are the most
bandwidth-efficient and suggest that CCSDS and SFCG Space Agencies adopt
recommendations specifying their use.
15.1.1
SUMMARY
For each modulation method, it reviews end-to-end system losses, examines RF
spectrum bandwidth, and discusses the spectrum improvement factor resulting
from baseband filtering.
15.1.1.1
Summary of Losses
Table below shows system and filtering losses occurring in the end-to-end system for
each modulation type. Column 2 contains losses relative to ideal BPSK/NRZ
modulation. Recall that ideal BPSK/NRZ assumes: perfect data (Pm = Ps = 0.5), an ideal
system (perfect carrier tracking and symbol synchronization), and no filtering
(BT = 4).
140
Filtering losses, inherent in GMSK and FQPSK-B, are included in leftmost column of
Table containing losses relative to ideal BPSK/NRZ.
NOTE: All modulation types exhibit a loss with respect to ideal BPSK/NRZ. To find the
true cost of a modulation method, one should subtract 0.56 dB which is the loss for filtered
BPSK.
Thus, the true loss for GMSK (BTS = 0.5) is about 0.8 dB and FQPSK-B is about 1.1 dB.
Phase 3 studies employed baseband filtering exclusively. A principal objective was the
selection of the proper filter bandwidth. Recall that filter selection criteria required
using a filter producing the narrowest RF spectrum while introducing only
moderate losses.
From Table it is clear that filters having a BTS = 1 often exceeded the allowable loss of
approximately 1 dB. However, filters having a BTS = 2 generally met the 1 dB loss
criterion.
8-PSK was the exception requiring a BTS = 3 filter bandwidth to be acceptable. For the
other modulation types, BER curves showed that there was no significant benefit in
using a BTS = 3 filter bandwidth. Thus, Butterworth and Bessel baseband filters, with a
BTS = 2, were used.
figure 110: System Losses
NOTES:
1. Losses determined at a Bit-Error-Rate of 1 x 10-3 with 0 = 0, Pm = 0.55 (negative numbers indicate a loss).
2. System losses were measured relative to ideal BPSK/NRZ (perfect data, lossless equipment).
3. Filtering Losses include: ISI + Mismatch + Imperfect Carrier Tracking & Symbol Synchronization.
4. BER reached a minimum of 1 x 10-2.
5. Filtering Losses Not Available (N/A) because BER measured with ideal system components.
6. Filter bandwidth BTS = 1 (BTB = 0.5).
7. Filter bandwidth BTS = 0.5 (BTB = 0.25).
141
15.1.1.2
RF Spectrum Efficiency
Another Phase 3 study objective was to determine the RF spectral bandwidth of each
modulation type. This was necessary to rank the several modulation methods with
respect to one-another.
Many Spectrum Managers are concerned principally with occupied bandwidth (i.e., 99%
power containment).
The Efficient Modulation Methods Study was motivated by a desire to pack a substantially
greater number of spacecraft into a given frequency allocation, particularly in the 2 and
8 GHz Category A mission bands. Maximum packing density occurs when spectra from
two spacecraft, operating on adjacent frequencies, just begin to overlap at n dB below
the peak of the data sideband’s spectrum.
This follows from a worst-case assumption that the Earth station’s antenna is bore
sighted on both spacecraft simultaneously. Where spacecraft are not coincidently within
the Earth station antenna’s beamwidth, the interferer’s and victim’s relative signal
strengths will determine the special separation necessary to avoid interference.
Obviously, even as frequency band usage increases, some spatial separation is
expected. This study attempted to determine the value of n.
Views differ regarding the optimal value of n. Some believe that spectra from spacecraft
on adjacent frequencies could be permitted to intersect at a level of 20 dB below the
peak sideband amplitude.
Others believe that the number should be greater or less than 20 dB.
In any event, Category A missions in highly elliptical orbits can undergo signal level
changes of 30 dB or more at the Earth’s surface. Thus, it would seem prudent to prohibit
RF spectra, from spacecraft operating on adjacent frequencies, from intersecting at
levels higher than 50 dB below the peak of the data sideband generated by the
spacecraft having the stronger signal.
To provide maximum flexibility, RF spectrum bandwidths have been tabulated at values
of n from 20 to 60 (dB) below the data sideband’s peak. RF spectrum width increases
as a function of n and each user must select the proper value. A value of n = 50 is
recommended for most applications.
For a specific value of n, one can calculate the improvement in spectral efficiency.
CCSDS concluded that BPSK/NRZ was to be the reference modulation type. A
Spectrum Improvement Factor (SIF) can be calculated by comparing the bandwidth of
unfiltered BPSK/NRZ to the bandwidth of the modulation method under discussion
according to the relationship:
eq 255
Since the bandwidth is a function of n, the SIF will also vary with n. Table below
contains the bandwidths and SIFs at several values of n for all modulation types
covered in this Phase 3 study.
142
Bandwidths for all phase modulation types were evaluated using a Butterworth, BTS = 2
filter.
For symmetrical data, no spikes are present in the spectra of unfiltered BPSK/NRZ. All
measurements in Table were made with respect to a continuous unfiltered BPSK/NRZ
reference spectrum. Conversely, all phase modulation schemes, which employ
baseband filtering, have both continuous and discrete parts to their spectrum.
SIF measurements in Table below were made with respect to the discrete part of the
baseband filtered modulation spectrum. This represents a worst case bandwidth
comparison. Readers should understand that no discrete spectral components exceed
the value of n in any of the SIFs shown in Table. Since SPW’s resolution bandwidth
was set to 1.33 Hz, one can conclude that the SIFs should be close to those obtained
using real hardware viewed on a spectrum analyzer with a 1 Hz resolution.
Preferred modulation types become immediately apparent when SIFs are plotted as a
function of n as in Figure below. Modulation types fall into two distinct groups FQPSK-B
/ GMSK and everything else. Even 8-PSK is not a competitor for those two types. The
message is clear:
If RF bandwidth is important, then the results of this study show that FQPSK-B and GMSK
(BTS = 0.5) are the modulation methods of choice.
figure 111: Bandwidth Efficiencies
143
figure 112 : Spectral efficiency relative to unfiltered BPSK/NRZ
Figure above relates the spectral efficiencies of the several modulation methods investigated in
the Phase 3 Efficient Modulation Methods Study. SIF, as defined in equation above is plotted as
a function of n (number of dB below the peak sideband amplitude). Three classes of bandwidth
efficiency are evident: High (FQPSK-B and GMSK); Medium (8-PSK, QPSK/OQPSK, MSK,
PCM/PM/NRZ, and BPSK/NRZ); and Low (PCM/PM/Bi-φ, BPSK/Bi-φ).
All Phase 3 modulation bandwidth measurements are made using a Butterworth 3RD order
BTS= 2 filter. MSK has no filtering and GMSK curves are labeled with the Gaussian filter’s BTs
factor. FQPSK-B measurements are based on a proprietary filter in FQPSK-B modulation.
15.2 CONCLUSIONS
Conclusions fall into distinct categories relating to filtering methods, losses, modulation
types, and Spectrum Improvement Factors (SIFs). Each conclusion is summarized in the
subsections below.
15.2.1
Filtering Conclusions
Baseband filtering significantly reduces the transmitted RF spectrum’s width. Study
conclusions are:
144
•
•
•
•
•
Filtering of transmitted signals will be required to obtain an acceptably narrow RF
spectrum.
Hardware limitations make post PA filtering impractical at data rates below
about 8 Ms/s.
o Realizable Qs limit the filter’s bandwidth to about 1-2% of the transmitted
frequency.
o Filtering power losses may be unacceptable, even at a 1-2% bandwidth.
o For low data symbol rates, post PA filtering may make turnaround
ranging difficult.
Depending upon its architecture, transponder i.f. filtering may not be practical.
o Q limitations stated above apply if modulation occurs at the transmitting
frequency.
o Filtering at i.f. requires transponders be modified for each mission.
o Filtering at i.f. makes data rate changes difficult.
o For low data symbol rates, i.f. filtering may make turnaround ranging
difficult.
o Filtering within the transponder risks introducing spurious emissions
causing lock-up.
Baseband filtering is the only practical alternative to unacceptable post PA and
i.f. filtering.
o Baseband filtering can be accomplished with a simple, passive low-pass
filter design.
A 3RD order Butterworth filter (BTS = 2) provides the best
performance-simplicity ratio.
o Filtering prior to phase modulation produces undesirable spikes in the RF
spectrum.
Spikes can only be avoided by using a different modulation method
(GMSK, FQPSK).
Both GMSK and FQPSK-B utilize baseband filtering and do not require i.f. nor
post PA filters.
15.2.2
Loss Conclusions
Table above partitions losses into two categories: System (losses relative to ideal
BPSK) and Filtering (ISI and Mismatch). One criterion for the Phase 3 study was that
end-to-end losses should be reasonable. CCSDS determined that approximately 1 dB
was reasonable. The following conclusions regarding losses were reached:
• High system loss (1.5 dB) found for PCM/PM/NRZ, resulted from a 10% data
imbalance.
o When a BTS = 2 Butterworth filter is used, data imbalance should not
exceed 5%.
• 8-PSK modulation exhibits an excessive system loss (3.4 dB).
o Filtering losses decreased for non-constant envelope modulation.
However, spectrum width increased.
Losses were not reduced to an acceptable level.
o High losses make 8-PSK modulation unsuitable for power-limited
Category A missions.
• GMSK (BTS =0.5) also exhibited high (1.4 dB) system losses.
145
•
o Increasing filter bandwidth to BTS = 1 reduced system losses to an
acceptable level.
o Losses were measured with an ideal (lossless) receiver.
FQPSK-B losses were found to be a high 1.7 dB.
o Losses were also measured with an ideal (lossless) receiver.
15.2.3
Modulation Methods Conclusions
Figures above , graphically identify the preferred modulation methods. For the several
modulation methods considered, the following conclusions were reached.
• FQPSK-B provides the narrowest RF spectrum of all modulation methods
studied.
o FQPSK-B should be considered for all high and very high data rate
missions.
Provided that losses are acceptable.
• GMSK, with a filter bandwidth BTS = 0.5, produces virtually equivalent results to
FQPSK-B.
o Further work is required to validate system losses using real hardware.
• 8-PSK, with its high losses, does not appear useful for most Category A
missions.
o Excessive losses and modest performance gains do not provide sufficient
advantages.
• QPSK has comparatively poorer bandwidth efficiency than does FQPSK-B and
GMSK.
o Its common usage may dictate its consideration in some applications.
o Absent spread spectrum, QPSK cannot provide simultaneous telemetry
and ranging.
• OQPSK could not be evaluated properly with the UPM.
o OQPSK should be reserved for applications requiring separate,
independent data channels.
o Orthogonally phased BPSK/NRZ modulators, with a ½ symbol offset
should be used.
• BPSK/NRZ has poor bandwidth efficiency and should not be used if bandwidth is
important.
o Bandwidth efficiency is slightly lower than PCM/PM/NRZ modulation.
o BPSK/NRZ may be an alternative to PCM/PM/NRZ when:
A residual carrier is not required.
The data imbalance is so great that PCM/PM/NRZ would suffer
excessive losses.
• PCM/PM/NRZ has poor bandwidth efficiency, but has best efficiency of residual
carrier types.
o Applications requiring a residual carrier should consider this modulation
method.
o When using PCM/PM/NRZ, care must be taken to ensure proper data
balance.
• MSK modulation is not highly spectrum efficient.
146
•
•
o No specific advantages were found to MSK, save the lack of spectral
spikes.
Bi-φ modulation has very poor RF spectrum efficiency.
o Bi-φ modulation should not be used unless the symbol transition density is
too low.
o This conclusion applies to both PCM/PM/Bi-φ and BPSK/Bi-φ modulations.
Subcarrier modulation tends to waste spectrum and should be avoided
whenever possible.
o When used, the subcarrier frequency-to-data symbol rate ratio should be
low
o CCSDS virtual channels should be used to separate data types.
15.2.4
Spectrum Improvement Conclusions
The following conclusions were reached regarding RF spectrum efficiency improvement:
• Baseband filtering greatly increases the number of spacecraft operating in a
frequency band.
o Spectrum utilization efficiency can increase by a factor from 2 to more
than 100 times.
o The amount of improvement depends upon modulation method and
sideband attenuation.
o This result attains despite non-linear system elements, non-ideal data, and
spectral spikes.
• Modulation method should be selected to maximize the Spectrum Improvement
Factor.
o Modulation schemes with low Spectrum Improvement Factors should be
avoided.
• Modulation method selection should be based on system capabilities, data
rates, and SIFs.
15.3 RECOMMENDATIONS
Based upon the results of the Phase 3 Efficient Modulation Methods Study, the CCSDS
and SFCG are encouraged to create and adopt Recommendations specifying the
preferred modulation methods.
Because space missions have a broad range of objectives, communication
requirements will vary. Some grouping of applications is necessary before assigning a
modulation type.
15.3.1
Mission Classification
One method for grouping applications is by specific attributes. Missions sharing those
attributes are assigned a classification and a modulation method(s) most appropriate to
that group are selected.
Where RF spectrum and modulation types are of paramount concern, the
telemetry data symbol rate appears to be the best discriminator. The following
classifications are recommended:
147
15.3.1.1
Low Data Rate (10 s/s - 20 ks/s)
This class includes low rate scientific missions as well as the Telemetry, Tracking, and
Command (TT&C) services for most missions. Turnaround ranging may be required. If it
is, subcarrier modulation may be appropriate (see CCSDS Recommendation 401
(3.3.4) B-1). If ranging is not required, then any appropriate modulation type should be
acceptable. All mission types operating in the space services can be found in this class.
15.3.1.2
Modest Data Rate (20 ks/s - 200 ks/s)
Most Category A missions fall in this and the following classification. If space agencies
are serious about reducing RF spectrum requirements, they must use appropriate
filtering and modulation techniques for spacecraft in these classes. Typical missions
operate in the SpaceResearch service and include NASA’s ISTP Wind and ESA’s Integral
missions.
The recommended modulation method depends upon whether or not simultaneous
telemetry and turnaround ranging signals are required (see CCSDS Recommendation
401 (3.4.1) B-1). If they are, a residual carrier modulation method is suggested
because users can independently control the division of power between the carrier,
telemetry, and ranging channels.
PCM/PM/NRZ is the most bandwidth-efficient residual carrier modulation method
and is recommended provided that the telemetry data imbalance is less than 5%
during a time interval equal to one time-constant of the Earth station receiver’s
phase-locked-loop.
At low data symbol rates, care must be taken with PCM/PM/NRZ modulation to ensure
that the Earth station’s receiver can distinguish between the RF carrier and the spectral
components of the data sidebands. The spacecraft’s modulation index and the Earth
station receiver’s phaselocked-loop bandwidth should be adjusted to ensure proper
operation.
If simultaneous telemetry and turnaround ranging is required and the data imbalance is
greater than 5%, then Unbalanced QPSK (UQPSK) is the recommended modulation
type. Within limits, telemetry and ranging powers can be set independently. If
simultaneous telemetry and turnaround ranging is not required or where data imbalance
exceeds 5%, BPSK/NRZ is recommended.
15.3.1.3
Medium Data Rate (200 ks/s - 2 Ms/s)
As noted, most Category A scientific missions fall into this and the prior classification.
Generally, such spacecraft operate in the Space Research service allocation. Examples
include NASA’s Polar and ESA’s SOHO missions.
Because many of these missions are collecting scientific data, simultaneous turnaround
ranging is frequently required. In these cases, PCM/PM/NRZ modulation is
recommended, providing the telemetry data symbol imbalance does not exceed 5% in
one time-constant of the Earth station receiver’s phase-locked-loop. If data imbalance
exceeds 5%, then UQPSK can be used.
In this classification, data symbol rates can be as high as 2 Ms/s, so bandwidth
conservation is important. If simultaneous turnaround ranging is not required, then
QPSK modulation is recommended.
148
15.3.1.4
High Data Rate (2 Ms/s - 20 Ms/s)
Typically, missions with data symbol rates in this range operate in the Earth Exploration
Satellite service. Examples include NASA’s Lewis and the Canadian Space Agency’s
(CSA’s) Radarsat projects. In this and the following classification, RF spectrum
limiting becomes imperative.
Decreasing bandwidth utilization by a factor of 10 saves considerably more RF
spectrum when the data symbol rate is 20 Ms/s than in the case when it is 200 ks/s.
Both the CCSDS and SFCG should immediately adopt filtering and modulation
Recommendations for these last two classes.
From Figures above, and Table above, FQPSK-B or GMSK (BTS = 0.5) modulation are
the clear choices if RF spectrum conservation is important. Modulator modifications may
be required to provide turnaround ranging with either of these modulation types and the
ranging signal will have to be sequential, not simultaneous, with the telemetry data.
15.3.1.5
Very High Data Rate (20 Mb/s - and Above)
Missions with data symbol rates in this range operate almost exclusively in the Earth
Exploration Satellite service. Examples include NASA’s Earth Observation Satellite
(EOS) and ESA’s Earth Resources Satellite (ERS-1). Previous comments regarding
bandwidth conservation and modulation methods apply emphatically to this class.
FQPSK-B or GMSK (BTS = 0.5) are the recommended modulation methods.
The CCSDS and SFCG are urged to move with all dispatch to obtain the additional
system performance information for both FQPSK-B and GMSK modulation types. The
authors recommend that tests, using real hardware, be conducted in a carefully
controlled environment to validate these simulations and to measure actual system
performance. Recommendations, consistent with Table below, should be adopted at the
earliest possible opportunity.
figure 113: Recommended Modulation Methods for Category A Missions
149
GLOSSARY
ARX II A Research and Development Earth Station Receiver, (Prototype for DSN Block
V)
BER Bit-Error-Rate
Bi-φ Binary-Phase [Manchester] modulation
BL Receiver phase-locked-loop’s bandwidth, expressed in Hz
BPSK Bi-Phase Shift Keying [modulation method]
BTB Bandwidth • Time Product Based on Bit-Period
BTS Bandwidth • Time Product Based on Symbol-Period
Category A Space Mission whose distance from Earth is less than 2 • 106 km
CCSDS Consultative Committee for Space Data Systems
DSN Deep Space Network
DTTL Digital Transition Tracking Loop
ESA European Space Agency
ESOC ESA Operation Center (Darmstadt, Germany)
ESTEC ESA Technical Center (Noordwijk, The Netherlands)
FQPSK Feher QPSK [modulation method]
GMSK Gaussian Minimum Shift Keying
HP Hewlett Packard
Hz Hertz
k Kilo (1,000)
kb/s Kilo Bits per Second
kHz Kilo Hertz
ks/s Kilo Symbols Per Second
M Mega (1,000,000)
MHZ Mega Hertz
MAP Maximum A Posteriori
MODEM Modulation-Demodulation
MSK Minimum Shift Keying
NRZ Non Return to Zero [format]
OQPSK Offset QPSK [modulation method]
PA Power Amplifier
PCS Personal Communications System
PM Phase Modulation
PSK Phase Shift Keying
PT Total Power [transmitted]
QPSK Quadrature Phase Shift Keying [modulation method]
SAW Surface Acoustic Wave [Filter]
SER Symbol-Error-Rate
SFCG Space Frequency Coordination Group
SPW Cadence Design Systems Inc. Signal Processing Worksystem
SRRC Square Root Raised Cosine [Filter]
SSPA Solid State Power Amplifier
Subpanel 1E CCSDS group concerned with RF and Modulation standards
150
16 8PSK MODULATION (Example implemented in mobile
telephone network)
16.1 Introduction
After GPRS, the next step in improving the GSM system data rate is to change the
signal to a type that has greater bandwidth efficiency, i.e. more bits per second can be
supported per unit bandwidth. This is most economically implemented throughout the
existing GSM infrastructure when the new signal type has identical bandwidth
occupancy characteristics to the original 0.3-GMSK signal.
EDGE is a modulation scheme that is more bandwidth efficient than the Gaussian prefiltered minimum shift keying (GMSK) modulation scheme used in the GSM standard.
The technology defines a new physical layer of an 8-Phase-Shift-Keying modulation
(8PSK), instead of Gaussian-Minimum-Shift Keying (GMSK). 8PSK enables each
pulse to carry 3 bits of information per symbol versus GPRS/GMSK’s 1 bit per symbol
per pulse rate. Thus, it has the potential to increase the data rate of existing GSM
system by a factor of three. For this reason, it requires a hardware upgrade of the RF
part in the base stations and new mobile stations that support EDGE modulation.
A traditional 8PSK system uses raised-cosine filtering to remove Inter-symbol
Interference (ISI). Although ISI is eliminated by using raised-cosine filtering, (270
Ksymbol/s results in a channl bandwidth greater than 200 KHz) the 8PSK signal with
rised-cosine filtering does not fit within 200 KHz of bandwidth.
D( symbols / s ) =
2B
1+ r
for a raised cosine filtering
⇓
2 B = D( symbols / s ) ⋅ (1 + r ) = 270000 *1.22 ≅ 330 KHz
eq 256
where instead
2 B = 200 Khz for GSM e EGPRS
r = rolloff _ factor ≅ 0.22
In order to achieve the desired symbol rate using 200 KHz of bandwidth, a more
severe filtering approach is required.
