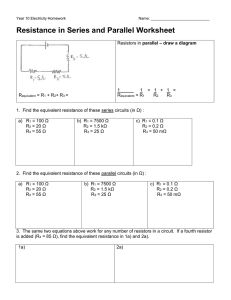
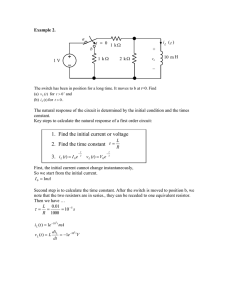
White Paper on Secure Integrated Circuits and Systems Project Name: Investigators:
advertisement

White Paper on Secure Integrated Circuits and Systems Project Name: Investigators: University: Mailing Address: Phone # and E-mail: Circuit Techniques and Methodologies for Trusted Silicon Applications Ioannis Savidis Drexel University Department of Electrical and Computer Engineering Drexel University 3120-40 Market Street, Bossone 313 Philadelphia, Pennsylvania 19104 (215) 571-4584, isavidis@coe.drexel.edu Problem: Integrated circuits (ICs) form the backbone of many electronic devices ranging from smart phones and computers, to the systems that control our banking, energy distribution, and defense infrastructure. The recent emergence of hardware Trojans, or malicious circuits inserted into an IC during the manufacturing process, poses an important new security threat to systems that rely upon ICs. This threat is sufficiently credible that the DARPA TRUST, IRIS, and more recent SHIELD programs were established to initiate research efforts to ensure the trustworthiness of ICs used in military systems. An adversary may alter electronic components and systems for a variety of reasons, including destabilizing system operation and data theft. Recent research has focused on detection of hardware Trojans (HT) [1]-[3]. HT circuits are malicious in nature and produce deliberate changes to the functionality, reliability, and stability of a system. Although much research effort has focused on the detection of hardware Trojans, there is minimal work on circuit techniques and methodologies that 1) maximize the cost of placing HTs by an adversary, and 2) assure secure and stable circuit operation for critical components of an IC after detecting foreign IP (HTs) or circuit manipulation. Methods to combat Trojan insertion and circuit manipulation will be explored. A real-time detection circuit that includes distributed on-chip sensors that monitor multiple side channels (power consumption, substrate noise, thermal profile) will be developed that provides circuit security beyond post-fabrication testing. Once the real-time detection circuits determine that the IC has been compromised, circuit-level countermeasures in response to the presence of a hardware Trojan or a compromised circuit block will be investigated. Finally, techniques to encrypt critical circuit functionality from possible tampering or reverse engineering will be explored. Objective: The primary focus of the proposed work is to prevent and respond to undesired circuit tampering. “encrypting” critical circuit functionality. Novel techniques and circuits are needed to encrypt the function of an IC. Multiple methods to encrypt circuit function will be pursued. A summary of the methods that will be examined to encrypt circuit functionality is provided below. Security Aware Circuit Techniques and Methodologies 1. Real-time IC monitoring: Current methods to detect HTs are performed during post-fabrication testing, and often do not detect dormant hardware Trojans. Sensors that monitor the side-channels of an integrated circuit provide real-time analysis of active circuits in the IC. On-chip voltage, current, and temperature sensors will be integrated directly into an IC, and will provide detailed time-varying measurements of the power supply noise, substrate noise, and temperature across the integrated circuit. These sensors can be placed in critical locations on an IC to deter adversaries from placing hardware Trojans in these locations. In addition, circuit strategies will be developed that intentionally increase the power supply to provide a signature of the power network. By intentionally permitting noise in certain regions of an IC, the voltage fluctuations caused by local circuits is more easily monitored and traces introduced by undesired circuits is more readily observable. This runs contrary to standard design considerations, which prioritize reducing the power supply noise. The use of power supply noise to increase security modifies the general paradigm that noise on the power distribution network negatively impacts the operation of an IC. 2. Provide a lock-and-key: A lock-and-key provides circuit encryption by requiring hardware based authentication. Prior work examined physically unclonable functions (PUFs) that provide hardware identification that a user can authenticate [4], [5]. Although this provides a level of security, the PUF is remotely verified, providing a means to compromise a system. A more robust approach to secure critical circuits is necessary. A mechanism to access critical circuits on an IC through hardware-to-hardware authentication provides an additional