Malicious Software A Technical B Breakdown
advertisement

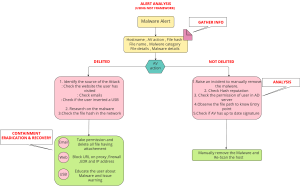
Malicious Software A Technical B Breakdown Josh Mc cCune Network Secu urity Analyst mccunej@ksu.edu Overrview • • • • • Types of Malware How does it get there? ? How do we find it? How do we analyze it? ? How do we contain it? Malware Definitions D • Spyware S o o o Gathers information for advertisement a purposes Sometimes called adwarre Created by businesses th hat want to know their customers' browsing hab customers bits Malware Definitions D • Viruses / Worms Self-replicating applications o Created by malicious programmers for a varietty of nefarious purposes o Malware Definitions D • Remote Access Trojans o o Server app plications that operate covertly Created byy malicious programmers to give them a means to get back in to a system oncce compromised Malware Definitions D • Rootkits Hard to detect Created by programmerss with advanced knowledg ge of system internals o Known to run for years unnoticed o o Attack Vectors V • Email & attachments • Deception (Social Engin neering) • Web Pages • Malicious Scripts • Counterfeit Websites • Browser vulnerabilities (drive e-by exploits) • • • • Scareware Worms Instant Messaging P2P File Sharing Netwo orks Common Malw ware Activities • S Spam • Denial of Service Attacks s • Information I f ti Stealing St li • Account Numbers • Credentials • Keyloggers • • • • Network scanning Infect Peers Illegal P2P file distributio on Pop-up advertisements Useful Ana alysis Tools • Virustotal • http://virusustotal.com • Sandbox Applications • • • • Anubis - http://anubis.iseclab.org/ Joebox - http://joebox.org/ CWSandbox - http://cwsandb box.org/ ThreatExpert – http://threatexpert.com/ • Deobfuscators • Wepawet – http://wepawet.ise eclab.org/ JJavascript i tD bfuscation ti Example E l Deobfu Infection Symptoms S • • • • • • Slow system performa ance Home page hijacking Excessive pop-up pop up adss Crashes Some websites don't don t work w (Antivirus sites) Unexplained hard driv ve activity Containment • Remove the system from f m the network • If the system contains se ensitive data, STOP! o Call C ll your IInformation f ti S Security it Offi Officer • Back-up critical data to external e storage • Reformat R f t Hard H dD Drive i • Reinstall Operating Syste em Malware Demonstration