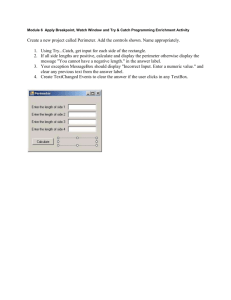
i A PROTOTYPE TO EVALUATE INFORMATION
advertisement

i A PROTOTYPE TO EVALUATE INFORMATION SECURITY AWARENESS LEVEL FOR TEACHER AND STUDENT IN SECONDARY SCHOOL NURUL HIDAYAH BT AB RAHMAN UNIVERSITI TEKNOLOGI MALAYSIA A PROTOTYPE TO EVALUATE INFORMATION SECURITY AWARENESS LEVEL FOR TEACHER AND STUDENT IN SECONDARY SCHOOL NURUL HIDAYAH BT AB RAHMAN A dissertation submitted in partial fulfillment of the requirements for the award of the degree of Master of Computer Science (Information Security) Faculty of Computer Science and Information System Universiti Teknologi Malaysia NOV 2009 iii Dedicated to Nadim and Eti iv ACKNOWLEDGEMENT In preparing this thesis, I received guidance and encouragement from my supervisor, Dr Rabiah Ahmad, without whom I might not be able to complete this thesis. I extended my appreciation to all of my family, colleagues and others who have provided assistance and support. To SMKTTDI staff and student who are willing to participate during user testing. May Allah bless all of us. v ABSTRACT This study attempted to develop a prototype to evaluate information security awareness level for teacher and student in secondary school. It identifies the information security awareness level by measure the level using an assessment model and automated tool. The assessment model for this study is Affect, Behavior, Cognitive (ABC) model from social cognitive theory where it equals with three dimensions which are attitude, behavior, and knowledge that have been used as measurement component for this study. The methodology for the whole study is System Development Life Cycle (SDLC) by applying waterfall model. The awareness level is evaluated based on the three dimensions from five focus areas for each teacher and student category. The user testing has been done among some teachers and students to test the prototype. As a result, all of the prototype function are working properly and able to produce the expected output. It shows that the prototype can be implemented in real world with some improvement for better result. vi ABSTRAK Kajian ini dilakukan untuk membina prototaip bagi menilai tahap kesedaran maklumat di kalangan guru dan pelajar sekolah menengah. Ia menilai tahap kesedaran keselamatan maklumat dengan mengukurnya menggunakan model penilaian. Model penilaian untuk kajian ini adalah ABC model, dari teori kognitif sosial. Model berkenaan bersamaan dengan tiga dimensi iaitu pengetahuan, kelakuan dan tingkah laku yang digunakan sebagai komponen pengukur untuk kajian ini. Metodologi untuk kajian ini adalah Kitar Hayat Pembangunan Sistem dengan mengaplikasikan model waterfall. Tahap kesedaran dinilai menggunakan tiga dimensi tersebut berpandukan lima topik utama untuk setiap kategori guru dan pelajar. Ujian pengguna telah dijalankan untuk mengenalpasti kebolehfungsian prototaip ini. Hasilnya, ia berjaya berfungsi seperti yang dirancang dan mengeluarkan output yang dikehendaki. Ini menunjukkan prototaip ini boleh dilaksanakan dengan sedikit penambahbaikan untuk menghasilkan produk dan keputusan yang lebih baik. vii TABLE OF CONTENTS TITLE CHAPTER 1 2 PAGE DECLARATION ii DEDICATION iii ACKNOWLEDGEMENT iv ABSTRACT v ABSTRAK vi TABLE OF CONTENT vii LIST OF TABLES x LIST OF FIGURES xi LIST OF ABBREVIATIONS xii LIST OF APPENDICES xiii INTRODUCTION 1 1.1 Overview 1 1.2 Problem Background 1 1.3 Problem Statements 3 1.4 Project Objectives 3 1.5 Project Scope 4 1.6 Project Summary 4 LITERATURE REVIEW 5 2.1 Introduction 5 2.2 Information Security 5 2.3 Information Security Awareness 7 2.4 Information Security Awareness for Student and Teacher 9 2.5 Affect, Behavior, Cognitive (ABC) Model 12 viii 2.6 2.7 3 6 16 18 3.1 Introduction 18 3.2 Methodology 18 3.2.1 Feasibility Study 19 3.2.2 Analysis 21 3.2.3 Design 26 3.2.4 Implementation 28 3.2.4.1 Hardware Requirement 28 3.2.4.2 Software Requirement 29 3.2.5 Testing 29 3.2.6 Maintenance 30 Summary 30 INFORMATION SECURITY AWARENESS FOR TEACHER AND STUDENT TOOL (ISATS) 31 4.1 Introduction 31 4.2 Information Security Awareness For Teacher And Student Tool (ISATS) 31 4.2.1 Admin Login 32 4.2.2 34 4.3 5 Summary 13 METHODOLOGY 3.3 4 Automated Tool to Measure Information Security Awareness Level Teacher Category Survey 4.2.3 Student Category Survey 34 4.2.4 Survey Result 35 4.2.5 Overall Survey Result 37 Summary 39 DISCUSSION 40 5.1 Introduction 40 5.2 Discussion of ISATS 40 5.3 Summary 41 CONCLUSION 42 6.1 Introduction 42 6.2 Limitations 42 6.3 Conclusion Remarks 43 ix 6.4 Future Work REFERENCES APPENDICES A-H 44 45 49-86 x LIST OF TABLES TABLE NO. TITLE PAGE 3.1 The Five Focus Area 22 3.2 The Part of Questions for Password Protection and 24 Management Focus Area (Teacher Category) 3.3 Weights Scale 25 3.4 Awareness Scale 26 xi LIST OF FIGURES FIGURE NO. TITLE PAGE 2.1 ABC Model 13 2.2 Interface of Evaluation Mode 14 2.3 Interface of Online Information Security 15 Awareness for Children 2.4 ASSET Interface 16 3.1 Waterfall Model 19 3.2 Top Internet Main Use (Student) 20 3.3 Top Internet Main Use (Teacher) 21 3.4 The Assessment Model 23 4.1 Login Form 32 4.2 Admin Access Menu 33 4.3 End User Access Menu 33 4.4 Teacher Category Survey 34 4.5 Student Category Survey 35 4.6 Survey Result 35 4.7 Retrieve Survey Result (Student Example) 36 4.8 Retrieve Result (Teacher Category Example) 37 4.9 Overall Survey Result 38 xii LIST OF ABBREVIATION ABC - Affect, Behavior, Cognitive ICT - Information and Communication technology ISATS - Information Security Awareness Level for Teacher and Student Tool SDLC - System Development Life Cycle (SDLC) SMKTTDI - Sekolah Menengah Kebangsaan Taman Tun Dr Ismail xiii LIST OF APPENDICES APPENDIX TITLE PAGE A Gantt Chart 49 B Survey Question 50 C Top Internet Main Use Survey Questions 56 D Entity Relationship Diagram 60 E Context Diagram 61 F Data Flow Diagram 62 G Flowchart 63 H ISATS Source Code 67 CHAPTER 1 INTRODUCTION 1.1 Overview This study is to develop a prototype to evaluate information security awareness level for teacher and student in secondary school. The purpose of the prototype is to identify the level of information security awareness based on assessment model. This chapter describes the problem background of this project, problem statements, objectives, scopes and plans for this project. 1.2 Problem Background Information and Communication Technology (ICT) has rapidly evolved and impacted on all age level. Most youth are ICT literate nowadays and topic like Friendster, MySpace, e-mail, and chatting have became their daily conversation. In 2 addition, most school especially in urban area also provides computer facilities with Internet service provided. Information security is the one of the concern when people use Internet. Particularly, secondary school students are gain exposure to the Internet technology but do they really aware on information security? Are they aware with the terms like Trojan horse, spyware, spamming and so on? Furthermore, do their teachers aware with information security issue? In fact, the level of security awareness among teachers must be addressed as well as they are suitable person to educate students. There are three reasons for information security professional need to aware of people attitude towards information security. As described in Information Security Management Handbook (2007), the three reasons are: i) Behavior predictor – Attitude is a good predictor of behavior. That is the point where survey can be a tool to determine the behavior of target population toward information security issues. The information can be used to predict how secure the environment will be. ii) Target of change - Subtly or directly change someone attitude, consequently change behavior. iii) Source of risk -Extreme attitude toward someone or something can lead to irrational cognitive function and behavior. According to above reasons, survey can be a tool to predict the security of an environment based on user behavior. In Malaysia, there is still no study to identify teacher and student information security awareness level. Research findings by Chai, et.al. in 2006 suggest that students, who have strong self-efficacy toward Information Security on the Internet and have an exposure of information security from school, parents and media, are more likely to practice information security such as updating anti-virus software, not opening emails from unknown senders, and protecting personal information on the Internet. To motivate students’ information security behavior, we need to provide more 3 information security education opportunities to students as well as chances for students to be exposed to information security issues. 1.3 Problem Statements a) There is no proper assessment model to evaluate the information security awareness level for teacher and student in secondary school. b) There is a need to identify teacher and student awareness level to have perception or give idea of their information security awareness level. 1.4 Project Objectives The objectives of this project will be as follows: i) To develop an appropriate model of information security awareness to secondary teacher and student. ii) To develop a prototype to evaluate information security awareness level for teacher and student in secondary school. iii) To identify the level of information security awareness in secondary school teachers and students. 4 1.5 Project Scope The prototype will focus on capture user input for questionnaire answer and generate the outputs as the survey result. The survey result will indicate the awareness level of user. Besides, the prototype will generate the average level of users according to their category. It will be evaluated from their knowledge, behavior, and attitude towards information security. The total of those three dimensions would be their total awareness level. The calculation and scale is based on reviewed previous study. In addition, there is an administrator to monitor and maintain the prototype. Administrator will manage the data of the prototype and only administrator has access to view the overall survey result. The end user only can view their individual result only. 1.6 Summary This project is carried out to develop an automated tool that can identify the information security awareness level so that it can be use to give input for more effective information security awareness program. This chapter highlights the problem background, project objective, problem statement, and project scope. Chapter 2 discusses the related secondary sources with this study like journal, article, and so on. 5 CHAPTER 2 LITERATURE REVIEW 2.1 Introduction In this chapter, some studies and works regarding information security awareness are reviewed. A few similar studies are assessed in order to determine the appropriate operational framework for this study. The Affect, Behavior and Cognitive (ABC) model, a model from social psychology field to assess attitude is discussed to obtain clear view regarding the method that will be used in this study. 