Document 11478804
advertisement

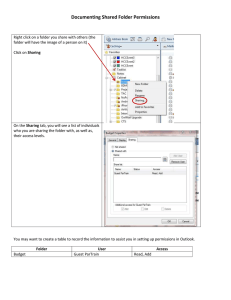
Instructor: Prof. Michael P. Harris, CCNA CCAI ITSY 2400 – Operating Systems Security Chapter 5 File, Directory, and Shared Resource Security Operating Systems Security - Chapter 5 File, Directory, and Shared Resource Security Chapter Overview In this chapter, students will learn how to configure directory, folder, and file security for Windows, Linux, NetWare, and Mac OS X. You will learn how to fine-tune this security for both common and unique circumstances. You will also learn about the specialized share permissions for Windows-based systems, used when folders are shared across a network through the FAT16/32 and NTFS file systems. Managing access to shared resources means learning how to configure and use security groups, which is another topic of this chapter. Some operating systems offer complex security group options and others, such as Mac OS X, offer automated options. Finally, you will learn how to use the effective permissions and effective rights tools in Windows and in NetWare to ensure that directory, folder, and file security is properly set and that there are no security holes. Chapter Objectives After reading this chapter and completing the exercises, students will be able to: Implement directory, folder, and file security Configure shared resource security, using share permissions in Windows Use groups to implement security Troubleshoot security Lecture Notes Directory, Folder and File Security Operating systems and directory services offer techniques to protect directories, folders, files, and other objects so that only the owners of the objects or specified accounts or groups can access them. This is accomplished through a collection of security properties sometimes cumulatively called a security descriptor in a directory service. In an operating system, a security descriptor, also referred to as an access control list (ACL) contains all information about access to a particular object. In a directory service, there are two components to an ACL or security descriptor; a discretionary access control list and a system access control list. A discretionary access control list (DACL) is a partial access control list of users, groups, and computers that are allowed or denied some form of permission to access an object. A system access control list (SACL) is a partial access control list that determines which, if any, events associated with an object are to be audited. Michael Palmer, GUIDE TO Operating Systems Security Thompson/Course Technology ©2004 Page 1 of 4 ISBN: 0-619-16040-3 Instructor: Prof. Michael P. Harris, CCNA CCAI ITSY 2400 – Operating Systems Security Chapter 5 File, Directory, and Shared Resource Security Each ACL for an object typically contains four categories of information: The user account(s) (or account groups) that can access the object The rights and permissions that determine the level of access The ownership of the object Whether specific events associated with an object are to be audited Each user account or group of accounts is assigned a type of access to an object, called a right or permission. Windows 2000, Windows XP, Windows Server, Linux, and Mac OS X use permissions, which involve privileges to access and manipulate resource objects. Also, in Windows 2000/XP/2003/2008, there are standard permissions and special permissions. In these systems, a standard permission is most frequently used and consists of the object permissions that are available by default. Special permissions are used when the default settings do not provide enough customization for the current security need. Windows Folder and File Security Windows and Windows Server can use attributes and permissions (S, H, A, & R) to control access to folders and files. The specific attributes and permissions are related to the file system used. When FAT16/32 is used, security is not as strong as with NTFS. From the standpoint of security and reliability, NTFS is a much better choice than FAT16/32 for any use, but especially for a system connected to a network. NTFS offers the ability to set standard and special permissions on folders and files for user accounts and for groups. NTFS supports the use of the Encrypting File System (EFS), and it enables disk quotas to be set on users and groups. FAT Folder & File -Attributes (SHAR) In FAT16 and FAT32, attributes are stored as header information with each folder and file, along with other characteristics including volume label, designation as a subfolder, date of creation, and time of creation. The folder and file attributes available in FAT16/FAT32-formatted disks are System, Hidden, Archive, and Read-only. NTFS Folder & File -Attributes and Security Folders and files on an NTFS-formatted disk also have the System, Hidden, Archive, and Read-only attributes, plus the Index, Compress, and Encrypt attributes. When you make a change to one of the attributes in the Advanced Attributes dialog box in a folder’s properties, you have the option to apply that change to only the folder and the files in that folder, or to apply the changes to the folder, its files, and all sub-folders and files within the folder. Index Attribute The NTFS index attribute is used to index the folder and file contents so that text, creation date, and other properties can be quickly searched, using the Search button in My Computer or Windows Explorer. Michael Palmer, GUIDE TO Operating Systems Security Thompson/Course Technology ©2004 Page 2 of 4 ISBN: 0-619-16040-3 Instructor: Prof. Michael P. Harris, CCNA CCAI ITSY 2400 – Operating Systems Security Chapter 5 File, Directory, and Shared Resource Security Encrypt Attribute A Windows