Active SNMP S. Keshav Cornell University OPENSIG Workshop
advertisement

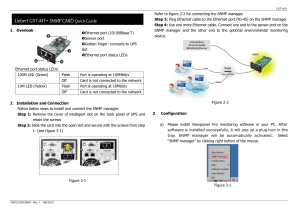
Active SNMP S. Keshav Cornell University (joint work with R. Sharma and M. Wu) OPENSIG Workshop October 6, 1997 Why do we need ambassadors? • Telecom revolution • Jets Ambassadors • • • • Keep track of local news Can react quickly to local events Summarize and report relevant information Can be “field-upgraded” Ambassadors and agents • Ambassadors – Keep track of local news • Agents – Keep track of local routes and multicast information • no horizon effect – Can react quickly to local events – Summarize and report relevant information – Can be “field-upgraded” – Can react quickly to local changes in network state – Summarize and report relevant information – Can be upgraded to provide extensible service Active network • Allows computation, in the form of agents, within a network • Network can actively manipulate data – filter • video layers • firewall – transform • compress – redirect • mobility Two approaches • Active packets – network elements provide runtime environment – extreme • Agents in control path – act on passive packets – more likely to succeed – already exists in a rudimentary form (scheduling) Top-level issues • What are agents allowed to do? • How do we communicate with them? • How do we work with existing infrastructure? What are agents allowed to do? • Effectiveness of an agent depends on – operations it is allowed to perform (execution model) – data it is allowed to see (data model) • Data model + execution model = execution environment • Tradeoff between richness of environment, computation cost, and security How to communicate with them? • Isomorphic to the problem of establishing state within networks • State is currently established by – signaling – routing – network management • Two options – use existing protocols for installing state – new protocol How to be backward compatible? • Subvert an existing protocol • Choices – RSVP – OSPF/BGP/RIP – SNMP SNMP Pros and Cons • Cons – clunky (ASN.1, no scoping) – poor security model (communities) • Pros – – – – widely available simple extensible well-understood Active SNMP • Execution model = Java runtime • Data model = MIB – exposed as a Java class • Snaplets monitor and manipulate MIBs Where do snaplets run? • On the managed object – requires JRE in every managed object – not backward compatible • On a proxy ‘close’ to managed object – not quite perfect, but works Architecture snmplets Get /Set /Get Next Requests Snmplets Manager Active SNMP Proxy SNMPD Naming and parameter passing • Snaplet is embeded in WWW namespace – http://snmp.cs.cornell.edu/snaplets/icmp_monitor/1/1.0/ 2/2.45 • Snaplet instance is embedded in the MIB – csgate1.cs.cornell.edu:1.3.2.5.6.2.6.1 Some applications • Real time control • Fine-grained measurement • Sophisticated trap generation algorithms • Semantic routing – find a path with the most RSVP-compliant routers between a source and a destination. Discussion • • • • • Active networks are not a panacea Add complexity, security holes, and overhead But can do some things otherwise impossible Active SNMP is a pragmatic first step Implementation is up and running at Cornell