2.2 Information Security Information security is not a new thing or issue. It has exists a long time ago before the invention of computer to protect information. Ceasar’s cipher was employed by Julius Caesar on his military campaign in order to safely communicate important messages to his generals (O’Regan, 2008). Dlamini quoted Russel and Gangeni (2008), in the 1840s when the telegraph was invented an encryption code was developed to safeguard the secrecy of the transmitted telegrams. Then, 6 legislation prohibiting wiretapping was applied one year after the invention of telephone. Information security has moved from protecting the secrecy of hand written messages to telegrams, to telephone conversations and later to the world of computing (Dlamini, et. al., 2008). The importance of information protecting has been aware a long time ago and initiates people to think on how to protect information, then invent encryption code and later integrate the code into computer technology. However, with the technology grown, security breaches make it move as well. In the early days, the viruses without causing any serious damage to computer system arouse. Currently, many types of computer security attack and critical damage has occurred make a lot of people scared especially when using online banking or any other online system. Here, information security scope become wider and many organizations take a move to take care about it. According to Thomson and Solms (1998), a great challenge has been brought by the advent of the personal computer, as well as the increasing complexity and reliability of networks, in the area of information security. The challenges as addressed by Thomson and Solms are described below: • The decreasing price and increasing capabilities of personal computers resulted in many people in the organization acquiring these machines. • The ever increasing number of software development packages available made it possible for these people to start developing their own systems. • The knowledge gained from developing these systems could often give them the capability to circumvent security measures built into the current systems. • The ever increasing use of the Internet meant that there were potential threats from outside the organization. 7 It shows that the emergence of technology also give impact in the area of information security. Each type of technology has its own pro and cons like Internet usage can bring user to borderless information searching but at the same also bring borderless virus attack. Internet and computer user is not limited to workers at organization but home users as well. As the result, the attack target become broader where home users can be the victim. IS027001 defined information security is all about protecting and preserving information. It is all about protecting and preserving the confidentiality, integrity, authenticity, availability, and reliability of information. Information systems may be secured by preventing, detecting, and correcting internal and external threats (Chen, et. al., 2006). In order to protect and preserve information, it is important to prevent, detect and correct any internal and external threats. Most industries are dependent to Information Technology (IT) technology and infrastructure to store information nowadays. Therefore, all security aspects must be addressed carefully to avoid any security breach or incidents. In addition, end user must have the basic of prevent and detect threats at least. 2.3 Information Security Awareness Attackers have matured from using hacking skills to show that they can circumvent the authentication process to access each other’s files to use them in the theft of confidential information (Dlamini, et al, 2008). Currently, most of our information is reside on electronic database and attract the adversary for social engineering, phishing, identity theft and other white collar crime. If users are not aware with the new type of stealing, they can easily expose their sensitive information and become victim. 8 Today’s security problems are primarily due to the inadequate security awareness of users, which can be mitigated without the need for sophisticated security technologies (Chen, et al., 2006). Human factor plays important factor as well especially to avoid human error factor. For that reason, it is important to create the awareness among user. The term ``information security awareness'' is used to refer to a state where users in an organization are aware of the ideally committed to their security mission (often expressed in end-user security guidelines) (Siponen, 2000). Besides technical computer security issue, information security awareness issue must be focused as well. Although the best security technology has been implemented, it cannot avoid other types of security attack like social engineering. User must really understand and know regarding IT security threats in order to ensure they can react for security incidents properly. A survey for security perception of personal novice Internet at United Kingdom (UK) user shows that 43% claimed not to understand the threats, 38% claimed they did not know how to use security packages, 35% indicated that they did not know how to secure their computer, and 32% indicating that they did not know about the threats (Furnell, Bryant and Phippen, 2007). Besides, it also reveals that 17% had systems that were used by children under 12, whereas 18% had computers that were used by children aged 12–18 (the overall proportion of respondents with children was 30%). With the advent of Internet users, the focus of information security awareness has become broader and not only cover end user at organization. Furnell (2007) also found that the fact that organizations are tightening their defenses leaves home user systems as attractive targets for compromise. As the security aspects whether physical or logical are not really being focused by home user, it leaves vulnerable for them. 9 2.4 Information Security Awareness for Student and Teacher The extra concern must be addressed to user between 12 – 18 years old. The user, obviously school student can be the main target for attacker. This can be explained by the fact that students are typically transient and have less credit history than more established adults (Yacine and Marks, 2008). It is crucial to protect them from exposed to security threat risk and they also need to be aware with information security. A study by Wee (1999) had identified the pattern of Internet use among upper secondary science students from fourteen schools in Kuala Lumpur, Malaysia. According to the study findings, about 51.5 percent of respondent used the Internet and they mainly accessed the Net from their homes and acquired Internet skills by self-teaching or learning from friends. The finding also stated that most of the Net users (91.4 percent) explored the World Wide Web while 75.4 percent used E-mail, 52.1 percent used IRC or ICQ, 15.7 percent joined Newsgroups, 2.2 percent used it for downloading, and 0.6 percent used it for playing online games. From the study on 1999, 51.1% respondent used the Internet and the total can be increased nowadays due to decreased price of personal computer and the ease of Internet access. Furthermore, the study also found that the students gained Internet skills by self teaching or learned from friend and it shows that the school student group might not have proper knowledge on how to use Internet safely. There is probability that they are lack of information security knowledge. In addition, hacking is a growing problem among the teenage community (Zahri and Sharifah Sajidah, 2005). Teenagers have gained interest in terms of computer hacking, software cracking, and Web site defacement. Furthermore, there are a lot of free hacking tool available on the Internet ease their intention without programming knowledge. However, they only look for excitement and do not understand the real implications of their actions. In fact, a group of computer-savvy youth, between 18 and 25 years old had been arrested in Kuala Lumpur after scoring a first of sorts for phishing (Lee Shi-Ian, 2006). 10 School can be a perfect place to educate and make them aware with information security. As described by Hentea (2005), information security awareness has to be provided to students at an earlier age and if we teach children security awareness earlier, they will be prepared to pay attention to security matters as well as to avoid getting engaged in illegal behavior. Student can be less interest on learning information security after they enter higher education as they have learned computer skills. It is more suitable to expose the information security knowledge earlier so that it can be guide for them in future and the knowledge gained parallel with computer skill. Hentea (2005) also suggests that educators and parents must be trained on how to handle information security issues and how to use computers so that they will be better prepared to provide training to youngsters. Teacher is suitable person to deliver the information security knowledge as they have well-trained to educate student. However, teacher must be prepared with the knowledge first. As a result, the information security awareness is important to both teacher and student. Professional Information Security Association (PISA) has conducted a survey of information security at education sector on 2003, in Hong Kong. The results show that most of the schools had some measures on basic security precautions such as installing anti-virus programs (98%) and using web content filtering (78%). But the use of more advanced information security measures was not popular (for example: only 52% use firewall, 9% use intrusion detecting system, etc.). The lack of competency among school personnel contribute to the result. They must be exposed or trained with at least basic information security requirement. A security awareness program at school has been launching at Hyderabad, India by Center for Development of Advanced Computing. The program scopes for student and teacher cover guidelines, information, handbook and quizzes. Besides, National Cyber Security Awareness (NCSA) also executed information security awareness program at 2004 and one of the audiences are education audiences including K-12 and higher education (Hentea, 2005). 