8PSK-EDGE makes this trade-off, resulting in a conservation of bandwidth versus the
increase of ISI. This also necessitates a more complex design for the receiver.
151
In the EDGE modulation system the serial bit stream is converted into 3 bit words and
mapped to the 8PSK modulation using Gray encoding. The symbol are than rotated by
3π/8 radians to ensure that the envelope of the signals does not go to zero. Next, the
symbols are up-sampled and filtered using Linearized Gussian Filter (similar to, but
different than the method used for GSM). In this manner, the spectrum of 8PSK signal
can be restricted to 200 KHz. Linearized Gussian Filtering allows the 8PSK signal
spectrum to occupy the same bandwidth as a GPRS/GSM signals. It also introduces a
considerable ISI component.
EDGE provides nine different coding schemes and is possible to switch a connection
between different schemes. The choice of the coding scheme is dynamic and depends
on the Carrier to Interference ratio (C/I).
As the signal quality deteriorates, switches to a more robust coding scheme with lower
throughput are done.
User
data MCS1 MCS2 MCS3 MCS4 MCS5 MCS6 MCS7 MCS8 MCS9
Rate
( in Kbps)
1 Timeslot
8.4
11.2
14.8
16.8
22.4
29.6
44.8
54.4
59.2
table 4
In this chapter the focus is on generating the EDGE signal, which unlike GMSK, has a
time-varying envelope which exposes in turns the signal to AM-PM distortion.
For simulations of EDGE I,Q signals we have been using a software program (winiq
downloadable by Internet on www.rohde-schwarz.com )
152
16.2 EDGE signal description: Modulating Symbol Rate and Symbol
Mapping
Coding, modulation, and filtering of EDGE signal, which is 3π/8-shifted 8-PSK, is
shown in figure below.
We assume rectangular-shaped input data pulses.
S
Bit
Input
source
dk=[0,1]
Group
into
3-bit
triplets
GRAY
Code
encoding
Cn
n
= e
j
2πC
IQ
generator
8
n
R
n
Rn
Sn
Cn =[0.1,2,3,4,5,6,7]
e
j
= S
n
j 3π n
8
e
Modulator IQ
i(t)
Complex
QAM
modulator
Filter
quadrature q(t)
S(t)
y(t)
3π ⋅n
8
Carrier fc
modulator
i(t)
y(t)
+
-90°
S(t)
Σ
-
q(t)
sin(ωct)
carrier
Figure 114
The bit source generates bits dk at a rate of fb=812.5 Kbps. Each group of 3 bits is
Gray-coded into an octal-valued symbol cn=[0,1,2,3,4,5,6,7] (see table below). This
symbols are produced at rate fs= fb/3=270.833 Ksps, which is identical to the GSM
symbol rate.
Table 1. Gray-coding of binary bit triplets into ocatal symbols
d1, d2, d3
0,0,0 0,0,1 0,1,0 0,1,1 1,0,0 1,0,1 1,1,0 1,1,1
cn
3
4
2
1
6
5
7
0
table 5
153
Index n in cn, is the n-th step used to send a symbol, for example we can decide to
send the same symbol for n-consecutive times.
The octal-valued symbols cn are used to phase modulate a carrier, yielding an
8-PSK-EDGE waveform sequence Sn :
S
= A e
n
c
j
2π C
8
n
= A cos
c
2π C n
2π C n
+ j A sin
= I + jQ
c
8
8
eq 257
where Ac is the amplitude, here set to one as an example.
The above formulation of Sn is also called I,Q, form of the base-band binary
signal. Values and vector module of Sn for n=0..7 are listed below. Note that each
constellation point is on unitary circle (i.e. the Sn vector module is always unitary).
= e
j 2 π ⋅0
8
= cos 0
+ j sin 0 = 1 + j 0
= e
j 2 π ⋅1
8
= cos
+ j sin
= e
j 2 π ⋅2
8
= cos
= e
j 2 π ⋅3
8
= cos
= e
j 2 π ⋅4
8
= cos
= e
j 2 π ⋅5
8
= cos
= e
j 2 π ⋅6
8
= cos
S7 = e
j 2 π ⋅7
8
= cos
S
S
S
S
S
S
S
0
1
2
3
4
5
6
π
4
π
2
+ j sin
π
4
≅ 0.7 + j 0.7
π
2
≅ 0 + j1
⇒ S
⇒ S
0
1
⇒ S
2
=1
=1
=1
3π
3π
+ j sin
≅ -0.7 + j 0.7 ⇒ S = 1
3
4
4
π + j sin π ≅ − 1 + j 0
⇒ S
5π
5π
+ j sin
≅ -0.7 - j 0.7
4
4
⇒ S
3π
3π
+ j sin
≅ 0 - j1
2
2
⇒ S
5π
5π
+ j sin
≅ 0.7 − j 0.7
4
4
⇒ S
4
5
6
7
=1
=1
=1
=1
eq 258
154
The baseband unfiltered 8PSK vector constellation implementation on the imaginary
unitary plane is shown in figure below:
Imaginary Part (Q)
S2= (010)
ϕ (S 2 ) = π 2
S3= (000)
S1= (011)
Q=0.7
ϕ (S1 ) = π 4
S0= (111)
S4= (001)
I=0.7
ϕ (S 0 ) = 0
Real Part (I)
S7= (110)
S5= (101)
S6= (100)
Figure 115
Figure below shows the i(t),q(t) signal time variation for an unfiltered 8PSK
modulation, when a sequence of 8 symbols, see table 1, is used as a single ordinate,
binary input data stream. To each single couple i(t),q(t), corresponds one and only one
point on the unitary imaginary plane, as showed above.
155
Figure 116
Figure below shows corresponding vector amplitude and phase time variation.
Note that in case of unfiltered constellation, the vector amplitude is constant. This is not
true when a complex filter is used, since amplitude modulation AM is introduced .
Figure 117
156
Figure below shows the corresponding vector constellation for unfiltered implementation.
S2(010)
S3(000)
S1(011)
S0(111)
S4(001)
S5(101)
S6(100)
Figure 118
To study either the spectrum or the vector constellation of an unfiltered 8PSK
configuration, we can use a pseudorandom PRBS9 as a binary input sequence data. If
the length of the symbols sequence chosen for winiq software program is for example
greeter than 1000, than the screen output will be as reported below:
Figure 119
157
In so doing we should keep in mind that in ideal case of unfiltered signals there is
no phase jitters, Hence each single constellation point remains easily selectable by the
receiver.
Another observation is that vectors constellation does go through origin. This is
the main problem since signal filtering introduces an Amplitude Modulation, and
hence, also a greeter sensitivity at low C/I with respect to GMSK modulation.
Figure below reports the relative FFT magnitude for unfiltered case we have
showed so far, note the great sidelobes that are a consequence of rectangular data
pulses.
≅13dB
Figure 120
What analyzed so far is an 8 PSK standard unfiltered constellation, in which each
of 8 constellation points is uniquely identified with a particular symbol value.
16.3 Symbol Rotation
In 8PSK-EDGE modulation, in order to ensure that the envelope of the signal
does not go instantaneously close to zero and hence to reduce AM phenomena due to
filtering action, the 8PSK symbols are continuously rotated with 3π/8 radians per
symbol before pulse shaping (i.e. each phase modulated symbol is additionally phase
shifted by 3π/8 radians per symbol).
The cumulatively phase shift (CPS) sample sequence Rn is:
Rn = S n ⋅ e
j
3π n
8
=e
j
2π C n
8
e
j
3π n
8
=e
j
π
8
( 2C n +3n )
= an + jbn
eq 259
If symbol Sn varies from 0 to 7 than the corresponding Rn shifted symbols are:
158
R
R
R
R
R
R
R
R
0
1
2
3
4
5
6
7
( ) = cos 0 +
jπ 0
= e 8
(
j sin 0 = 1 + j 0
⇒ R
)
jπ 2 + 3
= e 8
= cos
=
=
=
=
=
=
5π
5π
+ j sin
≅ - 0 . 38 + j 0.92
8
8
j π (4 + 6 )
10 π
10 π
+ j sin
≅ − 0.71 - j 0 . 71
= cos
e 8
8
8
j π (6 + 9 )
15 π
15 π
+ j sin
≅ 0.92 − j 0 . 38
= cos
e 8
8
8
j π (8 + 12 )
20 π
20 π
+ j sin
≅ 0 + j1
= cos
e 8
8
8
j π (10 + 15 )
25 π
25 π
+ j sin
≅ − 0 . 92 − j 0.38
= cos
e 8
8
8
j π (12 + 18 )
30 π
30 π
+ j sin
≅ 0.71 − j 0.71
= cos
e 8
8
8
j π (14 + 21 )
35 π
35 π
= cos
+ j sin
≅ 0.38 + j 0 . 92
e 8
8
8
⇒ R
0
=1
1
⇒ R
⇒ R
⇒ R
⇒ R
⇒ R
⇒ R
=1
2
3
4
5
6
7
=1
=1
=1
=1
=1
=1
eq 260
Table below reports Rn and the corresponding angle α. Note that the difference:
Rn- Rn-1 between two consecutive vector constellation point is always 112.5°
Rn
Rn- Rn-1
angle
R0
0
R1
112.5
112.5
R2
225
112.5
R3
337.5
112.5
R4
450
112.5
R5
562.5
112.5
R6
R7
675
112.5
787.5
112.5
0
table 6
The corresponding unfiltered vector implementation on the imaginary unitary plane is
shown below
159
Imaginary Part (Q)
R1=011
R4=001
R7=110
112.5°
112.5°
112.5° 112.5°
R0=111
112.5°
Real Part (I)
112.5°
R5=101
R3=000
112.5°
R6=100
R2=010
Figure 121
Imaginary Part (Q)
Rn=4--001
Rn=1--011
Rn=7--110
Rn=0--111
Real Part (I)
Rn=5--101
Rn=3--000
Rn=2-010
Rn=6--100
Figure 122
160
Transmitting at each time step n the same symbol we note that the relative position on
the constellation plane is continually rotated by 67.5°
67.5°
figure 123
Note that with symbol rotation we have no longer 8 constellation point but 16.
8PSK + shift (CPS)
8PSK
Fixed position
Shift
position
figure 124
161
Figure below shows i(t), q(t) signals time variation for an 3π/8 shifted 8PSKEDGE unfiltered modulating input signals when a single ordinate sequence of 8 symbols
(0,1,2,3,4,5,6,7), is used as a binary input data stream.
Figure 125
Figure below shows the corresponding vector amplitude and phase time variation. Note
that in case of unfiltered constellation, the vector amplitude is constant. This is not
true when a complex filter is used.
Figure 126
162
To study either the spectrum or the vector constellation of an unfiltered π/8 shifted
8PSK-EDGE configuration, we can use a pseudorandom PRBS9 as a binary input
sequence data.
If the length of the symbols sequence chosen for winiq software program is for
example greeter than 1000, than the screen output will be as reported below:
π/8 shifted 8PSK-EDGE
8PSK
Zero
Figure 127
As shown in figure above, the EDGE signal has a non-zero minimum magnitude when
3π/8 radiant rotation is used, therefore this phase rotation assures that the signal
envelope never goes to zero.
Without the CPS operation, the vectors constellation goes through origin.
Figure below reports the relative FFT magnitude, note that in case of unfiltered
signals there is no spectrum difference with a standard 8PSK. This is because the
points of constellation in 8PSK EDGE are only shifted by 3π/8 radiants.
163
≅13dB
Figure 128
For a non shifted standard 8PSK, we can try to explain passages of the vector through
the origin on the constellation imaginary plane.
For example, if we consider a pseudorandom PRBS9 as a binary input data sequence
and if we focusing our attention around a few random points transition, it is possible to
observe that some times, vectors i(t),q(t) have a contemporary passage through origin.
Figure 129
In order to switch from one constellation point to another opposite constellation point,
the corresponding i(t),q(t) resulting vector, has to pass through the origin. By doing
so, the amplitude of i(t),q(t) resulting vector goes to zero. Defining the envelope
dynamic range as the ratio between maximum and minimum envelope values, we note
that without CPS, the signal envelope goes to zero and the envelope dynamic range
becomes infinite.
164
16.4 (8PSK EDGE) modulation AM distortion
For unfiltered rectangular-shaped data pulses, as we have seen, the amplitude of
envelope of the 8PSK and 8PSK_EDGE signal is constant. That is, there is no AM on
the signal even for a 180° phase shift (for a non shifted 3π/8 radiant vector constellation,
since the data switches value say, from +1 to -1,instantaneously). We might wonder why
baseband filtering signal is then necessary?
The rectangular-shaped data produces a (sin(x) / x)^2 type power spectrum for a
signal that has large undesirable spectral sidelobes. The absolute bandwidth of
rectangular multilevel pulses is therefore infinity !
Because we never have an infinite bandwidth, we must use a filtering system in order to
reduce the bandwidth, but when this pulses are filtered improperly they will spread in
time, the pulse for each symbol may be smeared into adjacent time slot causing
intersymbol interference (ISI). One way to obtain an ISI reduction is by using a raised
cosine rolloff filter.
At the same time, when a phase transition occurs, the filtering operation causes an
amplitude modulation (AM), the larger the phase transition, the greater the amplitude
modulation.
These AM effects can be reduced with 3π/8 offset 8PSK in which we never have the
deep π phase shift transition.
Summarizing, we encounter two types of problems:
16.4.1
First problem (ISI):
Although ISI is eliminated using raised-cosine filter, a 200 KHz channel spacing
results in a symbol rate less than 200 KSymbol/s. The 8PSK EDGE signal with
rised-cosine filtering does not fit within 200 KHz of bandwidth, for example using
a raised cosine rolloff filter we could have:
D( symbols / s ) =
2B
for a raised cosine rolloff filter.
1+ r
eq 261
2 B = 200 Khz for GSM and EGPRS
r = rolloff _ factor
If r=0.22, the symbols would be only D=200000/1.22= 163.934,4 (Simbols/s)
which is less than 270.833 Ksymbol/s required for EDGE
In order to achieve the desired symbol rate, 270.833 Ks/s and constrain the
bandwidth of the output signal so that it remains below (or nearly below) the
transmit mask defined for EDGE (200 KHz GSM channel bandwidth) a more
severe filtering approach is required
165
The transmit filter used is a Linearized Gussian Filter (similar to, but different
than the method used for GSM).
In this manner, the spectrum of 8PSK signal can be restricted to 200 KHz and
the symbols filtering allow the 8PSK signal spectrum to occupy the same
bandwidth as a GPRS/GSM signals. In the same time it also introduces a
considerable ISI component.
Because of the severe ISI introduced by the linearized Gussian Filters, the
receiver includes an equalizer, and the Signal-to-Noise Ratio on Co-channel
interference of about C/N ≥ 18 dB is quite high if compared to a GMSK
modulation where C/N ≥ 9 dB
Since the EDGE transmit mask is nearly identical to the GSM transmit mask,
the EDGE signal succeeds in tripling the data throughput within the standard
GSM channel.
16.4.2
Second problem (AM):
Filtering produces Amplitude Modulation AM on the resulting EDGE signal
because the filtered data waveform cannot change instantaneously from one
peak to another, especially if 180° phase transitions occur as in a simple
8PSK modulation.
Although filtering solves the problem of poor spectral sidelobes, it creates
another: AM on the EDGE signal.
AM has several consequences:
•
•
•
8PSK EDGE constellations points are no longer on the unitary circle so
amplitude jitter experienced by resulting vector occur in a more C/I
sensitivity at receiver user side;
Because (for the reason above), when EDGE modulation is used, the
mean output transmitted power is lower compared to GSM modulation
(about 2 dB). Than if BCCH (broadcast control channel) carrier is used for
EDGE the cell-reselection-algorithm could experiences a fault.
Due to AM, low-efficiency, linear (class A or class B) amplifiers, instead
of high-efficiency non linear (class C) amplifiers, are required for the
8PSK signal without distortion. In portable communication applications,
these amplifiers increase the battery capacity requirements.
These AM effects can be reduced with 3π/8 offset 8PSK in which we never have
the π phase shift transition.
166
16.5 Used Gaussian EDGE Filter
The complex sequence Rn is next passed through a low-pass filter to produce the
filtered complex signal.
x(t ) = ∑ Rn ⋅ p(t − nT )
eq 262
n
where T=1/fs is the symbol interval, and p(t) is the filter pulse shape. We can rewrite in
the alternative form:
x(t ) = I (t ) + jQ (t ) = ∑ an ⋅ p(t − nT ) + j ∑ bn ⋅ p(t − nT )
n
eq 263
n
with real symbol an, bn and real pulse p(t), for two real filtered signals I(t) and O(t). Each
real filtered signals can be visualized as the output of a linear time-invariant (LTI) filter
driven by a stream of impulse scaled by an, (or bn), yielding a linear superposition of
scaled time-shifted pulses p(t).
The exact filter pulses shape p(t) defined for EDGE signal is non-zero over the interval
-5(T/2) ≤ t ≤ 5(T/2),
⎛ 5 ⎞
p ( t ) = c0 ⎜ t + T ⎟
⎝ 2 ⎠
eq 264
where c0 is the principal pulse in the Laurent decomposition of the 0.3-GMSK
modulation,
⎧ 3
f (t + iT )
⎪
c0 (t ) = ⎨∏
i =0
⎪⎩
0
⎫
0 ≤ t ≤ 5T ⎪
⎬
elsewhere ⎪⎭
eq 265
167
⎧ ⎛ t
⎞
⎪sin⎜⎜ π ∫ g (u )du ⎟⎟
⎠
⎪ ⎝ 0
⎪⎪ ⎛ t −4T
⎞
f (t ) = ⎨cos⎜⎜ π ∫ g (u )du ⎟⎟
⎠
⎪ ⎝ 0
⎪
0
⎪
⎪⎩
⎫
0 ≤ t ≤ 4T ⎪
⎪
⎪⎪
4T ≤ t ≤ 8T ⎬
⎪
elsewhere ⎪
⎪
⎪⎭
eq 266
The integrand g(t) is defined in terms of the frequency pulse in gGMSK(t) by
g (t ) =
1
g GMSK (t − 2T )
2
g GMSK (t ) =
Q (t ) =
eq 267
⎞ ⎞⎤
⎛
⎛ t − 5T / 2 ⎞ ⎞ ⎛
1 ⎡ ⎛⎜
⎟ ⎟ − q⎜ 2π ⋅ 0.3⎜ t − 3T / 2 ⎟ ⎟⎥
⎢Q 2π ⋅ 0.3⎜⎜
⎜ T ln( 2) ⎟ ⎟
⎟⎟ ⎜
2T ⎢ ⎜⎝
⎠ ⎠⎥⎦
⎝
⎝ T ln( 2) ⎠ ⎠ ⎝
⎣
1
2π
∞
∫e
r2
−
2
eq 268
dτ
t
The combination of expressions above is defined as the filter pulse shape.
Following, the base band signal is:
y (t ' ) = ∑ Rn ⋅ c0 (t '−nT + 2T )
eq 269
n
The time reference t’=0 is the starting of the active part of burst as shown figure this is
also the start of the symbol period of symbol 0 (containing the first tail bit)
168
9 tail bits
9 tail bits
111 111 111.......
.......111 111 111
Output phase
The useful part
1/2 symbol
1/2 symbol
The active part
figure above show Relation between active part of burst and tail bits. For the normal
burst the useful part lasts for 147 modulating symbols. Before the first bit of the bursts
as defined in GSM 05.02 [3] enters the modulator, the state of the modulator is
undefined. Also, after the last bit of the burst, the state of the modulator is undefined.
The tail bits (see GSM 05.02) define the start and the stop of the active and the useful
part of the burst as illustrated in figure above. Nothing is specified about the actual
phase of the modulator output signal outside the useful part of the burst.
169
16.6 Effect due to Gaussian EDGE filtering in 3π/8 shifted 8PSK
Figure below shows i(t),q(t) baseband time variation and the output modulated r(t)
signal, when a single ordinate sequence of 8 symbols, is used as a binary input data
stream.
No Gaussian edge filter
Gaussian EDGE filter
I
I
Q
Q
r
r
Ф
Amplitude
modulation
Ф
(AM)
Figure 130
Figure above shows the corresponding amplitude vector and phase time variation
for Gaussian EDGE filtered signals. Note that in case of an unfiltered constellation,
the vector’s amplitude is constant, this is not true when a complex filter is used having
Amplitude Modulation AM.
Using a PBR9 input data stream, we can evaluate The spectrum:
170
Gaussian EDGE filter
No Gaussian EDGE filter
Amplitude
of modulated
signal
Phase
of modulated
signal
Bandwidth
of modulated
signal
figure 131
Focusing out attention at the transmitter output, we can se haw the baseband signal
filtering produces ISI.
Obviously the same filter applied at the receiver side reduces these phenomena.
