Fighting Fraud and Validating Control Under Sarbanes -
advertisement

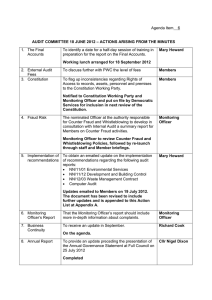
Slide 1 Fighting Fraud and Validating Control Under Sarbanes-Oxley Using Audit Software General Audit Management Conference 3/24/04 Presented by: Richard B. Lanza, CPA, CFE PMP www.richlanza.com Slide 2 Agenda A complete list of fraud computer reports to attack every occupational fraud identified to date An understanding of how software can improve each step in the audit process New usage of audit software to help comply with Sarbanes-Oxley and current auditing standards Free tools to help “jump start” the use of audit software in their departments Slide 3 Who am I? Richard B. Lanza, CPA, PMP Have saved millions of dollars for clients/organizations using CAATS Wrote the first book on how to practically apply a data extraction/analysis software….and three more Recently awarded the Outstanding Achievement in Commerce award by the Association of Certified Fraud Examiners Developed the first community focused around audit software Currently works as an Internal Audit manager for a Fortune 200 retailer, establishing continuous monitoring systems Slide 4 Fraud and the CAAT Auditor Slide 5 Slide 6 Benefits of Reducing Fraud Save 2% to 3% of revenues normally lost to fraud Enhance market value Reduce federal penalties Reduce audit fees Prevent civil lawsuits Recover more of the loss Maintain a positive brand image Slide 7 Proactively Detecting Fraud Document Purpose The purpose of this document is to assist auditors, fraud examiners, and management in implementing data analysis routines for improved fraud prevention and detection. To that end, the document provides: – General guidance in the implementation of audit software. – A comprehensive checklist of data analysis reports that are associated with each occupational fraud category per the Association of Certified Fraud Examiner’s classification system. – A report description and data file(s) needed to effectuate each identified report. Slide 8 Need for the Document The need for this document arises from the fact that there are many publications that discuss auditing for fraud using a computer but there was no comprehensive resource for the types of audit reports that needed to be run for each individual fraud type ….until now. It is hoped that through the dissemination of this new information that more consideration and analysis will be done using audit software to prevent and proactively detect organizational fraud. Slide 9 Fraud Categories Aligned to Reports Conflicts of Interest Bribery / Illegal Gratuities / Extortion Fictitious Revenues / Timing Differences Understated Liabilities and Expenses Overstated Assets/Valuation Improper Disclosures Non-Financial Fraudulent Statements Cash Larceny Skimming Inventory Misuse / Larceny Billing Schemes Payroll Schemes Expenses Reimbursement Schemes Check Tampering Register Disbursements Slide 10 Types of Analyticals Trend Analysis Stratifications/Agings Regression Benford’s Law Slide 11 Benefits of Analytical Tools To assist the auditor in planning the nature, timing, and extent of audit procedures To reduce risk in testing account balances To provide overall reasonableness at the end of the audit To assist in proposing financial statement adjustments based on analytical calculations To help direct auditors attention to the existence of management fraud. For example, the Association of Certified Fraud Examiners listed the use of analytical procedures as one of four means towards a proactive fraud policy. To identify areas of focus that are not on the income statement or balance sheet as analytical procedures help auditors look beyond what is being currently reported to what they expect to be reported based on business and industry trends. To help an auditor better understand the relationships existing within the financial information of the business entity. Slide 12 The “in” Analytical tools provide “shockers” to clients leading to the question, “How did you find that?” Audit Intelligence provides a “wow” factor of graphs and OLAP tools Departments using these tools are placed above the rest for their techsaviness Slide 13 Continuous Digital Analysis is the Answer Quarterly law 0.3500 0.3000 0.2500 4th 0.2000 3rd 2nd 0.1500 1st 0.1000 0.0500 Digits 95 90 85 80 75 70 65 60 55 50 45 40 35 30 25 20 15 0.0000 10 Frequency Benford Slide 14 Fraud Views Comprehensive tool based on over 30 references Provides only those indicators you need to assess the