11 Those information security awareness programs were focused on nontechnical security issue. The difference between technical and non-technical is technical information security issues focus mainly on the technical-oriented knowledge and tools (such as encryption techniques) that are required to secure and protect information whereas non-technical include all the non-technical-oriented knowledge that is required to secure and protect information and information systems (Kritzinger and Smith, 2008). Most of school teachers and students do not received formal or specialized knowledge in terms of computer security. Therefore, it is proper to measure their non-technical security issues. United States Computer Emergency Readiness Team (US-Cert) listed the non-technical security issues are as follows: i) General security – password, firewall ii) Attacks and threats iii) Email and communication iv) Mobile devices v) Privacy vi) Safe browsing vii) Software and Applications Some countries have implemented the information security awareness program at school. As school students are one of the computer and Internet users nowadays, it is very vital to provide them with the information security knowledge. The knowledge can avoid or reduce them from security threats like social engineering, phishing, and spyware attack. In addition, teachers at school must be prepared as well as they are accountable to educate the students. 12 2.5 Affect, Behavior, Cognitive (ABC) Model Attitude is defined as our positive or negative response to something. For example when people have positive feeling on privacy, automatically they are not willing to give out network password to unauthorized people. On the contrary, if they have negative feeling on privacy, they will be more willing to give password or any confidential information to unauthorized people. One of the most widely assumed models of attitude structure is the tripartite model (Anthony, R.P., 1989; Brecker, 1984; Rosenberg&Hovland, 1960). According to Information Security Management Handbook, ABC model also known as Tripartite model presents attitude as an amalgam of three separate measurable components which are affect, behavior, cognition (refer to Figure 2.1). ABC model stemming originally from the Yale Communication and Attitude Change Program at Yale University through the 1950s and 1960s, but sharing a fundamental viewpoint with many other philosophical traditions (Martha, A. et.al., 2006). The descriptions of the three components are as follows: i) Affect - emotional aspect of our attitude, our feelings toward an object or subject play an important role in determining our attitude. ii) Behavior - derived from the fact that our behavior serves as a feedback mechanism for our attitudes. iii) Cognitive - thoughtful, thinking aspect of our attitude. Opinions toward an object or subject can be developed based widely solely on insightful, process-based thinking. 13 Affect Attitude Behavior Cognitive Figure 2.1: ABC Model (Information Security Management Handbook, 2007) Other researchers have already performed work where the social sciences were related to the field of information security awareness like Schlienger and Teufel (2003) made use of social-cultural measures to define a model for analyzing information security culture in organizations. Besides, Chai, S. et. al. (2006) also applied social cognitive theory in an exploratory study of middle school children’s information security behavior. 2.6 Automated Tool to Measure Information Security Awareness Level A prototype model to measure information security awareness at an international gold mining company has been developed (Kruger and Kearney, 2006). The model makes use of a simple data gathering process and weighting system and, combined with certain multi-criteria problem solution techniques, provides a quantitative measurement of security awareness levels. The study used ABC model as a basis and three equivalent dimensions namely what does a person know (knowledge); how do they feel about the topic (attitude); and what do they do (behavior). 14 Furnell, Gennatou, and Dowland (2002) have developed a prototype tool for information security awareness in training. The tool implemented in Visual Basic (VB), in order to provide interactive and user-friendly approach to enhance user understanding of IT security. The tool comprises three modes of operation which are exploration mode, evaluation mode and author mode. The evaluation mode (refer to Figure 2.2) is similar with this study where the user can test their understanding of security by applying countermeasures to the example scenario. Figure 2.2: Interface of Evaluation Mode Another similar work is the online information security quiz for children developed by Center for Development of Advanced Computing (refer to Figure 2.3). The questions will test the children understanding and generate respond to children answer whether it is true or wrong. The awareness level is measured from the score obtained by answering quiz questions. 15 Figure 2.3: Interface of Online Information Security Awareness for Children (in http://infosecawareness.in/isea/children/quiz-for-children) National Institute of Standard and Technology (NIST) has developed a tool named Automated Security Self Evaluation Tool (ASSET) in 2003. The aim of ASSET is to provide a centralized place for the collection of data used to assess a system. The control objectives and techniques are taken from long-standing requirements found in statute, policy, and guidance on security. ASSET consists of two host-based applications: ASSET – System and ASSET – Manager. The report of ASSET is designed to give clear picture of their resources security status. ASSET – System facilitates the gathering of individual system data and provides a limited reporting capability. It allows the user to determine the completeness of an individual system assessment in progress. ASSET – Manager aggregates individual system assessments created by ASSET – System. It assists managers in developing an organization-wide perspective on the state of IT system security. Figure 2.4 shows the interface of ASSET. 16 Figure 2.4: ASSET Interface 2.7 Summary The reviewed of the term, attitude concept, and previous similar studies have given adequate input to precede this project. Some aspects of the previous study also can be guide for this study such as the issues to be covered in order to examine information security awareness level, research design and the example of system modules. The next chapter will discuss regarding project methodology used to accomplish this study. 17 CHAPTER 3 METHODOLOGY 3.1 Introduction This chapter discusses the proposed methodology in order to develop the prototype to evaluate information security awareness level among teachers and students at secondary school. The identified components from previous chapter will be mapped into the system architecture depending on its functionality and its requirement. 3.3 Methodology System Development Life Cycle (SDLC) is the method that would be used to develop the prototype for this study. SDLC is a conceptual model used in project management that describes the stages involved in an information system development project from an initial feasibility study through maintenance of the completed application. 18 Waterfall model is the methodology of SDLC that would be applied to his study. It takes the fundamental process activities of specification, development, validation and evolution and represents them as separate process phases (Sommerville, 2001). Six phases involved in waterfall model which are feasibility studies, analysis, design, implement, test and maintain. Figure 3.1 presents the schematically view of waterfall model. Figure 3.1: Waterfall Model 3.2.1 Feasibility Study At this stage, the major functions of the intended prototype will be defined. The goals and objective of this project is determined at this phase. The assumption of the project duration is defined using Gantt chart (refer to Appendix A) to ensure the development process going smoothly. Then, the major functions of the intended prototype would be defined. Journals, articles, conference papers and books are reviewed as secondary source for this study. The reviewed sources are from related topic like information security awareness, information security awareness among teacher and student, automated tool to evaluate information security awareness level and social cognitive 19 theory to measure people attitude. All inputs from reviewing secondary source are used to identify component for the prototype. The initial part to concern is what component to measure the information security awareness level among teacher and student. From earlier studies, social cognitive theory is widely used to explain individual behavior. As described in previous chapter, there are some similar studies which use social cognitive theory to measure the level of information security awareness level. The ABC model that comprises three components which are affect, behavior and cognitive is used as the base and the three equivalent dimension from the model was developed namely: i) knowledge - what does a person know ii) attitude - how do they feel about the topic iii) behavior - and what do they Knowledge is equivalent with cognitive, based on ABC model where cognitive means thoughtful or thinking aspect of our attitude. Attitude is equivalent with affect, to show feelings towards a subject or object while there is no change for behavior. This approach has been used by Kruger and Kearney (2006) to develop a measuring information security awareness tool in gold mining company environment. However, this study applies the model in secondary school environment with the teacher and student as end users. 