Procedure
advertisement
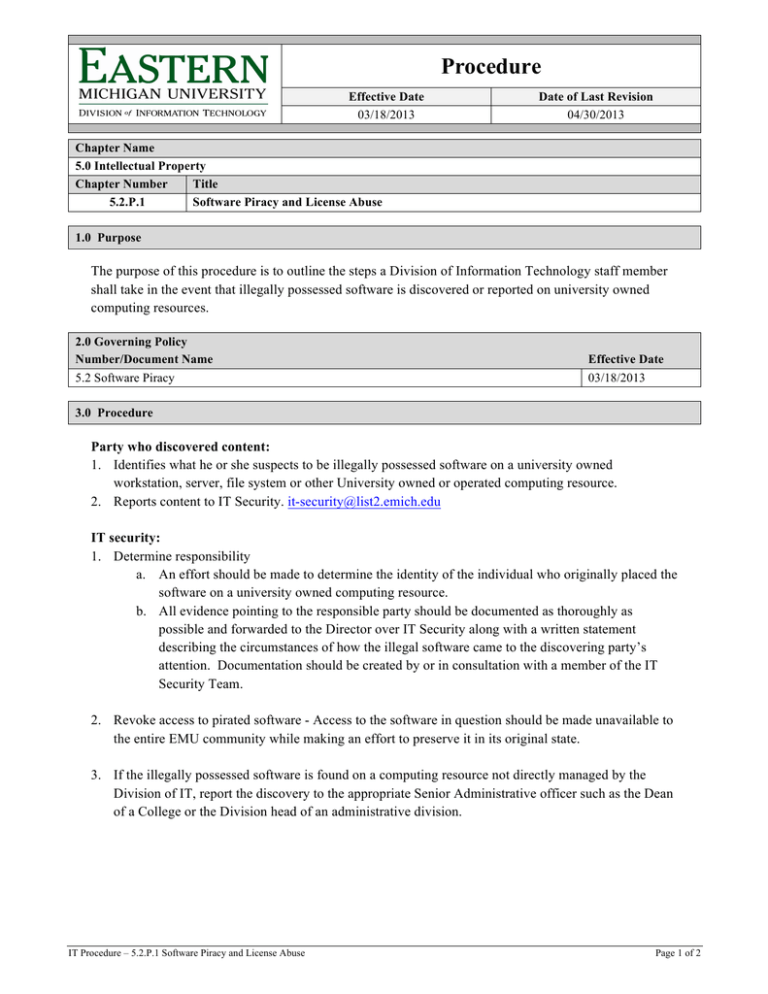
Procedure Effective Date 03/18/2013 Date of Last Revision 04/30/2013 Chapter Name 5.0 Intellectual Property Chapter Number Title 5.2.P.1 Software Piracy and License Abuse 1.0 Purpose The purpose of this procedure is to outline the steps a Division of Information Technology staff member shall take in the event that illegally possessed software is discovered or reported on university owned computing resources. 2.0 Governing Policy Number/Document Name 5.2 Software Piracy Effective Date 03/18/2013 3.0 Procedure Party who discovered content: 1. Identifies what he or she suspects to be illegally possessed software on a university owned workstation, server, file system or other University owned or operated computing resource. 2. Reports content to IT Security. it-security@list2.emich.edu IT security: 1. Determine responsibility a. An effort should be made to determine the identity of the individual who originally placed the software on a university owned computing resource. b. All evidence pointing to the responsible party should be documented as thoroughly as possible and forwarded to the Director over IT Security along with a written statement describing the circumstances of how the illegal software came to the discovering party’s attention. Documentation should be created by or in consultation with a member of the IT Security Team. 2. Revoke access to pirated software - Access to the software in question should be made unavailable to the entire EMU community while making an effort to preserve it in its original state. 3. If the illegally possessed software is found on a computing resource not directly managed by the Division of IT, report the discovery to the appropriate Senior Administrative officer such as the Dean of a College or the Division head of an administrative division. IT Procedure – 5.2.P.1 Software Piracy and License Abuse Page 1 of 2 Director in charge of IT security or a designee: 1. Reports the illegal software to the Office of Student Conduct and Community Standards or Human Resources as appropriate and provides copies of all evidentiary materials. 2. Reports the illegal software to University Police and provides copies of all evidentiary materials. 3. Once the investigation has concluded, the illegally possessed software should be completely removed from the EMU owned computing resources. 4.0 Responsibility for Implementation The Director of Network and Systems Services is responsible for the implementation of this procedure. 5.0 Definitions Term Illegally Possessed Software or Pirated Software Definition Any software, protected under copyright law, that is copied, distributed, modified, or sold without proper licensing, thereby denying the copyright holder due compensation for their creative works. 6.0 Revision History Description Approval Date Original 03/11/2013 Approved by CIO 04/30/2013 IT Procedure – 5.2.P.1 Software Piracy and License Abuse Page 2 of 2