171
Gaussian EDGE filter
No Gaussian EDGE filter
Gaussian EDGE filter cause:
Amplitude and phase Jitter
Increasing ISI
figure 132
172
16.7 Modulation
Let us indicate the frequency carrier fc. Follows that the QAM modulation is:
(
)
s (t ) = Re y (t ) ⋅ e jωct = Re( y (t ) ⋅ (cos ωc t + j sin ωc t ))
eq 270
because y(t)=i(t)+jq(t) than the real part of output modulated signal becomes:
(
)
s (t ) = Re y (t ) ⋅ e jωct = Re((i (t ) + jq (t ) ) ⋅ (cos ωc t + j sin ωct )) =
= Re(i (t ) cos ωc t + ji (t ) sin ωct + jq (t ) cos ωct − q (t ) sin ωc t ) =
eq 271
s (t ) = i (t ) cos ωct − q (t ) sin ωct
using the filtering equation already seen before for a single burst:
y (t ' ) = ∑ Rn ⋅ c0 (t '−nT + 2T )
eq 272
n
the modulated RF carrier during the useful part of the burst became:
s (t ' ) =
[
2 Es
Re y (t ' ) ⋅ e j (2πf ct ' +ϕ0 )
T
]
eq 273
where Es is the energy per modulating symbol, fc is the center frequency and φ0 is a
random phase and is constant during one burst (see TS 05.04).
16.8 Conclusion
The 3π/8 shifted 8PSK-EDGE signals succeeds in it’s primary goals of tripling the onair data rate while maintaining nearly the same spectral occupancy as the original GSM
signal. The 3π/8 shift assures that the signal envelope never falls below a certain level.
Nonetheless, this signal has a significant envelope variation, which exposes the signal
to AM-PM distortion impairments that don’t degrade the signal quality of GMSK.
173
17 EFFICIENT MODULATION METHODS STUDY AT NASA/JPL
17.1 PHASE SHIFT KEYED (8-PSK) MODULATION
8-PSK modulation is not currently used by CCSDS Space Agencies.
Inserting a filter in the modulator further degrades system performance because nonorthogonality increases crosstalk between phase states.
17.2 PSK Modulation Bit-Error-Rate (BER)
Losses are evident in Figure below showing the Bit-Error-Rate performance for 8-PSK
modulation. Relative to ideal BPSK/NRZ modulation, even an ideal (lossless) 8-PSK
system imposes heavy performance penalties. Ideal 8-PSK requires an EB / N0 of 9.5 10 dB to attain a BER = 1 x 10-3
When a Butterworth BTS = 3 filter is added, the required EB / N0 rises to 11.5 dB.
Compared to the EB / N0 of about 8 dB, needed for a filtered non-ideal QPSK system at
the same BER, it is clear that 8-PSK is not a useful modulation method in power limited
applications. Losses using a Square Root Raised Cosine (r = 1) filter were so great that
the plot is not even included in this report.
Excessive losses result from the non-orthogonal relationship between phase states.
This simulation shows that inherent 8-PSK modulation losses are unlikely to be
acceptable in most applications, even without filtering.
174
figure 133: 8-PSK modulation Bit Error Rate
17.3 8-PSK Modulation Spectra
Not with
standing the system losses, spectrum advantages of simultaneously
transmitting three data bits is clearly evident in Figure below 8-PSK modulation with a
Butterworth filter having a BTS = 2. A BTS =2 was used for consistency with studies of
the other modulation types. Figure below also demonstrates that filtering will be needed.
The unfiltered spectrum (top) is very similar to that for unfiltered QPSK. 8-PSK provides
a 1.8 dB improvement in data rate over QPSK and the spectral improvement appears to
be on the same order.
175
figure 134
176
17.4 PSK Modulation Power Containment
Power Containment curves, Figure below show the occupied bandwidth to be about 2.4
RB when using a Butterworth BTS = 2 filter. This bandwidth will increase with a BTS = 3
filter which is required to avoid the additional 1 dB loss.
figure 135
17.5 PSK Modulation Study Conclusions
Results of this study show 8-PSK modulation to be of little value for most space
telemetry data transmissions. While 8-PSK does provide a marginally narrower
spectrum, system losses make the modulation type unsuitable for most Category A
missions. 8-PSK modulation may be attractive in strong signal applications where
system losses are of little importance.
177
18 MINIMUM-SHIFT KEYNG (MSK) AND GMSK
MSK has the advantages of producing a constant-amplitude signal and, consequently,
can be amplified with Class C amplifiers without distortion. As we will see, MSK is
equivalent to OQPSK with sinusoidal pulse shaping [for hi(t)].
Definition: Minimum-shift keying (MSK) is a continuous-phase FSK with a minimum
modulation index (h=0.5) that will produce orthogonal signalling.
First, let us shown that h=0.5 is the minimum index allowed for orthogonal
continuous-phase FSK.
For the binary 1 to be transmitted over the bit interval 0<t<Tb, the FSK signal would be :
s1 (t ) = Ac cos(ω1t + θ1 )
eq 274
and for 0 to be transmitted the FSK signal would be
s2 (t ) = Ac cos(ω2t + θ 2 )
eq 275
where θ1=θ2 for the continuous phase condition at the switching time t=0.
For orthogonal signaling, we require the integral of the product of the two signals over
the bit period 2Tb to be zero. Thus, we require:
2Tb
∫ s (t )s
1
2Tb
2
(t )dt =
0
2Tb
=
∫
0
∫A
2
c
cos(ω1t + θ1 ) cos(ω 2 t + θ 2 )dt =0
i.e.
0
1
⎤
⎡1
Ac2 ⎢ cos[(ω1 + ω 2 )t + (θ1 + θ 2 )] + cos[(ω1 − ω 2 )t + (θ1 − θ 2 )]⎥ dt =
2
⎦
⎣2
⎡ 1 (ω1 + ω 2 )
⎤
1 (ω1 − ω 2 )
cos[(ω1 + ω 2 )t + (θ1 + θ 2 )] +
cos[(ω1 − ω 2 )t + (θ1 − θ 2 )]⎥ dt =
Ac2 ⎢
2 (ω1 − ω 2 )
⎣ 2 (ω1 + ω 2 )
⎦
0
2Tb
2Tb
⎡ 1 (ω1 + ω 2 )
⎤
⎡ 1 (ω1 − ω 2 )
⎤
cos[(ω1 + ω 2 )t + (θ1 + θ 2 )]⎥ dt + ∫ Ac2 ⎢
cos[(ω1 − ω 2 )t + (θ1 − θ 2 )]⎥ dt =
= ∫ Ac2 ⎢
⎣ 2 (ω1 + ω 2 )
⎦
⎣ 2 (ω1 − ω 2 )
⎦
0
0
2Tb
=
∫
= Ac2
+ Ac2
1
(ω1 + ω 2 )
1
(ω1 − ω 2 )
2Tb
⎡
∫ ⎢⎣(ω
1
0
2Tb
∫
0
1
⎤
+ ω 2 ) cos[(ω1 + ω 2 )t + (θ1 + θ 2 )]⎥ dt +
2
⎦
1
⎤
⎡
Ac2 ⎢(ω1 − ω 2 ) cos[(ω1 − ω 2 )t + (θ1 − θ 2 )]⎥ dt =
2
⎦
⎣
2Tb
2Tb
1
1
⎡1
⎤
⎡1
⎤
sin[(ω1 + ω 2 )t + (θ1 + θ 2 )]⎥ + Ac2
sin[(ω1 − ω 2 )t + (θ1 − θ 2 )]⎥ = 0
=A
⎢
⎢
(ω1 + ω 2 ) ⎣ 2
(ω1 − ω 2 ) ⎣ 2
⎦0
⎦0
2
c
178
2Tb
∫ s (t )s
1
2
(t )dt = Ac2
0
1
1
⎡1
⎤
sin[(ω1 + ω 2 )2Tb + (θ1 + θ 2 )] − sin[(θ1 + θ 2 )]⎥ +
⎢
(ω1 + ω 2 ) ⎣ 2
2
⎦
1
1
⎤
⎡1
sin[(ω1 − ω 2 )2Tb + (θ1 − θ 2 )] − sin[(θ1 − θ 2 )]⎥ = 0
+A
⎢
(ω1 − ω 2 ) ⎣ 2
2
⎦
eq 276
2
c
The first term is negligible, because (ω1+ω2) is large, so the requirements reduces to
2Tb
∫ s1 (t )s2 (t )dt =
0
Ac2 ⎡ sin[2(ω1 − ω 2 )Tb + (θ1 − θ 2 )] − sin[(θ1 − θ 2 )]⎤
⎢
⎥=0
ω1 − ω 2
2 ⎣
⎦
eq 277
for the continuous phase case the phase must be θ1=θ2; and the equation above is
satisfied (i.e. equal to zero) for a minimum value h=0.5 .
in fact sin[2(ω1 − ω 2 )Tb + (θ1 − θ 2 )] − sin[(θ1 − θ 2 )] = 0 is verified when
⇒ sin[π + (θ1 − θ 2 )] − sin[(θ1 − θ 2 )] = 0 when
2(ω1 − ω 2 )Tb = π
but
2(ω1 − ω 2 )Tb = π
⇒ 2 ⋅ 2π ( f1 − f 2 )Tb = π ⇒ 2 ( f1 − f 2 )Tb =
θ1 = θ 2
1
1
⇒ h=
2
2
Therefore calling the modulation index h as:
h = 2( f1 − f 2 )Tb = 2(∆f )Tb =
h = 1/ 2
2( f1 − f 2 )Tb =
2∆ϑ
π
2(ω1 − ω 2 )Tb ∆ω ⋅ Tb 2∆θ
=
=
π
π
2π
1
2
1
=
2
⇒
⇒
∆f = ( f1 − f 2 ) =
2∆ϑ =
1
4Tb
π
then when
eq 278
2
i.e. the peak to peak phase variation is 90° while the peak to peak frequency shift is ¼
Tb.
Now we will demonstrate that MSK signal is also a form OQPSK with sinusoidal pulse
shaping. First, consider the FSK signal over the signalling interval (0,Tb). Then using
equation:
s (t ) = Re[ g (t )e jωct ]
eq 279
the complex envelope is:
179
t
g (t ) = Ac e jθ ( t ) = Ac e
∫
j 2π ∆f m ( λ ) dλ
0
eq 280
where m(t)=±1, and
envelope became:
g (t ) = Ac e
jθ ( t )
= Ac e
0<t<Tb , therefore using h=0.5 and ∆f=1/4Tb the complex
± j 2π ∆f ⋅t
= Ac e
± j 2π
1
t
4Tb
= Ac e
±j
π t
2 Tb
eq 281
where the ± signs denote the possible data during the (0,Tb) interval. Thus,
g (t ) = Ac e jθ (t ) = Ac e
±j
πt
2Tb
⎡ ⎛ πt ⎞
⎛ π t ⎞⎤
⎟⎟ ± j sin ⎜⎜
⎟⎟⎥ = x(t ) ± jy (t ),
= Ac ⎢cos⎜⎜
⎝ 2Tb ⎠⎦
⎣ ⎝ 2Tb ⎠
0 < t < Tb
eq 282
and the MSK signal is therefore
⎡ ⎛ πt
s (t ) = Re[ g (t )e jωct ] = x(t ) cos ω c t − y (t ) sin ω c t = ⎢cos⎜⎜
⎣ ⎝ 2Tb
⎡ ⎛ πt
⎞⎤
⎟⎟⎥ cos ω c t m ⎢sin⎜⎜
⎠⎦
⎣ ⎝ 2Tb
⎞⎤
⎟⎟⎥ sin ω c t eq 283
⎠⎦
This type of FSK modulation with modulation index h=0.5 is a form of orthogonal FSK
with minimum bandwidth required, called MSK (Minimum Shift Keying). This type of
modulation is also a particular case of CPM (Continuous Phase Modulation).
In CPM techniques the phase is slowly varied in each symbol interval starting from the
phase value assumed in the preceding symbol interval. Consequently are also called
modulation technique with memory.
Since a frequency shift produces an advancing or a retarding in phase, frequency shifts
can be detected by sampling phase at each symbol period. Phase shifts of (2N + 1)π/2
radians are easily detected with an I/Q demodulator.
At even numbered symbols, the polarity of the I channel conveys the transmitted data,
while at odd numbered symbols the polarity of the Q channel conveys the data. This
orthogonally between I and Q simplifies detection algorithms and hence reduces power
consumption in a mobile receiver. The minimum frequency shift which yields
orthogonality of I and Q is that which results in a phase shift of ± π/2 radians per symbol
(90 degrees per symbol). FSK
The binary data of m(t) alternatively modulate the x(t) and y(t) components, and the
pulse shape for the x(t) and y(t) symbols( which are 2Tb wide instead of Tb) is a
sinusoid. Thus MSK is equivalent to OQPSK with sinusoidal pulse shaping.
180
FSK and MSK produce constant envelope carrier signals, which have no amplitude
variations. This is a desirable characteristic for improving the power efficiency of
transmitters. Amplitude variations can exercise nonlinearities in an amplifier’s amplitudetransfer function, generating spectral regrowth, a component of adjacent channel power.
Therefore, more efficient amplifiers (which tend to be less linear) can be used with
constant-envelope signals, reducing power consumption.
MSK has a narrower spectrum than wider deviation forms of FSK. The width of the spectrum is
also influenced by the waveforms causing the frequency shift. If those waveforms have fast
transitions or a high slew rate, then the spectrum of the transmitter will be broad. In practice,
these Waveforms are filtered with a Gaussian filter, resulting in a narrow spectrum. In addition,
the Gaussian filter has no time-domain overshoot, which would broaden the spectrum by
increasing the peak deviation.
MSK with a Gaussian filter is termed GMSK (Gaussian MSK).
An MSK modulator scheme is reported in figure below:
dI
Sinusoid
filter
I
Baseband
processing
modulator f=fc
X
cos(fc)
Delay
dQ
Cosinusoid Q
filter
+
MSK
X
sen(fc)
In OQPSK the rectangular pulse modulates the carrier directly:
modulator f=fc
dI
I
Baseband
processing
X
cos(fc)
Delay
dQ
Q
+
OQPSK
X
sen(fc)
figure 136
A block scheme of MSK modulator is reported below
181
Baseband
x data
Oscillator
f0=∆f=1/4R
m(t)
input
x(t)
X
X
Carrier
oscillator
fc
cos(πt/2Tb)
Serial-toparallel
converter
(2bit)
Accos(ωct)
+
-90°
phase
shift
-90°
phase
shift
Sync
input
sin(πt/2Tb)
y data
X
s(t)
MSK
signal
Acsin(ωct)
y(t)
X
figure 137: parallel generation of MSK
In order to make the difference between FSK and MSK we are going to show an
example for CPM using a Trellis phase transitions representation where phase
transitions permitted are only of 90°.
Particularly a phase shift of +90 degrees represents a data bit equal to “1”, while –90
degrees represents a “-1(or 0 in a binary form)”.
Because CPM can be represented also as an OQPSK modulation and, an MSK as a
pre-filtered OQPSK, by now on will call the two modulation types using the quadrature
meaning title.
Supposing an input NRZ data format, then one possible Trellis phase representation
could be the following:
182
+1
NRZ
data
2π
t
-1
3/2π
π
Sharp slope
variation
(discontinuity)
π/2
0
-π/2
-π
-3/2π
-2π
2Tb
4Tb
6Tb
8Tb
10Tb 12Tb
t
MSK
phase
+1 Tx
t
2Tb
4Tb
6Tb
8Tb 10Tb 12Tb
-1 Tx
figure 138: Trellis tree phase representation for a CPM
Although there are only π/2 phase shift, these discontinuity on the phase transitions
requiring a large bandwidth. In order to limit this bandwidth a filtering method is needed.
Anyway this filtering method introduce ISI.
OQPSK no filtered
OQPSK filtered
Phase
transition
rounded
It does not a shift phase
figure 139
183
The main difference between MSK and OQPSK is the sinusoidal pre-filtering method
used into MSK:
OQPSK
MSK
s (t ) = d I (t ) cos(2πfct ) + d Q (t ) sin( 2πfct )
eq 284
⎡π t ⎤
⎡π t ⎤
s (t ) = d I (t ) cos ⎢
⎥ sin( 2πfct )
⎥ cos(2πfct ) + d Q (t ) sin ⎢
⎣ 2 Tb ⎦
⎣ 2 Tb ⎦
eq 285
As an example we report a plot of the MSK signalling and that for the corresponding RF
output:
I baseband
MSK output
modulated signal
I(t)
I modulated
signal
I MSK
Modulated
signal
Q baseband
Σ
Q(t)
Q modulated
signal
Q MSK
Modulated
signal
figure 140
184
The peculiarity of MSK is not in the main lobe which is 50% more greater than a
OQPSK. Instead what is worth of consideration is that MSK has a fast side lobes
decaying. Spectrum of MSK decays with the four power of the frequency, while in the
case of QPSK and OQPSK the law is modestly of quadratic type.
Therefore we can say that MSK is characterized by a better interference control on
adjacent channels.
figure 141
18.1 GMSK
Another form of MSK is Gaussian-filtered MSK (GMSK). For GMSK, the data
(rectangular-shaped pulses) are filtered by a filter having a Gaussian-shaped frequency
response characteristic before the data are frequency modulated onto the carrier. The
transfer function of the Gaussian low pass filter is
⎡ ⎛ f ⎞ ⎛ ln 2 ⎞ ⎤
−⎢⎜ ⎟ ⎜
⎟⎥
⎣⎢ ⎝ B ⎠ ⎝ 2 ⎠ ⎦⎥
2
H( f ) = e
eq 286
Where B is the 3-dB bandwidth of the filter. This filter reduces the spectral sidelobes on
the transmitted MSK signal.
The product of B with bit period Tb:
185
α = B ⋅ Tb
eq 287
is called normalized bandwidth; BTb=0.3 used in GSM services, gives a good
compromise between relatively low sidelobes and tolerable acceptable ISI.
For example in GSM mobile we have
the figure on the right which represent
the time filter response, the smaller
time response, the greater frequency
bandwidth is required. Ideally MSK needed
for a great bandwidth, since a time
rectangular pulse shaping is equivalent
to an infinite frequency bandwidth.
For BTb=0.3 GMSK has lower spectral sidelobes than those for MSK, QPSK, or
OQPSK (with rectangular-shaped data pulses). In addition GMSK has a constant
envelope, since it is a form of FM. Consequently GMSK can be amplified without
distortion by high efficiency Class C amplifiers.
In figure below is reported an example of power efficiency
figure 142
186
In figure below are reported an example for amplitude and phase vector representation
and the vector and constellation diagrams.
We can see how the amplitude remains constant while the phase change continuously.
In this way the vector representation is a circle which has been made of all possible
phase point transitions, for the modulated signal s(t), from a symbol to another symbol.
In the other figures are reported the spectrum and bandwidth and the ISI representation
of modulated signal as a function of normalized bandwidth α = B ⋅ Tb . Its possible to
observe that the lower α = B ⋅ Tb the greater the ISI.
Constant
amplitude
Non ci sono salti di
fase pertanto i
punti infiniti della
simulazione
giacciono sulla
circonferenza
unitaria (cioè
ampiezza
costante )
No phase
discontinuity
Non sono salti di fase ma è la modalità
di rappresentazione tra -180° e 180°del programma
figure 143
187
BTb=0.5
BTb=0.5
BTb=0.2
BTb=0.2
figure 144
188
BTb=0.1
figure 145
189
18.1.1
How to implement GMSK modulator
An algorithm for a GMSK modulator is described below
1.
2.
3.
4.
5.
Create NRZ (-1,1) from the binary (0,1) input sequence
Create N samples per symbols
Integrate the NRZ sequence, in such a way to have an FSK (CPM)
Convolute with Gaussian function filter
Compute the corresponding I and Q component. At this stage we have the
quadrature components of the baseband GMSK equivalent signal
6. multiplying the I and Q component by the corresponding cos(ωct), -sin(ωct)
carriers
7. add the two resulting flow
Baseband process
Quadrature modulation
cos θ ( t )
0,1..
NRZ
-1,+1
code
NRZ code
∫
Integrator
b(t)
I(t)
L
θ (t )
Gaussia
LP
∑
900
BTb is
s(t)
RF
modulated
output
transformer
Q(t)
sin θ ( t )
figure 146
190
Mathematically:
∞
⎛ t − τ − iTb
m(t ) = ∑ mi Π ⎜⎜
Tb
−∞
⎝
NRZ Data:
Gaussian Filter:
π − ( απ t )
hG (t ) =
e
α
After Filter:
b(t ) = hG (t ) ∗ m(t ) =
∞
= ∑ mi
−∞
After integrator: θ (t ) = 1
4Tb
1
=
4Tb
∞
∫
−∞
, mi = ±1
2
∫h
G
(τ )m(t − τ )dτ
π − ( απ τ )
e
dτ
α
Tb
2
T
t −iTb − b
2
2
t −iTb +
b( z ) dz
⎧⎪ ∞
mi
∫-∞ ⎨⎪∑
⎩ −∞
= ∑ mi
−∞
t
∫
⎞
⎟⎟
⎠
t
1
4Tb
t
∫ ∫
−∞
∫
Tb
2
T
z −iTb − b
2
z −iTb +
Tb
2
T
z −iTb − b
2
z −iTb +
π − ( απ τ ) ⎫⎪
e
dτ ⎬ dz
α
⎪⎭
2
hG (τ )dτ dz
∞
= ∑ miθ i (t )
−∞
= LL +
m-2θ −2 (t ) + m-1θ −1 (t ) + m0θ 0 (t ) + m1θ1 (t ) + m 2θ 2 (t )
+ LL
191
18.1.2
How to implement GMSK demodulator
A coherent detector can be used to demodulate a GMSK signal:
figure 147 : MODULATOR
figure 148 : DEMODULATOR
However to avoid the receiver to have its own reference (i.e. the necessity of coherent
demodulation), a differential encoding can be used to create NRZ signal at the input of
demodulator.
