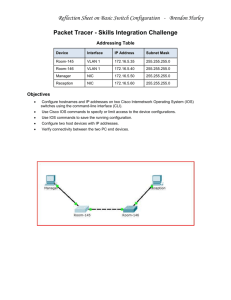
Cisco Secure Data Center for Enterprise Implementation Guide
advertisement

Cisco Secure Data Center for Enterprise Single Site Clustering with Cisco TrustSec Technology Implementation Guide Last Updated: March 19, 2014 About the Authors About the Authors Tom Hogue, Security Solutions Manager, Security Business Group, Cisco Tom is the Data Center Security Solutions Manager at Cisco with over 30 years in developing integrated solutions with Cisco and previous roles in the industry. Tom led the development of the industry leading data center solutions such as the FlexPods, Vblocks, and Secure Multi-tenancy. Tom Hogue Bart McGlothin, Security Systems Architect, Security Business Group, Cisco Bart is a Security Solutions Architect at Cisco with over 16 years of solutions experience. Bart leads Cisco's involvement with the National Retail Federation's Association for Retail Technology Standards Committee (ARTS) as a member of the ARTS board and Executive Committee. Prior to Cisco, Bart worked as the Network Architect at Safeway, Inc. Bart McGlothin Matt Kaneko, Security Systems Architect, Security Business Group, Cisco Matt Kaneko is the solution technical lead for Secure Data Center Solution team. In this role, Matt and his team work closely with product marketing teams of various business group along with customer’s feedback to create solution architecture. Prior to this role, Matt has worked as a Technical Marketing Manager for various Cisco Security Product lines which includes Cisco ASA Next Generation Firewall, Cisco Intrusion Protection System, Cisco AnyConnect and associated Management products line. Matt Kaneko 2 CONTENTS Introduction 4 Goal of this Document 4 Intended Audience 5 Validated Components 5 Solution Component Implementation 6 Cisco ASA Firewall Clustering 7 IPS Protection 15 Cisco TrustSec 17 Validation Testing 25 Summary of Tests Performed 25 Summary of Results 27 Conclusion 28 Appendix A—References 29 Appendix B—Device Configurations 30 ASA Cluster Configurations 30 Nexus 7000 Configuration 44 Nexus 1Kv 55 Appendix C—About the Cisco Validated Design Program 67 Cisco Secure Data Center for Enterprise 3 Introduction Introduction Goal of this Document The Single Site Clustering with Cisco TrustSec Technology Solution provides guidance for enterprises that are challenged with the exponential growth of data center resources and associated security policy complexity. Enterprises that want to protect against advanced data security threats can deploy a comprehensive set of security capabilities to address these needs, as shown in Figure 1. Using Cisco’s next-generation firewalls operating as a cluster with IPS and TrustSec, the goals of increased security capacity and simplicity can be jointly achieved. Figure 1 Single Site Clustering with Cisco TrustSec Technology TrustSec Cisco ASA Cluster with IPS Cisco Security Manager Policies at a Active Directory en tD ata vir on m nm viro En En User Identity Master D ent SXP SEA Flexpod User On-boarding SXP Environment Data Nexus 7k 347923 Identity Services Engine This document is specifically focused on providing implementation guidance on the Single Site Clustering with Cisco TrustSec Technology solution, which is part of the Cisco Secure Data Center for the Enterprise portfolio of solutions. These solutions provide the best protection available to address today’s advanced data security threats. They contain design and implementation guidance for enterprises that want to deploy secure physical and virtualized workloads in their data centers. The solution portfolio contains this solution and two others: Secure Enclaves Architecture and Cyber Threat Defense for the Data Center. Figure 2 illustrates the relationship among these solutions. For additional content that lies outside the scope of this document, see the following URL: http://www.cisco.com/c/en/us/solutions/enterprise/design-zone-secure-data-center-portfolio/index.html . 4 Introduction Figure 2 Cisco Secure Data Center for the Enterprise Solution Portfolio Cisco Secure Enclave Architecture Single-Site Clustering with Cisco TrustSec Technology Cisco Cyber Threat Defense for the Data Center Firewall Clustering Intrusion Prevention Real-time Updates Management Cisco TrustSec Technology • SXP (SGT Exchange Protocol) • SGT (Secure Group Tags • Policy Enforcement • SGACLs (Security Group ACLs) • FWACLs (Firewall ACLs) Lancope StealthWatch System • NetFlow • NSEL (NetFlow Security Event Logging) • Identity 347901 Integrated Systems • Compute • Storage • Hypervisor Virtualization Infrastructure Management Access Layer Secure Enclaves Intended Audience This document is intended for, but not limited to, security architects, system architects, network design engineers, system engineers, field consultants, advanced services specialists, and customers who want to understand how to deploy a robust security architecture. This document details how specific use cases of the designs were implemented for validation. This implementation guide assumes that the reader is familiar with the basic concepts of IP protocols, quality of service (QoS), high availability (HA), and security technologies. This guide also assumes that the reader is aware of general system requirements and has knowledge of enterprise network and data center architectures. Validated Components Table 1 lists the validated components for the solution. Table 1 Validated Components Component Cisco Adaptive Security Appliance (ASA) Role Data center firewall cluster Hardware Cisco ASA 5585-SSP60 Release Cisco ASA Software Release 9.1(4) Cisco Intrusion Prevention Module Application inspection Cisco ASA engines 5585-SSP-IPS60 7.2(1) Cisco Nexus 7000 Aggregation and Cisco 7004 FlexPod access switch NX-OS version 6.1(2) Cisco Identity Services Engine (ISE) Roles-based policy management N/A (virtual machine) Cisco ISE Software Version 1.2 5 Solution Component Implementation Solution Component Implementation As stated in the Single Site Clustering with Cisco TrustSec Technology Solution Design Guide, the solution is designed around the following key design principles: provisioning, performance, and protection. Figure 3 portrays an overview of the lab deployment used for validation. The following sections show how each product was configured to match specific use cases desired in the validation. Figure 3 Lab Overview Enterprise Core Storage SAN Nexus 1kv Virtual Supervisor Module Data CCL Cisco ASA Cluster NetFlow Generation Appliances Active Cisco Identity Directory Services Security Engine Manager SEA Flexpod 347929 Cyber Threat Defense Four Cisco ASA 5585-X SSP60 firewalls with IPS modules are deployed as a cluster with a combination of Layer 2 and Layer 3 mode contexts (multi-mode). The ASA cluster configuration is performed via CLI or Cisco Adaptive Security Device Manager (ASDM)—Cisco Security Manager did not support cluster creation at the time of this validation. Policies for the firewalls and IPS are managed via Cisco Security Manager. User/server device objects are managed in ISE along with TrustSec policy creation for the remaining platforms. User accounts and authentication are linked to Active Directory. Cisco UCS Director is used to manage the deployment of new virtual machines (VMs) across the infrastructure. 6 Solution Component Implementation Cisco ASA Firewall Clustering Initial configuration of the firewalls was performed via the console command line. After the first ASA was configured, additional firewalls were then added to the cluster. For additional information on cluster configuration options, see the following resources: • Cisco ASA 9.1 CLI configuration guide— http://www.cisco.com/c/en/us/td/docs/security/asa/asa91/configuration/general/asa_91_general_co nfig/ha_cluster.html • Cisco ASA Clustering within the VMDC Architecture— http://www.cisco.com/en/US/docs/solutions/Enterprise/Data_Center/VMDC/ASA_Cluster/ASA_C luster.html • Additional Cisco ASA configuration guides— http://www.cisco.com/c/en/us/support/security/asa-5500-series-next-generation-firewalls/products -installation-and-configuration-guides-list.html The cluster in this validation consists of four ASAs acting as a single unit. All units in the cluster are the same model with the same DRAM. The units used in the cluster were all running 9.1(4) software. When deploying the ASA cluster, all of the ASAs must have the exact same configurations for the ASA system to work properly. In addition, they should be deployed in a consistent manner. This applies to using the same type of ports on each unit to connect to the fabric. Use the same ports for the Cluster Control Link (CCL) to the switching fabric and the same with the data links. When the ASA cluster is deployed properly, the master unit of the cluster replicates its configuration to the other units in the cluster, and so the cluster must have a consistent deployment across all the units. Keep in mind that the following features are applied to each ASA unit, instead of the cluster as a whole: • QoS—The QoS policy is synced across the cluster as part of configuration replication. However, the policy is enforced on each unit independently. For example, if you configure policing on output, the conform rate and conform burst values are enforced on traffic exiting a particular ASA. In a cluster with eight units and with traffic evenly distributed, the conform rate actually becomes eight times the rate for the cluster. QoS was not implemented in this validation. • Threat detection—Threat detection works on each unit independently; for example, the top statistics are unit-specific. Port scanning detection, for example, does not work because scanning traffic is load balanced between all units (when using source-dest-ip-port balancing), and one unit does not see all traffic. • Resource management—Resource management in multiple context mode is enforced separately on each unit based on local usage. • IPS module—There is no configuration sync or state sharing between IPS modules. More information on this is available in the IPS section below. ASA Connectivity The ASA interfaces were configured as a spanned EtherChannel using a single port-channel for both inside and outside VLAN interfaces. These channels connect to a pair of Nexus 7000s using a virtual PortChannel (vPC). The EtherChannel aggregates the traffic across all the available active interfaces in the channel. A spanned EtherChannel accommodates both routed and transparent firewall modes per Cisco’s use case requirements. The EtherChannel inherently provides load balancing as part of basic operation using Cluster Link Aggregation Control Protocol (cLACP). Figure 4 shows the connections and port channels implemented. 7 Solution Component Implementation Figure 4 Cluster Connections Clustering Data Interface vPC-20 N7ka vPC-21 0/7 0/9 4/5 ASA-2 IPS-2 PC-2 PC-1 0/6 ASA-3 IPS-3 PC-2 vPC-23 4/7 4/8 PC-1 4/5 vPC-22 0/8 4/11 PC-1 0/9 ASA-4 IPS-4 PC-2 vPC peer-link vPC-21 0/6 0/7 4/10 4/12 4/6 N7ka vPC-24 0/9 4/9 vPC-22 0/7 0/8 vPC peer-link N7kb Clustering Control Interface 0/8 4/10 4/12 PC-1 0/6 PC-2 4/9 4/11 ASA-1 IPS-1 vPC-23 4/6 4/7 4/8 0/6 N7kb vPC-24 0/7 0/9 347918 0/8 It is important to point out that the clustered ASAs have the same port channel configuration because of the sync from the cluster, but the Nexus 7000s have different port channels configured because these are local and not spanned across the cluster. EtherChannels configured for the CCL are configured as discrete EtherChannels on the switch. Note Cisco recommends that the bandwidth of the CCL match at least the highest available bandwidth on the data interfaces. For example, if a 10GE port is used as a data interface, the CCL also needs to support 10GB bandwidth. The reason is that the load balancing performed by the switches connecting to the cluster can be asymmetric and as such, it is possible that all traffic hits just one unit in the cluster, resulting in increased traffic. The interface type mode is the first item that must be specified before configuration of the ASAs. You must set the mode separately on each ASA that you want to add to the cluster. If the device is already configured for multiple context mode, configure this setting in the system execution space. Procedure Step 1 Configure the cluster interface mode for each unit using the console port: ciscoasa(config)# cluster interface-mode spanned The ASA firewall then clears all improper configurations and reboots. Step 2 Next, configure the CCL interface, which must be enabled before joining the cluster. interface TenGigabitEthernet0/6 channel-group 1 mode active no shutdown ! interface TenGigabitEthernet0/7 channel-group 1 mode active no shutdown ! 