Security Exercise 9
advertisement

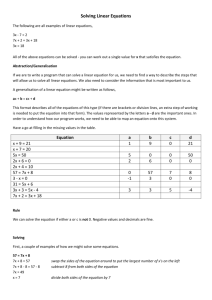
Security Exercise 9
Part I. Initial Set-up
The program you will use today is named note2.c and this program has already been placed on your machine in the EC310code
folder under your home directory. Copy this file to the work directory by carefully entering the following at the home
directory prompt:
midshipman@EC310:~ $
cp
Make sure you are at your home directory!
ec310code/note2.c
work
Enter this!
Verify that you have note2.c in your work directory by changing to the work directory:
cd work
and then listing the files in the work directory:
ls
If you do not have note2.c in your work directory STOP and ask your instructor or lab tech for help. Otherwise, proceed to Part
2.
Part II. A Truly Useful Program
Before looking at the code, let's discuss the motivation for this program. Here is the scenario: You are the Company Commander for
your Company. The intent of the program is to allow anyone in your Company (who, of course, all have Linux accounts) to send you
a note. All the notes that are sent to you by company-mates will be written into the file /tmp/notes, one after another. The idea is
that you can read all the notes that midshipmen in your Company send you, but the midshipmen cannot read the notes sent by anyone
else (in fact, they can’t even read their own notes once submitted).
To make this more concrete, you might, at the start of the day, write a note (to yourself) that says
Notes received today:
Then, later in the morning, you might get a note from instructor that says:
Nice job applying your Cyber2 skills in the Hall – keep it up..
Then, in the afternoon, your friend mia might send you a note that says:
The wardroom fridge might be on the fritz again.
In the evening, then, you could check the file named /tmp/notes and see all the notes that were left for you during the day. For
this example, you would enter cat /temp/notes and see:
Notes received today:
Nice job applying your Cyber2 skills in the Hall – keep it up.
The wardroom fridge might be on the fritz again.
But your program is even better than this! Your program includes the user ID of everyone who adds a note! Recall that the user IDs
for the users on your system are:
root
0
mia
500
joe
501
instructo
998
midshipman 999
All right! Time to look at the code!
1
1.
2.
3.
4.
5.
6.
7.
8.
9.
10.
11.
12.
13.
14.
15.
16.
17.
18.
19.
20.
21.
22.
23.
24.
25.
26.
27.
28.
29.
30.
31.
32.
33.
34.
#include<stdio.h>
#include<stdlib.h>
#include<string.h>
#include<fcntl.h>
#include<sys/stat.h>
int main( int argc , char *argv[ ] )
{
int fd ;
int userid;
char *buffer ;
buffer = (char *)malloc(100);
strcpy( buffer , argv[ 1 ] );
strncat( buffer , "\n" , 1 );
fd = open("/tmp/notes", O_RDWR|O_CREAT|O_APPEND , S_IRUSR|S_IWUSR );
userid = getuid( ) ;
write( fd , &userid , 4 );
write( fd , "\n" , 1 );
write( fd , buffer , strnlen( buffer ) );
free( buffer );
close( fd );
}
In the explanation that follows, let's presume that the executable file is named ./note2.exe (instead of ./a.out) and lets
presume that the user named mia runs the program by entering
./note2.exe
"What is for evening meal?"
Notice that argv[1] is the string:
"What is for evening meal?"
Line 9 declares and integer named fd that will later hold the file descriptor for the file /tmp/notes. Line 11 declares an integer
named userid that will later hold the user ID for the user entering a particular note.
Lines 13 and 15 allocate space for 100 bytes on the heap to hold a string of 100 characters. The name of the string is buffer (so
buffer points to the first character in the string). Line 17 copies argv[1] to buffer, so, in our example, buffer will now hold
the string "What is for evening meal?" (followed by the NULL).
Line 19 appends a newline character to buffer (and this occurs before the NULL), so, after line 19, buffer contains the string
"What is for evening meal?\n" followed by the NULL.
Line 21 assigned a file descriptor to the file named "/tmp/notes" and places the file descriptor in the integer variable named fd
that was declared on line 9. From this point onward, whenever we wish to refer to the file "/tmp/notes" we will use the file
descriptor fd.
Line 23 contains a function we have not seen before: the function getuid( ). This function returns the ID of the user running the
program. Recall that in our example, the user mia is running the program, so getuid( ) will return the value 500, which is mia's
ID.
So, line 23:
userid = getuid( ) ;
2
will assign the value 500 to the integer variable userid which was declared on line 11.
Up to this point in the program, information has been placed on the heap (in the string named buffer), but nothing yet has been
written to the file /tmp/notes. Line 25 performs the first operation to write to the file, and notice that what is written is the user's
ID followed by (on line 27) a new line character. Then, on line 29, we write the contents of buffer to the file. So, at this point, the
file /tmp/notes contains:
500
What is for evening meal?
Finally, line 31 frees space on the heap and line 33 closes the file.
Now, suppose an hour later, user instructor (whose ID is 998) runs the program by entering:
./note2.exe
"When is the next parade?"
After instructor is done running the program, the file "/tmp/notes" contains:
500
What is for evening meal?
998
When is the next parade?