given fraud in question Instant views and Excel matrix for guidance…just tick off which ones apply Slide 15 Available Fraud Views Overstated Revenue – – – Fictitious Revenues Timing Differences One Time Gains Understated Revenue – Timing Differences Overstated Assets – Improper Costing – Improper Valuation Understated Assets – Improper Costing – Improper Valuation Understated Liabilities/Expenses – Unrecognized and Timing – Improper Estimations Overstated Liabilities/Expenses – Cookie Jar Reserves – Write Offs Slide 16 Audit Intelligence – Balance Sheet Slide 17 Audit Intelligence – Trend Slide 18 Identify trends when none exist If VENDOR is 012737 Then AP_AMOUNT is -107,155.74 ... 614.68 (average = -190.09 ) Rule's probability: 0.999 The rule exists in 9560 records. Significance Level: Error probability is almost 0 Deviations (records' serial numbers): 21524, 21777, 22119, 22411, 22703, 30110, 30166, 30182, 30184, 30186, 30227, 30109 Slide 19 Control Environment Surveys Slide 20 Improving the Audit Process Slide 21 Group Exercise Why will I (and why will I not) use audit software? Slide 22 Why I Won’t Do This….. Every audit I do is different so why build software when I need to frequently change it? Getting data takes time I might actually find something wrong My ERP system does this already Management doesn’t want me to do such services….management should manage themselves Slide 23 What’s In It For Me? ….Why Do This For Me? Learn a “not-so-new” skill Learn about technology Have more free time to focus on understanding the business Have more free time Slide 24 Statement On Auditing Standards #80 & #94 “It may be difficult or impossible for the auditor to access certain information for inspection, inquiry, or confirmation without using information technology. Slide 25 What’s In It For Me? ….Why Do This For The Company? Maintain Sarbanes-Oxley compliance Reduce fraud Build automated intelligence Quick ROI (112% per recent CDC study) Increase efficiency/quality Slide 26 End-Goal of Business Intelligence Software The optimal BI solution is deployed across the entire enterprise, equipping hundreds or thousands of employees with analytic information. From line managers to the executive suite it gets widely deployed and used. Users can access real-time data,manipulate it,drill down to find root causes,analyze trends,and provide a check and balance. Workers at every level get the information they need to make the right decisions,at the right time,resulting in a more effective,responsive,and profitable company. (Informatica) Slide 27 A Strong Information & Communication Channel (COSO) Obtaining external and internal information, and providing management with necessary reports on the entity’s performance relative to established objectives Providing information to the right people in sufficient detail and on time to enable them to carry out their responsibilities efficiently and effectively Development or revision of information systems based on a strategic plan Management’s support for the development of necessary information systems Slide 28 What’s the Difference? NOTHING! Slide 29 The Audit Software Process Slide 30 The Audit Process Without Audit Software “Working around the system” Planning - Questionnaires, some analyticals, and review prior year workpapers Internal Control - Complete process memo, select samples and vouch to support Substantive Procedures – Scan reports, select manual samples, complete manual recalculations, vouch to support, perform physical inspection, inquire and observe with the client Slide 31 The Audit Process With Audit Software “Working through the system” Planning - Stratifications, stronger analyticals, and exception reporting on key indicators (using 100% of the data) Internal Control - Verify data and applications, identify “dirty” data, select samples, review exception reports on controls Substantive Procedures – Research exception reports, perform minimal sampling and use the 12 tools of audit software Slide 32 Continuously Monitor/ Build Automated Intelligence Select top exception reports Identify key analyticals Build automated routines to execute on a timed schedule Iterate the reports based on findings over time Slide 33 Prototype and Bridge Data Provided by MIS on Server Data Analyzed in an Ad-Hoc Fashion by ACL and Reports Reviewed Selected Reports Are Developed Using An ACL Batch and Reported in Access/Excel Slide 34 How Is Rich Doing It? ACL, Access, and Excel are used as ad-hoc reporting tools ACL is used for