8 Solution Component Implementation interface Port-channel1 no shutdown Step 3 For multi-mode, create or change to the Admin context. Be sure to assign the M0/0 interface. Step 4 In the Admin context, configure the Cluster IP pool and then assign an IP address to the M0/0 interface, specifying the cluster pool. ip local pool K02-SEA 172.26.164.157-172.26.164.160 mask 255.255.255.0 ! interface Management0/0 management-only nameif management security-level 0 ip address 172.26.164.194 255.255.255.0 cluster-pool K02-SEA no shutdown Step 5 Now you can either launch the Cluster Wizard in the ASDM, or use the following configuration statements to create the master node of the cluster. mtu cluster 9000 cluster group K02-SEA key ***** local-unit ASA-1 cluster-interface Port-channel1 ip 192.168.20.101 255.255.255.0 priority 1 console-replicate no health-check clacp system-mac auto system-priority 1 enable conn-rebalance frequency 3 Once completed, additional security contexts can be created and set as routed or transparent. Note Note that ASDM has a bug: you cannot add the IP address to the sub-interface (vlan) of the routed context for a spanned port channel. In this instance, the IP address was able to be configured via the CLI. There were no problems creating a bridge interface on the transparent firewall context. Adding Additional Slave Firewalls Note Be sure to upgrade ASA software version to match the cluster before adding to the cluster. Each unit in the cluster requires a bootstrap configuration to join the cluster. Typically, the first unit configured in the cluster will be the master unit. After you enable clustering, after an election period, the cluster elects a master unit. With only one unit in the cluster initially, that unit becomes the master unit. Subsequent units added to the cluster will be slave units. Add additional cluster members via the console; Telnet and SSH are not supported. First change the cluster interface mode to match the ASA cluster master, clear the configuration, configure the CCL interface, and join the cluster as a slave as follows: changeto system cluster interface-mode spanned force clear configure cluster mtu cluster 9000 9 Solution Component Implementation interface TenGigabitEthernet0/6 channel-group 1 mode active no shutdown interface TenGigabitEthernet0/7 channel-group 1 mode active no shutdown interface Port-channel1 no shutdown cluster group K02-SEA local-unit ASA-4 priority 3 cluster-interface Port-channel1 ip 192.168.20.104 255.255.255.0 key ********* enable as-slave noconfirm The MTU command enables jumbo-frame reservation, and should be added to the configuration manually because it is not synced via the cluster. Firewall Contexts The ASA cluster was partitioned into multiple virtual devices, known as security contexts. Each context acts as an independent device with its own security policy, interfaces, configuration, and administrators. Multiple contexts are similar to having multiple stand-alone devices. Routed Firewall Mode In routed firewall mode, the ASA is considered to be a router hop in the network. Routed firewall mode supports many interfaces. Each interface is on a different subnet. You can share interfaces between contexts. The ASA acts as a router between connected networks, and each interface requires an IP address on a different subnet. The ASA supports multiple dynamic routing protocols. However, Cisco recommends using the advanced routing capabilities of the upstream and downstream routers instead of relying on the ASA for extensive routing needs. Transparent Firewall Mode A security context can be operated in transparent mode, which acts like a Layer 2 firewall that appears to be a “bump in the wire” or a “stealth firewall”, and is not seen as a router hop to connected devices. The ASA connects to the same network between its interfaces. Because the firewall is not a routed hop, you can easily introduce a transparent firewall into an existing network. The Management and Data interfaces should not be connected to the same switch because the Data interface receives the MAC address table updates with a minimum of a 30-second delay for security reasons. At least one bridge group is required per context, but each context can support up to eight bridge groups. Each bridge group can include up to four interfaces. Note The transparent mode ASA does not pass CDP packets, or any packets that do not have a valid EtherType greater than or equal to 0x600. An exception is made for BPDUs and IS-IS, which are supported. All ASA 5585-X units within the cluster share a single configuration. When configuration changes are made on the master unit, the changes are automatically replicated to all slave units in the cluster. A configuration change directly made on slave units is prohibited. Two transparent mode contexts were created and one routed mode context was created. These were labeled as Enclaves 1 through 3 aligning with the Secure Enterprise Enclave (SEA) design guidance. Figure 5 shows the logical segmentation implemented. 10 Solution Component Implementation Figure 5 Logical Topology Core VLAN 200 - WAN Contexts Enclave 1 (L2) Enclave 2 (L2) Outside Inside Outside Inside Outside 10.3.0.254 Enclave 3 (L3) Inside 10.3.1.254 Cisco ASA Cluster VLAN 2001 VLAN 2002 VLAN 2003 VLAN 3001 10.1.1.254 10.2.1.254 10.3.0.1 10.10.0.1 VLAN 3002 VLAN 3003 Nexus 7k VM VM VM VM VMs in Enclaves 347921 Nexus 1k Management Network All units in the cluster must be connected to a management network that is separate from the CCL. Use the dedicated management interfaces of each ASA as shown in Figure 6. Each ASA is assigned a unique IP address, and a system IP is assigned to the master unit as its secondary IP address. For inbound management traffic, an application such as Cisco Security Manager accesses the master ASA by using the system IP address or individual ASAs by their own IP address. For outbound traffic, such as SNMP or syslog, each ASA uses its own IP address to connect to the server. In multi-context mode, the same configuration applies to the admin context and any user contexts that allow remote management. ip local pool enclave1-pool 10.0.101.101-10.0.101.108 mask 255.255.255.0 ! interface Mgmt101 description Enclave 1 Management management-only nameif management security-level 0 ip address 10.0.101.100 255.255.255.0 cluster-pool enclave1-pool 11 Solution Component Implementation Management Interface Connectivity IPS-1 Cisco ASA Cluster 0/6 M0/0 0/7 0/8 M0/0 0/9 ASA-2 M0/0 IPS-2 M0/0 ASA-1 0/46 0/47 0/43 0/45 Management Switch 0/41 0/42 0/39 0/40 ASA-3 M0/0 IPS-3 M0/0 ASA-4 M0/0 IPS-4 M0/0 0/6 0/7 0/8 0/9 0/6 0/7 0/8 0/9 0/6 0/7 0/8 0/9 4/5 4/9 4/6 4/10 4/7 4/11 4/8 4/12 4/5 4/9 4/6 4/10 4/7 4/11 4/8 4/12 N7ka vPC peer-link N7kb 347919 Figure 6 NetFlow and Syslog NetFlow and syslog are valuable tools for accounting, monitoring, and troubleshooting in such a high-throughput environment, and are key aspects of Cisco’s Cyber Threat Defense solution. ASA units in the cluster generate NetFlow and syslogs independently. The syslog’s HEADER field, which contains a timestamp and device ID, can be customized as required. A syslog collector uses the device ID to identify the syslog generator. The CLI is enhanced so that different ASAs can generate syslog with identical or different device ID. However, a per-unit NetFlow stream cannot be consolidated. The NetFlow collector handles each individual ASA separately. flow-export destination management 172.26.164.240 2055 flow-export template timeout-rate 1 TrustSec and SGT Exchange Protocol Each context maintains its own configurations, databases, credentials, and environment data. The master unit of the cluster contacts ISE via SGT Exchange Protocol (SXP) connections from each context, and obtains the secure group-to-IP address mappings data, which is then replicated to all units in the cluster via reliable messaging; therefore, security group-based policies are enforced on the slave units as well. Security group-based policies are replicated as part of the configuration sync. Both routed and transparent firewall modes are supported. In this validation, the management interface was used for SXP communication with peer devices to keep it out of the normal flow of production traffic. SXP flows from the Nexus 7000 to each of the contexts in the ASA cluster, as shown in Figure 7. The Nexus 7000s act as the “speakers” and send the secure group tag (SGT) and IP address mapping to the “listeners”, which include each of the ASA cluster contexts, via SXP. 12 Solution Component Implementation Figure 7 TrustSec Communication 172.26.164.218 172.26.164.217 Enclave 1 (L2) M101 10.0.101.100 Enclave 2 (L2) M102 10.0.102.100 Enclave 3 (L3) M103 10.0.103.100 Cisco ASA Cluster Nexus 7k 172.26.164.187 Identity 172.26.164.239 Services Engine RADIUS Request Environment Data SXP SG:IP Map 347922 Contexts Configuration of ASA Context (Enclave 1) cts cts cts cts cts sxp sxp sxp sxp sxp enable default password ***** default source-ip 10.0.101.100 connection peer 172.26.164.218 password default mode local listener connection peer 172.26.164.217 password default mode local listener Configurations of Nexus 7000 cts cts cts cts cts cts cts cts cts sxp enable sxp default password 7 <removed> sxp connection peer 10.0.101.100 source 172.26.164.218 password default mode listener sxp connection peer 10.0.102.100 source 172.26.164.218 password default mode listener sxp connection peer 10.0.103.100 source 172.26.164.218 password default mode listener sxp connection peer 172.26.164.18 source 172.26.164.218 password default mode speaker sxp connection peer 172.26.164.186 source 172.26.164.218 password default mode speaker sxp connection peer 192.168.250.22 source 192.168.250.252 password default mode listener role-based enforcement ASA Security Policy Cisco ASA Software Release 9.0.1 and above are necessary for secure group firewall (SGFW) functionality. Policy in the firewall has been expanded to include source and destination security groups that are downloaded from the ISE in the environment data after the ASA has established a secure connection by importing a proxy auto-configuration (PAC) file from the ISE. The ASA issues a RADIUS request for the TrustSec environment data, which includes the secure group table mapping secure group names to secure group numbers. The ASA receives the secure group numbers-to-secure group IP addresses mapping from the Nexus 7000 via SXP. If the PAC file downloaded from the ISE expires on the ASA and the ASA cannot download an updated security group table, the ASA continues to enforce security policies based on the last downloaded security group table until the ASA downloads an updated table. 13 Solution Component Implementation As part of configuring the ASA to integrate with Cisco TrustSec, you must configure each context so that it can communicate with the ISE servers via RADIUS. The last configuration identifies the AAA server group that is used by Cisco TrustSec for environment data retrieval. aaa-server ISE_Radius_Group protocol radius aaa-server ISE_Radius_Group (management) host 172.26.164.187 key ***** radius-common-pw ***** aaa-server ISE_Radius_Group (management) host 172.26.164.239 key ***** radius-common-pw ***** ! cts server-group ISE_Radius_Group When configuring access rules from ASDM and Cisco Security Manager, objects created in the PAC files are available as source and destination criteria. (See Figure 8.) Figure 8 Configuring Access Rules For more information on configuring the ASA to integrate with TrustSec, see the following URL: http://www.cisco.com/c/en/us/td/docs/security/asa/asa91/configuration/general/asa_91_general_config /aaa_trustsec.html 14 Solution Component Implementation IPS Protection The Single Site Clustering with Cscio TrustSec Technology Solution leverages the ASA Next Generation Firewall with IPS module to deliver most of the protection capabilities of the solution. Although TrustSec’s security group access control lists (SGACLs) also provide significant protection capabilities in the switching fabric, TrustSec is discussed in the provisioning section because of its ability to consolidate policies from a provisioning perspective. The IPS uses Cisco Security Intelligence Operations (SIO) cloud-based threat intelligence to simplify operations and creates a system that keeps itself updated. There is no configuration sync or state sharing between IPS modules. Some IPS signatures require IPS to keep the state across multiple connections. For example, the port scanning signature is used when the IPS module detects that someone is opening many connections to one server but with different ports. In clustering, those connections are balanced between multiple ASA devices, each of which has its own IPS module. Because these IPS modules do not share state information, the cluster may not be able to detect port scanning as a result. Not all IPS alerts are actionable, if detecting subtle port scanning is required, Cisco recommends that signatures be tuned across all of the IPS modules in the cluster to accommodate for these types of detection activities. These changes can be performed using Cisco Security Manager and a common policy for the IPS modules; customizations would include dividing the event count triggers by the number of systems in the cluster for the desired signatures. For more information on IPS signatures, see the IPS Sensor CLI Configuration Guide at the following URL: http://www.cisco.com/c/en/us/td/docs/security/ips/7-2/configuration/guide/cli/cliguide72/cli_signature _definitions.html The ASA IPS module runs as a separate application from the ASA. Traffic goes through the firewall before being forwarded to the ASA IPS module. When traffic is identified for IPS inspection on the ASA, traffic flows through the ASA and then the IPS module. Traffic to the ASA IPS module was configured using inline mode. This mode places the ASA IPS module directly in the traffic flow (see Figure 9). No traffic that is identify for IPS inspection can continue through the ASA without first passing through, and being inspected by, the ASA IPS module. This mode is the most secure because every packet identified for inspection is analyzed before being allowed through. Also, the ASA IPS module can implement a blocking policy on a packet-by-packet basis. This mode, however, can affect throughput. 