20 3.3.2 Analysis During analysis phase, a detailed study of the prototype needs is carried out. The information from the previous phase is gathered and being analyzed carefully to verify the prototype requirement as identified at feasibility phase. After identified three dimensions to measure information security awareness level, there is a need to identify the focus areas for this study. Non-technical security issue has been chosen as the main focus as most of the end users do not have proper knowledge regarding security term. The lists of non-technical areas from US-CERT as described in Chapter 2 become main reference to identify the focus area. Besides, a survey among 23 teachers and 99 students at Sekolah Menengah Kebangsaan Taman Tun Dr Ismail has been conducted to identify their Internet main uses. The survey question can be referred to Appendix C. The survey result (refer to Figure 3.2 ) indicated that 55.6% of students use Internet for Social Network Sites, 30.4% teachers use Internet for email and 26.1% teachers use for online banking or paying bills (refer to Figure 3.3). Figure 3.2: Top Internet Main Use (Student) 21 Figure 3.3: Top Internet Main Use (Teacher) There is also consideration for hacking problem among teenagers as reviewed earlier. The combination of the reviewed secondary source and survey, five focus areas has been identified for this prototype (refer to Table 3.1). However, the focus areas can be increased or modified in future. Focus Areas Teacher Student i) Password Protection i) Password Protection and and Management Management ii) Email and Internet ii) Virus threats and attack iii) Virus threat and iii) Hacking attack iv) Mobile device and iv) communication v) Identity engineering Email/Internet/Social Network Sites theft/social v) Mobile device communication Table 3.1: The Five Focus Areas and 22 A reviewed papers regarding hacking problem among teenagers is considered and hacking is one of the focus area for student. Meanwhile, the survey result shows that Social Network Sites is the main use of Internet among school student and it is also include as the student’s focus area. The survey result also shows that Internet banking is one of the Internet main uses for teacher, hence there is issue regarding their awareness on social engineering or identity theft. The rest of focus areas are referred to US-CERT list of non-technical issues. Five focus areas for each teacher and student are subdivided from each one of the three dimensions. Tree structure is used to aid in structuring the criteria and forms the assessment model. A tree structure is a way of representing the hierarchical nature of a structure in a graphical form. Figure 3.4 depicts the tree structure developed. From Figure 3.4, it shows that the five focus areas are mapped to each one of the three dimensions. 23 Password protection and management Email and Internet Knowledge Virus threat and attack Teacher Behavior Mobile devices and communication Attitude Identity theft and social engineering Overall Awareness Level Password protection and management Email/Internet/Soci al Network sites Knowledge Virus threat and attack Student Behavior Attitude Mobile devices and communication Hacking Figure 3.4: The Assessment Model 24 Questions that will be asked to end users are representing each focus area in associate dimension. Table 3.2 presents the part of questions for password protection and management focus area for teacher category. The full questions for both categories can be referred to Appendix B. The questionnaire are comes from several sources like from the Purdue University, Center for Education and Research in Information Security (CERIAS), Security Awareness Quiz Question (Melissa, G. 2001) and questionnaire from the University of Florida’s IT Security Team. Those questions were combined and revised based on this study suitability. Focus Area Questions Knowledge Behavior Attitude Password When constructing a Do you use same The best way that you protection password you should: password and A. use sport’s name, different for can online password management pet’s name and add accounts? number at the end. protect A. Always your from disclosure: A. Write it down and B. use phrases or B. Often kept it in secure place misspelled word with C. Rarely without embedded information. character D. Never header and number B. Kept in a computer C. file. use sequenced number and character from keyboard D. All of the above Table 3.2: The Part of Questions for Password Protection and Management Focus Area (Teacher Category) 25 The following weights scale is used to compute the measurement of information security awareness level (refer to Table 3.3). Each question has its own score where when the score is accumulated, it contributes to the total of weighting for each dimension. The scale has been used by Kruger and Kearney (2006) to compute the level of information security awareness level where the weight was determined using the Analytic Hierarchy Process (AHP). Thomas L. Saaty developed the AHP and a good description of the technical details and application possibilities can be found in Saaty (1980) and Vargas (1982). The AHP approach makes use of pair-wise comparisons to provide a subjective evaluation of factors based on management’s professional judgment and opinion. The comparisons are made using a preference scale, which assigns numerical values to different levels of preference. A square matrix is then derived from the pairwise comparisons and a scale is extracted based on the matrix’s eigenvector associated with the largest eigenvalue. When this vector is normalized to sum to one, the solution is unique and represents a numerical measure of the decision maker’s perceptions of the relative importance of criteria. Dimension Weighting Knowledge 30 Attitude 20 Behavior 50 Table 3.3: Weights Scale (Kruger and Kearney, 2006) In addition, Table 3.4 illustrates the awareness scale that will be applied to state their awareness level. 26 Awareness Scale Descriptions 80%-100% Good - satisfactory 79%-60% Average – need to monitor <=59% Poor - unsatisfactory Table 3.4: Awareness Scale (Kruger and Kearney, 2006) 3.3.3 Design Design phase involves focusing on designing what modules are needed and how they are going to interact, interface design and data design. Based on input from analysis phase, there are five modules for this prototype which are: i) Admin Login - This is to authenticate the prototype administrator and gives access to restricted options. ii) Teacher Survey - In this module, user needs to fill in the demographic information and answer questions from five focus areas described previously. Identified questionnaire from analysis phase is used in this module. iii) Student Survey - Similar with Teacher Survey. However, the contents for this module is different in terms of questions and answer. 27 iv) Survey Result - Survey Result module represent survey result for an individual user after answer survey question and can be used to retrieve past result as well. v) Overall Result - Overall result display the overall result from all respondents. The value displayed is the average score from all respondent based on survey category. - Only administrator can access this module. The fundamentals of user interface design principles has taken into account while designing the prototype user interface. Scott, W.A. describes a collection of principles for improving the quality of your user interface design. These principles are: i) The structure principle - organize the user interface purposefully, in meaningful and useful ways based on clear, consistent models that are apparent and recognizable to users. ii) The simplicity principle - Common tasks simple to do, communicating clearly and simply in the user’s own language. iii) The visibility principle - Keep all needed options and materials for a given task visible without distracting the user with extraneous or redundant information. iv) The feedback principle - Keep users informed of actions or interpretations, changes of state or condition, and errors or exceptions v) The tolerance principle - Flexible and tolerant, reducing the cost of mistakes and misuse by allowing undoing and redoing. 28 vi) The reuse principle - Reuse internal and external components and behaviors, maintaining consistency with purpose. Entity relationship diagram, context diagram, data flow diagram and flowchart is used to design data and system architecture. The diagrams can be referred to Appendix E, F, G, and H respectively. 3.3.4 Implementation In this phase, the design is translated into code. The prototype would be developed as a windows application using Microsoft Visual Studio suite and Visual Basic.Net as its programming language. The database application would be built in SQL Server to store the data. 3.3.4.1 Hardware Requirement Below is the list of hardware requirement in order to develop the prototype: i) Laptop ii) Processor – Intel Core 2 Duo T5550 (1.83 GHz) iii) RAM – 1 MB DDR2 iv) Hard Disk – 160 GB 29 3.3.4.2 Software Requirement Below is the list of software requirement in developing phase: 3.3.5 i) Operating System – Windows XP/Vista ii) Programming application - Microsoft Visual Studio suite iii) Database - Microsoft SQL Server Testing The prototype is tested in this phase. There are three types of test involved which are unit testing, system testing and user testing. In unit testing, each unit or module of the prototype is tested individually to ensure it works properly and as intended. In system testing, the prototype is tested as whole. The separate prototype units are brought together and tested as whole to ensure all of its can work and interact. In addition, it is also important to ensure the prototype can interact with database, works on the intended platform, and produces intended output. For user testing, some teachers and students from Sekolah Menengah Kebangsaan Taman Tun Dr Ismail, Selangor (SMK TTDI) has been chosen to test the prototype. The testing is to examine user acceptance and to collect data as the findings for this study. 30 3.3.6 Maintenance The maintenance phase is the last phase of waterfall model and it is important to ensure the functionality of a system can keep continue. For this project, maintenance phase involves upgrade the units like adding new survey questions, maintain the database, improving its user interface and other user requirement once it delivered to the customer. 3.4 Summary The method described in this chapter is used in order to accomplish this study objective as stated in Chapter 1. Waterfall model is applied to ensure this study execute with smoothly and systematically. In addition, social cognitive theory is applied as the measurement model for information security awareness model. The awareness and weights scale are from previous similar study by Kruger and Kearney (2006). However, some modifications have been done to suit with secondary school environment. Chapter 4 describes the findings for this study. 