Document 14645784
advertisement

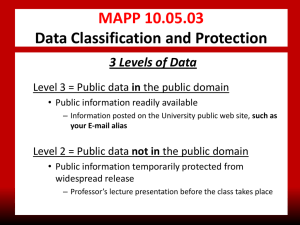
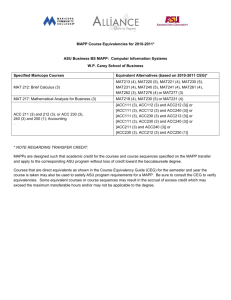
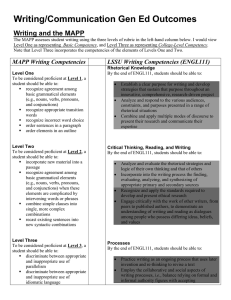
MISSION To serve UH colleges and administrative departments by: Delivering reliable and secure technology services Aligning with and serving our campus customers Supporting state-of-the-art student, financial, human resources (PeopleSoft) and other information systems By the numbers FY 2012 300,211 Email aliases 298,803,298 Email incoming messages processed 3,940,125 Finance transactions 86,451 CougarNet accounts 559,221,786 UH web site page views 232,960 IT Support Center service requests 229,852 Seats in Blackboard courses 4,589 Blackboard training courses 2,100 Data backup (in Terabytes) 1,541 Miles of network fiber 53,744 Active data ports 1,644 Wireless access points CIO Enterprise Systems Information Technology Security High Performance Computing Technology Services & Support Key IT Compliance Requirements Gramm-Leach-Bliley Act (GLBA) Requirement of institutions engaged in financial transactions to protect the security & confidentiality of customers’ nonpublic personal information Family Educational Rights & Privacy Act (FERPA) Protects the privacy of student education records Health Insurance Portability & Accountability Act (HIPAA) Health information privacy & security standards DMCA – Digital Millennium Copyright Act Protects against infringement of copyrights Payment Card Industry (PCI) Data Security Standard Credit card company’s information security standard for the protection of cardholders’ data required of all merchants and entities accepting credit cards or processing credit card transactions Texas Administrative Code 202 Title 1, Part 10, Chapter 202, Sub Chapter C - Security Standards for Institutions of Higher Education Section 202.70 Security Standards Policy Section 202.71 Mgmt & Staff Responsibilities Section 202.72 Managing Security Risks Section 202.73 Managing Physical Security Section 202.74 Business Continuity Planning Section 202.75 Info Resources Security Safeguards Section 202.76 Security Incidents Section 202.77 User Security Practices Section 202.78 Removal of Data from Data Processing Equipment UH Policies UHS Policies (SAMs): http://www.uh.edu/sam UH Policies (MAPPs) : http://www.uh.edu/mapp People Process PEOPLE Awareness Students, Faculty & Staff Technology TECHNOLOGY PROCESSES Finding our own weaknesses first Establishing cooperative business practices with UHS business owners * Web application * Campaign: Identifying phishing emails * Technology Partners Program vulnerability scanning * Identity Finder – locate, remove and * PCI compliance efforts * FTC red flag rule implementation * Data security protect sensitive framework – data copiers , shredding UH Division Technology Social Work CLASS NSM Pharmacy Law Center Hotel and Rest Mgt Honors College Engineering Education Business Architecture TECHNOLOGY PARTNERS PROGRAM University Information Technology (UIT) Network Infrastructure Data Center Enterprise Application IT Security Instructional Technology Support Centers Telephony MAPP 10.03.06 College/Division Responsibilities for Information Technology Resources College/Divisions required to appoint 3 roles: Information Resource Manager (C/D- IRM) Technology Manager (C/D-TM) Information Security Officer (C/D-ISO) College/Divisions must review their procedures annually and update them as appropriate MAPP 10.03.06 cont. IT to provide consultative, best practice services including: Facilitate university-wide coordination & planning Training to college/division based technical support staff Technical guidelines & reference materials Coordination of meetings of the C/D-IRMs, C/D-TMs, C/D- ISOs and relevant SMEs TECHNOLOGY PARTNERS PROGRAM Deliver innovation and support in the use of IT resources together with college/division identified roles: Strategy Operations Security • Information Resource Manager (IRM) • Technology Manager (TM) • Information Security Officer (ISO) MAPP 10.03.06 COLLEGE / DIVISION TECHNOLOGY REVIEWS PURPOSE: Iterative Review Framework Assessment of immediate critical needs 1. DELIVERABLE: Initial Review Action plan and resolution of critical needs 2. Comprehensive Review 3. PURPOSE: Comprehensive technology assessment DELIVERABLE: Comprehensive action plan and execution of recommendations Sustainability Review PURPOSE: Operationalize technology reviews through the University Technology Partners Program DELIVERABLE: Operational technical review plan