So when you, the Company Commander, review the file at the end of the day, you can see all the notes left for you and, just as
important, who it is that left each of the notes.
Part III. Practice Running the Program
Let's compile the program saving the machine language file under the name note2.exe by entering:
gcc
–g
–o
note2.exe
note2.c
Then add the first line to the file /tmp/notes by entering:
./note2.exe
"Notes received today:"
Examine the file /tmp/notes by entering:
cat /tmp/notes
Notice that your ID number is garbled! That is because you are attempting to print out the integer 999 (your ID number) as a
character. We'll address this later.
Now, check permissions for note2.exe and /tmp/notes by entering by entering:
ls
–l
note2.exe
/tmp/notes
You should see:
Question 1: Who owns the file note2.exe ?
Question 2: List all of the users who are able to write to the file named /tmp/notes.
You tell all of your company-mates that they have execute permission for the file note2.exe, and that they are to start sending you
messages during the day, and you will review their messages and reply each evening.
3
The first evening arrives, you look at the file /tmp/notes and you see only your message (Notes received today:). Your
company-mates mia and joe insist that they sent you messages during the day. Hmm…it seems that messages left by other
individuals are not being saved, even though everyone has permission to execute the program note2.exe.
Question 3: Why are other users not experiencing success with this program?
Question 4: What command should you enter to remedy the problem you noted in Question 3? (Do it!)
(Hint: if you answered Question 4 correctly, then, upon entering ls –l note2.exe you should see
Now, let's see how the program would look from mia's perspective.
First, switch to user mia by entering
sudo su mia
Now, the prompt should indicate that you are the user named mia.
Cool - You're mia!!!
Now, noticing that you are mia, run the program by entering:
./note2.exe
"A message from Mia."
Now, as mia, examine the file /tmp/notes by typing:
cat /tmp/notes
Question 5: Was mia successful in looking at the file /tmp/notes? Why/Why not?
Switch back to being the user named midshipman by entering
exit
Now, examine the file /tmp/notes by typing:
cat /tmp/notes
Question 6: Was the message from mia saved in the file?
Question 7: Is the following statement true or false:
Only the user named midshipman can freely read from or write to the file named /tmp/notes. Other users are
permitted to write to the file, but only in a very restricted sense: via the use of the program note2.exe.
Enter the command
ls –l /tmp/notes
Your friend sees the result and says: I see that only the file's owner, midshipman, is able to read or write to the file. But we just saw
4
that mia was able to write to the file? How is that possible?
Question 8: How would you answer your friend's question?
Part IV. Autopsy of the File Named /tmp/notes
First, let's delete the file current file named /tmp/notes so that we can start fresh.
rm
/tmp/notes
Recall that rm stands for "remove." Verify that the file has been removed by typing:
cat /tmp/notes
You should see the message: No such file or directory
From your work directory, carefully enter the following at the command prompt:
cp
../ec310code/notes
/tmp
Now, recall that you are the user midshipman. Not just any midshipman. The Company Commander! You are very proud of
having reached this position. Your people love you. You check the messages left by your company-mates by typing
cat /tmp/notes
and you see:
ARGGHH! You want to have a talk with the midshipman who sent you the next-to-last note. Was it your friend Mia? Or, perhaps it
was Joe? We need to find out who it is! That midshipman needs to be counseled on respectful communication and constructive
feedback! Haven’t we learned anything in this leadership laboratory?!
In Part III above we mentioned that the ID numbers are garbled. But we can look at the file in hexadecimal.
Enter:
hexdump –C /tmp/notes
You should see this:
5
Examining the hexdump of the file /tmp/notes , our goal is to determine who left the note
You suck – worst CC EVER.
For convenience, the ASCII table is presented below.
Let’s go to the top of the hex dump. We know that the first text we have is: Notes received today:
Let’s focus just on the capital N and small o (i.e., the first two letters of Notes received today)
6
Question 9:
Determine how the text No would be stored in memory in hexadecimal notation.
Locate these values (from Question 9) in the hex code display.
Question 10:
According to the ASCII table, what is the meaning of the byte that immediately precedes No in the
hexdump?
Question 11:
The first four bytes in the hex dump are e7 03 00 00. Since, for every note that is entered, the user id
number of the note writer, a new line, and the actual note are written to the /tmp/notes file, what is the
significance of these first four bytes?
Question 12.
Since the first four bytes are stored in little-endian order, rewrite these four bytes in their actual order.
Question 13.
Convert your answer to Question 12 to a decimal integer.
Question 14.
What is the significance of this value? (Hint, look at the top of the first page of this Security Exercise.)
Question 15.
Use all your sleuthing abilities to find the hexadecimal value associated with the unpleasant person who left
the note
You suck – worst CC EVER.
What is the hex value of the user id number of the person who left this note?
Question 16.
Convert your answer for Question 15 to a decimal value.
Question 17.
Who gets fried?
7
Security Exercise 9 Answer Sheet
Name:
Question 1:
Question 2:
Question 3:
Question 4:
Question 5:
Question 6:
Question 7:
Question 8:
Question 9:
Question 10:
Question 11:
Question 12:
Question 13:
Question 14:
Question 15:
Question 16:
Question 17:
8