ITSY 1300 - Learning Activity Plans Learning Activity 1
advertisement

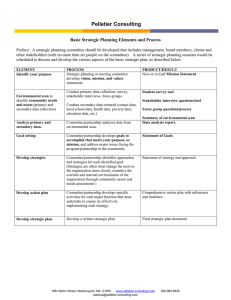
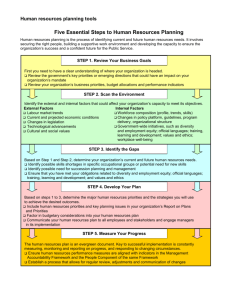
ITSY 1300 - Learning Activity Plans Learning Activity 1 Learning Outcome (Use Legion software to detect and map network shares, and attempt a brute force attack against password protected shares) Students will deploy Legion software on a work station to collect information about potential vulnerabilities within the network. By utilizing Legion the student will be able to identify network shares and map a drive to that share. This allows several things. First, an administrator can check to ensure that, if permitted, shares have adequate password protection. Second, this simple scan allows administrators to detect holes within the network that can be utilized by an intruder to insert/install additional monitoring software on the target computer. Recommended Resources for this Learning Activity Legion Available for download: http://packetstormsecurity.org/groups/rhino9/, Platforms supported: All versions of Windows and Unix. Legion is a NetBIOS scanner which can enumerate NetBIOS file shares across large ranges of IP addresses. Legion also provides a brute force password cracking component which can be directed against a single NetBIOS file share. Recommended Instructor Preparation for Learning Activity Instructor Notes: Legion performs its scan/enumeration of shares in two phases. First, Legion performs a simple port scan looking for systems which respond to connection attempts on TCP port 139 (NetBIOS-ssn). Second, Legion reconnects to each system share that responded to the port scan in phase one with a more extensive probe. As each share is probed again, Legion once again establishes a NetBIOS-ssn connection over TCP port 139. The way this looks to the system is as follows: 9 LEGIONBOX01 *SMBSERVER TCP: D=139 S=2168 SYN SEQ=100114 LEN=0 WIN=8192 10 *SMBSERVER LEGIONBOX01 TCP: D=2168 S=139 SYN ACK=100115 SEQ=173595 LEN=0 WIN=8760 11 LEGIONBOX01 *SMBSERVER TCP: D=139 S=2168 WIN=8760 ACK=173596 ***Note*** Legion follows the sequence numbers accordingly. Ask the students if the incremental sequence numbers could be used for something other than just this scan. (ie session hijacking) Once Legion completes the three way handshake it initiates a NetBIOS session request to the destination system using “*SMBSERVER<20>” as the Called NetBIOS name. If the destination system accepts the NetBIOS session request it responds positively and the session is established. 12 LEGIONBOX01 *SMBSERVER NETB: D=*SMBSERVER<20> S=LEGIONBOX01<00> Session request 13 *SMBSERVER LEGIONBOX01 NETB: Session confirm Once this has been accomplished, the target ends the NetBIOS session but leaves the NetBIOS-ssn TCP connection in place to allow further communication between these two systems in the future. Instructor Notes: At this point the instructor should have at least two (2) target machines that have at least two (2) network shares configured. One should be password protected and the other should be left open. Make note of the IP addresses for the target machines to give to the students. A more realistic approach would be to give them a small range to scan so they can discover the shares. Have the students download and install the Legion software. Once the installation is complete, have the students begin their scan. Scanning Using Legion: When Legion is started the initial screen appears, and gives the user two scan types choose from, “Scan Range” and “Scan List”. The Scan Range option allows the user to scan a range of IP addresses up to an entire class B network. To perform this function the user simply has to check the Scan Range radio button, fill in the starting and ending IP addresses of the range they wish to scan, choose a connection speed, and click the Scan button. In order to scan a list of individual IP addresses, the user needs to check the Scan List radio button, then type each targets IP address into the Scan List box, then click add, select a connection speed, then finally begin the scan by clicking the Scan button. If the user has a large list of target IP addresses to scan, Legion allows importing a list of IP addresses from a standard text file by clicking the Import List button. ***No matter which scan type chosen the results are given in an Explorer-type view. Simply navigating this tree the user can now map any share by highlighting it in the left-hand panel and clicking the Map Drive button at the bottom of the screen.*** Legion will then automatically display the shares detected and present them in a format as seen in the picture above. Instructor Notes: At this point have the students expand the shares by clicking the “+” in the left pane. This will show all available shares that can be mapped as virtual drives on the students machine. Instructor Notes: Have the students click the Map Drive button and the share will be mapped on their machine. A confirmation will be given. Instructor Notes: Have the students verify the share by exploring My Computer. Instructor Notes: The students can then open and explore the share, and save files or copy files that they need. This is intended to show the students the inherent security risks of not only allowing network sharing, but by having no password protection on the shares. Using Legion to Perform a Brute-force on a password protected share: When you need to attempt a brute force password cracking attack against a NetBIOS share with share level access, you can initiate the Brute Force Password Cracking Tool by clicking the Show BF Tool button at the bottom of the screen. The Force Share dialog box will appear. The user must type the name of the target share in the Path dialog box and add one or more word lists to the Word Lists dialog box, then click the