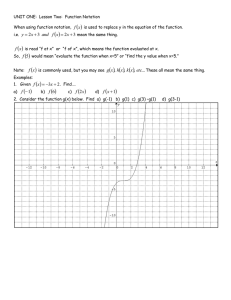
Tutorial: Formal representations of polynomial-time algorithms and security
advertisement

Formal Representation of
Polynomial-Time Algorithms
and Security
Bruce Kapron
University of Victoria
June 9, 2004
Poly-time Function(als) in
Cryptography
• Probabilistic polynomial time (PPT)
function(al)s play a central role in
(asymptotic) complexity-based
cryptography and security
• Appear in definition of: primitives,
adversaries, reductions, verifiers,
provers, simulators, …
PPT Functions in Cryptography
• Central concerns:
– Defining PPT functions or functionals
– Proving that these functions satisfy
appropriate properties
• What does this mean for formalization?
– Explicit vs. implicit representations
– At what level should we be reasoning about
PPT functions
Formalizing PPT Functions
• Do we really need to do this?
– Useful for “low-level” arguments (e.g.
soundness proofs)
– Can be directly applied in a “high-level”
setting, e.g. [MRST 2004]
– Possibility of “bottom-up” formalization
– Other payoffs: e.g., extraction of
reductions from proofs
Implicit vs. Explicit Reasoning
• E.g., reductions between primitives
– Have a PPT mapping M taking any instance f
of X to an instance M(f) of Y
– Security of f implies security of M(f)
• Can show this with a reduction, i.e., a PPT
mapping S taking any adversary A breaking M(f)
to an adversary S(A) breaking f
• Can we formulate proof systems which
guarantee a reduction (do all proof systems do
this?)
Formal representation of poly-time
functions
• We typically use probabilistic TM’s in
cryptographic arguments
• TM’s lack of structure make formal
reasoning difficult
• One approach is to use models with an
inductively defined syntax
Some History
• Beginning with [Cobham, 1964], there have
been numerous function algebras proposed
which characterize poly-time functions –
outgrowth of earlier work in subrecursion
• Focus has been on deterministic computation
without oracles
• Later work considers randomization [LMMS
2000], [IK 2004] and oracle computation
[Constable 1972], [Mehlhorn 1976], [KC 1996]
Function Algebras
f1,f2,…,fk – collection of initial functions
S1,S2,…,Sl – collection of closure schemes
[f1,…,fk,S1,…,Sl] – smallest class containing
f1,f2,…,fk and closed under S1,S2,…,Sl
Can we capture FPTIME, the class of all
poly-time functions?
Recursion on Notation
• Use primitive recursion on binary
notation of the recursion parameter to
capture polynomial time
f(x,0)=g(x)
f(x,s0(y))=h0(x,y,f(x,y))
f(x,s1(y))=h1(x,y,f(x,y))
Recursion on Notation
• Problem with this scheme: iterating a
poly-time function a polynomial number
of times can produce functions with
exponential growth rate:
• Define: f(x)=x2, g(y)=f|y|(2)
• Then: |g(y)|=2|y|
Bounded Recursion on Notation
(BRN) [Cobham, 1964]
f(x,0)=g(x)
f(x,s0(y))=h0(x,y,f(x,y))
f(x,s1(y))=h1(x,y,f(x,y))
|f(x,y)| · |k(x,y)|
Bounded Recursion on Notation
and Poly-time
• Let si(x)=2x+i (i=0,1), #(x)=2|x|¦|x|,
and I denote the set of all projection
functions. f is defined from g,h by
composition (COMP) if
f(x)=h(x,g(x))
• Theorem [Cobham,1964]:
[0,s0,s1,#,I;COMP,BRN] = FPTIME
Drawbacks of BRN
• The need for an explicit size-bound in
BRN is problematic in proofs
• In general, bounding is not decidable
• Term definition requires a bounding
proof – circularity problem
• One solution: modify BRN to only allow
hi with |hi(x,y,z)| · |ki(x,y)|+|z|
Safe Recursion on Notation
[Bellantoni & Cook, 1992]
• Idea: only allow recursion to iterate
functions which are not already defined
by recursion.