level of security. The “locked” circuits on one IC will require a key that is found on a separate IC. 3-D integration is well suited for this type of lock-and-key authentication, where two separately processed integrated circuits are joined to form a single combined system. The added benefit of 3-D ICs regarding circuit encryption is that each separately processed die can be produced by two independent foundries, thereby isolating the “lock” manufacturer from the foundry producing the “key”. Note that 3-D integration provides a set of unique design challenges that the PI will continue to examine as a continuation of prior research efforts on the topic. Preliminary research efforts on proper power delivery and synchronization in 3-D ICs have been completed, and efforts on how to synchronize and deliver power to completely disparate circuit technologies are ongoing. 3. Split functional circuit blocks into sub-blocks: Circuit blocks that perform a targeted function are often located in close proximity of one another. The locality of circuit blocks is of particular importance, as performance (speed and power) is highly dependent on the data path of a signal: Shorter data paths provide higher circuit performance. The data path is therefore an easy target for attack. Critical circuit blocks that are along targeted data paths must be modified to minimize such attack. Intentionally complicating the interconnect (data path) between circuit blocks by increasing the length and providing “false” data paths produces one level of circuit encryption. A more effective approach is to modify both the internal and external interconnects of a circuit block. Functional circuit blocks can be subdivided into smaller sub-blocks and distributed across the IC or between multiple ICs. Although splitting functional blocks into sub-blocks can be implemented in 2-D ICs, placing sub-blocks into two different device planes with 3-D integration adds an additional level of circuit encryption. An additional benefit of placing circuits on two separate device planes is that two different foundries can be used to produce each die, further reducing the risk of hardware Trojans. The cost of increased circuit encryption, however, is an increase in circuit complexity and potentially a degradation in circuit performance. An analysis investigating the trade-offs on circuit speed, power consumption, and area with increasingly smaller sub-blocks is required. In 4. 5. 6. 7. addition, circuit blocks placed on separate device planes will require novel techniques to synchronize and adjust voltage levels between disparate technologies. Clock and data signals will require tunable voltage level shifting circuits to convert between arbitrary voltage levels. Circuits will be developed to synchronize and transmit data between sub-blocks in both 2-D and 3-D IC topologies. Point-to-point signal encryption: On-chip interconnects comprised of critical signals can be encrypted to prevent the theft of sensitive data. Circuits will be developed and inserted into data paths that require encryption of sensitive information. Different encryption algorithms that can be implemented in hardware will be investigated, and a test circuit that implements a subset of the most effective algorithms will be designed, fabricated (through a foundry), and tested. An additional level of data security is possible by placing the encryption circuits on a separate device plane from the functional circuit blocks and fabricating the two device planes with two different foundries. The separate device planes can either be connected via an external bus, or 3-D integrated into a single stacked system. Deactivation of hardware Trojans: Once a malicious circuit is detected through techniques that analyze the power network (or other side-channels) for unexpected noise spikes [1] or increased path delays [2], mechanisms that isolate the malicious component from other functional blocks will be explored and implemented. An integrated circuit can be divided into smaller blocks, each with isolated functionality and design requirements. Sub-dividing an IC into smaller functional units that are disconnected from the power and clock distribution networks once a circuit anomaly is detected reduces the impact of hardware Trojans on other critical circuits that have not been tampered with. Circuits that terminate the operation of sections of an IC provide an additional defense against hardware Trojans. Circuit techniques that sub-divide the IC into self-contained units that can be independently powered on and off will be developed. Methodologies on delivering power and synchronizing the smaller sub-blocks under the assumption that a certain percentage will be inactive due to tampering will also be