15 Solution Component Implementation Figure 9 Inline Mode ASA Main System Firewall Policy inside VPN Decryption outside Block IPS inspection IPS 251157 Diverted Traffic IPS Security Policies You can create multiple security policies and apply them to individual virtual sensors. A security policy is made up of a signature definition policy, an event action rules policy, and an anomaly detection policy. Cisco IPS contains a default signature definition policy called sig0, a default event action rules policy called rules0, and a default anomaly detection policy called ad0. You can assign the default policies to a virtual sensor or you can create new policies. The use of multiple security policies lets you create security policies based on different requirements and then apply these customized policies per VLAN or physical interface. You can also apply the same policy instance, for example, sig0, rules0, or ad0, to different virtual sensors. You can assign interfaces, inline interface pairs, inline VLAN pairs, and VLAN groups to a virtual sensor. For this validation, all traffic was designated to pass through the IPS inspection module using the default global policy and no virtual sensor. The following sample commands show the IPS being implemented in inline mode on the ASA context, and the feature of failing open in the event of a module problem. policy-map global-policy class class-default ips inline fail-open On the IPS, the sensor is configured to use the default virtual-sensor in detect mode and use the backplane port-channel interface. service analysis-engine virtual-sensor vs0 anomaly-detection operational-mode detect exit physical-interface PortChannel0/0 16 Solution Component Implementation Understanding Global Correlation Global correlation enables the IPS sensors to be aware of network devices with a reputation for malicious activity, and enables them to take action against them. Participating IPS devices in a centralized Cisco threat database, the SensorBase Network, receive and absorb global correlation updates. The reputation information contained in the global correlation updates is factored into the analysis of network traffic, which increases IPS efficacy, because traffic is denied or allowed based on the reputation of the source IP address. The participating IPS devices send data back to the Cisco SensorBase Network, which results in a feedback loop that keeps the updates current and global. The sensor can participate in the global correlation updates and/or in sending telemetry data. Reputation scores in events can be viewed showing the reputation score of the attacker. Statistics from the reputation filter are also available. For enterprise data centers that allow connections from the Internet, the Cisco SIO service provides for global reputation and correlation relevant information to the IPS inspections. To configure global correlation features, follow these steps in the IPS module: service global-correlation global-correlation-inspection on global-correlation-inspection-influence standard reputation-filtering on test-global-correlation on For more information on Cisco IPS and Global Correlation, see the following URL: http://www.cisco.com/c/en/us/td/docs/security/ips/7-1/configuration/guide/cli/cliguide71/cli_collabora tion.html For more information on SIO, see the following URL: http://tools.cisco.com/security/center/home.x Cisco TrustSec The Single Site Clustering with Cisco TrustSec Technology Solution uses key technologies provided by Cisco TrustSec to bring typically disparate data center functions together for simplified provisioning and management. This enables you to bring the ISE, Cisco Security Manager, Cisco UCS Director, and the Cisco Nexus Switching Fabric together to participate in securing the data center. Cisco TrustSec Solution The Cisco TrustSec solution (see Figure 10) provides the customer with the ability to create policies to map end users, or consumers, to data center assets, or servers and applications. Typical policies for securing the data center are the 5-tuple or even recently, context-based policies. These policies have been placed at the edge of the data center in a border-based architecture. TrustSec enables you to create policies that are much deeper than just roles based or a 5-tuple-based approach, all while keeping a defense-in-depth architecture with enforcement points integrated throughout the fabric. Using the TrustSec SGTs and the advance policy capability, you can also leverage TrustSec at the data center virtualization layer to enable separation for your secure containers. For further details and comprehensive information about deploying TrustSec solutions, see the following URL: http://www.cisco.com/go/trustsec. 17 Solution Component Implementation Figure 10 Cisco TrustSec TrustSec Policies Active Directory Environment Data Secure Secure Group Name Group Tag HR 10 20 Engineering 30 John Doe 40 Web Server 50 Email Server ASA Cluster with IPS Cisco Security Manager Alerts API User Identity est equ R ta S Da DIU ent RA m n viro SXP En Master SEA Flexpod RADIUS Identity Services Engine Environment Data SXP Nexus 7k Secure Group Tag 10 20 30 IP Address 1.1.1.1 2.2.2.2 3.3.3.3 347924 User On-boarding Cisco Identity Service Engine Cisco Identity Services Engine (ISE) is an access control system. It provides authentication, authorization, and accounting (AAA) services for a variety of external actors. In the CTS architecture, it has the role of authentication and authorization server. In Figure 11, the ISE provides several key roles to the implementation of TrustSec in the data center: • End-user authentication • TrustSec device enrollment and authorization (switches, firewalls, management platforms) • Establishment and central management of SGTs • Establishment and management of roles-based policies • Propagates environment data (secure groups, secure group names, SGACLs) • Manages change of authorizations (CoAs) The ISE performs other functions, but these are of most interest and relevance to the Secure Data Center for the Enterprise solution. ISE installation was accomplished using the Cisco Identity Services Engine Installation and Upgrade Guides available at the following URL: http://www.cisco.com/c/en/us/support/security/identity-services-engine/products-installation-guides-li st.html. Installation was deployed using a pair of VMs because the laboratory utilizations are very low. Typical enterprise deployments should be on dedicated ISE hardware and scaled to meet enterprise requirements. Each RADIUS client must be added to the ISE network devices as shown in Figure 11. Within Cisco ISE, navigate to Administration> Network Resources > Network Devices. 18 Solution Component Implementation Figure 11 ISE Network Devices Add devices as follows: Procedure Step 1 Click Add. Step 2 Enter the device name and an IP address. Step 3 Under Network Device Group, select the Location and Device Type. Step 4 Scroll down and check the box for Authentication Settings, and configure the shared secret. Step 5 Scroll down and check the box for Security Group Access (SGA). Check the box to use the Device ID for SGA Identification, and configure the password to be used by the device during registration. Step 6 Scroll down and check the box for Device Configuration Deployment. Fill in the exec mode username and password. This step is necessary for deploying the IP/hostname-to-SGT mapping. Step 7 Click Submit. Figure 12 shows the configuration of the ASA Enclave 1, and Figure 13 shows the configuration of the Nexus 7000. 19 Solution Component Implementation 20 Figure 12 ISE ASA Context Device Figure 13 ISE Nexus 7000 Device Solution Component Implementation Each of the ASA contexts in the cluster is configured to communicate with the ISE server, as shown previously in the “ASA Security Policy” section on page 13. The Nexus 1000v and 7000 are both configured to join the Cisco TrustSec domain and receive the SGT PAC files. Procedure Step 1 First, configure the ISE RADIUS group as follows: radius-server host 172.26.164.187 key 7 <removed> authentication accounting radius-server host 172.26.164.239 key 7 <removed> authentication accounting aaa group server radius ISE-Radius-Grp server 172.26.164.187 server 172.26.164.239 use-vrf management source-interface mgmt0 Step 2 After the ISE RADIUS group is configured, next configure the Authentication and Authorization actions: aaa authentication dot1x default group ISE-Radius-Grp aaa accounting dot1x default group ISE-Radius-Grp aaa authorization cts default group ISE-Radius-Grp Step 3 Finally, configure the switch to join the Cisco TrustSec domain. This command invokes device registration with Cisco ISE and forces a PAC download. Make sure the device-id matches the name entry in Cisco ISE. cts device-id k02-fp-sw-a password 7 <removed> For more information on configuring TrustSec on Nexus devices, see the NX-OS Security Configuration Guide at the following URLs: • http://www.cisco.com/c/en/us/support/switches/nexus-7000-series-switches/products-installation-an d-configuration-guides-list.html • http://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/6_x/nx-os/security/configuration/guide /b_Cisco_Nexus_7000_NX-OS_Security_Configuration_Guide__Release_6-x/b_Cisco_Nexus_70 00_NX-OS_Security_Configuration_Guide__Release_6-x_chapter_01101.html Secure Group Tags The Cisco ISE enables end-to-end policies enforced on the basis of role-based access-control lists (RBACLs). Device and user credentials acquired during authentication are used to classify packets by security groups. Every packet entering the Cisco TrustSec domain is tagged with a secure group tag (SGT). The SGT identifies the packet as belonging to either a user or an asset in the data so that policy enforcement can be applied to the packet at the appropriate enforcement point or be processed by advance processing in the ASA 5585-X. Tagging helps trusted intermediaries identify the source identity of the packet and enforce security policies along the data path. An SGT is assigned to a device through IEEE 802.1X authentication, web authentication, or MAC authentication bypass (MAB), which happens with a RADIUS vendor-specific attribute. An SGT can be assigned statically to a particular IP address or to a switch interface. An SGT is passed along dynamically to a switch or access point after successful authentication. 