• Requires a typing of function
parameters as either safe or normal –
operations on safe inputs do not
increase length by more than an additive
constant
Safe Composition and Recursion
on Notation
• Composition scheme prevents safe
inputs from being substituted into
normal positions:
f(x;a)=h(r(x;);t(x;a))
normal
safe
no safe
input
Safe Recursion on Notation
f(0,x;a) = g(x;a)
f(si(y),x;a) = hi(y,x;a,f(y,x;a))
• No external bound required – basis for
purely type-theoretic characterization
of poly-time [Hofmann 1999], later used
by [LMMS 2000] to get a term algebra
for probabilistic polynomial time
Full Concatenation Recursion on
Notation (FCRN) [Ishihara 1999]
• Based on CRN [Clote 1990], which can
be used to characterize AC0
f(x,0)=g(x)
f(x,s0(y))=f(x,y) ± sg(h0(x,y,f(x,y)))
f(x,s1(y))=f(x,y) ± sg(h1(x,y,f(x,y)))
Equivalence
Let
msp(x,y)=b x/2|y| c,
c(x,y,z)= if x mod 2=0 then y else z
and
F1=[0,I,s0,s1,c,msp,#;COMP,FCRN]
F2=[0,I,s0,s,c,msp;SCOMP,SRN]
F3=[0,I,s0,s1,#;COMP,BRN]
Then
FPTIME=F1=F ’2=F3
Proof Systems
• PV [Cook 1975] : Terms are built up from
variables and function symbols re F3. formulas
are equations between terms
• Defining equations for every term of F3 are
included as axioms – need more initial
functions
• Rules include reflexivity, symmetry and
transitivity, rules for substitution and
induction on notation
Induction on Notation
• Counterpart to definition by BRN:
f1(x,0)=g(x)
f1(x,si(y))=hi(x,y,f1(x,y))
f2(x,0)=g(x)
f2(x,si(y))=hi(x,y,f2(x,y))
f1(x,y)=f2(x,y)
Beyond PV
• Extensions
– PV1 [Cook 1975] - adds propositional
connectives
– CPV, IPV [Cook Urquhart 1993] – adds
first-order logic
• Can obtain more natural induction rules,
e.g. for appropriate
((0) Æ 8x((bx/2c) ! (x))) ! 8x(x)
Beyond PV
• Implicit formal systems also possible,
e.g. S12 [Buss 1986] – poly-time
functions are those definable in the
system by a class of bounded formulas
and provably total using limited
induction on notation
• S12(PV) is conservative over PV
Adding Randomization
• [Impagliazzo Kapron 2004] takes the
following approach: terms are PV terms or of
the form
x ÃR {0,1}p(n).t
i ÃR [p(n)].t
where t is a term
• Formulas have the form u ¼ v (u,v closed)
• Intended interpretation of formulas:
ensembles represented by u and v are
computationally indistinguishable
“Induction” for Computational
Indistinguishability
H-IND rule:
i ÃR [p(n)] .t(i) ¼ i ÃR [p(n)] .t(i+1)
t(0) ¼ t(p(n))
Other Rules
PV ` t(x) = s(x)
x ÃR {0,1}p(n).t(x) ¼ x ÃR {0,1}p(n).s(x)
u¼v
t{u/x} ¼ t{v/x}
UNIV
SUB
Also need EDIT rule for basic manipulation,
e.g
x,y ÃR {0,1}p(n).x ± y ¼ z ÃR {0,1}2p(n).z
A Methodology for Reduction
Proofs
• Start with instance f of primitive X:
introduce new function symbol, axioms
expressing security property for X
• Obtain instance g of primitive Y in F3[f],
prove that it satisfies security property for
primitive Y using axioms for f
• What about reduction of adversaries?
Implicit – follows from soundness
An Example
• Stretching the output of a PRG
[Goldreich Micali ’89]
• Introduce a new function symbol f
representing a PRG which stretches by 1
bit:
x à {0,1}n.f(x) ¼ x à {0,1}n+1.x
• Abbreviate: b(x)=f(x)1, r(x)=f(x){2,…,|x|},
so f(x) = b(x) ± r(x)
Example (contd)
• Define by BRN
r’(x,0)=x
r’(x,i+1)=r(r’(x,i))
b’(x,0)=
b’(x,i+1)=b’(x,i) ± b(r’(x,i))
f’(x,i)=b’(x,i) ± r’(x,i)
Claim:
x ÃR {0,1}n.f’(x,n) ¼ x ÃR {0,1}2n.x
Example (contd)
• Need one lemma :
PV ` f’(x,i+1) = b(x) ± f’(r(x),i)
(straightforward induction). By UNIV,
x ÃR {0,1}n, i ÃR [n].f’(x,i+1)
¼ x ÃR {0,1}n, i ÃR [n].(b(x) ± f’(r(x),i))
Then from the definition of f, along with SUB
and transitivity, we get
x ÃR {0,1}n, i ÃR [n].f’(x,i+1)
¼ x ÃR {0,1}n+1, i ÃR [n].(x1 ± f’(x{2…n+1},i))
Example (contd)
It then follows from SUB that
x,z ÃR {0,1}n, i ÃR [n].(z{1…n-(i+1)} ± f’(x,i+1))
¼ z ÃR {0,1}n+1, x ÃR {0,1}n+1, i ÃR [n].
(z{1…n-(i+1)} ± x1 ± f’(x{2…n+1},i))
Define h(z,x,i)= z{1…n-i} ± f’(x,i).Then from the
preceding, with several applications of
EDIT and transitivity, we get:
x,z ÃR {0,1}n i ÃR [n].h(z,x,i)
¼ x,z ÃR {0,1}n i ÃR [n].h(z,x,i+1)
Example (contd)
By H-IND, we obtain
x,z ÃR {0,1}n.h(z,x,0) ¼ x,z ÃR {0,1}n.h(z,x,n)
Finally, several applications of UNIV (to
the definition of h), along with EDIT
and transitivity, yield
x ÃR {0,1}n.f(x,n) ¼ x ÃR {0,1}2n.x
The Full Example
• By running backwards through this proof,
we automatically construct, for any A
breaking f’, an A’ breaking f defined by:
A’(y)=zÃR {0,1}n, i ÃR [n].A(z{1…n-(i+1)}± y1 ±f’(y{2…|y|},i))
Conclusions
• Formal reasoning about PPT functions in
cryptographic settings is doable in a fairly
direct way – still seems far from practical
application
• Need to extend to more complex notions (e.g.
pseudorandom functions, ZK) and arguments
• Look for extensions of function algebras (e.g.
process calculi)
• Interesting theoretical questions (e.g.
formalization of non-black-box arguments)