Table below show as an example how to convert binary signal (0,1) to differential NRZ
symbol. It can be easily computed using the following operations:
192
table 7
Modulating binary signal at instant x[n-1], x[n]
X
Y NRZ
figure 149
193
19 EFFICIENT MODULATION METHODS STUDY AT NASA/JPL
19.1 MSK and GMSK Modulation Bit-Error-Rate (BER)
Figure below contains Bit-Error-Rate curves for MSK and GMSK. GMSK studies
included two separate filters with BTS = 0.5 (equivalent to BTB = 0.25) and BTS = 1
(equivalent to BTB = 0.5).
MSK is unfiltered and GMSK includes a Gaussian filter with two bandwidths (BTS = 0.5).
For simplicity, these, along with an ideal BPSK/NRZ reference curve, are placed on a
single BER graph.
Note that the EB / N0 required for a 1 x 10-3 BER is 7.3 - 8.2 dB which compares
favourably with BPSK/NRZ, even with a Gaussian filter bandwidth BTS = 0.5. Losses can
be expected to increase when a non-ideal modulator and receiver are employed;
however, Figure was generated using the ESA power amplifier operating in full
saturation.
figure 150
19.2 MSK and GMSK Modulation Spectra
Most MSK and GMSK applications have been applied in Personal Communication
Systems (PCSs). Spacecraft telemetry transmission systems have avoided GMSK
because of demodulation and synchronization difficulties. Often termed frequency
modulation, MSK and GMSK were included because of their inherently narrow spectral
bandwidths. Unlike the other modulation types, MSK is unfiltered and sidelobes are
reduced by avoiding phase change discontinuities. Figure below shows spectra for
unfiltered, ideal BPSK/NRZ (reference), MSK, and GMSK using the two filter
bandwidths. No discrete components are present in MSK or GMSK spectra despite
baseband filtering.
194
figure 151
figure 152
195
Figure above shows MSK modulation to be significantly more bandwidth-efficient than
the unfiltered BPSK/NRZ reference, reaching a level 60 dB below the peak sideband
amplitude at ± 8 RB. Its lack of discrete spectral components makes it attractive for
space telemetry applications.
However, from Figure it is apparent that MSK modulation is of little interest when
compared to GMSK. GMSK modulation is significantly more bandwidth-efficient than
any other method considered previously except of FQPSK. For example, it is 2 to 6
times more bandwidth-efficient than filtered QPSK modulation, depending upon the
specific filter bandwidths selected. When coupled with its BER performance, GMSK
should be seriously considered for high and very high data rate missions.
19.3 MSK / GMSK Modulation Power Containment
Figure below, concern Power Containment, show that GMSK has a high bandwidth
efficiency.
Occupied bandwidth is difficult to read, because of its small value, but it appears to be
less than 1.2 RB for both filter bandwidths. This represents a 16-times improvement over
the unfiltered [reference] BPSK/NRZ modulation and a 5-fold efficiency increase over
filtered BPSK/NRZ.
figure 153
196
19.4 MSK / GMSK Modulation Study Conclusions
Clearly, space agencies interested in RF spectrum efficiency should seriously consider
GMSK modulation. This is particularly true for high and very high data rate missions.
Unlike the phase modulation types described above, GMSK requires new modulator,
demodulator, and symbol synchronizer designs. In that respect, this recommendation
departs from one of the Efficient Modulation Methods Study guidelines: that only simple
modifications to existing Earth station equipment are permitted for any recommended
modulation method. However, GMSK’s bandwidth efficiency is too great to be ignored and
a departure from the guideline is warranted.
197
20 HISTORY OF SPECTRUM EFFICIENT MODULATION IN
TELEMETRY APPLICATIONS
Since 1992 the amount of available aeronautical telemetry spectrum has been
decreasing. Efforts by the national and international communities have reallocated 25
MHz of telemetry spectrum and efforts are under way to reallocate even more. This is
completely opposite of the requirements of the telemetry community as can be seen
from figure below. The chart clearly shows the data requirements of the test community
are increasing at an almost exponential rate. This increase in requirements is being
driven by the increasing complexity of the test articles coupled with compressed test
schedules. The increasing requirements for data coupled with the reduction in the
amount of available spectrum is causing the major test centers to have serious
concerns if there will be sufficient spectrum available to support all their programs.
Bit Rate (Kbps)
100,000
10,000
1,000
100
10
1970
1975
1980
1985
1990
1995
2000
2005
2010
Year
These trends of increasing data requirements and decreasing availability of
spectrum have focused attention on the efficient use of the remaining spectrum. It is the
responsibility of all programs to insure that their use of spectrum is as efficient as
possible and that spectrum is not needlessly being wasted. Some of the major test
ranges have already been forced to schedule use of the telemetry spectrum by the hour
to accommodate all of the required users. Under these conditions, it has become
imperative that all programs be as efficient and flexible as possible to ensure that they
are able to secure the use of a sufficiently large portion of the spectrum to complete
their required testing.
198
To be spectrally efficient means that data rates must be kept at the absolute
minimum bandwidth, so proper transmitter pre-modulation filtering techniques must be
used, and efficient modulation schemes must be employed. Currently the most
common modulation scheme is PCM/FM; this is a very robust modulation technique that
is fairly efficient. To be efficient these systems must have proper pre-modulation
filtering and be properly aligned. As can be seen from figure below, improper selection
of pre-modulation filtering, and over deviation of the transmitter can increase the
required channel bandwidth by over 50%. Figure shows ideal spectrum with proper
modulation filtering of .7 x Fb (Bit frequency), improper pre-modulation filtering at 1.4 x
Fb & 2 x Fb, and excessive transmitter deviation of 1.2 x Fb (.35 x Fb is ideal).
0
-10
-20
Improper
Pre-modulation Filter
2 x Fb
Over deviation
1.2 x Fb
-30
-40
-50
-60
-70
Ideal
PCM/FM
-80
-90
-100
1450.5
1452.5
1454.5
1456.5
1458.5
1460.5
figure 154
•
Ideal spectrum with proper modulation filtering of 0.7 x Fb (Bit frequency),
•
improper pre-modulation filtering at 2 x Fb,
•
excessive transmitter deviation of 1.2 x Fb (0.35 x Fb is ideal).
Improvement in pre-modulation filter selection and tighter controls on alignment
of systems will provide a great improvement in spectrum efficiency. New modulation
techniques such as GMSK and FQPSK have the potential to double spectrum
utilization. As can be seen from figure below, these new modulation techniques are
much more efficient than PCM/FM. Once the equipment can be developed, we can
199
expect to see vast improvements in spectrum efficiency. In the meantime efforts should
be concentrated on insuring that currently deployed telemetry systems have been
properly constructed and aligned.
figure 155. New Modulation Techniques vs PCM/FM.
200
21 CORRELATED DETECTION
Let us consider a linear system (filter) through which passes a signal when a white
noise is present. The aim of filter is to extract the signal with the maximum S/N ratio at
the output. We want to find the linear filter transfer function H(ω) that maximize the S/N
ratio at the output. Calling f(t) the signal applied to filter and ε, the noise spectral power
density which is present within the filter bandwidth.
Linear filter
H(ω)
f(t)
g(t)
ε
figure 156
• Considering first the signal f(t):
The Fourier transform of the input signal f(t) is
F (ω ) =
+∞
∫ f (t )e
− j ωt
dt
eq 288
−∞
The filter output signal voltage is therefore:
G (ω ) = F (ω ) H (ω )
eq 289
and
g (t ) = F −1 [F (ω )G (ω )] =
1
2π
+∞
∫ F (ω ) H (ω )e
j ωt
dω
eq 290
−∞
Its absolute value at time τ is
1
g (τ ) = F [F (ω )G (ω )] =
2π
−1
+∞
∫ F (ω ) H (ω )e
jωt
dω
eq 291
−∞
201
let us consider now the noise
The filter input noise power spectral density is
NoisePSD =
ε
(W/Hz)
2
eq 292
Where the spectrum is extended from positive to negative frequencies, then the
filter output noise power spectral density will be
G N (ω ) =
ε
H (ω )
2
2
eq 293
Where the filter Power spectrum is:
H (ω )
2
The filter output noise power is therefore
1
PN =
2π
+∞
ε
∫ 2 H (ω )
2
dω
eq 294
−∞
We want find H(ω) in order to maximize the output signal-to-noise ratio S/N:
⎛ g 2 (τ ) ⎞
⎟⎟
max⎜⎜
P
⎝ N ⎠
g 2 (τ ) = signal power
where
Ones the input signal is defined, it’s also defined its energy which is a constant given by
+∞
E=
∫
−∞
f 2 (t )dt =
1
2π
+∞
∫ F (ω )
2
dω
eq 295
−∞
The signal to noise ratio, we want to maximize, can be divided by the energy E without
altering the maximum S/N ratio determination. Therefore
⎧
⎪
⎛ g 2 (τ ) ⎞
⎪
⎟⎟ = max ⎨
max⎜⎜
⎝ E ⋅ PN ⎠
⎪ 1
⎪ 2π
⎩
⎫
⎧
⎪
⎪
∫−∞F (ω ) H (ω )e dω
⎪
⎪
⎬ = max ⎨
+∞
+∞
1 ε
2
2
⎪ 1
∫−∞ F (ω ) dω ⋅ 2π −∫∞ 2 H (ω ) ω ⎪⎪
⎪ 2π
⎭
⎩
1
2π
+∞
2
j ωt
⎫
⎪
∫−∞F (ω ) H (ω )e dω
⎪
⎬
+∞
+∞
ε
2
2
⎪
⋅
(
ω
)
ω
(
ω
)
ω
F
d
H
∫−∞
∫−∞ 2
⎪
⎭
+∞
2
j ωt
eq 296
202
In order to maximize the preceding ratio we can use the Schwarz theorem for complex
function integral:
2
+∞
∫ X (ω )Y (ω )dω
+∞
≤
−∞
∫ X (ω )
−∞
2
+∞
dω ⋅ ∫ Y (ω ) dω
2
eq 297
−∞
The “=” sign is applied only when
X (ω ) = kY ∗ (ω )
eq 298
so we have
2
+∞
∫ kY (ω )Y (ω )dω =
*
−∞
+∞
2
+∞
*
∫ kY (ω ) dω ⋅ ∫ Y (ω ) dω
−∞
2
eq 299
−∞
Where Y*(.) is the conjugate complex value of Y(.)
Therefore calling:
X (ω ) = H (ω )
eq 300
Y (ω ) = F (ω )e jω t
We can write
X (ω ) = H (ω ) = kY * (ω ) = kF * (ω )e − jω t
i.e. H (ω ) = kF * (ω )e − jω t
eq 301
Then substituting on the S/N ratio we can obtain the maximum value given by:
2
+∞
+∞
⎧
⎫
⎧ 1 +∞
⎫
1
2
2
j ωt
⎪
⎪
ω
ω
ω
F
H
e
d
(
)
(
)
ω
ω
ω
ω
⋅
F
d
H
d
(
)
(
)
⎪
⎪
∫
∫
∫
2π −∞
⎛ g 2 (τ ) ⎞
⎪
⎪
⎪ 2π −∞
⎪
−∞
⎟⎟ = max ⎨
max⎜⎜
⎬ = max ⎨
⎬=
+∞
+∞
+∞
+∞
⎝ E ⋅ PN ⎠
⎪ 1 F (ω ) 2 dω ⋅ 1 ε H (ω ) 2 ω ⎪
⎪ 1 F (ω ) 2 dω ⋅ 1 ε H (ω ) 2 ω ⎪
⎪ 2π −∫∞
⎪
⎪⎩ 2π −∫∞
⎪⎭
2π −∫∞ 2
2π −∫∞ 2
⎩
⎭
2
+∞
⎧
⎫
1
2
⎪
⎪
k ∫ F (ω ) dω
⎪ 2π −∞
⎪ 1
=
max ⎨
2⎬
+∞
⎪ 1 1 ε
⎪ ε
2
⎪ 2π 2π 2 k ∫ F (ω ) dω ⎪ 4π
−∞
⎩
⎭
203
Therefore this maximum S/N output correspond to a filter response given by
g max
k
=
2π
+∞
∫ F (ω )
2
dω = kE
eq 302
−∞
This is the optimum filter function to reveal the signal when white noise is present. If
we get k=1 then by Parseval theorem we can rewrite:
g max =
1
2π
+∞
∫ F (ω )
2
−∞
dω = ∫ f 2 (t )dt = E
eq 303
T
Where the second integral it has been extended to the duration T of the input signal.
Therefore, the optimum correlator receiver must to perform an integration, over the
signal period T, of the product between the input signal and the replica of the input
signal locally available. The term correlator follows by the correlation existing between
input signal and the locally available reference signal.
The reference signal (replica of input signal) can be obtained by PLL circuits. These
circuits have a bandwidth which can be reduced to a small bandwidth around the
carrier, thus the carrier can be extracted and can be used as a reference signal. Also
PLL circuits use the correlation.
From a general point of view we can say that the correlation detection is a way to use as
better as possible the known characteristics of the input signal (frequency. Shape, ..).
The equation for the correlation detection is:
g (t ) = ∫ v(t ) s R (t )dt
eq 304
T
Where
v(t)=s(t)+n(t) is the signal corrupted by noise
sR(t) is the reference replica signal obtained by use of PLL circuits
T= signal period
A blocks scheme of the correlator receiver is shown in figure below
204
v(t)=s(t)+n(t)
PLL
sR(t)
x
∫ (..)dt
g(t)
T
correlator
figure 157
The Modulation process must be conserve some power on the carrier (other to that on
the side band) in order to allow carrier extraction by the PLL circuits.
205
22 INTRODUCTION TO CDMA
22.1 Multiple Access
A cell in a cellular radio network could be seen as a multi-user communication system,
in which a large amount of users share a common physical resource to transmit and
receive information. The resource is the frequency band in the radio spectrum. There
are several different radio access techniques in which multiple users could send the
information through the common channel to the receiver:
FDMA
F
TDMA
FDMA
T
P
P - Power
T – Time
F - Frequency
F
T
CDMA
FDD
P
T
figure 158
In FDMA and TDMA the common channel is partitioned into orthogonal single user
subchannls. A problem arises if the data from the users accesing the network is bursty
in nature. A single user who has reserved a channel may transmit data irregularly so
that silent periods are even longer than transmission periods. For example, a speech
signal may contain long pauses. In such cases TDMA or FDMA tends to be inefficient
because a certain percentage of frequency or of the time slots allocated to the user
caries no information. An inefficiently designed multiple access system limits the
number of simultaneous users of the common communication channel.
206
One way of overcoming this problem is to allow more than one users to share the
channel or sub-channel by the use of spread spectrum signals. In this method each user
is assigned a unique code sequence or signature sequence that allow the user’s signal
to be spread on the common channel.
By designing these code sequence with relatively little cross correlation, the crosstalk
inherent in the demodulation signals received from multiple transmitters is minimized.
This multiple access method is called CODE DIVISION MULTIPLE ACCESS (CDMA)
22.2 Spread spectrum modulation
The general concept of spread spectrum modulation is presented in figure below:
Trasmitter
Receiver
Channel
Sn
Sn
ε()
n(t)
ε()=ε-1()
Sn
i(t)
figure 159: spread spectrum system concept
Formally the operation of both transmitter and receiver can be partitioned into two steps.
At the transmitter site:
• the first step is modulation in which the narrowband signal Sn, which occupies
frequency band Wi, is formed. In the modulation process, bit sequences of
length n are mapped to 2n different narrowband symbols constituting the
narrowband signal Sn.
• in the second step the spreading is carried out, in which the narrowband signal
Sn is spread in a large frequency band Wc. The spread signal is denoted by Sw,
and the spreading functions expressed as ε(). An example for spreading is
reported in figure below:
207
Bit period Tb
1
Data
-1
1
Spreading/expansion
code
-1
Expanded signal
= Data * Expansion code
1
-1
Chip period Tc
figure 160: spreading process
where:
Rb =
1
Tb
1
Rc =
Tc
BIT RATE;
Tc<<Tb and
Tb=N⋅Tc,
eq 305
CHIP RATE.
N i.e. the Rc/Rb, is defined as spreading factor, in the example above the spreading
factor is SF=8.
SF =
Rc Tb
=
Rb Tc
eq 306
208
A general CDMA modulating process can be represented as shown in figure below:
Antenna
Source of
information
B
Coding
Spreading
sequence
Modulator
O.L.
RF
signal
figure 161
At the receiver side the first step is dispreading, which can be formally represented by
the inversion function ε-1()=ε(). In dispreading, the wideband signal Sw, is converted
back to a narrowband signal Sn which can then be demodulated using digital
demodulation schemes.
The primary reason for going to the process of spreading and dispreading is to enable
the CDMA multiple access method, but due to the signal spreading and resulting
enlarged bandwidth, spread spectrum signals have many other interesting properties
that differ from those of narrowband signals. The most important are discussed in the
following section.
209
22.3 Tolerance to Narrowband Interference
A spread spectrum system is tolerant to narrowband interference, as shown in figure
below:
P[W/Hz]
P[W/Hz]
Sn
in
Despreading
iwr
Sw
iW
f0
fi
f [Hz]
f0
f [Hz]
fi
Wi
Wc
Wc
figure 162: dispreading process in the presence of interference
Assume that a signal Sw is received in the presence of a narrowband interference signal
in.
The despreading process can be presented as follows:
ε −1 (S w + in ) = ε −1 [ε (S n )] + ε −1 [in ] = S n + iw
eq 307
The dispreading operation converts the input signal into a sum of the useful narrowband
signal Sn and an interfering wideband signal iw.
210
After the dispreading operation a narrowband filtering (operation F()) is applied, with the
bandpass filter of bandwidth Bn equal to the bandwidth Wi of Sn , this result in:
F ( S n + iw ) = S n + F (iw ) = S n + iwr
eq 308
Only a small proportion of the interfering signal energy passes the filter and remains as
residual interference, because the bandwidth Wc of iw is much larger than Wi. The ratio
between the transmitted modulation bandwidth and the information signal bandwidth is
called processing gain, Gp:
Gp =
Wc
Wi
eq 309
To prevent any filter-or modulation-specific properties, from this point:
Wc=chip rate
Wì=bit rate
In WCDMA system the value of Wc is 3.84 Mcps which, owing to spectral sidel lobes,
results in 5 MHz carrier raster.
Its important to note that processing gain process is composed of the spreading part
and coding part.
22.4 Direct Sequence Spread Spectrum System
There are a number of techniques for spreading the information-bearing signal by use of
the code signals:
• Direct Sequence
• Frequency Hopping
• Time Hopping
The most common technique used in cellular radio networks is DS (Direct Sequence
Spread Spectrum).
In this system the signal spreading is achieved by modulating
data-modulated signal a second time by a wideband spreading signal.
the
The wideband spreading signal has to be approximated closely to a random signal with
uniform distribution of the symbols. Typical representatives of such signal in digital form
are pseudonoise (PN) sequence over a finite alphabet.
211
Since the WCDMA system has to maximize system capacity during the spreading, the
operation is done in two phases:
•
•
In the first the user signal is spread by the channelisation code. This is called
the Orthogonal Variable Spreading Factor (OVSF) Code, its construction is
based on the Hadmard Matrix. The code has the property that two different codes
from the family are perfectly orthogonal if in phase. Thus, its use guarantees
maximum capacity, measured by the number of active users. The channelization
operation, transforms every data symbol into a number of chips, thus increasing
the bandwidth of the signal. The number of chips per data symbol is called the
Spreading Factor (SF).
In the second, all the spread users’signals are scrambled by the cell specific
scrambling sequence, which has the statistical properties of random sequence.
The second operation is the scrambling operation, where a scrambling code is
applied to the spread signal.
Channelisation
code
Scrambling
code
Data
Bit rate
Chip rate
Chip rate
figure 163
22.4.1
Channelization operation
In 3GPP the OVSF codes used for different symbol rates are uniquely described as
Cch,SF,k, where SF is the Spreading Factor of the code and k is the code number
(0 ≤ k ≤ SF - 1). Each level of the code tree defines the channelization codes of length
SF, where SF is the spreading factor of the codes.
The channelization codes have orthogonal properties and are used for separating the
information transmitted from a single source, i.e.
• different connections within one cell in the downlink (thus reducing the own
interference),
• dedicated physical data channels from one UE in the uplink.
In the downlink the OVSF codes are a limited resources and need to be managed by
the radio network controller, whereas in the uplink such a problem does not exist.
The OVSF codes are effective only when the channels are perfectly synchronized at
chip level (the loss in crosscorrelation, e.g. due to multipath, is compensated for by the
additional scrambling operation).