batch applications Access and Excel are used for end user report delivery and querying Using the best tools for their requisite strengths Slide 35 Automated Routines Slide 36 Considering Production-Grade System Reports Full-service toolset (i.e., Cognos) implemented by MIS Real-time updates Centralized data mart for past versions Professional-grade data import tools Automatic notification (Email, Pager) Personalized Web dashboard Audit trails of all processing/reviews Unified security Slide 37 Comply With SarbOx Slide 38 SarbOx Key Requirements For Audit Software Section 302 - CEO and CFO certifications of quarterly and annual reports Section 409 - Disclose to public on a "rapid and current basis" material changes to financial condition or results of operations. Section 404 - Requiring annual assessments of the effectiveness of internal controls over financial reporting, including an attestation from an external auditor. Slide 39 Documentation Tools Documents risks, controls, issues, processes, assertions, accounts, test plans, and test results Allows for easy collection of self assessment results Provides a model of control Presents reports to all levels of the organization IIA research study/article expected early next year Slide 40 How Are You Tracking ROI? What? – Hard Benefits – Intangible Benefits – Lessons Learned How? – Finger In The Air – Informal Status – Database – Proactive Survey Slide 41 While You May Have a Project Plan….. What is your critical path? / How are you speeding the plan? How are you managing the scope? What are your estimates based on? What are your key dependencies? Slide 42 Earned Value Quantifies the “gut feel” Single control system providing consistent, reliable, and timely data to management at all levels Integrates technical scope of work with time commitments and authorize resources Over 700 DOD contracts have applied the technique and have demonstrated a pattern of predictable project performance used to predict the future Slide 43 Changes in Testing Controls CFOs to dig much deeper into how their companies control their financial reporting, and how they disclose material changes in their operations. For COSO ERM, they will need to improve their event identification procedures. Documentation will identify holes for validation testing Time will need to be afforded to dig deeper….more reports to review = more work This is a continual process….it’s not over on 12/31/2004 Slide 44 The Birth Of The Bionic Auditor Slide 45 How Do We Define Bionics? Having anatomical structures or physiological processes that are replaced or enhanced by electronic or mechanical components. Î Having extraordinary strength, powers, or capabilities; superhuman. Slide 46 Bionic Auditors Are Born! Slide 47 Examples of Automated Risk Management Savings Dell – New monitor sent with $100 adjustment automatically posted Î Cemex – Ready-mix load about to expire is auctioned to the highest bidder in the immediate area Î To be named – Unmitigated risk identified through control self assessment – Calculation of current impact assessed – Appropriate parties using a skills database are identified – Calendar system finds next available time for meeting to discuss Slide 48 Why Automate Risk Management? Manage Risk Better Allows analysis that goes beyond our brains Integrates risk data from various sources Frees up time for higher-end thinking Focuses efforts on the most fruitful opportunities React Quicker Automates your rote tasks Keeps tabs on thousands of risks, and only alerts you of key issues Maintains information in one central locale for easy retreival Slide 49 Diagram Slide 50 A Few Random Quotes Î “In 25 years, you’ll probably be able to get the sum total of all human knowledge on a personal device.” - Greg Blonder, VC [was Chief Technical Adviser for Corporate Strategy @ AT&T] Î “A bureaucrat is an expensive microchip.” Dan Sullivan, consultant and executive coach Slide 51 We Can Rebuild Him….. All of this technology exists today It is easier than ever to loosely couple the modular components with software going to more object orientated programming, .Net, etc.. To be effective, we need to think of all aspects of the risk management deployment design….not just one or two pieces. Slide 52 But Won’t The Computer Replace Me? Î It will replace rote functions Î It will free us up to do more value-added tasks We can become architects of risk management software solutions Slide 53 Not Bad To Be The Architect If it works for Bill, it works for me……