31 CHAPTER 4 INFORMATION SECURITY AWARENESS FOR TEACHER AND STUDENT TOOL (ISATS) 4.1 Introduction The focus of this chapter is to discuss the result of the prototype findings in evaluating the information security awareness level among teacher and student at secondary school. As the main prototype purpose to evaluate the information security awareness level among teacher and student, it was being named ISATS – Information Security Awareness Level for Teacher and Student Tool. The test has carried out at SMKTTDI as described in Chapter 3, and has given a result as expected. The findings will be described according to existing ISATS modules. 32 4.2 Information Security Awareness For Teacher And Student Tool (ISATS) Specifically, there are five modules in this prototype as identified in Chapter 3 which are Admin Login, Teacher Category Survey, Student Category Survey, Survey Result and Overall Survey Result. 4.2.1 Admin Login Admin Login module is to authenticate the correct system administrator by authorized the username and password (Figure 4.1). The purpose of admin login is to monitor the prototype and only admin can access the overall survey result. Figure 4.1: Login Form After the correct login, automatically the Overall Result menu will appear (Figure 4.2). The different can be seeing when the Overall Result menu disappears if someone who are not administrator or end users using ISATS (Figure 4.3). 33 Figure 4.2: Admin Access Menu Figure 4.3: End User Access Menu 34 4.3.2 Teacher Category Survey Teacher Category Survey module is where the end user under teacher category answer survey questions (Figure 4.4). The input for this module is the user demographic information and answer for each question. Figure 4.4: Teacher Category Survey End user must completely answer all questions from the three dimensions named Knowledge, Behavior and Attitude in order to obtain reliable result. Then the user input will be passed to database after user press on Submit Survey button. The survey output will be displayed in Survey Result module. 4.3.3 Student Category Survey Basically, Student Category Survey (Figure 4.5) is similar with Teacher Category Survey in terms of its functionality, data input and connection with database. However, the questions for student are different with teacher based on their age and computer or Internet experience. 35 Figure 4.5: Student Category Survey 4.3.4 Survey Result The result of survey will automatically generate after end user press Submit Survey button at Survey module. The result is calculated based on weight and awareness scale. During the user testing, this module managed to work properly and generate the weights and awareness scale (Figure 4.6). Figure 4.6: Survey Result 36 The scale output can be viewed in bar chart, number and text form. It depicts user knowledge, behavior and attitude level. The total of those three components represents user information security awareness level. There is also an indicator of awareness level whether Satisfactory, Average or Unsatisfactory. Another output is user’s reference number which is unique and it can be used if user would like to retrieve their result in future (Figure 4.7 and Figure 4.8). In order to retrieve result, user must enter survey category whether Teacher or Student and their reference number as data input. Figure 4.7: Retrieve Survey Result (Student Example) 37 Figure 4.8: Retrieve Result (Teacher Category Example) 4.3.5 Overall Survey Result As stated in Section 4.2.1, only ISATS administrator can access this module. This module function is to generate the overall result for both categories. The average of each dimension and awareness level is calculated in order to obtain the output. There is no data input from user in this module except for it needs for user input to press each Generate Result button. The output is in bar chart, text and number form. 38 Figure 4.9: Overall Survey Result There are three sections in this module. First section is the overall teacher result that displays the output of knowledge, behavior and attitude average. The second section depicts the same output type but for student category. The third or last section display overall awareness level result for both teacher and student. Besides of viewing the average and overall level, this module also presents the comparisons between teacher and student awareness level. This module has worked properly during the user testing. From the collected data, it has generated the average awareness level for 15 teachers and students which are 93% and 67%. It shows that teacher got satisfactory awareness level and student got average awareness level (Figure 4.9). However, the result can be change if more data will be collected in future. 39 4.4 Summary There are five modules of ISATS and each module has its own function to evaluate information security awareness level. It shows that ISATS can be use in future as an automated tool to evaluate information security awareness level among teacher and student in secondary school. Discussion for this study will be discussed in the next chapter. 40 CHAPTER 5 DISCUSSION 5.1 Introduction The application of ABC model from social cognitive theory as the assessment model and using automated tool to generate the output is the base for this study. The development of ISATS and the user testing has shown positive result in this study. However, there are a lot of viewpoint that can be taken into consideration in order to produce better result. 5.2 Discussion of ISATS From the user testing, we can see that ISATS has worked as intended. The main points to test are its ability to process weights and awareness scale from user answers and produce the output as expected. It is important with the aim of achieving this study objective. With the generated survey result in Result Survey module, ISATS has achieved one of its objectives which is to identify the information security awareness level of secondary school teacher and student. ISATS also can analyze the survey result from overall survey input instead of individual survey result. 41 The application of ABC model as the base of awareness level assessment and AHP to calculate the weights and awareness scale has shown that the next objective which is to develop an appropriate model of information security awareness to secondary teacher and student has achieved as well. The positive feedback from users also gives optimistic view for this project. They have given full cooperation in order to carry out the user testing. Furthermore, ISATS has created new experience to most of the users. Feedbacks from users are like they were curious to know detail about information security awareness and eager to assess their information security awareness level. There are some information security terms that they never know before like “phishing”, social engineering and this has made them interested to know detail about it. Instead of manage to execute user testing and achieved this study aim, it also has supplied new information to the users. Besides of get their awareness level, they found new terms and knowledge as well. It gives the idea to expand the information security awareness information or knowledge at secondary school environment based on their positive feedback. Moreover, the users also give some useful opinions to enhance ISATS especially in terms of interface design. 5.3 Summary Discussion described in this chapter has proven that ISATS has achieved its objectives. Although there are a few flaws especially for user interface design, it can be enhanced in order to produce better result in future. Chapter 6 concludes all this study, and discusses project limitation as well as future work suggestion. 42 CHAPTER 6 CONCLUSION 6.1 Introduction This chapter concludes this study by discussing numerous limitations and the right dimension for ISATS in the future. Besides, this chapter also summarized the result of this study. 6.2 Limitations Limitations identified for this study, as listed below: i) The survey questions are limited, which is one question for each focus area for the three dimensions. ii) User interface is not properly design, due to time constraints and researcher focus more on theory part. 43 iii) Sample size for user testing is only 15 teachers and students. The number of sample size should increase for future work in order to achieve more accurate result. 6.3 Conclusion Remarks Information security awareness is not a new thing but the continuous study is needed to find improved and better way in order to create the awareness among society. As our society is comprises of different group of age, lifestyle, status, job and so on, the approach to create the awareness would be different as well. There are a lot of secondary source regarding information security awareness. In addition, there is study of information security awareness in school environment. It shows that information security professional had identified that school student and teacher as a group to convey the idea of awareness as well. ISATS development can aid as an automated tool to evaluate their awareness level. It can be use to indicate or compare the different before and after they know about information security. However, there are some improvements that can improve ISATS. 6.4 Future Work ISATS has a potential to be improved further and provides more functionality before it can be implemented in real world. Here are several examples of future work suggestions: 44 i) Create a question bank - The question can be randomly generated every time it displayed to user. It can reduce answer learning among the user. Besides, ISATS administrator can update the question bank with new questions. ii) Improve user interface design – Some multimedia elements can be integrated into ISATS especially for student category to add their excitement while answering survey questions. iii) ISATS can be developed or upgraded as a web-based application. It is easier mainly if more than one school is interested in using ISATS. The school only needs to create an account and the users can access it online. Therefore, the administrator does not have to install ISATS at each site (school) and it can save budget. iv) The focus area can be modified as well. This is due to the latest issue that we always encounter in computer and information security world. v) Provide dual-language (English and Malay language) so that user can choose as there is some students who are not really literate in English. It can affect their answer if they do not understand the questions need and as a result, the output is not reliable. Optimistically, ISATS can give contribution to information security awareness field and other recommendations are welcomed so that ISATS can be implemented successfully. 