21 Solution Component Implementation Table 2 lists examples of secure group names and their respective SGTs. Table 2 Secure Group Names and Secure Group Tags Secure Group Name HR Secure Group Tag 10 Engineering 20 John Doe 30 Web server 40 Email server 50 SGT Exchange Protocol SGT Exchange Protocol (SXP) is a protocol developed for Cisco TrustSec to propagate the IP-to-SGT mapping database across network devices that do not have SGT-capable hardware support to hardware that supports SGTs and security group access lists. Typically, SXP is conceived as the protocol between the switches that is used to map SGTs to IP addresses. SXP, a control plane protocol, passes IP-SGT mappings from authentication points (such as legacy access layer switches) to upstream switches and authenticated devices in the network. The SXP connections are point-to-point and use TCP as the underlying transport protocol. SXP uses the well-known TCP port number 64999 when initiating a connection. In Figure 14, SXP flows between the Nexus 7000 and the ASA 5585-X, the Nexus 5000 access switch, and the Nexus 1000V. 22 Solution Component Implementation Figure 14 Cisco TrustSec The Nexus 5000 and the Nexus 1000V act as “speakers” and send the SGT and IP address mapping back to the Nexus 7000 via SXP. The Nexus 7000 then sends the SGT-to IP address map to the ASA 5585-X, again via SXP. Table 3 lists examples of SGTs and their respective IP addresses. Table 3 Secure Group Tags and IP Addresses Secure Group Tag 10 IP Address 1.1.1.1 20 2.2.2.2 30 3.3.3.3 Cisco Security Manager Cisco Security Manager manages the policies on the ASAs as would be expected in a traditional deployment model. Security group awareness is integrated into several existing firewall rules; there is no unique TrustSec firewall policy. Security groups are downloaded from the ISE in the environment data after the Cisco Security Manager has established a secure connection and imported a PAC file from the ISE. As described above, the Cisco Security Manager issues a request for the TrustSec environment data, 23 Solution Component Implementation which includes the secure group table mapping secure group names to secure group numbers and are presented as secure group objects. After the environment data is downloaded, creating policies for the firewall is similar to creating extended ACLs. All of the TrustSec and SGT Exchange Protocol configurations described earlier can be managed through common policies in Cisco Security Manager. For more information for using Cisco Security Manager and TrustSec, see Chapter 14 of the User Guide at the following URL: http://www.cisco.com/c/en/us/td/docs/security/security_management/cisco_security_manager/security _manager/4-4/user/guide/CSMUserGuide_wrapper.pdf TrustSec Enforcement In the Cisco TrustSec solution, enforcement devices use a combination of user attributes and end-point attributes to make role-based and identity-based access control decisions. Security group access transforms a topology-aware network into a role-based network, thus enabling end-to-end policies enforced on the basis of RBACLs. Tagged traffic is blocked by the closest device to the source of the traffic that is able to perform enforcement. 24 Validation Testing Validation Testing Summary of Tests Performed These test are designed to validate the integration and general functionality of the Secure Data Center design. The common structure of the architecture is based on Cisco’s integrated reference architectures. Table 4 outlines the various tests conducted to validate the deployment. Table 4 Test Scenarios Test Physical Cisco ASA failure and recovery—Clustered mode Methodology In this failure scenario, Cisco manually removed and recovered power from one of the slave ASA nodes in the cluster. Fail slave Physical Cisco ASA failure and recovery—Clustered mode In this failure scenario, Cisco manually removed and recovered power from the Master ASA node in the cluster. Fail master Physical Cisco ASA failure and recovery—Clustered mode IPS module ASA Cluster Data Link failures—Master and slave In this failure scenario, Cisco manually removed and reinserted an active IPS processor blade from a alave ASA node in the cluster. Fail and recover the following links: • Fail a data link to the master • Fail both data links to the master • Fail a data link to a slave • Fail both data links to a slave Fail a data link to the master, and verify SXP communication switches to the new master elected Fail and recover the following links: • ASA Cluster Control Link failures —Master and slave • Fail a cluster link to the master • Fail both cluster links to the master • Fail a cluster link to a slave Fail both cluster links to a slave Confirm SXP configuration across the infrastructure between the following devices: • SXP data propagation • Nexus 1000v and Nexus 7000 Nexus 7000 and ASA virtual context Confirm that the SGT tag is maintained across the enclave infrastructure. This requires data captures of the ingress and egress of the enclave components, including: • SGT integrity • Nexus 1000v and Nexus 7000 • ASA virtual context • ASAv 25 Validation Testing Table 4 Test Scenarios (continued) Intra-enclave communication Flows within each enclave models are verified point-to-point within the infrastructure. Uniform traffic patterns and then security policy is critical to SEA for each enclave. Steps include: • Baseline traffic established Connections mapped through the enclave Ensure centralized management access via private VLAN and firewall access control rules Asymmetric traffic flows are introduced to the test bed. Ensure the ASA implementation properly manages these flows. Traffic flows are passed through the IPS ASA Cluster configuration. Validate integrity of flow and ability to enforce policy based on SIO data. Confirm integration of the Cisco Security Manager • Management traffic flows Asymmetric traffic flow validation Validate integrity of IPS serviced flows Cisco Security Manager integration • ASA cluster and HA pair management – Virtual context discovery – Virtual context management • ISE integration – Security object learning Cisco Identity Services Engine (ISE) integration Confirm integration of the ISE with the components listed below. • ISE authentication and authorization services across the infrastructure – Nexus switching – UCS domain – ASA platforms – StealthWatch System • Directory service integration – Microsoft Active Directory Services • 26 Security Object Modeling and Security Group ACLs Validation Testing Summary of Results Table 5 lists the summary of test results. Table 5 Summary of Results Test Description Components Physical Cisco ASA Cluster Cisco ASA5585 failure and recovery (Fail Slave) Cisco Security Manager and (Fail Master) Spirent Cisco ASA behavior after IPS Cisco ASA5585 IPS module failure and recovery Cisco Security Manager and (Fail Slave) (Fail Master) Spirent Cisco ASA link failure on Cisco ASA5585 data/clustering link Cisco Security Manager and Spirent Cisco ASA management link Cisco ASA5585 failure Cisco Security Manager and Spirent TrustSec SXP recovery after Cisco ASA5585, ISE, 7000, cluster failure Cisco Security Manager Result No traffic interruption and notification syslog output with acceptable packet loss Verify NetFlow activity and collection All the NetFlow data has been transmitted and collected Cisco ASA5585, 7000 and NGA, Lancope ASA unit that contains the failed IPS module leaves the cluster No traffic interruption and notification syslog output with acceptable packet loss ASA unit with failed management interface leaves the cluster SXP communication reestablished with new master ASA 27 Conclusion Conclusion The Secure Data Center the Enterprise: Single Site Clustering with Cisco TrustSec Technology Solution is a Cisco Validated Design that enables customers to confidently integrate Cisco’s security portfolio to respond to the increasing sophisticated attacks being targeted at the data center. This solution is made even stronger when customers also leverage the Secure Enclaves Architecture for securing the workloads, and leverage the Cyber Threat Defense for Data Center solution for enabling behavioral analysis, which provides zero day mitigation protections in the data center. 28 Appendix A—References Appendix A—References • Access Control Using Security Group Firewall—Aaron Woolan, Cisco.com • Cisco TrustSec How-To Guide: Server-to-Server Segmentation Using SGA—Aaron Woolan, Cisco.com • Data Center Security Design Guide—Mike Storm • Cisco ASA Series CLI Configuration Guides • Cisco Adaptive Security Appliance Cluster Deployment Guide—Mason Harris, David Anderson, Mike Storm 29 Appendix B—Device Configurations Appendix B—Device Configurations ASA Cluster Configurations System Context ASA-1 ASA Version 9.1(4) <system> ! hostname K02-ASA-Cluster domain-name corp.sea9.com enable password <REMOVED> encrypted mac-address auto prefix 1 ! interface GigabitEthernet0/0 shutdown ! interface GigabitEthernet0/1 shutdown ! interface GigabitEthernet0/2 shutdown ! interface GigabitEthernet0/3 shutdown ! interface GigabitEthernet0/4 shutdown ! interface GigabitEthernet0/5 shutdown ! interface Management0/0 ! interface Management0/0.101 description ** Enclave 1 Mgmt ** vlan 101 ! interface Management0/0.102 vlan 102 ! interface Management0/0.103 vlan 103 ! interface Management0/0.164 description ** Flash Interface ** vlan 164 ! interface Management0/1 ! interface TenGigabitEthernet0/6 description N7k-a-T4/6 –vPC21 channel-group 1 mode active ! interface TenGigabitEthernet0/7 description N7k-b-T4/6 –vPC21 channel-group 1 mode active ! interface TenGigabitEthernet0/8 30 Appendix B—Device Configurations channel-group 2 mode active vss-id 1 ! interface TenGigabitEthernet0/9 channel-group 2 mode active vss-id 2 ! interface GigabitEthernet1/0 shutdown ! interface GigabitEthernet1/1 shutdown ! interface GigabitEthernet1/2 shutdown ! interface GigabitEthernet1/3 shutdown ! interface GigabitEthernet1/4 shutdown ! interface GigabitEthernet1/5 shutdown ! interface TenGigabitEthernet1/6 shutdown ! interface TenGigabitEthernet1/7 shutdown ! interface TenGigabitEthernet1/8 shutdown ! interface TenGigabitEthernet1/9 shutdown ! interface Port-channel1 description Clustering Control Interface ! interface Port-channel2 description Cluster Spanned Data Link to PC-20 port-channel span-cluster vss-load-balance ! interface Port-channel2.200 description Uplink network vlan 200 ! interface Port-channel2.2001 description Enclave1-outside vlan 2001 ! interface Port-channel2.2002 description Enclave2-outside vlan 2002 ! interface Port-channel2.2003 description Enclave3-outside vlan 2003 ! interface Port-channel2.3001 description Enclave1-inside vlan 3001 ! interface Port-channel2.3002 description Enclave2-inside 31 Appendix B—Device Configurations vlan 3002 ! interface Port-channel2.3003 description Enclave3-inside vlan 3003 ! class default limit-resource Mac-addresses 65535 limit-resource All 0 limit-resource ASDM 5 limit-resource SSH 5 limit-resource Telnet 5 ! boot system disk0:/asa914-smp-k8.bin ftp mode passive clock timezone EST -5 clock summer-time EDT recurring cluster group K02-SEA key ***** local-unit ASA-1 cluster-interface Port-channel1 ip 192.168.20.101 255.255.255.0 priority 1 console-replicate health-check holdtime 3 clacp system-mac auto system-priority 1 enable conn-rebalance frequency 3 pager lines 24 mtu cluster 9000 no failover asdm image disk0:/asdm-714.bin no asdm history enable arp timeout 14400 no arp permit-nonconnected console timeout 0 ! tls-proxy maximum-session 11000 ! admin-context admin context admin allocate-interface Management0/0.164 config-url disk0:/admin.cfg ! context Enclave1 description Secure Enclave 1 allocate-interface Management0/0.101 Mgmt101 allocate-interface Port-channel2.2001 outside allocate-interface Port-channel2.3001 inside config-url disk0:/enclave1.cfg ! context Enclave2 description Secure Enclave 2 allocate-interface Management0/0.102 Mgmt102 allocate-interface Port-channel2.2002 outside allocate-interface Port-channel2.3002 inside config-url disk0:/enclave2.cfg ! context Enclave3 description Secure Enclave 3 32 Appendix B—Device Configurations allocate-interface Management0/0.103 mgmt103 allocate-interface Port-channel2.2003 outside allocate-interface Port-channel2.3003 inside config-url disk0:/Enclave3.cfg ! prompt hostname context ! jumbo-frame reservation ! no call-home reporting anonymous Cryptochecksum:6b81be0e4ef0f963efbcb3219464df7f : end System Context ASA-3 ASA Version 9.1(4) <system> ! hostname K02-ASA-Cluster domain-name corp.sea9.com enable password <removed> encrypted mac-address auto prefix 1 ! interface GigabitEthernet0/0 shutdown ! interface GigabitEthernet0/1 shutdown ! interface GigabitEthernet0/2 shutdown ! interface GigabitEthernet0/3 shutdown ! interface GigabitEthernet0/4 shutdown ! interface GigabitEthernet0/5 shutdown ! interface Management0/0 ! interface Management0/0.101 description ** Enclave 1 Mgmt ** vlan 101 ! interface Management0/0.102 vlan 102 ! interface Management0/0.103 vlan 103 ! interface Management0/0.164 description ** Flash Interface ** vlan 164 ! interface Management0/1 ! interface TenGigabitEthernet0/6 description N7k-a-T4/6 -vPC3 33 Appendix B—Device Configurations channel-group 1 mode active ! interface TenGigabitEthernet0/7 description N7k-b-T4/6 -vPC3 channel-group 1 mode active ! interface TenGigabitEthernet0/8 channel-group 2 mode active vss-id 1 ! interface TenGigabitEthernet0/9 channel-group 2 mode active vss-id 2 ! interface GigabitEthernet1/0 shutdown ! interface GigabitEthernet1/1 shutdown ! interface GigabitEthernet1/2 shutdown ! interface GigabitEthernet1/3 shutdown ! interface GigabitEthernet1/4 shutdown ! interface GigabitEthernet1/5 shutdown ! interface TenGigabitEthernet1/6 shutdown ! interface TenGigabitEthernet1/7 shutdown ! interface TenGigabitEthernet1/8 shutdown ! interface TenGigabitEthernet1/9 shutdown ! interface Port-channel1 description Clustering Interface ! interface Port-channel2 description Cluster Spanned Data Link to PC-20 port-channel span-cluster vss-load-balance ! interface Port-channel2.200 description Uplink network vlan 200 ! interface Port-channel2.2001 description Enclave1-outside vlan 2001 ! interface Port-channel2.2002 description Enclave2-outside vlan 2002 ! interface