Start button. Legion will display a response informing the user whether the brute force attempt was successful or not. If a successful password crack is initiated, Legion will then map the share to the first available drive and let the administrator/hacker know. Instructor Notes: Show the event viewer logs from the server or target machine so the students become familiar with the pattern/fingerprint that a Legion attack leaves on the machine. This will help the future administrators identify the attack and allow then to fix the problem. Attack Signature The true signature of a Legion enumeration attempt, as well as many other enumeration attempts are inbound NetBIOS session TCP connections to TCP port 139. Unfortunately, Microsoft has not implemented a native capability into their platforms which will allow the monitoring and logging of network level events such at these. On systems the share enumeration component of Legion does result in the generation of a Privilege Use Success Event #576 in the Security Event Log, and the brute force password cracking tool results in the generation of Logon/Logoff Failure Events #529 (and potentially #539 if the account gets locked out) in the Security Event Log. Protect Against Legion For WinNT/2000/XP Systems: 1) 2) Prevent the anonymous user from connecting to a null session and enumerating system information by setting the RestrictAnonymous registry key. See Microsoft knowledge base article Q143474 for information regarding the implementation of this feature. If you are connected to a LAN and you must use NetBIOS file sharing, adhere to the Principle of Least Privilege when granting access to those shares. (i.e. Share only the directories that are absolutely required, make the share read only if possible, grant user level share access only to required individuals). 3) 4) Install a personal firewall, implement a security policy which denies inbound access to the NetBIOS over IP ports (TCP and UDP ports 135 through 139), and monitor the firewall logs for signs of illicit activity. Ensure that the account policy is configured to lock out all accounts after a small number of unsuccessful login attempts. For the Network: 1) Block all inbound network traffic destined for the NetBIOS over IP ports (TCP and UDP ports 135 through 139) at the perimeter firewall or perimeter router. Instructor Notes: At this time, have the students begin their scans. ITSY 1300 Hands-on Lab 1. Perform a Scan Range scan first. What is the range of the scan? ____________________________________________ 2. How many targets are identified in the scan? ____________________________________________ 3. How long did the scan take? ____________________________________________ 4. How many shares were found during the scan? ____________________________________________ 5. Once the scan was complete, were there any shares that had password protection? ____________________________________________ 6. Map a drive to the shares. Are you able to view My Computer and see your new share/ mapped drive? ____________________________________________ 7. Are you able to access that drive as if the mapped drive were on your machine? ____________________________________________ 8. What could be a potential threat associated with a share that is mapped? ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ 9. Choose your own IP range for a scan and list the range below. ____________________________________________ ____________________________________________ ____________________________________________ 10.Were any shares identified during this scan? If so, what were they? ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ 11.Are you able to map a drive to these shares? ____________________________________________ 12.Are you able to access the mapped drive that you just created? ____________________________________________ 13.From an Administrator point of view, what hazards does this share impose on the network? ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ 14.Are you allowed to copy or save from or to the mapped drives? ____________________________________________ 15.What hazards could this impose on the network? ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ 16.Perform a List Scan. What is/are the IP addresses of the scan? ____________________________________________ 17.How many targets are identified in the scan? ____________________________________________ 18.How long did the scan take? ____________________________________________ 19.How many shares were found during the scan? ____________________________________________ 20.Once the scan was complete, were there any shares that had password protection? ____________________________________________ 21.Map a drive to the shares. Are you able to view My Computer and see your new share/ mapped drive? ____________________________________________ 22.Are you able to access that drive as if the mapped drive were on your machine? ____________________________________________ 23.Try and copy a file to the shares. Was it successful? If yes, what advantages could this allow an intruder to do? ____________________________________________ ____________________________________________ ____________________________________________ ____________________________________________ 24.Choose your own IP range for a scan and list the range below. Then save the range as a text file. What is the name of the text file? ____________________________________________ ____________________________________________ ____________________________________________ 25.Were you able to scan that range using the text file? ____________________________________________ 26.In your own words, do you believe that network shares are a hazard or valuable tool that should continue to be utilized on a network regardless of the vulnerabilities?