CRYPTOGRAPHY AND THE DIFFIE–HELLMAN Presentation by CDT Ashcraft
CRYPTOGRAPHY AND THE
DIFFIE–HELLMAN KEY EXCHANGE
Presentation by CDT Ashcraft
ORIGIN
Following WWII, tensions between the USSR and the United States necessitated a way to both launch and defend against nuclear attacks from Intercontinental Ballistic Missiles (ICBM)
An important defense: the semiautomatic ground environment, automated system of 100 long-distance radars that transmitted tracking data, fed into primary warning center in Colorado. Machine to machine communication allowed operators to make split-second decisions using information transmitted and processed automatically by computers.
Computer Networking, Finances, Education.
Internet grows, problem emerges.
ENCRYPTING DATA
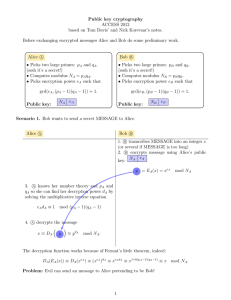
Required sharing a secret number, known as the “Key”
Symmetric key crypto lets two parties share secret messages as long as they already have a shared key
How can two people who have never met agree on a secret shared key without a third party, who is listening, also obtaining a copy???
Scenario: Alice and Bob are communicating on an unsecured network.
EVE THE EAVESDROPPER
Eve is an attacker who can see Alice and Bob’s messages
She cannot modify them
She is a Passive attacker
Examples:
Unencrypted wifi users
Government
Internet provider
Someone else on the same network
Alice and Bob need a way to encrypt messages, but how do they choose?
MODULAR ARITMATIC
We need a numerical procedure that is easy in one direction and difficult in the opposite direction
mod p
Clock Arithmetic
Pick a prime modulus such as 17
Use a prime root of 17, such as 3
3^x mod 17 = [0,16] equally likely
Reverse procedure is difficult to find
Discrete Logarithm
ONE WAY FUNCTION
To solve, it is easy with small numbers, but with big number it becomes impractical
Using a prime modulus hundreds on digits long, it could take thousands of years to solve using computers
The strength of a One Way Function is based on the time needed to reverse it.
Bob and Alice each come to a solution that is not known to Eve, an eavesdropping attacker