Document 12915566
advertisement

International Journal of Engineering Trends and Technology (IJETT) – Volume 28 Number 2 - October 2015
A Comprehensive and Comparative Study of Maze-Solving
Techniques by implementing Graph Theory- implementation
of Djikstra’s algorithm for solving a maze
Monika Tak (10BCE0313), SoumyadeepDatta (10BCE0334)
School of Computing Science and Engineering
Vellore Institute of Technology,
Vellore, Tamil Nadu, India
Abstract: Maze solving has become an interesting
activity for a lot of people in recent times. This has
become so advanced that there are robots also doing
the same these days. But there is a difference that we
talk about in this paper. Humans have the time and
patience to solve using graph theory techniques as
well as non-graph theory techniques. But robots on
the other hand need an algorithm to solve the maze
i.e. they use the graph theory algorithms. In the
following paper we will see the various maze solving
techniques with the application of graph theory along
with the implementation of djikstra’s algorithm.
II.
GRAPH THEORY AND ALGORITHMS
The various techniques for solving the mazes
have been shown in the section beneath.
A. Depth First Search
We convert the maze into its corresponding matrix
marking the nodes or vertices with black and white
accordingly. Then we start from the root and travel to
the end of the stack. After traversing to the end if we
reach the destination node then we end the algorithm
then and there.
Keywords—Djikstra, maze, wallflower, breadth first
search.
I.
INTRODUCTION
Mazes have become more complicated in the recent
times. Unlike the days where a simple viewing of the
maze was enough to solve them, they have too
evolved along with their solving techniques. Today
the basic techniques of maze solving either fail or
take a lot of time to be solved. Just using the
wallflower technique isn’t enough anymore. The
mazes being created today are much more complex
than they used to be for such simple techniques. The
difficultyof the mazes have evolved to such a level
where humans have started createdrobots andfeeding
them algorithms of graph theory to solve them.
The mazes considered in this paper are 3D mazes
which are solved using graph theory techniques. The
mazes are first converted into matrices of sizes 8X8
or 16X16 or 32X32 depending on the size of the
maze. For the algorithms to work the size of the
matrix has to be a minimum of 8X8.
The various graph theory techniques for finding the
solution to these mazes are:
Depth First Search
Floodfill
Algorithm
or
Bellmann’s
Algorithm
Breadth First Search
In the paper we will discuss the different techniques
these algorithms use to solve the mazes and display a
table of findings of the times that these algorithms
took to solving the same maze.
Fig. 1Depth First Search
ISSN: 2231-5381
http://www.ijettjournal.org
Page 61
International Journal of Engineering Trends and Technology (IJETT) – Volume 28 Number 2 - October 2015
If we don’t reach the destination node then we
backtrack and then apply the algorithm again. In this
manner we keep solving the maze and then finally
come up with a path to be taken by the user to solve
the maze.
B. Floodfill Algorithm or Bellmann’s Algorithm
This algorithm is a specialized version of the Depth
First Search. Here the vertices are marked with
distance values where the destination vertex holds the
distance value of 0(zero). The starting node holds
some value and it has to reach the destination
vertex using the algorithm.
Yes ->Do nothing
}
We start solving the maze by finding the
nodes/vertices connected to it and then keep
traversing them in the order that the least distance is
taken into account to reach the destination vertex.
C. Breadth First Search
This algorithm uses the technique of Uniform Cost
Search. Unlike the floodfill algorithm where we mark
the destination vertex as the vertex with distance
equal to 0(zero), here we mark the start vertex as the
one with the distance equal to 0(zero). In this
algorithm the user starts from the start vertex and
searches for the adjacent vertices that can be
traversed to reach the destination vertex. The
algorithm for the following technique is:
Fig. 2Floodfill Algorithm
Update Subroutine:
Confirm that the stack is empty and push the current
cell onto the stack. The current cell is the one where
we are standing.
Repeat the instructions given bellow. Iterate it until
stack is empty.
{
Pull a cell from the stack.
Distance value of present cell = 1 + the minimum
value of its open neighbors.
No -> Change the cell to 1 + the minimum value of
its open neighbors and push all of the cell's open
neighbors onto the stack to be checked
ISSN: 2231-5381
Fig. 3.Breadth First Search
III.
NON-GRAPH THEORY TECHNIQUES
The normal technique for the solving a maze before
the applications of these graph theory algorithms was
the wallflower algorithm.