developed. Mask circuit power consumption and thermal characteristics: The power consumption and heat profile of each circuit block provide a signature of the functional composition of the circuit. One goal is to effectively mask the power consumption of circuit blocks through circuit techniques and methods that prevent hardware Trojans that “snoop” circuit behavior. Techniques such as reducing or increasing the operating frequency or voltage of a circuit block results in variations in the power consumption and thermal profile of the circuit. In addition, on-chip metal layers used for signal propagation can be used to spread heat from a highly active circuit block. The metals used for the power and clock networks can also be used to spread heat. Circuit techniques that throttle the operating speed of a circuit block and methods to distribute heat away from highly active circuits provide a means to mask the functionality of the IC. Clock and power distribution networks for signal transmission: The clock and power distribution networks are typically distributed across the entire integrated circuit. The two interconnect networks provide a means of propagating a signal from one circuit block to another across the entire device plane. Novel circuit techniques similar to resonant clocking will be implemented to transmit a signal from one location and tune a receiver circuit to a particular frequency band to accept the transmitted signal. Transmitting signals on the clock and power network will require unconventional circuit techniques. Methodologies for delivering signals on each network will differ as one behaves like a carrier wave (the clock signal) and the other is a constant DC voltage with noise spurs introduced by circuit activity. The benefits and drawbacks of each will be investigated, and circuits to optimally deliver signals on both will be developed. Novelty: Circuits and methodologies for real-time detection of hardware Trojans or other circuit manipulations will be examined and implemented. Real-time countermeasures that isolate sections of an IC found to contain manipulated circuits or HTs will be developed. In addition, circuit-level techniques that encrypt the functionality of critical circuit blocks will be explored. An analysis of 3-D integration as an approach to further encrypt circuit block functions, secure critical signals, and isolate the fabrication (split fabrication) of circuit components by different foundry partners will be performed. Novel circuits and methodologies that encrypt the functionality of an IC for both 2-D and 3-D IC implementations will be designed and implemented. Circuits that will be developed include sensors to detect thermal, voltage, and current changes across the IC, tunable signal generators to transmit signals on the clock and power networks, hardware implementation of different encryption algorithms, and control circuits that deactivate portions of an IC once a hardware Trojan is detected. Research Output: The goal is to develop circuits and methodologies that detect circuit manipulations, respond to the presence of tampered circuits, and encrypt circuit block functionality. Protocols for signaling, power delivery, and clocking will be developed to encrypt IC functionality. Novel circuits and techniques that detect circuit manipulations in real-time will be developed. In addition, circuits and architecture level techniques to counter the hardware attack will be explored and implemented. The novel circuits, techniques, and methodologies will ensure secure and reliable operation of critical ICs that have been targeted by adversaries. References: [1] R. Rad, J. Plusquellic, and M. Tehranipoor, “A Sensitivity Analysis of Power Signal Methods for Detecting Hardware Trojans Under Real Process and Environmental Conditions,” IEEE Transactions on Very Large Scale Integration (VLSI) Systems, vol. 18, no. 12, pp. 1735-1744, December 2010. [2] C. Lamech and J. Plusquellic, “Trojan Detection based on Delay Variations Measured using a High-Precision, Low-Overhead Embedded Test Structure,” IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), pp. 75-82, June 2012. [3] H. Salmani and M. Tehranipoor, “Layout-Aware Switching Activity Localization to Enhance Hardware Trojan Detection,” IEEE Transactions on Information Forensics and Security, vol. 7, no. 1, pp. 76-87, February 2012. [4] R. Kumar and W. Burleson, “PHAP: Password based Hardware Authentication using PUFs,” IEEE/ACM International Symposium on Microarchitecture Workshops, pp. 24-31, December 2012. [5] F. Koushanfar, “Provably Secure Active IC Metering Techniques for Piracy Avoidance and Digital Rights Management,” IEEE Transactions on Information Forensics and Security, vol. 7, no. 1, pp. 51-63, February 2012.