Port-channel2.2003 description Enclave3-outside vlan 2003 34 Appendix B—Device Configurations ! interface Port-channel2.3001 description Enclave1-inside vlan 3001 ! interface Port-channel2.3002 description Enclave2-inside vlan 3002 ! interface Port-channel2.3003 description Enclave3-inside vlan 3003 ! class default limit-resource Mac-addresses 65535 limit-resource All 0 limit-resource ASDM 5 limit-resource SSH 5 limit-resource Telnet 5 ! boot system disk0:/asa914-smp-k8.bin ftp mode passive clock timezone EST -5 clock summer-time EDT recurring cluster group K02-SEA key ***** local-unit ASA-3 cluster-interface Port-channel1 ip 192.168.20.103 255.255.255.0 priority 3 console-replicate health-check holdtime 3 clacp system-mac auto system-priority 1 enable conn-rebalance frequency 3 pager lines 24 mtu cluster 9000 no failover asdm image disk0:/asdm-714.bin no asdm history enable arp timeout 14400 no arp permit-nonconnected console timeout 0 ! tls-proxy maximum-session 11000 ! admin-context admin context admin allocate-interface Management0/0.164 config-url disk0:/admin.cfg ! context Enclave1 description Secure Enclave 1 allocate-interface Management0/0.101 Mgmt101 allocate-interface Port-channel2.2001 outside allocate-interface Port-channel2.3001 inside config-url disk0:/enclave1.cfg ! context Enclave2 description Secure Enclave 2 allocate-interface Management0/0.102 Mgmt102 allocate-interface Port-channel2.2002 outside 35 Appendix B—Device Configurations allocate-interface Port-channel2.3002 inside config-url disk0:/enclave2.cfg ! context Enclave3 description Secure Enclave 3 allocate-interface Management0/0.103 mgmt103 allocate-interface Port-channel2.2003 outside allocate-interface Port-channel2.3003 inside config-url disk0:/Enclave3.cfg ! prompt hostname context ! jumbo-frame reservation ! no call-home reporting anonymous Cryptochecksum:faca7e6346ac9c9355f24f0011b0e902 : end K02-ASA-Cluster# Admin Context ASA Version 9.1(4) <context> ! hostname admin enable password <removed> encrypted names ip local pool K02-SEA 172.26.164.157-172.26.164.160 mask 255.255.255.0 ! interface Management0/0.164 management-only nameif management security-level 0 ip address 172.26.164.191 255.255.255.0 cluster-pool K02-SEA ! pager lines 21 logging enable logging standby logging buffer-size 128000 logging asdm-buffer-size 512 logging console notifications logging monitor notifications logging asdm informational logging facility 16 no logging message 106015 no logging message 313001 no logging message 313008 no logging message 106023 no logging message 710003 no logging message 106100 no logging message 302015 no logging message 302014 no logging message 302013 no logging message 302018 no logging message 302017 no logging message 302016 no logging message 302021 no logging message 302020 flow-export destination management 172.26.164.240 2055 36 Appendix B—Device Configurations flow-export template timeout-rate 1 mtu management 1500 icmp unreachable rate-limit 1 burst-size 1 icmp permit any management no asdm history enable arp timeout 14400 route management 0.0.0.0 0.0.0.0 172.26.164.254 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 aaa-server ISE_Radius_Group protocol radius aaa-server ISE_Radius_Group (management) host 172.26.164.187 key ***** radius-common-pw ***** aaa-server ISE_Radius_Group (management) host 172.26.164.239 key ***** radius-common-pw ***** user-identity default-domain LOCAL aaa authentication enable console ISE_Radius_Group LOCAL aaa authentication ssh console ISE_Radius_Group LOCAL aaa authentication http console ISE_Radius_Group LOCAL aaa authentication serial console ISE_Radius_Group LOCAL aaa accounting enable console ISE_Radius_Group aaa accounting serial console ISE_Radius_Group aaa accounting ssh console ISE_Radius_Group aaa local authentication attempts max-fail 3 aaa authorization exec authentication-server http server enable http 0.0.0.0 0.0.0.0 management no snmp-server location no snmp-server contact crypto ipsec security-association pmtu-aging infinite telnet timeout 5 ssh 0.0.0.0 0.0.0.0 management ssh timeout 60 ssh version 2 ssh key-exchange group dh-group1-sha1 threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200 ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect ip-options inspect netbios inspect rsh inspect esmtp inspect sqlnet inspect sunrpc inspect tftp inspect xdmcp 37 Appendix B—Device Configurations class class-default user-statistics accounting flow-export event-type all destination 172.26.164.240 ! service-policy global_policy global Cryptochecksum:85251c60c289c64cb8331d05b632c278 : end Enclave1 Context K02-ASA-Cluster/Enclave1# sh run : Saved : ASA Version 9.1(4) <context> ! firewall transparent hostname Enclave1 domain-name corp.sea9.com enable password <removed> encrypted passwd <removed> encrypted names ip local pool enclave1-pool 10.0.101.101-10.0.101.108 mask 255.255.255.0 ! interface BVI1 description Enclave1 ip address 10.1.1.251 255.255.255.0 ! interface Mgmt101 description Enclave 1 Management my management-only nameif management security-level 0 ip address 10.0.101.100 255.255.255.0 cluster-pool enclave1-pool ! interface outside nameif outside bridge-group 1 security-level 0 ! interface inside nameif inside bridge-group 1 security-level 100 ! dns domain-lookup management dns server-group DefaultDNS name-server 172.26.164.190 domain-name corp.sea9.com object network Management subnet 172.26.164.0 255.255.255.0 object network Enclave1-Mgmt-IP host 10.0.101.100 description Enclave 1 Managment IP address access-list CSM_FW_ACL_ extended permit icmp 10.10.66.0 255.255.255.0 10.1.1.0 255.255.255.0 access-list CSM_FW_ACL_ extended permit tcp 10.10.66.0 255.255.255.0 10.1.1.0 255.255.255.0 eq www access-list CSM_FW_ACL_ extended permit tcp 10.10.66.0 255.255.255.0 10.1.1.0 255.255.255.0 eq ftp access-list CSM_FW_ACL_ extended permit icmp 10.1.1.0 255.255.255.0 10.10.66.0 255.255.255.0 38 Appendix B—Device Configurations access-list CSM_FW_ACL_ extended permit tcp 10.1.1.0 255.255.255.0 10.10.66.0 255.255.255.0 eq www access-list CSM_FW_ACL_ extended permit tcp 10.1.1.0 255.255.255.0 10.10.66.0 255.255.255.0 eq ftp access-list CSM_FW_ACL_ extended permit ip security-group name SGT_1001_Enclave1 any security-group name enc1_30012_priv any access-list CSM_TFW_ACL_INBOUND_1 ethertype permit bpdu pager lines 24 logging enable no logging message 106015 no logging message 313001 no logging message 313008 no logging message 106023 no logging message 710003 no logging message 106100 no logging message 302015 no logging message 302014 no logging message 302013 no logging message 302018 no logging message 302017 no logging message 302016 no logging message 302021 no logging message 302020 flow-export destination management 172.26.164.240 2055 flow-export template timeout-rate 1 mtu management 1500 mtu outside 1500 mtu inside 1500 icmp unreachable rate-limit 1 burst-size 1 icmp permit any management icmp permit any outside icmp permit any inside no asdm history enable arp timeout 14400 access-group CSM_TFW_ACL_INBOUND_1 in interface outside access-group CSM_TFW_ACL_INBOUND_1 in interface inside access-group CSM_FW_ACL_ global route outside 0.0.0.0 0.0.0.0 10.1.1.254 1 route management 172.26.164.0 255.255.255.0 10.0.101.254 1 route management 192.168.250.18 255.255.255.255 10.0.101.254 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 aaa-server ISE_Radius_Group protocol radius aaa-server ISE_Radius_Group (management) host 172.26.164.187 key ***** radius-common-pw ***** aaa-server ISE_Radius_Group (management) host 172.26.164.239 key ***** radius-common-pw ***** cts server-group ISE_Radius_Group cts sxp enable cts sxp default password ***** cts sxp default source-ip 10.0.101.100 cts sxp connection peer 172.26.164.218 password default mode local listener cts sxp connection peer 172.26.164.217 password default mode local listener user-identity default-domain LOCAL aaa authentication enable console ISE_Radius_Group LOCAL aaa authentication http console ISE_Radius_Group LOCAL 39 Appendix B—Device Configurations aaa authentication ssh console ISE_Radius_Group LOCAL aaa accounting enable console ISE_Radius_Group aaa accounting ssh console ISE_Radius_Group aaa local authentication attempts max-fail 3 http server enable http 0.0.0.0 0.0.0.0 management no snmp-server location no snmp-server contact crypto ipsec security-association pmtu-aging infinite telnet timeout 5 ssh 172.26.164.0 255.255.255.0 management ssh timeout 5 ssh key-exchange group dh-group1-sha1 no threat-detection statistics tcp-intercept ! ! ! policy-map global-policy class class-default flow-export event-type all destination 172.26.164.240 ips inline fail-open ! service-policy global-policy global Cryptochecksum:bf5cfdd35116e819b568aef07919ffa0 : end Enclave 3 Context K02-ASA-Cluster/Enclave3# sh run : Saved : ASA Version 9.1(4) <context> ! hostname Enclave3 enable password <removed> encrypted names ip local pool enclave3-pool 10.0.103.101-10.0.103.108 mask 255.255.255.0 ! interface mgmt103 management-only nameif mgmt security-level 0 ip address 10.0.103.100 255.255.255.0 cluster-pool enclave3-pool ! interface outside nameif outside security-level 0 ip address 10.3.0.254 255.255.255.0 ! interface inside nameif inside security-level 100 ip address 10.3.1.254 255.255.255.0 ! access-list CSM_FW_ACL_ extended permit icmp 10.10.66.0 255.255.255.0 10.3.1.0 255.255.255.0 access-list CSM_FW_ACL_ extended permit tcp 10.10.66.0 255.255.255.0 10.3.1.0 255.255.255.0 eq ftp access-list CSM_FW_ACL_ extended permit tcp 10.10.66.0 255.255.255.0 10.3.1.0 255.255.255.0 eq www access-list CSM_FW_ACL_ extended permit icmp 10.3.1.0 255.255.255.0 10.10.66.0 255.255.255.0 40 Appendix B—Device Configurations access-list CSM_FW_ACL_ extended permit tcp 10.3.1.0 255.255.255.0 10.10.66.0 255.255.255.0 eq ftp access-list CSM_FW_ACL_ extended permit tcp 10.3.1.0 255.255.255.0 10.10.66.0 255.255.255.0 eq www access-list CSM_FW_ACL_ extended permit icmp any any pager lines 24 logging enable mtu inside 1500 mtu outside 1500 mtu mgmt 1500 icmp unreachable rate-limit 1 burst-size 1 icmp permit any inside icmp permit any outside icmp permit any mgmt no asdm history enable arp timeout 14400 access-group CSM_FW_ACL_ global route outside 0.0.0.0 0.0.0.0 10.3.0.1 1 route mgmt 172.26.164.0 255.255.255.0 10.0.103.254 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 aaa-server ISE_Radius_Group protocol radius aaa-server ISE_Radius_Group (inside) host 172.26.164.187 key ***** radius-common-pw ***** aaa-server ISE_Radius_Group (inside) host 172.26.164.239 key ***** radius-common-pw ***** cts server-group ISE_Radius_Group cts sxp enable cts sxp default password ***** cts sxp default source-ip 10.0.103.100 cts sxp connection peer 172.26.164.218 source 10.0.103.100 password default mode local listener cts sxp connection peer 172.26.164.217 source 10.0.103.100 password default mode local listener user-identity default-domain LOCAL aaa authentication enable console ISE_Radius_Group LOCAL aaa authentication http console ISE_Radius_Group LOCAL aaa authentication ssh console ISE_Radius_Group LOCAL aaa accounting enable console ISE_Radius_Group aaa accounting ssh console ISE_Radius_Group no snmp-server location no snmp-server contact auth-prompt prompt Enclave3 Context crypto ipsec security-association pmtu-aging infinite telnet timeout 5 ssh timeout 5 ssh key-exchange group dh-group1-sha1 no threat-detection statistics tcp-intercept ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto 41 Appendix B—Device Configurations message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect rsh inspect esmtp inspect sqlnet inspect sunrpc inspect xdmcp inspect netbios inspect tftp inspect ip-options class class-default ips inline fail-open ! service-policy global_policy global Cryptochecksum:02ed5d10127795179b0900f540e80f07 : end K02-ASA-Cluster/Enclave3# IPS Configuration sea-asaips-1# sh configuration ! -----------------------------! Current configuration last modified Fri Jan 17 19:57:45 2014 ! -----------------------------! Version 7.2(1) ! Host: ! Realm Keys key1.0 ! Signature Definition: ! Signature Update S771.0 2014-02-07 ! -----------------------------service interface exit ! -----------------------------service authentication exit ! -----------------------------service event-action-rules rules0 exit ! -----------------------------service host network-settings host-ip 172.26.164.195/24,172.26.164.254 host-name sea-asaips-1 telnet-option disabled sshv1-fallback enabled access-list 0.0.0.0/0 access-list 0.0.0.0/32 login-banner-text Connected to sea-asaips-1 dns-primary-server enabled address 172.26.164.190 exit dns-secondary-server disabled dns-tertiary-server disabled -proxy proxy-server address 64.102.255.40 port 8080 exit exit time-zone-settings 42 Appendix B—Device Configurations offset -5 standard-time-zone-name EST exit ntp-option enabled-ntp-unauthenticated ntp-server 172.26.164.254 exit summertime-option recurring