212
22.4.1.1
Channelization codes (OVSF codes) generation
The channelization codes are OVSF (Orthogonal Variable Spreading Factor) codes
that preserve the orthogonality between a user’s different physical channels. The OVSF
codes can be defined using the code tree of figure below:
( Cch, 2, 0 , Cch, 2, 0 )
Cch, 8, 0 = (1, 1, 1, 1, 1, 1, 1, 1)
( Cch, 2, 0 , - Cch, 2, 0 )
Cch, 4, 0 = (1, 1, 1, 1)
Cch, 8, 1 = (1, 1, 1, 1, -1, -1, -1, -1)
Cch, 2, 0 = (1, 1)
Cch, 8, 2 = (1, 1, -1, -1, 1, 1, -1, -1)
Cch, 4, 1 = (1, 1, -1, -1)
Cch, 8, 3 = (1, 1, -1, -1, -1, -1, 1, 1)
Cch, 1, 0 = (1)
( Cch, 2, 1 , Cch, 2, 1 )
Cch, 8, 4 = (1, -1, 1, -1, 1, -1, 1, -1)
Cch, 4, 2 = (1, -1, 1, -1)
Cch, 2, 1 = (1, -1)
Cch, 8, 6 = (1, -1, -1, 1, 1, -1, -1, 1)
Cch, 4, 3 = (1, -1, -1, 1)
( Cch, 2, 1 , - Cch, 2, 1 )
SF = 1
Cch, 8, 5 = (1, -1, 1, -1, -1, 1, -1, 1)
Cch, 8, 7 = (1, -1, -1, 1, -1, 1, 1, -1)
SF = 2
SF = 8
SF = 4
figure 164
Each level in the code tree defines channelization codes of length SF, corresponding to
a spreading factor SF. The channelization codes are Welsh codes. Their generation
method, which is based on the Hadamard matrix is shown in figure below:
⎧
⎪
⎪
⎪
⎪
⎪
⎨
⎪
⎪
⎪
⎪
⎪⎩
C ch,1,0 = 1
⎡Cch , 2, 0 ⎤ ⎡Cch ,1, 0 Cch ,1,0 ⎤ ⎡1
⎢
⎥=⎢
⎥=⎢
⎣Cch , 2,1 ⎦ ⎣Cch ,1, 0 − Cch ,1, 0 ⎦ ⎣1
⎡Cch ,3, 0 ⎤ ⎡ Cch , 2, 0 Cch , 2, 0 ⎤ ⎡ 1 1
⎢C
⎥ ⎢
⎥ ⎢
⎢ ch ,3,1 ⎥ = ⎢Cch , 2,0 − Cch , 2, 0 ⎥ = ⎢ 1 1
⎢Cch ,3, 2 ⎥ ⎢ Cch , 2,1 Cch , 2,1 ⎥ ⎢ 1 − 1
⎢
⎥ ⎢
⎥ ⎢
⎣Cch ,3,3 ⎦ ⎣ Cch , 2,1 − Cch , 2,1 ⎦ ⎣ 1 − 1
...
1⎤
− 1⎥⎦
1 1 ⎤
− 1 − 1⎥⎥
1 − 1⎥
⎥
− 1 1⎦
figure 165
It is easy to verify that all the codes with the same SF are orthogonal, i.e. they fulfil the
orthogonality condition specified by equation:
213
SF −1
∑S
k =0
1, k
⋅ S 2, k = 0
eq 310
This orthogonality, however, is not guaranteed between a generic code and the codes
belonging to its subtree. As a consequence, the selection of one code, blocks the
corresponding subtree.
22.4.2
Scrambling operation
The second operation is the scrambling operation, where a scrambling code is
applied on top of the spread signal, so it does not change the signal bandwidth but only
makes the signals from different sources separable from each other. With the
scrambling, it would not matter if the actual spreading were performed with identical
codes for several transmitters.
With the scrambling operation the real (I) part imaginary (Q) parts of the spread signal
are further multiplied by a complex-valued scrambling code.
The scrambling codes are used to
• separate different cells in the downlink,
• separate different terminals in the uplink.
The scrambling codes have good correlation properties (interference averaging) and
are always used on top of spreading codes, thus not affecting the transmission
bandwidth.
22.5 Orthogonal sequences reminder
Let us consider two finit energy signals s1 (t ) and s2 (t ) defined in the interval [a, b].
The AUTOCORRELATION Ri i (τ ) of the finite energy signal si (t ) (i = 1, 2) is defined
as
b
Ri i (τ ) =ˆ ∫ si (t + τ ) si∗ (t ) dt
eq 311
a
The CROSS CORRELATIONS R1 2 (τ ) and R2 1 (τ ) between the finite energy signals
s1 (t ) and s2 (t ) are defined as
b
R1 2 (τ ) =ˆ ∫ s1 (t + τ ) s2∗ (t ) dt
eq 312
a
and
b
R2 1 (τ ) =ˆ ∫ s2 (t + τ ) s1∗ (t ) dt
eq 313
a
214
Definition:
The finite energy signals s1 (t ) and s2 (t ) are ORTHOGONAL ⇔ R1 2 (0) = 0 ⇔
R2 1 (0) = 0 .
In other words, the finite energy signals s1 (t ) and s2 (t ) are ORTHOGONAL ⇔
b
b
∫ s (t ) s (t ) dt = 0 ⇔ ∫ s (t ) s (t ) dt = 0
1
∗
2
2
a
∗
1
eq 314
a
Let us now suppose that s1 (t ) and s2 (t ) are two channelisation sequences with the
same SF, as shown in figure below. We will show that
SF −1
the sequences s1 (t ) and s2 (t ) are ORTHOGONAL ⇔ ∑ S1, k ⋅ S 2, k = 0
k =0
Note:
SF −1
The term
∑S
k =0
1, k
⋅ S 2, k is also called the cross-product between the two
sequences. If we indicate
[
=ˆ [S
S1 =ˆ S1, 1 , S1, 2 , LS1, SF −1
S2
2, 1
, S 2, 2 , LS 2, SF −1
]
]
eq 315
the cross-product between the two sequences can also be indicated as
S1 ⋅ S 2T
eq 316
Proof:
The sequences s1 (t ) and s2 (t ) are ORTHOGONAL ⇔
∫ s (t ) s (t ) dt = 0 ⇔
1
∗
2
Tb
⇔
SF −1
∑S
k =0
1, k
SF −1
⋅ S 2, k ⋅ Tc = 0 ⇔ ∑ S1, k ⋅ S 2, k = 0
eq 317
k =0
215
Tb (One data symbol, SF chips)
Tc
0
S1, 0
S1, 1
S1, 2
S1, SF-1
s1 (t )
S2, 0
S2, 1
S2, 2
S2, SF-1
s2 (t )
Tc
2Tc
(SF-1)Tc
figure 166
22.6 Modulation and Tolerance to Wideband Interference
Figure below depict the basic operations of spreading and dispreading for DS-CDMA
system.
User data is here assumed to be a BPSK-modulated bit sequence of rate R, the user
data bit assuming the value of ±1. The spreading operation, in this example, is the
multiplication of each user data bit with a sequence of 8 code bits, called chips. The
resulting spread is at rate of 8xR, and has the same random (pseudo-noise like)
appearance as the spreading code.
During despreading we multiply the spread user data/chip sequence, bit by bit duration,
with the very same 8 code chips as we used during the spreading of this bits. As shown
the original user bit sequence has been recovered perfectly, provided we have also
perfect synchronization between the spread user signal and the despreading code.
The correlation receiver integrates the resulting products (data x code) for each user bit.
216
No interference scenario
Data
11
-11
Spreading
Spreding code
11
-11
Spreding signal=Data x code
11
-11
DeSpreading
Spreding code
11
-11
Data=spreading code x spreading signal
11
-11
88
Correlation result
-8
figure 167
Figure below show the effect of despreading operation when applied to the CDMA
signal of another user whose signal is assumed to have been spread with a different
spreading code. The result of multiplying the interfering signal with the own code and
integrating the resulting products leads to interfering signal values lingering around 0.
The basic idea is that the receiver works as a correlation receiver, which means that it
correlates a known (reference) code with an incoming signal that is composed of
several different CDMA signal (from different users or channels), with general
interference (from other RF systems), and with a noise (of thermal nature).
The output from the receiver is in the form of the autocorrelation function of the wanted
signal.
217
Interference example
Other interfering signal
11
-11
Spreding code
11
-11
Data after multiplication
11
-11
88
Correlation result
-88
figure 168
As can be seen, the amplitude of the own signal (correlation result in graphics)
increases on average by a factor of 8 relative to that of the user of the other interfering
system, i.e. the correlation detection has raised the desired user signal by the spreading
factor, here 8, from the interference presenting the CDMA system. This effect is termed
“processing gain” and is a fundamental aspect of all CDMA systems, and in general of
all spread spectrum system.
Processing gain is what gives CDMA systems the robustness against-interference that
is necessary in order to reuse the available 5 MHz carrier frequencies over
geographically close distances.
Let’s take an example with real WCDMA parameters. Speech service with a bit rate of
12.2 kbps has a processing gain of:
⎡ Rc ⎤
⎡ 3.84 ⋅10 6 ⎤
⎡ Chip _ rate ⎤
=
=
Pg = 10 Log ⎢
10
Log
10
Log
= 25dB
⎢ ⎥
⎢
⎥
3 ⎥
⎣ Bit _ rate ⎦
⎣ 12.2 ⋅10 ⎦
⎣ Rb ⎦
eq 318
After despreading, the signal power needs to be typically a few decibel above the
interference and noise power. The required power density over the interference power
density after despreading is designated as Eb/N0, where Eb is the energy, or power
density, per user bit and N0 is the interference and noise power density.
For speech service the ratio Eb/N0 is typically in the order of 5.0 dB, and the required
wideband signal to interference ratio C/I is therefore 5.0 dB minus the processing gain
i.e.
C
(dB) wdeband = 5dB − 25dB = −20dB
I
eq 319
218
In other words, the signal power can be 20 dB under the interference or thermal noise
power, and the WCDMA receiver can still detect the signal.
Due to spreading and despreading, C/I can be lower in WCDMA than, for example, in
GSM. A good quality speech connection in GSM requires C/I=9-10 dB.
Since the wideband signal can be around the thermal noise level, its detection is difficult
without knowledge of the spreading sequence. For this reason spread spectrum
systems were originated in military applications where the wideband nature of the signal
allowed have to be hidden below omnipresent thermal noise.
It should be observed that the more is the bit rate Rb, the lower is Pg(dB), therefore
higher bit-rate service require an increasing C/I.
Rb
(Kbit/sec)
12.2
64
384
2000
Pg
314.7541
60
10
1.92
Pg(dB)
25.0
17.8
10.0
2.8
table 8
It should be also observed that the processing gain comes at the price of an increased
transmission bandwidth (by the amount of the processing gain).
22.7 Uplink Modulation
In the uplink direction there are basically two additional terminal-oriented criteria that
need to be taken into account in the definition of the modulation and spreading
methods.
The uplink modulation should be designed so that the terminal amplifier efficiency is
maximized and/or the audible interference from the terminal is minimized.
Discontinuosus uplink transmission can cause audible interference to audio equipment
that is very close to the terminal; this is a completely separate issue from the
interference in the air interface. With GSM operation we are familiar with the occasional
audible interference with audio equipment that is not properly protected. The
interference from GSM has a frequency of 217 Hz, which is determined, by the GSM
frame frequency. With WCDMA system, the same issues arise when discontinuous
uplink transmission is used, for example with a speech service. During the silent period
no information bits need to be transmitted, only the information for link maintenance
purposes, such as power control with a 1.5 KHz command rate. With such a rate the
transmission of the pilot and the power control symbols with time multiplexing in the
uplink direction would cause audible interference in the middle of the telephony voice
219
frequency band. Therefore in WCDMA uplink the two dedicated physical channel are
not time multiplexed but I-Q/code multiplexing is used.
The continuous transmission achieved with an I-Q/code multiplexed control channel is
shown in figure below.
Data
(DPDCH)
DTX Period
Dedicate Phisical Data
Channel
User Data
(DPDCH)
Dedicate Phisical Data
Channel
Phisical Layer Control Information
(DPCCH)
Dedicate Phisical Control Channel
figure 169 : parallel transmission of DPDCH and DPCCH when data is present/absent (DTX)
Now, as the pilot and the power control signaling are maintained on a separate
continuous channel, non pulsed transmission occurs. The only pulse occurs when the
data channel DPDCH is switched on and off, but such switching has happens quite
seldom. For the best possible power amplifier efficiency, the terminal transmission
should have as low-peak-to-average ratio (PAR) as possible to allow terminal to operate
with a minimal amplifier back-off requirement.
With the I-Q/code multiplexing, also called dual-channel QPSK modulation, the
power level of the DPDCH and DPCCH are typically different, especially as data
rates increase, and would lead in extreme case to a BPSK-type transmission
when transmitting the branches independently. This has been avoided by using a
complex-valued scrambling operation after the spreading with channelisation
codes.
The signal constellation of the I-Q/code multiplexing before complex scrambling is
shown in figure below, the same constellation is obtained after descrambling in the
receiver for data detection.
Q
Q
G=0.5
I
G=1
I
figure 170: Constellation of I-Q/code multiplexing before complex scrambling, G denotes the relative gain
factor between DPCCH and DPDCH
220
Figure below illustrates the principle of the uplink spreading of DPCCH and DPDCHs.
The binary DPCCH and DPDCHs to be spread are represented by real-valued
sequences, i.e. the binary value "0" is mapped to the real value +1, while the binary
value "1" is mapped to the real value –1. The DPCCH is spread to the chip rate by the
channelization code cc, while the n-th DPDCH called DPDCHn is spread to the chip rate
by the channelization code cd,n. One DPCCH and up to six parallel DPDCHs can be
transmitted simultaneously, i.e. 1 ≤ n ≤ 6.
cd,1
βd
cd,3
βd
DPDCH1
Σ
DPDCH3
cd,5
I
βd
DPDCH5
Sdpch,n
I+jQ
cd,2
βd
cd,4
βd
cd,6
βd
cc
βc
S
DPDCH2
DPDCH4
DPDCH6
Σ
Q
j
DPCCH
figure 171: Spreading for uplink DPCCH and DPDCHs
After channelization, the real-valued spread signals are weighted by gain factors, βc for
DPCCH and βd for all DPDCHs.
At every instant in time, at least one of the values βc and βd has the amplitude 1.0. The
β-values are quantized into 4 bit words. The quantization steps are given in table below.
221
Signalling values for
βc and βd
15
14
13
12
11
10
9
8
7
6
5
4
3
2
1
0
Quantized amplitude ratios
βc and βd
1.0
14/15
13/15
12/15
11/15
10/15
9/15
8/15
7/15
6/15
5/15
4/15
3/15
2/15
1/15
Switch off
table 9: The quantization of the gain parameters
After the weighting, the stream of real-valued chips on the I- and Q-branches are then
summed and treated as a complex-valued stream of chips. This complex-valued signal
is then scrambled by the complex-valued scrambling code Sdpch,n. The scrambling code
is applied aligned with the radio frames, i.e. the first scrambling chip corresponds to the
beginning of a radio frame.
In the uplink, the complex-valued chip sequence generated by the spreading process (
spreding phase + scrambling phase) is QPSK modulated as shown in Figure below:
cos(ωt)
Complexvalued chip
sequence from
spreading
operations
S
Split
real
&
imag
Re{S}
Pulseshaping
Im{S}
Pulseshaping
-sin(ωt)
figure 172: Uplink Modulation
222
22.7.1
One UL parallel channel
Let us start by considering only one of two parallel channels,
SC=Scrambing Code
I
DPDCH OFF
I+jQ
S
Q
DPCCH
Cc
βc
Chanelisation
Code
j
figure 173: Only the DPCCH channel is active
Supposing the gain factor parameter equal to one: βc=1; then the signal can assume
only the values ±1 along the Q axes i.e. ±1j, in other word we are obtaining a BPSK
constellation.
Q
I
figure 174: BPSK modulation constellation
223
In order to minimize the zero crossing by the vector constellation, we are using the
scrambling codes which are formed in such a way that the rotations between
consecutive chips within one symbol period are limited to ±90°. The full 180° rotation
can happen only between consecutive symbols. This method further reduces the peakto-peak-average ratio of the transmitted signal from the normal QPSK transmission.
The scrambling codes, during the chip time, can assume only the values:
(1+j); (1-j); (-1+j); (-1-j);
which once multiplicand by the expanded code signal yield:
j ⋅ (1 + j ) = −1 + j
j ⋅ (1 − j ) = 1 + j
j ⋅ (− 1 + j ) = −1 − j
j ⋅ (− 1 − j ) = 1 − j
−
−
−
−
j ⋅ (1 + j ) = 1 − j
j ⋅ (1 − j ) = −1 − j
j ⋅ (− 1 + j ) = 1 + j
j ⋅ (− 1 − j ) = 1 − j
eq 320
As a consequence the vector constellation is no longer a BPSK constellation but a
balanced QPSK constellation.
Q
-1+j
1-j
1+j
1+j
I
-1-j
1-j
-1-j
1-j
figure 175: balanced QPSK constellation
224
22.7.2
Two UL parallel channel
As a second analysis case let us consider the transmission of two parallel channels,
DPDCH (dedicated physical data channel) and DPCCH (dedicated physical control
channel):
cd
βd
Sc
I
DPDCH
I+jQ
S
Q
DPCCH
cc
βc
j
figure 176
Consider the peak-to-average power ratio (PAR=crest factor) defined as the ratio
between the peak and average power.
The amplifier efficiency is maximized when the peak-to-average power ratio
(PAR=crest factor) is minimized. This mean that the mobile phone amplifier can
operate with a minimum back-off, in other word with a minimum output power reduction
with respect to the maximum output power allowed.
The peak-to-average power ratio (PAR=crest factor) is affected and degraded by
power unbalance of I and Q channels, notably in phase and quadrature component of
the signal. To minimize peak-to-average power ratio (PAR=crest factor) is required a
balanced QPSK constellation.
The power ratio between Q and I component is called G=βc/βd
The multicode transmission of more channels increases the peak-to-average power
ratio (PAR=crest factor) and, as in the case of one channel, the Scrambling code
application at the end, transform the Unbalanceed-QPSK into a Balanced-QPSK.
In such a way the efficiency of the power amplifier remains constant irrespective of the
power difference G=βc/βd between DPCCH and DPDCH.
This can be explained by figure below, which show the signal constellation for
I-Q/code multiplexed control channel with complex spreading.
There are three case study in which we use/not use scrambling operation:
•
•
•
one with G=βc/βd=0 dB i.e. βd=βc=1
one with G=βc/βd=-6 dB i.e. βd=1 βc=1/2
one with G=βc/βd=-10 dB
225
22.7.2.1
No scrambling code operation
When no scrambling code are used, we obtain an unbalance QPSK which is poorly
efficient from the amplifier point of view; this is shown in simulation below :
Q
Q
1
2
I
I
No scrambling code are used
Unbalance QPSK
G=βc/βd=-6 dB
No scrambling code are used
G=βc/βd=0 dB
In this condition especially for G= -6 dB the peak-to-average power ratio (PAR=crest
factor) is very poor
22.7.2.2
Scrambling code operation
When scrambling code are used, then even when G=βc/βd≠0 dB we obtain always a
balance rotated QPSK.
Thus, the signal envelope variations with complex spreading, are very similar to a
balanced QPSK transmission for all value of G=βc/βd:
•
G=βc/βd=0 dB i.e. βd=βc=1
Multiplication of signal and scrambling code yield:
226
(1 +
(1 +
(1 +
(1 +
j ) ⋅ (1 + j ) = 2 j
j ) ⋅ (1 − j ) = 2
j ) ⋅ (− 1 + j ) = −2
j ) ⋅ (− 1 − j ) = −2 j
(− 1 +
(− 1 +
(− 1 +
(− 1 +
j ) ⋅ (1 + j ) = −2 j
j ) ⋅ (1 − j ) = −2
j ) ⋅ (− 1 + j ) = 2
j ) ⋅ (− 1 − j ) = 2 j
(1 − j ) ⋅ (1 + j ) = 2
(1 − j ) ⋅ (1 − j ) = −2 j
(1 − j ) ⋅ (− 1 + j ) = 2 j
(1 − j ) ⋅ (− 1 − j ) = −2
Q
1
2
I
(− 1 − j ) ⋅ (1 + j ) = −2 j
(− 1 − j ) ⋅ (1 − j ) = −2
(− 1 − j ) ⋅ (− 1 + j ) = 2
(− 1 − j ) ⋅ (− 1 − j ) = 2 j
figure 177
In this example from constellation point of view, it doesn’t appear clearly the difference
between no scrambling and scrambling application.