45 REFERENCES Albrechtsen, E. (2007). A qualitative study of users' view on information security. Computers & Security. 26 (4): 276-289. Bandura, A. (1989). Social Cognitive Theory. Retrieved on March 3, 2009 from: http://www.des.emory.edu/mfp/Bandura1989ACD.pdf Beranek, L. (2009). Information Systems Security Education for Future Teacher At Secondary And Primary Schools. Journal of Technology and Information Education. 1(2): 89-93. Center for Development of Advanced Computing. Handbook of Information Security Awareness for Teacher and Parents. Retrieved on March 4, 2009 from: http://infosecawareness.in/downloads/isa-for-teacher-and-parents Center for Education and Research in Information Security (CERIAS). Information Security Questionnaire: K12 Outreach. Retrieved on February 2, 2009 from: www.cerias.purdue.edu/education/k12/cerias_resources/files/questionnaire/infosec_ questionnaire.pdf Chai, S., et.al. (2006). Role of Perceived Importance of Information Security: An Exploratory Study of Middle School Children’s Information Security Behavior. Issues in Informing Science and Information Technology. 3: 127-135. Chen, C.C., Shaw, R.S., Yang, S.C. (2006). Mitigating Information Security Risks by Increasing User Security Awareness: A Case Study of an Information Security Awareness System. Information Technology Learning and Performance Journal. 24 (1). Dlamini, M.T., Eloff, J.H.P., Eloff, M.M. (2008). Information security: The moving target. Computers & Security. In Press. Corrected Proof.Available online 11 December 2008. 46 Drevin, L., Kruger, H.A., Steyn, T. (2007). Value-focused assessment of ICT security awareness in an academic environment. Computers and security. 26: 36-43. ISO27001. Code of practice for information security management. UK: British Standards Institute; 2005. Furnell, S.M., Bryant, P., Phippen, A.D. (2007). Assessing the security perceptions of personal Internet users. Computers & Security. 26 (5): 410 – 417. Furnell, S.M., Gennatou, M., Dowland, P.S. (2002). A prototype tool for information security awareness in training. Logistics Information Management. 15 (5 – 6): 352-357. Hentea, M. (2005). A perspective on achieving information security awareness. Issues in Informing Science & Information Technology. (2): 169-178. Katz, F.H. (2005). The Effect of a University Information Security Survey on Instruction Methods in Information Security. Information Security Curriculum Development (InfoSecCD) Conference '05.43 – 48. Krejcie, R. V., & Morgan, D. W. (1970). Determining sample size for research activities. Educational and Psychological Measurement. 30: 607-610. Kritzinger, E., Smith, E. (2008). Information security management: An information security retrieval and awareness model for industry. Computers & Security. 27:224231. Kruger, H.A., Kearney, W.D., (2006). A prototype for assessing information security awareness. Computers & Security. 25 (4): 289-296. Matthew, C., Sewry, D.A. (2004). South African IT industry professionals' ethical awareness: an exploratory study. ACM International Conference Proceeding Series. 75: 269-273 47 Martha, A., Iain, W., and Ngaire, D. (2006). Social Cognition: An Integrated Approach.2nd Edition.SAGE Publisher. London. Micki, K., Harold, F. T. (2007). Handbook of Information Security Management. CRC Press LLC. O’Regan, G. (2008). A Brief History of Computing. Publisher:Springer. Professional Information Security Association (PISA). (2003). Report of Information Security Survey on Education Sector. Retrieved on March 3, 2009 from: http://www.pisa.org.hk/projects/edsec2003/pressrel_eng.pdf Saaty, T.L. 1980. The analytic hierarchy process. McGraw-Hill. Schlienger, T. & Teufel, S. 2003. Information security culture – from analysis to change, South African Computer Journal. 31:46-52. Scheffler, F.L., Logan, J.P. (2000). Computer Technology in Schools: What Teachers Should Do and Be Able To Do. Journal of Research on Computing in Education. 31(3): 305-325. Scott, W.A. (n.d). User Interface Design, Tips, techniques and Principle. Retrieved July 11, 2009 from: http://www.ambysoft.com/essays/userInterfaceDesign.html Siponen, M.T. (2000). A conceptual foundation for organizational information security awareness. Information Management & Computer Security. 8 (1): 31-41. Siponen, M.T. (2001). Five Dimensions of Security Awareness. Computer and Society. Siponen, M.T., Kukkonen, H.O. (2007). A review of information security issues and respective research contributions. The DATA BASE for Advances in Information Systems. 38(1):60-80. 48 University of Florida’s IT Security Team. Awareness Questionnaire. Retrieved on February 2, 2009 from: http://www.questionpro.com/akira/TakeSurvey?id=567135 Yacine, R., Mark, A. (2008). Information security awareness term in higher education: An exploratory study. Computers & Security. 27 (7-8):241 – 253. Vargas, L.G. & Dougherty, J.J. (1982). The analytic hierarchy process and multicriterion decision making. American Journal of Mathematical and Management Sciences, 19(1):59-92. Wee, S.H. (1999).Internet Use Amongst Secondary School Students in Kuala Lumpur, Malaysia. Malaysian Journal of Library & Information Science. 4 (2). pp. 1-20. ISSN 1394-6234 Zahri Yunos and Sharifah Sajidah. (2005). Keeping Kids Safe Online. Retrieved on February 2, 2009 from: http://www.cybersecurity.org.my/data/content_files/13/61.pdf?.diff=1176416899 49 APPENDIX A – GANTT CHART 50 APPENDIX B – SURVEY QUESTIONS Teacher Category: Knowledge 51 Teacher Category: Behavior 52 Teacher Category: Attitude 53 Student Category: Knowledge 54 Student Category: Behavior 55 Student Category: Attitude 56 APPENDIX C – TOP INTERNET MAIN USE SURVEY QUESTIONS TEACHER CATEGORY INFORMATION SECURITY QUESTIONNAIRE Directions: Please answer the questions honestly and to the best of your I am conducting a survey to evaluate the level of information security awareness among teachers at secondary school. I would appreciate if you could spare 10 minutes to answer a few brief questions about information security. ability. All information is confidential. Part A: Background Information Age : _____ Gender: _________ School: _______________________________________________ 1. On average, how much time do you spend on the Internet per day? A. < 2 hours B. 2 – 4 hours C. 4 – 6 hours D. > 6 hours 2. What are your top three main uses for the Internet? □ Email □ Shopping □ Chatting □ Work □ Games □ Banking/Paying bills □ Social network sites (eg. MySpace, Friendster, etc.) □ Others (please specify) __________________________ 3. Please tick (l) security related terms that you understand. □ Virus □ Hacker □ Firewall □ Spyware □ Phishing □ Identity theft □ Worm □ Trojan horse 57 STUDENT CATEGORY SOAL SELIDIK KESEDARAN KESELAMATAN MAKLUMAT DI KALANGAN PELAJAR SEKOLAH MENENGAH ARAHAN: SILA JAWAB SOALAN DI BAWAH DENGAN JUJUR. SEGALA MAKLUMAT AKAN DIRAHSIAKAN. Bahagian A: Maklumat Latarbelakang Umur : _____ Jantina: _________ Tingkatan: __________ Sekolah: __________________ 1. Secara purata, berapa banyak masa yang anda habiskan untuk melayari Internet setiap hari? A. < 2 jam B. 2 – 4 jam C. 4 – 6 jam D. > 6 jam 2. Apakah tiga perkara utama yang anda lakukan sewaktu melayari Internet? (Tandakan 3 sahaja) □ Email □ Membeli belah □ Berbual (chatting) □ Kerja sekolah □ Permainan komputer □ Laman rangkaian sosial (cth. MySpace, Friendster, dll.) □ Lain-lain (sila nyatakan) __________________________ 3. Tandakan istilah mengenai keselamatan komputer yang anda fahami. □ Virus □ Hacker □ Firewall □ Spyware □ Phishing □ Pencuri Identiti / Identity theft □ Worm □ Trojan horse 58 APPENDIX D - ENTITY RELATIONSHIP DIAGRAM password username Admin TeachTotal TeachAttitud 1 1 StudTotal StudKnow monitor TeachRefNo M M Teacher TeachAge StudBehav TeachKnow StudRefNo Student M TeachBehav StudAttitude StudGender TeachGender StudAge accumulate result accumulate result TeachAver AllTeachKnow StudAverage 1 AllStudBehav AllTeachAttitude 1 AllStudent AllTeacher AllTeachBehav AllStudKnow AllStudAttitude 59 APPENDIX E- CONTEXT DIAGRAM Admin Username and password Authorized admin Answer survey Teacher Survey Result Reference No. Retrieved survey result Answer survey ISATS Survey Result Reference No. Retrieved survey result Student 60 APPENDIX F– DATA FLOW DIAGRAM U s e rn a m e a n d p a s s w o rd A d m in 1 .0 A d m in d a ta A u th e n tic a te D 1 A d m in A d m in in f o A u th o riz e d a d m in T e a c h e r re s u lt d a ta R e q u e s t o v e r a ll r e s u lt A llT e a c h e r D 1 2 .0 O v e r a ll r e s u lt s u m m a ry T e a c h e r o v e r a ll G e n e ra te o v e r a ll r e s u lt S tu d e n t r e s u lt d a ta D 2 in f o r m a t io n A llS tu d e n t S tu d e n t o v e r a ll in fo r m a tio n T e a ch e r S u rv e y a n s w e r S u rv e y a n s w e r 3 .0 C a lc u la t e w e ig h ta g e T e a c h e r w e ig h ta g e d a ta S tu d e n t w e ig h ta g e d a ta D 3 T e a ch e r D 4 S t u d e n t w e ig h ta g e in f o r m a t io n S tu d e n t T e a c h e r r e s u lt S tu d e n t r e s u lt 4 .0 G e n e ra te s u r v e y r e s u lt T e a c h e r w e ig h ta g e in fo r m a tio n S tu d e n t 61 APPENDIX G – FLOWCHART FLOWCHART – MAIN MENU Start 5 System Survey Result yes yes yes 1 2 3 62 FLOWCHART – SYSTEM 1 Admin login Admin logoff Username and password Logout exit No Verifying authentication Valid login Yes 5 Exit 4 63 FLOWCHART – SURVEY 2 Teacher Student Yes Yes No No No Key-in survey answer Key-in survey answer Submit survey Submit survey 3 4 5 64 FLOWCHART – RESULT 3 Survey result Overall result Yes Yes No IS awareness level Generate all survey result Retrieve result Yes No Display all survey result Select category Reference no 4 5 65 APPENDIX H – ISATS SOURCE CODE MAIN MENU MODULE Public Class frmMain1 Private Sub lblAdmin_MouseHover(ByVal sender As Object, ByVal e As System.EventArgs) Handles lblSystem.MouseHover Panel1.Visible = True End Sub Private Sub lblSurvey_MouseHover(ByVal sender As Object, ByVal e As System.EventArgs) Handles lblSurvey.MouseHover Panel2.Visible = True End Sub Private Sub lblReport_MouseHover(ByVal sender As Object, ByVal e As System.EventArgs) Handles lblReport.MouseHover Panel3.Visible = True End Sub Private Sub Panel1_MouseLeave(ByVal sender As Object, ByVal e As System.EventArgs) Handles Panel1.MouseLeave Panel1.Visible = False End Sub Private Sub Panel2_MouseLeave(ByVal sender As Object, ByVal e As System.EventArgs) Handles Panel2.MouseLeave Panel2.Visible = False End Sub Private Sub Panel3_MouseLeave(ByVal sender As Object, ByVal e As System.EventArgs) Handles Panel3.MouseLeave Panel3.Visible = False End Sub Private Sub