summertime-zone-name EDT exit auto-upgrade cisco-server enabled schedule-option periodic-schedule start-time 00:00:00 interval 24 exit user-name bmcgloth exit exit exit ! -----------------------------service logger exit ! -----------------------------service network-access exit ! -----------------------------service notification exit ! -----------------------------service signature-definition sig0 variables ALLPORTS web-ports 0-65535 variables WEBPORTS web-ports 80-80,3128-3128,8000-8000,8010-8010,8080-8080,8888-8888,24326-24326 application-policy http-policy http-enable true aic-web-ports 80,3128,8000,8010,8080,8888,24326 exit exit signatures 2154 0 status enabled true exit exit signatures 64001 0 sig-description sig-name smb_nonstd_prt_1 exit engine fixed-tcp direction from-service max-payload-inspect-length 100 regex-string \xff[Ss][Mm][Bb] specify-service-ports yes service-ports 20,21,22,23,53,80,111,123,137,138,139,161,443,514,1433,1434 exit exit exit signatures 64003 0 sig-description sig-name snmp_nonstd_prt_1 exit engine fixed-udp event-action produce-alert max-payload-inspect-length 64 43 Appendix B—Device Configurations regex-string \x30[\x1A-\x7F]\x02\x01\[\x00\x01\x03] specify-service-ports yes service-ports 20,21,22,23,53,80,111,123,137,138,139,161,514,443,445,1433,1434 exit exit exit exit ! -----------------------------service ssh-known-hosts exit ! -----------------------------service trusted-certificates exit ! -----------------------------service web-server exit ! -----------------------------service anomaly-detection ad0 exit ! -----------------------------service external-product-interface exit ! -----------------------------service health-monitor exit ! -----------------------------service global-correlation global-correlation-inspection on global-correlation-inspection-influence standard reputation-filtering on test-global-correlation on exit ! -----------------------------service aaa exit ! -----------------------------service analysis-engine virtual-sensor vs0 anomaly-detection operational-mode detect exit physical-interface PortChannel0/0 exit exit sea-asaips-1# Nexus 7000 Configuration k02-n7k-a-k02-fp-sw-a# sh run !Command: show running-config !Time: Fri Feb 14 00:57:06 2014 version 6.1(2) switchname k02-fp-sw-a cfs ipv4 distribute cfs eth distribute feature private-vlan feature udld feature interface-vlan feature dot1x 44 Appendix B—Device Configurations feature hsrp feature lacp feature cts cts device-id k02-fp-sw-a password 7 <removed> cts role-based counters enable cts sxp enable cts sxp default password 7 <removed> cts sxp connection peer 10.0.101.100 source 172.26.164.218 password default mode listener cts sxp connection peer 10.0.102.100 source 172.26.164.218 password default mode listener cts sxp connection peer 10.0.103.100 source 172.26.164.218 password default mode listener cts sxp connection peer 172.26.164.18 source 172.26.164.218 password default mode speaker cts sxp connection peer 172.26.164.186 source 172.26.164.218 password default mode speaker cts sxp connection peer 192.168.250.22 source 192.168.250.252 password default mode listener cts role-based enforcement feature vpc feature pong logging level cts 6 logging level radius 6 username admin password 5 <removed> role vdc-admin username ise-user password 5 <removed> role vdc-operator ip domain-lookup ip domain-name corp.sea9.com ip name-server 172.26.164.190 use-vrf management radius-server key 7 <removed> radius distribute radius-server host 172.26.164.187 key 7 <removed> authentication accounting radius-server host 172.26.164.239 key 7 <removed> authentication accounting radius commit aaa group server radius ISE-Radius-Grp server 172.26.164.187 use-vrf management source-interface mgmt0 aaa group server radius aaa-private-sg server 172.26.164.187 use-vrf management source-interface mgmt0 system default switchport snmp-server user admin vdc-admin auth md5 <removed> priv <removed> localizedkey snmp-server user ise-user vdc-operator auth md5 0<removed> localizedkey rmon event 1 log trap public description FATAL(1) owner PMON@FATAL rmon event 2 log trap public description CRITICAL(2) owner PMON@CRITICAL rmon event 3 log trap public description ERROR(3) owner PMON@ERROR rmon event 4 log trap public description WARNING(4) owner PMON@WARNING rmon event 5 log trap public description INFORMATION(5) owner PMON@INFO ntp distribute ntp server 172.26.164.20 use-vrf management ntp source-interface Vlan3250 ntp master 8 ntp commit aaa authentication login default group ISE-Radius-Grp aaa authentication dot1x default group ISE-Radius-Grp aaa accounting dot1x default group ISE-Radius-Grp aaa authorization cts default group ISE-Radius-Grp aaa accounting default group ISE-Radius-Grp no aaa user default-role ip route 10.0.0.0/16 172.26.164.254 ip route 10.3.0.0/16 10.3.0.254 name Enclave3 ip route 10.71.1.186/32 172.26.164.186 vrf context management ip route 0.0.0.0/0 172.26.164.254 vlan 1-2,20,98-99,200-219,666,2001-2019,3001-3019,3170-3173,3175-3179,3250-3251,3253-3255 45 Appendix B—Device Configurations vlan 2 name Native_VLAN vlan 20 name ASA-Cluster-Control vlan 98 name vsg-ha vlan 99 name vsg-data vlan 201 name NFS-Enclave1 vlan 202 name NFS-Enclave2 vlan 203 name NFS-Enclave3 vlan 204 name NFS-Enclave4 vlan 205 name NFS-Enclave5 vlan 206 name NFS-Enclave6 vlan 207 name NFS-Enclave7 vlan 208 name NFS-Enclave8 vlan 209 name NFS-Enclave9 vlan 666 name WAN-on7k vlan 2001 name D1-Enclave1 vlan 2002 name D1-Enclave2 vlan 2003 name D1-Enclave3 vlan 2004 name D1-Enclave4 vlan 2005 name D1-Enclave5 vlan 2006 name D1-Enclave6 vlan 2007 name D1-Enclave7 vlan 2008 name D1-Enclave8 vlan 2009 name D1-Enclave9 vlan 2010 name D1-Enclave10 vlan 2011 name D1-Enclave11 vlan 2012 name D1-Enclave12 vlan 2013 name D1-Enclave13 vlan 2014 name D1-Enclave14 vlan 2015 name D1-Enclave15 vlan 2016 name D1-Enclave16 vlan 2017 name D1-Enclave17 vlan 2018 name D1-Enclave18 46 Appendix B—Device Configurations vlan 2019 name D1-Enclave19 vlan 3001 name D2-Enclave1 vlan 3002 name D2-Enclave2 vlan 3003 name D2-Enclave3 vlan 3004 name D2-Enclave4 vlan 3005 name D2-Enclave5 vlan 3006 name D2-Enclave6 vlan 3007 name D2-Enclave7 vlan 3008 name D2-Enclave8 vlan 3009 name D2-Enclave9 vlan 3010 name D2-Enclave10 vlan 3011 name D2-Enclave11 vlan 3012 name D2-Enclave12 vlan 3013 name D2-Enclave13 vlan 3014 name D2-Enclave14 vlan 3015 name D2-Enclave15 vlan 3016 name D2-Enclave16 vlan 3017 name D2-Enclave17 vlan 3018 name D2-Enclave18 vlan 3019 name D2-Enclave19 vlan 3170 name NFS-VLAN vlan 3171 name core-services-primary private-vlan primary private-vlan association 3172 vlan 3172 name core-services-isolated private-vlan isolated vlan 3173 name vMotion-VLAN vlan 3175 name IB-MGMT-VLAN vlan 3176 name Packet-Control-VLAN vlan 3177 name infra-vtep-vxlan vlan 3178 name monitor-primary vlan 3179 name monitor-isolated vlan 3250 name sea-prod-mgmt vlan 3251 47 Appendix B—Device Configurations name vMotion vlan 3253 name prod-vtep-vxlan vlan 3254 name services vlan 3255 name services_HA spanning-tree port type edge bpduguard default spanning-tree port type edge bpdufilter default spanning-tree port type network default vpc domain 100 role priority 10 peer-keepalive destination 172.26.164.183 source 172.26.164.182 peer-gateway auto-recovery port-profile type port-channel UCS-FI switchport switchport mode trunk switchport trunk native vlan 2 spanning-tree port type edge trunk mtu 9216 switchport trunk allowed vlan 2,98-99,201-219,666,2001-2019,3001-3019 switchport trunk allowed vlan add 3170-3173,3175-3179,3250-3251,3253-3255 description <<**UCS Fabric Interconnect Port Profile **>> state enabled port-profile type ethernet Stand-alone-Management-Servers switchport spanning-tree port type edge trunk switchport trunk allowed vlan 98-99,3170-3173,3175-3179,3250,3254-3255 switchport trunk native vlan 2 mtu 9216 description <<** C-Series Management Server Profile **>> state enabled port-profile type ethernet Cloud-Services-Platforms switchport switchport mode trunk spanning-tree port type edge trunk switchport trunk allowed vlan 98-99,3175-3176,3250 description <<** CSP Port Profile **>> state enabled port-profile type port-channel FAS-Node switchport switchport mode trunk switchport trunk native vlan 2 spanning-tree port type edge trunk mtu 9216 switchport trunk allowed vlan 201-219,3170 description <<** NetApp FAS Node Port Profile **>> state enabled vlan 1 cts role-based vlan 2 cts role-based vlan 98 cts role-based vlan 99 cts role-based vlan 3009 cts role-based vlan 3170 cts role-based vlan 3173 48 enforcement enforcement enforcement enforcement enforcement enforcement Appendix B—Device Configurations cts role-based enforcement vlan 3175 cts role-based enforcement vlan 3177 cts role-based enforcement interface Vlan1 no ip redirects no ipv6 redirects interface Vlan5 no ip redirects no ipv6 redirects interface Vlan20 description <** ASA Cluster control **> no shutdown no ip redirects ip address 192.168.20.201/24 no ipv6 redirects interface Vlan200 description <** Enclave Uplink **> no shutdown no ip redirects ip address 10.10.0.3/24 no ipv6 redirects hsrp 1 authentication text c1sc0 preempt delay minimum 180 priority 25 forwarding-threshold lower 0 upper 0 timers 1 3 ip 10.10.0.1 interface Vlan666 no shutdown no ip redirects ip address 10.10.66.1/24 no ipv6 redirects interface Vlan2001 description <<** Enclave 1-outside**>> no shutdown no ip redirects ip address 10.1.1.252/24 no ipv6 redirects hsrp 1 authentication text c1sc0 preempt delay minimum 180 priority 15 forwarding-threshold lower 0 upper 0 timers 1 3 ip 10.1.1.254 interface Vlan2002 description <<** Enclave2-outside DGW **>> no shutdown no ip redirects ip address 10.10.2.201/24 no ipv6 redirects hsrp 1 authentication text c1sc0 preempt delay minimum 180 priority 25 forwarding-threshold lower 0 upper 0 49 Appendix B—Device Configurations timers 1 3 ip 10.10.2.1 interface Vlan2003 description <** Enclave 3-outside **> no shutdown no ip redirects ip address 10.3.0.3/24 no ipv6 redirects hsrp 1 authentication text c1sc0 preempt delay minimum 180 priority 15 forwarding-threshold lower 0 upper 0 timers 1 3 ip 10.3.0.1 interface Vlan3001 description <<** Enclave 1 Inside **>> no ip redirects no ipv6 redirects interface Vlan3002 description <<** VLAN 3002 Inside Enclave2 **>> no shutdown private-vlan mapping 32 no ip redirects no ipv6 redirects interface Vlan3009 description <<** Enclave 9 DGW - No ASA **>> no shutdown no ip redirects ip address 10.9.1.252/24 no ipv6 redirects hsrp 1 authentication text c1sc0 preempt delay minimum 180 priority 15 forwarding-threshold lower 0 upper 0 timers 1 3 ip 10.9.1.254 interface Vlan3171 private-vlan mapping 3172 ip address 192.168.0.3/24 no ipv6 redirects ip local-proxy-arp interface Vlan3175 no shutdown management no ip redirects ip address 172.26.164.218/24 no ipv6 redirects interface Vlan3250 description <** Production Management SVI **>> no shutdown no ip redirects ip address 192.168.250.252/24 no ipv6 redirects hsrp version 2 hsrp 1 authentication text c1sc0 preempt delay minimum 180 50 Appendix B—Device Configurations priority 15 forwarding-threshold lower 0 upper 0 timers 1 3 ip 192.168.250.1 interface port-channel8 description <<** NGA SPAN PORTS **>> switchport mode trunk switchport monitor interface port-channel9 switchport access vlan 3175 spanning-tree port type normal vpc 9 interface port-channel10 description <<** vPC peer-link **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 10,20,32,71,98-99,200-209,211-219 switchport trunk allowed vlan add 300-319,400-419,666,2001-2135,3001-3135 switchport trunk allowed vlan add 3170-3177,3250-3251,3253-3255 spanning-tree port type network vpc peer-link interface port-channel11 inherit port-profile FAS-Node description <<** fas_node1 **>> vpc 11 interface port-channel12 inherit port-profile FAS-Node description <<** fas_node2 **>> vpc 12 interface port-channel13 inherit port-profile UCS-FI description <<** k02-ucs-fab-a **> switchport mode trunk switchport trunk allowed vlan 2, 98-99, 201-219, 666, 2001-2019, 3001-3019 switchport trunk allowed vlan add 3170-3173, 3175-3179, 3250-3251, 3253-3255 spanning-tree port type edge trunk mtu 9216 vpc 13 interface port-channel14 inherit port-profile UCS-FI description <<** k02-ucs-fab-b **>> switchport mode trunk switchport trunk allowed vlan 2, 98-99, 201-219, 666, 2001-2019, 3001-3019 switchport trunk allowed vlan add 3170-3173, 3175-3179, 3250-3251, 3253-3255 spanning-tree port type edge trunk mtu 9216 vpc 14 interface port-channel20 description <<** k02-ASA-Cluster-Data **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 200,666,2001-2135,3001-3135 spanning-tree port type normal vpc 20 interface port-channel21 description <<** k02-ASA-1-Control **>> 51 Appendix B—Device Configurations switchport access vlan 20 spanning-tree port type normal no logging event port link-status no logging event port trunk-status vpc 21 interface port-channel22 description <<** k02-ASA-2-Control **>> switchport access vlan 20 spanning-tree port type normal vpc 22 interface port-channel23 description <<** k02-ASA-3-Control **>> switchport access vlan 20 spanning-tree port type normal vpc 23 interface port-channel24 description <<** k02-ASA-4-Control **>> switchport access vlan 20 spanning-tree port type normal vpc 24 interface port-channel3250 shutdown switchport mode trunk switchport trunk allowed vlan 3250 vpc 3250 interface Ethernet4/1 description <<** fas_node1:e3a **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 201-219,3170 mtu 9216 channel-group 11 mode active no shutdown interface Ethernet4/2 description <<** fas_node2:e3a **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 201-219,3170 mtu 9216 channel-group 12 mode active no shutdown interface Ethernet4/3 description <<** SEA Production Management **>> switchport mode trunk switchport trunk allowed vlan 3250 channel-group 3250 mode active no shutdown interface Ethernet4/4 interface Ethernet4/5 description <<** VPC Peer K02-ASA-1:T6 **>> switchport access vlan 20 spanning-tree port type normal channel-group 21 mode active no shutdown 52 Appendix B—Device Configurations interface Ethernet4/6 description <<** VPC Peer K02-ASA-2:T6 **>> switchport access vlan 20 spanning-tree port type normal channel-group 22 mode active no shutdown interface Ethernet4/7 description <<** VPC Peer K02-ASA-3:T6 **>> switchport access vlan 20 spanning-tree port type normal channel-group 23 mode active no shutdown interface Ethernet4/8 description <<** VPC Peer K02-ASA-4:T6 **>> switchport access vlan 20 spanning-tree port type normal channel-group 24 mode active no shutdown interface Ethernet4/9 description <<** VPC Peer K02-ASA-1:T8 **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 200,666,2001-2135,3001-3135 spanning-tree port type normal channel-group 20 mode active no shutdown interface Ethernet4/10 description <<** VPC Peer K02-ASA-2:T8 **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 200,666,2001-2135,3001-3135 spanning-tree port type normal channel-group 20 mode active no shutdown interface Ethernet4/11 description <<** VPC Peer K02-ASA-3:T8 **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 200,666,2001-2135,3001-3135 spanning-tree port type normal channel-group 20 mode active no shutdown interface Ethernet4/12 description <<** VPC Peer K02-ASA-4:T8 **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 200,666,2001-2135,3001-3135 spanning-tree port type normal channel-group 20 mode active no shutdown interface Ethernet4/17 inherit port-profile Cloud-Services-Platforms description <<** k02-n1110-1:Eth1 **>> no shutdown interface Ethernet4/18 53 Appendix B—Device Configurations interface Ethernet4/19 inherit port-profile Cloud-Services-Platforms description <<** k02-n1110-2:Eth1 **>> no shutdown interface Ethernet4/20 interface Ethernet4/25 interface Ethernet4/26 interface Ethernet4/27 description <<** k02-ucs-fab-a:1/27 switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 2,98-99,201-219,666,2001-2019,3001-3019 switchport trunk allowed vlan add 3170-3173,3175-3179,3250-3251,3253-3255 mtu 9216 channel-group 13 mode active no shutdown interface Ethernet4/28 description <<** k02-ucs-fab-b:1/28 **> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 2,98-99,201-219,666,2001-2019,3001-3019 switchport trunk allowed vlan add 3170-3173,3175-3179,3250-3251,3253-3255 mtu 9216 channel-group 14 mode active no shutdown interface Ethernet4/41 description <<** VPC Peer k02-fp-sw-b:4/41 **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 10,20,32,71,98-99,200-209,211-219 switchport trunk allowed vlan add 300-319,400-419,666,2001-2135,3001-3135 switchport trunk allowed vlan add 3170-3177,3250-3251,3253-3255 channel-group 10 mode active no shutdown interface Ethernet4/42 interface Ethernet4/43 description <<** VPC Peer k02-fp-sw-b:4/43 **>> switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 10,20,32,71,98-99,200-209,211-219 switchport trunk allowed vlan add 300-319,400-419,666,2001-2135,3001-3135 switchport trunk allowed vlan add 3170-3177,3250-3251,3253-3255 channel-group 10 mode active no shutdown interface Ethernet4/44 description <<** IB-Mgmt:mgmt-sw **>> switchport access vlan 3175 channel-group 9 mode active no shutdown interface Ethernet4/45 description eth 4/45 to r9-5548-b eth 1/17 switchport mode trunk switchport trunk allowed vlan 666 no shutdown 54 Appendix B—Device Configurations interface Ethernet4/46 interface Ethernet4/47 switchport mode trunk switchport monitor channel-group 8 no shutdown interface Ethernet4/48 switchport mode trunk switchport monitor channel-group 8 no shutdown interface mgmt0 ip address 172.26.164.182/24 logging monitor 6 line vty ip radius source-interface mgmt0 monitor session 1 type erspan-source erspan-id 1 vrf default destination ip 172.26.164.167 source interface port-channel20 both monitor session 2 description SPAN ASA Data Traffic from Po20 source interface port-channel20 rx destination interface port-channel8 no shut monitor session 3 type erspan-source erspan-id 3 vrf default destination ip 172.26.164.167 source vlan 2001 both Nexus 1Kv !Command: show running-config !Time: Tue Feb 18 14:37:46 2014 version 4.2(1)SV2(2.1a) svs switch edition advanced no feature telnet feature private-vlan feature netflow feature cts feature segmentation segment mode unicast-only segment distribution mac feature vtracker logging level radius 6 username admin password 5 <removed> role network-admin banner motd #Nexus 1000v Switch# ssh key rsa 2048 ip domain-lookup ip domain-name corp.sea9.com ip domain-name corp.sea9.com use-vrf management 55 Appendix B—Device Configurations ip name-server 172.26.164.190 use-vrf management ip host sea-vsm1 172.26.164.186 radius-server key 7 <removed> ip radius source-interface mgmt0 radius-server host 172.26.164.187 key 7 <removed> authentication accounting radius-server host 172.26.164.239 key 7 <removed> authentication accounting aaa group server radius aaa-private-sg aaa group server radius ISE-Radius-Grp server 172.26.164.187 server 172.26.164.239 use-vrf management source-interface mgmt0 hostname sea-vsm1 errdisable recovery cause failed-port-state vem 3 host id 6bd69d26-eeff-8f4d-9127-9d3eccad32d7 vem 4 host id e1166bcf-4fc8-b34b-bdcc-2f1ded6bb532 vem 9 host id fb302753-a797-e146-a7cc-6e21df2debc1 vem 10 host id 7836efbb-6907-2144-b5e5-4e5d009bb234 snmp-server user admin network-admin auth md5 <removed> priv <removed> localizedkey snmp-server community private group network-admin ntp server 172.26.164.254 use-vrf management ntp source 172.26.164.186 aaa authentication login default group ISE-Radius-Grp aaa authentication cts default group ISE-Radius-Grp aaa authorization cts default group ISE-Radius-Grp aaa accounting default group ISE-Radius-Grp no aaa user default-role aaa authentication login error-enable vrf context management ip route 0.0.0.0/0 172.26.164.1 flow exporter sea-lancope-fc1 description <<** SEA Lancope Flow Collector **>> destination 172.26.164.240 use-vrf management transport udp 2055 source mgmt0 version 9 option exporter-stats timeout 300 option interface-table timeout 300 flow monitor sea-enclaves record netflow-original exporter sea-lancope-fc1 timeout inactive 15 timeout active 60 vlan 1-2,98-99,666,3170-3173,3175-3177,3250 vlan 2 name Native-VLAN vlan 98 name ServiceHAVlan vlan 99 name ServiceVlan vlan 666 name WAN-on7k vlan 3170 name NFS-VLAN vlan 3171 name core-services-primary private-vlan primary private-vlan association 3172 vlan 3172 56 Appendix B—Device Configurations name core-services-isolated private-vlan isolated vlan 3173 name vMotion-VLAN vlan 3175 name IB-MGMT-VLAN vlan 3177 name VXLAN_Encapsulation vlan 3250 name prod-ib-mgmt port-channel load-balance ethernet source-dest-ip-port-vlan port-profile default max-ports 32 port-profile default port-binding static port-profile type ethernet Unused_Or_Quarantine_Uplink vmware port-group shutdown description Port-group created for Nexus1000V internal usage. Do not use. state enabled port-profile type vethernet Unused_Or_Quarantine_Veth vmware port-group shutdown description Port-group created for Nexus1000V internal usage. Do not use. state enabled port-profile type ethernet system-uplink vmware port-group switchport mode trunk switchport trunk native vlan 2 switchport trunk allowed vlan 98-99,666,3170-3173,3175-3179,3250 system mtu 9000 channel-group auto mode on mac-pinning no shutdown system vlan 3170,3173,3175-3176,3250 state enabled port-profile type vethernet NFS-VLAN vmware port-group switchport mode access switchport access vlan 3170 no shutdown system vlan 3170 state enabled port-profile type vethernet IB-MGMT-VLAN vmware port-group switchport mode access switchport access vlan 3175 no shutdown system vlan 3175 state enabled port-profile type vethernet vMotion-VLAN vmware port-group switchport mode access switchport access vlan 3173 no shutdown system vlan 3173 state enabled port-profile type vethernet VM-Trafic-VLAN vmware port-group switchport mode access no shutdown state enabled port-profile type vethernet n1kv-L3 capability l3control vmware port-group switchport mode access 57 Appendix B—Device Configurations switchport access vlan 3175 no shutdown system vlan 3175 state enabled port-profile type vethernet WAN-on7k vmware port-group switchport mode access switchport access vlan 666 no shutdown system vlan 666 state enabled port-profile type vethernet VXLAN_Encapsulation vmware port-group switchport mode access switchport access vlan 3177 capability vxlan no shutdown state enabled port-profile type vethernet HA-Srvc vmware port-group switchport mode access switchport access vlan 98 no shutdown state enabled port-profile type vethernet vPath-Srvc vmware port-group switchport mode access switchport access vlan 99 no shutdown state enabled port-profile type vethernet PROD-IB-MGMT vmware port-group switchport mode access switchport access vlan 3250 no shutdown system vlan 3250 state enabled port-profile type vethernet core_services vmware port-group switchport mode private-vlan promiscuous switchport access vlan 3171 switchport private-vlan mapping 3171 3172 ip flow monitor sea-enclaves input no shutdown state enabled system storage-loss log time 30 vdc sea-vsm1 id 1 limit-resource vlan minimum 16 maximum 2049 limit-resource monitor-session minimum 0 maximum 2 limit-resource vrf minimum 16 maximum 8192 limit-resource port-channel minimum 0 maximum 768 limit-resource u4route-mem minimum 1 maximum 1 limit-resource u6route-mem minimum 1 maximum 1 cts device tracking cts interface delete-hold 60 cts sxp enable cts sxp default password 7 <removed> cts sxp default source-ip 172.26.164.186 cts sxp connection peer 172.26.164.217 password default mode listener vrf management cts sxp connection peer 172.26.164.218 password default mode listener vrf management interface port-channel1 58 Appendix B—Device Configurations inherit port-profile system-uplink vem 3 mtu 9000 interface port-channel2 inherit port-profile system-uplink vem 4 mtu 9000 interface port-channel7 inherit port-profile system-uplink vem 9 mtu 9000 interface port-channel8 inherit port-profile system-uplink vem 10 mtu 9000 interface mgmt0 ip address 172.26.164.186/24 interface Vethernet1 inherit port-profile core_services description sea-cs1, Network Adapter 1 vmware dvport 897 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.7F79 interface Vethernet2 inherit port-profile PROD-IB-MGMT description VMware VMkernel, vmk5 vmware dvport 866 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5664.103F interface Vethernet3 inherit port-profile PROD-IB-MGMT description VMware VMkernel, vmk5 vmware dvport 867 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5665.A497 interface Vethernet4 inherit port-profile IB-MGMT-VLAN description sea-cs1, Network Adapter 2 vmware dvport 78 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.34A7 interface Vethernet5 inherit port-profile IB-MGMT-VLAN description win2kr2-enterprise, Network Adapter 1 vmware dvport 79 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.7F34 interface Vethernet6 inherit port-profile core_services description sea-ad1, Network Adapter 3 vmware dvport 898 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.0ED1 interface Vethernet7 inherit port-profile IB-MGMT-VLAN description sea-ad1, Network Adapter 1 vmware dvport 64 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 000C.29E6.37E9 59 Appendix B—Device Configurations interface Vethernet8 inherit port-profile IB-MGMT-VLAN description sea-sql1, Network Adapter 1 vmware dvport 65 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 000C.29B6.1C11 interface Vethernet9 inherit port-profile IB-MGMT-VLAN description sea-vc1, Network Adapter 1 vmware dvport 66 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 000C.2997.C690 interface Vethernet10 inherit port-profile IB-MGMT-VLAN description sea-csm1, Network Adapter 1 vmware dvport 67 