The difference appears more clearly by considering G≠0 dB as in the following
examples:
•
G=βc/βd=-6 dB i.e. βd=1 βc=1/2
In this case the Q component is half of I component and the scrambling code operation
give the following:
1 3
⎛ 1 ⎞
1 ⎞
1 3
⎛
⎜1 + j ⎟ ⋅ (1 + j ) = + j
− 1 − j ⎟ ⋅ (1 + j ) = − − j
⎜
2
2
2
⎝
⎠
2 ⎠
2 2
⎝
Q
3 1
⎛ 1 ⎞
1
3
1
⎛
⎞
(
)
+
1
j
1
j
j
⋅
−
=
−
⎜
⎟
⎜ − 1 − j ⎟ ⋅ (1 − j ) = − + j
2 2
⎝ 2 ⎠
2 ⎠
2 2
⎝
3 1
⎛ 1 ⎞
1
3 1
⎜1 + j ⎟ ⋅ (− 1 + j ) = − + j ⎛⎜ − 1 − j ⎞⎟ ⋅ (− 1 + j ) = − j
2 2
2 ⎠
2 2
⎝ 2 ⎠
⎝
1 3
1 ⎞
1 3
⎛ 1 ⎞
⎛
⎜1 + j ⎟ ⋅ (− 1 − j ) = − − j ⎜ − 1 − j ⎟ ⋅ (− 1 − j ) = + j
2 2
2 ⎠
2 2
⎝ 2 ⎠
⎝
I
⎛ 1
⎜1 −
⎝ 2
⎛ 1
⎜1 −
⎝ 2
⎛ 1
⎜1 −
⎝ 2
⎛ 1
⎜1 −
⎝ 2
3 1
⎞
j ⎟ ⋅ (1 + j ) = − − j
2 2
⎠
1 3
⎞
j ⎟ ⋅ (1 − j ) = − j
2 2
⎠
1 3
⎞
j ⎟ ⋅ (− 1 + j ) = − + j
2 2
⎠
3 1
⎞
j ⎟ ⋅ (− 1 − j ) = + j
2 2
⎠
1
⎛
⎜ −1 +
2
⎝
1
⎛
⎜ −1 +
2
⎝
1
⎛
⎜ −1 +
2
⎝
3 1
⎞
j ⎟ ⋅ (1 + j ) = + j
2 2
⎠
1 3
⎞
j ⎟ ⋅ (1 − j ) = − + j
2 2
⎠
1 3
⎞
j ⎟ ⋅ (− 1 + j ) = − j
2 2
⎠
1 ⎞
3 1
⎛
⎜ − 1 + j ⎟ ⋅ (− 1 − j ) = − − j
2 ⎠
2 2
⎝
figure 178
227
scrambling code are used;
Unbalance QPSK;
G=βd/βc=0 dB
scrambling code are used;
Unbalance QPSK;
G=βd/βc=6 dB
figure 179
•
G=βc/βd=-10 dB and G=βc/βd=-20 dB
scrambling code are used;
Unbalance QPSK;
G=βd/βc=10 dB
scrambling code are used;
Unbalance QPSK;
G=βd/βc=20 dB
figure 180
228
The I-Q/code multiplexing solution with complex scrambling result in a power amplifier
output back-off requirements that remain constant as a function of the power difference
between DPDCH and DPCCH.
The power difference between DPDCH and DPCCH has been quantified in UTRA
physical layer specifications to 4-bit words, i.e. 16 different values. At a given point in
time the gain value for either DPDCH or DPCCH is set to 1 and then for the other
channels a value between 0 and 1 is applied to reflect the desired power difference
between channels.
Limiting the number of possible values to 4-bit representation is necessary to make the
terminal transmitter implementation simple. The power difference can have 15 different
values between -23.5 dB and 0 dB and one bit combination for non DPDCH when there
is non data to be transmitted.
UTRA will face challenges in amplifier efficiency when compared to GSM. The GSM
modulation is GMSK (Gaussian Minimum Khift Leyng) which has a constant envelope
and is thus optimized for amplifier peak-to-average ratio. As a narrowband system, the
GSM signal can be spread relatively more widely in the frequency domain.
This allows the use of a less linear amplifier with better power conversion efficiency.
Narrowband amplifiers are also easier to linearize if necessary. In practice, the
efficiency of the WCDMA power amplifier is slightly lower than that of the GSM
power amplifier. On the other hand, WCDMA uses fast power control in the uplink,
which reduces the average required transmission power.
229
22.7.3
Three UL parallel channel
Using three parallel channel one DPCCH and two DPDCH, we have the following
scheme:
cd,1
βd
DPDCH1
SC
I
cd,6
βd
cc
βc
I+jQ
S
DPDCH2
DPCCH
Σ
Q
j
figure 181
22.7.3.1
No Scrambling Code Operation
Supposing βc=βd=1; than on the I branch the normalized signal value are the same i.e.
±1.
Diversely on the Q branch the amplitude of two channel DPDCH and DPCCH channels
is added, therefore the chip to chip sum give four possible values: (1+1)=2; (1-1)=0; (1+1)=0; (-1-1)=-2.
Obviously the complex value on the Q branch is obtained multiplying by j, therefore the
possible values for the branch are (2J, 0 ,-2J).
The corresponding constellation and spectrum FFT of the output modulated RF signal
are:
230
Q
+2
j
I
-1
1
2j
figure 182: FFT and constellation obtained with 1 DPCCH + 2 DPDCH, βc=βd=1 e without SC
The constellation points coordinates are: (1+0j) (-1+0j) (1+2j) (-1+2j) (1-2j) (-1-2j).
The WINIQ configuration is shown below:
figure 183: configuration without scrambling code
231
22.7.3.2
Scrambling Code Operation
Multiplying I+jQ signal by scrambling code, we get the following result:
(1 + 0 j ) ⋅ (1 + j ) = +1 + j
(1 + 0 j ) ⋅ (1 − j ) = +1 − j
(1 + 0 j ) ⋅ (− 1 + j ) = −1 + j
(1 + 0 j ) ⋅ (− 1 − j ) = −1 − j
(− 1 + 0 j ) ⋅ (1 + j ) = −1 − j
(− 1 + 0 j ) ⋅ (1 − j ) = −1 + j
(− 1 + 0 j ) ⋅ (− 1 + j ) = +1 −
(− 1 + 0 j ) ⋅ (− 1 − j ) = +1 +
(1 + 2 j ) ⋅ (1 + j ) = +1 + j + 2 j − 2 = −1 + 3 j
(1 + 2 j ) ⋅ (1 − j ) = +1 − j + 2 j + 2 = 3 + j
(1 + 2 j ) ⋅ (− 1 + j ) = −1 + j − 2 j − 2 = −3 − j
(1 + 2 j ) ⋅ (− 1 − j ) = −1 − j − 2 j + 2 = 1 − 3 j
(− 1 + 2 j ) ⋅ (1 + j ) = −1 − j + 2 j − 2 = −3 + j
(− 1 + 2 j ) ⋅ (1 − j ) = −1 + j + 2 j + 2 = 1 + 3 j
(− 1 + 2 j ) ⋅ (− 1 + j ) = +1 − j − 2 j − 2 = −1 − 3 j
(− 1 + 2 j ) ⋅ (− 1 − j ) = +1 + j − 2 j + 2 = 3 − j
(1 − 2 j ) ⋅ (1 + j ) = +1 + j − 2 j + 2 = +3 − j
(1 − 2 j ) ⋅ (1 − j ) = +1 − j − 2 j − 2 = −1 − 3 j
(1 − 2 j ) ⋅ (− 1 + j ) = −1 + j + 2 j + 2 = +1 + 3 j
(1 − 2 j ) ⋅ (− 1 − j ) = −1 − j + 2 j − 2 = −3 + j
(− 1 − 2 j ) ⋅ (1 + j ) = −1 − j − 2 j + 2 = +1 − 3 j
(− 1 − 2 j ) ⋅ (1 − j ) = −1 + j − 2 j − 2 = −3 − j
(− 1 − 2 j ) ⋅ (− 1 + j ) = +1 − j + 2 j + 2 = +3 + j
(− 1 − 2 j ) ⋅ (− 1 − j ) = +1 + j + 2 j − 2 = −1 + 3 j
j
j
Q
1
2
3
I
figure 184: constellation obtained with 1 DPCCH + 2 DPDCH, ( βc=βd=1 e with SC
232
Simulations by WINIQ software are shown below:
figure 185: configuration of channels with scrambling code
figure 186: constellation obtained with 1 DPCCH + 2 DPDCH, βc=βd=1 e with SC
The output amplitude as well as the constellation configuration is changed; this
constellation permits a more efficient use of final amplifier.
233
figure 187: FFT magnitude and Eye Diagram of constellation obtained with 1 DPCCH + 2 DPDCH, βc=βd=1
e with SC.
22.7.3.2.1
Changing of the βc and βd
The changes of βc=βd bring to a different constellation, for instance if we get
DPCCH+DPDCH1+DPDCH2 and βc=1/2, βd=1 e SC long, then the constellation is:
figure 188: configuration panel
234
S
figure 189: constellation and vector constellation with: DPCCH+DPDCH1+DPDCH2 and βc=1/2, βd=1 e SC
long
figure 190: FFT Magnitude and Eye I(channel) figure with :DPCCH+DPDCH1+DPDCH2 and βc=1/2, βd=1
and SC long
235
From figure above we note that the FFT magnitude remains the same for both
configurations i.e. βc=1, βd=1 and βc=1/2, βd=1.
22.7.4
Filtering
Until now we have been considered transmission without any kind of filtering action.
Because we have no-unlimited bandwidth we must consider a filtering system, thus
reducing the bandwidth and simultaneously without introducing to much inter-symbol
interference.
Choosing a Rised Cosine Filter with r=0.22 in Tx end Rx we obtain the following:
figure 191: panel configuration
figure 192: FFT Magnitude and Eye I(channel) figure with :DPCCH+DPDCH1+DPDCH2 and βc=1/2, βd=1
and SC long and Tx/Rx Rised Cosine Filter with Rolloff Factor r=0.22
236
figure 193: constellation and vector constellation with: DPCCH+DPDCH1+DPDCH2 and βc=1/2, βd=1 and SC
long and Tx/Rx Rised Cosine Filter with Rolloff Factor r=0.22.
After filtering operation we can observe haw the bandwidth has been limited to
approximately 5(Mhz) ≅3.84*(1+0.22) but at the same time the Intersymbol interference
has been increased. Choosing a rolloff factor r=0.62 the situation became the following:
237
22.8 Downlink Spreading and Modulation
The spreading and scrambling concept for all downlink physical channels is illustrated in
figure below.
P-SCH
Gp
S-SCH
Any d-link
phisical
channel
except SCH
Seri
al to
Para
llel
con
Cos(ωt)
Sdl,n
I
I+jQ
cch,SF,m
GS
I
S
Q
G1
DL modulated
signal
Q
-sin(ωt)
J
G2
figure 194 : spreading and scrambling scheme for all downlink physical channel
Apart from SCHs, each pair of to consecutive symbols is first serial-to-parallel converted
and mapped onto I and Q branches. The I and Q branches are then spread to the chip
rate by the same channelisation code Cch,SF,m. The sequence of real-valued chips on
the I and Q branches are then scrambled using a complex-valued scrambling code,
denoted Sdl,n . The scrambling code is applied aligned with the scrambling code applied
to the P-CCPCH, where the first complex chip of the spread P-CCPCH frame is
multiplied by chip number zero of the scrambling code.
After spreading, each physical downlink channel (except SCHs) is separately weighted
by a weigh factor, denoted Gi. The comlex-valued P-SCH and S-SCH are separately
weighted by weight factor GP and GS.
All downlink physical channel are combined using a complex addition and the resulting
sequence generated by spreading and scrambling process is then QPSK modulated.
22.8.1
Downlink Spreading Codes
In the downlink the same channelisation codes as in the uplink (OVSF codes) are used.
Typically only one code tree per cell is used and the code tree under a single
scrambling code is then shared between several users.
By definition, the channelisation codes used for P-CPICH and P-CCPCH are Cch,256,0
and Cch,256,1 respectively.
In compressed mode there are three methods for generating gaps:
238
•
•
•
Rate matching
Reduction of the spreading factor by a factor of 2
higher-layer scheduling.
When the mechanism for opening the gap is to reduce the SF by factor of 2, the OVSF
code used for compressed frames is Cch,SF/2,[n/2] if and ordinary scrambling code is used,
and Cch,SF/2,n mod SF/2 if an alternative scrambling code is used where, Cch,SF,n is the
channelisation code used for non compressed frames.
In the downlink the SF of the dedicated physical channel does not vary on
frame-by-frame basis.
The dedicated physical channel (DPCH) structure is shown in figure below. In this
model each two-bit pair represents an I/Q pair of QPSK modulation (symbol).
As shown in the figure, the frame structure consists of a sequence of radio frames.
One radio frame (10 ms, 38400 chips) corresponds to 15 slots and one slot
corresponds to 2560 chips 1 (2/3 ms, i.e. 0.667 ms 2), which equals one power control
period (PC period).
N.B.: 38400 chips in 10 ms ⇒ 3840000
chips/second, i.e. 3.84 Mchips/second
Radio frame
(10 ms, 38400 chips)
#0
#1
# 71
#1
# 14
Slot (i.e. one PC period)
(0.667 ms, 2560 chips)
#0
Data
DPDCH
Uplink
structure
DPCCH
Pilot
TFCI
FBI
TPC
I/Q code
multiplexed
with complex
scrambling
Time multiplexed with complex scrambling
Downlink
structure
Data
DPDCH
TPC
TFCI
DPCCH
Data
Pilot
DPDCH
DPCCH
The data rate variation on the DPCH is managed by a rate-matching operation or by L1
discontinuous transmission (DTX), where the transmission is interrupted during a part of
the DPDCH slot.
In the case of multicode transmission, the parallel code channels have different
channelisation codes but the same spreading factor under the same scrambling code.
1
2
38400 chips / 15 slots = 2560 chips/slot.
10 ms / 15 slots = 2/3 ms/slot, i.e. 0.667 ms/slot
239
Different spreading factors may employed in the case of several CCTrCHs received by
the same UE.
The OVSF code my vary from frame to frame on the PDSCH. The rule is that the OVSF
code(s) below the smallest spreading factor is from the branch of the code tree pointed
by the code with smallest spreading factor used for that connection.
240
23 ORTHOGONAL FREQUENCY DIVISION MULTIPLEXING
(OFDM)
23.1 Introduction
Research has just recently begun on the development of 4th generation (4G) mobile
communication systems. The commercial rollout of these systems is likely to begin
around 2008 - 2012, and will replace 3rd generation technology. Few of the aims of 4G
networks have yet been published, however it is likely that they will be to extend the
capabilities of 3G networks, allowing a greater range of applications, and improved
universal access. Ultimately 4G networks should encompass broadband wireless
services, such as High Definition Television (HDTV) (4 - 20 Mbps) and computer
network applications (1 - 100 Mbps). This will allow 4G networks to replace many of the
functions of WLAN systems. However, to cover this application, cost of service must be
reduced significantly from 3G networks. The spectral efficiency of 3G networks is too
low to support high data rate services at low cost.
As a consequence one of the main focuses of 4G systems will be to significantly
improve the spectral efficiency.
figure 195: Current and future mobile systems. The general trend will be to
provide higher data rates and greater mobility.
Orthogonal Frequency Division Multiplexing (OFDM) is an alternative wireless
modulation technology to CDMA. OFDM has the potential to surpass the capacity of
CDMA systems and provide the wireless access method for 4G systems.
OFDM is a modulation scheme that allows digital data to be efficiently and reliably
transmitted over a radio channel, even in multipath environments. OFDM transmits data
by using a large number of narrow bandwidth carriers. These carriers are regularly
spaced in frequency, forming a block of spectrum. The frequency spacing and time
synchronisation of the carriers is chosen in such a way that the carriers are orthogonal,
241
meaning that they do not cause interference to each other. This is despite the carriers
overlapping each other in the frequency domain. The name ‘OFDM’ is derived from the
fact that the digital data is sent using many carriers, each of a different frequency
(Frequency Division Multiplexing) and these carriers are orthogonal to each other,
hence Orthogonal Frequency Division Multiplexing. The origins of OFDM development
started in the late 1950’s with the introduction of Frequency Division Multiplexing (FDM)
for data communications. In 1966 Chang patented the structure of OFDM and
published the concept of using orthogonal overlapping multi-tone signals for data
communications. In 1971 Weinstein introduced the idea of using a Discrete Fourier
Transform (DFT) for implementation of the generation and reception of OFDM signals,
eliminating the requirement for banks of analog subcarrier oscillators. This presented an
opportunity for an easy implementation of OFDM, especially with the use of Fast Fourier
Transforms (FFT), which are an efficient implementation of the DFT. This suggested
that the easiest implementation of OFDM is with the use of Digital Signal Processing
(DSP), which can implement FFT algorithms. It is only recently that the advances in
integrated circuit technology have made the implementation of OFDM cost effective.
The reliance on DSP prevented the wide spread use of OFDM during the early
development of FDM. It wasn’t until the late 1980’s that work began on the
development of OFDM for ommercial use, with the introduction of the Digital Audio
Broadcasting (DAB) system.
23.2 Digital Audio Broadcasting
DAB was the first commercial use of OFDM technology. Development of DAB started in
1987 and services began in U.K and Sweden in 1995. DAB is a replacement for FM
audio broadcasting, by providing high quality digital audio and information services.
OFDM was used for DAB due to its multipath tolerance.
Broadcast systems operate with potentially very long transmission distances (20 -100
km). As a result, multipath is a major problem as it causes extensive ghosting of the
transmission. This ghosting causes Inter-Symbol Interference (ISI), blurring the time
domain signal. For single carrier transmissions the effects of ISI are normally mitigated
using adaptive equalisation. This process uses adaptive filtering to approximate the
impulse response of the radio channel. An inverse channel response filter is then used
to recombine the blurred copies of the symbol bits. This process is however complex
and slow due to the locking time of the adaptive equaliser. Additionally it becomes
increasing difficult to equalise signals that suffer ISI of more than a couple of symbol
periods.
OFDM overcomes the effects of multipath by breaking the signal into many narrow
bandwidth carriers. This results in a low symbol rate reducing the amount of ISI. In
addition to this, a guard period is added to the start of each symbol, removing the
effects of ISI for multipath signals delayed less than the guard period. The high
tolerance to multipath makes OFDM more suited to high data transmissions in terrestrial
environments than single carrier transmissions.
242
table 10: DAB Transmission parameters for each transmission mode
Table above, shows the system parameters for DAB. DAB has four transmission
modes. The transmission frequency, receiver velocity and required multipath tolerance
all determine the most suitable transmission mode to use.
Doppler spread is caused by rapid changes in the channel response due to movement
of the receiver through a multipath environment. It results in random frequency
modulation of the OFDM subcarriers, leading to signal degradation. The amount of
Doppler spread is proportional to the transmission frequency and the velocity of
movement. The closer the subcarriers are spaced together, the more susceptible the
OFDM signal is to Doppler spread, and so the different transmission modes in DAB
allow trade off between the amount of multipath protection (length of the guard period)
and the Doppler spread tolerance.
23.3 Digital Video Broadcasting
The development of the Digital Video Broadcasting (DVB) standards was started in
1993. DVB is a transmission scheme based on the MPEG-2 standard, as a method for
point to multipoint delivery of high quality compressed digital audio and video. It is an
enhanced replacement of the analogue television broadcast standard, as DVB provides
a flexible transmission medium for delivery of video, audio and data services. The DVB
standards specify the delivery mechanism for a wide range of applications, including
satellite TV (DVB-S), cable systems (DVB-C) and terrestrial transmissions (DVB-T). The
physical layer of each of these standards is optimised for the transmission channel
being used. Satellite broadcasts use a single carrier transmission, with QPSK modulation,
which is optimised for this application as a single carrier allows for large Doppler shifts, and
QPSK allows for maximum energy efficiency. This transmission method is however unsuitable
for terrestrial transmissions as multipath severely degrades the performance of high-speed single
carrier transmissions. For this reason, OFDM was used for the terrestrial transmission standard
for DVB. The physical layer of the DVB-T transmission is similar to DAB, in that the
OFDM transmission uses a large number of subcarriers to mitigate the effects of
243
multipath. DVB-T allows for two transmission modes depending on the number of
subcarriers used. Table below shows the basic transmission parameters for these two
modes. The major difference between DAB and DVB-T is the larger bandwidth used
and the use of higher modulation schemes to achieve a higher data throughput. The
DVB-T allows for three subcarrier
modulation schemes: QPSK, 16-QAM (Quadrature Amplitude Modulation) and 64-QAM;
and a range of guard period lengths and coding rates. This allows the robustness of the
transmission link to be traded at the expense of link capacity. Table below shows the
data throughput and required SNR for some of the transmission combinations.
DVB-T is a uni-directional link due to its broadcast nature. Thus any choice in data rate
verses robustness affects all receivers. If the system goal is to achieve high reliability,
the data rate must be lowered to meet the conditions of the worst receiver.
table 11: DVB transmission parameters
table 12: SNR required and net bit rate for a selection of the coding and modulation combinations for
DVB. Note: Code rate can be any of the following values: 1/2, 2/3, 3/4, 5/6, 7/8. The Guard Period
duration can be any following values: 1/4, 1/8, 1/16, 1/32.
23.4 Basic principle of OFDM
Orthogonal Frequency Division Multiplexing (OFDM) is very similar to the well known
and used technique of Frequency Division Multiplexing (FDM). OFDM uses the
principles of FDM to allow multiple messages to be sent over a single radio channel. It is
however in a much more controlled manner, allowing an improved spectral efficiency.
