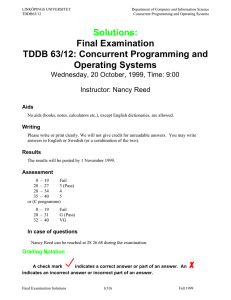
Final Examination TDDB 12/63: Concurrent Programming and Operating Systems
advertisement

Concurrent Programming and Operating Systems
TDDB12/63
Final Examination
TDDB 12/63: Concurrent Programming and
Operating Systems
Friday, 2 June 2000, Time: 14:00
Instructor: Nancy Reed
Aids
No aids (books, notes, calculators etc.), except English/Swedish dictionaries are allowed.
Writing
Please write or print clearly. We will not give credit for unreadable answers.
You may write answers in English or Swedish (or a combination of the two).
Show your solution method. You will not get full credit for just an answer.
Results
The results will be posted by 19 June, 2000.
In case of questions
Prof. Reed can be reached at 28 26 68 during the examination.
LINKÖPINGS UNIVERSITET
1(4)
Department of Computer and Information Science
Concurrent Programming and Operating Systems
TDDB12/63
1. Operating System Structures (4 p)
a) Define the term multiprogramming (in detail). (1 p)
b) What are caches and when are they useful? Explain. (1 p)
c) Name and describe three hardware aids that are essential when writing an operating system to achieve
protection from malicious or buggy programs. What type of protection does each type of hardware
provide in the OS? (2 p)
2. Processes and threads (4 p)
a) Describe exactly what happens during a context switch, including all data structures and any effects on
the TLB (if present). (2 p)
b) What does the term co-operating processes mean? Explain. Are peer threads co-operating in this way?
(2 p)
3. CPU Scheduling (6 p)
Consider the following set of processes with arrival times and CPU execution times given in milliseconds. A
process with a larger priority number has a higher priority. State any assumptions that you make.
a) Draw and label Gantt charts (with process numbers and times) for execution using:
i) RR scheduling with a time quantum of 5 msec. (1 p)
ii) Immediately preemptive SJF scheduling. (1 p)
iii) Immediately preemptive priority (use SRTF for equal priorities). (1 p)
iv) Priority scheduling (non-immediately preemptive) with a time quantum of 6 msec. (1 p)
Process
P1
P2
P3
P4
P5
Arrival time
0
0
6
7
15
Execution time
11
16
7
13
19
Priority
3
5
5
2
3
b) Calculate the average waiting times for schedules i and ii above, ignoring priority values. Which method
gives a better waiting time for this data? (1 p)
c) For schedules iii and iv above, use each job’s priority as its weight and calculate the weighted average
waiting time. Which method gives better weighted average performance for this data? (1 p)
LINKÖPINGS UNIVERSITET
2(4)
Department of Computer and Information Science
Concurrent Programming and Operating Systems
TDDB12/63
4. Synchronization (6 p)
a) Define what a critical section is and explain at least two techniques used to solve synchronization
problems in critical sections. Hint: think of how you handled synchronization in NACHOS. (2 p)
b) Describe the dining philosophers problem. Write C++, Pascal or pseudo-code to implement a solution
to the problem that is (must be) free from deadlock (explain how they are avoided). If your solution is
also free from starvation, you can receive two extra points (explain how). (4 or 6 p)
5. Deadlocks (6 p)
a) A resource allocation grid shows illegal, safe, and unsafe states for a sequence of requests (REQ) and
releases (REL) of resources for 2 processes. Draw a resource allocation grid like the one below and
identify the illegal (forbidden), safe, and unsafe states (assume the Banker’s algorithm is used) for 2
processes, P1 and P2, with the following list of requests. All resources are non-shareable. State any
assumptions you make. (3 p)
Note: REQ can be represented by + and REL by -.
P1: REQ{b,c}, REL{b}, REQ{a}, REQ{d}, REL{a,c,d}
P2: REQ{b,e} REL{b}, REQ{d}, REQ{c}, REL{c,d,e}
P2
4
3
2
1
+{b,e}
P1
+{b,c}
b) Justify how and why you determined the states of squares 1, 2, 3 and 4. (3 p)
LINKÖPINGS UNIVERSITET
3(4)
Department of Computer and Information Science
Concurrent Programming and Operating Systems
TDDB12/63
6. Virtual Memory (6 p)
a) Generate the reference string for the following sequence of page requests. (1 p)
1 2 5 5 7 4 1 3 3 3 2 7 3 1 2 2 6 7 3
b) Show the sequence of pages put into frames in main memory for the reference string above using each
algorithm specified below. How many page faults are there for each algorithm? (4 p)
i. Using 3 available frames and the OPT algorithm.
ii. Using 4 available frames and the FIFO algorithm.
iii. Using 5 available frames and the OPT algorithm.
iv. Using 6 available frames and the LRU algorithm.
Show the page numbers in the exact frames. For example, 3 frames looks like this:
………
c) What is the absolute minumum number of page faults necessary to process the reference string above?
Describe how you calculated your answer. (1 p)
7. File Systems (6 p)
a) Describe and justify at least three major advantages of distributed file systems (compared to nondistributed file systems). (2 p)
b) Describe at least two potential problems that affect distributed file systems (compared to nondistributed file systems). (1 p)
c) Consider a file currently consisting of 111 blocks of information. Assume that the file control block
(and index block, in the case of indexed allocation) is already in memory. Calculate the number of disk
I/O operations required for contiguous, linked, and indexed allocation strategies to make the following
changes to the file. In the contiguous case, you may assume there is no space to grow at the beginning,
but there is room to grow at the end. Assume that the new information to be added to the file is already
available in memory. (3 p)
Put your answers into table form in the following format, x Read + y Write = z (total) I/O:
Disk I/O operations Contiguous allocation
i)add 1 block in the 17th __R + __ W = __
position
ii)add 2 blocks before the __ R + __ W = __
current last block
iii) remove the middle block __ R + __ W = __
Linked allocation
Indexed allocation
__ R + __ W = __
__ R + __ W = __
__ R + __ W = __
__ R + __ W = __
__ R + __ W = __
__ R + __ W = __
8. Protection and security (2 p)
a) Describe the concept of a computer hacker as the term was used in the 1980s and as the term is used
today. Which definition do you prefer? (1 p)
b) Each computer virus is limited to one type of operating system, True or False. Justify your answer. (1 p)
LINKÖPINGS UNIVERSITET
4(4)
Department of Computer and Information Science