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 000C.292E.9471 interface Vethernet11 inherit port-profile VM-Trafic-VLAN description W2K8R2X64GPT-VM, Network Adapter 1 vmware dvport 130 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.6D3E interface Vethernet12 inherit port-profile IB-MGMT-VLAN description sea-ise1, Network Adapter 1 vmware dvport 69 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.6C4D interface Vethernet13 inherit port-profile IB-MGMT-VLAN description sea-n1kvsg-1, Network Adapter 2 vmware dvport 75 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.6EE4 interface Vethernet14 inherit port-profile IB-MGMT-VLAN description sea-vsc-oc, Network Adapter 1 vmware dvport 70 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.050E interface Vethernet15 inherit port-profile PROD-IB-MGMT description sea-pnsc1, Network Adapter 1 vmware dvport 871 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.75AA interface Vethernet16 inherit port-profile IB-MGMT-VLAN description sea-ocb, Network Adapter 1 vmware dvport 72 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.738B interface Vethernet17 inherit port-profile IB-MGMT-VLAN description sea-ocb-proxy, Network Adapter 1 vmware dvport 73 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.04A8 interface Vethernet18 inherit port-profile HA-Srvc description sea-n1kvsg-1, Network Adapter 3 vmware dvport 416 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" 60 Appendix B—Device Configurations vmware vm mac 0050.56AD.704E interface Vethernet19 inherit port-profile IB-MGMT-VLAN description sea-lancope-fc1, Network Adapter 1 vmware dvport 74 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.1DB3 interface Vethernet20 inherit port-profile IB-MGMT-VLAN description sea-ise2, Network Adapter 1 vmware dvport 76 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.314E interface Vethernet21 inherit port-profile IB-MGMT-VLAN description sea-splunk1, Network Adapter 1 vmware dvport 77 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.2DC7 interface Vethernet22 inherit port-profile n1kv-L3 description VMware VMkernel, vmk0 vmware dvport 167 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 5478.1A87.1BA6 interface Vethernet23 inherit port-profile PROD-IB-MGMT description sea-lancope-fc2, Network Adapter 1 vmware dvport 868 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.5E02 interface Vethernet24 inherit port-profile core_services description sea-app1, Network Adapter 1 vmware dvport 899 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.18DB interface Vethernet25 inherit port-profile core_services description sea-client1, Network Adapter 1 vmware dvport 900 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.55C6 interface Vethernet26 inherit port-profile IB-MGMT-VLAN description sea-inet1, Network Adapter 1 vmware dvport 85 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.3807 interface Vethernet27 inherit port-profile IB-MGMT-VLAN description app-1, Network Adapter 1 vmware dvport 82 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.74F1 interface Vethernet28 inherit port-profile IB-MGMT-VLAN description sea-lancope-smc1, Network Adapter 1 vmware dvport 80 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.4F2A interface Vethernet29 inherit port-profile vPath-Srvc 61 Appendix B—Device Configurations description sea-n1kvsg-1, Network Adapter 1 vmware dvport 448 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.6DDC interface Vethernet30 inherit port-profile IB-MGMT-VLAN description sea-n1kvsg-2, Network Adapter 2 vmware dvport 81 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.683C interface Vethernet31 inherit port-profile HA-Srvc description sea-n1kvsg-2, Network Adapter 3 vmware dvport 417 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.16CF interface Vethernet32 inherit port-profile vPath-Srvc description sea-n1kvsg-2, Network Adapter 1 vmware dvport 449 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.4E1C interface Vethernet33 inherit port-profile core_services description sea-splunk1, Network Adapter 2 vmware dvport 896 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.15C8 interface Vethernet34 inherit port-profile IB-MGMT-VLAN description sea-SpirentATC1, Network Adapter 1 vmware dvport 83 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.1EEA interface Vethernet35 inherit port-profile WAN-on7k description sea-SpirentATC1, Network Adapter 2 vmware dvport 514 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.5E1F interface Vethernet36 inherit port-profile IB-MGMT-VLAN description CUCSD-4.1.0.0, Network Adapter 1 vmware dvport 84 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.6F90 interface Vethernet37 inherit port-profile IB-MGMT-VLAN description sea-lancope-fc2, Network Adapter 2 vmware dvport 88 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.5E26 interface Vethernet38 inherit port-profile IB-MGMT-VLAN description sea-ucsd-BMA, Network Adapter 1 vmware dvport 86 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.0975 interface Vethernet39 inherit port-profile IB-MGMT-VLAN description sea-SpirentClient, Network Adapter 1 vmware dvport 87 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.63FF 62 Appendix B—Device Configurations interface Vethernet40 inherit port-profile PROD-IB-MGMT description sea-SpirentClient, Network Adapter 2 vmware dvport 869 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.4AEB interface Vethernet41 inherit port-profile IB-MGMT-VLAN description sea-ocum, Network Adapter 1 vmware dvport 89 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.0C5B interface Vethernet42 inherit port-profile n1kv-L3 description VMware VMkernel, vmk0 vmware dvport 160 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac A80C.0DDC.65D3 interface Vethernet43 inherit port-profile n1kv-L3 description VMware VMkernel, vmk0 vmware dvport 161 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac A80C.0DDC.7609 interface Vethernet44 inherit port-profile NFS-VLAN description VMware VMkernel, vmk1 vmware dvport 32 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5662.BE8C interface Vethernet45 inherit port-profile vMotion-VLAN description VMware VMkernel, vmk2 vmware dvport 100 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5661.361E interface Vethernet46 inherit port-profile VXLAN_Encapsulation description VMware VMkernel, vmk3 vmware dvport 288 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5661.12D9 interface Vethernet47 inherit port-profile VXLAN_Encapsulation description VMware VMkernel, vmk4 vmware dvport 289 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5660.B6DD interface Vethernet48 inherit port-profile NFS-VLAN description VMware VMkernel, vmk1 vmware dvport 33 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.566D.DE42 interface Vethernet49 inherit port-profile vMotion-VLAN description VMware VMkernel, vmk2 vmware dvport 101 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.566D.098D interface Vethernet50 inherit port-profile VXLAN_Encapsulation description VMware VMkernel, vmk3 vmware dvport 290 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" 63 Appendix B—Device Configurations vmware vm mac 0050.5665.FEFC interface Vethernet51 inherit port-profile VXLAN_Encapsulation description VMware VMkernel, vmk4 vmware dvport 291 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5663.370B interface Vethernet52 inherit port-profile n1kv-L3 description VMware VMkernel, vmk0 vmware dvport 169 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 5478.1A87.31D7 interface Vethernet53 inherit port-profile NFS-VLAN description VMware VMkernel, vmk1 vmware dvport 34 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5669.F2F9 interface Vethernet54 inherit port-profile vMotion-VLAN description VMware VMkernel, vmk2 vmware dvport 102 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5662.7871 interface Vethernet55 inherit port-profile VXLAN_Encapsulation description VMware VMkernel, vmk3 vmware dvport 292 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.566F.A14D interface Vethernet56 inherit port-profile VXLAN_Encapsulation description VMware VMkernel, vmk4 vmware dvport 293 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5663.2EE7 interface Vethernet57 inherit port-profile NFS-VLAN description VMware VMkernel, vmk1 vmware dvport 35 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5666.5098 interface Vethernet58 inherit port-profile vMotion-VLAN description VMware VMkernel, vmk2 vmware dvport 103 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.5666.03F8 interface Vethernet59 inherit port-profile VXLAN_Encapsulation description VMware VMkernel, vmk3 vmware dvport 294 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.566B.4BC1 interface Vethernet60 inherit port-profile VXLAN_Encapsulation description VMware VMkernel, vmk4 vmware dvport 295 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.566E.41A8 interface Vethernet61 inherit port-profile PROD-IB-MGMT 64 Appendix B—Device Configurations description sea-vc1, Network Adapter 2 vmware dvport 865 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.6ED1 interface Vethernet62 inherit port-profile PROD-IB-MGMT description sea-ad1, Network Adapter 2 vmware dvport 864 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.1CEF interface Vethernet63 inherit port-profile PROD-IB-MGMT description sea-cs1, Network Adapter 3 vmware dvport 870 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.26AA interface Vethernet64 inherit port-profile PROD-IB-MGMT description sea-vpxmgr, Network Adapter 2 vmware dvport 872 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.51BA interface Vethernet65 inherit port-profile core_services description sea-vpxmgr, Network Adapter 1 vmware dvport 901 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.5AAB interface Vethernet66 inherit port-profile IB-MGMT-VLAN description sea-vpxmgr, Network Adapter 3 vmware dvport 71 dvswitch uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" vmware vm mac 0050.56AD.1566 interface Ethernet3/5 inherit port-profile system-uplink interface Ethernet4/5 inherit port-profile system-uplink interface Ethernet9/5 inherit port-profile system-uplink interface Ethernet10/5 inherit port-profile system-uplink interface control0 ip address 192.168.250.186/24 clock timezone EST -5 0 line console boot kickstart bootflash:/nexus-1000v-kickstart.4.2.1.SV2.2.1a.bin sup-1 boot system bootflash:/nexus-1000v.4.2.1.SV2.2.1a.bin sup-1 boot kickstart bootflash:/nexus-1000v-kickstart.4.2.1.SV2.2.1a.bin sup-2 boot system bootflash:/nexus-1000v.4.2.1.SV2.2.1a.bin sup-2 ip route 10.71.1.182/32 172.26.164.218 ip route 10.71.1.183/32 172.26.164.217 monitor session 1 type erspan-source source interface Vethernet19 tx destination ip 172.26.164.167 erspan-id 1 ip ttl 64 ip prec 0 ip dscp 0 mtu 1500 65 Appendix B—Device Configurations header-type 2 monitor session 2 type erspan-source destination ip 172.26.164.167 erspan-id 2 ip ttl 64 ip prec 0 ip dscp 0 mtu 1500 header-type 2 no shut svs-domain domain id 101 control vlan 3176 packet vlan 3176 svs mode L3 interface mgmt0 svs connection vCenter protocol vmware-vim remote ip address 172.26.164.200 port 80 vmware dvs uuid "ba 86 2d 50 14 7b 59 7a-59 b7 87 d2 f3 59 d8 24" datacenter-name FlexPod_DC_1 max-ports 8192 connect vservice global type vsg tcp state-checks invalid-ack tcp state-checks seq-past-window no tcp state-checks window-variation no bypass asa-traffic vservice node sea-vsg1 type vsg ip address 172.26.164.168 adjacency l2 vlan 99 fail-mode close vnm-policy-agent registration-ip 192.168.250.250 shared-secret ********** policy-agent-image bootflash:/vnmc-vsmpa.2.1.1b.bin log-level info sea-vsm1# 66 Appendix C—About the Cisco Validated Design Program Appendix C—About the Cisco Validated Design Program The CVD program consists of systems and solutions designed, tested, and documented to facilitate faster, more reliable, and more predictable customer deployments. For more information, visit http://www.cisco.com/go/designzone. ALL DESIGNS, SPECIFICATIONS, STATEMENTS, INFORMATION, AND RECOMMENDATIONS (COLLECTIVELY, “DESIGNS”) IN THIS MANUAL ARE PRESENTED “AS IS,” WITH ALL FAULTS. CISCO AND ITS SUPPLIERS DISCLAIM ALL WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THE DESIGNS, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THE DESIGNS ARE SUBJECT TO CHANGE WITHOUT NOTICE. USERS ARE SOLELY RESPONSIBLE FOR THEIR APPLICATION OF THE DESIGNS. THE DESIGNS DO NOT CONSTITUTE THE TECHNICAL OR OTHER PROFESSIONAL ADVICE OF CISCO, ITS SUPPLIERS OR PARTNERS. USERS SHOULD CONSULT THEIR OWN TECHNICAL ADVISORS BEFORE IMPLEMENTING THE DESIGNS. RESULTS MAY VARY DEPENDING ON FACTORS NOT TESTED BY CISCO. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at http://www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1005R) Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental. 67 Appendix C—About the Cisco Validated Design Program 68