encrypted folder or file uses Microsoft’s Encrypted File System (EFS), which sets up a private encryption key that is associated with the user account that encrypted the folder or file. Encrypted folders are listed in green within explorer. Configuring Folder and File Permissions In Windows, NTFS permissions control access to an object. To modify permissions, use the Add and Remove buttons on the folder properties Security tab. See Figure 5-3 on page 201 of the text to see how to change which users and groups have permissions to a folder. Table 5-1 on page 202 of the text, lists the folder & file permissions supported by NTFS. Notice in Figure 5-3 that all of the Allow boxes for permissions are checked and deactivated (grayed out). These are inherited permissions, which mean that the same permissions on a parent objectthe Program Files folder, in this caseapply to the child objects, such as files and subfolders within the parent folder. Quick Reference Discuss the general steps used to change the inherited permissions as listed on pages 202 and 203 of the text. Table 5-2 on page 204 of the text lists the NTFS special permissions. Quick Reference Discuss the general steps you would use to take ownership of a folder, using an account with Administrator privileges shown on pages 205-206 of the text. UNIX/Linux Directory and File Security (-rwxrwxrwx) u g o [a] UNIX/Linux files are assigned a combination of three sets of three permissions: read, write, and execute (rwx). Executable files can have a special set of permissions called Set User ID (SUID) and Set Group ID (SGID). When either of these is associated with an executable file, the group or other members who run it have same access as the user(owner). Permissions (u, g, o, [a]) are granted on the basis of four criteria: ownership (user), group membership, other, and all. Permissions are set up using the chmod command in UNIX & Linux. The chmod command has two different formats, symbolic and octal. In the symbolic format, you specify three parameters: (1) who has the permission (u, g, o, a), (2) the actions to be taken on the permission (+ or -), and (3) the permission (r, w, x). Example: chmod ug+x file.ext adds execute permission to user and group accounts. The octal permission format is more complex, because it assigns a number on the basis of the type of permission and on the basis of user(owner), group, and other all is omitted from this scheme. Each permission setting is calculated as: read = 4, write = 2, and execute = 1. For example the command; chmod 754 file.ext gives rwx (4+2+1=7) user(owner) permissions, r-x (4+1=5) group permissions, and r-- (4) to all other(s). Use the ls –l command to view the permissions for a group of files in a directory. Figure 5-5 on page 208 shows the permissions in /etc directory (ls –l /etc), which contains configuration files used by the system, including the passwd and shadow files. Table 5-3 on page 209 of the text lists system directories used in Linux. Ownership of a folder or file can be changed by using the chown command from the root account. Michael Palmer, GUIDE TO Operating Systems Security Thompson/Course Technology ©2004 Page 3 of 4 ISBN: 0-619-16040-3 Instructor: Prof. Michael P. Harris, CCNA CCAI ITSY 2400 – Operating Systems Security Chapter 5 File, Directory, and Shared Resource Security NetWare Directory and File Security In NetWare, access to files and directories is controlled through: Attributes associated with files and directories Access rights granted to trustees Netware attributes follow the same principle as the attributes used in Windows-based systems, in that they are flags associated with a directory or file that manage access and other properties, such as information showing that a directory or file needs to be backed up. Table 5-4 on page 211 lists the attributes used for files and Table 5-5 on page 212 of the text shows the attributes used for directories. NetWare access rights are similar to permissions in Windows and UNIX/Linux systems. NetWare access rights give privileges to access directories and files. Access rights are associated with specific users or groups, called trustees, through a directory’s or file’s discretionary access control list. Table 5-6 on page 213 of the text lists the access rights that you can configure for a directory or folder using the ConsoleOne tool. Quick Reference Discuss the general steps for adding an inherited rights filter as illustrated on page 214 of the text. Mac OS X Folder and File Security There are two ways to configure folder and file permissions in Mac OS X: through commandline commands and through setting the Get Info properties of a file. You configure permissions through a terminal window, using the same commands and settings that apply to Linux. (Mac OS X is a variant of Free BSD Linux) Both the chmod and the chown commands apply equally well to Mac OS X. Figure 5-9 on page 215 of the text illustrates using the ls –l command to view permission settings, and then using chmod to change those settings. Table 5-7 on page 216 of the text shows the permissions that can be set for each of these categories. Discussion Questions 1) Discuss the advantages and/or disadvantages of using the NTFS file system over FAT16 or FAT32. 2) Discuss the similarities of creating groups in UNIX/Linux and Windows (if any). Additional Activities 1) Compare the methods for sharing printers in UNIX/Linux, Windows, and Mac OS X and chart the differences. 2) Compare the methods used for creating groups in UNIX/Linux, Windows, and Mac OS X and chart the differences. Michael Palmer, GUIDE TO Operating Systems Security Thompson/Course Technology ©2004 Page 4 of 4 ISBN: 0-619-16040-3