A simple example of FDM is the use of different frequencies for each FM (Frequency
Modulation) radio stations. All stations transmit at the same time but do not interfere
with each other because they transmit using different carrier frequencies. Additionally
244
they are bandwidth limited and are spaced sufficiently far apart in frequency so that their
transmitted signals do not overlap in the frequency domain. At the receiver, each signal
is individually received by using a frequency tuneable band pass filter to selectively
remove all the signals except for the station of
interest. This filtered signal can then be demodulated to recover the original transmitted
information.
OFDM is different from FDM in several ways. In conventional broadcasting each radio
station transmits on a different frequency, effectively using FDM to maintain a
separation between the stations. There is however no coordination or synchronisation
between each of these stations. With an OFDM transmission such as DAB, the
information signals from multiple stations is combined into a single multiplexed stream
of data. This data is then transmitted using an OFDM ensemble that is made up from a
dense packing of many subcarriers. All the subcarriers within the OFDM signal are time
and frequency synchronised to each other, allowing the interference between
subcarriers to be carefully controlled. These multiple subcarriers overlap in the
frequency domain, but do not cause Inter-Carrier Interference (ICI) due to the
orthogonal nature of the modulation. Typically with FDM the transmission signals need
to have a large frequency guard-band between channels to prevent interference. This
lowers the overall spectral efficiency. However with OFDM the orthogonal packing of the
subcarriers greatly reduces this guard band, improving the spectral efficiency.
Each of the carriers in a FDM transmission can use an analogue or digital modulation
scheme. There is no synchronisation between the transmission and so one station could
transmit using FM and another in digital using FSK. In a single OFDM transmission all
the subcarriers are synchronised to each other, restricting the transmission to digital
modulation schemes. OFDM is symbol based, and can be thought of as a large number
of low bit rate carriers transmitting in parallel. All these carriers transmit in unison using
synchronised time and frequency, forming a single block of spectrum. This is to ensure
that the orthogonal nature of the structure is maintained. Since these multiple carriers
form a single OFDM transmission, they are commonly referred to as ‘subcarriers’, with
the term of ‘carrier’ reserved for describing the RF carrier mixing the signal from base
band. There are several ways of looking at what make the subcarriers in an OFDM
signal orthogonal and why this prevents interference between them.
OFDM is a multi carrier modulation scheme that transmits data over a number of subcarriers. A conventional transmission uses only a single carrier, which is modulated with
all the data to be sent. OFDM breaks the data to be sent in to small chunks, allocating
each sub data stream to a sub-carrier. The data is sent in parallel, so that instead of
sending just a single bit of information per symbol, many bits are sent per symbol. The
symbol rate for OFDM is N times lower than single carrier modulation, where N is the
number of subcarriers in the OFDM transmission.
245
power
Conventional
sigle carrier
frequency
OFDM
frequency
figure 196: in EFDM data is transmitted over many narrow bandwidth carriers
23.5 Orthogonality
Signals are orthogonal if they are mutually independent of each other. Orthogonality is a
property that allows multiple information signals to be transmitted perfectly over a
common channel and detected, without interference. Loss of orthogonality results in
blurring between these information signals and degradation in communications.
Many common multiplexing schemes are inherently orthogonal. Time Division
Multiplexing (TDM) allows transmission of multiple information signals over a single
channel by assigning unique time slots to each separate information signal. During each
time slot only the signal from a single source is transmitted preventing any interference
between the multiple information sources. Because of this TDM is orthogonal in nature.
In the frequency domain most FDM systems are orthogonal as each of the separate
transmission signals are well spaced out in frequency preventing interference. Although
these methods are orthogonal the term OFDM has been reserved for a special form of
FDM.
The subcarriers in an OFDM signal are spaced as close as is theoretically possible
while maintain orthogonality between them.
OFDM achieves orthogonality in the frequency domain by allocating each of the
separate information signals onto different subcarriers. OFDM signals are made up from
a sum of sinusoids, with each corresponding to a subcarrier. The baseband frequency
of each subcarrier is chosen to be an integer multiple of the inverse of the symbol time,
resulting in all subcarriers having an integer number of cycles per symbol. As a
consequence the subcarriers are orthogonal to each other. Figure below shows the
construction of an OFDM signal with four subcarriers
246
figure 197: Time domain construction of an OFDM signal:
(1a), (2a), (3a) and (4a) show individual subcarriers, with 1, 2, 3, and 4 cycles per symbol
respectively. The phase on all these subcarriers is zero. Note, that each subcarrier has an integer
number of cycles per symbol, making them cyclic. Adding a copy of the symbol to the end would
result in a smooth join between symbols. Plot (1b), (2b), (3b) and (4b) show the FFT of the time
waveforms in (1a), (2a), (3a) and (4a) respectively. (4a) and (4b) shows the result for the summation
of the 4 subcarriers
Orthogonal Frequency Division Multiplexing (OFDM), is a technique for transmitting data
in parallel by using a large number of modulated carriers with sufficient frequency
spacing so that the carriers are orthogonal. OFDM provides resistance to data errors
caused by multipath channels.
Over a T-sec interval, the complex envelope for the OFDM signal is:
N −1
g (t ) = Ac ∑ ω nϕ n (t ),
where 0 < t < T
eq 321
n =0
where:
Ac is the carrier amplitude
ωn is the element of the N-element parallel data vector w =[ω0, ω1,…….., ωN-1]
The orthogonal carriers are
ϕ n (t ) = e j 2π f t
n
eq 322
where
247
fn =
N −1 ⎞
1⎛
⎜n −
⎟
T⎝
2 ⎠
⎧
1 ⎛ N −1 ⎞ ⎫
⎪⎪ for n = 0 ⇒ f n = T ⎜ − 2 ⎟ ⎪⎪
⎝
⎠
⇒⎨
⎬
−
1
1 ⎞⎪
N
⎪ for n = N − 1 ⇒ f n = ⎛⎜ +
⎟
⎪⎩
2 ⎠⎪⎭
T⎝
eq 323
The duration of the data symbol on each carrier is T seconds, and carriers are spaced
1/T Hz apart in fact:
f n+1 − f n =
1⎛
N −1⎞ 1 ⎛
N −1⎞ 1
⎜n +1−
⎟ − ⎜n −
⎟ =
2 ⎠ T⎝
2 ⎠ T
T⎝
eq 324
This assures that the carriers are orthogonal, since ϕn(t) satisfy the orthogonality
condition over the T-sec interval:
b
∫ϕ
n
(t )ϕ m* (t )dt = 0
eq 325
a
in fact recalling that:
b
∫ϕ
n
fn =
1⎛
N −1 ⎞
1⎛
N −1 ⎞
⎜n −
⎟ and f m = ⎜ m −
⎟ with n≠m consequently:
T⎝
2 ⎠
T⎝
2 ⎠
(t )ϕ m* (t )dt = 0
a
T
⇒ ∫e
j 2πf nt
0
e
− j 2πf mt
T
dt = ∫ e
j 2π ( f n − f m ) t
0
T
1
dt =
j 2π ( f n − f m )e j 2π ( f n − f m ) t =
∫
j 2π ( f n − f m ) 0
T
⎡ j 2π ⎡⎢ 1 ⎛⎜ n− N −1 ⎞⎟− 1 ⎛⎜ m− N −1 ⎞⎟ ⎤⎥ t ⎤
1
⎢e ⎣ T ⎝ 2 ⎠ T ⎝ 2 ⎠ ⎦ ⎥ =
⎡1 ⎛
N −1 ⎞ 1 ⎛
N − 1 ⎞⎤ ⎢
⎥⎦
j 2π ⎢ ⎜ n −
0
⎟ − ⎜m −
⎟⎥ ⎣
2 ⎠ T⎝
2 ⎠⎦
⎣T ⎝
T
⎡ j 2π ⎡⎢ T1 ( n−m )⎤⎥ t ⎤
⎡ j 2π ⎡⎢ T1 (n−m )⎤⎥T ⎤
1
⎦
⎦
− 1⎥ =
⎢e ⎣
⎢e ⎣
⎥ =
1
⎡1
⎤ ⎢⎣
⎡
⎤
⎥⎦
⎥
⎢
⎦ 0 j 2π (n − m ) ⎣
j 2π ⎢ (n − m )⎥
⎢
⎥
⎣T
⎦
⎣T
⎦
1
1
[cos[2π (n − m )] + j sin[2π (n − m )] − 1]
=
e j 2π ( n − m ) − 1 =
⎡1
⎤
⎡1
⎤
j 2π ⎢ (n − m )⎥
j 2π ⎢ (n − m )⎥
⎣T
⎦
⎣T
⎦
1
[1 − 1] = 0
=
⎡1
⎤
j 2π ⎢ (n − m )⎥
eq 326
⎣T
⎦
1
[
]
248
Because the carriers are orthogonal, data can be detected on each of these closely
spaced carriers without interference from the other carriers.
Another way of thinking to orthogonality concept is that if we look at a matched receiver
for one of the orthogonal functions, a subcarrier in the case of OFDM, then the receiver
will only see the result for that function. The results from all other functions in the set
integrate to zero, and thus have no effect.
Equation below shows a set of orthogonal sinusoids, which represent the subcarriers
for an unmodulated real OFDM signal.
k = 1,2,......M ⎫
0<t <T
⎧sin( 2πkf 0t )
sk (t ) = ⎨
⎬
otherwise
0
⎩
⎭
eq 327
Where f0 is the carrier spacing, M is the number of carriers, T is the symbol period.
Since the highest frequency component is Mf0 the transmission bandwidth is also Mf0.
These subcarriers are orthogonal to each other because when we multiply the
waveforms of any two subcarriers and integrate over the symbol period the result is
zero. Multiplying the two sine waves together is the same as mixing these subcarriers.
This results in sum and difference frequency components, which will always be integer
subcarrier frequencies, as the frequency of the two mixing subcarriers has integer
number of cycles. Since the system is linear we can integrate the result by taking the
integral of each frequency component separately then combining the results by adding
the two sub-integrals. The two frequency components after the mixing have an integer
number of cycles over the period and so the sub-integral of each component will be
zero, as the integral of a sinusoid over an entire period is zero. Both the sub-integrals
are zeros and so the resulting addition of the two will also be zero, thus we have
established that the frequency components are orthogonal to each other.
23.5.1
FREQUENCY DOMAIN ORTHOGONALITY
Another way to view the orthogonality property of OFDM signals is to look at its
spectrum. In the frequency domain each OFDM subcarrier has a sinc, sin(x)/x,
frequency response, as shown in Figure below. This is a result of the symbol time
corresponding to the inverse of the carrier spacing. As far as the receiver is concerned
each OFDM symbol transmitted for a fixed time (TFFT) with no tapering at the ends of the
symbol. This symbol time corresponds to the inverse of the subcarrier spacing of 1/TFFT
Hz 1. This rectangular, boxcar, waveform in the time domain results in a sinc frequency
response in the frequency domain. The sinc shape has a narrow main lobe, with many
side-lobes that decay slowly with the magnitude of the frequency difference away from
the centre. Each carrier has a peak at the centre frequency and nulls evenly spaced
with a frequency gap equal to the carrier spacing.
The orthogonal nature of the transmission is a result of the peak of each subcarrier
corresponding to the nulls of all other subcarriers. When this signal is detected using
249
a Discrete Fourier Transform (DFT) the spectrum is not continuous as shown in Figure
below, but has discrete samples. The sampled spectrum are shown as ‘o’s in the figure.
If the DFT is time synchronised, the frequency samples of the DFT correspond to just
the peaks of the subcarriers, thus the overlapping frequency region between subcarriers
does not affect the receiver. The measured peaks correspond to the nulls for all other
subcarriers, resulting in orthogonality between the subcarriers.
figure 198: Frequency response of the subcarriers in a 5 tone OFDM signal.
(a) shows the spectrum of each carrier, and the discrete frequency samples seen
by an OFDM receiver. Note, each carrier is sinc, sin(x)/x, in shape.
(b) Shows the overall combined response of the 5 subcarriers (thick black line).
23.6 OFDM generation and reception
OFDM signals are typically generated digitally due to the difficulty in creating large
banks of phase lock oscillators and receivers in the analog domain. Figure below shows
the block diagram of a typical OFDM transceiver. The transmitter section converts digital
data to be transmitted, into a mapping of subcarrier amplitude and phase. It then
transforms this spectral representation of the data into the time domain using an
Inverse Discrete Fourier Transform (IDFT). The Inverse Fast Fourier Transform
(IFFT) performs the same operations as an IDFT, except that it is much more
computationally efficiency, and so is used in all practical systems. In order to transmit
the OFDM signal the calculated time domain signal is then mixed up to the required
frequency.
The receiver performs the reverse operation of the transmitter, mixing the RF signal to
base band for processing, then using a Fast Fourier Transform (FFT) to analyse the
signal in the frequency domain. The amplitude and phase of the subcarriers is then
picked out and converted back to digital data.
250
Carrier
Phase
Serial
TX
data
Serial
to
para.
TRANSMITTER
Subcarrier
Modulation
&
Mapping
IFFT
I
Q
Carrier
Amplitude
I
Guard
Period
Insertion
Frame
Sync
Insertion
Q
Para
To
Serial
RF
Modulation
Amplifier
Q
Time Waveform
Frequency Correction
Serial
RX
data
I
Carrier
Modulation Phase FFT
Slicer
I
Guard
Period
Removal
I
RF
Demod
Amplifier
Q
Q
Carrier
Amplitude
OL
Time Sync
Frame
Detection
RECEIVER
figure 199
23.6.1
Serial To Parallel Conversion
Data to be transmitted is typically in the form of a serial data stream. In OFDM, each
symbol typically transmits 40 - 4000 bits, and so a serial to parallel conversion stage
is needed to convert the input serial bit stream to the data to be transmitted in each
OFDM symbol. The data allocated to each symbol depends on the modulation scheme
used and by the number of subcarriers. For example, for a subcarrier modulation of
16-QAM each subcarrier carries 4 bits of data, and so for a transmission using 100
subcarriers the number of bits per symbol would be 400.
For adaptive modulation schemes, the modulation scheme used on each subcarrier can
vary and so the number of bits per subcarrier also varies. As a result the serial to
parallel conversion stage involves filling the data payload for each subcarrier. At the
receiver the reverse process takes place, with the data from the subcarriers being
converted back to the original serial data stream.
When an OFDM transmission occurs in a multipath radio environment, frequency
selective fading can result in groups of subcarriers being heavily attenuated, which in
turn can result in bit errors. These nulls in the frequency response of the channel can
cause the information sent in neighbouring carriers to be destroyed, resulting in a
clustering of the bit errors in each symbol. Most Forward Error Correction (FEC)
schemes tend to work more effectively if the errors are spread evenly, rather than in
251
large clusters, and so to improve the performance most systems employ data
scrambling as part of the serial to parallel conversion stage. This is implemented by
randomising the subcarrier allocation of each sequential data bit. At the receiver the
reverse scrambling is used to decode the signal. This restores the original sequencing
of the data bits, but spreads clusters of bit errors so that they are approximately
uniformly distributed in time. This randomisation of the location of the bit errors improves
the performance of the FEC and the system as a whole.
23.6.2
Subcarrier modulation and mapping
Once each subcarrier has been allocated bits for transmission, they are mapped using a
modulation scheme to a subcarrier amplitude and phase, which is represented by a
complex In-phase and Quadrature-phase (IQ) vector. Figure below shows an example
of subcarrier modulation mapping. This example shows 16-QAM, which maps 4 bits for
each symbol. Each combination of the 4 bits of data corresponds to a unique IQ vector,
shown as a dot on the figure. A large number of modulation schemes are available
allowing the number of bits transmitted per carrier per symbol to be varied.
figure 200:
Example IQ modulation constellation. 16-QAM, with gray coding
of the data to each location
Subcarrier modulation can be implemented using a lookup table, making it very efficient
to implement.
In the receiver, mapping the received IQ vector back to the data word performs
subcarrier demodulation. During transmission, noise and distortion becomes added to
the signal due to thermal noise, signal power reduction and imperfect channel
equalisation. Figure below shows an example of a received 16-QAM signal with a SNR
of 18 dB. Each of the IQ points is blurred in location due to the channel noise. For each
received IQ vector the receiver has to estimate the most likely original transmission
vector. This is achieved by finding the transmission vector that is closest to the received
vector. Errors occur when the noise exceeds half the spacing between the transmission
IQ points, making it cross over a decision boundary.
252
figure 201: IQ plot for 16-QAM data with added noise.
23.6.3
Frequency to time domain conversion
After the subcarrier modulation stage each of the data subcarriers is set to an
amplitude and phase based on the data being sent and the modulation scheme; all
unused subcarriers are set to zero. This sets up the OFDM signal in the frequency
domain. An IFFT is then used to convert this signal to the time domain, allowing it to
be transmitted. Figure below shows the IFFT section of the OFDM transmitter. In the
frequency domain, before applying the IFFT, each of the discrete samples of the IFFT
corresponds to an individual subcarrier. Most of the subcarriers are modulated with
data. The outer subcarriers are unmodulated and set to zero amplitude. These zero
subcarriers provide a frequency guard band before the Nyquist frequency and
effectively act as an interpolation of the signal and allows for a realistic roll off in the
analog anti-aliasing reconstruction filters.
Time
End
Frequency
I
Input
data
SubcarrierM
odulation &
Mapping.
Parallel
to Serial
IFFT
IQ vector
Amplitue and
phase
zeros
Output baseband
OFDM signal
Q
Guard
Period
Symbol
start
253
23.7 OFDM Transmitter
A key advantage of OFDM is that it can be generated by using FFT digital signal
processing techniques. For example, if we suppress the frequency offset (N-1)/2T of
equation:
ϕ n (t ) = e j 2π f t
where
n
i.e.
fn =
n
T
N −1⎞
1⎛
⎜n −
⎟
T⎝
2 ⎠
fn =
then ϕ n (t ) = e
N −1
N −1
n =0
n =0
n
j 2π t
T
eq 328
= e j 2 kπ where t = k
g (t ) = Ac ∑ wnϕ n = Ac ∑ wn e j 2 kπ where
T
, and substitute into equation;
n
w = [w0 , w1 , w2 ,......wn−1 ]
eq 329
then the elements of the IFFT vector, as defined by the equation already seen, are
obtained.
n = +∞
n = +∞
n = −∞
n = −∞
W ( f ) = H ( f ) ∑ f 0δ ( f − nf 0 ) =
∑ f H (nf
0
0
)δ ( f − nf 0 )
Thus, the OFDM signal may be generated by using the IFFT algorithms as shown in
figure below.
In that figure, the complex envelope, g(t), is described by the I and Q components x(t)
and y(t), where g(t)=x(t) and jy(t).
Baseband signal processing
w
RF circuits
g
x(t)
m(t)
Serial
data
Serial to
Parallel
converter
IFFT
Parallel
to Serial
converter
+
cos(ωct)
y(t)
-90°
phase
shift
OFDM
signal
sin(ωct)
Carrier
oscillator, fc
v(t)=x(t)cos(ωct)-y(t)sin(ωct)
figure 202: OFDM Transmitter
254
Let the input serial data symbol have a duration of Ts second each. These data can be
binary (±1) to produce BPSK modulated carriers or can be multilevel complex-valued
serial data to produce (as appropriate) QPSK, MPSK, or QAM carriers.
Ds=1/Ts, is the input symbol (baud) rate. The serial-to-parallel converter reads in N input
serial symbol at a time and hold their values (element of w) on the parallel output line
for T=NTs seconds, where T is the time span of the IFFT. The IFFT uses w to evaluate
output IFFT vector g, which contains elements representing samples of the complex
envelope.
The parallel-to-serial converter shifts out the element values of g. These are the sample
of the complex envelope for the OFDM signal described by the equation
N −1
N −1
n =0
n =0
g (t ) = Ac ∑ wnϕ n = Ac ∑ wn e j 2 kπ
where x(t) and y(t) are the I and Q components of the complex envelope.
The OFDM signal is at the end produced by the classic IQ modulators.
1. At the receiver, the serial data are recovered from the received OFDM signal by
demodulating the signal to produce serial I and Q data,
2. converting the serial data to parallel data,
3. evaluating the FFT, and
4. converting the FFT vector (parallel data) to serial output data.
The length-of-the-FFT vector determines the resistance of OFDM to errors caused by
multipath channels. N is chosen so that T=NTs is much larger than the maximum delay
time of echo components in the received multipath signal.
The PSD (power spectral density) of the OFDM signal can be obtained recalling that
OFDM signal consists of orthogonal carriers modulated by data with rectangular pulse
shapes that have a duration of T sec. consequently, the overall PSD of the complex
envelope of the OFDM signal is of the form
N −1
Pg ( f ) = C ∑
n =0
sin[π ( f − f n )T ]
π ( f − f n )T
2
where C = Ac2 ωn T
2
eq 330
and ϖ n = 0
Since the spacing between carriers is 1/T [Hz] and there are N carriers, the null
bandwidth of the OFDM signal is
BT =
N +1 N +1 1
=
≈ = Ds
T
NTs Ts
[Hz ]
eq 331
where the approximation is reasonable for N>10.