A. Wallflower Technique
This algorithm tells the user to either use the left
wallflower technique or the right wallflower
http://www.ijettjournal.org
Page 62
International Journal of Engineering Trends and Technology (IJETT) – Volume 28 Number 2 - October 2015
technique. This algorithm basically tells the user to
either keep going left if the user follows the left
wallflower algorithm or keep going right if the user
follows the right wallflower algorithm. When the
dead end is arrived at then the user backtracks and
again goes either left or right.
IV.
SIMULATION RESULT, ANALYSIS
and COMPARISON
To find a comparative study of the algorithms there
are 3 mazes given and solved using the graph theory
and the non- graph theory algorithms.
The three mazes are:
On solving the mazes these are the data available
from the experiment. To further study the difference
in the techniques graphs have been constructed to
show the time taken to traverse the maze.
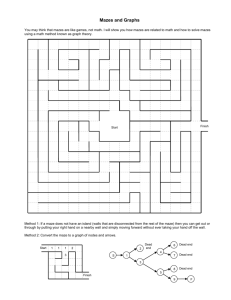
Fig. 4.(a)- Maze 1, (b) - Maze 2, (c) - Maze 3
After solving the three mazes using the algorithms
the results were tabulated and the result is given
below:
TABLE I
Fig 5.Graphical comparison between GT & NGT considering maze
solvingtechniques.
V.
Implementation of Djikstra’s Algorithm
The above maze solving techniques help to find the
paths which can be used to traverse from the start
node to the destination node. When these paths are
constructed then it can be seen that there are multiple
paths that form from the start node to the destination
node. To optimize the solution we use the djikstra’s
algorithm and find the shortest path from the start
node to the destination node, so that all the cost
optimization can be done and then find the final
solution of the maze i.e. the path from the start vertex
to the destination vertex.
ISSN: 2231-5381
http://www.ijettjournal.org
Page 63
International Journal of Engineering Trends and Technology (IJETT) – Volume 28 Number 2 - October 2015
The algorithm for the following technique is:
This algorithm follows the principle of finding out
the shortest distance between two adjacently separate
nodes and then traces the path that is required and
finds the optimal path from the multiple paths that are
formed from the starting node to the destination node.
VI.
CONCLUSIONS
From the analysis we can see that the graph theory
techniques we use to solve the mazes against the nongraph techniques and we see that the graph theory
techniques are faster than the non- graph theory
techniques.
ACKNOWLEDGEMENT
We would like to thank Prof. Selvakumar R Senior
Professor & Controller of Examinations Professor,
School of Advanced Sciences, VIT University for
mentoring us in the research done on this paper.
REFERENCES
[1] Sadik A. M. J, Farid H. M. A. B., Rashid T. U., Syed A., Dhali
M.A. “Performance analysis of micromouse algorithms,” Proc. 25 th
International Technical Conference on Circuits/Systems,
Computers and Communications (ITC-CSCC), Pattaya, Thailand
on 4-7 July, 2010; PID 0242, pp. 544–547.
[2] "Micromouse 2010 Competition Rules." IEEE Region 2
Student Activities Conference 2010 Web Page.Web.21 Nov.
2009.[http://www.temple.edu/students/ieee/SAC/competitions.html
.]I . S. Jacobs and C. P. Bean, “Fine particles, thin films and
exchange anisotropy,” in Magnetism, vol. III, G. T. Rado and H.
Suhl, Eds. New York: Academic, 1963, pp. 271–350.
[3] ManojSharma,“Algorithms for Micro-mouse”, Proc. 2009
International Conference on Future Computer and Communication.
DOI 10.1109/ICFCC.2009.38
[4]J.C.Russ,TheImageProcessingHandbook,ThirdEdition,CRCPres
s,1999.
[5]E.W.Dijkstra,“A Note n Two Problems in Connexion with
Graphs”,NumerischeMathematik,1,pp.269–271,1959.
[6]P.E.Hart,N.J.Nilsson,andB.Raphael,“AFormalBasisfortheHeuris
ticDeterminationofMinimumCostPaths”,IEEETrans.SystemsScienc
eandCy-bernetics,Vol.ssc-4,No.2,pp.100–107,1968.
ISSN: 2231-5381
http://www.ijettjournal.org
Page 64