lblStudent_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles lblStudent.Click 'show form frmStudent.Show() Me.Hide() End Sub Private Sub lblTeacher_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles lblTeacher.Click Me.Hide() frmTeacher.Show() End Sub Private Sub lblResult_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles lblResult.Click Me.Hide() 66 frmResult.Show() End Sub Private Sub lblOverall_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles lblOverall.Click Me.Hide() frmOverall.Show() End Sub Private Sub lblAdmin_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles lblAdmin.Click LoginForm1.Show() Me.Hide() End Sub Private Sub lblLogoff_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles lblLogoff.Click lblWelcome.Visible = False lblOverall.Visible = False MsgBox("You've been signed out from system") End Sub Private Sub Label2_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Label2.Click Me.Close() End Sub End Class 67 TEACHER CATEGORY SURVEY MODULE Public Class frmTeacher Dim TeachKnow As Integer = 0 Dim TeachBehav As Integer = 0 Dim TeachAtt As Integer = 0 Private Sub frmTeacher_Load(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles MyBase.Load 'fill data adapter SqlDataAdapter1.Fill(DsTeachInfo1) myTransfer.Fill(DsTransfer1) End Sub Private Sub rdbK1b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbK1b.CheckedChanged TeachKnow = TeachKnow + 6 End Sub Private Sub rdbKa2_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbKa2.CheckedChanged TeachKnow = TeachKnow + 6 End Sub Private Sub rdbK3a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbK3a.CheckedChanged TeachKnow = TeachKnow + 6 End Sub Private Sub rdbK4a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbK4a.CheckedChanged TeachKnow = TeachKnow + 6 End Sub Private Sub rdbK5c_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbK5c.CheckedChanged TeachKnow = TeachKnow + 6 End Sub Private Sub rdbB1d_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB1d.CheckedChanged TeachBehav = TeachBehav + 10 End Sub Private Sub rdbB1c_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB1c.CheckedChanged TeachBehav = TeachBehav + 5 End Sub Private Sub rdbB2a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB2a.CheckedChanged TeachBehav = TeachBehav + 10 End Sub 68 Private Sub rdbB3d_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB3d.CheckedChanged TeachBehav = TeachBehav + 10 End Sub Private Sub rdbB3c_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB3c.CheckedChanged TeachBehav = TeachBehav + 5 End Sub Private Sub rdbB4a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB4a.CheckedChanged TeachBehav = TeachBehav + 10 End Sub Private Sub rdbB5b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB5b.CheckedChanged TeachBehav = TeachBehav + 10 End Sub Private Sub rdbB5bc_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB5bc.CheckedChanged TeachBehav = TeachBehav + 10 End Sub Private Sub rdbA1a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbA1a.CheckedChanged TeachAtt = TeachAtt + 4 End Sub Private Sub rdbA2b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbA2b.CheckedChanged TeachAtt = TeachAtt + 4 End Sub Private Sub rdbA3a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbA3a.CheckedChanged TeachAtt = TeachAtt + 4 End Sub Private Sub rdbA3b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbA3b.CheckedChanged TeachAtt = TeachAtt + 2 End Sub Private Sub rdbA4a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbA4a.CheckedChanged TeachAtt = TeachAtt + 4 End Sub Private Sub rdbA4b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbA4b.CheckedChanged TeachAtt = TeachAtt + 2 End Sub 69 Private Sub rdbA5a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbA5a.CheckedChanged TeachAtt = TeachAtt + 4 End Sub Private Sub rdbA5b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbA5b.CheckedChanged TeachAtt = TeachAtt + 2 End Sub Private Sub btnSubmit_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnSubmit.Click 'insert(New row) Dim drNewRow As DataRow = DsTeachInfo1.Tables("Teacher").NewRow drNewRow("TeachKnow") = TeachKnow drNewRow("TeachAttitude") = TeachAtt drNewRow("TeachBehav") = TeachBehav drNewRow("TeachGender") = cboGenderT.Text drNewRow("TeachAge") = Val(txtAgeT.Text) DsTeachInfo1.Tables("Teacher").Rows.Add(drNewRow) SqlDataAdapter1.Update(DsTeachInfo1) drNewRow.AcceptChanges() 'update total value in AllTeacher table CalcTotal() calcTotalBehav() calcTotalAttit() 'display category on frmResult frmResult.lblCategory.Text = "Teacher" 'show form result Me.Close() frmResult.Show() End Sub Public Sub CalcTotal() 'update total value Dim strKnow As String strKnow = "UPDATE AllTeacher SET TotKnow =TotKnow + " & TeachKnow myTransfer.SelectCommand.CommandText = strKnow myTransfer.Update(DsTransfer1) myTransfer.Fill(DsTransfer1) End Sub Public Sub calcTotalBehav() Dim strBehav As String strBehav = "UPDATE AllTeacher SET TotBehav =TotBehav + " & TeachBehav 70 myTransfer.SelectCommand.CommandText = strBehav myTransfer.Update(DsTransfer1) myTransfer.Fill(DsTransfer1) End Sub Public Sub calcTotalAttit() Dim strAtt As String strAtt = "UPDATE AllTeacher SET TotAtt =TotAtt + " & TeachAtt myTransfer.SelectCommand.CommandText = strAtt myTransfer.Update(DsTransfer1) myTransfer.Fill(DsTransfer1) End Sub Private Sub btnHome_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnHome.Click Me.Close() frmMain1.Show() End Sub Private Sub btnExit_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnExit.Click End End Sub End Class 71 STUDENT CATEGORY SURVEY Public Class frmStudent Dim knowStudent As Integer = 0 Dim BehavStudent As Integer = 0 Dim AttStudent As Integer = 0 Private Sub frmStudent_Load(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles MyBase.Load 'fill data adapter SqlDataAdapter1.Update(DsStudent1) myStudent.Fill(DsMyStudent1) End Sub Private Sub rdbQK1c_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQK1c.CheckedChanged knowStudent = knowStudent + 6 End Sub Private Sub rdbQ2a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQ2a.CheckedChanged knowStudent = knowStudent + 6 End Sub Private Sub rdbQK3b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQK3b.CheckedChanged knowStudent = knowStudent + 6 End Sub Private Sub rdbQK4b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQK4b.CheckedChanged knowStudent = knowStudent + 6 End Sub Private Sub rdbQK5a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQK5a.CheckedChanged knowStudent = knowStudent + 6 End Sub Private Sub btnSubmit_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnSubmit.Click 'insert(New row) Dim drNewRow As DataRow = DsStudent1.Tables("Student").NewRow drNewRow("StudKnow") = knowStudent drNewRow("StudAttitude") = AttStudent drNewRow("StudBehav") = BehavStudent drNewRow("StudGender") = cboGender.Text 'drNewRow("SurveyDate") = lblTimer.Text drNewRow("StudAge") = Val(txtAge.Text) DsStudent1.Tables("Student").Rows.Add(drNewRow) SqlDataAdapter1.Update(DsStudent1) 72 drNewRow.AcceptChanges() 'update total awareness level CalcTotal() calcTotalBehav() calcTotalAtt() 'set category frmResult.lblCategory.Text = "Student" 'go to chart output Me.Close() frmResult.Show() End Sub Private Sub rdbB2_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbB2.CheckedChanged BehavStudent = BehavStudent + 10 End Sub Private Sub rdbQB2a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQB2a.CheckedChanged BehavStudent = BehavStudent + 10 End Sub Private Sub rdbQB2b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQB2b.CheckedChanged BehavStudent = BehavStudent + 5 End Sub Private Sub rdbQB2c_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQB2c.CheckedChanged BehavStudent = BehavStudent + 3 End Sub Private Sub rdbQB3b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQB3b.CheckedChanged BehavStudent = BehavStudent + 10 End Sub Private Sub rdbQB3c_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQB3c.CheckedChanged BehavStudent = BehavStudent + 10 End Sub Private Sub rdbQB4a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQB4a.CheckedChanged BehavStudent = BehavStudent + 10 End Sub Private Sub rdbQB5a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQB5a.CheckedChanged BehavStudent = BehavStudent + 10 End Sub 73 Private Sub rdbQA1b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQA1b.CheckedChanged AttStudent = AttStudent + 4 End Sub Private Sub rdbQA2b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQA2b.CheckedChanged AttStudent = AttStudent + 4 End Sub Private Sub rdbQA3b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQA3b.CheckedChanged AttStudent = AttStudent + 4 End Sub Private Sub rdbQA4b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQA4b.CheckedChanged AttStudent = AttStudent + 4 End Sub Private Sub rdbQA5a_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQA5a.CheckedChanged AttStudent = AttStudent + 4 End Sub Private Sub rdbQA5b_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQA5b.CheckedChanged AttStudent = AttStudent + 2 End Sub Private Sub rdbQA5c_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles rdbQA5c.CheckedChanged AttStudent = AttStudent + 1 End Sub Public Sub CalcTotal() 'update total value Dim strKnow As String strKnow = "UPDATE AllStudent SET TotKnowStud =TotKnowStud + " & knowStudent myStudent.SelectCommand.CommandText = strknow myStudent.Update(DsMyStudent1) myStudent.Fill(DsMyStudent1) End Sub Public Sub calcTotalBehav() Dim strBehav As String strBehav = "UPDATE AllStudent SET TotBehavStud =TotBehavStud + " & BehavStudent myStudent.SelectCommand.CommandText = strBehav 74 myStudent.Update(DsMyStudent1) myStudent.Fill(DsMyStudent1) End Sub Public Sub calcTotalAtt() Dim strAtt As String strAtt = "UPDATE AllStudent SET TotAttitStud =TotAttitStud + " & AttStudent myStudent.SelectCommand.CommandText = strAtt myStudent.Update(DsMyStudent1) myStudent.Fill(DsMyStudent1) End Sub Private Sub btnHome_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnHome.Click Me.Close() frmMain1.Show() End Sub Private Sub btnExit_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnExit.Click End End Sub End Class 75 SURVEY RESULT MODULE Public Class frmResult Public Sub createChart() Dim I As Integer = 3 'First Step AxMSChart1.RowCount = 1 'Specify count of rows to be 5 AxMSChart1.ColumnCount = 3 'Specify count of graphs to be 2 If lblCategory.Text = "Student" Then 'the loop For I = 1 To AxMSChart1.RowCount 'Here it is dynamically and will work in all cases of values for AxMSChart1.Row 'Set that we want to edit the row "I" AxMSChart1.Row = I 'Setting it's label to I AxMSChart1.RowLabel = I 