255
A key advantage of OFDM is that it can be generated by using FFT digital signal
processing techniques. An Example of FFT theory is reported in the following
paragraph.
23.8 FFT(Line Specra for Periodic Waveforms)
For periodic waveforms, the Fourier series representations are valid over all time
(i.e.-∞<t<+∞). Consequently, the (two sided) spectrum, which depends on the
waveshape from t=-∞ to t=∞, my be evaluated in terms of Fourier coefficients.
23.8.1
Theorem
If a waveform is periodic with period T0, the spectrum of the waveform w(t) is:
W( f ) =
n = +∞
∑ c δ ( f − nf ) = F [w(t )]
n = −∞
eq 332
0
n
Where:
f0=1/T0, ω0=2π f0=2π /T0,
1
cn =
T0
a +T0
∫ w(t )e
− jnw0t
dt
are the complex (phasor) Fourier coefficients of the complex
a
exponential Fourier series, and w(t ) =
+∞
∑c e
n = −∞
n
jnω0t
is used to represent a physical
waveform (i.e. finite energy) over the interval a<t<a+T0. When w(t) is periodic with
period T0, this Fourier series representation is valid over all time (i.e. over the interval ∞<t<∞).
Proof.
w (t ) =
+∞
∑c
n = −∞
n
e
jn ω 0 t
eq 333
Taking the Fourier transform of both sides, we obtain
256
+∞
⎛ +∞
⎞
W ( f ) = ∫ ⎜ ∑ cn e jnω0t ⎟e − jωt dt =
⎠
− ∞⎝ n = −∞
=
+∞
+∞
∑ c ∫e
n = −∞
=
e
− jωt
+∞
∑ c ∫e
n
+∞
+∞
∑ c ∫e
n
n = −∞
− j ( −2πf 0 + 2πf ) t
dt =
∑ c δ ( f − nf
n
0
j ( nω0 −ω ) t
dt =
+∞
+∞
∑ c ∫e
n
+∞
+∞
∑ c ∫e
n = −∞
−∞
n = −∞
−∞
+∞
n = −∞
dt =
−∞
+∞
n = −∞
=
n
jnω0t
− j 2π ( − nf 0 + f ) t
dt =
n
dt =
−∞
+∞
+∞
∑ c ∫e
n = −∞
−∞
− j ( − nω0 +ω ) t
n
eq 334
− j 2π ( f − nf 0 ) t
dt =
−∞
)
where the integral representation for a delta function, was used.
This theorem indicates that a periodic function always has a line (delta function)
spectrum, with the lines being at f=nf0 and having weight given by the cn values.
An illustration of the property is the spectrum of a sinusoid:
v(t ) = A sin ω0 t
where ω0 = 2πf 0
then the spectrum will be:
+∞
V( f ) =
⎛ e jω0t − e − jω0t
A
∫ ⎜⎜ 2 j
−∞ ⎝
+∞
=
+∞
+∞
⎞ − jωt
A
A
jω0t − jωt
⎟⎟e dt =
−
e − jω0t e − jωt dt =
e
e
dt
∫
∫
2
2
j
j
⎠
−∞
−∞
+∞
+∞
+∞
A
A
A
A
e − j 2π ( f + f0 )t dt ) =
e − j 2π ( f − f0 ) t dt −
e − j 2πf0t e − j 2πft dt =
e j 2πf0t e − j 2πft dt −
∫
∫
∫
∫
2 j −∞
2 j −∞
2 j −∞
2 j −∞
+∞
= j
eq 335
+∞
A
A
A
A
− e − j 2π ( f − f0 )t dt + j ∫ e − j 2π ( f + f0 ) t dt ) = j δ ( f + f 0 ) − j δ ( f − f 0 ) =
∫
2 −∞
2 −∞
2
2
c−1δ ( f + f 0 ) + c1δ ( f − f 0 )
V( f ) =
A
A
δ ( f + f0 ) − δ ( f − f0 )
2
2
Magnitude Spectrum
Phase Spectrum
θ(f)
V(f)
A/2
-f0
+90°
f0
f
f
-90°
257
figure 203
In this case c1=-jA/2 and c-1=jA/2 and the other cn’s were zero.
It is also obvious that there is no dc component, since there is no line at f=0 (i.e. c0=0).
Conversely, if a function does not contain any periodic component, the spectrum will be
continuous (no lines), except for a line at f=0 when the function has a dc component.
It is also possible to evaluate the Fourier coefficients by sampling the Fourier transform
of a pulse corresponding to w(t) over a period. This is shown by the following theorem:
23.8.2
Theorem
If w(t) is a periodic function with period T0 and is represented by
w(t ) =
n =∞
∑ h(t − nT0 ) =
n= −∞
n =∞
∑c e
n =−∞
n
jnω0t
eq 336
where
T
⎧
⎫
⎪w(t ), t < 0
⎪
h(t ) = ⎨
2
⎬
⎪⎩0,
t elsewhere⎪⎭
eq 337
then the Fourier coefficients are given by
cn = f 0 H (nf 0 )
eq 338
where
H(f)=F[h(t)] and f0=1/T0
Proof.
w(t ) =
n= +∞
∑ h(t − nT0 ) =
n= −∞
n= +∞
∑ h(t ) ∗ δ (t − nT0 ) =
n= −∞
⎡
⎤
n = +∞ +∞
∑ ⎢ ∫ h(τ ) ⋅ δ [(t − τ ) − nT ]dτ ⎥ =
⎣
n = −∞ −∞
⎧
⎫
= ∑ ⎨ ∫ h(τ ) ⋅ δ [− [τ − (t − nT0 )]]dτ ⎬
n =−∞⎩ −∞
⎭
n =+∞ +∞
0
⎦
eq 339
where * denotes the convolution operation.
258
Thus,
w(t ) =
n= +∞
n = +∞
∑ h(t − nT ) = h(t ) ∗ ∑ δ (t − nT )
0
n= −∞
eq 340
0
n = −∞
But the impulse train may itself be represented by its Fourier series; that is,
n = +∞
∑ δ (t − nT0 ) =
n = −∞
n =+∞
∑c e
n =−∞
n
jnω0t
eq 341
Where all the Fourier coefficients are just cn=f0. Substituting the last in the preceding
equation we have:
w(t ) =
n= +∞
n =+∞
n =+∞
∑ h(t − nT ) = h(t ) ∗ ∑ δ (t − nT ) = h(t ) ∗ ∑ c e
0
n= −∞
0
n =−∞
n =−∞
n
jnω0t
= h(t ) ∗
n= +∞
∑fe
n= −∞
0
jnω0t
eq 342
Taking the Fourier transform of both sides we have
n = +∞
W ( f ) = H ( f ) ∑ f 0δ ( f − nf 0 )
eq 343
n = −∞
Using the preceding theorem W ( f ) =
n = +∞
∑ c δ ( f − nf ) = F [w(t )]
n = −∞
n
0
to compare the last
equation with we obtain
n = +∞
n = +∞
n = −∞
n = −∞
W ( f ) = H ( f ) ∑ f 0δ ( f − nf 0 ) =
∑ f H (nf
0
0
)δ ( f − nf 0 )
eq 344
As an example we find the Fourier coefficients for the periodic rectangular wave shown
below:
259
w(t)
T
A
1
T0
2
1
− T0
2
Waveform
3
T0
2
T0
t
2T0
T0
Envelope =
A/2
W( f ) =
A/4
Magnitude Spectrum
-3f0
-2f0
-f0
f0 2f0
A sin (πfT )
2 πfT
A sin (nπ / 2 )
δ ( f − nf 0 )
nπ / 2
n = −∞
n = +∞
∑2
3f0
f
4f0
figure 204
The complex Fourier coefficients for the periodic rectangular wave shown above is:
1
cn =
T0
T0 / 2
∫ Ae
0
− jnω0t
A 1
dt = −
T0 jnω0
T0 / 2
∫ jnω e
0
0
− jnω0t
dt = −
[
A 1
e − jnω0t
T0 jnω0
]
T0 / 2
0
=−
[
]
A 1
e − jnω0T0 / 2 − 1
T0 jnω0
which reduces, (using l’Hospital’s rule, for evaluating the indeterminant form for n=0), to
260
c0 =
A
= dc term
2
[
]
A 1
A 1 − jω0T0 / 2
c1 = −
e
−1 = −
T0 j 2π
T0 jω0
T0
⎡ − j 2Tπ T0 / 2 ⎤
A 1
A 1
A
e − jπ − 1 = −
[
− 1⎥ = −
− 1 − 1] = − j
⎢e 0
T0 j 2π
T0 j 2π
π
⎢⎣
⎥⎦
T0
T0
[
]
2π
A 1
A 1 ⎡ − j T0 T0 ⎤
A 1 − j 2π
A 1
− 2 jω0T0 / 2
c2 = −
e
−1 = −
− 1⎥ = −
e
−1 = −
[1 − 1] = 0
⎢e
T0 j 2ω0
T0 jω0 ⎣⎢
T0 jω0
T0 jω0
⎥⎦
A
c3 = − j
3π
c4 = 0
[
c5 = − j
]
[
]
A
5π
⇓
W( f ) =
n =−∞
∑ c δ ( f − nf ) = .......... − c δ ( f − 5 f ) − c δ ( f − 4 f ) − c δ ( f − 3 f ) − c δ ( f − 2 f ) − c δ ( f − f )
n =−∞
n
0
5
0
4
0
3
0
2
0
1
0
A
δ ( f ) + c1δ ( f − f 0 ) + c3δ ( f − 3 f 0 ) + c4δ ( f − 4 f 0 ) + c5δ ( f − 5 f 0 ) + ...........
2
A
A
A
= .......... + j
δ ( f − 5 f0 ) + j δ ( f − 3 f0 ) + j δ ( f − f0 )
5π
3π
π
A
A
A
A
− δ ( f ) − j δ ( f − f0 ) − j δ ( f − 3 f0 ) − j
δ ( f − 5 f 0 ) + ...........
2
π
3π
5π
− c0δ ( f ) +
eq 345
These coefficients may be verified by using the last Theorem and the spectrum of the
single flat-top impulse:
⎛ t
h(t) = ∏ ⎜⎜
⎝ TS
Ts ⎫
⎧
⎞ ⎪1, se t ≤ 2 ⎪
⎟⎟ ≡ ⎨
⎬
⎠ ⎪0, se t > Ts ⎪
2⎭
⎩
is a flat top inpulse (rectangular inpulse shaping)
261
1
0.8
0.6
1
2/Ts
0.4
0.2
-Ts/2
Ts/2
t
0
-20
-15
-10
-5
0
5
10
15
20
freq
-0.2
-0.4
time domain
frequency domain
figure 205
The frequency domain of a single flat-top impulse is obtained by Fourier transform
H( f ) =
Ts / 2
∫1⋅ e
−Ts / 2
− jωt
T /2
+ Ts / 2
⎡ e − jωt ⎤
e − jωTs / 2 − e + jωTs / 2
1 s
− jωt
=
=
dt =
j
e
dt
ω
−
⋅
=
⎢ − jω ⎥
− jω
− jω −T∫s / 2
⎦ −T / 2
⎣
s
⎛ T ⎞
Ts
sen⎜ ω s s ⎟
− jωTs / 2
+ jωTs / 2
+ jωTs / 2
− jωTs / 2
2Ts e
−e
−e
e
2⎠
⎝
= 2
=
= Ts
Ts
T
− jω
2j
Tsω s
ωs s
2
2
eq 346
Then the coefficients cn for the periodic repetition of the flat top pulse, which period is
T0=2Ts, are:
262
T0
⎛
⎜
sen⎜ nω0 2
⎛ Ts ⎞
2
⎜
sen⎜ ω0 ⎟
⎜
1
1
1
2 ⎠ 1 T0
⎝
⎝
cn = f 0 H (nf 0 ) = H (n ) = Ts
=
T
T0
T0
T0
T0
T0 2
ω0 s
2
nω0 2
2
⎛ 2π T0 ⎞
⎛ π⎞
⎟⎟
sen⎜⎜ n
sen⎜ n ⎟
T
4
1 T0
⎝ 2⎠
⎝ 0
⎠=1
=
T
2
π
T0 2
2 nπ
0
n
T0 4
2
⎞
⎟
⎟
T0 ⎞
⎛
⎟
⎟ 1 T sen⎜ nω0 ⎟
4⎠
⎝
⎠=
0
=
T
T0 2
nω0 0
4
eq 347
since the pulse serie is offset in time, we lost the symmetry with respect to zero
⎧1, 0 < t < Ts
⎫
⎛ t −T / 2 ⎞
h(t ) = ⎨
⎟
⎬ = ∏⎜
t elsewere⎭
⎝ 2 ⎠
⎩0,
1
0
Ts
t
T0
figure 206
Then using the time delay theorem we get the spectrum
⎛ T ⎞
sen⎜ ω s ⎟
⎝ 2⎠
H ( f ) = e − jπ f Ts Ts
T
ω s
2
eq 348
263
1
cn = e − jnπ f Ts
2
⎛ π⎞
⎛ π⎞
⎛ π⎞
sen⎜ n ⎟
1 T0 sen⎜ n
⎟
⎟
π sen⎜ n
− jnπ
−
jn
1
1
⎝ 2⎠
⎝ 2⎠ = e 2
⎝ 2 ⎠ = e T0 2
π
π
π
2
2
n
n
n
2
2
2
eq 349
which is identical to the preceding form of cn.
The magnitude spectrum is illustrated by the solid lines on figure above. Since delta
functions have infinite value, they can not be plotted; but the weights of the delta
functions can be plotted as shown by the dashed line on figure.
Now compare the spectrum for this periodic rectangular wave with the spectrum for the
rectangular pulse alone. Note that the spectrum for the periodic wave contains spectral
lines, whereas the spectrum for the non periodic pulse is continuous.
Note that the envelope of the spectrum for both cases is the same [sin(x)/x] shape.
Consequently, the null bandwidth (for the envelope) is 1/T for both cases, where T=Ts
is the pulse with. This is a basic property of the digital signalling with rectangular pulse
shapes: the null bandwidth is the reciprocal of the pulse with.
23.9 Guard Period
For a given system bandwidth, the symbol rate for an OFDM signal is much lower than
a single carrier transmission scheme. For example for a single carrier BPSK modulation,
the symbol rate corresponds to the bit rate of the transmission. However for OFDM the
system bandwidth is broken up into Nc subcarriers, resulting in a symbol rate that is Nc
times lower than the single carrier transmission. This low symbol rate makes OFDM
naturally resistant to effects of Inter-Symbol Interference (ISI) caused by multipath
propagation.
Multipath propagation is caused by the radio transmission signal reflecting off objects in the propagation environment,
such as walls, buildings, mountains, etc. These multiple signals arrive at the receiver at different times due to the
transmission distances being different. This spreads the symbol boundaries causing energy leakage between them.
The effect of ISI on an OFDM signal can be further improved by the addition of a guard
period to the start of each symbol. This guard period is a cyclic copy that extends the
length of the symbol waveform. Each subcarrier, in the data section of the symbol, (i.e.
the OFDM symbol with no guard period added, which is equal to the length of the IFFT
size used to generate the signal) has an integer number of cycles. Because of this,
placing copies of the symbol end-to-end results in a continuous signal, with no
discontinuities at the joins. Thus by copying the end of a symbol and appending this to
the start results in a longer symbol time. Figure below shows the insertion of a guard
period.
264
IFFT
IFFT
Output
Guard
Period
TG
Symbol N+1
TFFT
TS
IFFT
Guard
Period
Time
Symbol N+1
figure 207: Addition of a guard period to an OFDM signal
The total length of the symbol is TS=TG + TFFT, where Ts is the total length of the symbol in
samples, TG is the length of the guard period in samples, and TFFT is the size of the IFFT
used to generate the OFDM signal.
In addition to protecting the OFDM from ISI, the guard period also provides protection
against time-offset errors in the receiver.
In multipath environments ISI reduces the effective length of the guard period leading to
a corresponding reduction in the allowable time offset error.
24 DVBT and DVBH
24.1 Signal Constellation and mapping
The system uses Orthogonal Frequency Division Multiplex (OFDM) transmission. All
data carriers in one OFDM frame are modulated using either
• QPSK, 16-QAM, 64-QAM,
• non-uniform 16-QAM or non-uniform 64-QAM constellations.
The constellations, and the details of the Gray mapping applied to them, are illustrated
in figure.
The exact proportions of the constellations depend on a parameter α, which can take
the three values 1, 2 or 4, thereby giving rise to the three diagrams figures 9a to 9c. α is
the minimum distance separating two constellation points carrying different HP-bit
values divided by the minimum distance separating any two constellation points.
Non-hierarchical transmission uses the same uniform constellation as the case with
α = 1, i.e. figure 9a.
265
Im(z) y1,q’
QPSK
Bit ordering:
y0,q’ y1,q’
10 1
-1
11 -1
00
1
Re(z) y0,q’
01
QPSK
Bit ordering:
y0,q’ y1,q’
266
25 Appendix
25.1 Convolution process
The product convolution between two time functions is defined as:
f1 (t ) ∗ f 2 (t ) =
+∞
Inversion process
+∞
∫ f (τ ) ∗ f (t − τ )dτ = ∫ f (τ ) ∗ f [− (τ − t )]dτ
1
−∞
2
1
2
−∞
As an example taking f1 and f2 as shown below and considering a shift τ=0 we have:
267
Step 1: definizione delle funzioni
f1(t)
o
f2(t)
o
t
t
Step 2: inversione della f2 e shift temporale di τ=0
f1(τ)
o
f2(t-τ)= f2[-(τ-t)]→ τ=0→ f2(t)= f2[-(-t)]
o
τ
τ
Step 3: prodotto integrale da - ∞ a +∞ delle funzioni dello step 2
Convoluzione di f1 con f2
f1(τ)
f2(t-τ)
o
τ
o
τ
In the following example taking f1 and f2 as shown below and considering a shift τ=a we
have:
268
Step 1: definizione delle funzioni
f1(t)
o
f2(t)
o
t
t
Step 2: inversione della f2 e shift temporale di τ=a
f1(τ)
o
f2(t-τ)= f2[-(τ-t)]→ τ=a→ f2(t)= f2[-(a-t)]
o
τ
a
τ
Step 3: prodotto integrale da - ∞ a +∞ delle funzioni dello step 2
Convoluzione di f1 con f2
f1(τ)
f2(t-τ)
o
τ
o
τ
269
25.2 Dirac delta function and convolution process
One property of Dirac delta function is that:
f1 (t ) ∗ δ (0) =
+∞
∫ f (0) ∗ δ (t − 0)dτ = f (0)
1
1
−∞
i.e.
f1 (t ) ∗ δ (t ) =
+∞
∫ f (τ ) ∗ δ (t − τ )dτ = f (t )
1
1
−∞
If there is a shift T0 then:
f1 (t ) ∗ δ (t − T0 ) =
+∞
∫ f (τ ) ∗ δ [(t − τ ) − T ]dτ = f (t − T )
1
0
1
0
−∞
in this example τ=t-T0
270
26 Reference
[1]
[2]
[3]
3GPP TS 05.04 V8.4.0 (2001) [ www.3gpp.org ]
Digital and Analog Communication System [Leon W.Couch 2001]
Implementation Effects on GSM,s EDGE Modulation [ Steven V.Schell, www.tropian.com]
E:\documenti per
corsi\ELETTRONICA T
[4]
[5]
WINIQ software for simulating EDGE signal [ www.rhode-swartz.com ]
Introduzione alla modulazioni numeriche [www.univpm Proff. Chiaraluce]
E:\documenti per
corsi\ELETTRONICA T
[6]
Digital modulation in a communications system [Hewlet Packard application note]
E:\documenti per
corsi\EDGE_modulatio
[7]
GMSK in nutshell [Thyerry Turletty 1996 Massachusetts Institute of Technology]
E:\documenti per
corsi\EDGE_modulatio
[8]
[9]
[10]
Digital modulation and GMSK [University of Hull]
Trasmissione delle informazioni [Proff. Diruscio]
Bandwidth efficient modulation [CCSDS 413.0-G-1 april 2003]
E:\documenti per
corsi\telemeteryng en
[11]
PROCEEDINGS OF THE CCSDS RF AND MODULATION SUBPANEL 1E
MEETING OF MAY 2001 CONCERNING BANDWIDTH-EFFICIENT MODULATION [CCSDS
1999]
E:\documenti per
corsi\telemeteryng en
[12]
Theory of frequency and phase modulation [http://www.vk1od.net/FM/FM.htm#Frequency]
[13]
http://telemetry.nmsu.edu/Conference_Pub.html
C:\documenti davide\
documenti per corsi\E
[14]
http://www.ee.byu.edu/faculty/mdr/publications.phtml
[15]
SFCG Meeting SF17 - 28/D Galveston, Texas 16-25 September 1997: CCSDS - SFCG
EFFICIENT MODULATION METHODS STUDY AT NASA/JPL PHASE 3: END-TO-END SYSTEM PERFORMANCE
C:\documenti davide\
documenti per corsi\E
[16]
[17]
OFDM_thesys_lawray
UMTS Architecture model vers 33 [Massaccesi Andrea]
271