'Editing the first graph AxMSChart1.Column = 1 'Set that I want to edit the second graph AxMSChart1.Data = txtKnowledge.Text 'Editing the second Graph AxMSChart1.Column = 2 'Set that I want to edit the second graph AxMSChart1.Data = txtBehavior.Text 'editing the third Graph AxMSChart1.Column = 3 'Set that I want to edit the second graph AxMSChart1.Data = txtAttitude.Text Next ElseIf lblCategory.Text = "Teacher" Then For I = 1 To AxMSChart1.RowCount 'Here it is dynamically and will work in all cases of values for AxMSChart1.Row 'Set that we want to edit the row "I" AxMSChart1.Row = I 'Setting it's label to I AxMSChart1.RowLabel = I 'Editing the first graph AxMSChart1.Column = 1 'Set that I want to edit the second graph AxMSChart1.Data = txtKnowT.Text 'Editing the second Graph AxMSChart1.Column = 2 'Set that I want to edit the second graph 76 AxMSChart1.Data = txtBehavT.Text 'editing the third Graph AxMSChart1.Column = 3 'Set that I want to edit the second graph AxMSChart1.Data = txtAttiT.Text Next End If End Sub Private Sub frmResult_Load(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles MyBase.Load Dim strLast As String DsChart1.Clear() DsChartT1.Clear() If (lblCategory.Text) = "Student" Then 'visible group box GroupBox1.Visible = True 'load database strLast = "SELECT StudRefNo,StudKnow,StudAttitude,StudBehav FROM Student WHERE StudRefNo = (SELECT MAX(StudRefNo)FROM Student)" myData.SelectCommand.CommandText = strLast myData.Fill(DsChart1) TotalStudent() ElseIf (lblCategory.Text) = "Teacher" Then GroupBox4.Visible = True strLast = "SELECT TeachRefNo,TeachKnow,TeachAttitude,TeachBehav FROM Teacher WHERE TeachRefNo = (SELECT MAX(TeachRefNo)FROM Teacher)" myTeachData.SelectCommand.CommandText = strLast myTeachData.Fill(DsChartT1) TotalTeacher() End If createChart() End Sub Private Sub btnHome_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnHome.Click Me.Close() frmMain1.Show() End Sub Public Sub FindTeacher() Dim strSelectString As String DsChartT1.Clear() strSelectString = "SELECT * FROM Teacher WHERE TeachRefNo =" & txtRef.Text 77 myTeachData.SelectCommand.CommandText = strSelectString myTeachData.Fill(DsChartT1) lblCategory.Text = "Teacher" End Sub Public Sub FindStudent() Dim strSelectString As String DsChart1.Clear() strSelectString = "SELECT * FROM Student WHERE StudRefNo =" & txtRef.Text myData.SelectCommand.CommandText = strSelectString myData.Fill(DsChart1) lblCategory.Text = "Student" End Sub Public Sub TotalStudent() Dim StdTotal As Integer StdTotal = Val(txtKnowledge.Text) + Val(txtBehavior.Text) + Val(txtAttitude.Text) txtTotal.Text = StdTotal & "%" If StdTotal >= 80 Then lblIndStud.Text = "Satisfactory" ElseIf StdTotal >= 60 And StdTotal <= 79 Then lblIndStud.Text = "Average" Else lblIndStud.Text = "Unsatisfactory!!" lblIndStud.ForeColor = Color.Red End If lblRef.Visible = True End Sub Public Sub TotalTeacher() Dim TeachTotal As Integer TeachTotal = Val(txtKnowT.Text) + Val(txtBehavT.Text) + Val(txtAttiT.Text) txtTotalT.Text = TeachTotal & "%" If TeachTotal >= 80 Then lblIndTeach.Text = "Satisfactory" ElseIf TeachTotal >= 60 And TeachTotal <= 79 Then lblIndTeach.Text = "Average" Else lblIndTeach.Text = "Unsatisfactory!!" lblIndTeach.ForeColor = Color.Red End If lblRefT.Visible = True End Sub Private Sub btnResult_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnResult.Click Dim intnumrows As Integer If cboCategory.Text = "Teacher" Then FindTeacher() intNumRows = DsChartT1.Tables("Teacher").Rows.Count 78 If intNumRows = 0 Then MsgBox("Nobody with that reference number") txtRef.Text = "" Exit Sub End If GroupBox4.Visible = True GroupBox1.Visible = False lblRef.Visible = False TotalTeacher() createChart() ElseIf cboCategory.Text = "Student" Then FindStudent() intnumrows = DsChart1.Tables("Student").Rows.Count If intnumrows = 0 Then MsgBox("Nobody with that reference number") txtRef.Text = "" Exit Sub End If GroupBox1.Visible = True GroupBox4.Visible = False lblRefT.Visible = False TotalStudent() createChart() End If End Sub Private Sub cboCategory_SelectedIndexChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles cboCategory.SelectedIndexChanged GroupBox1.Visible = False GroupBox4.Visible = False txtRef.Text = "" End Sub Private Sub btnExit_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnExit.Click End End Sub End Class 79 OVERALL RESULT MODULE Public Class frmOverall Dim kT, bT, aT, kS, bS, atS As Double Dim totStud, totTeach As Integer Private Sub frmOverall_Load(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles MyBase.Load 'clear data adapter DsConnTeacher1.Clear() DsConnStudent1.Clear() End Sub Public Sub countTeacher() Dim strCount As String 'DsConnTeacher1.Clear() strCount = "update AllTeacher set TotTeach=(SELECT COUNT (TeachRefNo) FROM Teacher) " connTeacher.SelectCommand.CommandText = strCount connTeacher.Update(DsConnTeacher1) connTeacher.Fill(DsConnTeacher1) kT = (lblKT.Text) / (lblTotTeach.Text) bT = (lblBT.Text) / (lblTotTeach.Text) aT = Val(lblAT.Text)/ Val(lblTotTeach.Text) End Sub Public Sub countStudent() Dim strCount As String 'DsConnStudent1.Clear() strCount = "update AllStudent set TotStudent=(SELECT COUNT (StudRefNo) FROM Student) " connStudent.SelectCommand.CommandText = strCount connStudent.Update(DsConnStudent1) connStudent.Fill(DsConnStudent1) kS = (lblKS.Text) / (lblTotStud.Text) bS = (lblBS.Text) / (lblTotStud.Text) atS = Val(lblAS.Text)/ Val(lblTotStud.Text) End Sub Public Sub AveKnowT() Dim strKnow As String strKnow = "UPDATE AllTeacher SET AveKnow =" & kT connTeacher.SelectCommand.CommandText = strKnow 80 connTeacher.Update(DsConnTeacher1) connTeacher.Fill(DsConnTeacher1) End Sub Public Sub aveBehavT() Dim strBehav As String strBehav = "UPDATE AllTeacher SET AveBehav =" & bT connTeacher.SelectCommand.CommandText = strBehav connTeacher.Update(DsConnTeacher1) connTeacher.Fill(DsConnTeacher1) End Sub Public Sub aveAttiT() Dim strAtt As String strAtt = "UPDATE AllTeacher SET AveAtt =" & aT connTeacher.SelectCommand.CommandText = strAtt connTeacher.Update(DsConnTeacher1) connTeacher.Fill(DsConnTeacher1) End Sub Public Sub knowS() Dim strKnow As String strKnow = "UPDATE AllStudent SET AveKnowStud =" & kS connStudent.SelectCommand.CommandText = strKnow connStudent.Update(DsConnStudent1) connStudent.Fill(DsConnStudent1) End Sub Public Sub BehavS() Dim strBehav As String strBehav = "UPDATE AllStudent SET AveBehavStud =" & bS connStudent.SelectCommand.CommandText = strBehav connStudent.Update(DsConnStudent1) connStudent.Fill(DsConnStudent1) End Sub 81 Public Sub AttS() Dim strAtt As String strAtt = "UPDATE AllStudent SET AveAttitStud =" & atS connStudent.SelectCommand.CommandText = strAtt connStudent.Update(DsConnStudent1) connStudent.Fill(DsConnStudent1) End Sub Public Sub createChart() Dim I As Integer = 3 'First Step AxMSChart1.RowCount = 1 'Specify count of AxMSChart1.ColumnCount = 3 'Specify count AxMSChart2.RowCount = 1 'Specify count of AxMSChart2.ColumnCount = 3 'Specify count rows to be 5 of graphs to be 2 rows to be 5 of graphs to be 2 'the loop For I = 1 To AxMSChart1.RowCount 'Here it is dynamically and will work in all cases of values for AxMSChart1.Row 'Set that we want to edit the row "I" AxMSChart1.Row = I AxMSChart2.Row = I 'Setting it's label to I AxMSChart1.RowLabel = I AxMSChart1.RowLabel = I 'Editing the first graph AxMSChart1.Column = 1 'Set that I want to edit the second graph AxMSChart1.Data = txtAverKnowS.Text AxMSChart2.Column = 1 'Set that I want to edit the second graph AxMSChart2.Data = txtAveKnowT.Text 'Editing the second Graph AxMSChart1.Column = 2 'Set that I want to edit the second graph AxMSChart1.Data = txtAveBehavS.Text AxMSChart2.Column = 2 'Set that I want to edit the second graph AxMSChart2.Data = txtAveBehavT.Text 'editing the third Graph AxMSChart1.Column = 3 'Set that I want to edit the second graph AxMSChart1.Data = txtAverAttiS.Text AxMSChart2.Column = 3 'Set that I want to edit the second graph AxMSChart2.Data = txtAverAttiT.Text Next End Sub 82 Private Sub btnHome_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnHome.Click frmMain1.Show() Me.Close() End Sub Private Sub btnTeacher_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnTeacher.Click Dim mangkuk As String DsConnStudent1.Clear() mangkuk = "SELECT * FROM AllTeacher" connTeacher.SelectCommand.CommandText = mangkuk connTeacher.Fill(DsConnTeacher1) 'count average countTeacher() 'update average value AveKnowT() aveBehavT() aveAttiT() 'display value txtAveKnowT.Text = Int(kT) txtAveBehavT.Text = Int(bT) txtAverAttiT.Text = Int(aT) 'generate chart createChart() End Sub Private Sub btnStudent_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnStudent.Click Dim mangkuk As String DsConnStudent1.Clear() mangkuk = "SELECT * FROM AllStudent" connStudent.SelectCommand.CommandText = mangkuk connStudent.Fill(DsConnStudent1) 'count average countStudent() 'update average value knowS() BehavS() AttS() 'display value 83 txtAverKnowS.Text = Int(kS) txtAveBehavS.Text = Int(bS) txtAverAttiS.Text = Int(atS) 'generate chart createChart() End Sub Public Sub TotAverTeacher() Dim totTeach As Integer totTeach = Int(kT + aT + bT) txtTeachT.Text = totTeach If totTeach >= 80 Then lblIndTeach.Text = "Satisfactory" ElseIf totTeach >= 60 And totTeach <= 79 Then lblIndTeach.Text = "Average" Else lblIndTeach.Text = "Unsatisfactory!!" lblIndTeach.ForeColor = Color.Red End If End Sub Public Sub TotAverStudent() totStud = (kS + atS + bS) txtStudentS.Text = Int(totStud) If totStud >= 80 Then lblIndS.Text = "Satisfactory" ElseIf totStud >= 60 And totStud <= 79 Then lblIndS.Text = "Average" Else lblIndS.Text = "Unsatisfactory!!" lblIndS.ForeColor = Color.Red End If End Sub Public Sub createPieChart() Dim I As Integer = 3 'First Step AxMSChart3.RowCount = 1 'Specify count of rows to be 1 AxMSChart3.ColumnCount = 2 'Specify count of graphs to be 3 'the loop For I = 1 To AxMSChart3.RowCount 'Here it is dynamically and will work in all cases of values for AxMSChart1.Row 'Set that we want to edit the row "I" AxMSChart3.Row = I 84 'Setting it's label to I AxMSChart3.RowLabel = I 'Editing the first graph AxMSChart3.Column = 1 'Set that I want to edit the second graph AxMSChart3.Data = txtTeachT.Text 'Editing the second Graph AxMSChart3.Column = 2 'Set that I want to edit the second graph AxMSChart3.Data = totStud Next End Sub Private Sub btnOverall_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnOverall.Click TotAverStudent() TotAverTeacher() createPieChart() AxMSChart3.Visible = True gbxPie.Visible = True End Sub Private Sub btnExit_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles btnExit.Click End End Sub End Class